2 Managing Mobile Security Access Server Instances
You manage Mobile Security Access Server (MSAS) instances using the Environments page in the MSAS console component of the OAM console. From this page you can view all the MSAS instances in the environment, view the configuration for each instance, and create new logical MSAS instances.
2.1 Viewing MSAS Instances in the Environment
To view all the MSAS instances in the environment:
-
From the Oracle Access Management home page, click the Mobile Security tab from the list of tabs at the top of the page.
-
From the Mobile Security Launch Pad, select Environments in the Mobile Security Access Server section.
The Environments page opens in a new tab. From this page you can:
-
View the total number of MSAS instances configured in the environment.
-
View the total number of MSAS applications deployed on the MSAS instances. For more information about MSAS applications, see Chapter 3, "Managing Mobile Security Access Server Applications."
-
View the total number of URLs configured in all the applications. For more information about MSAS application URLs, see "Managing URLs in an MSAS Application".
-
Create a new logical MSAS instance and register it in the environment. For instructions, see "Creating and Registering a Logical MSAS Instance".
-
-
Click MSAS or Instances in the MSAS tile.
The MSAS Instances Summary page opens in a new tab. You can use this page to view summary information for each instance.
The first 8 instance in the environment are displayed. Click Show More to show additional instances.
-
Use the Search field to refine the list of instances or to locate a specific instance. Enter all or part of a name in the Search field and press the search icon.
2.2 Viewing the Configuration of an MSAS Instance
To view the configuration of an MSAS instance:
-
Navigate to the MSAS Instances Summary page as described in "Viewing MSAS Instances in the Environment".
-
If necessary, use the Search field to refine the list of instances or to locate a specific instance. Enter all or part of a name in the Search field and press the search icon.
-
Click Configure or the instance name in the tile for the instance to be viewed.
The MSAS Instance Configuration page displays in a new tab. The tab name is the name of the instance. The General tab on this page provides summary information about the instance, such as Name, Display Name, MSAS URL of the physical instance, instance statistics such as number of applications and URLs in the instance, and version information.
-
Click the remaining tabs on this page to view the configuration details. Additional information and procedures for configuring the instance are provided in Chapter 6, "Configuring a Mobile Security Access Server Instance."
2.3 Synchronizing MSAS Instance Configuration
When you change an MSAS instance, for example to modify the configuration or edit applications or URLs, synchronization with the run-time server typically occurs at a user-specified polling interval specified using a cache refresh property. As a result, the changes may not go into effect until the next scheduled polling interval.
Note:
The default polling interval is 86,400,000ms (24 hours). You can adjust this property setting as described in "Configuring the Cache Refresh Time" and "Configuring the Cache Refresh Time Using WLST".You can force immediate synchronization of the changes as follows:
-
Navigate to the MSAS Instances Summary page as described in "Viewing MSAS Instances in the Environment".
-
If necessary, use the Search field to refine the list of instances or to locate the specific instance for which you want to synchronize the changes. You can also enter all or part of a the instance name in the Search field and press the search icon.
-
Click Synchronize in the tile for the instance that contains the changes to be synchronized.
An information message displays indicating that the synchronization process has been initiated for the instance.
Note:
It may take approximately 60 seconds for the changes to go into effect in the run time. -
Click OK in the message window.
2.4 Creating and Registering a Logical MSAS Instance
You can create a logical MSAS instance and register it with the Mobile Security Manager (MSM) using the MSAS console. You can use this logical instance to create applications, and configure the instance, without being bound to a physical machine. This might be useful in a test to production environment, for example, where you can automate the data creation process without being dependent on the availability of the physical hardware.
Once the configuration is complete, you can bind this logical instance to a physical instance using the configMSAS configuration script. For more information, see "Binding a Logical MSAS Instance to a Physical Instance" in Installing Oracle Mobile Security Access Server.
To create a logical MSAS instance and register it with the MSM server:
-
From the Oracle Access Management home page, click the Mobile Security tab from the list of tabs at the top of the page.
-
From the Mobile Security Launch Pad, select Environments in the Mobile Security Access Server tile.
The Environment Summary page opens in a new tab.
-
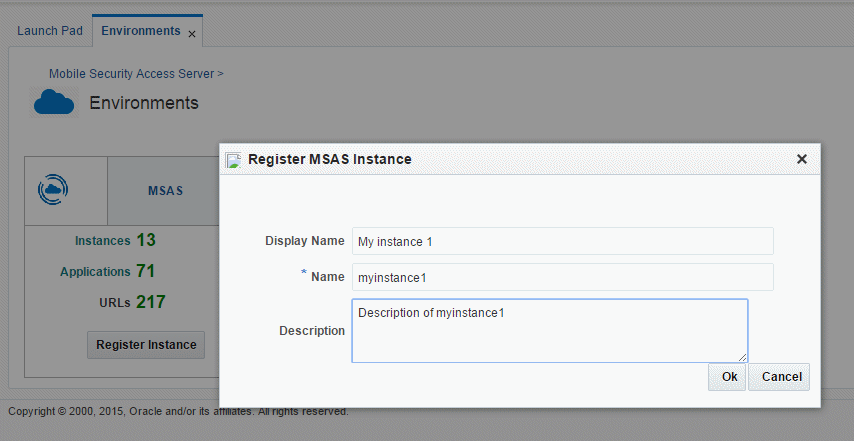
Click Register Instance.
-
In the Register MSAS Instance window, complete the fields then click OK. The Register MSAS Instance window is shown in Figure 2-1.
Field Description Display Name Optionally, enter a meaningful name that can be used to identify the instance in the console. Name Enter a name for the MSAS instance. The name must: -
Be unique within the MSAS environment.
-
Adhere to the XML xs:NCName format using only valid NCName ASCII characters. For example, it must start with a letter or underscore (
_), and cannot contain any space characters or colons (:).For the NCName format definition, see the W3C document Namespaces in XML 1.0 (Third Edition) at
http://www.w3.org/TR/REC-xml-names/#NT-NCName
Description Optionally, enter a short description of the MSAS instance. -
-
Configure the instance using the MSAS Instance Configuration page. This page displays in a new tab using the instance ID as the tab name. Use the subtabs on this page to configure the instance. Much of the configuration can also be completed using WLST commands. For details, see Chapter 6, "Configuring a Mobile Security Access Server Instance."
2.5 Changing the MSM Server Associated with an MSAS Instance
To change the Mobile Security Manager URL to which an MSAS instance is registered, you need to run the MSAS configuration script (configMSAS) on the machine on which you configured the MSAS instance. You can perform this update in interactive mode by responding to the prompts, or in silent mode using a properties file.
-
If a logical MSAS instance with the same name does not already exist on the MSM server to which you are assigning this instance, log into the OAM console on that MSM server to access the MSAS console pages and create a logical instance using the same name as the instance to be updated. For details about creating a logical MSAS instance, see "Creating and Registering a Logical MSAS Instance".
-
Go to the machine on which the MSAS instance to be updated is configured and change to the
ORACLE_HOME/omsas/bindirectory, whereORACLE_HOMEis the directory you specified for Oracle Home when you installed Mobile Security Access Server, for example,/u01/oracle/omsas/Oracle_MSAS. -
Enter the following command to start the MSAS configuration script in update mode:
sh configMSAS.sh -update
Note:
To execute this script in silent mode, provide the name of the properties file on the command line, for example:sh configMSAS.sh -update myupdatefile.properties
You must include the following properties in the properties file:
-
MSM_URL -
MSM_USER_NAME -
MSM_PASS -
MSAS_INSTANCE_ID -
MSAS__INSTANCE_ROOT_DIR
For descriptions of these properties, and details about executing this script in silent mode, see "Using Silent Mode to Configure an MSAS Instance" in Installing Oracle Mobile Security Access Server.
-
-
Respond to each prompt as described in Table 2-1. If you make an error and need to exit the script without completing the update, press
Ctrl-c.
Table 2-1 MSAS Configuration Script Prompts to Update Bootstrap Credentials
| Prompt | Description |
|---|---|
|
Enter the MSAS Instance ID |
Enter the name of the MSAS instance for which you want to update the bootstrap credentials. |
|
Enter the MSAS Instance Root Dir |
Enter the full path to the directory containing the MSAS instance to be updated. |
|
Do you want to update the Mobile Security Manager (MSM) URL |
Enter or |
|
Enter the Mobile Security Manager (MSM) URL |
If you entered For an SSL URL, use:
For a non-SSL URL, use the following format:
In both formats, If you configured other ports when you created the MSM domain, be sure to enter the appropriate MSM server listen port. |
|
Do you want to update the Mobile Security Manager (MSM) credential |
Enter If you are updating the MSM URL, be sure to enter the correct credentials for the new MSM server. |
|
Enter the Username to connect to the Mobile Security Manager (MSM) |
Enter the username for the updated credential. |
|
Enter the Password to connect to the Mobile Security Manager (MSM) |
Enter the password for the new credential. |
When the process completes successfully, the following message displays:
The Instance For MSAS Instance Id - instance_name Configured Successfully.
You will now be able to manage this MSAS instance using the MSAS console or WLST commands on the MSM server with which this instance is now registered.
Note:
The list of MSAS URLs on the General tab of the MSAS Instance Configuration page in the MSAS console is not updated to reflect the physical instances to which this logical instance is linked.2.6 Deleting a Logical MSAS Instance
To delete a logical MSAS instance:
-
Navigate to the MSAS Instances Summary page as described in "Viewing MSAS Instances in the Environment".
-
If necessary, use the Search field to refine the list of instances or to locate a specific instance. Enter all or part of a name in the Search field and press the search icon.
-
Delete the desired instance by clicking the X in the upper-right corner of the instance tile.
You are prompted to confirm that you want to delete the instance. Click OK. Once deleted, the instance is deleted from the MSAS Instances Summary page and is no longer managed by the MSM server.
Note:
When the logical instance ID is deleted in the console, any associated physical instances can not be managed from MSM and will result in runtime errors.
2.7 Starting and Stopping MSAS
To start or stop MSAS:
-
Change to the
MW_HOME/instances/instance_name/bindirectory, whereMW_HOMEis the Middleware home directory in which you installed Mobile Security Access Server andinstance_nameis the name of the MSAS instance you want to start or stop. -
To start MSAS, enter the following command:
sh startServer.sh -
To stop MSAS, enter the following command:
sh stopServer.sh