1 Introducing Oracle Communications Services Gatekeeper
This chapter provides a high-level view of the Oracle Communications Services Gatekeeper product and its most important features.
Understanding Services Gatekeeper
Services Gatekeeper is an API management and governance platform that enables you to provision and monetize web resources quickly and securely using the provided APIs, or the APIs that you or your partners create. Your product can be the APIs, or you can use Services Gatekeeper to create and monetize applications or services based on these APIs. Services Gatekeeper is most useful for productizing the lightweight REST, SOAP, or other XML-based services used in today's world of web services.
Services Gatekeeper also provides a comprehensive collection of communication services (preconfigured APIs) for use with telecom networks to enhance the capability of telecom legacy networks.
You install Services Gatekeeper in one of two ways based on the needs of your implementation. The default or single-tier version of Services Gatekeeper comes preconfigured and is designed to install and deploy quickly on a single self-contained system. Single-tier Services Gatekeeper is robust enough to use as a production platform for testing and small to medium-size implementations. You can also cluster single-tier Services Gatekeeper on several systems to take advantage of high availability features. The single-tier Services Gatekeeper includes an integrated Oracle Java DB database to store information that the Services Gatekeeper GUIs and other processes use to store data. You also have the option to use your own MySQL, or Oracle Real Application Cluster (Oracle RAC) database instead of Oracle Java DB.
Single-tier Services Gatekeeper can use all the same features, APIs, applications, communication services, protocols, that multi-tier Services Gatekeeper offers.
This documentation set generally refers to both the single-tier Services Gatekeeper and multi-tier Services Gatekeeper as simply ”Services Gatekeeper.” It makes the distinction between the two when the difference is important, such as in the installation and configuration documents.
In contrast, the mult-tier version of Services Gatekeeper is designed for you to install its various components on different, dedicated hardware systems. You can install multi-tier components on a single system for testing or evaluation, but it is designed to be used on multiple systems. The multi-tier version also comes with the embedded JavaDB database, primarily for testing. Other than JavaDB, the multi-tier Services Gatekeeper expects that you use a database that is installed on its own system.
For information to help you decide which Services Gatekeeper implementation you need, see "When to use Multi-tier Services Gatekeeper".
Multi-tier Services Gatekeeper comes preconfigured to work with the Oracle Enterprise Manager cloud control product. Or you can integrate it with your own cloud management product.
Both Services Gatekeeper configurations are built using a version of Oracle WebLogic Server hardened and extended to support the specialized needs of API management with an emphasis on telecom networks. See ”About the Oracle WebLogic Platform” in Services Gatekeeper System Administrator's Guide for more information.
Understanding What Services Gatekeeper Provides
Services Gatekeeper offers these Partner Relationship Management (PRM) GUI tools to create and manage your APIs, and the partners that provide them:
-
The Services Gatekeeper Partner and API Management Portal graphical user interface (GUI) tool. You use this tool to:
-
Create and manage APIs, including selecting individual methods to expose to your partners. These elements are displayed as menu selections and input fields in Partner Portal. You also have a robust set of tools available to build, configure, manipulate, translate, and add on-the-fly functionality to your APIs and applications.
-
Create, approve, and manage the partners who create applications and view their statistics using the Services Gatekeeper Partner Portal GUI. You can authorize partners to access Partner Portal.
-
Collect partners into groups, and then apply bandwidth limits to those groups. You can change the bandwidth limits on individual APIs as necessary.
-
Create, approve, and manage the NSS operators who create interfaces that you use in APIs and applications. You can also make them available to your other partners for use in their APIs.
-
Analyze statistics about the APIs your implementation is running. The Partner and API Management Portal interfaces with Oracle Business Intelligence Enterprise Edition release 11.1.1.7.0 (OBIEE) to provide statistics that you use to track API usage, response times, and failure rates. You use these tools to monitor application usage and figure out where to make the necessary adjustments in your products.
-
-
The Services Gatekeeper Partner Portal GUI that your partners use to create and modify applications based on the APIs you make available. You must grant your partners access to the Partner Portal. Once they have access, they can quickly and easily create applications for you to use in the Partner and API Management Portal. They do so by subscribing to and using the APIs previously configured in Partner and API Management Portal and displayed in Partner Portal as menu selections and input fields. A statistics feature is also included for partners to monitor and manage their applications.
All applications created or updated in Partner Portal are instantly displayed in Partner and API Management Portal for approval by the associated network operator.
-
The Network Service Supplier Portal GUI that your network service suppliers use to make create network interfaces, and make them available to you and your partners.
-
The Oracle Communications WebLogic Administration Console GUI to configure the back end. You use the Administration Console to configure Services Gatekeeper for your hardware and for administration tasks.
-
An expandable self-contained back end to support the portals. The back end includes a single-tier deployment that can contain everything required for Services Gatekeeper on a single host system.
-
An API Management API that you can use to customize or replace the PRM Portals.
-
An interface to Oracle Business Intelligence Enterprise Edition (OBIEE) that you use to capture statistics on your API usage.
In addition to the PRM portals, Services Gatekeeper includes:
-
Built-in API management and governance.
-
Comprehensive policy, SLA, and subscriber and network resource management.
-
Multiple service facades including support for REST, SOAP, SOA, and native interfaces.
-
Extensive list of pre-built network plug-ins.
-
Multi-channel authorization and privacy management leveraging the OAuth standard.
-
An easily customizable and extensible graphical user interface.
When to Use a Communication Service Instead of an API
If you need to create an API with capabilities that the Partner and API Management Portal does not support, you can use one of the Services Gatekeeper communication services, or use the Services Gatekeeper Platform Developer's Studio to create a new communication service. You use communication services to process traffic in much the same ways that APIs do, but they are more flexible. The tradeoff is that you manage them programmatically; you cannot manage them using the Partner and API Management Portal.
You would create a communication service instead of an API if:
-
If the API requires a capability that the Partner and API Management Portal does not support. for example if it requires a protocol that the Services Gatekeeper Portals do not support.
-
If the API requires simultaneous processing of network nodes. For example is you send requests to three network nodes and want to change processing depending on which of the network nodes responds first.
Services Gatekeeper provides a robust collection of existing telecom-based communication services out of the box for you to use if your implementation requires it. See "Using Services Gatekeeper with a Traditional Telecom Network" for a list of the pre-packaged Services Gatekeeper communication services. These communication services wrap the plug-ins in various telecom protocols.
Understanding Services Gatekeeper API Management and Governance
Services Gatekeeper installation provides a cloud-ready API management implementation that uses the Partner and API Management GUIs to create, protect, manage, and monetize your APIs.
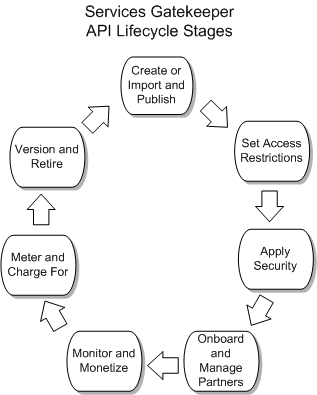
Figure 1-1 shows the Services Gatekeeper API life cycle stages, and illustrates how APIs are created, protected, managed, and monetized. These life cycle stages are explained in sections that follow.
You use the Services Gatekeeper Partner and API Management Portal shown in Figure 1-2 for most of the API management and governance tasks.
Figure 1-2 Partner and API Management Portal Example
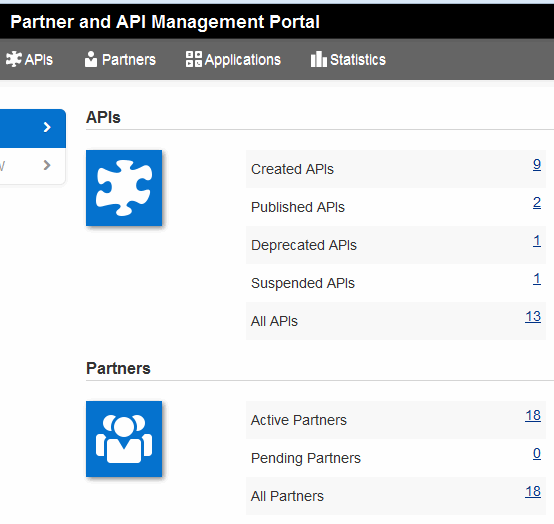
Description of ''Figure 1-2 Partner and API Management Portal Example''
Create or Import and Publish APIs
If you already have created web services, you can use the Partner and API Management Portal wizard to create APIs from those web services and publish the APIs for your partners and customers. You can create an API from an existing web service URI, a REST-based WADL file, a SOAP-based WSDL file, an existing registered network service, or one of the pre-packaged Services Gatekeeper plug-ins. See ”Developing Telephony Applications for Services Gatekeeper” in for a list of the plug-ins.
You expose the API using one of the interface combinations listed in Table 1-1.
Table 1-1 Services Gatekeeper API Interface Translation Options
| Web Service Interface (Payload Format) | Network Interface (Payload Format) |
|---|---|
|
SOAP (XML) |
SOAP (XML) |
|
SOAP (XML) |
REST (XML/JSON) |
|
REST (XML/JSON) |
REST (XML/JSON) |
|
REST (XML/JSON) |
SOAP (XML) |
Services Gatekeeper also enables you to interface with XML remote procedure calls on both the web service and network interfaces.
Dynamically Apply Actions to API Traffic
Once you have created an API, you use the Partner and API Management Portal to apply SLA and QoS restrictions, and perform a variety of actions on the HTTP requests and responses in API traffic. The tasks you can perform on API traffic include:
-
Changing the throttling (quota) settings.
-
Restricting access to a specific API endpoint.
-
Using Cross-reference Origin Resource Support (CORS) to provide secure access to third-party resources.
-
Authenticating an application (as an alternative to other authentication mechanisms)
-
Converting request/response body data from XML to JSON and JSON to XML.
-
Using an XLST on body of the request/response.
-
Validating your API Schema.
-
Adding REST-based callouts.
-
Performing any othermessage manipulation tasks that your implementation requires, using a Groovy programming language script.
You can create and apply actions to an API when you are creating it, and then update them dynamically afterward, as long as the action is still in a PUBLISHED or DEPRICATED state. These dynamic changes take effect immediately; no other action is required.
These actions replace the Services Gatekeeper service intercepter features for HTTP to HTTP communication. The Services Gatekeeper communication services that use non-HTTP protocols must use the services interceptor features for these capabilities.
Apply Security to the API
You use the Network Security options on the Partner and API Management GUI to apply network security to an API. You can configure the security strategy for the APIs to be one of the following:
-
None
-
Text-based
-
OAuth-based
During API creation, the partner manager has the option to make the API public (available to all partners) or private and only accessible to specific chosen partners.
Onboard and Manage Partners and Partner Groups
You use the Partner and API Management GUI to create partners and collect them into groups. You group partners together that require the same access to a set of APIs. However, you can specify different throttling parameters for each API, and for each partner in the group. A partner could be within your organization, a separate organization or entity, or even a single person.
Meter and Charge for Your APIs and Applications
The most common ways that Services Gatekeeper customers charge for the services they provide are content-based charging and call data record (CDR) charging. Content-based charging allows external billing systems to probe your Services Gatekeeper database and bill customers based on information that matches certain parameters. Charging by CDR is appropriate for online services for which you charge for services as they are used. For example, charging for access to services, or by duration of service.
Understanding the Multi-tier Services Gatekeeper Configuration
The multi-tier version of Services Gatekeeper includes all of the features of a single-tier Services Gatekeeper, but can be configured into a more robust and flexible environment.
When to use Multi-tier Services Gatekeeper
As previously mentioned, the single-tier Services Gatekeeper installation is appropriate for small to medium size API management implementations. As your implementation grows, and you find that you need increase performance by separating the various Services Gatekeeper components on dedicates systems, you can convert your system to a multi-tier version. A multi-tier Services Gatekeeper implementation is more flexible, but more complex. The multi-tier implementation uses the same GUI portals and administration console GUI tools as the default implementation, but spreads the back-end work across multiple physical servers. The difference is how the Services Gatekeeper back end is configured.
The multi-tier installation is appropriate for implementations that:
-
Process enough traffic through the Application Tier (AT) and Network Tier (NT) that they require separate physical servers.
-
Require the Application Test Environment tool to test multi-tier Services Gatekeeper telecom traffic with your applications.
-
Require the Platform Test Environment to test your Services Gatekeeper implementation is performing as you expect it to.
-
Require large amounts of data that are more efficiently accessed using a robust database (such as Oracle RAC) on a dedicated hardware system. Although the Oracle JavaDB database is supported for testing or small implementations.
The single-tier Services Gatekeeper usually uses the embedded and easy-to-use Oracle Java DB database, which is appropriate for test small production implementations.
Access to Oracle Communications Converged Application Server for Connectivity to SIP Network Infrastructure
In addition to providing access to traditional telecom network functionality, Services Gatekeeper can also connect application services to SIP-based functionality, using Oracle Communications Converged Application Server product (Converged Application Server). Calls set up using the Parlay X 2.1 or RESTful Third Party Call communication services can be routed through SIP. Parlay X 2.1 or RESTful Call Notifications can be established using SIP and Parlay X 2.1 or RESTful Presence watchers (consumers of presence information) and presentities (providers of presence information) can be set up.
Simplifying and Automating Partner Management Using Web Services
Managing numerous services, particularly when the providers are third-party partners, can be time and effort consuming. As the market expands, you use the Partner and API Management Portal interfaces to handle processes such as partner registration, service activation, and provisioning. These web service interfaces support automating a wide range of partner-related tasks and provide partners with easily available access to information about their accounts. The interface also enables operators to create groups of partners sharing sets of data, which can be used for tiering or segmentation of partners. Operators can then focus their administrative and partner management resources on their most rewarding partners.
Secure Access Control for Both Internal and Third-Party Applications
Services Gatekeeper can function as a single point of contact for access to the functionality of the underlying network, providing common authentication, authorization, and access control procedures for all applications, both internal and third-party based. For SOAP-based interfaces, Services Gatekeeper leverages the flexible security framework of Oracle WebLogic Server to provide robust system protection. Applications can be authenticated using plaintext or digest passwords, x.509 certificates, or SAML 1.0/1.1 tokens. Service requests can use XML encryption, based on the W3C standard, for either the whole request message or specific parts of it. And, to ensure message integrity, requests can be digitally signed, using the W3C XML digital signature standard. For RESTful interfaces, Services Gatekeeper uses HTTP basic, OAuth 2.0, or security assertion markup language (SAML) authentication of user name/password and SSL.
Flexible Authorization Control Based on Fine-Grained Policy Decisions
The Services Gatekeeper includes a powerful and responsive policy enforcement mechanism uses service level agreements (SLAs) to regulate service provider and application access to particular communication service functionality down to the level of supported operations and parameters. It also supports a range of quality-of-service (QoS) guarantees that you can modulate by Time of Day/Day of Week, Rates, and Quotas. You can add more rules to limit access. SLA management and maintenance can be simplified by organizing service provider and application accounts into groups. You can also create custom SLA versions to enhance the set of broadly comprehensive SLAs provided by Services Gatekeeper.
You control subscriber permissions and preferences in a separate Subscriber SLA, created by the operator or an integrator using tools available in the Platform Development Studio. Subscribers can indicate, for example, that they want to allow service provider X to query for the location of their mobile terminals, but not service provider Y.
Enhanced Network Protection
In addition to the service level agreements that cover access to functionality within Services Gatekeeper itself, other SLAs explicitly define service provider access to underlying network nodes. Services Gatekeeper throttles and shapes traffic to protect the underlying network during periods of heavy load, using node SLAs.
Built-in Network Routing
Services Gatekeeper provides a fine-grained internal system for routing service requests directly to appropriate network nodes based on various parameters, including the sending application, the destination address, or any other request parameter. Services Gatekeeper supports in-production deployment of multiple instances of most network protocol plug-ins (the module that interacts most directly with the underlying nodes) on an as needed basis.
Carrier Grade and Fully Scalable Architecture
The Services Gatekeeper architecture is based on the performance and clustering features provided by Oracle WebLogic Server, including:
-
Tiering
Services Gatekeeper is deployed in two tiers, an application tier (AT), and a network tier (NT). You can separate these tiers by a firewall for increased security. State is held only in the network-facing tier, and each tier can be built out independently of the other.
-
High availability and failover
Services Gatekeeper is designed throughout to ensure multi-level protection against single points of failure.
-
Geographic-redundancy
To protect the system in the face of catastrophic failure, geographically distant sites can be set up as site pairs. Service Provider and Application Group SLA enforcement is synchronized across geographic sites and SLAs are enforced between the site pairs. Any changes in account configuration information are also replicated across sites.
-
Storage Service
All traffic that passes through Services Gatekeeper is transactionally wrapped. Maintaining state consistently and durably in clustered and high performance environments is traditionally difficult, but the Services Gatekeeper Storage Service uses a sophisticated strategy of optimizing storage based on state access patterns. An in-memory store distributed among all the nodes serves as the entrance to data access. Reading from disk, and its attendant overhead, is reduced because the disk-based database functions as an archive rather than as a system of first use. The reduced overhead has two important benefits:
-
Speed: Because the data is available in memory, data access is extremely fast.
-
Scalability: As a system scales out, relying exclusively on disk-based database access often becomes a performance bottleneck. Because the data in Services Gatekeeper is distributed among the network tier nodes, adding more servers to the network tier actually increases data availability.
In addition, the Storage Service optimizes access to exactly the kinds of data that matter most in telecom traffic processing. Designed as a POJO java.util.Map -based API, client access is simplified for both storing data and making retrieval queries.
Coherence is used as the storage provider for configuration, core services, and a set of communication services.
-
OSS and Billing System Integration
All or selected parts of the Services Gatekeeper management mechanism can be integrated with your external Operation Support Systems (OSS) through JMX/JMS or SNMP interfaces. The tasks associated with administering current service providers and adding new ones can be folded into existing systems.
The Services Gatekeeper internal charging mechanisms can also be integrated with your existing billing systems. Offline and online (using the Parlay X 3.0 Payment API) Diameter-based charging is supported.
Subscriber Personalization and Protection
Using Services Gatekeeper, operators can customize their application functionality for individual subscriber by accessing subscriber profile information stored on network LDAP servers. At the same time, operators can protect subscriber privacy by using filters based on those same profiles to regulate the access that applications have, limiting the information that applications can acquire to what the subscriber wants to make available.
In addition, operators can optionally create Subscriber SLAs, which create service provider groupings called service classes that can be associated with individual subscriber URIs. Operators or integrators can do this using the Profile Provider service provider interface (SPI) included in the Platform Development Studio. Using Subscriber SLAs allows subscribers to customize their interactions with application service providers and at the same time keeping all their subscriber data within the confines of your domain.
Extensible Architecture
A flexible architecture using the robust capabilities of Oracle WebLogic Server means that operators can extend existing communication services to support new network interfaces, for example, Unstructured Supplementary Service Data. They can also create entirely new communication services to allow application service developers access to the unique feature of their networks using the Services Gatekeeper Platform Development Studio.
About Developing Applications
Services Gatekeeper includes various documentation and tools to assist application developers:
-
Services Gatekeeper Application Developer's Guide
-
Services Gatekeeper Java API Reference
-
Services Gatekeeper OAM Java API Reference
-
Services Gatekeeper Actions Java API Reference
-
The Application Test Environment graphical user interface (in the Services Gatekeeper SDK) that you use to test applications on a simulation of Services Gatekeeper.
-
The Platform Test Environment graphical user interface that you use to test your application against network and application simulators.
-
Web services WSDL and WADL files
Developing New Applications
The Services Gatekeeper documentation set includes the Services Gatekeeper Application Developer's Guide which describes the SOAP, REST, Native, and OneAPI interfaces and includes additional information that application developers need. Because the SOAP and Restful interfaces are Web services based, applications can be developed using any environment that the developer chooses.
Using the Application Test Environment GUI to Test Applications
Application developers can use the Services Gatekeeper Software Developer Kit (SDK) to test their applications. The SDK consists of the Application Test Environment (ATE), GUI which is a lightweight tool that simulates an instance of Services Gatekeeper called the Virtual Communication Service (VCS). The VCS exposes both SOAP and RESTful interfaces.
You can perform functional tests on tasks involving communication with Services Gatekeeper, such as opening sessions, sending and receiving messages, and examining delivery reports through the simulator. You can perform these tests without having to connect to an actual Services Gatekeeper implementation. When the time comes to test and later deploy the application with an actual Services Gatekeeper installation, you only need to change a few URLs in the application.
Application developers configure their applications to interface with the ATE. They then monitor the application's activity in the ATE interface, by checking whether messages have been received, and by examining information returned to the application. The ATE GUI includes a map in which developers can delineate geographic regions, insert and move terminals, and send messages to and receive messages from the terminals as if they were mobile devices in an actual network.
For more information, see "Testing Applications with the Application Test Environment" in Services Gatekeeper Application Developer's Guide.
Using the Platform Test Environment GUI to Test Features
Services Gatekeeper includes the Platform Test Environment (PTE), a graphical user interface (GUI) that you use to test default Services Gatekeeper features and your own custom communication services. The PTE simulates both the application-facing interfaces and network-facing protocols so you can test Services Gatekeeper behavior.
You use the PTE to configure an actual running Services Gatekeeper implementation using MBeans and specify access and budgets with service-level agreements (SLAs) just as you would in a production environment. The PTE includes clients, simulators, tools, and plug-ins to mimic most of the default Services Gatekeeper features. The PTE is a complete telecom testing environment. You create actual applications within the PTE to use as application-facing interfaces. Each client module interacts with a simulated network protocol on the network-facing part of the PTE. The client modules interact with simulated network protocols just as they would in a production environment. You can also extend the PTE to test your own custom features.
For more information see ”Understanding the Platform Test Environment” in Services Gatekeeper Platform Test Environment User's Guide for details.
Using Services Gatekeeper with a Traditional Telecom Network
The Services Gatekeeper API management features are directed mainly at HTTP-to-HTTP communication. Services Gatekeeper has also traditionally provided a variety of preconfigured capabilities to use with network that communicate using traditional dedicated telephony protocols.
Subscribers continue to require services that provide them with functionality and flexibility that cross the traditional boundaries between the world of the Internet and the world of their phones. Operators want to be responsive to the desires of their subscribers, and to provide services that satisfy subscriber demands, promote subscriber loyalty, increase average revenue per user (ARPU), and drive traffic to their networks.
The telephony-based Services Gatekeeper features allow operators to:
-
Offer simplified access to their network's capabilities, for both internal developers and external partners
-
Provide tooling and support for application service development and testing
-
Manage external partners efficiently
-
Protect the security and stability of the underlying network
-
Integrate new services with their existing operations and management facilities
-
Protect subscriber privacy and control
-
Support flexibility of access as networks change and grow
-
Do all this in a way that scales and meets the performance needs subscribers have come to expect
With the help of Services Gatekeeper, operations can effectively reduce the overhead of creating the applications that provide required services and enable a wider ranging development community to contribute to a better subscriber experience.
Figure 1-3 Oracle Communications Services Gatekeeper in Context
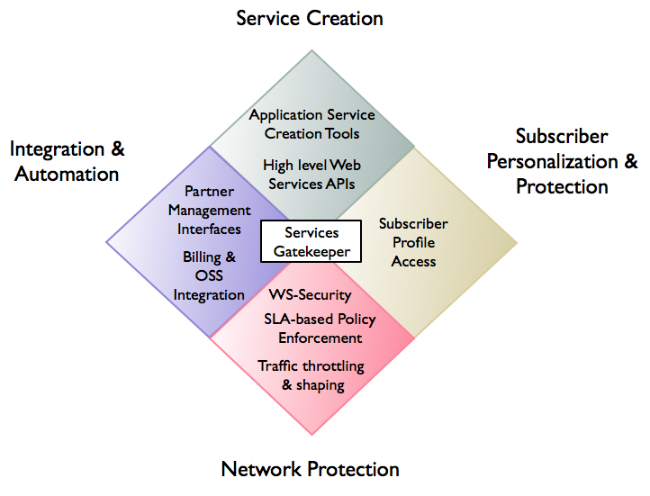
Description of ''Figure 1-3 Oracle Communications Services Gatekeeper in Context''
Access to Telecom Network Service Capabilities Using APIs Based on Well-Known Standards
The protocols required by underlying telecom network capabilities are often complex, and the learning curve associated with using them is steep. To help application service developers, Services Gatekeeper includes standard network capabilities such as Short Message Service (SMS), Multimedia Messaging Service (MMS) or Call Control through a set of easy-to-use interfaces (called facades in Services Gatekeeper).
-
Services Gatekeeper offers SOAP-style facades based on well-known standards such as Parlay X and some native protocol interfaces.
-
Various RESTful web service interfaces designed for ease of use in pure HTTP environments.
-
The Oracle Service Bus environment also contains SOAP-style interfaces that pre-integrated, offering application developers SOAP-based functionality and the flexibility of SOA.
-
The Oracle extended web services supports protocols which have not yet been incorporated into standardized forms (WAP Push, Binary SMS, and Subscriber Profile). These extended web services interfaces are published as standard Web Services Definition Language (WSDL) files, so application service developers can use their choice of toolsets.
-
E-mail communication service which uses MMS in the northbound interface and a plug-in that enables the sending of e-mail through SMTP and receiving e-mail through POP3 and IMAP protocols. You use the RESTful Email Communication interface to send e-mail messages and to fetch information about e-mail messages that have been received for the applications and stored on Services Gatekeeper.
-
OneAPI interfaces for MMS, SMS, and various other services.
Developers can focus on creating compelling and innovative services, leaving the communication services components of Services Gatekeeper to handle the mechanics of interacting with the various underlying network elements.
Services Gatekeeper also provides an xparam mechanism to manipulate network protocol parameters which do not exist in the web service API. The xparams are listed in the individual Communication Service descriptions in the Services Gatekeeper Communication Service Reference Guide.
Figure 1-4 Standardized Application Interfaces
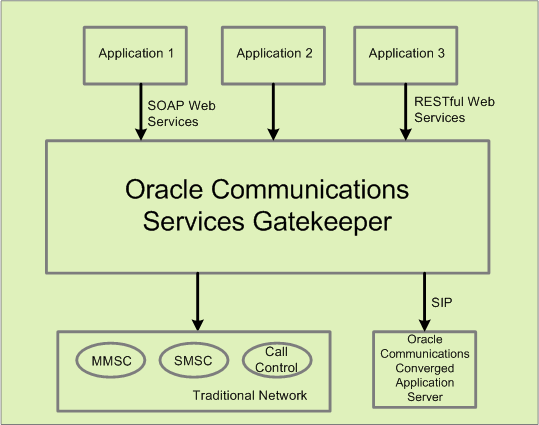
Description of ''Figure 1-4 Standardized Application Interfaces''