1 Introducing Oracle Audit Vault and Database Firewall
1.1 Downloading the Latest Version of This Manual
You can download the latest version of this manual from the following website:
http://www.oracle.com/pls/topic/lookup?ctx=avdf122
You can find documentation for other Oracle products at the following website:
1.2 Learning About Oracle AVDF
We recommend you read Oracle Audit Vault and Database Firewall Concepts Guide to understand the features, components, users, and deployment of Oracle AVDF.
1.3 The Auditor's Role
As an auditor, you use the Audit Vault Server console to configure the following for databases or non-databases you are monitoring with Oracle Audit Vault and Database Firewall:
-
Secured Targets - For each target you are monitoring, the Oracle Audit Vault and Database Firewall administrator must configure a secured target in the Audit Vault Server. As an auditor, you can then specify audit and/or firewall policies for the secured target, as well as other requirements.
-
Firewall Policies - For any supported database, you can use the Database Firewall and design a firewall policy based on analyzed SQL statements from your secured targets.
-
Audit Policies - For Oracle databases, you can use Oracle Audit Vault and Database Firewall to design audit policies and provision them to the database.
-
Alerts and Notifications - You can create simple or complex alerts based on conditions you specify for the secured targets you are monitoring. You can also specify alert notifications using email templates.
-
Audit Trails - For any secured target type, you can monitor the status of audit trails and see audit reports.
-
Reports - You can schedule and generate a variety of audit and firewall reports in Oracle Audit Vault and Database Firewall, create report notifications, as well as add your own customized reports.
Auditor Roles in Oracle Audit Vault and Database Firewall
There are two auditor roles in Oracle Audit Vault and Database Firewall, with different access levels:
-
Super Auditor - This role has access to all secured targets and can grant access to specific secured targets and groups to an auditor. A super auditor can also assign the super auditor role to others.
-
Auditor - This role can only see data for secured targets to which they have been granted access by a super auditor.
1.4 Understanding Secured Targets
A secured target is any supported database or non-database that you monitor with Oracle Audit Vault and Database Firewall. Secured targets can be monitored by the Audit Vault Agent, the Database Firewall, or both.
The Oracle Audit Vault and Database Firewall administrator creates and configures secured targets, providing host addresses, usernames, passwords, and other necessary information.
If a secured target is monitored by a Database Firewall, the Oracle Audit Vault and Database Firewall administrator configures the Database Firewall, and also configures an enforcement point for each secured target.
Once secured targets are configured, an auditor can do the following for each one:
-
Collect audit data
-
Enable stored procedure auditing (SPA)
-
If the target is a database secured by a Database Firewall:
-
Design and apply a firewall policy
-
View the status of configured enforcement points
-
-
If the secured target is an Oracle database:
-
Define and provision the audit policies
-
Retrieve user entitlement information
-
-
Set a data retention policy
-
Generate a variety of reports
-
Monitor audit trail status
Super auditors can create secured target groups for access control purposes. Super auditors grant auditors access to individual secured targets or to target groups.
See Also:
Managing Secured Targets for details on secured targets.
1.5 Understanding Firewall Policies
See Chapter 4 of Oracle Audit Vault and Database Firewall Concepts Guide for detailed information.
See also "Creating Database Firewall Policies".
1.6 Understanding Audit Policies and Audit Data Collection
See Chapter 3 of Oracle Audit Vault and Database Firewall Concepts Guide for detailed information.
See also "Creating Audit Policies for Oracle Databases".
1.6.1 Requirements for Collecting Audit Data from Secured Targets
Topics
1.6.1.1 Requirements for Oracle Database
Topics
1.6.1.1.1 Ensuring That Auditing Is Enabled in the Secured Target Database
Before Oracle AVDF can collect audit data from the secured target databases, auditing must be enabled in those databases. A database administrator can check the type of auditing your database uses by logging in to SQL*Plus and running the appropriate command.
For example, to check if standard auditing is enabled:
SQL> SHOW PARAMETER AUDIT_TRAIL NAME TYPE VALUE ---------------------- ----------- ----------- audit_trail string DB
This output shows that standard auditing is enabled and audit records are being written to the database audit trail.
For fine-grained auditing, you can query the AUDIT_TRAIL column of the DBA_AUDIT_POLICIES data dictionary view to find the audit trail types that are set for the fine-grained audit policies on the database.
1.6.1.1.2 Using Recommended Audit Settings in the Secured Target Database
After your database administrator checks that auditing is enabled, Oracle recommends that the following areas of the database have auditing enabled:
-
Database schema or structure changes. Use the following
AUDITSQL statement settings:-
AUDIT ALTER ANY PROCEDURE BY ACCESS; -
AUDIT ALTER ANY TABLE BY ACCESS; -
AUDIT ALTER DATABASE BY ACCESS; -
AUDIT ALTER SYSTEM BY ACCESS; -
AUDIT CREATE ANY JOB BY ACCESS; -
AUDIT CREATE ANY LIBRARY BY ACCESS; -
AUDIT CREATE ANY PROCEDURE BY ACCESS; -
AUDIT CREATE ANY TABLE BY ACCESS; -
AUDIT CREATE EXTERNAL JOB BY ACCESS; -
AUDIT DROP ANY PROCEDURE BY ACCESS; -
AUDIT DROP ANY TABLE BY ACCESS;
-
-
Database access and privileges. Use the following
AUDITSQL statements:-
AUDIT ALTER PROFILE BY ACCESS; -
AUDIT ALTER USER BY ACCESS; -
AUDIT AUDIT SYSTEM BY ACCESS; -
AUDIT CREATE PUBLIC DATABASE LINK BY ACCESS; -
AUDIT CREATE SESSION BY ACCESS; -
AUDIT CREATE USER BY ACCESS; -
AUDIT DROP PROFILE BY ACCESS; -
AUDIT DROP USER BY ACCESS; -
AUDIT EXEMPT ACCESS POLICY BY ACCESS; -
AUDIT GRANT ANY OBJECT PRIVILEGE BY ACCESS; -
AUDIT GRANT ANY PRIVILEGE BY ACCESS; -
AUDIT GRANT ANY ROLE BY ACCESS; -
AUDIT ROLE BY ACCESS;
-
1.6.1.2 Requirements for SQL Server, Sybase ASE, and IBM DB2 Databases
Ensure that auditing is enabled in these databases. You also should ensure that they are correctly configured to send audit data to the Audit Vault Server. A database administrator can check these requirements for you. For more information, check the documentation for these databases and Oracle Audit Vault and Database Firewall Administrator's Guide.
1.7 Configuring Alerts and Notifications
Oracle Audit Vault and Database Firewall lets you define rule-based alerts on audit records and specify notification actions for those alerts. Whenever an audit event meets the rule or condition defined in the alert definition, an alert is raised and a notification is sent as specified. You can define alerts by type of secured target, the number of times an event occurs, and by using available fields in audit records to define a Boolean condition that must be met. You can also configure email templates to be used for alert notifications.
You can monitor and respond to alerts from the Audit Vault Server console and from alert reports.
See Also:
1.8 Generating Reports
As an Oracle Audit Vault and Database Firewall auditor, you can generate various audit reports for the secured targets to which you have access. You can schedule, print, and/or email the reports to others, in PDF or XLS format. Reports include information on audit data, entitlements, and stored procedures. You can also generate compliance reports to meet regulations associated with credit card, financial, data protection, and health care-related data.
Oracle Audit Vault and Database Firewall also lets you browse and customize report data interactively, and upload your own custom reports created with third party tools.
See Also:
1.9 Creating Users and Managing Access
A super auditor creates auditor accounts, and manages auditor access to secured targets and secured target groups.
See Also:
Managing Access and Other Settings for information on these functions.
1.10 Logging in and Understanding the Audit Vault Server Console UI
Topics
1.10.2 Understanding the Tabs in the Audit Vault Server Console UI
When you log into Audit Vault Server console as an auditor or super auditor, you see the auditor's dashboard on the Home page, and the functions available for the auditor roles.
From the Home tab (dashboard), you can:
-
Select a date range for viewing event data, and if Oracle Database In-Memory is enabled, see the date range of audit data that is stored in memory, as shown in Figure 1-1. Reports for the date ranges in memory will run faster.
-
View five types of graphical summaries (pie charts and bar graphs) of alert activity and event activity over the specified time period. These graphical summaries include:
-
Recently Raised Alerts
This area displays alerts raised within the period you selected. You can view specific alert levels by clicking See all Warning Alerts or See All Critical Alerts.
-
Attestation Actions
See report attestation actions you need to take within your selected time range.
-
Top Five Audit Sources by Number of Alerts
Click a bar in this bar graph to find more detailed critical and warning alert information that shows a severity level for a particular source.
-
Failed Logins
See failed logins within your selected time range.
-
Figure 1-1 Data Range Selection and In-Memory Date Range
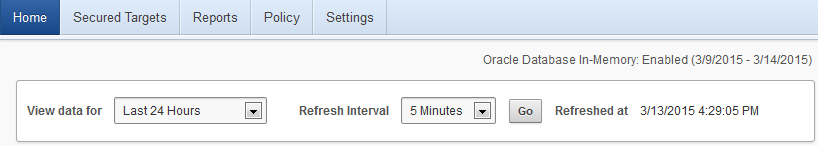
Description of "Figure 1-1 Data Range Selection and In-Memory Date Range"
Other tabs let you access the following functions:
-
Secured Targets - lets you set firewall, audit, and data retention policies for each secured target, manage entitlement snapshots, set up secured target groups, see audit trails and enforcement points
-
Reports - lets you generate default reports, schedule reports, customize reports online, and upload your custom reports
-
Policy - lets you manage audit and firewall policies, and configure alerts
-
Settings - lets you change your password, create and manage email distribution lists, configure email notification templates for alerts and reports, view audit trail and enforcement point status, manage user accounts and access, and view job status.
The following Quick Links are available from all tabs:
-
Enforcement Points - lets you check enforcement point details and status
-
Audit Trails - lets you check audit trail details and status
1.10.3 Working with Lists of Objects in the UI
Throughout the Audit Vault Server UI, you will see lists of objects such as reports, users, secured targets, firewall policies, etc. You can filter and customize any of these lists of objects in the same way as you can for Oracle Audit Vault and Database Firewall reports. This section provides a summary of how you can filter and custom the display of lists of objects.
To filter and control the display of lists of objects in the Audit Vault Server UI:
-
To find an item in the list, enter its name in the search box, and then click Go.
-
To customize the list, from the Actions menu, select any of the following:
-
Rows Per Page: Select the number of rows to display per page.
-
Select Columns: Select which columns to display.
-
Filter: Filter the list by column or by row using regular expressions with the available operators. When done, click Apply.
-
Format: Format the list by selecting from the following options:
-
Sort
-
Control Break
-
Highlight
-
Chart
-
Group By
Fill in the criteria for each option as needed and click Apply.
-
-
Save Report: Save the current view of the list. Enter a name and description and click Apply.
-
Reset: Reset the list to the default view.
-
Download: Download the list. Select the download format (CSV or HTML) and click Apply.
-