| User Data Repository Diameter User's Guide Release 12.4 E92984-01 |
|
 Previous |
 Next |
S6a/S6d HSS Topology Hiding is concerned with hiding the identities of a Protected Network's HSS when it exchanges messages with Untrusted Networks. An HSS's host name is embedded in the Origin-Host and Session-Id AVPs sent in Request messages and the Origin-Host AVP sent in Answer messages. This capability is associated with the Diameter S6a/S6d application message set defined in 3GPP TS 29.272, Mobility Management Entity (MME) and Serving GPRS Support Node (SGSN) related interfaces based on Diameter protocol.
S6a/S6d HSS Topology Hiding determines which entity (HSS or MME/SGSN) initiated a message based on the Command Code in the message.
HSS identities are hidden by replacing the Hostname portion of the Origin-Host and Session-Id AVPs (Session-Id format: <host name><implementation portion>) with an operator-defined HSS Pseudo Hostname that is assigned to the Protected Network in the S6a/S6d HSS Topology Hiding Configuration Set.
Protected-HSS to Untrusted-MME/SGSN Transactions
The Session-Id AVP values are restored at TH Trigger Point ATR, from the Hostname portion of the Session-Id AVP value that is saved in the Pending Transaction Record (PTR).
The Hostname restoral procedure is not required for Answers initiated by internal nodes (Diameter Routing Function and applications) as these Answer responses are based upon the original Request message content and thus do not contain Pseudo Hostnames.
An example of a Protected-HSS to Untrusted-MME/SGSN Diameter transaction is shown in Figure 10-12.
Figure 10-12 S6a/S6d HSS TH Protected-HSS to Untrusted-MME/SGSN Diameter Transaction
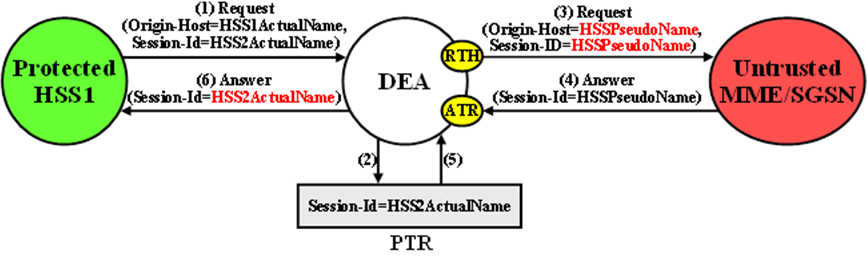
For Protected-HSS to Untrusted-MME/SGSN transactions, S6a/S6d HSS topology information hiding is performed only on Answer messages that meet the following criterion:
When the above criterion is met, Session-Id AVP restoral is performed using the HSS's Actual Hostname stored in the PTR.
Untrusted-MME/SGSN to Protected-HSS Transactions
The Destination-Host AVP contains an S6a/S6d HSS pseudo-host name. If a single pseudo-name is assigned in S6a/S6d HSS TH Configuration Set, then no restoral of the Destination-Host is done by TH (instead the operator can deploy host Resolution Application such as RBAR/FABR). If a single pseudo-name is not assigned per S6a/S6d HSS Configuration Set and instead a unique pseudo-name is assigned per actual S6a/S6d HSS name, then the pseudo-host name must be replaced with the S6a/S6d HSS actual-host name at TH trigger point RTR.
Restoral of a Protected-HSS's actual-host name in the Untrusted-MME/SGSN to Protected-HSS Request message is not performed by topology hiding if a single pseudo-name is used in S6a/S6d HSS TH Configuration Set assigned to a protected network. Instead, this replacement function is required of a HSS Address Resolution application such as FABR or RBAR applications.
HSSAn example of an Untrusted-MME/SGSN to Protected-HSS Diameter transaction is shown in Figure 10-13 and when pseudo-name per S6a/S6d HSS host name in S6a/S6d HSS TH Configuration Set.
Figure 10-13 S6a/S6d HSS TH Untrusted-MME/SGSN to Protected-HSS Transaction
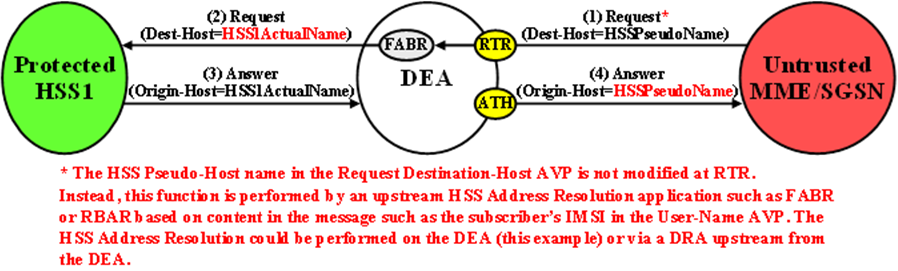
Figure 10-14 S6a/S6d HSS TH Untrusted-MME/SGSN to Protected-HSS Transaction
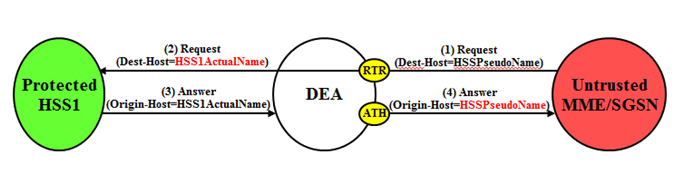
Restoral of a Protected-HSS's actual-host name in the Untrusted-MME/SGSN to Protected-HSS Request message is performed by topology hiding if a unique pseudo-name is assigned per S6a/S6d HSS host name in S6a/S6d HSS TH Configuration Set.