| Oracle® Retail Integration Bus Installation Guide Release 13.1 |
|
 Previous |
 Next |
This section details the process of creating a separate RIB related OC4J admin role and user. This is an optional, but recommended step that will allow the RIB installation and administration by a user other that the oc4jadmin.
General steps to create the roles and user:
Create a role (rib-oc4j-administrators) specific to rib.
Create a user (riboc4jadmin) with password.
Add the previously created user to this role.
Assign privileges and permissions to the created role. This will assign the "deployment-role" with the required permissions.
Create security mappings to this role.
These steps have to be performed on each rib-<app>-oc4j-instance where a RIB (rib-app>) will be deployed.
This section describes how the Oracle Application Server Enterprise Manager can be used to create the role and users.
|
Note: For details on security and information on creation of roles and users refer to the Oracle® Application Server Administrator's Guide 10g Release 3 (10.1.3.3). |
These steps require a user that has ascontrol_admin role. By default this is the oc4jadmin user and role.
Open a browser and go to the Oracle Application asconsole url:
http://<hostname>:<port>/em
where hostname - is the hostname on which the OAS is running.
port - is the port in which the OAS is listening for http request.
e.g: http://localhost:7777/em
Make sure that the rib-<app>-oc4j-instance is up and running.
Select the oc4j instance for which the role and user needs to be created.
For example, rib-rms-oc4j-instance.
Select the Administration tab.
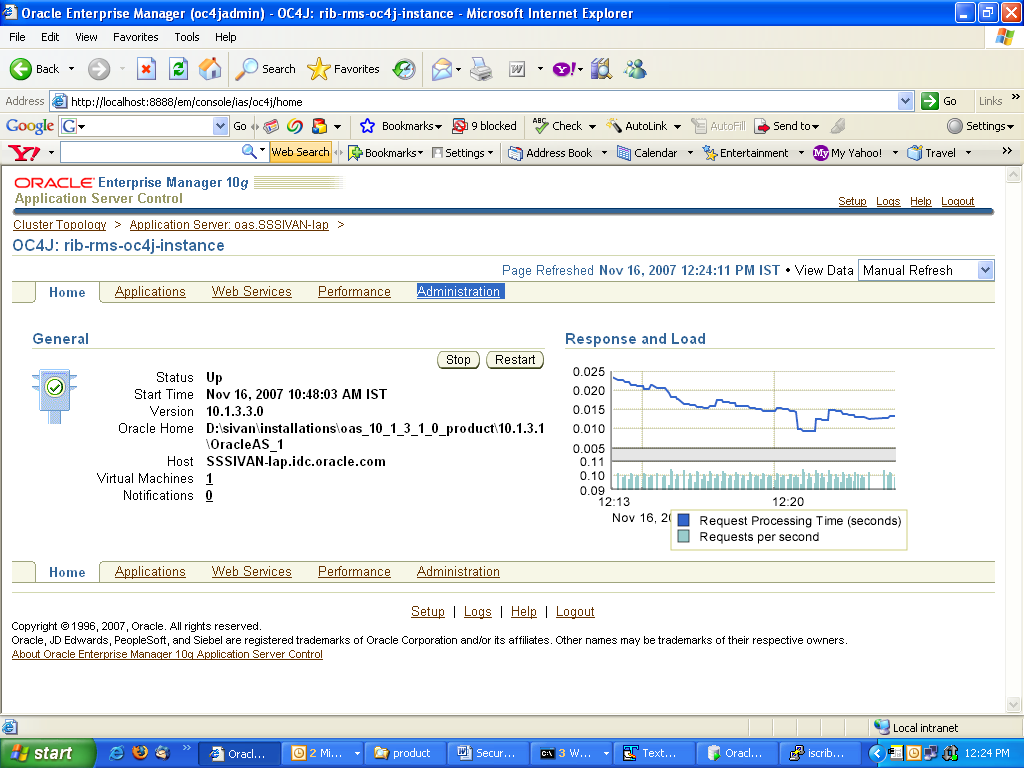
This displays a page with Administration tasks like "Properties", "Services", "Security," etc.
Under "Security" option, select Security Providers and select the icon under the Go to task column of the table.
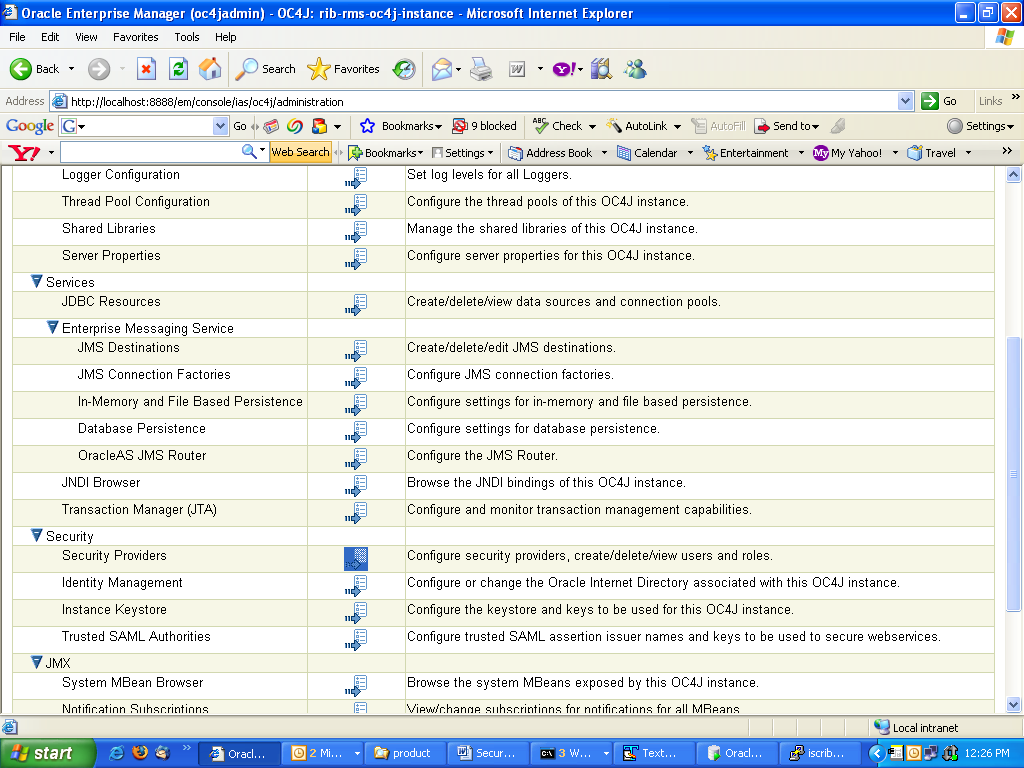
On the Security Providers screen, select the Instance Level Security.
Select the Realms tab on the Instance Level Security.

Select the jazn.com realm. Click the number in the roles column to create roles.
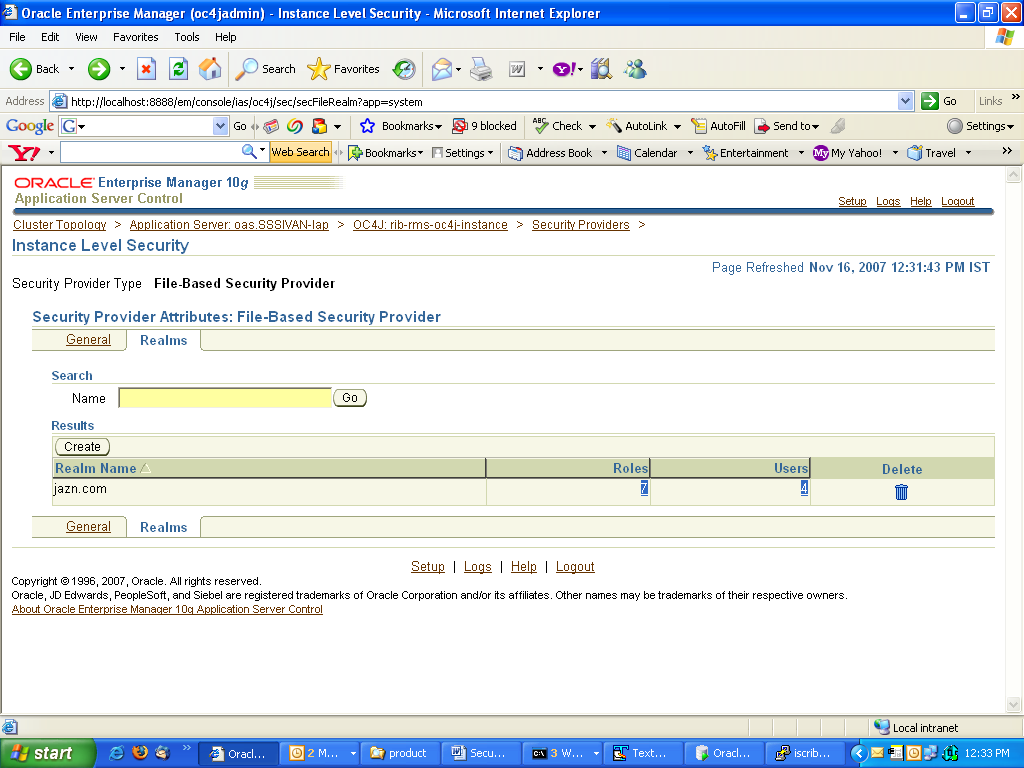
Select Create.
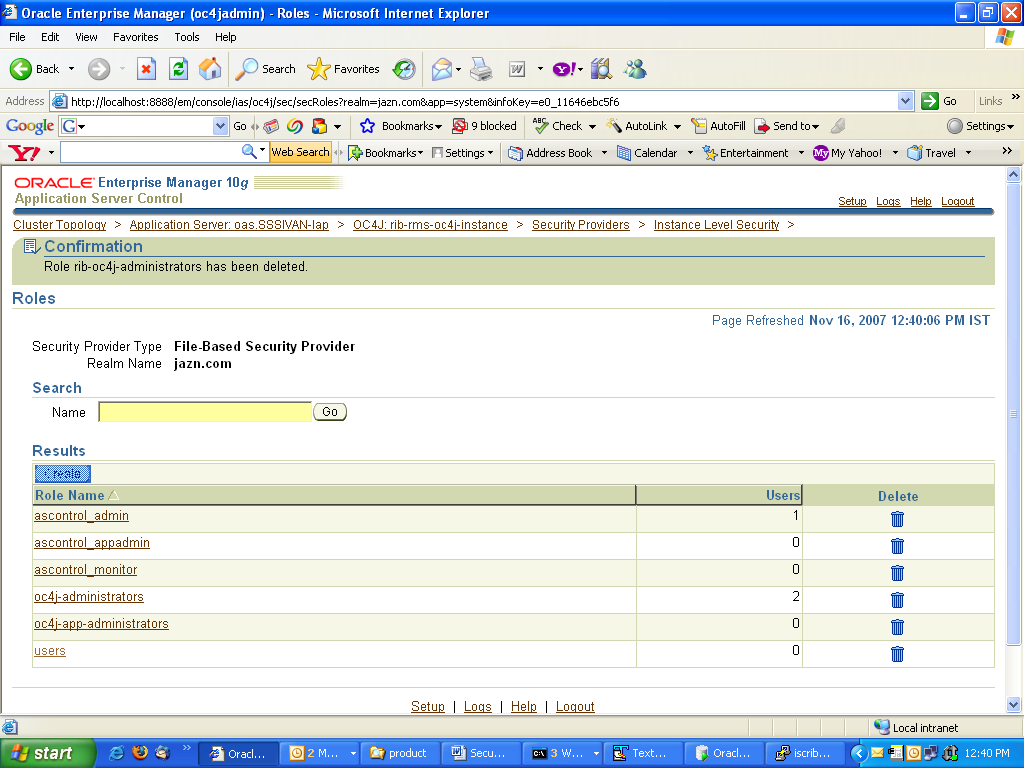
Provide the name of the role as "rib-oc4j-administrators" and choose Grant RMI login Permissions check box option and create the role.
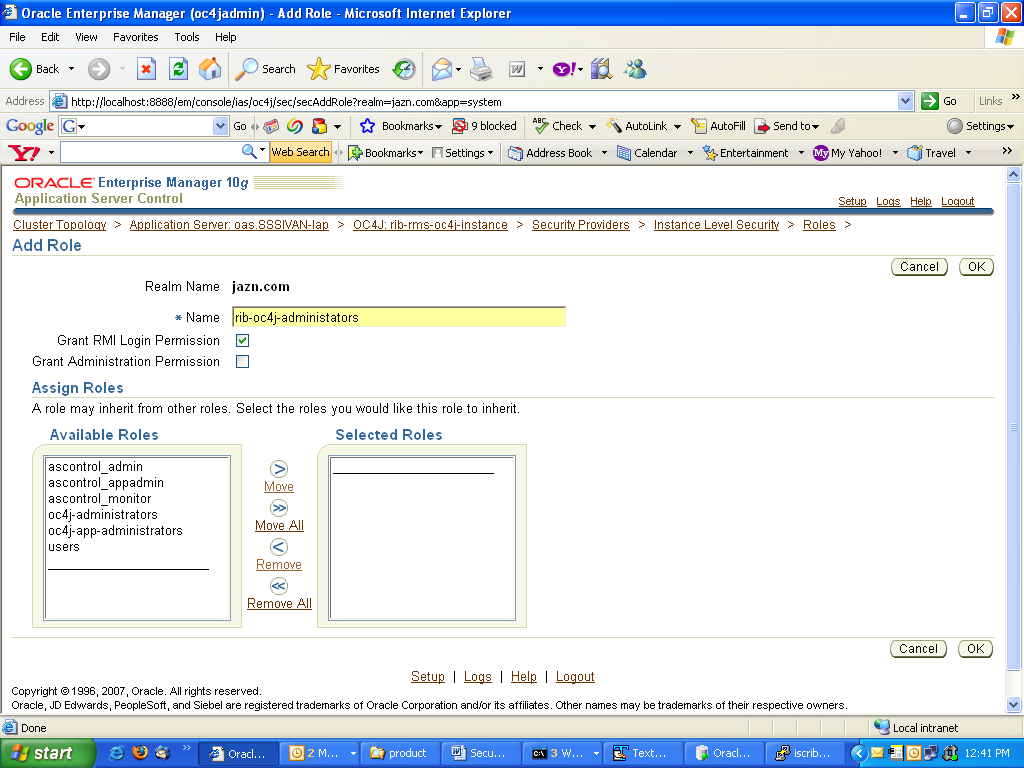
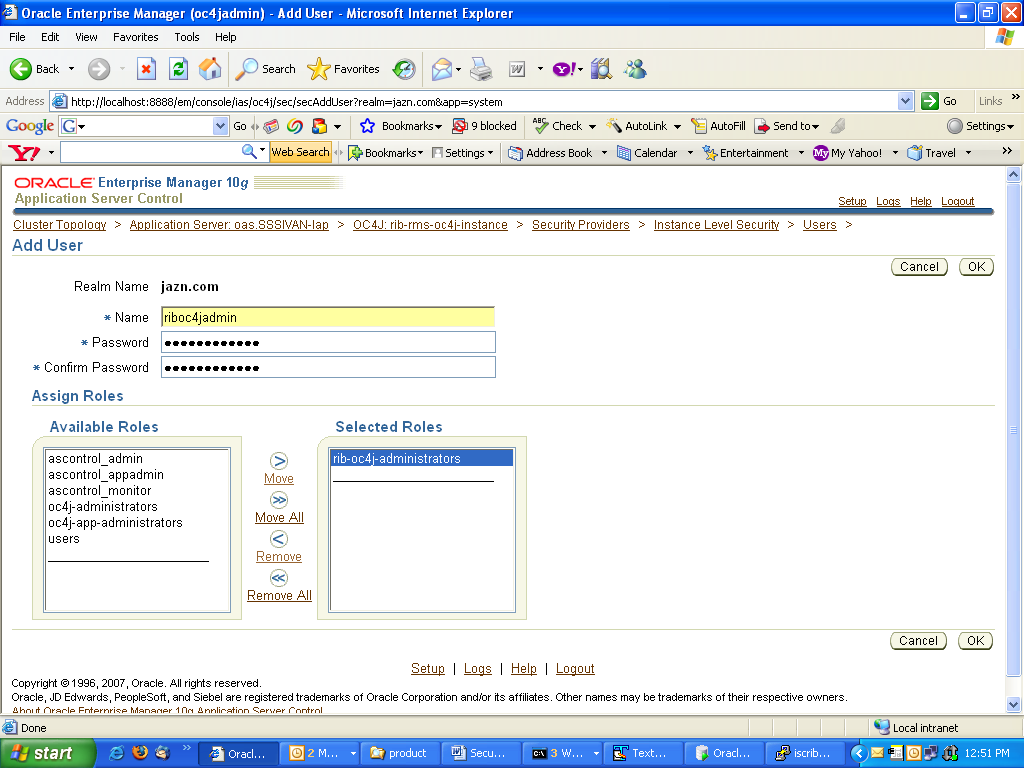
Return to the "Instance Level Security" screen. Select the Users column to display the "Users" page.
On the "Users" page, use the Create button to create a user with name = "riboc4jadmin" and a suitable password. Move the previously created role "rib-oc4j-administrators" to the "Selected Roles" text selection box.
The new "rib-oc4j-administrators" role must be added to the <security-role-mapping> in the appropriate oc4j-instance XML files. This requires using a text editor to directly edit the content of these files.
|
Note: Create a backup of the files before editing. |
All of the files are located in the <rib-app-oc4j-instance> home directory in the $ORACLE_HOME/j2ee sub-directories.
For example: /home/wsadmin/product/10.1.3.3/OracleAS_6/j2ee/rib-rms-oc4j-instance
In the system-application.xml file under the <oc4j-instance-home>/config directory, the role has to be added in the <security-role-mapping> node.
For example: /home/wsadmin/product/10.1.3.3/OracleAS_6/j2ee/rib-rms-oc4j-instance/config
<namespace-access>
<read-access>
<namespace-resource root="">
<security-role-mapping>
<group name="administrators" />
<group name="oc4j-administrators"/>
<group name="ascontrol_admin"/>
<group name="rib-oc4j-administrators"/>
<group name="users"/>
</security-role-mapping>
</namespace-resource>
</read-access>
<write-access>
<namespace-resource root="">
<security-role-mapping>
<group name="administrators" />
<group name="oc4j-administrators"/>
<group name="ascontrol_admin"/>
<group name="rib-oc4j-administrators"/>
<group name="users"/>
</security-role-mapping>
</namespace-resource>
</write-access>
</namespace-access>
In the orion-application.xml file under the <oc4j-instance-home>/application-deployment/ascontrol directory, the role has to be added in the <security-role-mapping> node.
For example: /home/wsadmin/product/10.1.3.3/OracleAS_6/j2ee/rib-rms-oc4j-instance/>/application-deployment/ascontrol
<security-role-mapping name="rib-oc4j-administrators">
<group name="rib-oc4j-administrators" />
</security-role-mapping>
This step maps the deployment role to the J2EE role.
To allow the J2EE role to be used inside the application, edit the orion-ejb-jar.xml file present under <oc4j-instance-home>/application-deployments/admin_ejb directory.
For example: /home/wsadmin/product/10.1.3.3/OracleAS_6/j2ee/rib-rms-oc4j-instance/>/application-deployment/ admin_ejb
This completes the creation and mapping of the users and roles. Restart the oc4j instance after these changes.