5.3 Managing the Identity Directory Service User Identity Stores
(IDS) is a flexible and configurable service used by Access Manager as the means for accessing multiple identity data stores. The purpose of IDS is to allow the management of users or groups from identity stores not deployed with Access Manager itself.
The following sections contain the details.
5.3.1 Identity Directory Services
offers a consistent and rationalized technology to access identity stores that eliminates redundant configurations and simplifies Identity Management operations.
IDS provides the following benefits:
-
Support for different types of user directories including integration with native user/password state managed by the directory.
-
Consistent administration user interface and a paradigm for working with different identity stores across Oracle Identity Management components.
-
Built in failover and load balancing capabilities.
-
Logical to physical attribute mapping and entity relationships.
The following list of directory servers are among those supported.
-
Microsoft Active Directory
-
Novell eDirectory
-
Oracle Directory Server Enterprise Edition
-
Oracle Internet Directory
-
Oracle Unified Directory
-
Oracle Virtual Directory
-
OpenLDAP
-
IBM Tivoli Directory Server
-
WebLogic Server Embedded LDAP
Note:
Oracle recommends that you use the Profiles to access identity data stores rather than the legacy OAM ID Stores function as it will be deprecated in a future release.
Figure 5-3 is a screen capture of the console page.
Figure 5-3 Identity Directory Service Console Page
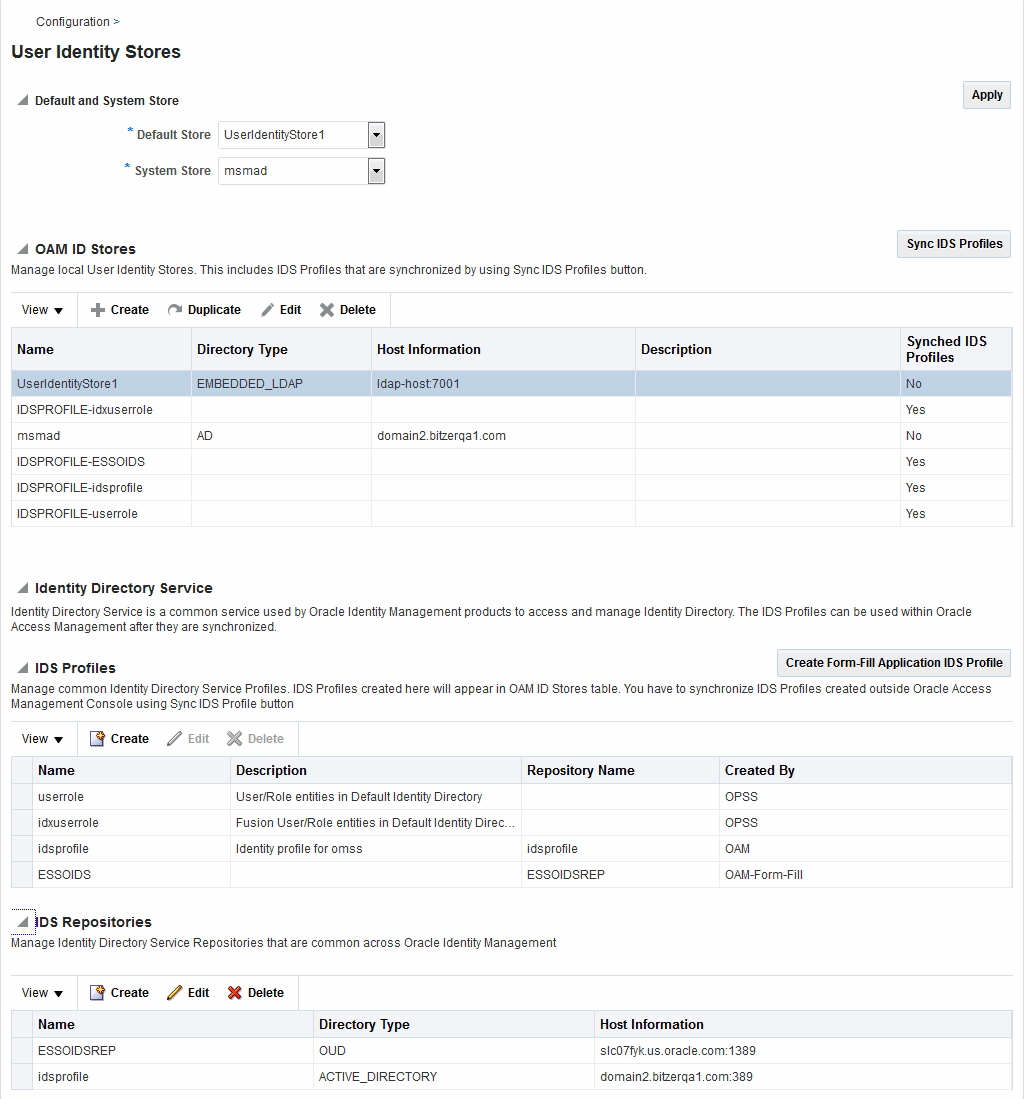
Description of "Figure 5-3 Identity Directory Service Console Page"
Note:
Note this page contains the configuration panel for the legacy OAM ID Stores. Oracle recommends that you use the Profiles to access identity data stores rather than the legacy OAM ID Stores function as it will be deprecated in a future release.
Configuring an Identity Directory Service store involves configuring parameters for an IDS Profile and an IDS Repository. The IDS Profile specifies the full scope of traits for a particular type of identity store. It is the logical configuration for the repository and contains the following data.
-
Entity definition
-
Entity relationship definition
-
Default operational configuration (including the tenant search/create base, the tenant filter, timeouts and cache configuration)
The IDS Repository configuration defines the actual location of the store. The IDS Repository is a physical configuration that containing the following data.
-
Connection details (including the host machine, port number and credentials)Connection pool detailsHigh-availability/failover configurationEntity attribute mapping
5.3.2 Creating an Identity Directory Service Profile
You can create an profile form the Configuration console.
To create:
-
At the top of the Oracle Access Management Console, click Configuration.
-
In the Configuration console, click User Identity Stores.
-
In the IDS Profiles section, click Create.
The Create IDS Profile page is displayed as in Figure 5-4.
-
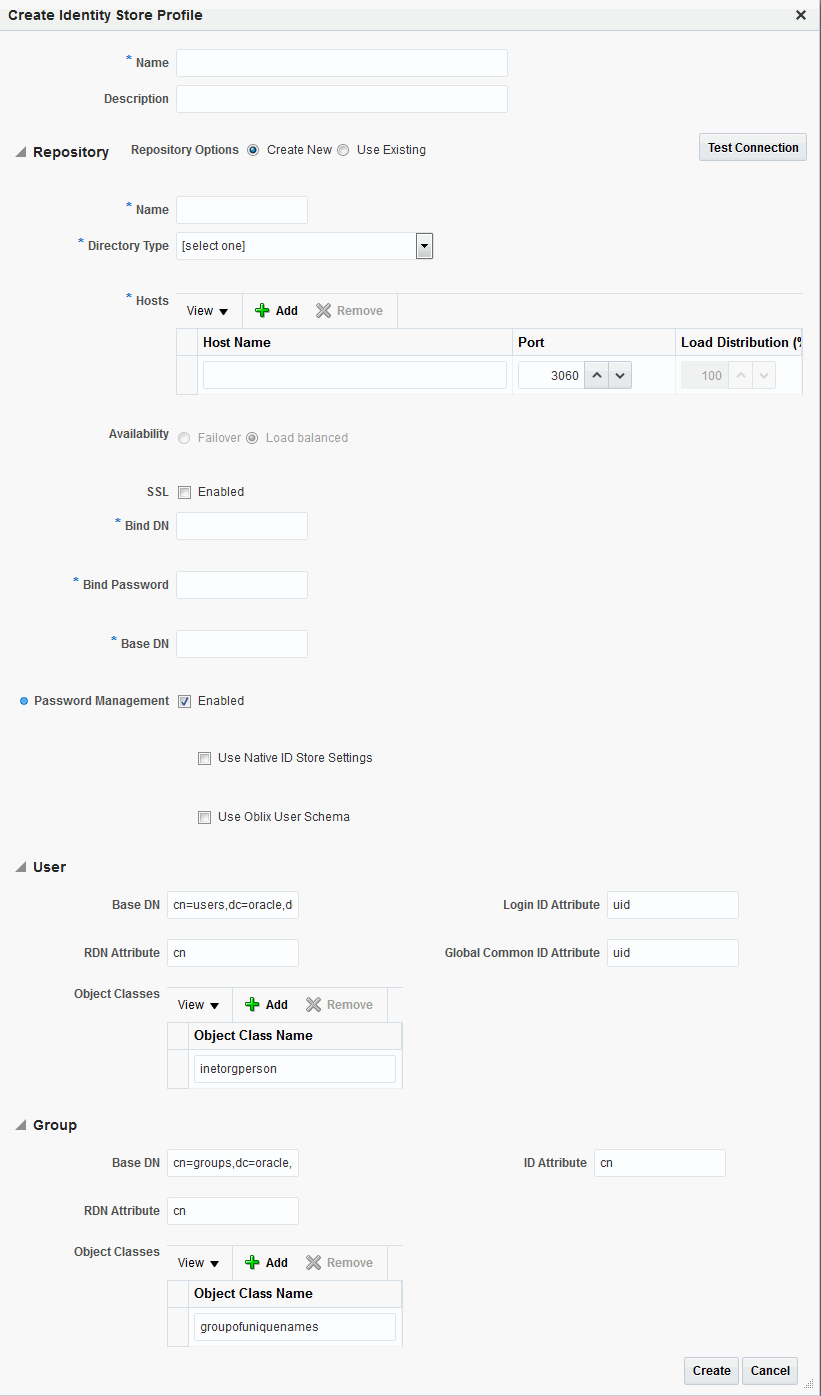
Provide the following values for the new profile.
-
Name - Type a unique name for this User Profile Service Provider.
-
Description - (Optional) Type a short description that will help you or another Administrator identify this service in the future.
-
-
Configure the Repository properties by selecting Create New or Use Existing.
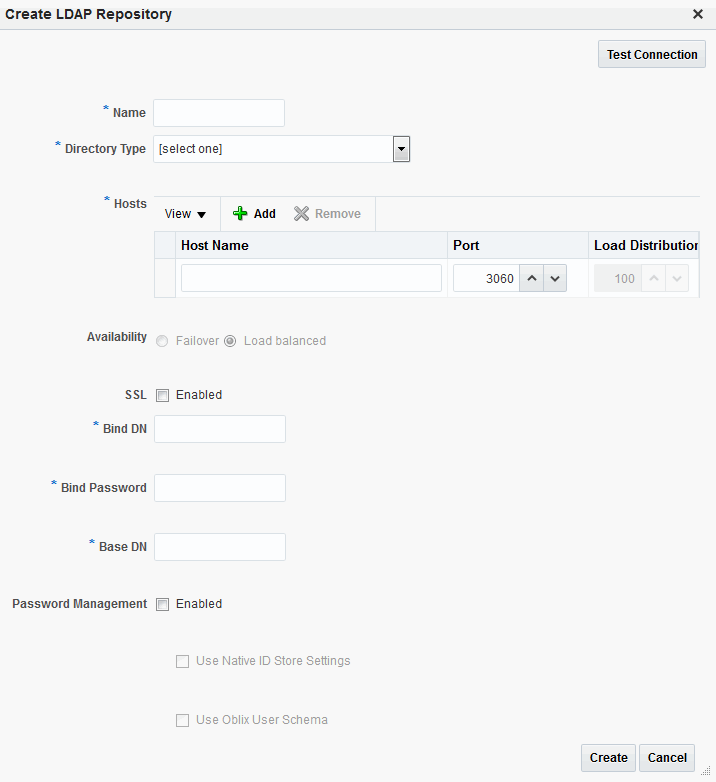
Create New defines a new Repository object (that is, a reference to an LDAP directory server) for the Identity Directory Service connection. Click Test Connection after you have defined the values in the Repository section to verify they are correct. This option is only available when defining a new Identity Directory Service connection. Use Existing allows you to choose a previously defined Repository object by selecting it from the drop down menu.
-
(Repository) Name - Enter a new unique name to create, or choose an existing one from the menu. After entering a new name, configure properties for the Identity Directory Service connection.
-
Directory Type - Select the type of directory server software hosting the Repository; for example, Microsoft Active Directory or Oracle Internet Directory. If your directory is not listed, leave this field empty. If you are not defining a new Identity Directory Service connection or creating a new repository, this field is read-only.
-
Host Information - Contains information about the host computer on which the Identity Directory Service Repository is located. Add multiple hosts if the directory server is part of a cluster. Click Add to add a new host to the table. In the Host Name column type either the IP Address or the name of the computer (or virtual computer) on which the Directory server is running. In the Port column, type the port number that the directory server is configured to use. If the hosts are part of a cluster, in the Load Distribution column type the load amount as a percentage that should be directed to each host. For multiple hosts, the amount should add up to 100%. To delete a host, select its row in the table and click Remove. If you are not defining a new Identity Directory Service connection or creating a new repository, this field is read-only.
-
Availability - Choose Failover if the cluster is configured for failover operation, or choose Load balanced if the cluster distributes the load across multiple hosts. This field is read-only if you are using an existing repository.
-
SSL - Select Enabled if the connection is configured for SSL. (See the Securing Applications with Oracle Platform Security Services for SSL configuration details.)
Note:
Follow this procedure to add the SSL certificates required for setting the TLS connection.
-
Create the LibOVD keystore by running this command.
MW_HOME/oracle_common/bin/libovdconfig.sh -host WLS_ADMIN_HOST -port WLS_ADMIN_PORT -userName weblogic -domainPath WLS_DOMAIN_PATH -createKeystore -contextName ids
Enter the AdminServer password and the password used for the LibOVD keystore when requested.
-
Import the OID server certificate into the LibOVD keystore.
keytool -importcert -keystore DOMAIN_HOME/config/fmwconfig/ovd/ ids/keystores/adapters.jks -storepass KEYSTORE_PASSWORD -alias ALIAS_NAME -file FULL_PATH_TO_CERTFILE -noprompt
-
-
Bind DN - Type the distinguished name (DN) of the LDAP Administrator used to authenticate to the Directory server.
-
Bind Password - Type the Bind DN password used to authenticate to the Directory server.
-
Base DN - Type the base distinguished name (DN) where User and Group data is located.
-
Password Management - selecting Enable Password Management enables password policy enforcement against the attribute values listed in Table 5-4. The corresponding options in the password policy must be configured as well.
-
-
Configure the User properties to configure the LDAP User object in Mobile and Social User Profile services.
Note:
These fields are read-only if using an existing Identity Directory Service connection.
-
Object Classes - Click Add to add a custom object class that represents people in an organization as defined on your directory server.
-
RDN Attribute - Type the relative distinguished name attribute (for example, cn) designated for the User object on the directory server.
-
Base DN - Type the base DN (in LDAP form) for the User object on the directory server.
-
Login ID Attribute - Type the LDAP attribute from which the login ID specifying the User will be extracted.
-
Global Common ID Attribute - Type the global common user ID attribute.
-
-
Configure the Group properties to configure the LDAP group object in Mobile and Social User Profile services.
-
Object Classes - Click Add to add a custom object class that represents a group of people in an organization as defined on your Directory server.
-
RDN Attribute - Type the relative distinguished name attribute (for example, cn) designated for the Group object on the directory server.
-
Base DN - Type the base DN (in LDAP form) for the Group object on the directory server.
-
ID Attribute - Type the LDAP attribute from which the ID designated for the Group object will be extracted.
-
-
Click Create.
The profile is displayed in the IDS Profiles table.
5.3.3 Editing or Deleting an Identity Directory Service Profile
To edit or delete an IDS Profile, select the name in the table and click Edit or Delete in the tool bar.
Editing the profile allows for additional configuration properties for the Identity Directory Service connection.
-
Name - Choose an Identity Directory Service connection to associate with the User Profile Service Provider from the drop down menu.
-
If you choose either of the default Identity Directory Services (either
userroleoridxuserrole) you cannot view or edit the configuration values. -
If you choose an Identity Directory Service connection that you or another Administrator created, you can view and edit the configuration values as needed.
-
-
General and Repository - Use the fields under this tab to edit the Directory Service and Repository configuration values that Mobile and Social uses to connect to the Directory Service.
-
Repository Name - Choose from the menu a repository to associate with the Identity Directory Service connection. After choosing a repository, configure its properties using the following form fields.
-
Directory Type - Displays the type of Directory server software hosting the Repository, for example Microsoft Active Directory, Oracle Internet Directory, and so on. This field is read-only.
-
Host Information - Displays information about the host computer where the Identity Directory Service Repository is located. Add multiple hosts if the Directory server is part of a cluster. Click Add to add a new host to the table. In the Host Name column type either the IP Address or the name of the computer (or virtual computer) that the Directory server is running on. In the Port column, type the port number that the Directory server is configured to use. If the hosts are part of a cluster, in the Load Distribution column type the load amount as a percentage that should be directed to each host. For multiple hosts, the amount should add up to 100%. To delete a host, select its row in the table and click Remove. If you are not defining a new Identity Directory Service connection or creating a new repository, this field is read-only.
-
Availability - Choose Failover if the cluster is configured for failover operation, or choose Load balanced if the cluster distributes the load across multiple hosts. This field is read-only if you are using an existing repository.
-
SSL - Select Enabled if the connection is configured for SSL. Otherwise clear the option box. See SSL in Creating an Identity Directory Service Profile for information on how to add the SSL certificates required for the TLS connection.
-
Bind DN - Type the distinguished name (DN) of the LDAP Administrator used to authenticate to the Directory server.
-
Bind Password - Type the Bind DN password used to authenticate to the Directory server.
-
Base DN - Type the base distinguished name (DN) where User and Group data is located.
-
Password Management - selecting Enable Password Management enables password policy enforcement against the attribute values listed in Table 5-4. The corresponding options in the password policy must be configured as well.
-
-
Entity Attributes - Use the fields under this tab to view or edit the attributes that Mobile and Social uses to navigate the corporate directory service schema. Click Add to add an attribute to the table or click Remove to delete an attribute.
-
Name - The attribute name.
-
Physical Attribute - The name of the corresponding physical attribute type in the underlying Repository.
-
Type - The attribute's data type.
-
Description - A brief description of the attribute.
-
Sensitive - Select to mark that the attribute contains sensitive information such as a password.
-
Read-only - Select to protect the attribute from modification.
-
-
Entities / User Properties - Use the fields under the User sub head to configure how Mobile and Social interacts with the User entities on the LDAP server.
-
Create Base - Specifies the base DN (the top level of the LDAP directory tree) at which Users are defined.
-
Search Base - Specifies the search base DN for Users. Only entries at or below the search base DN are considered when processing the search operation.
-
Create Object Classes - Specifies the object class under which attributes associated with a person are stored.
-
RDN Attribute - Specifies the relative distinguished name attribute, for example cn.
-
ID Attribute - Specifies the attribute that uniquely identifies the User, such as the uid attribute or the loginid attribute.
-
Filter Object Classes - Specifies the object class by which to filter.
-
Attributes Configuration - Specify the User attributes that should be available to, and searchable by, the User Profile Service Provider.
-
Used - Specifies if the attribute is used for Users in the directory service.
-
Attribute Name - Specifies the name of the attribute as defined on the Entity Attributes tab.
-
In Results - Select if the specified attribute should be returned in search results.
-
Searchable - Select if the specified attribute should be available for search operations.
-
Search Operator - Select a search operator from the menu to restrict how the specified attribute is searched.
-
-
Operations Configuration - Select from Create, Update, Delete, and Search to enable those operations at the User entity level. Clear the option boxes to disable them.
-
-
Entities / Group Properties - Use the fields under the Group sub head to configure how Mobile and Social interacts with the Group entities on the LDAP server.
-
Create Base - Specifies the base DN (the top level of the LDAP directory tree) at which Users are defined.
-
Search Base - Specifies the search base DN for Groups. Only entries at or below the search base DN are considered when processing the search operation.
-
Create Object Classes - Specifies the object class under which attributes associated with a Group are stored.
-
RDN Attribute - Specifies the relative distinguished name attribute; for example, cn.
-
ID Attribute - Specifies the LDAP attribute that uniquely identifies the Group.
-
Filter Object Classes - Specifies the object class by which to filter.
-
Attributes Configuration - Specify the Group attributes that should be available to, and searchable by, the User Profile Service Provider.
-
Used - Specifies if the attribute is used for Users in the directory service.
-
Attribute Name - Specifies the name of the attribute as defined on the Entity Attributes tab.
-
In Results - Select if the specified attribute should be returned in search results.
-
Searchable - Select if the specified attribute should be available for search operations.
-
Search Operator - Select a search operator from the menu to restrict how the specified attribute is searched.
-
-
Operations Configuration - Select from Create, Update, Delete, and Search to enable those operations at the Group entity level. Clear the option boxes to disable them.
-
-
Relationships - Use the fields under this tab to configure the relationship between attributes for this Identity Directory Service.
-
Name - The relationship name.
-
(From) Entity - Choose User to select from User attributes or choose Group to select from Group attributes in the (From) Attribute column.
-
(From) Attribute - Choose the attribute from which you are mapping.
-
Relation - Choose the menu option that describes the relationship between the specified attribute in the From column and the specified attribute in the To column.
-
(To) Entity - Choose User to select from User attributes or choose Group to select from Group attributes in the (To) Attribute column.
-
(To) Attribute - Choose the attribute to which you are mapping.
-
Recursive - Select if the relationship extends down the directory tree to include nested child entities or up the directory tree to include parent entities.
-
-
Relationship Configuration - Type the URI segment used to access the corresponding column in the Identity Directory Service. Use Add to add a new relationship or Remove to remove a configured relationship.
-
Access URI - Type a URI segment that will be used to access a corresponding data column in the Identity Directory service. For example, if
memberOfis the Access URI, then:http://host:port/.../idX/memberOf
would be the URI to access related entities of an entity with ID
idX. -
Identity Directory Service Relation - Choose the Directory Service relationship that is to be accessed by the Access URI segment. You can configure relationships on the Relationships tab in the Identity Directory Service configuration section provided that the Identity Directory Service is not the pre-configured UserProfile Identity Provider. (You cannot configure Identity Directory Service relationships for the UserProfile Service Provider.)
-
Entity URI Attribute - Type the JSON attribute name to be used in the URI response sent from the Mobile and Social server. For example, if person-uri is the specified entity URI attribute, the URI response would be as follows:
{ {"person-uri":uriY1, ...}, {"person-uri":uriY2, ...}, ... }where
uriY1anduriY2are the direct URIs to access each of the related entities. -
Scope for Requesting Recursion - Use Scope attribute values with the scope query parameter to retrieve a nested level of attributes in a relationship search. To access related entities recursively, type the value to be used. The Mobile and Social default configuration uses two scope attribute values:
toTopandall. If the Scope for Requesting Recursion value is the attribute valueall, then the following REST URI example is used to make the request:http://host:port/.../idX/reports?scope=all
In this example, the URI returns the entities related to the entity with ID
idX, as well as all further related entities.
-
5.3.4 Creating a Form-fill Application Identity Directory Service Profile
To create an Identity Directory Service Profile for a Form-fill Application, click the Create Form-fill Application IDS Profile button on the left of the User Identity Stores console page.
(See Figure 5-3.)
Creating an Identity Directory Service Profile and Editing or Deleting an Identity Directory Service Profile contain definitions for most of the Form-fill attributes. Additional definitions for the Entity Search Bases section specific to this type of profile are listed below.
-
User Search Base - Full DN for the node at which enterprise users are stored in the directory; for example, cn=Users,realm_DN.
-
App Template Search Base - Full DN for the node from which searches for the Application Templates will begin.
-
Top Search Base - Full DN for the node from which searches will begin; for example, cn=realm_DN.