| User Data Repository Diameter User's Guide Release 12.4 E92984-01 |
|
 Previous |
 Next |
Path Topology Hiding can be enabled for each Protected Network by assigning a Path TH Configuration Set to the configured Protected Network.
Route-Record AVP Hostname Hiding - Request Messages
Route-Records AVPs are appended to Request messages to assist in message loop detection. When Diameter node N relays a Request message received from Diameter node –1 to Diameter node N+1, Diameter node N appends a Route-Record AVP to the Request message containing the Hostname of Diameter node –1. For Request messages that are forwarded from a Protected Network N1 to an Untrusted Network, there could be Protected Network N1 Hostnames embedded in one or more of the Route-Record AVPs.
An example of Route-Record AVP Hostname hiding for a Request message routed from a Protected Network to an Untrusted Network is shown in Figure 10-6.
Figure 10-6 Route-Record Hiding - Request Message
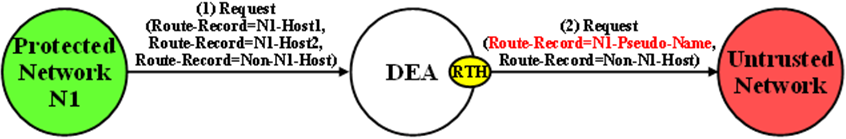
Route-Record AVP Hostname hiding is performed by replacing all of the Route-Record AVPs that meet the Route-Record AVP hiding criteria with a single Route-Record AVP that contains a single configured Pseudo Hostname. Route-Record AVP Hostname hiding occurs after the Diameter Routing Function appends any Route-Record AVPs to the Request message.
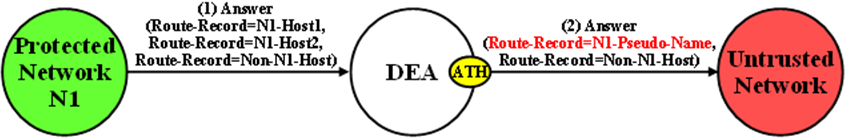
Route-Record AVP Hostname Hiding - Answer Messages
Diameter Relay and Proxy Agents are required to append a Route-Record AVP into any forwarded Request message. There are no Relay Agent or Proxy Agent requirements to perform this function for Answer messages. However, in certain Diameter specifications (such as S6a/S6d and RFC 4006), the Route-Record AVP is specified as an optional AVP in certain Answer messages (including CCA and most of the S6a/S6d Answer messages). Thus, it is probable that Answer messages initiated by a Protected Network node and forwarded to an Untrusted Network by a DEA can contain one or more Route-Record AVPs with Protected Network Hostnames. Therefore, Route-Record AVP Hostname hiding is applied to Answer messages using the same procedure that is used for Request messages.
An example of Route-Record AVP Host Name hiding for an Answer message initiated by a Protected Network to an Untrusted Network is shown in Figure 10-7.
Figure 10-7 Route-Record Hiding - Answer Message
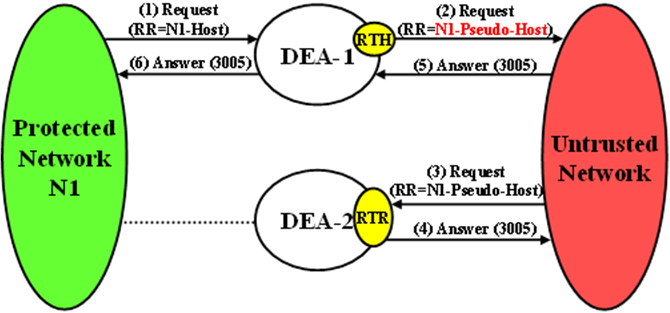
Route-Record AVP Hiding and Inter-Network Message Loop Detection
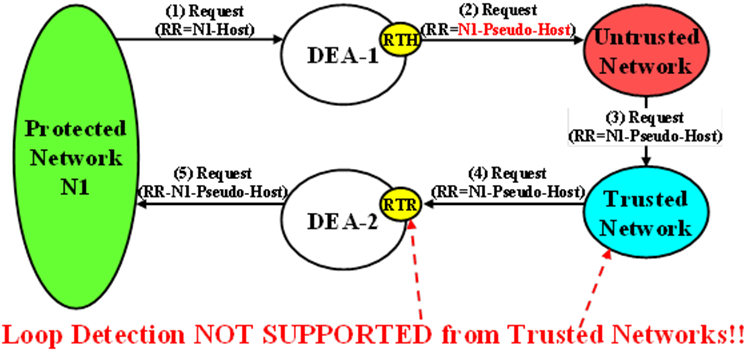
The technique of replacing one or more Route-Record AVPs with a single Route-Record AVP containing a Pseudo Hostname must not defeat the fundamental purpose of the Route-Record AVP - message loop detection. Because Route-Record Topology Hiding is considered a DEA function and is applied only to Request messages leaving a network, inter-network ingress message loop detection is needed at the inter-network boundary. For example, a Request message can egress the network from DEA-1 but loop back to the network through DEA-2 as shown in Figure 10-8. If an inter-network message loop is not detected by a DEA, the loop is not detected within the Protected Network because a DEA replaced the Route-Records for the internal nodes with a single Route-Record AVP containing a Pseudo Hostname.
Topology Hiding configuration components must be managed from the NOAM so that an identical copy of all Topology Hiding configured components is distributed to all DEAs controlled by the NOAM. This allows inter-network ingress message loop detection to be supported by any DEA.
Inter-network ingress message loop detection is supported at the RTR Trigger Point. A typical message loop path between two DEAs with Path Topology Hiding enabled is illustrated in Figure 10-8.
Figure 10-8 Multi-DEA Route-Record Message Loop Detection
It is possible but highly unlikely (as in an invalid inter-network relationship) that a Request message that leaves the Protected Network addressed to an Untrusted Network will loop back to the Protected Network through a Trusted Network, as shown in Figure 10-9. This type of message loop detection is NOT supported.
Figure 10-9 Unsupported Pseudo-Host Route-Record Loop Detection
Proxy-Host AVP Hiding and Restoral
The grouped Proxy-Info AVP allows stateless agents to add local state to a Diameter Request message with the guarantee that the same state is present in the Answer message response. The embedded Proxy-Host AVP identifies the Diameter node that appended the Proxy-Info AVP to the Request message. A Protected Network Hostname in any Proxy-Host AVP must be hidden when the AVP is forwarded to an Untrusted Network. More than one Proxy-Host AVP instance can exist in a Request message. Every instance that contains a Protected Network Hostname must be hidden with a unique Pseudo Hostname.
An example of Proxy-Host AVP Hiding for a Request message initiated by a Protected Network to an Untrusted Network is shown in Figure 10-10.
Figure 10-10 Proxy-Host Hiding
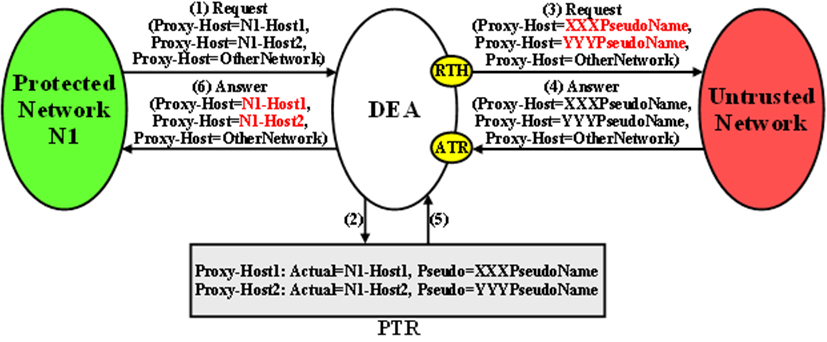
Because the Proxy-Info AVP is used by stateless agents to store local transaction state information into a Request message and retrieve that information from the Answer response, it is important that the DEA restore the original Proxy-Host AVP values (received in the original Request message) when it forwards the Answer response message. Thus, any Proxy-Host AVP value that is replaced at TH Trigger Point RTH must be saved in its respective Diameter Routing Function PTR.
When the criterion is met, Proxy-Host AVP Restoral is performed. The Diameter Routing Function replaces every Proxy-Host AVP value that matches a Proxy-Host Pseudo Hostname (stored in the PTR) with the original Hostname (also stored in the PTR).
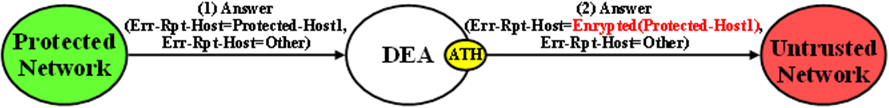
Error Reporting Host AVP Hiding
The Error-Reporting-Host AVP contains the identity of the Diameter node that set the Result-Code AVP to a value other than 2001 (Success), only if the host setting the Result-Code is different from the one encoded in the Origin-Host AVP.
From a Topology Hiding perspective, the Hostname in this AVP must be hidden if it contains a Protected Network Hostname and is being sent to an Untrusted Network.
The content of this AVP is hidden using encryption. Troubleshooters in the Protected Network must have the ability to decrypt the value. Topology Hiding uses Advanced Encryption Standard (AES), which is described in Encryption.
Although unlikely, more than one Error-Reporting-Host AVP could exist in an Answer message; each Error-Reporting-Host AVP containing a Protected Network's Hostname must be encrypted.
An example of Error-Reporting-Host AVP Hiding for an Answer message received from a Protected Network that is being forwarded to an Untrusted Network is shown in Figure 10-11.
Figure 10-11 Error-Reporting-Host AVP Hiding