48 Managing Compliance
Compliance Management provides the ability to evaluate the compliance of targets and systems as they relate to business best practices for configuration, security, and storage. This is accomplished by defining, customizing, and managing compliance frameworks, compliance standards, and compliance standard rules. In addition, Compliance Management provides advice of how to change configuration to bring your targets and systems into compliance.
This chapter explains how Compliance Management verifies that applications in your enterprise comply with preestablished standards and how to manage the compliance structure. This chapter includes:
48.1 Overview of Compliance
The Compliance Management solution provides the tools to evaluate targets and systems for compliance with business best practices in terms of configuration, security, storage, and so on. In addition, Compliance Management provides the capability to define, customize, and manage the entities used to evaluate compliance.
The compliance solution:
-
Automatically determines if targets and systems have valid configuration settings and whether they are exposed to configuration-related vulnerabilities.
-
Advises how to change configurations to bring targets and systems into compliance with respect to best practices.
-
Provides real-time monitoring of a target's files, processes, and users to let Oracle Enterprise Manager Cloud Control (Cloud Control) users know where configuration change or unauthorized action are taking place in their environment.
-
Provides Oracle provided compliance frameworks (for example, Oracle Generic Compliance Framework) and compliance standards to map to compliance standard rules. This mapping makes it possible to visualize how out-of-compliance settings and actions will affect any compliance framework an organization follows.
-
Provides a compliance-focused view of IT configuration and change that is suitable for Line of Business Owners, IT Managers, and Compliance Managers to refer to regularly to check on their organization's compliance coverage.
Before you start using the compliance features, there are a few basics you need to know. See the following for details:
48.1.1 Terminology Used in Compliance
The following terms are used throughout this chapter when discussing the compliance feature:
-
A compliance framework is an organized list of control areas that need to be followed for a company to stay in compliance in their industry. Enterprise Manager uses compliance frameworks as a foldering structure to map standards and rules to the control areas they affect. Compliance frameworks are hierarchical to allow for direct representation of these industry frameworks.
A single framework control area maps to one or more compliance standards. The outcome of these compliance standard evaluations results in a score for the given framework area.
-
A compliance standard is a collection of checks or rules that follow broadly accepted best practices. It is the Cloud Control representation of a compliance control that must be tested against some set of IT infrastructure to determine if the control is being followed. This ensures that IT infrastructure, applications, business services and processes are organized, configured, managed, and monitored properly. A compliance standard evaluation can provide information related to platform compatibility, known issues affecting other customers with similar configurations, security vulnerabilities, patch recommendations, and more. A compliance standard is also used to define where to perform real-time change monitoring.
A compliance standard is mapped to one or more compliance standard rules and is associated to one or more targets which should be evaluated.
-
A compliance standard rule is a specific test to determine if a configuration data change affects compliance. A compliance standard rule is mapped to one or more compliance standards.
Cloud Control has the following types of compliance standard rules.
-
Used to perform a check against any metric collection data in the Management Repository
-
WebLogic Server Signature Rule
Used to check a WebLogic target to support best practice configurations.
-
Used to monitor actions to files, processes, and database entities in real-time as the changes occur. Also captures users logging in and logging out, and SU and SUDO activities.
-
Used to perform configuration checks on the agent and upload violations into the Management Repository.
-
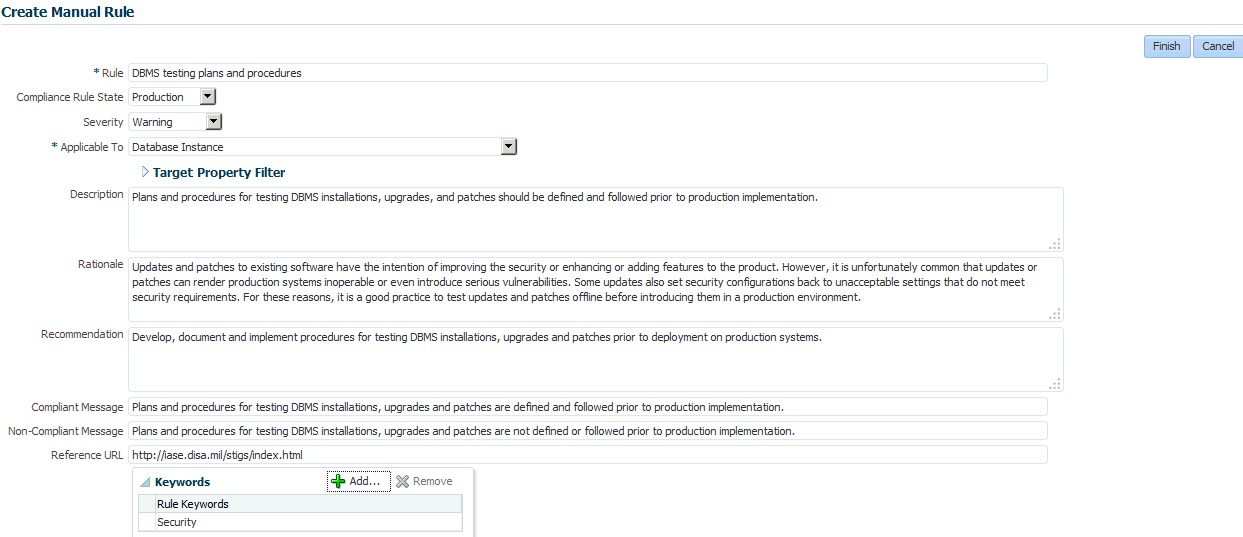
Checks that must be performed but cannot be automated. For example: "Plans for testing installations, upgrades, and patches must be written and followed prior to production implementation."
-
-
Compliance Standard Rule Folder
Compliance standard rule folders are hierarchical structures that contain compliance standard rules.
-
Importance is a setting that the user can make when mapping compliance frameworks, standards, and rules. The importance is used to calculate the affect a compliance violation will have on the compliance score for that framework control area or compliance standard.
For compliance frameworks, when mapping a compliance standard, the importance for this compliance standard indicates the relative importance to other compliance standards in this framework.
For compliance standards, when mapping a compliance standard rule, importance indicates the relative importance of a compliance standard rule to all other compliance standard rules in the compliance standard.
-
A target's compliance score for a compliance standard is used to reflect the degree of the target's conformance with respect to the compliance standard. The compliance score is in the range of 0% to 100% inclusive. A compliance score of 100% indicates that a target fully complies with the compliance standard.
-
The real-time monitoring rule definition includes facets that specify what is important to monitor for a given target type, target properties, and entity type. A facet is a collection of patterns that make up one attribute of a target type. For example, the networking configuration files for your operating system could be defined by one facet containing multiple file names or file patterns.
-
Observations are the actions that were seen on a host or target that were configured to be monitored through real-time monitoring rules. Each distinct user action results in one observation.
-
Every observation has an audit status that determines if the observation was authorized, or unauthorized, or neither (unaudited). The audit status can be set manually or automatically through the real-time monitoring compliance standard rule configuration.
-
Single observations are not reported from the Management Agent to the server. They are instead bundled with other observations against the same target, rule, and user performing the action. Bundles help combine like observations and make it easier to manage the observations in Cloud Control.
48.1.2 Accessing the Compliance Features
To access the compliance features, navigate to the Enterprise menu, select Compliance, then select one of the following:
-
The dashboard provides a very high level view of results that show how compliant or at risk your organization or your area is. The dashboard contains dials representing the compliance score for a selected framework, least compliant systems and targets, and unmanaged discovered hosts.
-
Compliance results include evaluation results and errors for compliance frameworks and compliance standards, as well as target compliance.
-
The Compliance Library page contains the entities used for defining standards. From the Compliance Library page you can manipulate compliance frameworks, compliance standards, compliance standard rules, and real-time monitoring facets.
Note: The real-time monitoring facets are only for real-time monitoring rules.
-
Observations are the actions that were seen on a host or target that were configured to be monitored through real-time monitoring rules. Each distinct user action results in one observation. Observations are additionally bundled if there are multiple observations done in a short period of time by the same user on the same target and against the same real-time monitoring rule.Multiple UI-based reports are provided to allow users to analyze the actions that are being observed.
48.1.3 Roles and Privileges Needed to Use the Compliance Features
To use the compliance standard features, you need to have access to the following roles privileges.
| Role | Description | Contains the Privileges |
|---|---|---|
|
Enables you to create, modify, and delete compliance frameworks, compliance standards, compliance standard rules, and real-time monitoring facets. |
Target Privileges:
Resource Privileges:
|
|
|
Enables you to view compliance framework definition and results. |
No target privileges Resource Privilege
|
The target and resource privileges used in compliance include:
| Privilege | Type of Privilege | Included in Role | Description |
|---|---|---|---|
|
Target |
EM_COMPLIANCE_DESIGNER |
Allows you to mange the compliance of any target including the association of a compliance standard to a target. |
|
|
Target |
EM_COMPLIANCE_DESIGNER |
Enables you to manage a metric for any target. |
|
|
Target |
EM_COMPLIANCE_DESIGNER |
Allows you to view all managed targets in Enterprise Manager. |
|
|
Target |
EM_COMPLIANCE_OFFICER EM_COMPLIANCE_DESIGNER |
Allows you to view compliance framework definition and results NOTE: This privilege is part of the Compliance Framework resource privilege. This privilege is granted by default for EM_COMPLIANCE_OFFICER role but it is not granted by default for the EM_COMPLIANCE_DESIGNER role. |
|
|
Resource |
EM_COMPLIANCE_DESIGNER |
Allows you to create compliance frameworks, compliance standards, compliance standard rules, and real-time monitoring facets. This privilege is part of the Compliance Framework resource privilege. |
|
|
Resource |
EM_COMPLIANCE_DESIGNER |
Allows you to edit and delete compliance frameworks, compliance standards, compliance standard rules, and real-time monitoring facets. This privilege is part of the Compliance Framework resource privilege. |
|
|
Resource |
EM_COMPLIANCE_DESIGNER EM_COMPLIANCE_OFFICER |
Provides the capability to define, customize, and manage compliance frameworks, compliance standards, and compliance standard rules, and evaluate the compliance of targets and systems with regards to business best practices for configuration, security, storage, and so on. This privilege contains the following privileges:
|
|
|
Resource |
EM_COMPLIANCE_DESIGNER |
Allows extending target configuration collections. This privilege contains the following privileges:
|
|
|
Resource |
EM_COMPLIANCE_DESIGNER |
Job is a unit of work that may be scheduled that an administrator defines to automate the commonly run tasks. This privilege contains the following privileges:
|
The following table lists the compliance tasks with the roles and privileges required.
| Task | Roles and Privileges Required |
|---|---|
|
Create compliance framework |
Create Compliance Entity privilege View any Compliance Framework privilege |
|
Edit and delete compliance framework |
Full any Compliance Entity privilege View any Compliance Framework privilege |
|
Create, edit, and delete compliance framework |
EM_COMPLIANCE_DESIGNER role EM_COMPLIANCE_OFFICER role |
|
Associate a compliance standard to a target |
Manage any Target Compliance privilege or MANAGE_TARGET_COMPLIANCE privilege on the target |
|
Import or export a compliance framework |
EM_COMPLIANCE_DESIGNER role EM_COMPLIANCE_OFFICER role |
|
Create a real-time monitoring rule |
EM_COMPLIANCE_DESIGNER role |
|
Create a real-time monitoring facet |
EM_COMPLIANCE_DESIGNER role |
Note: In addition, ensure you have privileges to access the target you will be associating with a compliance standard. In particular, you need the Manage any Target Compliance privilege on the target.
48.2 Evaluating Compliance
Compliance evaluation is the process of testing the compliance standard rules mapped to a compliance standard against a target and recording any violations in the Management Repository.
By evaluating a target against a compliance standard, you are determining whether a target complies with the checks of the standard. In the case when a target does not meet the desired state, the test may suggest what changes are required to make that target compliant.
Compliance evaluation generates a score for a target based on how much the target is compliant with the standard. A 100% compliance score means that all checks of the compliance standard passed on the target. For real-time monitoring, the compliance score will drop as you have observations that have been marked as unauthorized either manually or through change request management integration. As these unauthorized observations are either cleared or changed to authorized, the score will improve.
Because target compliance is required to be monitored regularly, you need to associate a compliance standard with targets. Evaluation is automatically performed for any associated targets, when the target state refreshes, that is when new data has been collected from the target. For repository rules, when new data for the target gets loaded into the Management Repository, evaluation happens again. For Real-time Monitoring, evaluation happens every time an observation of a user action is seen.
What You Can Do To Ensure Compliance
When using Cloud Control to evaluate your compliance, you should regularly perform the following actions:
-
Regularly monitor the compliance dashboard to find areas that may indicate your organization has a low compliance score or is at risk.
-
View the results of an evaluation
Study the results of the evaluations and make the needed changes to the targets
Only results from the targets for which you have View privilege will be available. The compliance standard rule evaluation results are rolled up in order to produce a compliance standard evaluation state as well as a compliance summary.
-
Study Oracle provided reports
Regularly monitor real-time monitoring observation UI reports to see if detected observations are normal or abnormal. Set abnormal observations to unauthorized until any unauthorized change can be reverted or until the actions can be investigated to the level required by your auditors.
-
Study the trend overview as a result of the evaluation
Use the graphs in the Trend Overview pages to visually determine whether the targets are adhering to or distancing themselves from the compliance best practices.
To access the Trend Overview pages for compliance standards:
-
From the Enterprise menu, select Compliance, then select Results.
-
From the Compliance Standards tab, choose Evaluation Results.
-
On the Evaluation Results page, choose the compliance standard you want to investigate and click Show Details.
-
On the resulting details page, click the Trend Overview tab.
Note: You can also review Trend Overview pages for compliance frameworks.
-
-
Ensure your environments match baselines (or each other) by creating rules on top of configuration compare capabilities. Then monitor for configuration drift using real-time monitoring.
-
Evaluate validity of configuration settings.
-
Evaluate exposure to configuration-related vulnerabilities, storage, and security.
-
Modify targets and systems to be compliant.
-
Verify authorization of configuration changes or user actions.
-
Continually test your systems, services, and targets, ensuring the best possible protection and performance your system can have.
-
Use Oracle provided compliance standards and compliance standard rules to determine compliance.
-
Keep an eye on hosts in your environment that are not monitored for compliance as these introduce a large amount of compliance risk in your environment.
The following sections provide additional details:
48.2.1 Accessing Compliance Statistics
Compliance statistics are available throughout the interface in Compliance Summary regions located on pages such as the Compliance Dashboard, the Enterprise Summary page, and a target's home page.
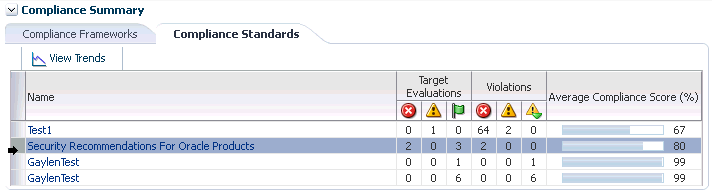
These regions report the violations and compliance scores for the particular targets. However, the region only reports that there is a violation; it does not give the details. For example, a violation can be against the Secure Port compliance standard rule that is part of the Secure Configuration for Host compliance standard. But you will not know the details just by looking at the Compliance Summary regions.
48.2.1.1 Using the Compliance Dashboard Effectively
The compliance dashboard is a top level view of the Cloud Control compliance features. The dashboard includes several regions which give you a very good insight into how compliant your IT environment is according to the standards you have configured.
To access the Compliance Dashboard:
- From the Enterprise menu, select Compliance.
- Select Dashboard.
The Compliance Dashboard is also one of the pages available from the "Select Your Home" page and can be set as your home page when you log in to Cloud Control.
The Compliance Dashboard includes the following regions:
-
Compliance Framework Summary
This region lets the user choose one Compliance Framework and it shows the compliance score for each second-level folder under that Compliance Framework. The needle on the dial shows the current compliance score for that given framework element. The score is based on the targets that the logged-in Enterprise Manager user is allowed to see.
Clicking on the dial will take you to the Compliance Results page for the given second-level framework folder giving you more details on the next framework folders down and/or the compliance standards belonging to this folder.
-
Compliance Summary
This region has a view for frameworks and a view for standards. In the Framework view, this region shows you the list of all defined compliance frameworks and their overall score and violation details. In the standard view, this region will list the worst scoring compliance standards along with their violation details. Clicking on a framework or standard name will take you to a screen showing you more details of that framework or standard.
From this region, you can also click on the View Trends link to see a historic trend graph of the compliance score
-
Least Compliant Generic Systems
This region shows the generic systems that have the lowest compliance score. The score for a given system is calculated by including all rules that are associated with all elements of that system. A generic system is used to define your IT Business Applications, such as HRIS, Payroll, and so on. Reporting these systems that have the lowest score can help identify which business units have compliance risk leading up to audit time.
-
Most Recent Discovered Unmanaged Hosts
This region shows hosts that have been discovered recently using the Cloud Control automatic host discovery feature that have not been promoted to managed hosts. These hosts represent a specific compliance risk in that unmanaged hosts in an IT environment can be lead to many access control and data access risks. The intent of this region is to highlight the hosts that have recently been discovered but may not be under compliance control.
-
Least Compliant Targets
This region is similar to the Least Compliance Generic Systems except it shows you all targets (including the generic systems again). This region is less useful for an IT management or auditor perspective since it may not be clear what these individual targets are used for. It however can be used as another data point to find the areas where you are at highest risk leading up to an IT compliance audit.
48.2.2 Viewing Compliance Summary Information
Compliance summary information is available from the Cloud Control Compliance Results page and individual target home pages.
To view compliance summary information from the Cloud Control home page, follow these steps:
-
From the Enterprise menu, select Compliance, then select Results.
To view compliance summary information from a target's home page, follow these steps:
- From the Targets menu, select the target type, and click the target.
- On the target's home page, select the target menu located at the top-left of the page.
- Select Compliance, then select Results. On the Results page, click Target Compliance.
48.2.3 Viewing Target Compliance Evaluation Results
Target-specific compliance evaluation results are available on the Cloud Control home page and individual target home pages. By evaluating compliance rules and standards, the possible evaluation results will be:
| Evaluation Results | Description |
|---|---|
|
Compliant |
Target meets the desired state and there are no unauthorized real-time monitoring observations. |
|
Non-Compliant |
Target does not meet the desired state. At least one test in the compliance standard detected a deviation from the desired state or there is at least one unauthorized real-time monitoring observation. |
|
Error |
No results returned due to an error. The error may be an unexpected internal error or an error in the test. Examples of errors in the test include attempts to:
|
To view results using Cloud Control home page, follow these steps:
-
From the Enterprise menu, select Compliance, then select Results.
-
Click the Target Compliance tab. The page displays the targets with their Average Compliance Score.
To view compliance evaluation results from a target's home page, follow these steps:
- From the Targets menu, select the target type.
- Click the name of the target in which you are interested.
- On the target menu located at the top-left of the page, select Compliance, then select Results.
- Click the Target Compliance tab. The page displays the targets with the Average Compliance Score.
Use the page or region to get a comprehensive view about a target in regards to compliance over a period of time. Using the tables and graphs, you can easily watch for trends in progress and changes.
Note: Trend overview data might take up to six hours after initial compliance standard to target association to display in the time series charts.
48.2.4 Viewing Compliance Framework Evaluation Results
To effectively use a compliance framework, organize the frameworks to reflect the compliance framework control areas you use in your organization. The hierarchical structure of the framework should map directly to the control areas of the frameworks you follow.
Oracle provides a number of frameworks, for example, Oracle Generic Compliance, Fusion Applications Compliance, and Security Technical Implementation Guide (STIG). These frameworks can be used as a starting point for you to create your own frameworks to match your needs or can be used to understand how best to organize your own frameworks based on internal standards or based on SOX, HIPAA, NIST-800, or other common frameworks.
To view the results of a compliance framework evaluation, use the Evaluations Results page accessed through the Compliance Frameworks tab.
- From the Enterprise menu, select Compliance, then select Results.
- On the Compliance Results page, click the Compliance Frameworks tab and highlight the compliance framework of interest.
Since compliance frameworks are a hierarchical structure, each folder or node of the framework will have its own score. The bottom most children of the hierarchy will have their score roll up to the parent folder and so on. If one person viewing these reports is primarily interested in one control area of the framework they follow, they can focus on the score for that specific control area as represented by the folder they look at under the framework.
48.2.5 Managing Violations
Using the Compliance Results feature you can suppress and unsuppress violations, as well as clear manual violations.
Suppressing a violation enables you to acknowledge an existing violation while removing the violation from the compliance score calculation. Suppressing a violation prevents the violation from negatively impacting the compliance score but not delete it from the list of violations. Suppression can be indefinite or for a specified period of time.
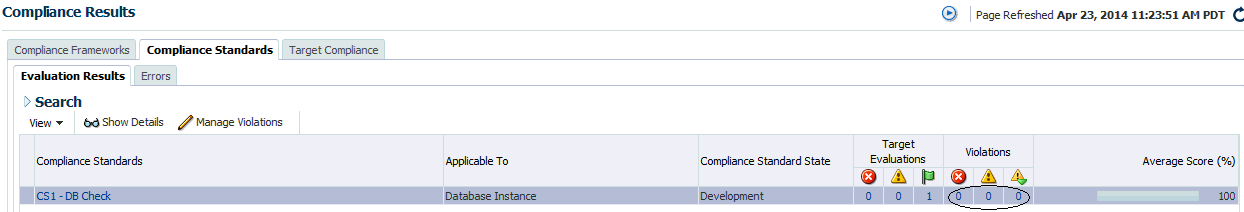
Unsuppressing a violation causes the compliance score to be recomputed accounting for the violations that were unsuppressed.
Clearing of manual rule violations causes the violations to be cleared, and the compliance score to go up for the corresponding compliance standard or target. Clearing a manual rule violation can be indefinite or for a specified period or time.
Accessing the Managing Violations Feature
To access Managing Violation feature:
-
From the Enterprise menu, select Compliance, then select Results.
-
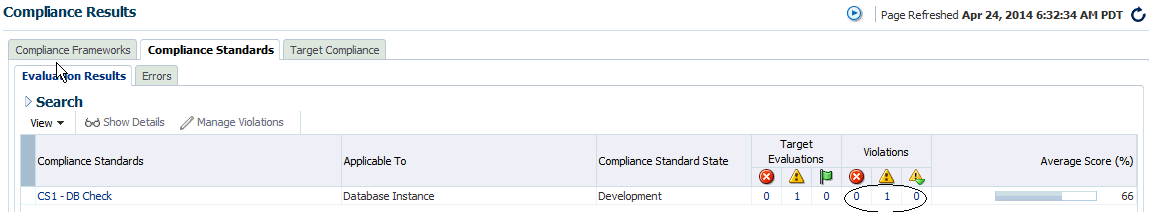
Highlight a compliance standard and click Manage Violations.
The following tabs are available:
-
Unsuppressed Violations
-
Suppressed Violations
-
Manual Rule Violations
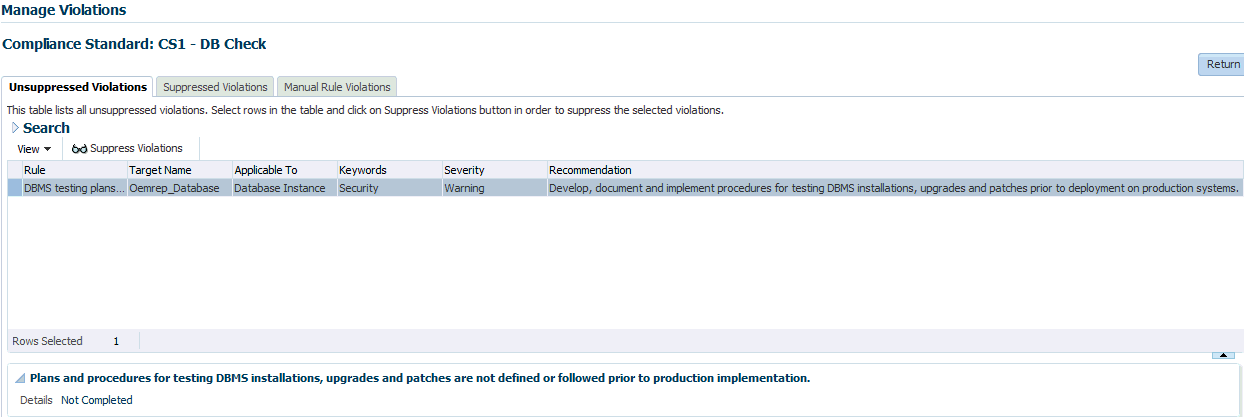
Unsuppressed Violations Tab
Use this tab to suppress violations.
-
Select one or more violations.
-
Click Suppress Violations.
-
On the Violation Suppressed Confirmation popup, you can suppress the violation indefinitely or provide a date by which the suppression will end. Optionally, you can provide an explanation for the suppression.
-
Click OK.
This submits a job to do the suppression asynchronously and returns you to the Result Library page. A suppression adds an annotation to the underlying event stating that the violation is suppressed along with the reason (if a reason was provided). Note: The job results are not instantaneous. It may take a few minutes for the results to be displayed.
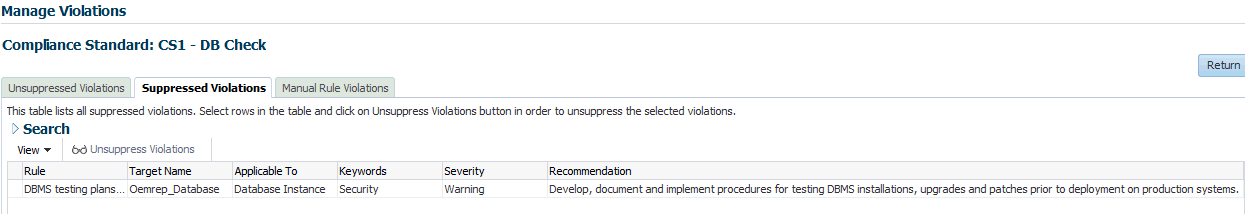
Suppressed Violations Tab
Use this tab to unsuppress violations.
-
Select one or more violations.
-
Click Unsuppress Violations.
-
On the Violation Unsuppressed Confirmation popup, you can provide an explanation for the unsuppression.
-
Click OK.
This submits a job to do the unsuppression asynchronously and returns you to the result library. An unsuppression adds an annotation to the underlying event that the violation is unsuppressed along with the reason (if a reason was provided). Note: The job results are not instantaneous. It may take a few minutes for the results to be displayed.
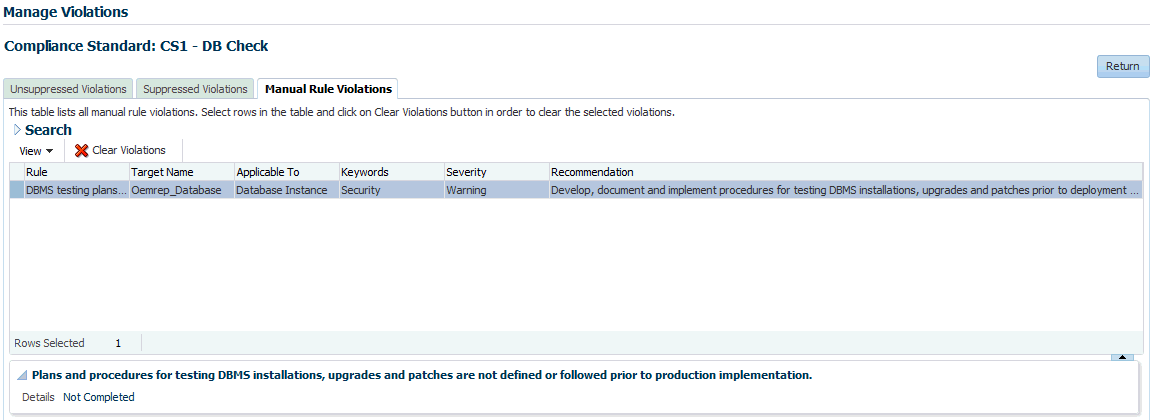
Manual Rule Violations Tab
To clear a manual rule violation:
- Select one or more manual rule violations.
- Click Clear Violations.
- On the Clear Violations Confirmation popup, you can clear the violation indefinitely or provide a date by which the clear will end. Optionally, you can provide an explanation for the clear.
- Click OK.
This submits a job to do the manual rule violations clearing asynchronously and returns you to the Result Library page. Clearing manual rule violations also clears the underlying violation event. Note: The job results are not instantaneous. It may take a few minutes for the results to be displayed.
48.2.6 Investigating Compliance Violations and Evaluation Results
Here are a few suggestions for investigating compliance violations. Attend to the most critical violations or those that have the biggest impact on your overall IT enterprise compliance.
-
Monitor the compliance framework scores along with the systems and targets that have the lowest scores on the compliance dashboard.
-
Ensure that recently discovered hosts are either being monitored using Cloud control for compliance risk or are not possibly introducing risk in your IT compliance.
-
Study the statistics on the Enterprise Summary Home page. In particular, look at the statistics in the Compliance Summary region. The compliance violations with "Critical" severity should be dealt with first.
-
Address generic systems (IT business applications) and targets that have the lowest compliance scores.
-
For the compliance violations of a particular target, examine the home page for that target. The Compliance Standard Summary region provides overview information, but it also gives you access to the Trend for that target.
-
Review compliance violation-related events in the Incident Management area of Cloud Control.
-
Navigate to the Results page for a particular compliance standard. In the navigation tree, click the name of the compliance standard and a summary page lists all the targets along with the number of violations.
-
Navigate to the Trend Overview page to see charts relating to the number of targets evaluated, the average violation count per target, number of targets by compliance score, and the average compliance score.
Note:
Only results from those targets for which you have View privilege will be available for viewing.
48.2.6.1 Investigating Violations of Repository Compliance Standard Rules and Targets Causing Violations
If you are looking at the Enterprise Summary page and you notice that there are critical violations against the Secure Configuration for Host compliance standard, you need to find what targets are causing the violations. Follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- In the Evaluations Results tab for Compliance Standards, highlight the Secure Configuration for Host compliance standard. Click Show Details.
- In the Summary tab on the Compliance Standard Result Detail page, you can look at the results either by target or compliance standard rule. For this example, we will use Result by Compliance Standard Rule.
- In the navigational list, click the Secure Ports compliance standard rule. In the resulting Secure Ports Summary tab, you will get a list of all the targets that are violating the Secure Ports rule. This is a security issue that needs to be addressed.
48.2.6.2 Viewing All the Violations Reported for Your Enterprise
If you want to see all the targets that are not compliant with the compliance standards:
-
From the Enterprise menu, select Compliance, then select Results.
You have the option of viewing violations associated with compliance standards and compliance frameworks.
-
Click the Target Compliance tab for a roll-up view of all violations across all targets, that is, all those targets that are out of compliance.
-
Click the Compliance Standards tab to view the list of compliance standards against which there are violations. From this tab, you can also access the Errors tab to view the errors against the compliance standard.
-
-
Navigate to the Home page for a particular target. The Compliance Standard Summary region lists the compliance violations according to severity level. Click the name of the compliance standard of interest to view the details of the violations.
48.2.6.3 Examples of Viewing Violations
As noted in the previous sections, the compliance feature provides violation details that help you resolve compliance issues. There are a number of ways to access violation details.
Violations are available from the following:
-
Compliance Summary region located on the Enterprise Summary page.
You can easily see the violations against compliance frameworks and compliance standards.
-
Compliance Results page. From the Enterprise menu, select Compliance, then select Results.
The following are examples of how to find violation details.
Example 1 - Accessing Violation Details of a Compliance Framework
To see the violations of a compliance framework, click the Compliance Frameworks tab then the Evaluation Results tab. The Violations columns list how many violations exist for each framework. When you click the number in a Violations column, all the targets with their associated compliance standards are listed.
In turn, when you click the number in the Violation Count column, the resulting Violations page lists the compliance standard rule that is violated. Again when you click the number in the Violation Count column, the resulting Violation Details page lists all metrics for a particular compliance standard rule that are responsible for the violations.
Example 2 - Accessing Violation Details of a Compliance Standard
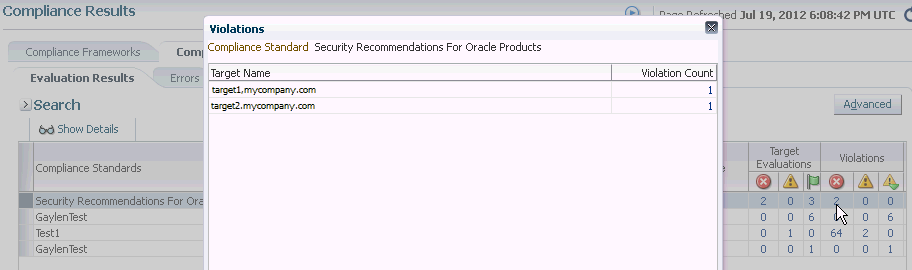
When you click the Compliance Standards tab then the Evaluation Results tab, the Violations columns report how many violations exist for each compliance standard.
When you click the number in a Violations column, the Violations pop-up appears listing all the targets violating the standard.
Figure 48-1 Violations for a Compliance Standard
Again, click the number in the Violation Count column and the Violations pop-up appears. All the Compliance Standard Rules, for example Security Recommendations, are listed.
You continue the process by clicking the number in the Violation Count column again in the Violations pop-up. The subsequent pop-up displays the Violations Details. For example, the Violations Details pop-up displays the name of the patch that is causing the problem.
Example 3 - Accessing Violations of a Target
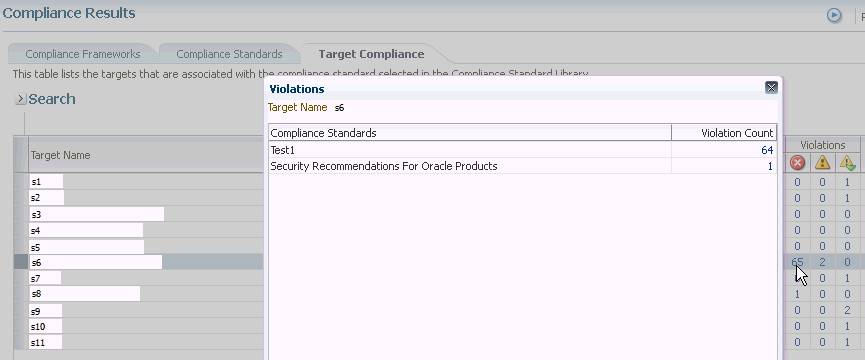
When you click the Target Compliance tab, the Violations columns report how many violations exist for each target.
When you click the number in a Violations column, the Violations pop-up appears listing all the targets violating the standard. See Figure 48-2.
Figure 48-2 Violations Using the Target Compliance Tab
Again, click the number in the Violation Count column and the Violations pop-up appears. All the Compliance Standard Rules, for example Security Ports, are listed.
You continue the process by clicking the number in the Violation Count column again in the Violations pop-up. The subsequent pop-up displays Violations Details. For example, the Violations Details pop-up displays the numbers of the ports violating the compliance standard.
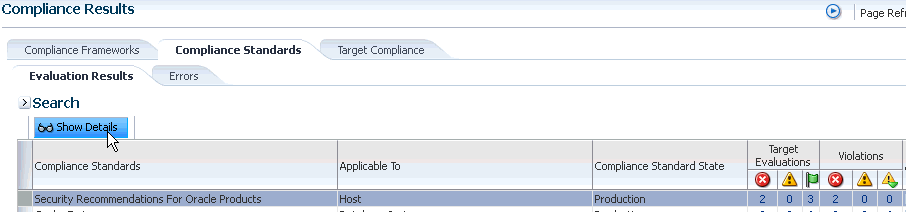
Example 4 - Violations Using Show Details on Compliance Standards Page
You can also drill-down on violations using the Show Details option on the Compliance Results page. Highlight a standard and click Show Details. See Figure 48-3.
On the resulting page, you have the option of seeing violations by target or by compliance standard rule.
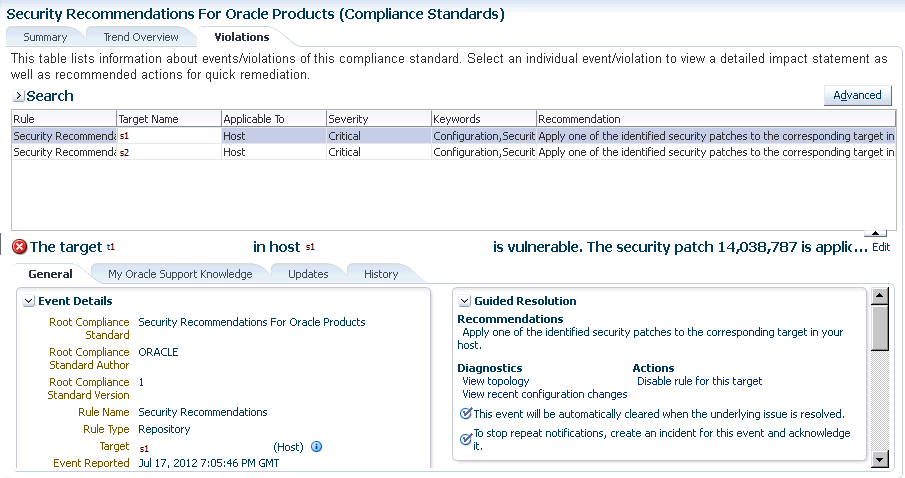
When you click the Violations tab, details regarding the compliance standard are listed including Event Details and Guided Resolution. See Figure 48-4.
Figure 48-4 Event Details and Guided Resolution
Example 5: Accessing Violations from Enterprise Summary Page
When you click the name of a compliance standard in the Compliance Summary region of the Enterprise Summary page, the Compliance Standard Result Detail page appears. By clicking the Violations tab, you can view all the targets that violate the particular compliance standard. See Figure 48-5.
Figure 48-5 Compliance Summary Region on Enterprise Summary Page
On the Compliance Standard Result Detail page, when you click the Summary tab then the Result By Target tab, the number of violations against the target display. When you click a number in the violations columns, the Violations pop-up appears listing the compliance standard rules that are causing the violation. In turn, when you click the number in the Violation Count column, the name of the offending metric or patch displays.
Note: Similar drill-downs are available from the Target Compliance tab.
Tip: To get to the end result of a Violation, continue clicking the number in the Violation Count column. More and more details are presented, narrowing the cause of the problem.
Note: Target evaluations are only one level while Violations are multi-level.
48.2.7 Investigating Evaluation Errors
The Evaluation Errors page reports statistics about the problems encountered during the evaluation. On initial display, the Evaluation Errors page shows all the evaluation errors.
-
Use the Evaluation Errors page to view the errors that occurred as a result of metric collection, as well as those that occurred during the last evaluation.
-
Use the search filter to view only those evaluation errors that meet a set of search criteria that you specify.
-
Click the message in the Message column to decide what your course of action should be to resolve the error.
-
Normally the results of an evaluation overwrite the previous evaluation's results. However, in the case of evaluation failure or data provider collection failure, the previous results are left untouched.
After the underlying problem is fixed, the error will no longer be reported.
Search Filter for Evaluation Errors
By default, all the evaluation errors in your enterprise configuration appear in the results table. However, you can specify a set of search criteria and then perform a search that will display only the evaluation errors that meet those criteria in the results table.
For example, if you choose Host in the Target Type list, contains in the Target Name list, and "-sun" in the adjacent Target Name text field, and then click Go, Cloud Control displays, in the results table, only the compliance standard rule evaluation errors for the hosts that contain "-sun" in their names.
48.2.8 Analyzing Compliance Reports
Cloud Control provides reports specific to compliance. To access these reports:
- From the Enterprise menu, select Reports, then select Information Publisher Reports.
- Scroll to the Compliance section
Compliance reports include the following:
-
Descriptions reports
The Descriptions reports list all the available compliance standards, compliance frameworks, and compliance standard rules available in the Compliance Library. These reports enable you to decide whether additional compliance standards and compliance frameworks need to be defined for your enterprise to attain and maintain its compliance to the standards.
-
Results reports
The Results reports provide details of the various evaluations against compliance standards and compliance frameworks. Using the Results reports you can view, in one place, all the statistics regarding the compliance of your enterprise against the defined standards. To view the target that is most likely in need of your immediate attention, view the Target with Lowest AVG COMPLIANCE SCORE report. The following are examples of the reports provided:
-
Compliance Standard Results Details
Displays the compliance summary for all the compliance standards evaluated against a target. Data includes compliance score, compliant and non-compliant rules, violations, and last evaluation date.
-
Compliance Standard Result Summary
Displays the compliance summary of a particular compliance standard. For example, if there are three targets each reporting on Security Recommendations for Oracle Products compliance, the Result Summary rolls up the information into one report. Data includes average compliance score, the number of targets that need immediate attention, and the number of rules that are non-compliant.
-
Cloud control also provides a set of reports using the BI Publisher integration. The following reports are available:
-
Real-time Monitoring Violation Report
Shows current violations based on real-time monitoring rule type.
-
Compliance Summary Report
Shows current compliance score, compliance trends, top 10 least compliant system targets and framework violation summary for a specific Compliance framework and all second-level framework folders.
-
Observation Journal Report
Tabular report showing observations that have occurred over a period of time. The user can choose which targets and the start and end time for the report.
Note: To enable BI Publisher reports that include Compliance Frameworks to function, the user running the reports must have the EM_COMPLIANCE_OFFICER role.
48.2.9 Overview of Compliance Score and Importance
A target's compliance score for a compliance standard is used to reflect the degree of the target's conformance with respect to compliance standard. The compliance score is in the range of 0% to 100% inclusive. A compliance score of 100% indicates a target fully complies with the compliance standard.
During an evaluation, a target is found to be compliant or non-compliant with that compliance standard.
Types of Importance
Importance is a setting that the user can make when mapping compliance frameworks, standards, and rules. The importance is used to calculate the affect a compliance violation will have on the compliance score for that framework control area or compliance standard.
For compliance frameworks, when mapping a compliance standard, the importance for this compliance standard indicates the relative importance to other compliance standards in this framework.
For compliance standards, when mapping a compliance standard rule, importance indicates the relative importance of a compliance standard rule to all other compliance standard rules in the compliance standard.
However, just because a compliance standard rule has an importance of 'low' does not mean that it can safely be ignored. All compliance violations should be triaged and cleared once the risk has been removed through a fix or a compensating control.
Importance is used to weight compliance scores as they roll up in a compliance standard hierarchy.
The following sections provide examples of how the compliance score is calculated.
48.2.9.1 Compliance Score of a Compliance Standard Rule -Target
Note: This calculation is used for WebLogic Server Signature rules and Repository rules.
Compliance score of a compliance standard rule-target is calculated by taking the severity and importance of the compliance standard rule and multiplying the result by the total number of violations divided by the total number of rows evaluated for that target.
The formula is:
hirange - (hirange - lorange) * (number of violations / number of rows evaluated)
The following table provides the combination of the severity and importance values used to calculate a compliance score.
Table 48-1 Importance and Severity Ranges
| Importance | Critical Severity (1) | Warning Severity (1) | Minor Warning Severity (1) |
|---|---|---|---|
|
High |
0-25 (2) |
66-75 |
95-96 |
|
Normal |
26-50 |
76-85 |
97-98 |
|
Low |
51-75 |
86-95 |
99-99 |
(1) low range and high range of the severity
(2) 0 is the lorange; 25 is the hirange
48.2.9.2 Real-time Monitoring Rule Compliance Score
The compliance score of a real-time monitoring rule is based on the number of observation bundles that have violations compared to how many observation bundles there have been over time. An observation bundle is a collection of all observations that happen over a short period of time (few minutes) by the same user against the same target. For instance, if user A is logged into a host and makes 10 file changes in 5 minutes. These 10 observations will all belong to the same bundle. The bundling is handled automatically by Enterprise Manager.
When calculating the count of past observation bundles, the most recent bundles are weighted higher and they have a different weighting as they get older.
The score is calculated using the formula:
1 - V/T
where T is the sum of all the weighted bundle counts
and V is the count of the current bundles in violation
The result of the calculation of 1-V/T will be a number around 1 as V is 0 (100% compliant) or will be a number near 0 when V is close to the value of T (0% compliant).
48.2.9.3 Compliance Score of a Compliance Standard for a Target
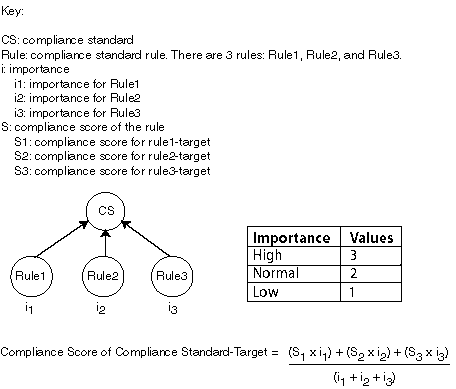
The compliance score of a compliance standard for each target is calculated by taking the individual compliance score of each rule - target and multiplying it by its importance. This multiplication is repeated for each rule then the resulting products are added. The sum of the products is then divided by the sum of the importance of each rule.
Figure 48-6 How Compliance Score of a Compliance Standard-Target Is Calculated
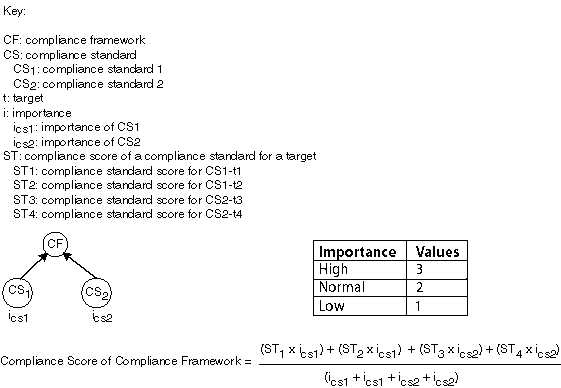
48.2.9.4 Compliance Framework Compliance Score
The compliance framework score is a rolled up weighted average of all compliance standard-target scores across all compliance standards within the compliance framework hierarchy. The weight is based on the importance of a compliance standard. In the following graphic, compliance framework CF has 2 standards CS1 and CS2. CS1 is associated and evaluated on targets t1 and t2 and CS2 is associated and evaluated on targets t3 and t4.
Figure 48-7 How Compliance Score of a Compliance Framework Is Calculated
48.2.9.5 Parent Node Compliance Score
The compliance score of a hierarchy node/parent node is calculated as shown in Figure 48-8. Compliance standards are hierarchical, thus the top node in the tree is known as the parent node.
Figure 48-8 Compliance Score of Parent Node
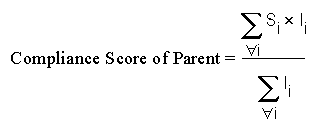
Description of "Figure 48-8 Compliance Score of Parent Node"
In Figure 48-8:
-
i represents the number of children
-
S is the score of the child node
-
I is the importance of the child node
48.3 Investigating Real-time Observations
As previously described, observations are the actions that were seen on a host or target that were configured to be monitored through real-time monitoring rules. Each distinct user action results in one observation.
Observations can have one of many audit statuses. The basic audit status "unaudited" means that the observation was detected, there just is no indication that this action was good or bad. The authorized status means that some review has happened for the observation and it should be treated as expected to occur (it was a good change). The unauthorized status means that this observation has been reviewed and has been found to be against policy. This may result in either a corrective fix, a change to policy, or a compensating control being put in place. The audit status for observations can be automatically set by a rule so that all observations triggered by the rule get a default audit status. The status can also be set manually through the UI reports discussed below. The most advanced capability involves integrating with a Change Management Request server through a Cloud Control connector to automatically determine on a per-observation basis if that action was supposed to happen.
The following sections provide additional details regarding real-time monitoring observations:
48.3.1 Viewing Observations
There are four key ways to see what real-time monitoring observations have occurred in your environment:
The first three observation screens are available from the Enterprise menu by selecting Compliance, then selecting Real-time Observations. This page that lets you choose which of the three reports to look at and also shows any Management Agent warnings related to configuration of Real-time monitoring rule configuration. These warnings are reported from the Management Agent and could impact observations from being delivered to the Cloud Control server. If you are missing observations that are expected, review these warnings and address any configuration issues that is causing them.
48.3.1.1 Viewing Observations By Systems
When observations occur, they can be marked as authorized or unauthorized automatically. This provides one way you to find observations that are important for you to look into. However, if a rule is not configured to reconcile observations with a change management server, it can be difficult to find the observations that are important to you through only an attribute search. Being able to view observations by business application (generic systems) and drilling down into observation details allows you to discover where there may be issues that should be investigated regardless of the observation's audit status.
Typically, IT managers and line of business owners must identify when unwanted configuration drift occurs in their business applications. By browsing observations by systems, you can easily see which changes affect specific business applications. Observations can be filtered by whether they are authorized, unauthorized, unaudited or both. They can also be filtered by time.
This begins with you choosing one or more business applications and being able to see the relative counts of observations. This report starts at the business application level (generic systems) because an IT manager and compliance auditor may not know what a target is used for. A business application is modeled in Cloud Control as a generic system.
If you are more technical, you still may want to start at this business application level if this is the business application you are working on.
To view observations by systems, follow these steps:
48.3.1.2 Viewing Observations By Compliance Framework
The ability to view observations as they relate to a compliance standard structure is something that is typically done by a non-technical role such as an IT Manager, Line of Business Owner, Compliance Manager, or Executive.
You can identify some set of Compliance Frameworks that reflect the IT compliance framework that the organization follows. Observations can be filtered by whether they are authorized, unauthorized, unaudited or both. They can also be filtered by time.
To view observations by Compliance Framework, follow these steps:
This drill-down capability provided by these screens makes it easy for you to easily find where observations are occurring. When you have an environment with tens of thousands of targets across hundreds of business applications, it is impossible to view observations simply using a table and search unless you know exactly the search conditions they are looking for. In a matter of an hour, with this large of an environment even with little activity, there can be thousands of observations.
48.3.1.3 Viewing Observations By Search
For cases when the two browse by screens cannot provide the best view of what observations have happened in your environment, Cloud Control also provides a search capability to find observations.
To search observations, follow these steps:
48.3.1.4 Viewing Details of an Incident
Observations are logically bundled together based on the compliance standard rule, target and user that performed the action. This bundling is discussed in more detail in Creating a Real-time monitoring Rule section.
When one or more observations of a bundle are unauthorized, the bundle is considered to be in violation. This violation will lead to an event being created in Cloud Control Incident Management. The event name will be based on the message field defined in the real-time monitoring rule. When viewing this event in the incident management UI, several fields will show details of the bundle; the target type, entity type, number of observations in the bundle, observations by audit status, and so on. You can click on the Update Audit Status link to go to the bundle observations page.
This Observations page shows the list of observations in the observation bundle for this event. You can filter on various attributes for each observation, including but not limited to the authorized/unauthorized status, user, time, and so on.
48.3.2 Operations on Observations During Compliance Evaluation
The following sections describe how a real-time monitoring observation's audit status can be adjusted and how notifications can help in evaluating compliance results.
48.3.2.1 Manually Setting an Observation As Authorized Or Not Authorized
Any time a user is viewing the details of a real-time observation, the user can change the audit status for the observation. You can override the audit status of an observation if you investigate the user action and determine that the activity should have resulted in a different audit status. Based on the real-time monitoring rule, all observations will either have a pre-set audit status or will have an audit status determined by an integration with a Change Request Management server. The available audit statuses are:
-
Unaudited: No evaluation has happened to determine if the observation was good or bad.
-
Authorized: The observation has been determined to be good, some action that was desired to occur.
-
Unauthorized: The observation has been determined to be bad, some action that was not wanted.
-
Unauthorized-Cleared: The observation had previously been determined to be bad, some action that was not wanted, but it has been handled through a fix, a policy change, or a compensating control and has now been cleared.
To change the audit status of an observation, view the observation from either of the browse by UI pages, the observation search page, or the incident manager UI. Select the observation and click Update Audit Status. A popup will come up allowing you to select the new audit status and a comment describing the reason for the status change. The history of all audit status changes is maintained for each observation.
If the Cloud Control instance is using the Change Request Management server connector for integration, there are some special considerations:
-
If you change an unauthorized observation into an authorized observation, then you have the option of entering a change request ID that is known to authorize the change. This change request ID should match a request that already exists in your change request management system. You can also enter a comment. If a change request ID is provided, then the change request is annotated with the change just as if the system had automatically authorized it. If an incident had been created for the observation bundle, then the event/incident is updated with the new number of unauthorized observations.
-
If you change an authorized observation into an unauthorized or unaudited observation, any annotations that were made to any change requests are rolled back. If there was already an incident raised for the observation bundle, then the annotation is changed to update the number of unauthorized observations in the incident. If this is the first unauthorized observation in a group, then an event is created an incident is raised. You can provide a comment for the change.
-
When you manually set the observation to be authorized and enter a change request ID and the rule has change management integration enabled, no attributes of the change request are compared with the observation. The change request is simply updated with the observation details.
-
When rolling back annotations in the change management server, the observation annotations are marked as rolled-back instead of actually removing the annotation. This occurs to avoid user confusion not knowing possibly why the annotations were removed. Also, if the observation later becomes authorized again, the rolled-back marking can simply be removed to bring the annotation back.
48.3.2.2 Notifying a User When an Observation Occurs
If a compliance standard rule is created and you do not use change management reconciliation with the rule, then there will be no automated authorized/unauthorized check done on the observations. You can specify for this rule that each observation bundle should result in informational event being generated for the observation bundle. Details on how to configure this is in the section Creating a Real-time Monitoring rule.
The event will have a notation. From the Incident Management console the user can look at events and incidents. When looking at a single event, there is a link available to see the observations associated with this observation bundle's event. Each observation bundle can only have one event. If at least one observation in the bundle is unauthorized, then the bundle is considered to be in violation which results in the event being generated.
Since this notification does not require user intervention or follow-up action, it is treated as informational. If at a later time, someone changes one of these unaudited observations into an authorized or unauthorized one, a new informational event for the unaudited observations will not be re-delivered. It is delivered only once for the observation bundle. However if one of the observations is manually set to unauthorized, then a violation is raised for the entire observation bundle.
When at least one observation in a bundle is in an unauthorized state, a violation is created. That violation becomes an event in the Incident Manager Console. Use the Incident Manager feature to set up a notification. For more information about this, on the Incident Manager page, click on the online help link, Setting Up Notifications With Rules under the Setting Up Notifications section under Getting Started.
48.3.2.3 Notifying a User When an Authorized Observation Occurs
When an authorized observation occurs, it is not typical for you to receive a notification on these observations since the activity that caused the observation was expected. If you are using change management reconciliation, you have an option to annotate the authorizing change request with the observation details. The updates to the change request is one way customers can learn of authorized activity. You can set filters in their change management system to let them know that a change request has had authorized activity against it.
48.4 Configuring Compliance Management
Before you can use the compliance features, compliance frameworks, compliance standards, and compliance standard rules must be defined for your enterprise.
The following sections describe how to define and maintain these compliance entities.
48.4.1 About Compliance Frameworks
A compliance framework is a hierarchical structure where any node can be mapped to one or more compliance standards, compliance standard rule folders, and compliance standard rules. Compliance frameworks provide a way to map your standards to a structure similar to the regulatory or standards-based compliance structure you use in your company.
Managing Compliance Frameworks
To manage compliance frameworks, follow these steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
Click Compliance Frameworks tab.
-
Highlight the compliance framework you want to manage and choose the action you want to perform.
Frameworks Provided by Oracle and User-Defined Compliance Frameworks
There are compliance frameworks provided by Oracle and user-defined compliance frameworks.
-
Compliance frameworks provided by Oracle include
-
Oracle Support Compliance is a collection of controls that check for expected environment compliance for Oracle Supportability.
-
Oracle Generic Compliance Framework is a standard set of compliance standards and associated controls for tracking changes and events taking place across your IT infrastructure for determining how well your organization is in compliance with your IT policies.
-
Security Technical Implementation Guide (STIG) is a set of standards to ensure Security Technical Implementation Guide (STIG) compliance.
-
-
User-defined compliance frameworks
You can define a compliance framework to satisfy the needs of your organization.
Compliance frameworks provided by Oracle cannot be deleted or edited. However, if you want to extend these frameworks, use the Create Like functionality to create your own user-defined frameworks based on the Oracle provided frameworks and then edit the new frameworks.
Recommendation: It is highly recommended that you create a top level compliance framework like the ones provided for STIG and Oracle Generic compliance.
Benefits of Using Compliance Frameworks
Compliance standards are defined to perform tests on targets. Examples include: testing if a configuration value is set properly, test to see if real-time file changes are occurring, and so on. A compliance framework is a way to map how different control areas of your compliance initiative are going to be affected by the results of those tests.
An organization may choose to define a compliance framework that extends an Oracle provided compliance framework. This is accomplished by creating a new compliance framework like the Oracle provided compliance framework and include new or existing compliance standards.Then each compliance standard is mapped to an appropriate framework hierarchy folder so that any violation against the standard is also mapped to that framework folder. Each folder in the framework represents one control area.
Reasons for Using Compliance Frameworks
There are a number of reasons for creating compliance frameworks including:
-
Mapping underlying IT violations to the regulatory and standard compliance controls used by your company so you can easily identify the compliance control areas that will be affected by the violations
-
Compliance auditing at compliance specification level
-
Auditing, security evaluation, and trend analysis
What Compliance Frameworks Can Do
A compliance framework can:
-
Represent industry-standard compliance control areas or can be created to match your internal frameworks in use.
Many companies may start by using an industry-standard framework, but modify it according to their own needs and auditing requirements.
-
Help in IT audits by identifying which compliance controls are at risk and may need compensating controls based on the violations. Without mapping your compliance checks to the control areas affected, it is hard to identify what the real impact would be in a compliance audit.
-
Since compliance frameworks can contain compliance standards of different types (Repository, WebLogic Server Signature, Real-time monitoring), they provide a good way of grouping similar checks of different types for reporting purposes.
Usage Note
Evaluation Results for a repository rule may become invalidated if a compliance standard rule within a compliance framework is modified or deleted. Evaluation of a compliance standard always references the current compliance standard rule definition for each compliance standard rule within the compliance standard.
48.4.2 Operations on Compliance Frameworks
You can perform the following operations on a compliance framework:
The following sections explain these operations.
Note: Before you perform any of the operations on compliance frameworks, ensure you have necessary privileges. For example, when creating a compliance framework, ensure you have access to the compliance standards you will be including during the definition of the framework. (See Roles and Privileges Needed to Use the Compliance Features.)
48.4.2.1 Creating a Compliance Framework
To make the creation for the compliance framework easier, ensure that the compliance standards, which will be referred to by the compliance framework, are already defined in the Cloud Control. You can add system out-of-the-box and user-defined compliance standards to any hierarchical element of the compliance framework. If you do not define the compliance standards before hand, you must add them later.
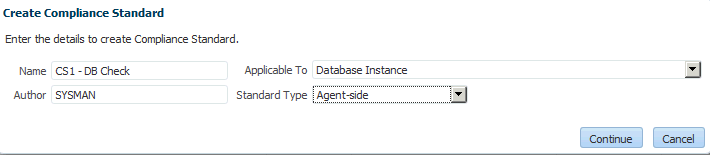
To create a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- Click Create button.
- Provide the Name and Author and click OK.
- Once you have provided the information on the definition page, look at the options available when you right-click the name of the compliance framework (located at the top-left of the page). From this list you can create subgroups, include compliance standards, and so on.
- Click Save.
Usage Notes
-
Lifecycle status can be either Development or Production.
-
Development
Indicates a compliance framework is under development and that work on its definition is still in progress. While in development mode, all management capabilities of compliance frameworks are supported including editing of the compliance framework and deleting the compliance framework. Results of development compliance standards will NOT be viewable in target and console home pages, and the compliance dashboard.
Lifecycle status default is Development. It can be promoted to Production only once. It cannot be changed from Production to Development.
-
Production
Indicates a compliance framework has been approved and is of production quality. When a compliance framework is in production mode, its results are rolled up into a compliance dashboard, target and console home page.
Production compliance frameworks can only refer to Production compliance standards. A production compliance framework can be edited to add/delete references to production compliance standards only.
Lifecycle status cannot be changed from Production to Development.
-
-
All compliance frameworks with the same keyword will be grouped together when sorted by the Keyword column.
-
If you modify a repository or WebLogic Server signature compliance standard that has been added to a compliance framework, either by editing the compliance standard directly, or by using Import to overwrite the compliance standard with new settings, the existing evaluations become invalid. That is, if this modified compliance standard was included in a compliance framework that was previously evaluated, and has evaluation results, these results are no longer viewable.
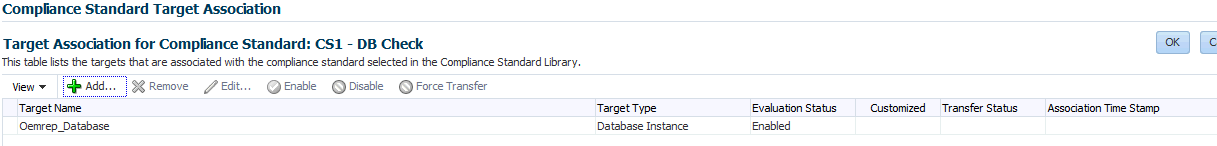
Adding a Compliance Standard to a Compliance Framework
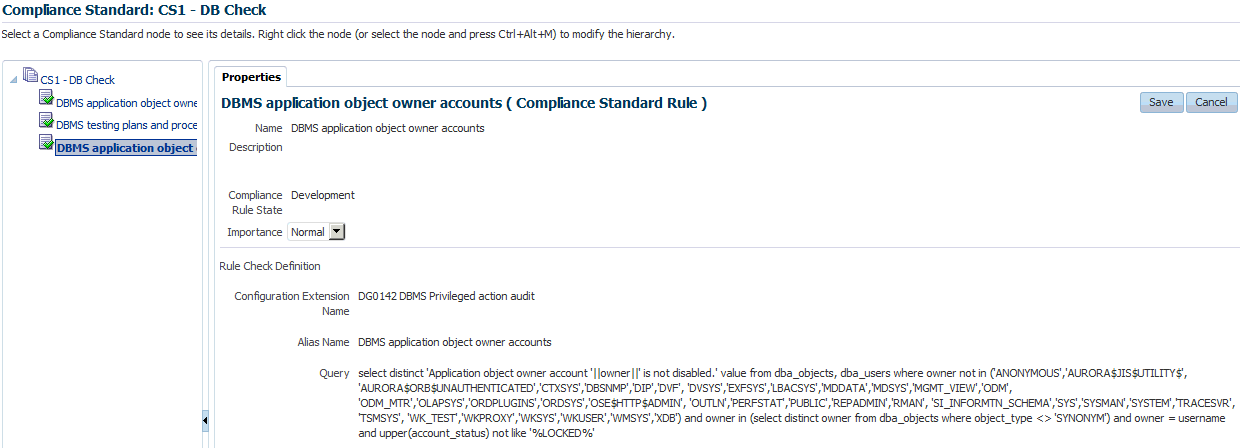
Click on a framework folder element that you want to map a compliance standard to. Right click and select Add Standards to bring up a popup to allow you to select the standards to map to this folder.
Use the search criteria to minimize the number of compliance standards that display in the select list.
Once you make your selections, click OK. The framework hierarchy screen refreshes and shows your newly included compliance standards under the framework folder element.
Editing Importance
After you map the compliance standards that are to be part of the selected compliance framework folder, you can edit the importance of each compliance standard for this specific folder.
The importance impacts the way the compliance score is calculated for this compliance standard in this framework folder.
See Overview of Compliance Score and Importance for details on how this score is computed.
48.4.2.2 Creating Like a Compliance Framework
To create a compliance framework like another compliance framework, follow these steps:
48.4.2.3 Editing a Compliance Framework
Use the edit compliance framework feature to add new compliance standard rules to a compliance framework, or edit details of existing compliance frameworks, or remove compliance standards from the compliance framework.
To edit a compliance framework, follow these steps:
Usage Notes
-
Changing a compliance framework definition may impact trend analysis.
-
The compliance standards you add to a compliance framework may be system-defined and user-defined compliance standards as displayed on the Compliance Standard Library page.
-
If you modify a repository or WebLogic Server signature compliance standard that has been added to a compliance framework, either by editing the compliance standard directly, or by using Import to overwrite the compliance standard with new settings, the existing evaluations become invalid. That is, if this modified compliance standard was included in a compliance framework that was previously evaluated, and has evaluation results, these results are no longer viewable. The compliance framework evaluation results will again become visible after the next evaluation happens. The new evaluation includes the changes to the compliance standard within the compliance framework.
-
The importance impacts the way the compliance score is calculated for this compliance standard in this framework folder.
-
A compliance standard can be added to more than one compliance framework, and can have a different importance when added to a different compliance framework. For example, you could have a compliance standard called Check Password Expired which flags user accounts with expired passwords. This compliance standard may be a member of two compliance frameworks: All System Passwords Secure and 30-day Password Validation. The All System Passwords compliance framework verifies a password's security, whereas the 30-day Password Validation compliance framework checks the date that this password was last set.
-
The Check Password Expired compliance standard could have Extremely High importance for the 30-day Password Validation compliance framework, since this check is warning users that their passwords are about to expire.
-
In the All System Passwords Secure compliance framework, the Check Password Expired compliance standard could have a Normal importance, and other added compliance standards that do security checks could have a higher importance within the compliance framework.
-
48.4.2.4 Deleting a Compliance Framework
To delete a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- Highlight the compliance framework you want to delete, click Delete button.
- Confirm that you want to delete the compliance framework by clicking OK.
Usage Notes
-
You can delete a single compliance framework or a list of compliance frameworks. When you delete a compliance framework, the associated metadata and evaluation results are also deleted.
-
YOU CANNOT DELETE COMPLIANCE FRAMEWORKS DEFINED BY ORACLE. These are indicated by the presence of a lock icon in front of the compliance framework name on the compliance framework listing page.
48.4.2.5 Exporting a Compliance Framework
The Export feature provides a mechanism for transporting user-defined compliance framework definitions across Management Repositories and Cloud Control instances. The export stores the definitions in an operating system file. Because the exported compliance framework definitions are in XML format, they conform to the Oracle Compliance Standard Definition (XSD) format. You can then change the definition of the compliance framework and re-import the generated compliance framework definitions into another Management Repository.
To export a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- Highlight the compliance framework you want to export.
- From the Actions menu, select Export.
- Provide the file name to which the compliance framework definition is to be exported. All leaf level rules and compliance standards are exported.
The system generates an XML representation of the compliance framework in the directory and file you specify.
48.4.2.6 Importing a Compliance Framework
Importing allows you to re-use a compliance framework that you already have, share framework definitions across multiple instances of Cloud Control, or enable offline editing of the framework.
Before you import a compliance framework, ensure the compliance framework to be imported is defined in a file. The file should be locally accessible to the browser you are using to access Cloud Control. Also ensure that you have privileges to access the compliance framework definition XML file to be imported.
Note:
When importing a compliance standard containing rules (or a framework containing standards) from the UI or command-line interface, import the xml file with <ComplianceContent> as root. This root file might have a list of rules, standards, frameworks, and standard groups.
This ensures that the framework and standard definition will be successfully imported. Also all associated targets will be re-evaluated based on the definition change made.
To import a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- From Actions menu, select Import.
- Provide the file name from which the compliance framework definition (as per Compliance Framework XSD) will be imported. Specify whether to override an existing definition if one already exists. Specify whether to import referring content as well where all leaf level rules and compliance standards are imported. Real-time monitoring facets are also imported for real-time monitoring type of rules.
- Click OK.
48.4.2.7 Browsing Compliance Frameworks
To browse a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- To view the details of a particular compliance framework, highlight the compliance framework and click Show Details.
48.4.2.8 Searching Compliance Frameworks
To search for a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
48.4.2.9 Browsing Compliance Framework Evaluation Results
To browse compliance framework evaluation results, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Frameworks tab and then the Evaluation Results tab.
- Highlight the compliance framework and click Show Details to view the details of a particular compliance framework.
Results include the following:
-
Average compliance score for different targets evaluated for compliance standards referred to by the compliance framework
-
Count of target evaluations (critical, warning, compliant) for different compliance standards referred to by the compliance framework
-
Count of violations (critical, warning, minor warning) related to compliance standards referred to by the compliance framework
48.4.2.10 Searching Compliance Framework Evaluation Results
To search compliance framework evaluation results, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Frameworks tab and then the Evaluation Results tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
48.4.2.11 Browsing Compliance Framework Errors
To browse compliance framework errors, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Frameworks tab and then the Errors tab.
Usage Notes
The error may be an unexpected internal error or an error in the test.
Evaluation errors can often be due to configuration and installation issues. See the following manuals for information:
-
Oracle Enterprise Manager Cloud Control Basic Installation Guide
-
Oracle Enterprise Manager Cloud Control Advanced Installation and Configuration Guide
If the installation and configuration are correct and the errors persist, call Oracle for assistance.
48.4.2.12 Searching Compliance Framework Errors
To search for compliance framework errors, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Frameworks tab and then the Errors tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
Usage Notes
The error may be an unexpected internal error or an error in the test.
Evaluation errors can often be due to configuration and installation issues. See the following manuals for information:
-
Oracle Enterprise Manager Cloud Control Basic Installation Guide
-
Oracle Enterprise Manager Cloud Control Advanced Installation and Configuration Guide
If the installation and configuration are correct and the errors persist, call Oracle for assistance.
48.4.3 About Compliance Standards
A compliance standard is a collection of checks or rules. It is the Cloud Control representation of a compliance control that must be tested against some set of IT infrastructure to determine if the control is being followed.
Compliance standards are made up of the following in a hierarchical structure (see Figure 48-9):
-
Compliance standard rules
-
Rule folders that can include nested rule folders and individual compliance standard rules.
Rule Folders are hierarchical structures that contain compliance standard rules. A rule folder has an importance attribute that denotes the importance of the rule folder relative to its siblings at the same level. This importance is considered when determining compliance scores being rolled up from other sibling rule folders. A certain rule folder may have multiple tests that occur, in this way a certain test can be given more weight than other tests.
-
Included compliance standards. A compliance standard can include other compliance standards.
Figure 48-9 Compliance Standard Definition
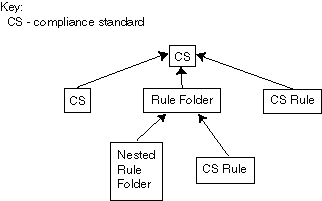
Description of "Figure 48-9 Compliance Standard Definition"
What Compliance Standards Can Do
-
Can represent industry-wide standards. A compliance standard is applicable to a single target type.
-
Be used as a reference configuration or a certified configuration
-
Be a collection of compliance standard rules describing best practices in an enterprise
For example, when a target fails to adhere to a compliance standard, the target is not in compliance with the compliance standard.
Accessing Compliance Standards
The compliance standards, including those provided by Oracle, are available on the Compliance Standard Library page. To access this page, follow these steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
Click the Compliance Standards tab.
To view the compliance standard rules associated with the compliance standard, click the name of the compliance standard and click Show Details. Once the Compliance Standard Detail page appears, right click the name of the standard located at the top left of the page, and select either Collapse, Expand All Below or Collapse All Below.
Note: The compliance standards defined by Oracle cannot be changed. However, you can create a standard similar to the one provided by Oracle by using the Create Like feature.
General Usage Notes for Compliance Standards
You can override an existing compliance standard by checking the Overwrite existing compliance standards check box. As a result, evaluations of compliance standards require that the compliance standard is associated to one or more targets.
-
For repository compliance standards, evaluation starts after the standard is associated with a target based on data collected from that target in the Management Repository.
-
For WebLogic Server compliance standards, evaluation happens when the Management Agent-side evaluation metric is refreshed. The refresh occurs once every 24 hours for Oracle WebLogic Domain, Oracle WebLogic Java EE Server, and Oracle WebLogic Cluster targets.
-
For Real-time Monitoring compliance standards, monitoring at the Management Agent starts when a compliance standard is associated to a target. A violation occurs when an observation bundle contains at least one observation that is unauthorized
Usage Note Specific to Repository Rules
If you manually type a WHERE clause in the compliance standard rule XML definition, then the < (less than) symbol must be expressed as <, to create a valid XML document. For example:
<WhereClause>:status < 100</WhereClause>
Example of How to Set Up Compliance Standards for Auditing Use
For auditors to verify that database targets are in compliance with the compliance frameworks, the Cloud Control structure needs to be defined. The steps to provide this structure includes the following:
-
Super Administrator creates three Cloud Control users: Compliance Author, IT Administrator, and Compliance Auditor.
-
Super Administrator assigns the appropriate roles and privileges to the Compliance Author and IT Administrator.
-
Super Administrator assigns the same target privileges to IT Administrator and Compliance Auditor.
-
Compliance Author logs in to Cloud Control and views Oracle provided compliance frameworks, compliance standards, and compliance standard rules.
He then enables and disables the appropriate compliance standard rules and creates new compliance standard rules.
-
IT Administrator logs in to Cloud Control and associates the targets for which he has target privileges with the appropriate compliance standards.
-
IT Administrator sets up the correct configuration parameters and settings for the compliance frameworks, compliance standards, and compliance standard rules for a particular target.
He then creates a monitoring template from this target and applies it to the other targets, to which he has privileges, that require compliance standards.
-
Compliance Auditor logs in to Cloud Control to view the compliance dashboard, violations and errors at the Enterprise level, for which he has view privileges, and at each target level.
He would then take the necessary actions to rectify the errors and violations.
48.4.4 Operations on Compliance Standards
You can perform the following operations on a compliance standard:
The following sections explain these operations.
Note: Before you perform any of the operations on compliance standards, ensure you have necessary privileges. For example, when creating a compliance standard, ensure you have access to the compliance standard rules you will be including during the definition of the compliance standard. (See Roles and Privileges Needed to Use the Compliance Features.)
48.4.4.1 Creating a Compliance Standard
You can use the compliance standards provided by Oracle, for example, Security Configuration for Oracle Database, or create your own standard.
Before creating a compliance standard, ensure the compliance standards and compliance standard rules, which will be referred to by the compliance standard, are defined in the Management Repository.
To create a compliance standard, follow these steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
Click the Compliance Standards tab.
-
Click the Create button. You will prompted for the Name, Author, target type to which the standard is applicable., and the standard type. The standard types are:
-
Repository
-
WebLogic Server Signature
-
Real-time Monitoring
-
Agent-side
Click Continue.
-
-
On the resulting Properties tab, provide the property values.
Click Add to either add a keyword by which this standard is identified or use an existing keyword.
-
To further define the compliance standard, right-click the name of the compliance standard located at the top left of the page. From this menu, you can create rule folders, add rules, and included compliance standards.
By using rule folders, you can view the summary of results, categorized by the targets that were evaluated against the selected rule folder and the Compliance Standard Rules evaluated for the selected rule folder.
-
Click Save.
Once you define the compliance standard, associate the standard with a target and define the target type-specific settings.
-
While on the Compliance Standards Library page, ensure the correct compliance standard is highlighted.
-
Click the Associate Target button.
-
On the Target Association for Compliance Standard page, click Add to choose the target to be evaluated against the standard.
-
In the Search and Select: Targets popup, choose the appropriate targets.
-
Click Select.
After you associate the targets with the compliance standard, you can edit the parameters associated with the target.
-
While on the Target Association for Compliance Standard page, click Edit.
-
On the Customize Compliance Standard Parameters page, change the parameters as needed.
Note:
You can also associate a compliance standard with a target from the target home page. At the top left of the target's home page, right click the name of the target. On the resulting menu, select Compliance, then select Standard Associations.
Including a Compliance Standard into Another Compliance Standard
Use the Include Compliance Standard page to select one or more compliance standards to be included into the compliance standard. This list is prefiltered by the target type of the compliance standard.
To include a compliance standard into another compliance standard:
Usage Notes
-
Because compliance standards are hierarchical, the top node in the tree is known as the root node.
-
When you create a compliance standard, the version is 1.
-
Lifecycle status default is Development. It can be promoted to Production only once. It cannot be changed from Production to Development.
-
Development
Indicates a compliance standard is under development and that work on its definition is still in progress. While in Development mode, all management capabilities of compliance standards are supported including complete editing of the compliance standard, deleting the compliance standard, and so on. However, while the compliance standard is in Development mode, its results are not viewable in Compliance Results nor on the target or Cloud Control home page.
-
Production
Indicates a compliance standard has been approved and is of production quality. When a compliance standard is in production mode, you have limited editing capabilities, that is, you can add references to production rules, and you can delete references to rules ONLY from a compliance standard. All other management capabilities such as viewing the compliance standard and deleting the compliance standard will be supported. Results of production compliance standards are viewable in target and console home pages, and the compliance dashboard. Production compliance standards can only refer to production compliance standards and production compliance standard rules.
Once the mode is changed to Production, then its results are rolled up into compliance dashboard, target home page, and Cloud Control home page. Production compliance standards can only refer to other production compliance standards and production compliance standard rules. A production compliance standard can be edited to add and delete references to production compliance standards and production compliance standard rules only.
-
48.4.4.2 Creating Like a Compliance Standard
To create a compliance standard like another compliance standard, follow these steps:
48.4.4.3 Editing a Compliance Standard
You can customize compliance standards by editing the existing compliance standard rule settings. You can change the added rules' importance for the compliance score calculation, prevent template override, override default parameter values (when possible), and exclude objects from a compliance standard rule's evaluation (when possible).
Note: You cannot edit an Oracle provided compliance standard, that is, a compliance standard defined by Oracle.
To edit a compliance standard, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- Highlight the standard you want to edit and click the Edit button.
- Update the parameters as needed.
- Click Save.
48.4.4.4 Deleting a Compliance Standard
Before you delete a compliance standard, ensure the compliance standard is not in use by a compliance framework. You must remove any references to the compliance standard in all compliance frameworks.
Note: You cannot delete an Oracle provided compliance standard, that is, a compliance standard provided by Oracle.
To delete a compliance standard, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- Highlight the compliance standard you want to delete, click Delete button.
- Confirm that you want to delete the standard by clicking OK.
48.4.4.5 Exporting a Compliance Standard
The Export feature provides a mechanism for transporting user-defined compliance standard definitions across Management Repositories and Cloud Control instances. The export stores the definitions in an operating system file. Because the exported compliance standard definitions are in XML format, they conform to the Oracle Compliance Standard Definition (XSD) format. You can then change the definition of the compliance standard and re-import the generated compliance standard definitions into another Management Repository.
Before you export a compliance standard, ensure that you have privileges to access the compliance standard to be exported.
To export a compliance standard, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- Highlight the standard you want to export.
- From the Actions menu, select Export.
- Provide the file name to which the standard definition is to be exported. All leaf level rules and compliance standards are exported.
- The XML representation of the compliance standard is generated. The file is located in the directory you specify.
48.4.4.6 Importing a Compliance Standard
The Import feature uploads an XML-based compliance standard definition file containing definitions of a single user-defined compliance standard or a list of user-defined compliance standards. This upload creates a new user-defined compliance standard or a list of user-defined compliance standards. This compliance standard must have been previously exported.
The compliance standard xml definition must comply with the compliance standard XML Schema Definition (XSD) as defined in User-Defined Compliance Standard XML Schema Definition.
Before importing a compliance standard, ensure the compliance standard to be imported is defined in a file. The file should be locally accessible to the browser you are using to access Cloud Control. Also ensure that you have privileges to access the compliance standard definition XML file to be imported.
To import a compliance standard, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- From the Actions menu, select Import.
- Provide the file name from which the compliance framework definition (as per Compliance Framework XSD) will be imported. Specify whether to override an existing definition if one already exists. Specify whether to import referring content as well.
- Click OK.
You can override an existing compliance standard by checking the Overwrite existing compliance standards check box. As a result:
-
If you override a compliance standard, the override deletes all target and template associations, as well as evaluation results for that compliance standard.
-
If the overwritten compliance standard is part of a compliance framework, the compliance standard is updated in the compliance framework. However, the evaluation results for that compliance standard within the compliance framework are invalidated.
48.4.4.7 Browsing Compliance Standards
To browse a compliance standard, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- To view the details of a particular standard, highlight the standard and click Show Details.
48.4.4.8 Searching Compliance Standards
To search for compliance standards, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
48.4.4.9 Browsing Compliance Standard Evaluation Results
To browse compliance standard evaluation results, follow these steps:
48.4.4.10 Searching Compliance Standard Evaluation Results
To search for compliance standard evaluation results, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Standards tab and then the Evaluation Results tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
48.4.4.11 Browsing Compliance Standard Errors
To browse compliance standard evaluation errors, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Standards tab and then the Errors tab.
48.4.4.12 Searching Compliance Standard Errors
To search for compliance standard errors, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Standards tab and then the Errors tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
Usage Notes
-
Use the Evaluation Errors page to view the errors that occurred as a result of metric collection, as well as those that occurred during the last evaluation.
-
Use the search filter to view only those evaluation errors that meet a set of search criteria that you specify.
-
Click the message in the Message column to decide what your course of action should be to resolve the error.
-
On initial display, the Evaluation Errors page shows all the evaluation errors.
-
Normally the results of an evaluation overwrite the previous evaluation's results. However, in the case of evaluation failure or data provider collection failure, the previous results are left untouched.
Once the underlying problem is fixed, the error is no longer reported.
Example of Search Filter
By default, all the evaluation errors in your enterprise configuration appear in the results table. However, you can specify a set of search criteria and then perform a search that will display only the evaluation errors that meet those criteria in the results table.
For example, if you choose Host in the Target Type list, contains in the Target Name list, and "-sun" in the adjacent Target Name text field, and then click Go, Cloud Control displays, in the results table, only the compliance standard rule evaluation errors for the hosts that contain "-sun" in their names.
48.4.4.13 Associating a Compliance Standard with Targets
After you create a compliance standard, you can associate the standard with one or more targets. As part of the association, you can customize parameters, that is, the importance of the standard in relation to the target, status of the compliance standard evaluation, reason for changing the evaluation status, and the thresholds.
Before you associate a compliance standard with a target, ensure you have privileges to access the targets you want to associate compliance standards to.
To associate a compliance standard with a target, follow these steps:
To further customize the evaluation of a compliance standard against a target, you can alter compliance standard parameters: importance, critical threshold, and warning threshold. Customizations can also be made on the compliance standard rules used within the compliance standards. For example, for the Secure Ports compliance standard rule, DFLT_PORT is an override parameter. You can change the default value of the port. You can also exclude objects from the evaluation, for example a particular port from the evaluation.
Note: For real-time monitoring, you can change parameters that are used in facet patterns. You can also change Automatic Change Management reconciliation settings.
By changing critical and warning thresholds, you signify how the Compliance standard score event is generated. For example, if the actual score is less than the critical threshold, then a critical score event is raised.
Best Practices
You can perform compliance association in two ways: for testing and editing, and production and mass associations.
-
For testing and editing a standard/target and standard rule, or rule folder/target association settings purposes, associate the target with a compliance standard as previously described in this section.
Using the Compliance UI, you can:
-
Test the association and remove it after testing is complete.
-
Edit the association for importance, evaluation status, and thresholds.
Note: You cannot edit an association using the Administration Groups and Template Collections page.
-
-
For production and mass associations, associate the target using the Administration Groups and Template Collections page:
From the Setup menu, select Add Target, then select Administration Groups. Click the Associations tab.
Because each Administration Group in the hierarchy is defined by membership criteria, a target is added to the group only if it meets the group's membership criteria. Therefore, when a target is successfully added to a group, it is automatically associated with the eligible compliance standards for that group. This makes it easier to associate a target to a large number of compliance standards.
48.4.4.14 Associating a Compliance Standard with a Group Target
After you create a compliance standard, you can associate the standard with a group target. This enables the association of key standards to targets when they are part of the group.
Before you associate a compliance standard with a group target, ensure the following prerequisite is met:
-
You have privileges to access the group target you want to associate the compliance standards to
See Privileges and Roles Needed to Use the Compliance Feature.
Perform the following steps:
48.4.4.15 Viewing Real-time Monitoring Compliance Standard Warnings
When you associate a real-time monitoring compliance standard to targets, there is a chance that there are setup steps that were not followed on the target to enable real-time monitoring or there could be inconsistency with the configuration. Any warnings will be shown on the Associate Targets screen. This screen is reached by selecting a compliance standard and selecting Associate Targets button. If there are any warnings, there will be a warning icon with a link above the table of target associations. Clicking on this link will take you to a screen that lists all current warnings for this compliance standard.
All warnings can be fixed by correcting some configuration problem on the host/target you are monitoring or by fixing rule/facet content. Once the underlying problem is fixed, these warnings will be cleared automatically.
This list of warnings is also available on the Real-time Observations page (from the Enterprise menu, select Compliance, then select Real-time Observations) where you can pick one of three types of reports to view your observations. The bottom half of the screen shows all active warnings across all targets and compliance standards related to real-time monitoring.
48.4.4.16 Enabling Security Metrics
Because security collections are disabled by default, they must be enabled before using security features like security compliance standards, reports, and so on. To enable Security metrics, follow these steps:
- From the Enterprise menu, select Monitoring, then select Monitoring Templates.
- In the Search area, select Display Oracle provided templates and Oracle Certified templates and click Go.
- Select Oracle Certified-Enable Database Security Configuration Metrics and click Apply.
- In the Destination Targets region on the Apply Monitoring Template Oracle Certified-Enable Database Security Configuration Metrics: General page, click Add.
- On the Search and Select: Targets page, select the database instances in which you are interested and click Select.
- In the Destination Targets region of the Apply Monitoring Template Oracle Certified-Enable Database Security Configuration Metrics: General page, select the database instances in which you are interested and click OK.
After you click OK, a confirmation message on the Monitoring Templates page appears.
48.4.4.17 Considerations When Creating Compliance Standards
A compliance standard will refer to one or more Compliance Standard Rules. When creating a compliance standard, the standard should be granular enough that it can be appropriately mapped to one or more related Compliance Frameworks. For example, consider this Compliance Framework structure that exists in the Oracle Generic Compliance Framework:
-
Change and Configuration Management (compliance framework subgroup)
-
Database Change (compliance framework subgroup)
-
Configuration Best Practices for Oracle Database (compliance standard)
-
Configuration Best Practices for Oracle RAC Database (compliance standard)
-
Configuration Best Practices for Oracle Pluggable Database (compliance standard)
-
-
Many compliance standards will exist that should be mapped to this part of the Compliance Framework structure, each with their own rules to address this specific requirement. One may check that configuration settings are set properly. Another may be used to check in real-time if anyone changes a configuration setting.
In this example, the "Database Change compliance framework subgroup" can relate to many different types of targets. Oracle Database, Oracle RAC Database, and Oracle Pluggable Database all have their own types of configurations that all need to be secured. Any Standards created to monitor these target-specific configurations would map to the same "Database Changes subgroup".
If compliance standards are structured in a granular way so that they can map to existing and future compliance frameworks, then violations in a rule can be rolled up to impact the score of the compliance framework properly.
48.4.5 About Compliance Standard Rule Folders
Rule Folders are optional hierarchical structures used to group similar compliance standard rules within a compliance standard. You can add individual compliance standard rules to a compliance standard, or group them if you have a large number of rules in a standard. A compliance standard rule can be added to multiple Rule Folders within a compliance standard, each with different importance settings. Rule Folders can be nested within a compliance standard.
A rule folder has an importance attribute that denotes the importance of the rule folder relative to its siblings at the same level. This importance is considered when determining compliance scores being rolled up from other sibling rule folders. A certain rule folder may have multiple tests that occur, in this way a certain test can be given more weight than other tests.
The following topics address compliance standard rule folders:
48.4.5.1 Creating Rule Folders
To create a rule folder, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- On the Compliance Standard Library page, highlight the compliance standard and click Edit.
- On the Properties page, right-click the name of the compliance standard. The name of the standard is located in the top-left corner of the page.
- Select Create Rule Folder.
- Type the name of the folder and click OK.
- On the Properties page, provide a description, ReferenceUrl, and importance. See Overview of Compliance Score and Importance.
48.4.5.2 Managing Rule Folders in a Compliance Standard
After you create a rule folder and populate it with compliance standard rules, you can perform the following actions on the folder:
-
Edit the tree structure by re-ordering the Rule Folder, Rule Reference, and Compliance Standard Reference nodes in the tree or by deleting any of these nodes.
-
Select any node (except the top-level Compliance Standard node) object and then click Remove menu item from context menu. The Remove option is disabled on the root node. You can also select multiple objects and click Remove to delete multiple nodes.
48.4.6 About Compliance Standard Rules
A compliance standard rule is a test to determine if a configuration data change affects compliance. Based on the result of the test, a compliance score is calculated. These rule compliance scores are rolled up to compute the compliance standard score and then this score can be rolled up and reported along with the compliance framework scores.
Types of Compliance Standard Rules
There are three types of compliance standard rules are:
-
Used for detecting configuration problems on the agent. This enables the implementation of the Security Technical Implementation Guide (STIG) security specifications. Agent-side rules generate violations for a target which is based on the results data collected for the underlying configuration extension target.
-
Configuration Consistency rule
Determines the consistency of targets of similar target types within a composite target. For example, a user has a Cluster Database made up of 15 databases. He can use the Cluster Database Comparison Template for configuration consistency to flag databases that may have changed within the cluster.
-
Configuration Drift rule
Determines the deviation of targets of similar target types. For example, a user has 10 databases that he is monitoring. He needs to ensure that the Initialization Parameter File Permission compliance standard rule is the same across all the databases. This deviation can occur when the database configuration has been updated.
-
Manual rule
Enables you to account for checks that cannot be performed automatically, thus allowing you to account for these types of checks in the compliance framework.
For example, a common security check is "To ensure secure access to the data center". When a standard is associated to a target, each manual rule will have one violation. A user must manually attest to the positive status of the rule. In other words, a person responsible for the task ensures he has performed the task. The compliance framework records when and who clears the violation of the manual check so it can be reported.
-
Missing Patches rule
Used for detecting patches that have not been applied to the appropriate targets. This rule generates violations which appear on the compliance results UI and subsequent compliance dashboard regions. A rolled up violation count appears on the dashboard regions. The user can drill down to examine violation details and then correct the issue by applying the missing patches to the appropriate targets.
-
If the rule is based on a list of patches, then the rule checks if none of the patches are applied to the target. If any of the patches are applied, then no violation is generated. If none of the patches are applied, then one violation is generated listing the patches that are not applied.
-
The patch numbers can refer to Oracle recommended patches or manually entered patches.
-
After a patch is applied, the corresponding ORACLE_HOME configuration is uploaded. Oracle then reevaluates all associated missing patches rule for the target.
-
After you create the Missing Patches rule, you can add missing patches rules to compliance standards of type Repository. You can then associate the standard to targets by selecting a standard, and clicking the Associate Target button. Upon association, the missing patch rule will be evaluated on the applied targets.
-
If a standard with the missing patches rule is associated to a group, when new targets are added to the group, the new target is automatically evaluated for missing patches.
-
-
Real-time Monitoring rule
Monitors operating system and database level entities that store configuration data. Real-time monitoring rules define the entities to monitor, user actions to watch for, and any types of filters to apply to the monitoring. Monitoring can be filtered by: when changes occurred, who made the changes, and what process made the changes.
The real-time monitoring rule definition includes facets that are used to determine what is important to monitor for a given target type, target properties, and entity type. A facet is a collection of patterns that make up one attribute of a target type. For example, you may choose to define a facet that lists all of the critical configuration files for the Host target type. These configuration files would be the ones that, if changed, would most likely result in instability of the host. You may also create a facet that lists all users which are DBA users.
The real-time monitoring rule can be part of a compliance standard that is associated with one or more targets. The monitoring can occur on any operating system level entity, for example, file, process, user, registry, and so on. Real-time monitoring rules can additionally specify whether observations captured by the rule are automatically reconciled. This reconciliation determines whether the actions observed were authorized or not.
Change Request Management reconciliation compares open change requests to actions performed on targets. If there is a match of expected actions to actual actions, then those actions are authorized, otherwise they are unauthorized. Authorizations can also be done manually. All observations are captured and bundled by rule, target and user. Attributes can be set on the frequency of observation data collection.
-
Used to perform a check against any metric collection data in the Management Repository.
Used for checking the configuration state of one or multiple targets. A rule is said to be compliant if it is determined that the configuration items do in fact meet the desired state and the rule test failed to identify any violations. Otherwise, a rule is said to be non-compliant if it has one or more violations. The data source that is evaluated by a compliance standard rules test condition can be based on a query against the Cloud Control Management Repository. A compliance standard rules test condition can be implemented using a threshold condition based on the underlying metrics (or queries) column value or SQL expression or a PLSQL function. To use a rule, it must be associated to one or more compliance standards. The compliance standard then will be associated to one or more targets. This effectively enables this rule to be evaluated against these targets.
-
WebLogic Server Signature rule
Preemptively identifies WebLogic Server configuration problems. The purpose of the WebLogic Server Signature rules is to evaluate at the WebLogic Server if certain configuration data satisfies some conditions (or checks) and the evaluation results are sent as violation information to the Management Service.
Detailed information about how to identify problems is specified in the WebLogic Server Signature rule definition. The WebLogic Server Signature rule definition includes Dataspec and XQuery logic that are used to determine what is important to collect and evaluate for a given target type and target properties. A Dataspec is a group of MBeans used to collect from a WebLogic Server. The XQuery logic contains the check on the collected data (by the MBeans). The WebLogic Server Signature rule can be associated with one or more specific Web Logic targets: Web Logic Domain, Web Logic Java EE Server, and Web Logic Cluster.
Version-specific details include:
-
To enable data collection for the WebLogic Server signature-based rules on WebLogic Server targets earlier than v10.3.3, you need a copy of bea-guardian-agent.war. You can find a copy of this war file in your OMS installation's work directory: $T_WORK/middleware/wlserver_10.3/server/lib/bea-guardian-agent.war
-
For WebLogic Server v9 and v10.0
Install and deploy bea-guardian-agent.war to all servers in the domain. Do not change the context root. See
http://<host>:<port>/console-help/doc/en-us/com/bea/wlserver/core/index.htmlfor more information on installing a web application. -
For WebLogic Server v10.3 up to and including v10.3.2
Copy the war file from your OMS installation into each target's $WL_HOME/server/lib directory. Restart all the servers in the target domain.
-
For WebLogic Server v.10.3.3 and higher
No action is required.
-
48.4.7 Operations on Compliance Standards Rules
The following sections explain the operations you can perform on compliance standard rules.
Note: Before you perform any of the operations on compliance standard rules, ensure you have the necessary privileges. (See Roles and Privileges Needed to Use the Compliance Features.)
48.4.7.1 Creating a Repository Compliance Standard Rule
To create a repository compliance standard rule to check if a target has the desired configuration state based on collected configuration data, follow these steps:
Additional Notes for Repository Rules
-
All rules are visible in the global rule library and are visible to all users.
-
Once the compliance standard rule is created, it is not automatically evaluated. Users must associate a rule to a compliance standard before it can be used. Only when a compliance standard is associated with one or more targets will a rule evaluation occur. Rules cannot be evaluated directly.
-
One rule can be associated to multiple compliance standards.
-
Various attributes of a rule can be customized through the compliance standard this rule is associated with. These customizations occur in the Compliance Standard screens. One of these attributes that can be customized per compliance standard is the importance of the rule in relationship to this standard.
-
Because the user-defined compliance standard rule is defined by a privileged user, only privileged users can modify the compliance standard rule. Violation results are available to all users.
-
To share this user-defined compliance standard rule with other privileged users, provide the XML schema definition (using the Export feature) so they can import the compliance standard rule to their Management Repository.
-
You can minimize scrolling when reading the Description, Impact, and Recommendation information by restricting the text to 50 characters per line. If more than 50 characters are needed, start a new line to continue the text.
-
Look at the context-sensitive help for information for each page in the Compliance Standard Rule wizard for specific instructions.
-
If you manually type a WHERE clause in the compliance standard rule XML definition, then the < (less than) symbol must be expressed as <, to create a valid XML document. For example:
<WhereClause>:status < 100</WhereClause>
48.4.7.2 Creating a WebLogic Server Signature Compliance Standard Rule
There are several hundred out-of-the box WebLogic Server signature rules designed to uncover compliance violations known to occur in WebLogic installations based primarily on in-depth knowledge of common pitfalls and best practices. You can also create your own rules to extend the checks that are performed.
A signature describes a potential problem in a WebLogic installation. It consists of categorization metadata, a user-readable description of the problem, and an XQuery expression for evaluating whether the problem exists at the target.
A WLS Signature rule is an Management Agent-side rule that checks a signature definition against an associated target for the existence of the problem the signature defines. WebLogic Server targets include: WLS Domain; WLS Cluster; WebLogic Managed Server. The first two are composite target types: logical groupings of instances of simple WebLogic Server targets. Rules must be evaluated against the whole domain or cluster to render meaningful violation results.
WLS Signature rules, like other compliance rules, are grouped into Compliance Standards, which are logical groupings based on signature metadata such as severity and remedy.
To create a WebLogic Server Signature compliance standard rule to evaluate if certain configuration settings satisfy known good configurations, follow these steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
Click the Compliance Standard Rules tab.
-
Click the Create button.
-
In the Create Rule popup, select the WebLogic Server Signature rule type.
-
Click Continue.
-
On the next screen, you are asked to fill out several key attributes of the rule:
-
Rule Name
Provide a unique name for the rule.
-
Compliance Rule State
Set whether the state of this rule is development or production. Development means that the rule is still being defined or tuned and is not yet ready to be used on targets yet. After you promote a rule to production, you cannot change it back to development.
-
Severity
The rule can have a severity level, which could be Critical (serious issue if this rule is violated), Warning (not a serious issue if violated), or Minor Warning (a minor issue if violated). Severity impacts the compliance score along with the importance that may be set for this rule when it is added to a compliance standard.
-
Applicable To
Target type this rule works against.
-
Target Property Filter
You can specify specific target properties that determine which targets this rule can work against when it is associated with a compliance standard. These properties are Operating System, Target Lifecycle State, Version, and Platform. When you specify a target property filter for this rule, for instance for Linux OS, it will only be applicable to targets on Linux Operating System.
-
Description
Description of the rule
-
Rationale
Text describing what this rule is checking and what the effect of a violation of this rule may be.
-
Recommendation
Recommendation text describing how to fix a problem when a violation occurs.
-
Reference URL
URL to a document that describes the compliance control in more details. Many times these documents may be stored in a content management system.
-
Keywords
Keywords can be assigned to a rule so that you can control how data is organized in various reports.
-
-
Click Next.
-
On the next screen, you select the method of providing the signature definition file. You can either load it by uploading a file, or enter the text directly into the UI.
-
Enter Compliant and Non-Compliant Message. These are the messages that will be shown in regards to the evaluation. When a violation occurs, the Non-Compliant message will be the string describing the event under the Incident Management capabilities.
-
Choose the columns that will be displayed along with violations. These columns should be defined as return columns in the signature definition.
-
Click Next.
-
The next screen will allow you to test your rule. You can choose a target in your environment and click the Run Test button. Any issues with the rule will be displayed and you can resolve them before saving the rule.
-
Click Next.
-
The final page allows you to review everything you have configured for this rule. Ensure that everything is correct and click the Finish button to save the rule.
This newly crated rule does not function until it is associated to one or more compliance standards and those compliance standards are associated to targets. Once this association happens, the following is the workflow of this rule:
-
The standard/rule combination gets transferred to and then evaluated on the Management Agent-side against a metric collected specifically for the Compliance Standard and target type to determine compliance.
-
The evaluation generates violations (if any).
-
Violations are uploaded to Cloud Control server, from where they are subsequently processed into violations in Management Repository tables.
-
Violations are then viewable in compliance results pages and the Compliance Dashboard.
Example WebLogic Server Signature
Using the rule creation wizard makes it simple to add a new rule, but the important part of the WebLogic Server signature rule is the signature definition. A signature definition consists of a list of managed beans (MBeans) and an XQuery expression. Managed beans represent the configuration data to collect. They define a type and the attributes within the type to collect. They also declare which attributes to consider in determining whether there are violations. The XQuery expression defines the logic to use in evaluating the collected data for compliance. An XML example signature definition follows.
<SignatureDefinition>
<MBeanList>
<MBean scoreBase="true" mBeanType="ServerRuntime">
<AttributeName>Name</AttributeName>
<AttributeName>WeblogicVersion</AttributeName>
</MBean>
</MBeanList>
<XQueryLogic>declare function local:getServerRuntimesEqualToVersionWithPatch($targetData, $major as xs:integer,
$minor as xs:integer, $servicePack as xs:integer, $crNumber as xs:string) {
for $ServerRuntime in $targetData/DataCollection/ServerRuntime
let $weblogicVersion := fn:replace($ServerRuntime/@WeblogicVersion, "WebLogic Server Temporary Patch", "")
let $majorVersion :=
let $spaceParts := fn:tokenize(fn:substring-after($weblogicVersion, "WebLogic Server "), " ")
let $majorVersionParts := fn:tokenize($spaceParts[1], "\.")
return
$majorVersionParts[1] cast as xs:integer
let $SP_MP :=
if ($majorVersion = 8) then
"SP"
else
if ($majorVersion >= 9) then
"MP"
else " "
let $minorVersion :=
let $spaceParts := fn:tokenize(fn:substring-after($weblogicVersion, "WebLogic Server "), " ")
let $minorVersionParts := fn:tokenize($spaceParts[1], "\.")
return
$minorVersionParts[2] cast as xs:integer
let $servicePackVersion :=
let $spaceParts := fn:tokenize(fn:substring-after($weblogicVersion, "WebLogic Server "), " ")
let $servicePackParts := fn:substring-after($spaceParts[2], $SP_MP)
return
if ($servicePackParts = "") then
0
else
$servicePackParts cast as xs:integer
where $majorVersion = $major and $minorVersion = $minor and $servicePackVersion = $servicePack and
fn:contains(fn:upper-case($ServerRuntime/@WeblogicVersion),fn:upper-case($crNumber))
return
$ServerRuntime
};
for $server in local:getServerRuntimesEqualToVersionWithPatch(/,10,0,1,"CR366527")
|
local:getServerRuntimesEqualToVersionWithPatch(/,10,0,0,"CR366527")
return <Server
Name="{fn:data($server/@Name)}"/></XQueryLogic>
</SignatureDefinition>
Effectively, this definition collects the server name and WebLogic version of all runtime servers. Much of the definition iterates over the preciseness of the version-major and minor patch, service pack, CR number, and so forth. A violation occurs if any server has either of the stated patches (10.0.1 CR366527 or 10.0.0 CR 366527), in which case return the name of the server to be reported in violation. Hence, the rule definition must include a column to account for display of the server name. The version is irrelevant in the context of the display. Those alerted are interested only in which servers are in violation.
Important Prerequisite Steps to Use WebLogic Server Signature Rules
The following are some required steps that are specific to the version of WebLogic you are trying to monitor:
Additional Notes for WebLogic Server Signature Rules
-
All rules are visible in the global rule library and are visible to all users.
-
After the compliance standard rule is created, it is not automatically evaluated. Users must associate a rule to a compliance standard before it can be used. Only when a compliance standard is associated with one or more targets will a rule evaluation occur. Rules cannot be evaluated directly.
-
One rule can be associated to multiple compliance standards.
-
Various attributes of a rule can be customized through the compliance standard this rule is associated with. These customizations occur in the Compliance Standard screens. One of these attributes that can be customized per compliance standard is the importance of the rule in relationship to this standard.
-
Because the user-defined compliance standard rule is defined by a privileged user, only privileged users can modify the compliance standard rule. Violation results are available to all users.
-
To share this user-defined compliance standard rule with other privileged users, provide the XML schema definition (using the Export feature) so they can import the compliance standard rule to their Management Repository.
-
You can minimize scrolling when reading the Description, Impact, and Recommendation information by restricting the text to 50 characters per line. If more than 50 characters are needed, start a new line to continue the text.
-
Look at the context-sensitive help for information for each page in the Compliance Standard Rule wizard for specific instructions.
-
Look at the context-sensitive help for information for each page in the Compliance Standard Rule wizard for specific instruction.
48.4.7.3 Creating a Real-time Monitoring Compliance Standard Rule
To create a Real-time monitoring compliance standard rule to monitor for user actions that occur on a target such as file changes, user access, and process activity, follow these steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
Click the Compliance Standard Rules tab.
-
Click the Create button.
-
In the Create Rule popup, select Real-time Monitoring type.
-
Click OK.
-
On the next screen, you are asked to fill out several key attributes of the rule:
-
Rule Name
Provide a unique name for the rule.
-
Compliance Rule State
Set whether the state of this rule is development or production. Development means that the rule is still being defined or tuned and is not yet ready to be used on targets yet. After you promote a rule to production, you cannot change it back to development.
-
Severity
The rule can have a severity level, which could be Critical (serious issue if this rule is violated), Warning (not a serious issue if violated), or Minor Warning (a minor issue if violated). Severity impacts the compliance score along with the importance that may be set for this rule when it is added to a compliance standard.
-
Applicable To
Target type this rule works against.
-
Entity Type
A type of object that is part of a target being monitored. For example, for the Operating System (OS), entity type may be OS File, OS Process, or OS User. For Database, an entity type may be Database Table, Database Function, Database Procedure, or Database User.
-
Target Property Filter
You can specify specific target properties that determine which targets this rule can work against when it is associated with a compliance standard. These properties are Operating System, Target Lifecycle State, Version, and Platform. When you specify a target property filter for this rule, for instance for Linux OS, it will only be applicable to targets on Linux Operating System.
-
Description
Description of the rule
-
Rationale
Text describing what this rule is checking and what the effect of a violation of this rule may be.
-
Details URL
URL to a document that describes the compliance control in more details. Many times these documents may be stored in a content management system.
-
Message
The message that will be used for the violation when an observation is determined to be unauthorized.
-
Clear Message
The message that will be used for a previous violation after it is cleared.
-
Keywords
Keywords can be assigned to a rule so that you can control how data is organized in various reports.
For additional information, see Importance of Target Property Filters for a Real-time Monitoring Rule.
-
-
Click Next.
-
On the next page, you select the facets that are to be monitored for this rule. You can include facets that are already defined or create a new facet inline with this rule creation. A facet is simply a list of patterns to monitor. For instance, a list of files, user names, processes, and so on. Facets are discussed later in the section Real-time Monitoring Facets.
-
Click Next after including existing facets or adding new facets.
-
On the next screen, you will choose the actions you want to monitor. The actions you choose will depend on what entity type you chose for the rule. For instance, for OS File Monitoring, you can watch for actions such as file create, modify, delete, rename, and so on. For OS User monitoring, you can watch for actions such as login, logout, SU, SSH, and so on. You must choose at least one action to monitor for a rule.
For additional information, see Selecting the Types of Actions You Want to Monitor.
-
Click Next.
-
On the next screen, you can optionally configure filters for monitoring. Filters are used to limit when or under what conditions you want an action to be observed. For instance, if you are monitoring a file facet FILES1, you can add a filter so that only file changes done by a specific list of users are captured, or if the change happens during a certain time window, or a certain process is used to modify the file. Filters are also facets, just of different entity types. If you are monitoring OS File entity type, you can apply an OS User, OS Process, or Time Window facet as a filter. You can include an existing facet, or create a new facet inline with the rule creation. If you cancel the rule wizard, any facet you created inline will still exist in the facet library.
For additional information, see Using Facets as Filters in Real-time Monitoring Rules.
-
Click Next.
-
On the next screen, you can configure several settings related to how the observations are handled when detected at the Management Agent.
-
Authorize Observations Manually
-
Authorize Observations Automatically using Change Request Management System
-
Collection Settings
For additional information, see Configuring Audit Status and Controlling Observation Bundle Lifetimes.
-
-
Click Next.
-
On this screen you can review the settings of the rule.
-
Click Finish to save the rule and return to the rule listing page.
Importance of Target Property Filters for a Real-time Monitoring Rule
When creating a rule, you must choose a target type for the rule. Since the Real-time monitoring capabilities on the Management Agent have some dependencies on operating system and versions of operating systems, you must be allowed to set the criteria for a rule. The target may be different on a target type, so patterns in the facets may be different. For instance, Oracle Database on Microsoft Windows is not the same as it is on the UNIX operating system.
If target property filters are not set, all rule options are available then at target-cs association time, if a target's settings do not match, then that rule and facet is ignored. If you only set, for example, the platform name, but not version, then only the options that are common across all versions of the platform are available.
The list of facets that are selectable when creating a rule are filtered by the target properties that are set when a facet is created. For instance if you have a facet, FACET1, that works on Linux or HPUX and you create a rule for Windows, FACET1 will not be available to select for your rule. This applies both when selecting the monitoring facet or using a facet as a filter. However if you create a rule for either Linux or HPUX, FACET1 will be available because the criteria for the rule at least overlapped with that of the facet.
Using Facets as Filters in Real-time Monitoring Rules
When creating a rule, facets can be used in two ways. The first is to use the facet to specify what entities to monitor in the rule. The second is to use the facet as a filter to apply on top of activities detected by the Management Agent.
You can use the same facet as a monitoring facet in one rule and a filtering facet in another rule. The benefit is once you define a collection of patterns, for example to define your administrative users, you can use that collection in many ways without having to redefine the collection again.
Filters in rules are set up to reduce the observations that are captured and reported to Cloud Control. If there are no filters defined, then all observations related to the monitoring facet(s) selected in the rule are captured. When selecting a facet as a filter, the default is to only include observations that have attributes that match. The following example IT compliance control demonstrates an example for the filtering:
IT Control: Monitor all changes to critical OS configuration files by administrators during production hours.
To implement this IT control, you can create a compliance standard rule with the following:
-
Create a rule and select the file facet "Critical OS configuration files" for the monitoring facet that has patterns covering all critical OS configuration files.
-
Select "content change" as the action types to capture.
-
Add an OS Users filter selecting facet "Administrators" that lists patterns describing all of the OS user accounts that are considered administrators.
-
Add a Time Window filter selecting facet "Production Hours" that lists patterns describing the times of the week that are considered to be production hours. For example, Every day 4am-2pm PST.
When the Management Agent sees any content change to the patterns in Critical OS configuration files, it will only report these changes back to Cloud Control if the change happened during production hours and if any user described in the Administrator's facet is the one making the change. Filters can also be inverted to monitor anyone not in the administrators group or for changes outside of production hours.
More details on how to use filters is described in the section above on Creating a Real-time monitoring rule.
Configuring Audit Status
Each observation can have an audit status. This audit status can change over time and be set manually or automatically by Cloud Control. The way audit statuses are managed is configured when creating or editing a real-time monitoring rule.
When creating a rule, on the settings page of the wizard, the user has an option of choosing whether all observations detected against this rule will get their audit status manually from the user or automatically using connector integration with a Change Request Management server.
When the user chooses to manually set audit status in a rule, there are two options available:
-
Default Audit status can be set so that all observations that are found against this rule are by default unaudited, authorized, or unauthorized. Unaudited is the same as saying they have not been reviewed and there has been no determination of whether the observation is good or bad.
-
The user can choose an informational event during manual authorizations. This is used to create a new event of informational class in the Incident Manager when a new observation bundle occurs. Based on this event, an event rule could be created to send a notification based on the observation bundle or perform any other action the Incident Manager can perform.
If the user chooses to use automatic reconciliation using a Change Request Management server, then steps must be taken to set up the Cloud Control connector for Change Management. This is explain in detail in the later section, Additional Setup for Real-time Monitoring.
Once the connector has been configured, there will be a drop down in this settings step of the rule creation wizard to choose which connector to use for this rule. Based on attributes of the observation and observations defined in any open change requests, the observation will be automatically determined to be authorized if there are open matching change requests, otherwise it will be considered unauthorized.
When using automatic reconciliation, an additional option is available to specify that the details of any authorized observations should be annotated back into the change request in the Change Request Management Server that allowed the observation to be authorized.
Multiple observations can belong to the same Observation Bundle. Even though an observation is part of group, the determination of authorized versus unauthorized is done for a single observation, not at the group level. If a group has at least one observation that is marked as "unauthorized", then the group is considered to be a "violation" and an event or incident can be raised for this group violation.
Controlling Observation Bundle Lifetimes
Observation bundles are logical groupings of observations that occur over a relatively short period of time against the same rule on the same target and by the same user. The last three factors cannot be configured by the user because they will be how the Management Agent groups observations before sending them back to the Cloud Control server.
The user creating the rule however does have three variables that they need to be able to configure:
-
Idle timeout: The amount of time after the user has no more activity from their last activity against a specific rule on a given target. The use case for this is that a user logs into a server, starts making a few file changes and then no more file changes are made after 15 minutes. This 15 minute waiting period is the idle timeout. After this idle timeout period is reached, the current observation bundle is closed and sent to the Cloud Control server. The next time a new observation is detected, a new group will be started and the process starts over.
-
Maximum lifespan of a group: If a user were to set the idle timeout to 15 minutes and a user on a host was making one file change every 10 minutes for an indefinite period of time (say through a script or even manual), the observation bundle will never close and therefore never get sent to the Cloud Control server for reporting/processing. Setting the maximum lifespan of a group tells the Management Agent to only allow a group to accumulate for a maximum specific time. For example, this maximum lifespan may be 30 minutes or an hour.
-
Maximum number of observations in a bundle: If a rule is being triggered because of an activity that is causing a lot of observations to be detected, it may be desirable for the user to not bundle every observation together if there are too many. Bundles have a management lifecycle to them where observations can be set to authorized/unauthorized, after they arrive at the Cloud Control server. Having observation bundles with tens of thousands of observations could become hard to manage.
The user creating a rule cannot choose to turn off bundling, but if they desired to reduce delays in observation reporting to Cloud Control server, they could set the idle timeout and maximum lifespan of a bundle to be lower.
The event/incident subsystem will track only the observation bundles, not each individual observation. If one observation is marked as unauthorized, then the entire bundle will be in violation. This bundle is the entity that will be tracked by the Incident Management event.
Observation bundles are built at the Management Agent and will only be sent to the Cloud Control server when the bundle is complete according to the above criteria. In most compliance use cases, this is acceptable because you will not need to view the results immediately. Capturing and bundling results together is more important for understanding what is happening and making observations easier to manage.
When an observation becomes part of two or more bundles on the Management Agent because the same facet is used in multiple rules or multiple targets on the same host monitor the same facet with shared entities, then whenever the first bundle either hits its ending criteria (idle timeout, group maximum life, or maximum group entries), then all of the bundles containing these shared observations are closed at the same time.
To control observation bundle lifetimes, see the section above on how to create Real-time Monitoring Rules and set the appropriate settings on Settings page of the rule creation wizard.
Selecting the Types of Actions You Want to Monitor
When creating a rule, you can decide which types of observations or user actions are important to be monitored and reported back to Cloud Control. The Management Agent has a specific set of observations that are possible for each entity type. Some options may be specific to certain operating system platforms or versions. You can select one or more of these options.
The observation types that you may be able to select can also be limited by the target properties/criteria selected for the rule. For instance, some operating systems may not have every monitoring capability for files. When building the list of available observation types available, the target type, entity type, and target properties are all taken into consideration to come up with the resulting available observation types.
To select the type of observations you want to monitor in a rule, follow these steps:
Additional Notes for Real-time Monitoring Rules
-
All Rules are visible in the global rule library and are visible to all users.
-
Once the compliance standard rule is created, it is not automatically evaluated. Users must associate a rule to a Compliance Standard before it can be used. Only when a compliance standard is associated with one or more targets will a rule evaluation occur. Rules cannot be evaluated directly.
-
One rule can be associated to multiple compliance standards.
-
Various attributes of a rule can be customized through the compliance standard this rule is associated with. These customizations occur in the Compliance Standard screens. One of these attributes that can be customized per compliance standard is the importance of the rule in relationship to this standard.
-
Because the user-defined compliance standard rule is defined by a privileged user, only privileged users can modify the compliance standard rule. Violation results are available to all users.
-
To share this user-defined compliance standard rule with other privileged users, provide the XML schema definition (using the Export feature) so they can import the compliance standard rule to their Management Repository.
-
You can minimize scrolling when reading the Description, Impact, and Recommendation information by restrict the text to 50 characters per line. If more than 50 characters are needed, start a new line to continue the text.
-
Look at the context-sensitive help for information for each page in the Compliance Standard Rule wizard for specific instructions.
-
If you choose to monitor OS File entity type, you will notice one action type "File Content Modified (successful) - Archive a copy of the file [Resource Intensive]". If you select this option, every time a file modify action is observed, a copy of the file will be archived locally on the Management Agent. This can be used later to visually compare what changed between two versions of the file. There is an additional setting to set how many archived copies to store on the Actions to Monitor page of the rule creation wizard.
-
When you add a facet inline with the create rule wizard either as a monitoring facet or as a filtering facet, if you cancel the rule wizard, the newly created facets will still exist and be usable in future rules. You can delete these facets by going to the facet library. Real-time monitoring facets are discussed in a separate section later in this document.
48.4.7.4 Creating an Agent-side Rule
Note: Before you create an agent-side rule, you must create a configuration extension.
To create an agent-side compliance standard rule to check if a target has the desired configuration state based on collected configuration data, follow these steps:
48.4.7.5 Creating a Manual Rule
To create a manual compliance standard rule to check if a target has the desired configuration state based on collected configuration data, follow these steps:
48.4.7.6 Creating a Missing Patches Compliance Standard Rule
To create a missing patches compliance standard rule to detect patches that have not been applied to the appropriate targets, follow these steps:
Tips
-
Once the compliance standard rule has been created, it is not automatically evaluated. Consider adding the compliance standard rule to a compliance standard.
-
Assign a corrective action to the rule after the rule has been created.
-
On the Compliance Standard Rules tab, highlight the rule you just created.
-
From the Actions menu, select Assign Corrective Action.
-
From the Assign Creative Action popup, select an existing corrective action and click OK.
-
48.4.7.7 Creating a Configuration Consistency Rule
To create a configuration consistency compliance standard rule to determine the consistency of targets of similar target types within a composite target, follow these steps:
48.4.7.8 Creating Configuration Drift Rule
To create a configuration drift compliance standard rule to determine the deviation of targets of similar target types, follow these steps:
48.4.7.9 Creating Like a Compliance Standard Rule
To create a compliance standard rule like another compliance standard rule, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- Highlight the rule you want to replicate.
- Click Create Like button.
- Customize the fields as needed.
- Click Save.
48.4.7.10 Editing a Compliance Standard Rule
To edit a compliance standard rule, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- Highlight the rule you want to edit and click the Edit button.
- Step through the screens of the rule creation wizard as previously described when creating a rule.
- Click Save.
Usage Notes
-
For repository rules, you can change all the rule properties except the Rule Name, State (if it is already production), and Applicable To.
For real-time monitoring rules, you cannot change Rule Name, State (it is already production), Applicable To, Target Property Filters, and Entity Type.
-
If you change the critical rule properties for a repository rule, for example, rule query, violation condition, parameters, or severity, then editing the rule invalidates the results for compliance standards which refer to the rule. The compliance standards compliance score will be reevaluated at the next rule evaluation.
-
For rules in production mode, you have a choice to create and save a draft of the rule or to overwrite the existing production rule. If you create a draft, you can edit the draft rule, at a later point in time, test it, and then overwrite and merge it back to the original production rule the draft was made from. Note: You cannot include a draft rule into any compliance standard.
-
For WebLogic Server Signature rule or Real-time Monitoring rule, if the rule being edited is referred to by a compliance standard which is associated with a target, then the rule definition will be deployed to the Management Agent monitoring the target, so that the Management Agent can evaluate the latest definition of the rule. In the case where the Management Agent is down or unreachable, the rule definition changes will be propagated to the Management Agent as soon as the Management Agent is available.
48.4.7.11 Deleting a Compliance Standard Rule
Before you delete a rule, you must ensure that compliance standard rule references have been removed from compliance standards before deleting the compliance standard rule. You cannot delete a rule that is in use by a compliance standard.
To delete a compliance standard rule, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- Highlight the rule you want to delete, click Delete button.
- Confirm that you want to delete the rule by clicking OK.
48.4.7.12 Exporting a Compliance Standard Rule
The Export feature provides a mechanism for transporting user-defined compliance standard rule definitions across Management Repositories and Cloud Control instances. The export stores the definitions in an operating system file. Because the exported compliance standard rule definitions are in XML format, they conform to the Oracle Compliance Standard Definition (XSD) format. You can then change the definition of the compliance standard rule and re-import the generated compliance standard rule definitions into another Management Repository.
To export a compliance standard rule, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- Highlight the rule you want to export.
- From the Actions menu, select Export.
- Provide the file name to which the standard rule is to be exported.
- The XML representation of the compliance standard rule is generated and placed in the directory and file you specified.
48.4.7.13 Importing a Compliance Standard Rule
Importing allows you to re-use a compliance standard rule that you already have, share rule definitions across multiple instances of Cloud Control, or enable offline editing of the rule.
Before you import a compliance standard rule, ensure the compliance standard rule to be imported is defined in a file. The file should be locally accessible to the browser you are using to access Cloud Control. Also ensure that you have privileges to access the compliance standard rule definition XML file to be imported.
To import a compliance standard rule, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- From Actions menu, select Import.
- Provide the file name from which the rule definition (as per Compliance Standard Rule XSD) will be imported. Specify whether to override an existing definition if one already exists. The override option is not available to Real-time monitoring rules.
- Click OK.
48.4.7.14 Browsing Compliance Standard Rules
To browse compliance standard rules, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- To view the details of a particular standard rule, highlight the rule and click Show Details.
48.4.7.15 Searching Compliance Standard Rules
To search for compliance standard rules, follow these steps:
48.4.7.16 Using Corrective Actions
A corrective action is a script that fixes the problem causing a violation to a compliance standard rule.
There are two types of corrective actions:
-
Manual - Created in the context of the compliance standard rule.
-
Automatic - Created in the context of an incident rule.
Manual Corrective Action
To create a corrective action manually, perform the following steps:
-
From the Enterprise menu, select Monitoring, then select Corrective Actions.
-
On the Job page:
-
Select SQL Script in the Create Library Corrective Action field, and click Go.
-
On the General tab, type a name for the corrective action (for example, CA1), provide a description, and select Compliance Standard Rule Violation as the Event Type. Select Database Instance as the Target Type.
-
On the Parameters tab, select the default: WHENEVER SQLERROR EXIT FAILURE;. Click Save to Library.
Note: To enable intelligent remediation, pass parameters from the compliance violation to the corrective action. For example, to lock changes to Well Known Accounts, add the following SQL statement:
alter user %EVTCTX.dbuser% account lock; where dbuser is the event context parameter
You can make similar changes to any parameter. Ensure that the parameter name matches the name of the column in the SQL query.
-
Select the corrective action you just created and click Publish.
-
On the confirmation page, click Yes.
-
-
From the Enterprise menu, select Compliance, then select Library. Choose a database compliance standard rule with the rule type of agent-side or repository. In the Actions menu, select Assign Corrective Action. Select a corrective action and click OK.
You will then see the corrective action in the Show Details page for the compliance standard rule.
Automatic Corrective Action
To create a corrective action that is automatically triggered when the violation occurs, follow these steps:
-
From the Setup menu, select Incidents, then select Incident Rules.
-
On the Incident Rules - All Enterprise Rules page, click Create Rule Set. Provide a name for the rule, select All targets in the Targets region, and click Create... in the Rules region.
-
On the Select Type of Rule to Create dialog box, select Incoming events and updates to events. Click Continue.
-
For the type, select Compliance Standard Rule Violation.
-
Select either All events of type Compliance Standard Rule Violation or Specific events of type Compliance Standard Rule Violation.
-
In the Advanced Selection Options, select Corrective action completed. Click Next.
-
On the Create New Rule: Add Actions page, click Add. On the Add Conditional Actions page, click Select corrective action. Select the corrective action. Click Continue.
-
In the Create New Rule: Add Actions page, click Next. Provide a description on the Create New Rule: Specify and Description page and click Next.
-
Review the information and click Continue.
-
Click Save. Note that newly added rules are not saved until the Save button is clicked. After you click Save, verify that the rule set entity has added the new incident rule by reviewing the details.
48.5 Real-time Monitoring Facets
The real-time monitoring rule definition includes facets that are used to determine what is important to monitor for a given target type, target properties, and entity type. A facet is a collection of patterns that make up one attribute of a target type.
The following sections explain real-time monitoring facets in detail:
48.5.1 About Real-time Monitoring Facets
A target type has several facets to it. A target type will have a facet of which files are critical configuration files, which files are log files, which files are executables, which database tables have sensitive configuration data, and so on. The sum of all of these facets for a given target type makes up everything that is important to monitor for the given target type in terms of compliance.
For a given target type, you can create any number of facets. A facet is not only for a specific target type, but for a specific target type plus a combination of some number of target type properties. For instance, creating a facet for a Host Target Type on Windows is different than creating a facet for a Host Target type on Linux. A facet can have several target type properties or can be open to any target without specifying any properties.
Facets are reusable in many rules. The benefit is that you can add or remove entries from a facet without having to modify every rule. For instance, if today there are 5 log files you want to monitor, you can setup your rules to monitor a facet listing those 5 files. When a new log file should be added tomorrow, you only need to change the facet, not each rule.
Facets can be created on their own, or created inline with a Real-time Monitoring rule creation. No matter how they are created, they can be used again at a later time in any number of rules.
Real-time Monitoring facets based on target types are used to specify the entities to monitor in real-time monitoring rules. As an example, if monitoring a host for file changes, a facet can be a list of distinct single files, patterns with wildcards that would include many files, or simply an entire directory. These patterns can also include parameters that have a default, but can be overridden as needed for each target. Built-in parameters, such as ORACLE_HOME will be dynamically filled in for each target. If you wanted to specify monitoring the database configuration file tnsnames.ora, your pattern may be {ORACLE_HOME}/network/admin/tnsnames.ora.
Facets can be used in two totally distinct ways. Primarily, facets describe what to monitor. In the rule creation wizard, these facets are selected on the wizard step "Entities to Monitor". Facets also can be used to filter your monitoring results. These filtering facets are specified on the Filters step of the rule creation wizard. When monitoring an OS file entity type for instance, you can filter your results based on the user that made a file change, the time the file change happened, or the process used to make the file change.
When performing continuous real-time monitoring, it is important to scope your monitoring only to critical entities. Monitoring more activity than is important to the organization will result in higher CPU loads on the Management Agent as well as a very large amount of data to be processed/stored by the Oracle Enterprise Manager servers.
48.5.1.1 Facet Entity Types
Each facet has an entity type which defines what kind of entities the facet describes. For example, for OS level monitoring, there are OS File, OS Process, OS User, Windows Registry, and several Active Directory entity types. For database monitoring, the entity types include Table, View, Index, Procedure among others. The possible entity types are fixed by the continuous real-time configuration change monitoring capabilities available from the Management Agent.
Creation of facets is possible through the Facet Library screen. In this screen, you can add/edit patterns for facets, and see which facets are being consumed by rules.
Given below are the entity types Cloud Control supports for real-time monitoring:
-
OS File
-
OS Process
-
OS User
-
Microsoft Windows Registry
-
Microsoft Active Directory User
-
Microsoft Active Directory Computer
-
Microsoft Active Directory Group
-
Oracle Database Dimension
-
Oracle Database Synonym
-
Oracle Database Type
-
Oracle Database Table
-
Oracle Database View
-
Oracle Database Procedure
-
Oracle Database User
-
Oracle Database Index
-
Oracle Database Sequence
-
Oracle Database Function
-
Oracle Database Profile
-
Oracle Database Public Synonym
-
Oracle Database Role
-
Oracle Database Package
-
Oracle Database Library
-
Oracle Database Trigger
-
Oracle Database Tablespace
-
Oracle Database Materialized View
-
Oracle Database Cluster
-
Oracle Database Link
-
Oracle Database Public DB Link
-
Oracle Database Segment
-
Oracle Database SQL Query Statement
48.5.1.2 Facet Patterns
A facet contains one or more patterns. These patterns can express inclusion or exclusion filters. For instance, you may define a facet for critical configuration files that looks like the following:
Include c:\myapp1\config
Exclude c:\myapp1\config\dummy.cfg
In this case, everything under c:\myapp1\config will be considered to be a member of this facet except for the individual file c:\myapp1\config\dummy.cfg. In general there are some rules to how patterns work given the most common use cases listed below. Each entity type might have special cases or special formats of patterns.
-
Patterns of the same specificity with one being include and one being exclude, the include will win.
-
Patterns that are more specific override (like in the previous example, exclude dummy.cfg overrides the inherited include c:\dummy.cfg from the first pattern.)
-
If there are no patterns at all, exclude * is assumed (for example, no entities in the facet)
For each pattern that you add to a facet, an optional description field is available to let you document their patterns.
48.5.2 Operations on Facets
The following sections explain the operations you can perform on facets:
Ensure you have the privileges to create, delete, and modify facets as these configurations relate to the compliance monitoring. See Roles and Privileges Needed to Use the Compliance Features for information.
48.5.2.1 Viewing the Facet Library
Any user who can view observation data is able to also view the facet library and see the facet history for any facet.
There are two ways to view the facet library, search mode and browse mode. In search mode, all facets meeting the search criteria are shown in a flat list. In browse mode, facets are shown along with a folder hierarchy that the facets belong to. This folder structure can help users manage a very large number of facets in Cloud Control.
To view the facet library in search mode, follow these steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
Choose the Real-time Monitoring Facets Library tab.
Cloud Control displays the Facet Library page that lists all existing facets along with their target type, entity type, and other details about the facet. From this page you can perform administrative tasks such as create, create like, view, delete, import, and export if you have the audit author role.
-
Click the Search Facets tab.
The Facet Library page displays the Facet Name, Author, Target Type, Entity Type, Rules Using the facet, Description, and the Last Updated time of the facet. You can see the details of any facet by selecting it from the table and clicking Show Details.
-
You can choose which columns to display in the table by clicking View and then choosing Columns. You can either choose to Show All columns or you can select individually the columns you want to appear in the table. You can reorder the columns by clicking Reorder after you click View and then changing the order in which the columns appear by moving them up or down using the arrow keys.
-
You can expand the area of the page titled "Search" to choose the search criteria to apply to the view of facets.
-
You can view a history of a selected facet by choosing it from the table and then clicking History. The View History page appears.
To view the facet library in browse mode, follow these steps:
48.5.2.2 Creating and Editing Facets
When you create a facet and subsequently use a facet in a Real-time Monitoring Compliance Standard Rule, the compliance rule only references the facet. If the content changes, then the rule will use the new content automatically.
The content of the facet only begins being used when it is added to a rule that is part of a compliance standard that is associated to one more targets.
Each facet is assigned a description that allows you to document the facet. Each pattern also has an optional description field. only begins being used when it is added to a rule that is part of a compliance standard that is associated to one more targets.
To create or edit a facet, follow these steps:
48.5.2.3 Creating and Editing Facet Folders
When viewing the facets in Browse Facets mode, you will see two regions on the page. The left side will show the facet folders which exist. The right side will show the facets that exist in the currently selected folder.On the left side showing the folders, there are three actions available for folders.
-
Create: Allow you to create a new folder. A popup will display asking for the folder name to create. You will also have the choice of making this new folder a top level folder or adding it as a child to the currently selected folder.
-
Rename: Allows you to rename an existing user-defined folder
-
Delete: Allows you to delete a user-defined folder. You cannot delete a folder that has facets or other folders inside of it.
You cannot delete, rename or move out-of-the-box folders that are populated by Oracle.
There is a default folder that exists called Unfiled. Anytime a facet is created or imported without specifying a folder, it will go into this Unfiled folder.
You can move facets into folders by simply finding the facet you want to move in the right side, selecting it and dragging it to the folder on the left where you want to place it. The facet will move to that folder. A facet can only belong to one folder at a time and it always must belong to a folder (even if it is just the Unfiled folder). You can also click on the facet and click on the MOVE button. A popup window will appear letting you choose which folder to move the facet to.
Folders have no impact on observation analysis or compliance score. They are only used in the Real-Time Monitoring Facets library screen to make it easier to manage a very large number of facets that exist.
48.5.2.4 Deleting a Facet
Deleting a facet is not possible as long as the facet is in use either as a monitoring facet in a rule or as a filter facet in a rule. If this facet is not in use in any rules, then the facet can be deleted. If a facet is in use, the user is alerted to the current use and not allowed to delete the facet until the rules using it are modified to no longer include it.
When deleting a facet, any historic observation data will no longer be referenced to the facet and instead it will show "(Deleted Facet)" as the name of the facet to which it is related. This observation data will only be available through the Search Observations page, not the Browse pages.
For compliance-focused users, customers typically would want to keep the unused facet available so the compliance data is not lost. You can also remove the patterns as long as you keep the actual facet to maintain collected observations. Then only after the compliance data related to this old facet is no longer available, you can delete the facet without any data loss.
To delete a facet, follow these steps:
48.5.2.5 Using Create Like to Create a New Facet
Facets that ship with the product or with a plug-in cannot be changed. If you want to enhance or modify the Oracle provided content, you must use the create-like functionality to make your own copy of the facet which can then subsequently be edited.
An important limitation to the Create Like function is that you cannot change the target type or entity type. The patterns contained in the facet may be dependent on target type or entity type. If you want to use Create Like and change these attributes, you should use Export to export the original facet, edit the name, target type, entity type in the XML, and then import as a new facet.
To use create like to create a new facet, follow these steps:
48.5.2.6 Importing and Exporting Facets
You can select facets and export or import them. All selected facets will be exported into one output file.
On import, if a facet of the same name/target type/entity type combination already exists, the import fails with an error that the facet already exists. The user must change the import file to remove the duplicate name and retry the import.
The combination of name, target type, and entity type define a unique facet. You can have the same name facet across different target types and entity types.
To export a facet, follow these steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
Choose the Real-time Monitoring Facets Library tab.
Cloud Control displays the Facet Library page that lists all existing facets along with their target type, entity type, and other details about the facet. From this page you can perform administrative tasks such as create, create like, view, delete, import, and export.
-
Select one or more facets from the list of facets on the Facet Library page that you want to export and then click Export.
-
On the Open dialog box, you can choose to open or save the facet xml file using an XML editor of your choice and then either edit or save the file to another location.
To import a facet, follow these steps:
48.5.2.7 Changing Base Facet Attributes Not Yet Used In a Rule
After a facet is in use in at least one rule (either as a monitoring facet or as a filter facet), you cannot change the facet name, target type, entity type, or target criteria of the facet since the rules that have been created are already bound to these attributes. The only attributes that can be changed are the facet patterns, parameters and description fields. Although the rule is not dependent on the facet name, users have used them in their rules based on the name of the facet. Allowing the name of the facet to change after consumption will only lead to confusion of the rule authors when analyzing compliance results and observations.of the rule authors.
If a facet is not currently in use but has been in use in the past, then it is treated the same as an in-use facet since the historic observation data will still be tied to the past facet.
You cannot make changes to the Oracle provided facets that ship with the Cloud Control product. If you want to use an Oracle provided facet with changes, you can perform a “Create Like" operation and then modify the newly created facet as needed.
To change base facet attributes, follow these steps:
48.6 Examples
This section provides examples of using compliance. Examples include:
48.6.1 Creating Repository Rule Based on Custom Configuration Collections
This example illustrates how a compliance rule can be created and run on a custom configuration which collects a sample configuration file (for this example, /tmp/foo.xml) for targets of type Host.
For this example, create a sample /tmp/foo.xml file with following contents:
<some_config> <prop foo="1"/> <prop bar="2"/> </some_config>
The steps include how to:
-
Create a custom configuration
-
Create a custom-based repository rule
-
Create a compliance standard
-
Associate a target
-
View results
To create a custom configuration:
-
From the Enterprise menu, select Configuration, then select Configuration Extensions.
-
From the Configuration Extensions page, click Create. The Create Configuration Extension page appears.
-
Type the Name (for example, compliance_ccs), a description (optional), select Target Type (for this example, Host).
-
In the Files & Commands section, type the Default Base Directory. [Use /tmp as the directory.]
This is an example. For a real target it should be the directory containing the target's configuration files.
Note: All files collected by custom configurations MUST NOT change on a daily basis, but should only change very rarely due to an explicit action by an administrator.
-
Click Add.
- In the Type column, select File.
- In the File/Command column, type foo.xml. The Alias column is automatically filled in with foo.xml.
Note: You can use any file or files, not just xml and not just "foo.xml" expressions. Custom configuration supports many files and corresponding parsers.
- In the Parser column, select XML Parser (default).
-
Click Save located at the bottom of the page.
-
-
In the Custom Configurations page, highlight compliance_css and click Deploy. The Deployments page appears.
-
Click Add to select targets on which CSS needs to be deployed.
-
On the Search and Select: Targets page, highlight the host target where file /tmp/foo.xml was created and click Select.
-
Click Apply on the Deployments page.
-
-
On the Submit Pending Deployment Actions popup, select Yes. This action will submit the deployment action.
On the Deployments page, click Refresh Status to refresh the status of the deployment until the Status column displays "Successfully deployed".
-
Now that deployment is submitted, click Cancel to exit the page. (Note: Clicking Save instead of Apply earlier, would have exited the page right after the submission of the deployment action.)
To create a custom-based repository rule based on custom configuration collection:
-
From the Enterprise menu, select Compliance, then select Library.
-
On the Compliance Library page, click the Compliance Standard Rules tab.
-
Click Create.
-
On the Create Rule popup, select Repository Rule and click Continue.
-
On the Create Rule: Repository Rule: Details page, type in the Rule name, for our example, compliance_css_rule.
-
For the Compliance Rule State, select Development, then select Minor Warning for the Severity. For Applicable To: select Host. Click Next located at the top-right of the page.
-
-
On the Create Rule: Repository Rule: Check Definition (Query) page, click Model Query. New Search Criteria page appears.
-
Select compliance_css (Parsed Data) from the Configuration Item menu under "Commonly Used Search Criteria".
-
Under the Host section and Parsed Data subsection, type foo.xml for Data Source contains. For the Attribute, select is exactly comparison operator and type foo to refer to the "foo" attribute in our sample file. (Note: % sign can also be used as a wild card character in these expressions for Data Source and Attribute.)
-
Click Search to see the rows returned for this filter. A table displays the data with value 1 for attribute foo in our file.
-
Click OK.
-
The Create Rule: Repository Rule: Check Definition (Query) displays again but this time the SQL Source appears.
-
Click Next. Note: In general, you could also update the query before proceeding, if needed.
-
-
The Create Rule: Repository Rule: Check Definition (Violation Condition) page displays.
-
Check all the columns as Key columns (VALUE, ATTR, CONTAINER, and DATA SOURCE NAME), except the INFO column.
-
In the Condition Type section of the page, select Simple Condition, and in the Column Name select VALUE and change the Comparison Operator to equal sign (=). In the Default Value column, type 1. Click Next.
-
-
In the Create Rule: Repository Rule: Test page, click the icon next to Target Name field. The Search and Select: Targets popup appears. Find the host where the custom configuration was deployed. Select it and click Select.
-
In the Create Rule: Repository Rule: Test page, click Run Test. When the test runs successfully, you get a confirmation stating that the Run Test - Completed Successfully.
You should see one violation after running the test because we specified value of "1" in step 5 above for violation condition and our sample file had value "1" for attribute foo. Click Close.
-
On the Create Rule: Repository Rule: Test page, click Next.
-
In the Create Rule: Repository Rule: Review page, ensure that all the information that you added is correct. Click Finish.
To create a compliance standard:
-
From the Enterprise menu, select Compliance, then select Library.
-
Click the Compliance Standards tab and click Create.
-
On the Create Compliance Standard popup, type compliance_css_cs in the Name field, select Host from Applicable To menu, and select Repository as the Standard Type. Click Continue.
-
The compliance standard page displays with the information regarding the compliance_css_cs compliance standard. Right-click on compliance_css_cs on the left side and select the Add Rules... option in the right-click menu.
-
On the Include Rule Reference popup, select compliance_css_rule. Click OK. Click Save to save the compliance_css_cs.
-
A confirmation message appears on the Compliance Library page stating that the compliance standard has been created. Click OK.
To associate targets:
-
Select the compliance_css_cs that was just created. Click Associate Targets.
-
On the "Target Association for Compliance Standard: compliance_css_cs" page, click Add to add targets.
-
On the Search and Select: Targets page, select a target where /tmp/foo.xml is present and click Select. Click OK.
You will then be prompted whether you want to Save the association or not. Click either Yes or No. You will then get an Informational message stating that the compliance standard has been submitted to the target for processing.
To view results:
-
From the Enterprise menu, select Compliance, then select Results.
On the Compliance Results page, select the compliance_css_cs compliance standard and click Show Details to view the details of the compliance standard created.
-
Click the Violations tab associated with the compliance_css_rule. The target is associated with one violation.
-
Click on the rule node in the tree to see the Violation Events tab, then click on this tab to see the violation details for the rule. Click on a violations row in the violations table, to view details of the violation.
48.6.2 Creating Compliance Standard Agent-side and Manual Rules
The purpose of this example is to create an agent-side compliance standard rule and a manual rule that test for DBMS privileged actions.
When creating an agent-side compliance standard rule, perform the following steps:
-
Create a configuration extension
-
Create the agent-side compliance rule
-
Create a manual rule
-
Create a compliance standard
-
Add the rules to the configuration standard
-
Associate the compliance standard to a target
Creating a Configuration Extension
Perform the following steps to create a configuration extension:
-
From the Enterprise menu, select Configuration, then select Configuration Extensions.
-
On the Configuration Extensions page, click Create.
-
Type a name for the extension, for example,
DG0142 DBMS Privileged action audit. You will use this name on the Check Definition page. -
Select Database Instance for the Target Type.
-
Click the SQL tab.
-
Click Add to add the first SQL statement.
-
In the SQL field, type:
select distinct 'Unauthorized user '||owner||' owns application objects in the database.' value from dba_objects where owner not in ('ANONYMOUS','AURORA$JIS$UTILITY$', 'AURORA$ORB$UNAUTHENTICATED', 'CTXSYS','DBSNMP','DIP','DVF','DVSYS','EXFSYS','LBACSYS','MDDATA', 'MDSYS','MGMT_VIEW','ODM','ODM_MTR', 'OLAPSYS','ORDPLUGINS', 'ORDSYS', 'OSE$HTTP$ADMIN','OUTLN','PERFSTAT', 'PUBLIC','REPADMIN','RMAN','SI_INFORMTN_SCHEMA', 'SYS','SYSMAN','SYSTEM','TRACESVR', 'TSMSYSWK_TEST','WKPROXY','WKSYS', 'WKUSER','WMSYS','XDB', 'OWBSYS', 'SCOTT', 'ORACLE_OCM', 'ORDDATA', 'APEX_030200', 'OWBSYS_AUDIT', 'APPQOSSYS', 'FLOWS_FILES') and owner not in (select grantee from dba_role_privs where granted_role='DBA') -
Type an alias, for example,
DBMS application object ownership. This alias is useful when defining the rule on top of this configuration extension. -
For the Parser, use Database Query Parser.
-
-
Click Add to add the second SQL statement.
-
SQL
select distinct 'Application object owner account '||owner||' is not disabled.' value from dba_objects, dba_users where owner not in ('ANONYMOUS','AURORA$JIS$UTILITY$', 'AURORA$ORB$UNAUTHENTICATED','CTXSYS','DBSNMP','DIP','DVF', 'DVSYS','EXFSYS','LBACSYS','MDDATA','MDSYS','MGMT_VIEW','ODM', 'ODM_MTR','OLAPSYS','ORDPLUGINS','ORDSYS','OSE$HTTP$ADMIN', 'OUTLN','PERFSTAT','PUBLIC','REPADMIN','RMAN', 'SI_INFORMTN_SCHEMA','SYS','SYSMAN','SYSTEM','TRACESVR', 'TSMSYS', 'WK_TEST','WKPROXY','WKSYS','WKUSER','WMSYS','XDB') and owner in (select distinct owner from dba_objects where object_type <> 'SYNONYM') and owner = username and upper(account_status) not like '%LOCKED%' -
Type an alias, for example,
DBMS application object owner accounts. -
For the Parser, use Database Query Parser.
-
-
Click Save then click Yes on Configuration box.
Figure 48-10 Completed Create Configuration Extension Page
Creating an Agent-Side Compliance Standard Rule
To create an agent-side compliance rule:
-
From the Enterprise menu, select Compliance, then select Library.
-
On the Compliance Library, click Compliance Standard Rules.
-
Click Create. On the Create Rule pop-up, choose Agent-side Rule.
-
Click Continue.
-
On the Create Rule: Agent-side Rule: Details page provide the following information (see Figure 48-11):
-
Name: DBMS application object ownership
-
Compliance Rule State: Development
-
Severity: Critical
-
Applicable To: Database Instance
-
Description: Application objects should be owned by accounts authorized for ownership.
-
Rationale: Database object ownership implies full privileges to the owned object including the privilege to assign access to the owned objects to other subjects. Unmanaged or uncontrolled ownership of objects can lead to unauthorized object grants and alterations.
-
Click Next.
Figure 48-11 Completed Compliance Standard Rule Details Page
-
-
On the Create Rule: Agent-side Rule: Check Definition Page search for the configuration extension and alias you defined earlier. See Figure 48-12.
Note: The configuration extension name and the alias name are concatenated together to form the name in the Configuration Extension and Name field. For this example, the complete name is: DG0142 DBMS Privileged action audit-DBMS application object ownership.
Click Next.
Figure 48-12 Completed Compliance Standard Rule Check Definition Page
-
On the Create Rule: Agent-side Rule: Test Page, search for a target, and then click Run Test. A pop-up displays stating that the test is running. Click Close on the Confirmation pop-up. See Figure 48-13.
Note: You can have test results that intentionally show violations. For example, if you are testing target type equal to host and you are evaluating a host target, then you will see violation results.
Click Next.
Figure 48-13 Completed Compliance Standard Rule Test Page
-
On the Create Rule: Agent-side Rule: Review, ensure the information is as you intended. If not, click Back and make the necessary corrections. When the information is correct, click Finish. See Figure 48-14.
Note: The compliance standard rule is not defined until you click Finish.
Tips
-
Once the compliance standard rule has been created, it is not automatically evaluated. Consider adding the compliance standard rule to a compliance standard.
-
Assign a corrective action to the rule after the rule has been created.
-
On the Compliance Standard Rules tab, highlight the rule you just created.
-
From the Actions menu, select Assign Corrective Action.
-
From the Assign Creative Action popup, select an existing corrective action and click OK.
-
Figure 48-14 Completed Compliance Standard Rule Review Page
-
-
Repeat these steps for the second rule.
Note: The compliance standard rule is not defined until you click Finish.
Creating a Manual Rule
The purpose of creating this manual rule is to keep track of the checks that cannot be automated: ensuring that test plans and procedures have been followed prior to production.
To create a manual rule:
-
On the Compliance Library, click Compliance Standard Rules.
-
Click Create. On the Create Rule pop-up, choose Manual Rule.
-
Click Continue.
-
On the Create Manual Rule page, provide the following information (see Figure 48-15).
-
Name: DBMS testing plans and procedures
-
Compliance Rule State: Production
-
Severity: Warning
-
Applicable To: Database Instance
-
Description: Plans and procedures for testing DBMS installations, upgrades, and patches should be defined and followed prior to production implementation.
-
Rationale: Updates and patches to existing software have the intention of improving the security or enhancing or adding features to the product. However, it is unfortunately common that updates or patches can render production systems inoperable or even introduce serious vulnerabilities. Some updates also set security configurations back to unacceptable settings that do not meet security requirements. For these reasons, it is a good practice to test updates and patches offline before introducing them in a production environment.
-
Recommendation: Develop, document and implement procedures for testing DBMS installations, upgrades and patches prior to deployment on production systems.
-
Compliant Message: Plans and procedures for testing DBMS installations, upgrades and patches are defined and followed prior to production implementation.
-
Non-Compliant Message: Plans and procedures for testing DBMS installations, upgrades and patches are not defined or followed prior to production implementation.
-
Reference URL: http://iase.disa.mil/stigs/index.html
-
Rule Keywords: Security
-
Click Finish.
-
Creating a Compliance Standard
To create a compliance standard, perform the following steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
On the Compliance Library page, click Compliance Standards.
-
Click Create. On the Create Compliance Standard pop-up, provide the following (see Figure 48-16):
-
Name: CS1 - DB Check
-
Applicable To: Select Database Instance
-
Author: SYSMAN
-
Standard Type: Agent-side
-
Click Continue
Figure 48-16 Completed Create Compliance Standard Pop-Up
-
-
On the Compliance Standard: CS1 - DB Check page, right-click the standard in the navigation tree. Select Add Rules. On the Include Rule Reference, select DBMS application object ownership, DBMS application owner accounts, and DBMS testing plans and procedures. See Figure 48-17. Click OK.
-
Click Save.
Associating the Compliance Standard to a Target
To associate the compliance standard to a target, perform the following steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
On the Compliance Library page, click Compliance Standards.
Figure 48-18 Compliance Standards Library Page
-
Highlight the newly created standard (CS1 - DB Check) and click the Associate Targets button.
-
On the Target Association for Compliance Standard: CS1 - DB Check page click Add.
-
Choose one or more targets, for example, Oemrep_Database. See Figure 48-19.
Figure 48-19 Completed Target Association Page
-
Click Select. Click OK.
-
Click Yes to Save the Association.
48.6.3 Suppressing Violations
The purpose of this example is to suppress violations. We will suppress the violation that arose due to the manual rule defined in Creating Compliance Standard Agent-side and Manual Rules.
Follow these steps: