42.1 Typical Token Ecosystem
A typical environment where security tokens, based on the security model required, are used to serve an end goal is known as typical security token ecosystem.
The abstract model has been chosen because the requirements placed on Security Token Service must support such models. The phrase security token ecosystem is used to represent a typical environment where security tokens are in use. In such environments the security token, based on the security model required for the environment, could be used to serve an end goal such as to enable brokered trust or single-sign-on and so on. Regardless of the environment and the type of security token, several aspects are common across all models, as shown and described here.
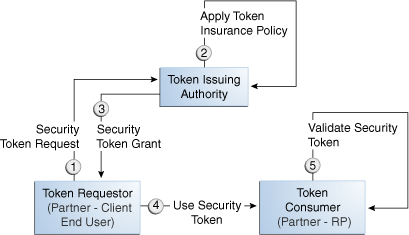
Figure 42-1 illustrates a typical token ecosystem, which includes: Token Issuing Authority, Token Requestor, Token Consumer, and the Security Token.
42.1.1 Actors and Process Overview: In a typical token ecosystem
The following process describes a typical environment where security tokens are in use:
-
The Token Requestor places a request for a security token at the Token Issuing Authority.
This security token is required to communicate and request access to a service provided by a Service Provider (a Token Consumer who accepts the security token).
-
A Token Requestor could be a Partner of the Token Issuing Authority (generally registered with the Token Issuing Authority).
-
A Token Requestor could be an End User (generally not registered with the Token Issuing Authority).
-
-
The Token Issuing Authority (Access Manager and Security Token Service, for example) receives and processes the security token request and returns a security token, as follows:
-
Authenticate the input credentials.
-
Authorize the security token request based on a Token Issuance Policy that specifies which Token Requestors are authorized to request a security token for a given Token Consumer.
-
-
The Token Consumer (typically a service provider).
-
Accepts the security token as part of the service request and provides service based on the validity of the input security token.
-
Validates the input security token with Token Issuing Authority.
Note:
A Token Consumer is typically a registered Partner of the Token Issuing Authority. A Token Consumer is also known as a Relying Party, because it trusts and relies on the Token Issuing Authority for Token Requestor authentication. Token Consumers (Relying Party Partner) are Web Applications (for Access Manager, Security Token Service is the Token Issuing Authority) or STS Relying Party Web Services.
-