11 Using an Oracle Database Firewall with Oracle RAC
Topics:
11.1 Configuring a Database Firewall with Oracle RAC for DPE Mode
Topics:
11.1.1 About Configuring a Database Firewall with Oracle RAC for DPE Proxy Mode
To use Database Policy Enforcement (DPE) mode in an Oracle Database Firewall with Oracle RAC, Oracle recommends that you perform the configuration proxy mode.
The procedures in this section assume that you have one Oracle Database Firewall and one Oracle Audit Vault Server, but you can easily include more Database Firewalls by following the examples shown. The Database Firewall will be configured in proxy mode, in which the following takes place:
- SQL client connects to Database Firewall.
- Database Firewall connects to SCAN Listener.
- SCAN Listener redirects the connection to a RAC node.
- Database Firewall handles the redirection, makes a outbound connection to the re-directed RAC node.
- The response from Oracle RAC node is passed to the client.
All components must be in the same subnet. If the client and the SCAN Listener are in different subnets, then 2 Network Interface Cards are needed (one in the client subnet and the other in SCAN Listener subnet).The internal Database Firewall routing must be adjusted if the client, Database Firewall, and database server reside in a different subnet.
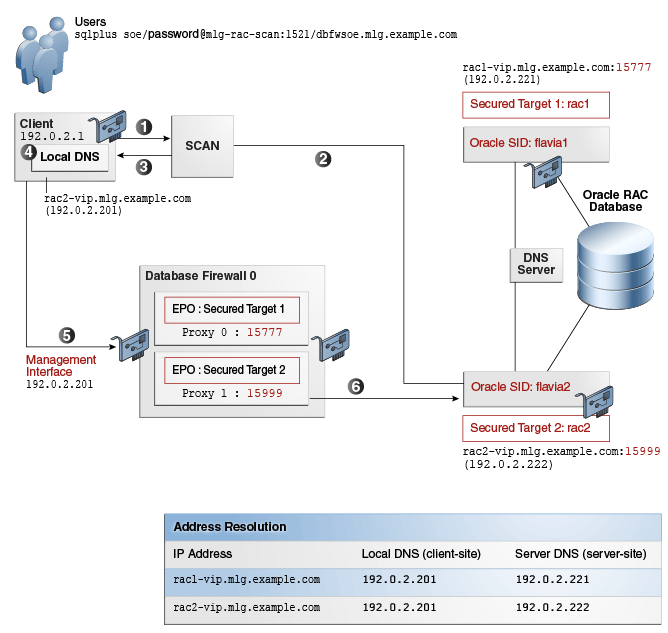
Figure 11-1 shows the setup environment that will be used in the procedure that this chapter covers.
Figure 11-1 Oracle Database Firewall and Oracle RAC SCAN VIP Architecture
A typical request flow is as follows:
-
An application issues a request to SCAN to find the least loaded instance for the database service (for example,
soe.mlg.example.com). -
SCAN returns the connection information of the least loaded instance, in the form of
node_id_fqdn:node_id_local_port.Traditionally SCAN will returnnode_vip_ip:node_id_local_port. However, for the procedure that is described here, the IP address is replaced with the corresponding fully qualified domain name. -
The application looks up and resolves
node_id_fqdninto the Database Firewall proxy interface IP using a separate local DNS service. -
The request is forwarded to the respective enforcement point in the Database Firewall, and assuming the proxy in the Database Firewall has already been created using the same port as
node_id_local_port, the connection takes place. -
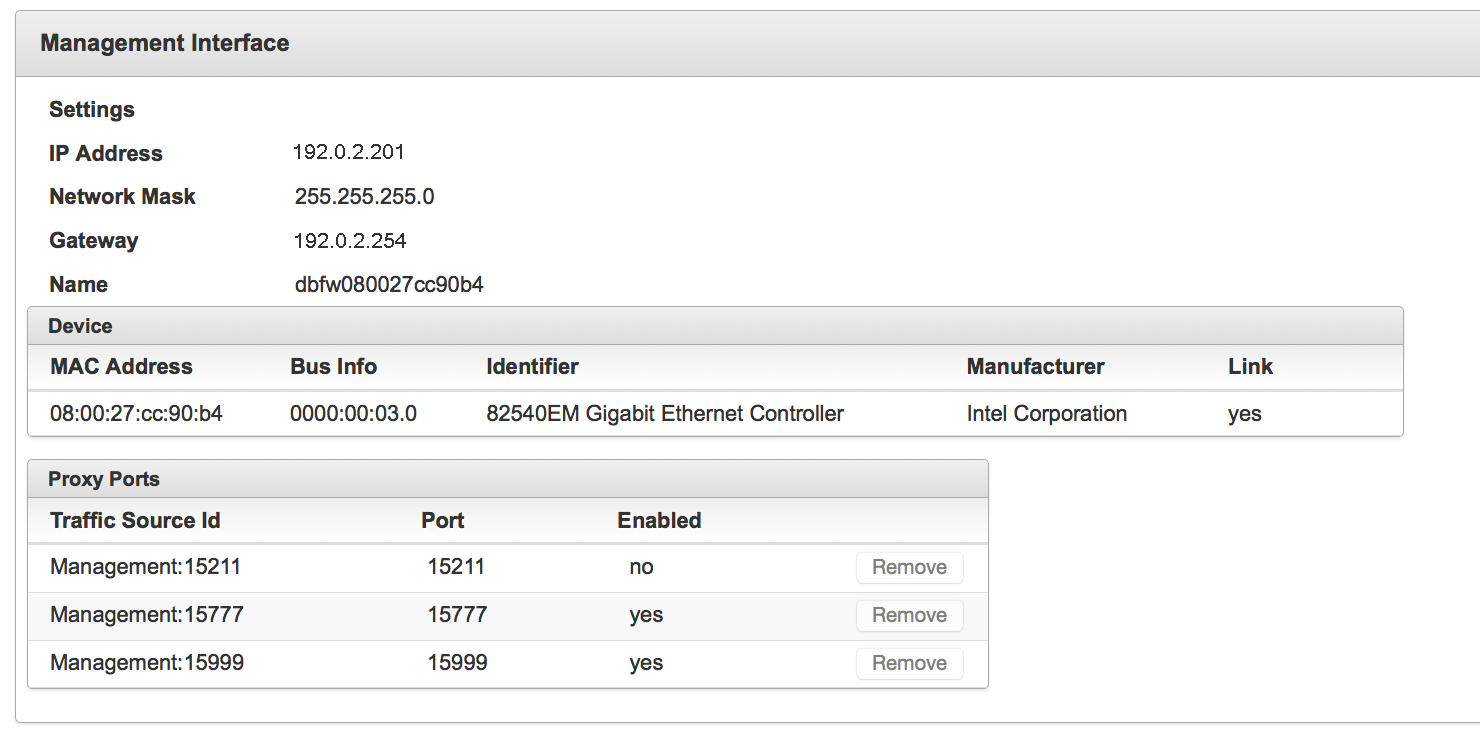
The user then is able to connect to the Database Firewall using the appropriate management interface.
-
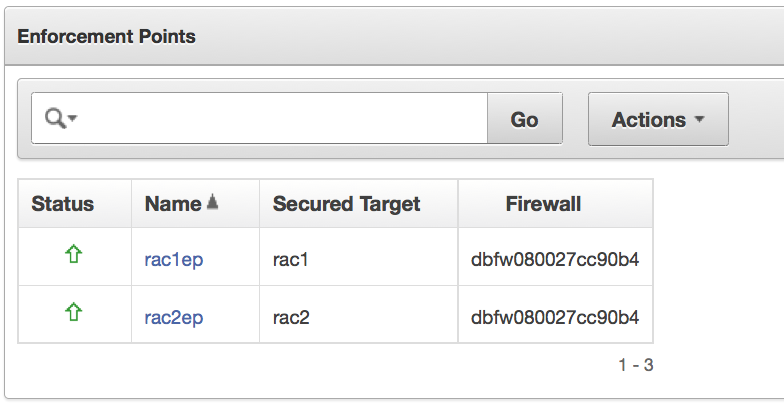
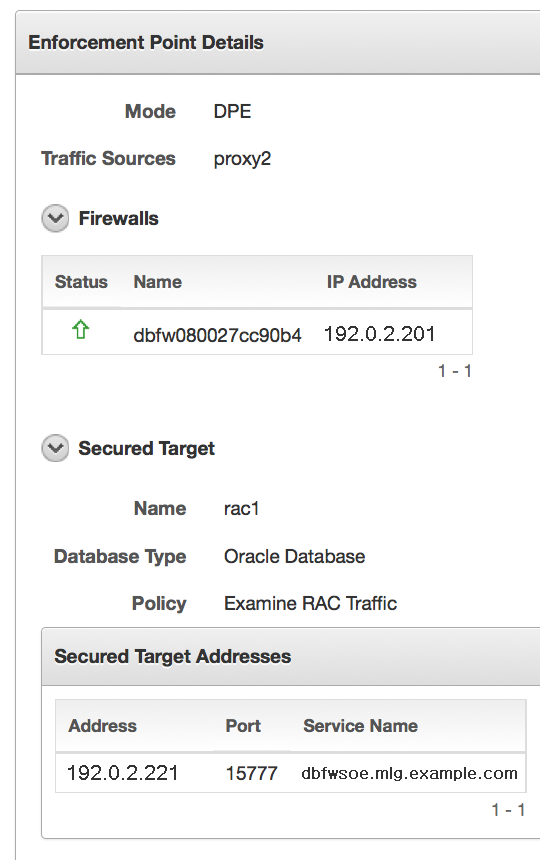
When the user makes this connection, the Oracle RAC node is available as a secured target.
11.2 Configuring a Database Firewall with Oracle RAC for DAM Mode
You can configure an Oracle Database Firewall with Oracle RAC to use Database Activity Monitoring (DAM) inline and out-of-band mode. This type of configuration is the most straightforward (that is, it works out of the box).
To accomplish this, you must ensure that all the IP addresses for the Oracle RAC nodes are included in the secured target configuration. This can be a single secured target configuration with multiple IPs for each Oracle RAC node. Alternatively, it can be a separate secured target for each node.