1 Introducing Oracle Audit Vault and Database Firewall
To begin using Oracle Audit Vault and Database Firewall (Oracle AVDF), you should perform some preliminary tasks, such as downloading the latest version of this manual and understanding the basic concepts of using Oracle AVDF.
Topics
1.1 Downloading the Latest Version of This Manual
You can download the latest version of this manual from the following website:
http://www.oracle.com/pls/topic/lookup?ctx=avdf122
You can find documentation for other Oracle products at the following website:
1.2 Learning About Oracle AVDF
Oracle recommends that you read Oracle Audit Vault and Database Firewall Concepts Guide to understand the features, components, users, and deployment of Oracle AVDF.
1.3 Supported Platforms for Oracle Audit Vault and Database Firewall
You can run Oracle Audit Vault and Database Firewall on various platforms.
See Oracle Audit Vault and Database Firewall Installation Guide for detailed platform support for the current release.
1.4 System Features
Topics
1.4.1 About Audit Vault and Database Firewall
Oracle Audit Vault and Database Firewall (AVDF) secures databases and other critical components of IT infrastructure (such as operating systems) in these key ways:
-
Provides a database firewall that can monitor activity and/or block SQL statements on the network based on a firewall policy.
-
Collects audit data, and makes it available in audit reports.
-
Provides dozens of built-in, customizable activity and compliance reports, and lets you proactively configure alerts and notifications.
This section provides a brief overview of the administrative and auditing features of Oracle AVDF.
Oracle AVDF auditing features are described in detail in Oracle Audit Vault and Database Firewall Auditor's Guide.
We strongly recommend that you read Oracle Audit Vault and Database Firewall Concepts Guide for more information on the features, components, users, and deployment of Oracle AVDF.
1.4.2 Security Technical Implementation Guides and Implementation for Oracle Audit Vault and Database Firewall
Learn about Oracle Audit Vault and Database Firewall compliance with Security Technical Implementation Guides (STIG) standards.
Oracle Audit Vault and Database Firewall (Oracle AVDF) is compliant with the Security Technical Implementation Guides (STIG) standards.
See Also:
1.4.3 System Requirements for Oracle Audit Vault and Database Firewall
Read about the Oracle AVDF hardware and software requirements.
For hardware and software requirements, see Oracle Audit Vault and Database Firewall Installation Guide.
1.4.4 Supported Secured Targets
A secured target is a database or nondatabase product that you secure using either the Audit Vault Agent, the Database Firewall, or both. If the secured target is a database, you can monitor or block its incoming SQL traffic with the Database Firewall. If the secured target, whether or not it is a database, is supported by the Audit Vault Agent, you can deploy the agent on that target's host computer and collect audit data from the internal audit trail tables and operating system audit trail files.
Oracle AVDF supports various secured target products out of the box in the form of built-in plug-ins.
See Also:
-
Plug-in Reference for detailed information on each plug-in.
-
Table B-1 for supported secured target products and versions.
-
Table B-17 for the data collected and platforms supported for each audit trail type.
See Also:
-
Oracle Audit Vault and Database Firewall Developer's Guide for information on creating custom plug-ins to capture audit trails from more secured target types using the Oracle AVDF SDK.
-
Oracle Big Data Appliance Owner's Guide for more information on Oracle Big Data Appliance as a secured target on Oracle Audit Vault and Database Firewall.
1.4.6 Oracle Audit Vault and Database Firewall Auditing Features
Learn about Oracle Audit Vault and Database Firewall auditing features.
Oracle Audit Vault and Database Firewall auditing features enable you to configure and manage the following:
-
Firewall policies
-
Audit policies for Oracle Database
-
Reports and report schedules
-
Entitlement auditing for Oracle Database
-
Stored procedure auditing
-
Alerts and e-mail notifications
See Also:
Oracle Audit Vault and Database Firewall Auditor's Guide for detailed information about these auditing features
1.4.7 Integrating Oracle Audit Vault and Database Firewall with Third-Party Products
Learn about integrating Oracle Audit Vault and Database Firewall with third-party products.
You can integrate Oracle Audit Vault and Database Firewall with the following third-party products:
-
F5 BIG-IP Application Security Manager (ASM): This product, from F5 Networks, Inc., is an advanced web application firewall that provides comprehensive edge-of-network protection against a wide range of web-based attacks. ASM analyzes each HTTP and HTTPS request and blocks potential attacks before they reach the web application server.
Note:
-
This functionality is only supported on F5 BIG-IP ASM version
10.2.1. -
F5 BIG-IP ASM integration is deprecated in release
12.2.0.7.0, and will be desupported in19.1.0.0.0.
-
-
Micro Focus Security ArcSight SIEM: This product is a centralized system for logging, analyzing, and managing syslog messages from different sources.
Note:
ArcSight Enterprise Security Manager (ESM) Security Information and Event Management (SIEM) (previously known as HP ArcSight SIEM) is deprecated in 12.2.0.8.0 and is desupported in 12.2.0.9.0. Use the syslog integration feature instead.
See Also:
-
Configuring Integration with BIG-IP ASM for more information on integrating with F5 BIG-IP Application Security Manager.
-
Integration with Third Party SIEM and Log-data Analysis Tools for more information on integrating with ArcSight Enterprise Security Manager (ESM) Security Information and Event Management (SIEM).
1.4.8 Integrating Oracle Audit Vault and Database Firewall with Oracle Key Vault
You can integrate Oracle Audit Vault and Database Firewall with Oracle Key Vault.
See Oracle Key Vault Administrator's Guide for instructions about integrating Oracle Key Vault with Oracle Audit Vault and Database Firewall
1.5 Understanding the Administrator's Role
Oracle AVDF Administrator Tasks
As an administrator, you configure Audit Vault and Database Firewall. The administrator's tasks include the following:
-
Configuring system settings on the Audit Vault Server
-
Configuring connections to the host computers where the Audit Vault Agent is deployed (usually the same computer as the secured targets)
-
Creating secured targets in the Audit Vault Server for each database or operating system you are monitoring
-
Deploying and activating the Audit Vault Agent on the secured target host computers
-
Configuring audit trails for secured targets that are monitored by the Audit Vault Agent
-
Configuring Database Firewalls on your network
-
Creating enforcement points for secured targets that are monitored by a Database Firewall.
-
Backing up and archiving audit and configuration data
-
Creating administrator users and managing access (super administrator only)
Administrator Roles in Oracle AVDF
There are two administrator roles in Oracle AVDF, with different levels of access to secured targets:
-
Super Administrator - This role can create other administrators or super administrators, has access to all secured targets, and grants access to specific secured targets and groups to an administrator.
-
Administrator - Administrators can only see data for secured targets to which they have been granted access by a super administrator.
1.6 Summary of Configuration Steps
With Oracle AVDF, you can deploy the Audit Vault Agent, the Database Firewall or both. This section provides suggested high-level steps for configuring the Oracle AVDF system when you are:
1.6.1 Configuring Oracle AVDF and Deploying the Audit Vault Agent
- Configure the Audit Vault Server. See "Configuring the Audit Vault Server".
- Register the host computers where you will deploy the Audit Vault Agent. Then deploy and activate the Audit Vault Agent on those hosts. See "Registering Hosts and Deploying the Agent".
- Create user accounts on your secured targets for Oracle AVDF to use. See "Scripts for Oracle AVDF Account Privileges on Secured Targets".
- Register the secured targets you are monitoring with the agent in the Audit Vault Server, and configure audit trails for these secured targets. See "Configuring Secured Targets, Audit Trails, and Enforcement Points".
After you have configured the system as an administrator, the Oracle AVDF auditor creates and provisions audit policies for Oracle Database secured targets, and generates various reports for other types of secured targets.
1.6.2 Configuring Oracle AVDF and Deploying the Database Firewall
After you have configured the system as an administrator, the Oracle AVDF auditor creates firewall policies and assigns them to the secured targets. The auditor's role and tasks are described in Oracle Audit Vault and Database Firewall Auditor's Guide.
1.7 Planning the System Configuration
1.7.1 Guidance for Planning Your Oracle Audit Vault and Database Firewall Configuration
Learn about the steps for planning your Oracle Audit Vault and Database Firewall configuration.
The steps in this section summarize the planning steps with links to specific instructions in this user guide.
See Also:
Oracle Audit Vault and Database Firewall Concepts for guidance on planning deployments of Oracle Audit Vault Server, Oracle Audit Vault Agent, and Oracle Database Firewall.
1.7.2 Step 1: Plan Your Oracle Audit Vault Server Configuration
Plan your Oracle Audit Vault Server configuration.
In this step, plan whether to configure a resilient pair of servers, whether to change the network configuration settings that were made during the installation, and how to configure optional services.
See Also:
-
Configuring the Audit Vault Server for information on the Oracle Audit Vault Server configuration settings.
-
Configuring High Availability for information about setting up resilient pairs of Oracle Audit Vault Servers.
1.7.3 Step 2: Plan the Database Firewall Configuration
If you are using Database Firewalls, plan how many you will need, which secured target databases they will protect, where to place them in the network, whether they will be in DAM (monitoring only) or DPE (monitoring and blocking) mode, and whether to configure a resilient pair of firewalls. Also plan whether to change the Database Firewall network configuration specified during installation.
See Also:
-
Configuring the Database Firewall for information on the Database Firewall configuration settings.
-
Configuring High Availability for information on setting up resilient pairs of firewalls.
1.7.4 Step 3: Plan the Audit Vault Agent Deployments
If you are deploying the Audit Vault Agent(s), determine the secured targets for which you want to collect audit data, and identify their host computers. You will register these hosts with Oracle Audit Vault and Database Firewall and deploy the Audit Vault Agent on each of them. Then you will register each secured target in the Audit Vault Server.
1.7.5 Step 4: Plan the Audit Trail Configurations
If you are deploying the Audit Vault Agent to collect audit data, you will need to configure audit trails. This section provides guidelines for planning the audit trail configuration for the secured targets from which you want to extract audit data. The type of audit trail that you select depends on the secured target type, and in the case of an Oracle Database secured target, the type of auditing that you have enabled in the Oracle Database.
1.7.6 Step 5: Plan Your Integration Options
Learn how to plan your integration options.
You can integrate Oracle Audit Vault and Database Firewall with the following third-party products:
-
F5 BIG-IP Application Security Manager (ASM), from F5 Networks, Inc.
Note:
-
This functionality is only supported on F5 BIG-IP ASM version
10.2.1. -
F5 BIG-IP ASM integration is deprecated in release
12.2.0.7.0, and will be desupported in19.1.0.0.0.
-
-
ArcSight Security Information Event Management (SIEM)
Note:
Micro Focus Security ArcSight SIEM is deprecated in
12.2.0.8.0and is desupported in12.2.0.9.0. Use thesyslogintegration feature instead.
1.7.7 Step 6: Plan for High Availability
In this step, consider the high availability options outlined in "Configuring High Availability".
1.7.8 Step 7: Plan User Accounts and Access Rights
As a super administrator, you can create other super administrators and administrators. Super administrators will be able to see and modify any secured target. Administrators will have access to the secured targets you allow them to access. In this planning step, determine how many super administrators and administrators you will create accounts for, and to which secured targets the administrators will have access.
See Also:
1.8 Logging in to the Audit Vault Server Console UI
Topics
1.8.1 Log in to Oracle Audit Vault Server Console
Learn how to log in to Oracle Audit Vault Server Console.
When you first log in after installing Oracle Audit Vault Server, you must set up a password.
See Also:
Oracle Audit Vault and Database Firewall Installation Guide for information on post-installation tasks.
To log in to Oracle Audit Vault Server Console:
1.8.2 Understanding the Tabs and Menus in the Audit Vault Server Console
The Audit Vault Server console UI includes the following five tabs:
-
Home - Displays a dashboard showing high level information and status for:
-
Server Throughput
-
Disks Usage
-
CPU
-
RAM
-
Hosts
-
Database Firewalls
At the top of the page, you can select the time range for the data displayed and the refresh interval, as shown in Figure 1-1.
Figure 1-1 Selecting the Time Range for the Dashboard in the Home Tab
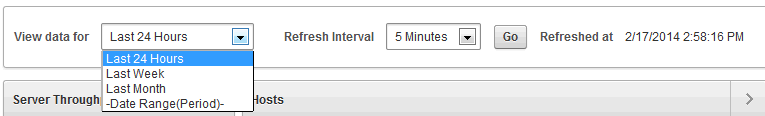
Description of "Figure 1-1 Selecting the Time Range for the Dashboard in the Home Tab" -
-
Secured Targets - Provides menus for registering secured targets, managing secured target groups, managing access rights, and monitoring audit trails and enforcement points.
-
Hosts - Provides menus for registering and managing host computers (where the agent is deployed), and downloading and activating the Audit Vault Agent on those hosts.
-
Database Firewalls - Provides menus for registering Database Firewalls in the Audit Vault Server, and creating resilient pairs of firewalls for high availability.
-
Settings - Provides menus for managing security, archiving, and system settings. From here, you can also download the AVCLI command line utility.
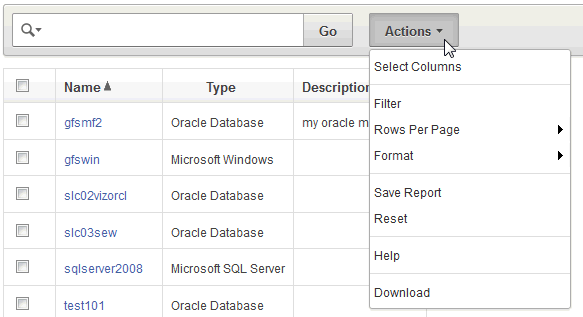
1.8.3 Working with Lists of Objects in the UI
Throughout the Audit Vault Server UI, you will see lists of objects such as users, secured targets, audit trails, enforcement points, etc. You can filter and customize any of these lists of objects in the same way as you can for Oracle AVDF reports. This section provides a summary of how you can create custom views of lists of objects. For more detailed information, see the Reports chapter of Oracle Audit Vault and Database Firewall Auditor's Guide.
To filter and control the display of lists of objects in the Audit Vault Server UI:
1.9 Logging in to the Database Firewall Console UI
1.9.1 Log in to the Database Firewall Console UI
When you first log in after installing the Database Firewall, you are required to set up a password.
See Also:
Oracle Audit Vault and Database Firewall Installation Guide for information on post-installation tasks.
To log in to the Database Firewall Console UI:
1.9.2 Using the Oracle Database Firewall UI
Learn about using the Oracle Database Firewall UI.
As administrator, use the Oracle Database Firewall UI to configure the network, services, and system settings on Oracle Database Firewall. Also use the Oracle Database Firewall UI to identify the Oracle Audit Vault Server that manages each firewall. Also use it to configure network traffic sources so that the firewall can monitor or block threats to your target databases.
See Also:
Configuring the Database Firewall for detailed information on configuring the Oracle Database Firewall using the Database Firewall console UI
1.10 Using the Audit Vault Command-Line Interface
Learn about using the Audit Vault command-line interface (AVCLI).
You can download AVCLI and use it as an alternative to Audit Vault Server Console for configuring and managing Oracle Audit Vault and Database Firewall.
See Also:
-
Downloading and Using the AVCLI Command Line Interface for information on downloading and using AVCLI
-
AVCLI Commands Reference for details of available commands and syntax
1.11 Using the Audit Vault and Database Firewall Enterprise Manager Plug-in
If you have Oracle Enterprise Manager Cloud Control installed, you can install Oracle Audit Vault and Database Firewall plug-in. This plug-in can be used to manage and monitor Oracle Audit Vault and Database Firewall through the Enterprise Manager.
The following tasks can be performed:
-
View Audit Vault and Database Firewall topology
-
Monitor availability and performance of Audit Vault components
-
Provision Audit Vault Agent on Secured Targets
-
Initialize and integrate Audit Vault and Database Firewall with Secured Targets including Oracle Database, Hosts, and Audit Trails for Hosts as well as Oracle Database.
-
Perform discovery of sensitive columns on Secured Targets
-
Monitor Secured Targets
Using Oracle Enterprise Manager Audit Vault and Database Firewall plug-in, the following components can be managed to perform certain operations:
| Components | Operations Performed |
|---|---|
|
Database Firewall |
|
|
Audit Vault Agent |
|
|
Enforcement Point |
|
|
Audit Trail |
|
|
Secure Target |
|