| User Data Repository Diameter User's Guide Release 12.4 E92984-01 |
|
 Previous |
 Next |
To facilitate potential candidates, the Peer Node configuration element called Topology Hiding Status must be set to Enabled on any Peer Node that is associated with at least one Untrusted Network.
Figure 10-5 TH Network Deployment in an Interworking Network
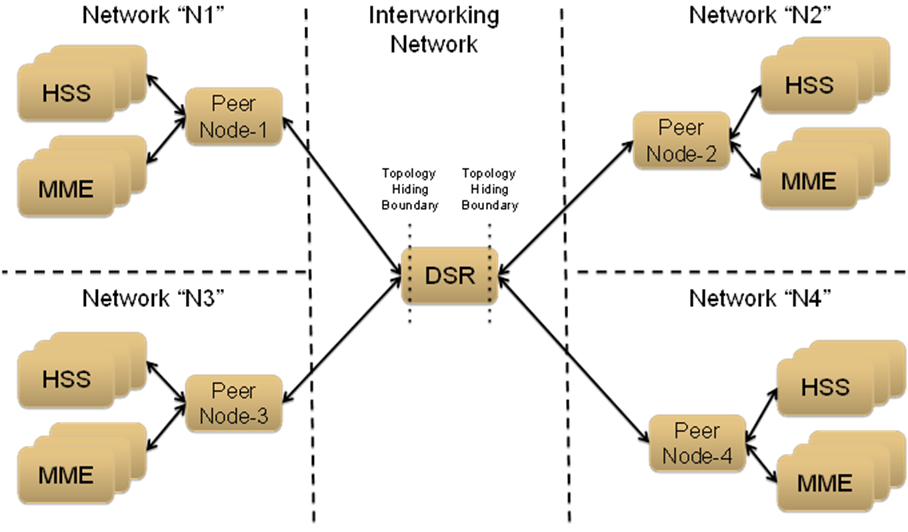
For the sake of discussion, assume that all of the networks are Protected Networks and the Protected Networks and Trusted Network Lists shown in Table 10-9 and Table 10-10 are configured:
Table 10-9 Example Protected Networks Configuration
| Protected Network Name | Protected Network Realm Name | Trusted Network List Name |
|---|---|---|
| N1 | n1.com | Trusted Networks-1 |
| N2 | n2.com | Trusted Networks-2 |
| N3 | n3.com | Trusted Networks-3 |
| N4 | n4.com | Trusted Networks-4 |
Table 10-10 Example Trusted Network Lists Configuration
| Protected Network Name | Network Realm List |
|---|---|
| Trusted Networks-1 | n3.com |
| Trusted Networks-2 | n3.com n4.com |
| Trusted Networks-3 | n2.com |
| Trusted Networks-4 | n1.com n2.com n3.com |
Based on the example Protected Networks and Trusted Network Lists, the trust relationship matrix among the four networks in this example configuration is shown in Table 10-11.
Table 10-11 Network Trust Relationship Matrix
| Protected Network | Relationship with Peer Network | |||
|---|---|---|---|---|
| N1 | N2 | N3 | N4 | |
| N1 | Trusted | Not Trusted | Trusted | Not Trusted |
| N2 | N2 | Not Trusted | Trusted | Trusted |
| N3 | Not Trusted | Trusted | Trusted | Not Trusted |
| N4 | Trusted | Trusted | Trusted | Trusted |
| Is this network Untrusted by at least one other network? | Yes | Yes | No | Yes |
Based on the Network Trust Relationship Matrix, the Peer Node element settings for the network shown in Table 10-12 would be used:
Table 10-12 Example Topology Hiding Status Settings
| Peer Node | Topology Hiding Status Element Setting |
|---|---|
| Peer Node-1 | Enabled |
| Peer Node-2 | Enabled |
| Peer Node-3 | Disabled |
| Peer Node-4 | Enabled |
With the information in Table 10-5, the TH type-independent criteria for determining whether a message is a potential candidate for Topology Hiding/Restoral are defined in Table 10-13.
Table 10-13 General Criteria for Determining Whether a Message is a TH Candidate
| TH Trigger | Message | Message Path | General Topology Hiding/Restoral Candidate Criteria |
|---|---|---|---|
| RTH | Request | Protected-to-Untrusted | Egress Peer Node Topology Hiding Status is Enabled, AND Origin-Realm is a Protected Network X, AND Destination-Realm is an Untrusted Network to Protected Network X |
| RTR | Request | Untrusted-to-Protected | Ingress Peer Node Topology Hiding Status is Enabled, AND Destination-Realm is a Protected Network X, AND Origin-Realm is an Untrusted Network to Protected Network X |
| ATH | Answer | Protected-to-Untrusted | Egress Peer Node Topology Hiding Status is Enabled, AND Origin-Realm is a Protected Network X, AND Realm of the Diameter Node that originated the transaction is an Untrusted Network to Protected Network X TH Trigger point ATH occurs after the Diameter Routing Function deallocates the PTR for the transaction. Therefore, the Origin-Realm value that was received in the Request message must be stored in the Application-Data stack event just before deallocating the PTR in order for the Diameter Routing Function to make an evaluation at ATH of whether the Answer response is being sent to an Untrusted Network. |
| ATR | Answer | Untrusted-to-Protected | PTR contains one or more indications that topology information restoral is required For Untrusted-to-Protected Answer messages, any information that was hidden in the egress Request is a candidate for restoral regardless of which "Network" sends the Answer message response. Topology information restoral at ATR is always performed regardless of the egress Peer Node's Topology Hiding Status if Topology Hiding was performed on the egress Request message for this Diameter transaction. |
If the TH Trigger Point criteria defined in Table 10-13 are met, then the Diameter Routing Function must determine which TH types are enabled for the associated Protected Network. Each TH type might have additional criteria that must be met in order to determine whether topology-related information hiding or restoral is required.
The Protected Networks configuration component defines which TH types are enabled for the Protected Network. If a Configuration Set for the TH type is assigned to the Protected Network, then that TH type is enabled for that Protected Network and the rules for that TH type are applied. The Path, S6a/S6d HSS, MME/SGSN, S0 PCRF, and S9 AF/pCSCF TH types are supported. An example Protected Network component for the use case network defined in this section could look like the configuration in Table 10-14:
Table 10-14 Protected Network Configuration Example
| Protected Network Name | Protected Network Realm Name | Trusted Network List Name | Path TH | S6a/S6d HSS TH | MME/SGSN TH | S9 PCRF TH | S9 AF/pCSCF TH |
|---|---|---|---|---|---|---|---|
| N1 | n1.com | Trusted Networks-1 | Path Config Set-1 | S6a/S6d HSS Config Set-1 | MME/SGSN Config Set-1 | NULL | NULL |
| N2 | n2.com | Trusted Networks-2 | Path Config Set-2 | S6a/S6d HSS Config Set-1 | MME/SGSN Config Set-1 | NULL | NULL |
| N3 | n3.com | Trusted Networks-3 | Path Config Set-3 | NULL | NULL | S9 PCRF Config Set-1 | S9 AF/pCSCF onfig Set-1 |
| N4 | n4.com | Trusted Networks-4 | Path Config Set-4 | NULL | NULL | S9 PCRF Config Set-2 | S9 AF/pCSCF onfig Set-2 |
In the example, if a message associated with Protected Network N3 is a candidate for topology hiding/restoral, then the Diameter Routing Function invokes only the Path Topology Hiding Configuration Set rules for that message.
The TH type-specific Hiding/Restoral rules are defined in Topology Hiding Types.