S9 PCRF Topology Hiding is concerned with hiding the identities of a Protected Network's PCRFs, as well as the number of PCRFs in the network, when it exchanges messages with Untrusted Networks. A PCRF's identity is embedded in the Origin-Host and Session-ID AVPs sent in Request messages and the Origin-Host AVP sent in Answer messages. This capability (and S9 AF/pCSCF Topology Hiding) is associated with the Diameter S9 and Rx application message set.
S9 PCRF topology hiding is concerned with all S9 messages and Rx messages when AF/pCSCF is deployed in client/
server mode. If the PCRF is deployed in client/
server mode for Rx messages, then S9 AF/pCSCF TH Configuration Set should not be enable for the protected network.
Note:
All S9 messages initiated by hPCRF or vPCRF have S9 PCRF Topology Hiding applied (if enabled). If S9 AF/pCSCF TH is not enabled, then all Rx messages initiated by hPCRF or vPCRF have S9 PCRF Topology Hiding applied (if enabled). If S9 AF/pCSCF TH is enabled (i.e., if vPCRF is proxying AF/pCSCF messages to hPCRF), then only AAA/STA/RAR and ASR Rx messages have PCRF TH applied.
PCRF identities are hidden by replacing the actual host name portion of the Origin-Host and Session-ID AVPs with a PCRF pseudo-host name. The Origin-Hose and Session-ID AVPs may have different PCRF host names. A unique pseudo- name must be created for each PCRF in a Protected Network. When the vPCRF initiates a transaction to the hPCRF, the hPCRF saves the vPCRF's identity for use in subsequent hPCRF-to-vPCRF transactions. This vPCRF pseudo-host name must not only be unique, but the DEA must be able to convert the vPCRF's pseudo-name to an actual vPCRF host name for these subsequent hPCRF to vPCRF transactions.
To hide the number of PCRFs in a network, each PCRF is assigned either a random or fixed number of pseudo-host names (the maximum is defined by an S9 PCRF TH Configuration Set attribute called Maximum Pseudo-Host Names per PCRF). The GUI creates the randomized PCRF pseudo-host names and assign them to actual pseudo-host names to be used by DRL. The TH Host Names allows DRL to map a Protected-PCRF actual-host name to a set of PCRF pseudo-host names as well as map a PCRF pseudo-host named received from an Untrusted Network to a Protected-PCRF actual-host name.
Protected-vPCRF to Untrusted-hPCRF Transactions
When vPCRF is in a Protected Network, S9 Diameter sessions are initiated by vPCRF in a Protected Network on behalf of an inbound roamer to request PCC or QoS rules to the hPCRF.
When AF/pCSCF and PCRF are in a Protected Network and AF/pCSCF uses vPCRF in client/server mode to communicate Rx messages initiated by vAF/pCSCF to hPCRF in an Untrusted network, then S9 PCRF TH is used to hide PCRF host names to an Untrusted Network.
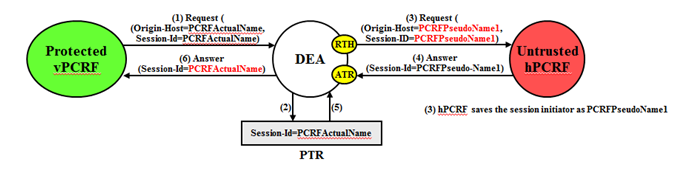
For Protected-vPCRF to Untrusted-hPCRF S9 Diameter transactions, S9 PCRF TH is concerned with the following topology information hiding and restoral issues:
- The AVPs containing a PCRF's actual-host name in Request messages must be hidden with one of the pseudo-host names assigned to the PCRF at TH trigger point RTH
- The Untrusted network's PCRF (hPCRF in this case) saves the subscriber's location using the Origin-Host AVP contents containing a pseudo-host name. This has the following impact:
- In subsequent hPCRF-vPCRF transactions(e.g RAR/ASR), the vPCRF may be addressed by one of its pseudo-host names requiring a pseudo-to-actual name restoral
- All vPCRF-to-hPCRF transactions associated with a particular session must use the same vPCRF pseudo-host name. The Session is identified by Session-ID AVP, a mandatory AVP in all S9/Rx messages.
Note:
Although the Origin-Host and Session-ID AVPs both have actual PCRF host names, they may be different. Because S9/Rx is a session based application , actual PCRF host names must be restored in subsequent hPCRF-vPCRF transactions. Hence both Origin-Host and Session-ID AVPs must be selected from Actual Host Names in S9 PCRF TH.
- The hPCRF sends an Answer response to the transaction with the Session-ID received in the Request (also containing a PCRF pseudo-host name). Because the Session-ID value returned in the Answer must match the Request, the PCRF pseudo-host name in the Session-ID AVP must be replaced with its corresponding value received in the Request message. This value is restored at TH trigger point ATR. This requires saving the host name portion of the Session-ID AVP value in the PTR. This host name restoral procedure is not required for Answers initiated by internal nodes as these Answer responses are based upon the original Request message content
An example of a Protected-vPCRF to Untrusted-hPCRF Diameter transaction is shown in Figure 10-17.
To ensure all S9/Rx messages for the same session are modified using the same pseudo-name, the Session-ID AVP can be used as a key to select a Pseudo Host Name for an Actual Host Name.
Untrusted-hPCRF to Protected-vPCRF Transactions
For Protected-vPCRF to Untrusted-hPCRF S9/Rx transactions, PCRF topology hiding is only required on Request messages which meet the following criteria:
- The message was a candidate for topology hiding as defined by topology trigger point RTH and
- S9 PCRF TH is enabled for the Protected network (S9 PCRF TH Configuration Set is assigned to the Protected Network) and
- The Request message is a member of the S9 message and was initiated by a PCRF or
- The Request message is a member of the Rx message set and was initiated by a PCRF and S9 AF/pCSCF TH is not enabled and
- The Origin-Host and/or Session-ID AVPs in the Request contain an actual PCRF host name assigned to the Protected Network via the S9 PCRF Configuration Set.
For Protected-vPCRF to Untrusted-hPCRF transactions, PCRF topology information restoral is only performed on Answer messages which meet the following criteria:
- At topology trigger point ATR, the PCRF TH ATR flag in the PTR associated with the Answer message is set to Enabled.
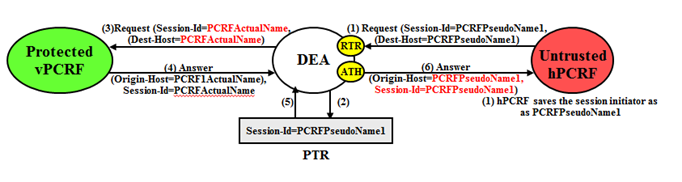
When an Untrusted-hPCRF initiates a transaction to a Protected-vPCRF, it is most likely addressed to one of the vPCRF pseduo-host names that the hPCRF saved in a previous vPCRF-to-hPCRF transaction for which S9 PCRF TH was applied. For Untrusted-hPCRF to Protected-vPCRF Diameter transactions (RAR, ASR, and so on), S9 PCRF TG is concerned with the following topology information hiding and restoral issues:
- The Destination-Host AVP contains a vPCRF pseudo-host name. This pseudo-host name must be replaced with the vPCRF's actual-host name at TH trigger point RTR. Pseudo-to-actual host name mapping is performed using the internal TH Host Names. It's perfectly acceptable that an Untrusted-hPCRF to Protected-vPCRF Request message does not contain a PCRF pseudo-host name. If the Destination-Host AVP value does not match an entry in the TH Pseudo-Host Name, then no host name conversion is required and the Request message is routed as normal. Destination-Host name conversion is performed to prevent the following problems:
- Certain vPCRFs do not accept messages that do not contain its actual host name
- Diameter routing problems associated with pseudo-host names. For example, DRL Implicit Routing currently only works with actual host names (for example, the FQDN assigned to the Peer Node and used for the Capabilities Exchange procedure [CER/CEA]).
- The host portion of Session-ID AVP containing a PCRF pseudo-host name must be replaced back with vPCRF's actual host name at TH trigger point RTR. Pseudo-to-actual host name mapping is performed using the internal TH Host Names.
- An Origin-Host AVP containing a vPCRF's actual-host name in the Answer response from the Protected-vPCRF must be hidden with one of the pseudo-host names assigned to that PCRF. This procedure is done at TH trigger point ATH.
- Session-ID AVP containing a vPCRF's actual-host name in the Answer response from the Protected-vPCRF must be hidden with one of the pseudo-host names assigned to that PCRF. This is done at TH trigger point ATH.
An example of an Untrusted-hPCRF to Protected-vPCRF Diameter transaction is shown in Figure 10-18.
For Untrusted-hPCRF to Protected-vPCRF transactions, S9 PCRF TH is only invoked on Request messages at topology trigger point RTR which meet the following criteria:
- The message was a candidate for topology hiding as defined by topology trigger point RTR and
- S9 PCRF TH is enabled for the Protected Network (S9 PCRF TH Configuration Set is assigned to the Protected Network) and
- The Request message is a member of the S9 message set and was initiated by a PCRF or
- The Request message is a member of Rx message set and was initiated by a PCRF and S9 AF/pCSCF TH is not enabled and
- The Destination-Host AVP or host portion of Session-ID AVP contains a PCRF pseudo-host name that is assigned to the Protected Network as determined from the internal Pseudo-Host Name
For Untrusted-hPCRF to Protected-vPCRF transactions, S9 PCRF
HSS topology hiding is only invoked on Answer messages at topology trigger point ATH which meet the following criteria:
- Message was a candidate for topology hiding as defined by topology trigger point ATH
- S9 PCRF TH is enabled for the Protected Network (S9 PCRF TH Configuration Set is assigned to the Protected Network)
- The Answer message is a member of the S9 message set and was initiated by a PCRF or
- The Answer message is a member of Rx message set and was initiated by a PCRF and S9 AF/pCSCF TH is not enabled and
- The Origin-Host AVP or host portion of Session-ID AVP contains an actual PCRF host name that is assigned to the Protected Network via the S9 PCRF TH Configuration Set
Protected-hPCRF to Untrusted-vPCRF Transactions
When an hPCRF is in Protected Network, S9 Diameter sessions are initiated by a vPCRF in an Untrusted Network on behalf of an outbound roamer to request PCC or QoS rules to the hPCRF. hPCRF can send RAR in the session initiated by vPCRF.
When AF/pCSCF and PCRF is in an Untrusted network and AF/pCSCF uses vPCRF in client/server mode to communicate Rx messages initiated by vAF/pCSCF to hPCRF in a Protected Network, then S9 PCRF TH is used to hide PCRF host names from an Untrusted Network. hPCRF can send RAR or ASR messages in the session intiated vPCRF.
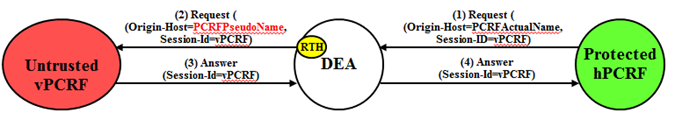
For Protected-hPCRF to Untrusted-vPCRF S9 Diameter transactions, S9 PCRF TH is concerned with the following topology information hiding and restoral issues:
- S9 Sessions are initiated from untrusted network using CCR and Rx Sessions are initiated from untrusted network using AAR. Hence the host portion of Session-ID AVP contains the host of the untrusted network, which does not need to be hidden.
- The Origin-Host AVP containing an PCRF's actual-host name in Request messages must be hidden with one of the pseudo-host names assigned to the PCRF at TH trigger point RTH.
An example of a Protected-hPCRF to Untrusted-vPCRF Diameter transaction is shown in
Figure 10-19.
To ensure all S9/Rx messages for same session are modified using same pseudo-name , Session-ID AVP can be used as key to select a Pseudo Host Name for an Actual Host Name.
For Protected-hPCRF to Untrusted-vPCRF S9/Rx transactions, PCRF topology hiding is only required on Request messages which meet the following criteria:
- The message was a candidate for topology hiding as defined by topology trigger point RTH and
- S9 PCRF TH is enabled for the Protected Network (S9 PCRF TH Configuration Set is assigned to the Protected Network) and
- The Request message is a member of the S9/Rx message set and was initiated by a PCRF and
- The Origin-Host AVP in the Request contain an actual PCRF host name assigned to the Protected Network via the S9 PCRF TH Configuration Set
Untrusted-vPCRF to Protected-hPCRF Transactions
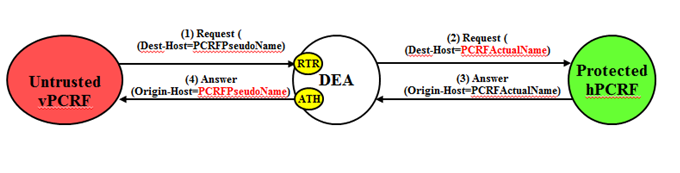
When an Untrusted-vPCRF initiates a transaction to a Protected-hPCRF, it is most likely addressed to one of the hPCRF pseudo-host names that the vPCRF saved in a previous hPCRF-to-vPCRF transaction for which PCRF TH was applied. For Untrusted-vPCRF to Protected-hPCRF Diameter transactions (CCR, AAR/STR, and so on), PCRF TH is concerned with the following topology information hiding and restoral issues:
- The Destination-Host AVP contains a PCRF pseudo-host name. This pseudo-host name must be replaced with the hPCRF's actual-host name at TH trigger point RTR. Pseudo-to-actual host name mapping is performed using the internal TH Host Names table. It's perfectly acceptable that an Untrusted-vPCRF to Protected-hPCRF Request message does not contain a PCRF pseudo-host name. If the Destination-Host AVP value does not match an Pseudo-Host Name entry in the TH Host Names, then no host name conversion is required and the Request message is routed as normal. Destination-Host name conversion is performed to prevent the following problems:
- Certain hPCRFs do not accept messages that do not contain its actual host name
- Diameter routing problems associated with pseudo-host names. For example, DRL Implicit Routing currently only works with actual host names (i.e., the FQDN assigned to the Peer Node and used for the Capabilities Exchange procedure (CER/CEA))
- An Origin-Host AVP containing an vPCRF's actual-host name in the Answer response from the Protected-hPCRF must be hidden with one of the pseudo-host names assigned to that PCRF . This is done at TH trigger point ATH.
An example of an Untrusted-vPCRF to Protected-hPCRF Diameter transaction is shown in
Figure 10-20.
For Untrusted-vPCRF to Protected-hPCRF transactions, S9 PCRF
HSS topology hiding is only invoked on Request messages at topology trigger point RTR which meet the following criteria:
- Message was a candidate for topology hiding as defined by topology trigger point RTR and
- S9 PCRF TH is enabled for the Protected Network (S9 PCRF TH Configuration Set is assigned to the Protected Network) and
- The Request message is a member of the S9 message set and was initiated by a PCRF as determined and
- The Request message is a member of Rx message set and was initiated by a PCRF and S9 AF/pCSCF TH is not enabled and
- The Destination-Host AVP contains a PCRF pseudo-host name that is assigned to the Protected Network as determined from the internal Pseudo-Host Name
For Untrusted-vPCRF to Protected-hPCRF transactions, S9 PCRF
HSS topology hiding is only invoked on Answer messages at topology trigger point ATH which meet the following criteria:
- Message was a candidate for topology hiding as defined by topology trigger point ATH
- S9 PCRF TH is enabled for the Protected Network (S9 PCRF TH Configuration Set is assigned to the Protected Network)
- The Answer message is a member of the S9 message set and was initiated by a PCRF
- The Origin-Host AVP contains an actual PCRF host name that is assigned to the Protected Network via the S9 PCRF TH Configuration Set