4Communications and Data Encryption
Communications and Data Encryption
This chapter provides an overview of communications paths between Siebel Enterprise components and of how to configure components for secure communications. It also describes encryption technologies available for transmitting and storing Siebel application data. It includes the following topics:
About Certificates and Key Files Used for TLS Authentication
Configuring TLS Mutual Authentication for SHA-2 Certificates Using EAI HTTP Transport
About Configuring Encryption for Siebel Enterprise and Siebel Application Interface
Configuring TLS Encryption for Siebel Enterprise or Siebel Server
Enabling SSL Acceleration for Application Interface/Enabling HTTP
Configuring Encryption for Mobile Web Client Synchronization
Types of Encryption
Encryption is a method of encoding data for security purposes. Siebel Business Applications support industry standards for secure Web communications, and for encryption of sensitive data such as passwords. The following topics outline the standards supported:
Communications Encryption
To make sure that information remains private, Siebel Business Applications support the use of the following encryption technologies for communications:
TLS encryption for Web client connections. For data security over the Internet, Siebel Business Applications support the use of the Transport Layer Security (TLS) capabilities of supported Web servers to secure transmission of data between the Web browser and the Web server. The use of TLS for Web server and Siebel Web Client communications is transparent to Siebel Business Applications. For information on configuring TLS for Web server communications with the browser, see the vendor documentation.
Siebel Business Applications can be configured to run completely under HTTPS or simply handle login requests under HTTPS. For more information, see About the Siebel Web Client and Using HTTPS and Implementing Secure Login.
Encryption for Siebel component connections (TLS). Siebel administrators can enable encryption for communications between Siebel components. The Siebel communications protocol provides a security and compression mechanism for network communications based on TLS.
By default, encryption based on TLS uses the AES algorithm with 256-bit encryption keys.
TLS also supports certificate authentication between the Web server and the Siebel Server, or between Siebel Servers.
TLS encryption for connections to directory servers. TLS encryption is supported for connections to certified LDAP directories.
TLS encryption for connections to email servers. TLS encryption is supported for connections to email servers using Siebel Communications Server components. TLS encryption is supported for connections to Microsoft Exchange Server email servers. For information, see Siebel Email Administration Guide.
Encryption of communications between the Siebel Server and the Siebel database. Encryption of communications between the Siebel Server and the Siebel database. The encryption technologies available to encrypt communications between the Siebel Server and the database depends on the encryption methods supported by your RDBMS vendor. For information on how to configure communications encryption between the Siebel Server and the Siebel database, contact your third-party RDBMS vendor.
The following figure shows some of the types of communications encryption available for Siebel Business Applications environment.
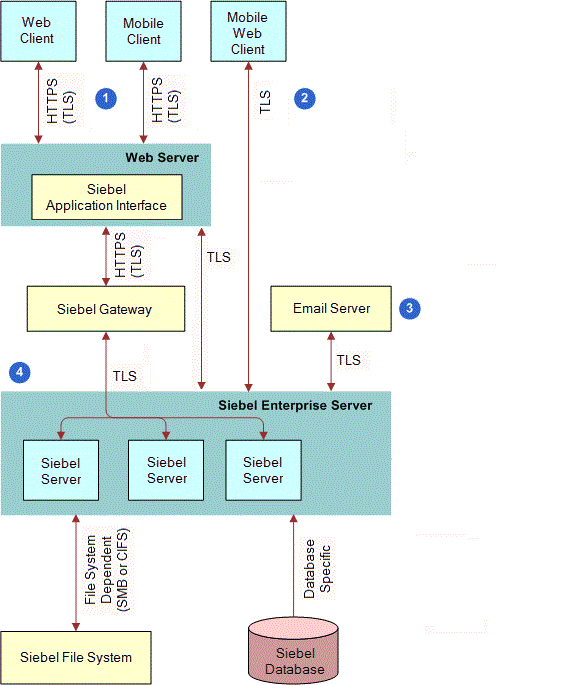
The encryption mechanisms illustrated in this figure are as follows:
Web client and mobile client connections. TLS is used to secure transmission of data between the Web browser and the Web server.
A reverse proxy should be used if HTTPS is disabled.
A reverse proxy should be placed in front of Siebel Application Interface for the following specific topologies:
When Single Sign-On (SSO) is configured with Siebel Application Interface.
If using a compatible SSO solution such as Oracle Access Manager and Oracle Webgate, then you can use any Web server to provide reverse proxy functionality and also any Siebel compatible SSO Web server plug-in on that Web server, provided the plug-in is supported by the Web server platform.
When Siebel Application Interface cannot be deployed or hosted in a DMZ.
Here, you can configure a reverse proxy in the DMZ for Siebel Application Interface, which is expected to be hosted inside a firewall. You can use any Web server to configure this.
For more information on reverse proxies in the DMZ, consult your web server vendor documentation.
Siebel Mobile Web Client connections. You can use SISNAPI with TLS encryption for Mobile Web Client communications with the Siebel Remote server.
Email server connections. TLS encryption for connections to email servers is supported.
Siebel component connections. Communications between Siebel components are based on TLS algorithms.
Certificate Requirements for Communications
Siebel installer for Siebel Business Applications enforces HTTPS during installation, as follows:
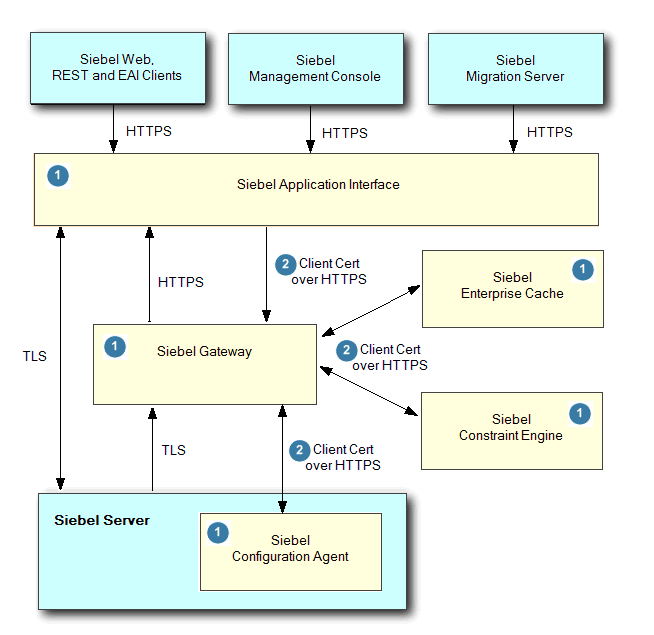
Siebel Web Clients, Siebel Management Console and the Siebel Migration server all communicate with the Siebel Application Interface over HTTPS.
All communication between Siebel services (Siebel Application Interface, Siebel Gateway, Siebel Configuration Agent, Siebel Enterprise Cache, and Siebel Constraint Engine) are enforced over HTTPS by Siebel installer.
Siebel Application Interface is an external interface accessing Siebel services. All other Siebel services are internal services and they are protected by client certificate based authentication.
Any Siebel service-to-service access is over HTTPS with client certificate based authentication (for example, two-way SSL). Client certificates are used for service-to-service authentication.
Certificate requirements for communications are illustrated in the following figure as follows:
Siebel Application Interface, Siebel Gateway, Siebel Configuration Agent, Siebel Enterprise Cache and Siebel Constraint Engine are hosted in application containers (Apache Tomcat).
For information on configuring application containers, see Siebel Installation Guide for the operating system you are using. For information on starting and stopping application containers, see Siebel System Administration Guide.
During Siebel installation (of the aforementioned components), the installer prompts you to specify valid keystore and truststore files, as follows:
Keystore Name. Specify a file (such as a JKS file) you have generated that will serve as the keystore. For example, import the client or server certificate into the keystore using the Java Keytool utility.
Truststore Name. Specify a file (such as a JKS file) you have generated that will serve as the truststore. For example, import the Certificate Authority (CA) certificate into truststore using the Java Keytool utility.
Since Siebel internal nodes are configured for client certificate based authentication, make sure that you use the correct client identity in the CN and Subject Alternate Name (SAN) fields. You can create certificates with the exact FQDN or IP address, or with a wildcard in the FQDN. For example, if you replace
host.domain.subdomain.comwith*.domain.subdomain.com, then this eliminates the need to create separate client certificates for each machine.Note: It is recommended that you use the certificates provided by the Certificate Authority (CA) rather than self-signed certificates. For production environments, you must create a certificate request and get it signed either by your internal CA (for employee-only environments) or an external CA (for customer, consumer, or partner environments). Self-signed certificates are suitable for development environments, for example, where you can provide instructions to users to import the self-signed certificate, since clients will not trust such a certificate unless it is manually installed into the certificate store.For more information, see About Importing Certificates into Keystore and Truststore and About Generating Keystore and Truststore Files.
Password. Specify the password for the specified keystore and truststore files.
Confirm Password. Confirm the password for the specified keystore and truststore files.
Note: The Siebel Gateway requires that client connections from the Siebel Application Interface be authenticated using a client certificate (mutual authentication). As such, the SSL certificate on the Application Interface must be valid for use as a client certificate as well as a server certificate. When requesting the certificate, ensure that it will include both the"clientAuth"and"serverAuth"Extended Attributes. These are typically included in certificates issued by commercial Certificate Authorities, but may or may not be included by default in certificates issued by an internal CA.
About Importing Certificates into Keystore and Truststore
When you import your certificate into the keystore or truststore, you typically give it an alias (for example, —alias server) as follows:
keytool -import -trustcacerts -alias server -file your_site_name.p7b -keystore your_site_name.jks
Then in your server.xml file, you must declare the same alias (for example, keyAlias=”server”) as follows:
<Connector port="443" maxHttpHeaderSize="8192" maxThreads="150" minSpareThreads="25" maxSpareThreads="75" enableLookups="false" disableUploadTimeout="true" acceptCount="100" scheme="https" secure="true" SSLEnabled="true" clientAuth="false" sslProtocol="TLS" keyAlias="server" keystoreFile="/home/user_name/your_site_name.jks" keystorePass="your_keystore_password" />
About Generating Keystore and Truststore Files
The keystore and truststore files are JKS files containing certificates. These files are necessary for the application container to be able to use secure two-way communications when connecting with other Siebel modules, as occurs during Siebel Management Console configuration and in normal operation. Note the following about generating the keystore and truststore files:
The keystore and truststore files must contain the server certificate chain and an imported CA certificate.
Generate your files so that the keystore file references both the private key and the public key, while the truststore file references the public key only.
Generate your certificates using the Java Runtime Environment (JRE) provided with your release.
Specify the password that was previously configured to open the certificate files.
Use the same password for the keystore and truststore files.
Note: It is recommended that you create all keystores with the same password as the one entered in the installer. The ability to have different passwords for the truststore and keystore is not currently supported by the installer. However if different passwords are required, then you can modify the keystore password by editing the server.xml file and all the relevant properties files in the webapps directory.Use the fully qualified domain names rather than IP addresses.
Note: If you use IP address instead of FQDN, then certificates must be created with both FQDN and IP address as two separate SAN entries and in such cases, the Siebel Server fails. As a result, it is recommended that you use the FQDN rather than IP address.If you do not configure the keystore and truststore files correctly, then you will not be able to configure the Siebel Business Applications, as described in Configuring Security Adapters Using the Siebel Management Console, Configuration Parameters Related to Authentication and Siebel Installation Guide for the operating system you are using.
Modifying Keystore and Truststore Files
In cases where it is necessary to modify the keystore and truststore file details, complete the steps in the following procedure.
To modify keystore and truststore files
Go to the location where the keystore and truststore files are stored.
This location is specific to Siebel Application Interface, Siebel Gateway, Siebel Configuration Agent, or any other component.
Use the Java Keytool commands to edit the keystore and truststore file details as required.
It is recommended that you keep the same keystore and truststore names and passwords to avoid editing the corresponding properties and server.xml files. However, in the event where you change the keystore and truststore names and passwords, then do the following to change the details in the properties and server.xml files:
Encrypt the password using the encryptstring.jar utility
$<javahome>\bin>java - jar $<siebelhome>\siebel\classes\original\encryptstring.jar <<plaintext>>
Go to the corresponding properties file and update the KeyStorePassword and TrustStorePassword with the encrypted value.
You must update the encrypted password in the applicationinterface.properties file, which is located in the application interface layer in the
ai\applicationcontainer\webappsfolder.Go to the corresponding server.xml file (located under
..\conf) and update the truststorepass and keystorepass.To change the password, update the truststorepass and keystorepass in the
\conf\server.xmlfile for Siebel Application Interface, Siebel Gateway, Siebel Configuration Agent, Siebel Enterprise Cache, and Siebel Constraint Engine.Update truststorepass and keystorepass under the HTTP connector.
Update the plain text password here:
$<javahome>\bin>java - jar <connector port="<https port>" ... . keystorepass="xxx" ... . truststorepass="xxx"/>
Restart the application containers for all components where you made changes. For details, see Siebel System Administration Guide.
Copy the new JKS file (with the same password, but with different domain name and hostname) to the siebcerts folder under Siebel Application Interface, Siebel Gateway, Siebel Configuration Agent, or any other component.
Restart the application containers. For details, see Siebel System Administration Guide.
Disabling Certificate Based Mutual Authentication
You can disable certificate based authentication and run all components over HTTPS, however, this action is not recommended for security reasons. The following procedure shows you how to disable certificate based authentication.
To disable certificate based authentication
Set
clientAuth="false"in theconf\server.xmlfile for Siebel Gateway, Siebel Configuration Agent, Siebel Enterprise Cache, and Siebel Constraint Engine to disable certificate based mutual authentication.For example, set the HTTPS connector as follows to keep all communication over HTTPS without client certificate authentication:
<Connector port="xxxx" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="150" SSLEnabled="true" scheme="https" secure="true" SSLVerifyClient="require" SSLEngine="on" SSLVerifyDepth="2" keystoreFile=" xxxx" keystorePass=xxx" " keystoreType="JKS" truststoreFile="xxx " truststorePass="xxx " truststoreType="JKS" clientAuth="false" sslProtocol="TLS" />
Restart the application containers for all components: Siebel Application Interface, Siebel Gateway, Siebel Configuration Agent, Siebel Enterprise Cache, and Siebel Constraint Engine.
For information on starting and stopping application containers, see Siebel System Administration Guide.
Access the UI using the following address:
HTTPS://<hostname>:https_port/.
Data Encryption
To make sure that information remains private, Siebel Business Applications support the use of the following encryption technologies for storing data:
AES database encryption. Siebel Business Applications allow customers to encrypt sensitive information stored in the Siebel database (for example, credit card numbers, Social Security numbers, birth dates, and so on) so that it cannot be viewed without access to the Siebel application.
Customers can configure Siebel Business Applications to encrypt a column’s data before it is written to the database and decrypt the same data when it is retrieved. This encryption prevents attempts to view sensitive data directly from the database. Sensitive data can be encrypted by using AES encryption at various key lengths. Encryption can be enabled using Siebel Tools. For more information, see About Data Encryption.
Siebel Business Applications also use AES encryption to encrypt passwords stored in the Siebel Gateway registry. The Siebel Gateway registry stores information required by the gateway. For more information about encrypted passwords in the Siebel Gateway registry, see About Encryption of Siebel Gateway Password Parameters.
RSA SHA-1 password hashing. Siebel administrators can enable password hashing for user passwords or for database credentials. Hashing uses a one-way hashing algorithm. The default password hashing method is RSA SHA-1. (The previous mangle algorithm is still available for existing customers.)
The Siebel administrator password is stored for Siebel Gateway in the Siebel Gateway registry, and is not hashed; passwords in the Siebel Gateway registry are encrypted using AES encryption.
Password hashing invalidates the password to unauthorized external applications and prevents direct SQL access to the data by anything other than Siebel Business Applications. For more information, see About Password Hashing.
Encryption of the Siebel File System and server disks containing Siebel Business Applications data. It is recommended that you encrypt the Siebel File System and all server disks containing Siebel Business Applications data using third-party products or encryption features provided by your operating system. For information on the encryption technologies available, see the relevant operating system or third-party documentation. For additional information about securing the Siebel File System, see Siebel Security Hardening.
About Certificates and Key Files Used for TLS Authentication
When you configure TLS authentication for a Siebel Enterprise, Siebel Server, or Siebel Application Interface, you specify parameter values that indicate the names of certificate files, certificate authority files, and private key files on the computers that host these components. The certificate files you use for this purpose can be issued by and obtained from third-party certificate authorities. Certificate authority files identify the third-party certificate authority who issued the certificate.
Certificate files must adhere to the following requirements:
Use a supported certificate file format:
On Microsoft Windows environments, certificate authority files can use either ASN (Abstract Syntax Notation) or PEM (Privacy Enhanced Mail) format.
The ASN.1 format is also referred to as the Distinguished Encoding Rules (DER) format. Rename certificate files in DER format to have the file extension .asn.
On UNIX environments, certificate authority files must use the PEM (Base 64 encoded X.509) format. Certificate files in ASN format cannot be used in UNIX environments.
Private key files must use the PEM format.
The certificate file must use the file extension that corresponds to the certificate file format in use: .pem for the PEM format and .asn for the ASN format. You can convert PEM-based certificate files to the ASN-based format.
Certificate files on each computer must be unique and belong to that computer if Enable Peer Authentication parameter is set to TRUE on the remote computer.
If an intermediate certification authority is used, then both the intermediate and the root certificate authority certificates must be in the same file. You specify the name of this file in the Certificate Authority (CA) Certificate File Name parameter when you configure TLS for communication between Siebel components.
Certificate files and private key files are typically installed on each computer that hosts a component or module for which you configure TLS, such as the Siebel Server or Siebel Application Interface. You do not have to authenticate or encrypt communications between components on the same computer. For information on installing certificate files, see Installing Certificate Files.
About Supported Values for Certificate Encryption Keys
A certificate authority certifies ownership of the public and private key pairs that are used to encrypt and decrypt TLS communications. Messages are encrypted with the public key and decrypted with the private key. The certificate key size refers to the size, in bits, of the encryption key provided with the certificate.
For TLS authentication in a Siebel Enterprise, Siebel Server, or Siebel Application Interface, Siebel Business Applications support certificates that use an encryption key size of 1024 bits by default. You can use a higher encryption key size, such as 2048 or 4096 bits, as well.
The size of the certificate key supported depends on the components for which you are configuring TLS communications. The following table shows the certificate key sizes supported for communications between different components in a Siebel Business Applications deployment.
Table Encryption Key Sizes Supported For TLS Certificates
TLS Communication Type |
Supported Key Size |
|---|---|
TLS communications Communications between the Siebel Server and the Web server (Siebel Application Interface), and between Siebel Servers. |
1024-bit certificate keys are supported by default. Certificate key sizes larger than 1024 bits, such as 2048-bit or 4096-bit keys, are also supported. |
TLS communications between Web clients and the Web server. |
The acceptable protocols and key sizes are determined by the underlying operating system and Web server software. In most cases, these systems support larger private key sizes. |
TLS communications between developer clients (including Siebel Tools) and components in the Siebel environment. |
1024-bit certificate keys only are supported. |
TLS communications between the Siebel Server and the Siebel database. |
The key size supported is determined by the third-party database used and database client software. |
TLS communications between Siebel security adapters and external directory servers. |
These connections can support larger bit sizes for certificate keys. |
TLS communications for Web services. |
Web services support up to 4096-bit certificate keys. |
Process of Configuring Secure Communications
This topic describes how to set up encryption for communication between components in the Siebel environment. Encryption can be configured for data traffic between the Web server, Siebel Server, and Siebel Web Client.
To configure secure communications in your Siebel environment, perform the following tasks, as appropriate for your environment:
Configuring TLS Mutual Authentication for SHA-2 Certificates Using EAI HTTP Transport
Configuring TLS Encryption for Siebel Enterprise or Siebel Server
Enabling SSL Acceleration for Application Interface/Enabling HTTP
Configuring Encryption for Mobile Web Client Synchronization
The encryption options described in this topic are not used to encrypt data in the database. For information about data encryption, see About Data Encryption. Also, these encryption options are not used for communications with the database; for such encryption, check with your database vendor.
Installing Certificate Files
This topic describes how to install certificate files on Microsoft Windows and on Unix operating systems, and includes information about the following:
For information on using certificate files, see About Certificates and Key Files Used for TLS Authentication.
This task is a step in Process of Configuring Secure Communications.
About Installing Certificate Files on Windows
If you have enabled Oracle’s Siebel Open UI, and if you are not using Internet Explorer to run your Siebel application, see your browser documentation for information on installing certificate files.
About Installing Certificate Files on UNIX
If you are using a UNIX operating system, then refer to the following for information on obtaining certificate authority files and certificate files:
TLS Encryption for Siebel component connections. Obtain the required certificate files and locate them on a local volume; they do not have to be installed.
TLS encryption for connections to LDAP directories. The LDAP security adapter uses Oracle Wallet Manager to handle the installation of certificates. For information, see Creating a Wallet for Certificate Files When Using LDAP Authentication with TLS.
Communications encryption between the Siebel Server and the Database Server. Refer to your third-party RDBMS vendor for information on configuring communications encryption and certificate requirements.
Installing Certificate Files on UNIX for Client Authentication
When using the EAI HTTP Transport business service with the TLS protocol, you might have to install certificate files, for example, if you want to enable client authentication. For information on client authentication, see Configuring TLS Mutual Authentication for SHA-2 Certificates Using EAI HTTP Transport.
If you are using a UNIX-based operating system, then Siebel Business Applications provide a utility, the mwcontrol utility, that enables you to install on your Siebel Server the certificate authority and certificate files required when using EAI HTTP Transport with TLS.
When you use the mwcontrol utility to install a certificate file, the certificate file must be located on a local volume. You cannot use the mwcontrol utility to install certificate files that are located on a network-attached storage (NAS) device or other remote volume.
The following procedure describes how to use the mwcontrol utility to install certificate files. Execute the mwcontrol utility on each Siebel Server and Siebel Application Interface computer where you want to install client authentication certificate files.
To invoke the mwcontrol utility and install certificate files
Depending on the type of UNIX operating system you use, enter the following commands:
For Bourne shell or Korn shell:
. ./siebenv.sh
For C shell:
source siebenv.csh
Set your
DISPLAYenvironment variable to the IP address of the computer that hosts the mwcontrol utility:For Bourne shell or Korn shell:
export DISPLAY ipaddress of the computer that hosts the mwcontrol utility:0.0
For C shell:
setenv DISPLAY ipaddress of the computer that hosts the mwcontrol utility:0.0
If you are using an X-Windows client, then 00 is the connection identifier.
To invoke the mwcontrol utility, execute the following command:
mwcontrol $SIEBSRVR_ROOT/mw/lib/inetcpl.cplwhere $SIEBSRVR_ROOT is the Siebel Server installation directory.
The wizard appears.
Select the Content tab, then click the Certificates button.
The Certificate Manager appears.
Select the tab that corresponds to the type of certificate you want to install.
For example to install a certifying authority certificate, select Trusted Root Certification Authorities tab.
Click Import to display the Certificate Manager Import Wizard, then click Next to navigate to the location where you stored the certificate file you want to install.
Select the certificate, and click Next.
Select the check box Automatically select the certificate store based on the type of certificate, then click Next.
Click Next, then Finish to complete the installation, and terminate the execution of the mwcontrol utility.
Note the following points about your application’s configuration file before you modify it in the next step:
The configuration files for a client are stored in the client’s
bin\LANGUAGEdirectory, where LANGUAGE represents an installed language pack, such as ENU for U.S. English.When synchronization is performed within an application (using File, Synchronize, and then Database), configuration is read from the configuration file associated with the application (for example, siebel.cfg for Siebel Sales).
For more information about working with the Siebel application configuration files, see Siebel System Administration Guide.
Locate the DockConnString parameter in the [Local] section of the file.
This parameter specifies the name of the Siebel Server used to synchronize with the client. It has the following format:
siebel_server_name:sync_port_#:service:encryption
The encryption element in the DockConnString parameter indicates the type of encryption used during synchronization. Examples of a
DockConnStringparameter value follow:If using TCP-IP, the format is:
APPSRV:40400.If using TLS, the format is:
APPSRV:40400:TLS.
Save your changes and exit the file.
For more information about editing configuration files for Siebel Remote and Mobile Web Clients, see Siebel Remote and Replication Manager Administration Guide and Siebel System Administration Guide.
Restart the Siebel Server or Siebel Application Interface computer on which you installed the certificate file.
Setting HTTP Proxy for UNIX Using the mwcontrol Utility
The following procedure shows you how to set HTTP proxy for UNIX using the mwcontrol utility. A proxy server is a computer that acts as an intermediary between a user’s computer and the Internet. A proxy server allows client computers to make indirect network connections to other network services.
To set HTTP proxy for UNIX using the mwcontrol utility
Change directory to Siebel root bin as follows:
cd $SIEBEL_ROOT/mw/bin
Enter the following command:
mwcontrol $SIEBEL_ROOT/mw/lib/inetcpl.cpl
The Internet Properties window opens.
In the Internet Properties window, click the Connections tab, and then enter the proxy server address and port, for example, as follows:
Address:
www.proxyservername.comPort: 80
Proxy server details are specific to an organization.
Configuring TLS Mutual Authentication for SHA-2 Certificates Using EAI HTTP Transport
Mutual authentication is a process in which a connection between two parties is established only after each party has authenticated the other. In TLS mutual authentication, the client is authenticated to the server and the server is authenticated to the client during the TLS handshake.
Siebel supports server authentication. Client authentication is supported for TLS-based communications using the EAI HTTP Transport business service, and for workflows or outbound Web service calls that call the EAI HTTP Transport business service. In previous releases, client authentication was supported on SHA-1 only but now it is supported on SHA-2 (that is, TLS v1.2).
If you choose to enable client authentication, then the Siebel Server presents a client certificate to an external Web server by supplying values for the HTTPCertSerialNo and HTTPCertAuthority EAI HTTP Transport parameters. The following procedure describes how to configure client authentication using the EAI HTTP Transport business service.
This task is a step in Process of Configuring Secure Communications.
To configure client authentication with SHA-2 certificates using EAI HTTP Transport
Obtain the following files, according to the operating system you are using, and install them on Siebel Server:
For Microsoft Windows operating systems:
A certificate authority file.
A client certificate file that is in PKCS#12 format.
For non-windows operating systems:
Import the client certificate into the keystore JKS file.
Import the CA certificate in to the truststore JKS file.
For information on how to import certificates into JKS files, see Siebel Installation Guide for the operating system you are using.
Make sure that the CONTAINERURL parameter for the OUTBOUNDSHA2 named subsystem has the correct HTTP port number of the application container running on Siebel Server, using the command:
list parameter for the named subsystem OUTBOUNDSHA2
For example:
CONTAINERURL value http://localhost:9001/siebel/outboundeai
Assign the subsystem name to the EAIOutboundSubSys parameter of the component used, using the following command for example:
change param EAIOutboundSubSys=OUTBOUNDSHA2 for comp eaiObjMgr_enu
Restart Siebel Server before testing SHA-2 using EAI HTTP Transport.
For information on installing certificate files, see Installing Certificate Files.
Configure the Web server for client authentication.
For information on configuring client authentication on the Web server, refer to your Web server vendor documentation.
Provide client authentication information by specifying values for the following EAI HTTP Transport parameters:
HTTPCertSerialNo. Specify the client certificate serial number. This is a hexadecimal string which cannot contain spaces.
HTTPCertAuthority. Specify the name of the authority that issued the client certificate. The issuing authority name must be in FQDN format and is case sensitive.
The certificate authority and serial number details are displayed on the certificate, which you can view using your browser (Windows) or the mwcontrol utility (UNIX).
The EAI HTTP Transport business service can be called directly or indirectly.
If the EAI HTTP Transport business service is invoked directly by an eScript script or workflow, then you can specify the HTTPCertSerialNo and HTTPCertAuthority parameters using the Set Property method of the business service call. For additional information, see Transports and Interfaces: Siebel Enterprise Application Integration.
If the EAI HTTP Transport business service is invoked indirectly by an outbound Web service, then you can specify the HTTPCertSerialNo and HTTPCertAuthority parameters as input arguments for the outbound Web Service Dispatcher. For additional information, see Integration Platform Technologies: Siebel Enterprise Application Integration.
About Configuring Encryption for Siebel Enterprise and Siebel Application Interface
When you configure your Siebel Enterprise or Siebel Application Interface profile after installation using the Siebel Management Console, you specify the encryption type to use for communications between the Siebel Server and Web server (Siebel Application Interface), and between Siebel Servers.
The Security Encryption Level or Type parameter setting determines how encryption is defined within generated connect strings for Siebel Business Applications. The Security Encryption Level or Type parameter options for configuring the encryption type are:
Without Encryption.
Using TLS 1.2. TLS encryption is supported on Siebel Server at the server and component level; TLS works for Siebel Remote and Mobile Web Client connections. For information on configuring TLS, see the following topics:
For Siebel installations that include both UNIX and Microsoft Windows operating systems, it is recommended that you use an encryption method supported across operating systems, such as TLS.
For information about running the Siebel Management Console, see the Siebel Installation Guide for the operating system you are using.
About Key Exchange for TLS Encryption
If you are using TLS encryption between the Web server (Siebel Application Interface) and Siebel Server or between Siebel Servers, then the key exchange is handled through a standard TLS handshake.
Configuring TLS Encryption for Siebel Enterprise or Siebel Server
This topic describes how to configure a Siebel Enterprise or Siebel Server to use TLS encryption and authentication for communications between Siebel Servers and the Web server (Siebel Application Interface), and between Siebel Servers. Configuring TLS for communications is optional.
This task is a step in Process of Configuring Secure Communications.
Configuring TLS communications between Siebel Servers and the Web server also requires that you configure the Siebel Application Interface to use TLS. When configuring TLS for Siebel Server and the Siebel Application Interface, you can also configure connection authentication for the relevant modules. In other words, when a module connects to another module, modules might be required to authenticate themselves against the other using third-party certificates.
Connection authentication scenarios are:
Siebel Server authenticates against the Web server.
Web server authenticates against the Siebel Server.
Siebel Server authenticates against another Siebel Server.
If you select the peer authentication option, mutual authentication is performed.
Configuring a Siebel Enterprise or Siebel Server to use TLS encryption involves the following tasks:
Run the Siebel Management Console for the Siebel Enterprise or Siebel Server and select the appropriate option to deploy TLS.
This task is described in Deploying TLS for Siebel Enterprise or Siebel Server.
For each Application Object Manager that is to use TLS, set the CommType parameter to TLS as appropriate.
This task is described in Setting Additional Parameters for Siebel Server TLS.
Deploying TLS for Siebel Enterprise or Siebel Server
The following procedure describes running the Siebel Management Console to deploy TLS for a Siebel Server or a Siebel Enterprise. Performing this procedure adds parameters to the Siebel Gateway; these parameters can alternatively be set using Siebel Server Manager.
To deploy TLS encryption for the Siebel Server or Enterprise:
Before you begin, obtain and install the necessary certificate files that you need if you are configuring TLS authentication.
Depending on whether you are enabling TLS encryption for the Siebel Enterprise or for the Siebel Server, do one of the following:
If you are running the Siebel Management Console to configure the Siebel Enterprise, then do the following:
Start the Siebel Management Console and configure values for the Enterprise.
For information on this task, see Siebel Installation Guide for the operating system you are using.
When the Additional Tasks for Configuring the Enterprise screen appears, select the Enterprise Network Security Encryption Type option.
On the Security Encryption Level or Type screen, select the following option: SISNAPI to use TLS 1.2.
To run the Siebel Management Console directly on a Siebel Server computer, do the following:
Start the Siebel Server Management Console directly and configure values for the Siebel Server.
For information on this task, see Siebel Installation Guide for the operating system you are using.
When the Additional Tasks for Configuring the Siebel Server screen is displayed, select the Server-Specific Security Encryption Settings option.
On the Security Encryption Level or Type screen, select the following option: SISNAPI to use TLS 1.2.
Note: If you change to a different Siebel Management Console, then you might need to redeploy the profile. The easiest way to do this is to create a new profile and apply it to the required server using Siebel Management Console (or Siebel Server Manager, although this is harder).Specify the name and location of the certificate file and the certificate authority file.
The parameters to configure in the Siebel Gateway are:
Certificate File Name (CertFileName)
Certificate Authority (CA) Certificate File Name
For more information about these parameters, see Parameters for Configuring Security Adapter Authentication.
Specify the name of the private key file, and the password for the private key file, then confirm the password. The password you specify is stored in encrypted form.
The parameters to configure in the Siebel Gateway are:
Private Key File Name
Private Key File Password
For more information about these parameters, see Parameters for Configuring Security Adapter Authentication.
Specify whether or not you want to enable peer authentication.
Peer authentication means that this Siebel Server authenticates the client (that is, Siebel Application Interface or another Siebel Server) that initiates a connection. Peer authentication is disabled (or false) by default.
The peer authentication parameter is ignored if TLS is not deployed between the Siebel Server and the client (either the Siebel Application Interface or another Siebel Server). If peer authentication is enabled (set to True) on the Siebel Server, then a certificate from the client is authenticated provided that the Siebel Server has the certifying authority’s certificate to authenticate the client’s certificate. The client must also have a certificate. If TLS is deployed and the Siebel Application Interface has a certificate, then it is recommended that you enable peer authentication on both the Siebel Server and the Siebel Application Interface to obtain maximum security.
The parameter to configure in the Siebel Gateway is Enable Peer Authentication.
Specify whether or not you require peer certificate validation.
Peer certificate validation performs reverse-DNS lookup to independently verify that the hostname of the Siebel Server computer matches the hostname presented in the certificate. Peer certificate validation is false by default.
The parameter to configure in the Siebel Gateway is Validate Peer Certificate.
Depending on whether you are running Siebel Management Console for Siebel Enterprise or Siebel Server, return to either the Siebel Enterprise or the Siebel Server configuration process.
Continue to configure values for the Siebel Enterprise or Siebel Server, then review the settings, finish configuration, and restart the server (which is required only if you are reconfiguring TLS encryption for Siebel Enterprise or Siebel Server).
Perform the tasks in Setting Additional Parameters for Siebel Server TLS.
Repeat this procedure for each Siebel Server in your environment, as necessary.
Make sure you also configure each Siebel Application Interface in your environment. For information, see Configuring TLS Encryption for Siebel Application Interface.
Setting Additional Parameters for Siebel Server TLS
After configuring TLS for a Siebel Server, you must set additional server parameters (on the gateway) to enable TLS for the Siebel Server as described in the following procedure.
To set additional parameters for Siebel Server TLS
Using Siebel Server Manager, set the Communication Transport parameter (alias CommType) to TLS as appropriate for each Application Object Manager that is to use TLS. (TCP/IP is used by default.)
For information on using Siebel Server Manager, see Siebel System Administration Guide.
If you previously used RSA encryption, then, using Siebel Server Manager, set the Security Encryption Level or Type parameter (alias Crypt) to
NONEfor the Siebel Enterprise.
Configuring TLS Encryption for Siebel Application Interface
This topic describes how to configure the Siebel Application Interface to use TLS encryption and, optionally, authentication for communications with Siebel Servers. Configuring TLS communications between Siebel Servers and the Web server also requires that you configure a Siebel Enterprise or Siebel Server to use TLS. For information on this task, see Configuring TLS Encryption for Siebel Enterprise or Siebel Server.
This task is a step in Process of Configuring Secure Communications.
You must include TLS-related parameters in the applicationinterface.properties file if you are using TLS to encrypt communications between the Web server and the Siebel Server.
To configure TLS encryption for Siebel Application Interface
Ensure that the following parameters are set in the applicationinterface.properties file by the Siebel installer:
TrustStoreName
KeyStoreName
TrustStorePassword
TrustStoreType=JKS
KeystoreType=JKS
KeyStore and TrustStore with valid certificate, are a prerequisite for the application interface component installer to pick and use.
The applicationinterface.properties file is located in the application interface layer in the
ai\applicationcontainer\webappsfolder.In addition to these parameters, set the following parameter in the setenv.bat file under
$build$\swsm\applicationcontainer\bin:set CATALINA_OPTS=-Djavax.net.ssl.keyStoreAlias=<<keystore alias name>>
Enabling SSL Acceleration for Application Interface/Enabling HTTP
This topic describes how to configure SSL acceleration for communications between application interface traffic. The instructions in this topic apply to all channels (UI and EAI).
This task is a step in Process of Configuring Secure Communications.
If you are using a third party HTTP-based load balancer for Siebel Application Interface load balancing and you want to off-load the processing of SSL encryption and decryption algorithms to the hardware accelerator on your load balancer, then you must enable the EnforceSSL parameter. Doing so improves application performance and ensures that SSL is used to encrypt URLs. EnforceSSL is False by default. To enforce the use of SSL acceleration, you change the EnforceSSL parameter for an Application Object Manager to True.
To enable SSL acceleration for application interface/enable HTTP
Set the Application Object Manager parameter, EnforceSSL, to TRUE as follows:
Navigate to the Administration - Server Configuration screen, then the Servers view.
In the Siebel Servers list, select the Siebel Server of interest.
Click the Components view tab.
In the Components list, select the Application Object Manager of interest, such as Call Center Object Manager (ENU).
Click the Parameters subview tab.
In the Parameter field, perform a case-sensitive query on EnforceSSL.
Click in the Value on Restart field and type TRUE.
Set the SecureLogin and SecureBrowse server parameters to FALSE for the Application Object Manager (see Step 1 for details).
Enable HTTP for Siebel Application Interface.
To do this, set the
<transport-guarantee>value to NONE (instead of CONFIDENTIAL) in the web.xml file of Siebel Application Interface:<security-constraint> <web-resource-collection> <web-resource-name>securedapp</web-resource-name> <url-pattern>/*</url-pattern> </web-resource-collection> <user-data-constraint> <transport-guarantee>NONE</transport-guarantee> </user-data-constraint> </security-constraint>Note: When enabling HTTP/disabling HTTPS for the application interface, the implementer must take full responsibility for ensuring overall security of the deployment. When enabling HTTP, protecting intranet ports preservation of secure function involves the following:A reverse proxy must be implemented in front of all application interfaces in the DMZ to secure the intranet ports behind the DMZ.
Adjustments to HTTP in linked Web applications to avoid mixed content errors may be needed ( if supported). This may require reverse proxies and/or a new security design for any impacted UI based integrations.
Restart Siebel Application Interface and Siebel Servers.
About Configuring Encryption for Web Clients
This topic describes the encryption options available for Web client communications. To use encryption, both the server and the client must enforce encryption in their connection parameters. If these parameters do not match, then connection errors occur.
Siebel Business Applications support the following types of clients:
Siebel Web Client. This client runs in a standard browser from the client computer and does not require any additional persistent software installed on the client. Encryption settings you set for the Siebel Application Interface or Siebel Server are automatically recognized by this Web client.
Siebel Business Applications support the use of the TLS capabilities of supported Web servers to secure communications between the Siebel Web Client and the Web server. For information on configuring Siebel Business Applications to specify whether or not URLs must use TLS over HTTP (HTTPS protocol) to access views in a Siebel application, see About the Siebel Web Client and Using HTTPS.
Siebel Mobile Web Client. This client is designed for local data access, without having to be connected to a server. Periodically, the client must access the Siebel Remote Server using a modem, WAN, LAN or other network to synchronize data. You can use SISNAPI with TLS encryption for Mobile Web Client synchronization.
For information on setting encryption for transmissions between the Mobile Web Client and Siebel Remote Server, see Configuring Encryption for Mobile Web Client Synchronization. See also Siebel Remote and Replication Manager Administration Guide.
Siebel Developer Web Client. This client connects directly to the Siebel database for all data access. It does not store any Siebel data locally. With the exception of the database, all layers of the Siebel Business Applications architecture reside on the user’s personal computer.
The encryption technologies available to encrypt communications between the Siebel Developer Web Client and the Siebel database depends on the encryption methods supported by your RDBMS vendor. For information on how to configure communications encryption between the Siebel Developer Web Client and the Siebel database, contact your third-party RDBMS vendor.
About Session Cookies and Web Clients
The Application Object Manager in the Siebel Server communicates with the Siebel Web Client through the Web server using TCP/IP protocol. An independent session is established to serve incoming connection requests from each client. Siebel Business Applications use session cookies to track the session state. These session cookies persist only within the browser session and are deleted when the browser exits or the user logs off. A session cookie attaches requests and logoff operations to the user session that started at the login page.
Instead of storing the session ID in clear text in the client’s browser, Siebel Business Applications create an encrypted session ID and attach an encryption key index to the encrypted session ID. In Siebel Remote, the encryption algorithm and key exchange are the same as for session-based components.
Configuring Encryption for Mobile Web Client Synchronization
This topic describes how to enable encryption for Siebel Mobile Web Client synchronization. During this synchronization, DX files are transferred between the Siebel Server and Mobile Web Clients. DX files use messages to transfer information between the Siebel Server and Mobile Web Clients.
This task is a step in Process of Configuring Secure Communications.
The Siebel Mobile Web Client reads configuration parameters in the Siebel application configuration file (for example siebel.cfg, used by Siebel Sales) to determine the type of encryption to use during synchronization. Encryption options are defined as one of the elements in the DockConnString parameter.
For information about authentication for Siebel Mobile Web Client and Siebel Remote, see About Authentication for Mobile Web Client Synchronization. For general information on configuring encryption for Web clients, see About Configuring Encryption for Web Clients. For information about other security issues for Siebel Mobile Web Client, including encrypting the local database, see Siebel Remote and Replication Manager Administration Guide.
To enable encryption of synchronization on the Mobile Web Client
Open the Siebel application configuration file you want to edit. You can use any plain text editor to make changes to the file.
Note: When you edit configuration files, do not use a text editor that adds additional, nontext characters to the file.Configuration files for a client are stored in the client’s
bin\LANGUAGEdirectory, where LANGUAGE represents an installed language pack, such as ENU for U.S. English.When synchronization is performed within an application (using File, Synchronize, and then Database), configuration is read from the configuration file associated with the application, for example, siebel.cfg for Siebel Sales. For more information about working with Siebel application configuration files, see Siebel System Administration Guide.
Locate the DockConnString parameter in the [Local] section of the file.
This parameter specifies the name of the Siebel Server used to synchronize with the client. It has the following format:
siebel_server_name:sync_port_#:service:encryption
The encryption element in the DockConnString parameter indicates the type of encryption used during synchronization. Examples of a
DockConnStringparameter value follow:If using TCP-IP, the format is:
APPSRV:40400.If using TLS, the format is:
APPSRV:40400:TLS.
Save your changes and exit the file.
For information about editing configuration files for Siebel Remote and Mobile Web Clients, see Siebel Remote and Replication Manager Administration Guide and Siebel System Administration Guide.
About Data Encryption
You can encrypt sensitive data in the Siebel database using AES encryption. It is recommended that you implement AES encryption for increased data security.
See the following topics for information about data encryption:
You configure encryption using Siebel Tools. For details, see Configuring Encryption and Search on Encrypted Data.
How Data Encryption Works
When encryption is enabled for a column in a database table, unencrypted data from all the fields in this column is sent through the AES Encryptor. The encryptor encrypts the data using an encryption key stored in the key file.
After the data is encrypted, it is sent back to the database. When a user accesses this data, the encrypted data is sent through the encryptor again to be decrypted. The data is decrypted using the same encryption key from the key file that was used for encryption. The decrypted data is then sent to the business component field to be displayed in the application. For information on configuring encryption for a database column, see Configuring Encryption and Search on Encrypted Data.
The key file stores a number of encryption keys that encrypt and decrypt data. The key file is named keyfile.bin and is located in the SIEBSRVR_ROOT/admin directory of each Siebel Server. Additional encryption keys can be added to the key file. For security, the keyfile.bin file is itself encrypted with the key file password. For information on using the Key Database Manager utility to add encryption keys and to change the key file password, see Managing the Key File Using the Key Database Manager.
Requirements for Data Encryption
This topic outlines the restrictions and requirements to bear in mind when encrypting data.
The following requirements exist for data encryption:
Because encryption and decryption have performance implications, encrypt only column data that is truly sensitive, such as credit card numbers and social security numbers.
Siebel Assignment Manager does not decrypt data before making assignments. Assignment rules must take this limitation into consideration.
When creating a link object to define a one-to-many relationship between a master business component and a detail business component, the source and destination fields specified in the link object definition must not be encrypted fields. If encrypted fields are specified, then the Siebel application cannot create the association between the two business components. For detailed information on configuring links, see Configuring Siebel Business Applications.
Data that is moved into or out of the Siebel database using Siebel EIM is not encrypted or decrypted by EIM.
For additional information on encrypting EIM data after it is imported into an encrypted column, see Running the Encryption Upgrade Utility.
Encrypted data is retrieved, decrypted, and displayed from the fields in the encrypted column when records are selected. Users can perform exact-match queries on the unencrypted values for these fields if you create a hash column to store the hash values. For information, see Configuring Encryption and Search on Encrypted Data.
You can only apply AES encryption to data in database columns that are at least 32 bytes long. You cannot encrypt database columns of type VarChar that are less than 30 bytes long.
Encrypted data requires more storage space in the database than unencrypted data. You must specify appropriate data length for the affected columns. Use the following formulae when you allocate storage space for encrypted data:
For ASCII characters, the column size must be: (number of characters * [multiplied by] 2) + [plus] 10.
For non-English characters, the column size must be: (number of characters * [multiplied by] 4) + [plus] 10.
If you create a Hash Column (to enable search on encrypted data), then specify VarChar as the physical type of the column. The column size must be at least 30 characters; this is a requirement for use of the SHA-1 algorithm.
Field-level AES encryption is not supported for Developer Web Clients.
Encryption is not supported for List of Values (LOV) columns or multilingual LOV (MLOV) columns.
Encryption is not supported for join columns or foreign key columns.
Encryption for a Mobile Web Client.
Rather than encrypt data using AES encryption, the local database is encrypted. For information about encrypting the local database, see Siebel Remote and Replication Manager Administration Guide. For information about configuring encryption when the Mobile Web Client's local database is synchronized, see Configuring Encryption for Mobile Web Client Synchronization.
Encrypted Database Columns
Siebel Business Applications provide a number of database columns that are encrypted by default. The following information lists the database table columns encrypted by default in the Siebel database. For information on how to encrypt a database column, see Configuring Encryption and Search on Encrypted Data.
Table Encrypted Database Table Columns
Table |
Table Column |
|---|---|
S_AGREE_TERMS |
CC_NUMBER |
S_CM_CNCTR_PARM |
ENCRYPTED_VALUE |
S_CONTACT_FNX |
YL_PASSWD |
S_DOC_ORDER |
CC_NUMBER |
CCV_NUMBER |
|
S_INV_PROF |
CC_NUMBER |
CCV_NUMBER |
|
S_ORDER |
CC_NUMBER |
S_PTY_PAY_PRFL |
PAY_ACCNT_NUM |
VERIFICATION_NUM |
|
S_SMQ_ADDR |
SECURITY_TOKEN |
S_SRC_PAYMENT |
CC_NUM |
S_SSO_SYS_USER |
SSO_PASSWORD |
S_USER |
CHALLENGE_ANSWER |
CHALLENGE_QUESTION |
|
T_DETAIL |
ENCRPTD_COL |
The CC_NUMBER and CC_NUM columns listed in the table are used to store credit card number data. The Payment Card Industry (PCI) Data Security Standard (DSS) is a set of standards designed to enhance the security of credit card data in organizations that process such data. It is contrary to the PCI standards to store credit card numbers in a database. The CC_NUMBER and CC_NUM columns are provided for backwards-compatibility purposes only and might be removed in a future release.
Upgrade Issues for Data Encryption
This topic describes data encryption issues to consider when upgrading from a previous release of Siebel Business Applications to a Siebel 8.x release.
Application developers enable data encryption by encrypting columns in database tables. All fields in the encrypted columns are encrypted.
When you upgrade from an earlier release to the current release, the upgrade process automatically migrates business component field user properties to database table column properties so that all fields in the encrypted column are encrypted.
Configuring Encryption and Search on Encrypted Data
This topic describes how to use Siebel Tools to enable encryption for a column in a database table and to enable search on the encrypted column.
You encrypt a column and its data by specifying values for certain parameters of the column in the database table. You can also enable search on the encrypted data by creating an additional column (hash column) that stores the result of applying the SHA-1 algorithm to the plain text value of the encrypted data. Search can be case-sensitive or case-insensitive depending on how you configure search.
The following procedure describes how to encrypt data and, optionally, how to enable search on this data. Before carrying out the procedure, note the following points:
The encrypted column, hash column, and the column that stores the index number to the key file must come from the same database table.
You cannot encrypt a column that has a denormalized column, because this feature is not supported.
For example, column NAME of account table S_ORG_EXT has a denormalized column in: S_ACCNT_POSTN.ACCOUNT_NAME.
The encrypted column and the hash column must be of type String (VARCHAR), while the column that stores the index number to the key file must be of type Integer.
For more information on requirements for data encryption, see Requirements for Data Encryption.
To encrypt a column and enable search on the encrypted column in a database table
Start Siebel Tools.
Select the column in the database table that contains the data you want to encrypt.
Add values to the following parameters of the column you selected in the previous step:
Computation Expression. Specify the algorithm to encrypt data in the column as follows:
Siebel Encrypt.AES[ColumnName])For information on the Siebel AES encryption options, see About Data Encryption.
Encrypt Key Specifier. Specify the column that stores the index number to the key file.
If you want to allow search on encrypted data, then create another column with a name of your choice or with the following name format:
C_HASH_NAMEwhere
Nameis the name of the column you selected earlier in this procedure.C_HASH_NAMEstores the value that results from applying the SHA-1 algorithm to the plain text values of the column you selected earlier in this procedure.The following table shows the syntax for a number of search scenarios.
Scenario
Enter these values
Encrypt data in column C_SSI using the AES algorithm
For Computation Expression, enter:
SiebelEncrypt.AES ([C_SSI])For Encrypt Key Specifier, specify the column that stores the index key for the key file. For example:
C_KeyIndexTo enable case-sensitive search on the data that you encrypt in column C_SSI, you create an additional column C_HASH_SSI
Enter the following syntax in the field for the Computation Expression of column C_HASH_SSI:
SiebelHash.SHA1 ([C_SSI])To enable case-insensitive search on the data that you encrypt in column C_SSI, you create an additional column C_HASH_SSI
Enter the following syntax in the field for the Computation Expression of column C_HASH_SSI:
SiebelHash.SHA1CI ([C_SSI])Now do one of the following:
If the column that you have enabled for encryption does not yet contain data, then there are no further steps to perform.
If the column that you have enabled for encryption does contain data, then proceed to the next step of this procedure.
If the database column that you have enabled for encryption previously contained data, then run the Encryption Upgrade utility (encryptupg.exe) to encrypt the existing data and, if applicable, to create searchable hash values for the data.
Encrypt existing data immediately after you configure a column for encryption. You can create searchable hash values for the column at a later time if you choose.
Encrypting Columns in a Business Component
The following example procedure shows you how to create a new encrypted field/column named Password for the Account business component. Note the following requirements:
The encrypted column must be larger than the largest value you want to encrypt. That is, (4x +10) times larger where x is the longest password allowed. If you allow a 20 character password, then you need 90 characters (4*20+10) for the encrypted field/column.
For encryption to work, a minimum of two columns are required as follows:
The column that you want to encrypt (in the following example, this is PASSWORD).
A second column, which stores the Encryption Key Specifier, or the index number to the key file (PASSWORD_ENCRYPKEY_REF).
To encrypt a column in the Account BusComp
Locate the base table where data is stored for the Account BusComp.
Since Account BusComp is an S_PARTY BusComp, use the Inner Join Extension Table 1 (S_ORG_EXT).
Navigate to S_ORG_EXT and extend it to include the following new columns:
PASSWORD_ENCRYPKEY_REF. This column stores information about the key file that is used to encrypt the password field (of size VARCHAR(30)).
PASSWORD. This column stores the encrypted password and contains the following attributes:
The VARCHAR size must be (4x +10) times larger than the longest possible password.
The Computation Expression is
SiebelEncrypt.AES([PASSWORD]).The Encrypt Key Specifier is
PASSWORD_ENCRPKEY_REF.
C_HASH_PASSWORD (Optional). This column allows case-sensitive searches against the encrypted column:
The VARCHAR must be the same size as PASSWORD.
Set the Computation Expression to
SiebelHash.SHA1 ([C_PASSWORD]).
C_HASH_PASSWORD_CI (Optional). This column allows case-insensitive searches against the encrypted column:
The VARCHAR must be the same size as PASSWORD.
Set the Computation Expression to
SiebelHash.SHA1CI ([C_PASSWORD]).
Return to the Account Business Component and add new fields based on the columns created earlier in this procedure.
To partially show a field in the UI (for example, to show a partial credit card number as xxxxxxxxxxx1234), perform the following configuration steps:
Create a new field named
"Field Name - Display".Mark it as a Calculated Field with no Calculated Value attribute.
Create the following Field User Properties for the calculated field.
Encrypt Source Field. The name of the field that stores the actual encrypted field (for example: "Password").
Display Mask Char. The character to be used to mask part of the encrypted string (for example: "x").
Add the calculated field to the appropriate applets.
Managing the Key File Using the Key Database Manager
This topic describes how to run the Key Database Manager utility to add new encryption keys to the key file (keyfile.bin) and to change the key file password. The AES Encryptor uses the key in the key file to encrypt new data.
The Key Database Manager utility is named keydbmgr.exe on Microsoft Windows and keydbmgr on UNIX operating systems. It is located in the bin subdirectory of the Siebel Server directory.
To run the Key Database Manager
Shut down any server components that are configured to use encryption.
For information on shutting down server components, see Siebel System Administration Guide.
From the bin subdirectory in the Siebel Server directory, run Key Database Manager using the following syntax:
keydbmgr /u db_username /p db_password /l language /c config_file
For descriptions of the flags and parameters, see the table in this topic.
When prompted, enter the key file password:
To add a new encryption key, see Adding New Encryption Keys.
To change the key file password, see Changing the Key File Password.
To exit the utility, enter 3.
Restart any server components that were shut down in the first step of this procedure.
For information on starting server components, see Siebel System Administration Guide.
The following table lists the flags and parameters for the Key Database Manager utility.
Table Key Database Manager Flags and Parameters
Flag |
Parameter |
Description |
|---|---|---|
|
db_username |
user name for the database user |
|
db_password |
Password for the database user |
|
language |
Language type |
|
config_file |
Full path to the application configuration file (siebel.cfg for Siebel Sales). |
The following topics provide information on adding new encryption keys to the key file and changing the key file password:
Adding New Encryption Keys
You can add new encryption keys to the key file, keyfile.bin, which is located in the SIEBSRVR_ROOT/admin directory. The AES Encryptor uses the latest key in the key file to encrypt new data; existing data is decrypted using the original key that was used for encryption, even if a newer key is available. There is no limit to the number of encryption keys that you can store in the key file.
To add new encryption keys
Shut down any server components that are configured to use encryption.
From the
SIEBSRVR_ROOT/bindirectory, run Key Database Manager.For details, see Managing the Key File Using the Key Database Manager.
To add an encryption key to the key file, enter 2.
Enter some seed data to provide random data used in generating the new encryption key.
The key must be at least seven characters and no more than 255 characters in length.
Exit the utility by entering 3.
When exiting the Key Database Manager utility, monitor any error messages that are generated. If an error occurs, then you might have to restore the backup version of the key file.
Distribute the new key file by copying the file to the
SIEBSRVR_ROOT/admindirectory of all Siebel Servers in the Enterprise.Caution: When copying the keyfile.bin file to Siebel Servers, take care that the file does not become damaged. If the key file is damaged, then it is impossible to recover encrypted data without a backup key file.Restart any server components that were shut down in the first step of this procedure.
For information on starting server components, see Siebel System Administration Guide.
Changing the Key File Password
The key file is encrypted by the key file password. To prevent unauthorized access, you can change the key file password using the Key Database Manager utility. The key file is re-encrypted using a new encryption key generated from the new key file password.
Before using AES encryption for the first time, change the key file password, because all versions of the Key Database Manager utility are shipped with the same default password. The default key file password is kdbpass. Consider changing the key file password regularly to make sure the file is secured.
To change the key file password
Shut down any server components that are configured to use encryption.
Run the Key Database Manager utility from the bin subdirectory in the Siebel Server directory.
For more information, see Managing the Key File Using the Key Database Manager.
To change the key file password, enter 1.
Enter the new password.
Confirm the new password.
Exit the utility by entering 3.
When exiting the Key Database Manager utility, monitor any error messages that might be generated. If an error occurs, then you might have to restore the backup version of the key file.
Distribute the new key file to all Siebel Servers by copying the file to the admin subdirectory in the Siebel Server root directory.
Restart any server components that were shut down in the first step of this procedure.
For information on starting server components, see Siebel System Administration Guide.
Process of Upgrading Data to a Higher Encryption Level
To upgrade your data to a higher encryption level, perform the following tasks:
Verify that all requirements are met.
For information, see Requirements for Upgrading to a Higher Encryption Level.
Make sure that the input file includes every column that you want to upgrade.
For information, see Modifying the Input File.
Run the Key Database Manager utility to change the password or add a new key to the database.
For information, see Managing the Key File Using the Key Database Manager.
Upgrade the data to a higher level of encryption.
For information, see Running the Encryption Upgrade Utility.
Requirements for Upgrading to a Higher Encryption Level
This topic lists the tasks you must complete before you upgrade your data to a higher encryption level.
This task is a step in Process of Upgrading Data to a Higher Encryption Level.
To upgrade to a higher encryption level, the following requirements must be fulfilled:
The Siebel Gateway and Siebel Server are installed.
The Siebel repository has been upgraded to the schema for the current release, so that a new column has been created to store the key index for the encrypted column.
If you created or customized columns to use the standard encryptor of Release 6.x or 7.0.x, for each encrypted column that you want to upgrade, you must create a new column to store the key index.
If, in releases prior to release 8.0, you customized business component fields to use the standard encryptor, then verify that you define the correct properties for the columns in the database table that holds encrypted data. For further information, see Configuring Encryption and Search on Encrypted Data.
Verify that column sizes for custom extension columns are large enough to hold the new AES values.
The key database file (keyfile.bin) must already exist. (A default key file was created in the
SIEBEL_ROOT/siebsrvr/admindirectory when you installed the Siebel Server.)If you require AES encryption, then you must upgrade the key database file to use AES encryption (192 and 256 bits). For more information, see About Siebel Encryption.
Modifying the Input File
Before upgrading to a higher encryption level, you must modify the encrypt_colums.inp input file to list every table column that you want to upgrade. The input file, encrypt_colums.inp, indicates the table and column that store the encrypted data, and the table and column that store the key index.
This task is a step in Process of Upgrading Data to a Higher Encryption Level.
The following procedure describes how to modify the input file.
To modify the encrypt_colums.inp file
Navigate to the
SIEBEL_ROOT/dbsrvr/bindirectory where the input file is located.If you want to execute the Encryption Upgrade Utility from the command line, then place this file in the
SIEBEL_ROOT/siebsrvr/bindirectory.Using a text editor, edit the input file to include every column that you want to upgrade.
The first line of the input file indicates a table name with brackets around it. On subsequent lines following the table name, list all the columns to be upgraded for that table.
Each column that stores encrypted data requires a table column to store the key index, which is specified after the column name; for example:
[TABLE_NAME] COLUMN_NAME TABLE_NAME_FOR_KEY COLUMN_NAME_FOR_KEY WHERE clause
After each table, skip a line, and continue to list the columns for subsequent tables, as shown in the following example:
[S_ORDER] CC_NUMBER S_ORDER CCNUM_ENCRPKEY_REF WHERE S.CC_NUMBER='1234567890' [S_DOC_ORDER] CC_NUMBER S_DOC_ORDER CCNUM_ENCRPKEY_REF WHERE S.CC_NUMBER='1231231231' [S_PER_PAY_PRFL] PAY_ACCNT_NUM S_PER_PAY_PRFL CCNUM_ENCRPKEY_REF WHERE S.CC_NUMBER='1231231231'
When you have added information for every table column that you want to upgrade, save the input file.
About Using the Where Clause and Flags in the Input File
On the line following the name of each column to be upgraded, you can optionally specify the WHERE clause, the N flag, and the H flag for the column:
Use the WHERE clause if you want to partition the data to encrypt. Every column name that you specify for the WHERE clause must have the letter S added to the start of the column name. If you do not want to partition data, then omit the WHERE clause, as in the following example:
[S_ORDER] CC_NUMBER S_ORDER CCNUM_ENCRPKEY_REF WHERE
If you have imported data from EIM into an encrypted column, then use the WHERE clause to specify that only the unencrypted EIM records, that is, records where the value of the key index column is NULL, are to be encrypted. For example, the following entry is for a table named S_PER_PAY_PRFL. This table contains an encrypted column, PAY_ACCNT_NUM, which has a key index column, ENCRPKEY_REF:
[S_PER_PAY_PRFL] PAY_ACCNT_NUM S_PER_PAY_PRFL CCNUM_ENCRPKEY_REF WHERE S.CCNUM_ENCRPKEY_REF IS NULL
To support upgrade of non-encrypted fields to use encryption, add the letter
Nafter the column name; for example:[S_NEW_TABLE] COLUMN_NAME S_NEW_TABLE NAME_KEY_INDEX N
If you want to enable search on the upgraded encrypted column, then add the letter
Hto the end of the column; for example:[S_NEW_TABLE] COLUMN_NAME S_NEW_TABLE NAME_KEY_INDEX H
This creates a hash column which stores the values that are returned when you apply the SHA-1 algorithm to the plain text values of the encrypted column.
If you want to enable search on an existing encrypted column, then add the following entry in the input file to create a column which stores the hash value of the plaintext in the encrypted column:
[S_TABLE_NAME] COLUMN_NAME S_TABLE_NAME COLUMN_NAME_ENCRPKEY_REF H WHERE S.ROW_ID=’123123’
For information about search on encrypted data, see Configuring Encryption and Search on Encrypted Data.
Running the Encryption Upgrade Utility
This topic describes how to run the Encryption Upgrade utility. You must run the utility if you want to perform either of the following tasks:
Encrypt data that is not encrypted
Increase the encryption level of data that is already encrypted
This task is a step in Process of Upgrading Data to a Higher Encryption Level.
To run the encryption upgrade utility
Verify that the input file encrypt_colums.inp includes all the columns that you want to upgrade. If necessary, review Modifying the Input File.
Run encryptupg.exe by navigating to
SIEBEL_ROOT\siebsrvr\binand entering the following command:encryptupg.exe /f FromEncrytionStrength /t ToEncryptionStrength /j InputFileName /l Language /u UserName /p Password /c ConfigurationFile /L LogFile
where:
FromEncrytionStrengthis the encryption strength that you want to upgrade from. The following table describes valid parameters to enter in this command.Parameter
Description
NONEUnencrypted data.
STANDData encrypted by the Siebel Standard Encryptor. This type of encryption is no longer supported.
Caution: When you run the Encryption Upgrade utility on unencrypted data and specify the NONE parameter, the utility will encrypt the data. Be careful that you do not run the utility in this mode on the same data twice. If you do, then you will encrypt data that is already encrypted, leading to a permanent loss of data.ToEncryptionStrengthis the encryption strength that you want to upgrade to. The recommended value to enter for this parameter is AES.InputFileNameis the filename of your input file (the default isencrypt_columns.inp).Languageis the language code, for example, to specify U.S. English, enterENU.UserNameis the user name for the database.Passwordis the password for the database.ConfigurationFileis the application configuration file where you specify the data source for the Encryption Upgrade utility to retrieve data from.LogFileis the log file that the Encryption Upgrade utility writes to; the default file isencryptupg.log.
After the upgrade is complete, make sure that the encrypted database columns specify the value for the encryption method used in the Computation Expression parameter. For more information, see Configuring Encryption and Search on Encrypted Data.
Update the repository and deliver the updates.
About Siebel Encryption
Siebel encryption is installed during Siebel Enterprise and Siebel Web Server installations. Siebel encryption provides the following:
AES encryption (192 and 256 bits), using AES Encryptor
The following files for AES 192-bit or 256-bit data encryption.
File |
Purpose |
|---|---|
sslcrsa256.dll (Windows) libsslcrs |
Provides AES 192-bit or 256-bit data encryption. |
sslcnapi128.dll (Windows) sslcnapi128.so (UNIX) |
Supports 2048-bit or 4096-bit data encryption. |
AES encryption for data is provided as a Siebel business service and is configured using Siebel Tools. For more information, see Configuring Encryption and Search on Encrypted Data.
Reencrypting Password Parameters in Siebel Gateway Registry
This topic provides information on how to reencrypt parameters that are encrypted in the Siebel Gateway registry after you have increased the level of encryption you use with Siebel Business Applications.
Masked parameters are parameters that have their values encrypted. In the Siebel Gateway registry, parameters that specify password values are masked when they are written to the registry. Siebel uses strong encryption by default as of Innovation Pack 2017, but if you are upgrading from a prior release, the upgrade process upgrades data automatically to a higher encryption level but it does not upgrade the masked parameters to the higher encryption level. While existing passwords will continue to work with the higher encryption level, it is recommended that you reencrypt existing passwords, as described in the following procedure, so that they use the higher encryption level as well.
The table in this topic lists the parameters that are encrypted in the Siebel Gateway registry that must be reencrypted when you increase the encryption level. Most, but not all, of the masked parameters are Siebel Server parameters that can be changed using the Server Manager program. The following procedure describes how to reset encrypted parameters to use a new encryption level using Server Manager.
To reset encrypted parameters to use a new encryption level using Server Manager
Log in to the Server Manager command-line interface (srvrmgr program). For more information on how to start and use the srvrmgr program, see Siebel System Administration Guide.
Change each of the masked parameters so that it uses the increased encryption level; see the table in this topic for a list of the masked parameters.
For example, enter the following command to reset the Password parameter at the enterprise level:
change ent param Password=NewPassword
The following table lists the parameters that you must reencrypt if you increase the encryption level and indicates how you can reencrypt each parameter.
Table Encrypted Parameters
Parameter |
Description |
How to Reencrypt the Parameter |
|---|---|---|
Application Password |
This parameter is defined for named subsystems of type InfraSecAdpt_LDAP [the default name is LDAPSecAdpt]. This parameter is set if LDAP security adapter authentication is used. |
Siebel Web Clients can use the Server Manager command. Siebel Mobile Web Clients or Developer Web Clients must edit the appropriate application configuration file. |
CRC Checksum CustomSecAdpt_CRC |
This parameter is defined for named subsystems of type InfraSecAdpt_DB, InfraSecAdpt_LDAP, or InfraSecAdpt_Custom. This parameter specifies the checksum validation value for the security adapter DLL file and is set for LDAP, database, and custom security adapters. For further information on checksum validation, see Configuring Checksum Validation.
Caution: Do not reset or change the value of the DBSecAdpt_CRC parameter. Changing the value of the CRC parameter for the database security adapter can disrupt the correct functioning of your Siebel application.
|
Siebel Web Clients can use the Server Manager command. Siebel Mobile Web Clients or Developer Web Clients must edit the appropriate application configuration file. |
ClientDBAPwd |
This parameter is specified for the Database Extract server component. |
Use the Server Manager command. |
DSPassword |
This parameter is defined for named subsystems of type InfraDataSource (it can be set for the ServerDataSrc named subsystem, or another data source). It is specified for database security adapter authentication. |
Siebel Web Clients can use the Server Manager command. Siebel Mobile Web Clients or Developer Web Clients must edit the appropriate application configuration file. |
DSPrivUserPass PrivUserPass |
These parameters are specified for the Generate Triggers Siebel Server component. |
Use the Server Manager command. |
DbaPwd NewDbaPwd |
These parameters are specified for the Generate New Database Siebel Server component used with Siebel Remote. |
Use the Server Manager command. For information on changing these parameters, see Siebel Remote and Replication Manager Administration Guide. |
ExtDBPassword |
This parameter provides credentials for the database specified in the external database subsystem. |
Use the Server Manager command. |
Private Key File Password |
The key file stores the encryption keys that encrypt and decrypt data. The file is encrypted with the private key file password. |
Using the Key Database Manager utility. For further information, see Changing the Key File Password. You can also change the parameter in the Siebel Application Interface profile. |
MailPassword |
This parameter is set for the email account that Siebel Email Response uses to connect to the SMTP/POP3 or SMTP/IMAP email servers. |
Use the Server Manager command. For information on this parameter, see the topics on assigning parameter overrides for a communications profile in Siebel Email Administration Guide. |
Password |
This parameter, set at the Siebel Enterprise level, is the password for the system user (for example, SIEBADMIN) specified by the Username parameter. It is recommended that you do not change the value for this parameter when you reencrypt it. |
Use the Server Manager command. |
TableOwnPass |
This parameter specifies the password for the Database Table Owner (DBO) account, which is used to modify the Siebel database tables. |
Siebel Web Clients can use the Server Manager command. Siebel Developer Web Clients must edit the appropriate application configuration file. Change the parameter in the Siebel database. See Changing the Table Owner Password for instructions. |
Trust Token CustomSecAdpt_TrustToken |
These parameters apply in a Web SSO environment only, and are defined for named subsystems of type InfraSecAdpt_LDAP and InfraSecAdpt_Custom. These parameters are also specified for the Siebel Application Interface; the setting must be the same on both the Siebel Application Interface and the security adapter. |
Siebel Web Clients can use the Server Manager command. Siebel Mobile Web Clients or Developer Web Clients must edit the appropriate application configuration file. Edit the Siebel Application Interface profile. |
Security Considerations for Unicode Support
Siebel Business Applications support Unicode. For comprehensive Unicode compliance, consider the following encryption and authentication issues.
Using Non-ASCII Characters in a Unicode Environment
For database authentication, the user ID and password must use characters that are supported by the Siebel database.
Login problems might occur if you log into a Unicode Siebel site, then use Web Single Sign-On to access a third-party Web page that does not support Unicode. Make sure all applications accessible from Web SSO are Unicode-compliant.
Logging In to a Siebel Application
Make sure that the characters used in the login form are supported by the Siebel database.
Encrypted Data
Siebel Business Applications provide AES encryption to encrypt data for sensitive information such as credit card numbers. For encryption with Unicode, you must use AES encryption. For more information, see About Data Encryption.
About Encoding UI Values
You can use the control user property Encode to encode (or not encode) values in the UI as follows:
Set the control user property Encode to False to skip or ignore HTML encoding for control values.
All control values that come from trusted sources, set Encode to False by default.
Set the control user property Encode to True to encode all control values.
For customized or newly introduced controls, all control values are encoded if Encode is set to True. True is the default value for Encode.
Siebel distinguishes the source for the calculated field value by taking the value from one of the following:
The Business Component fields.
Field values are user-entered, un-trusted, and are not provided to the browser for execution to avoid cross site scripting flaws.
The hard coded value, provided in the Siebel repository.
Hard coded values are from a trusted source and do not require encoding.