User Authentication
User authentication enables single sign-on (SSO) functionality across Oracle Enterprise Performance Management System components by validating the login information of each user to determine authenticated users. User authentication, along with component-specific authorization, grants the user access to EPM System components. The process of granting authorization is called provisioning.
Authentication Components
The following sections describe the components that support SSO:
Native Directory
Native Directory refers to the relational database that Oracle Hyperion Shared Services uses to support provisioning and to store seed data such as default user accounts.
Native Directory functions:
-
Maintain and manage the default EPM System user accounts
-
Store all EPM System provisioning information (relationships among users, groups, and roles)
Native Directory is accessed and managed using Oracle Hyperion Shared Services Console. See "Managing Native Directory" in the Oracle Enterprise Performance Management System User Security Administration Guide.
External User Directories
User directories refer to corporate user and identity management systems that are compatible with EPM System components.
EPM System components are supported on several user directories, including LDAP-based user directories; for example, Oracle Internet Directory, Sun Java System Directory Server (formerly SunONE Directory Server), and Microsoft Active Directory. Relational databases also are supported as user directories. User directories other than Native Directory are referred to as external user directories throughout this document.
For a list of supported user directories, see the Oracle Enterprise Performance Management System Certification Matrix posted on the Oracle Fusion Middleware Supported System Configurations page on Oracle Technology Network (OTN).
From Shared Services Console, you can configure many external user directories as the source for EPM System users and groups. Each EPM System user must have a unique account in a configured user directory. Generally, EPM System users are assigned to groups to facilitate provisioning.
Default EPM System Single Sign-on
EPM System supports SSO across EPM System web applications by allowing authenticated users from an application to seamlessly navigate to other applications without reentering credentials. SSO is implemented by integrating a common security environment that handles user authentication and provisioning (role-based authorization) across EPM System components.
The default SSO process is depicted in the following illustration.
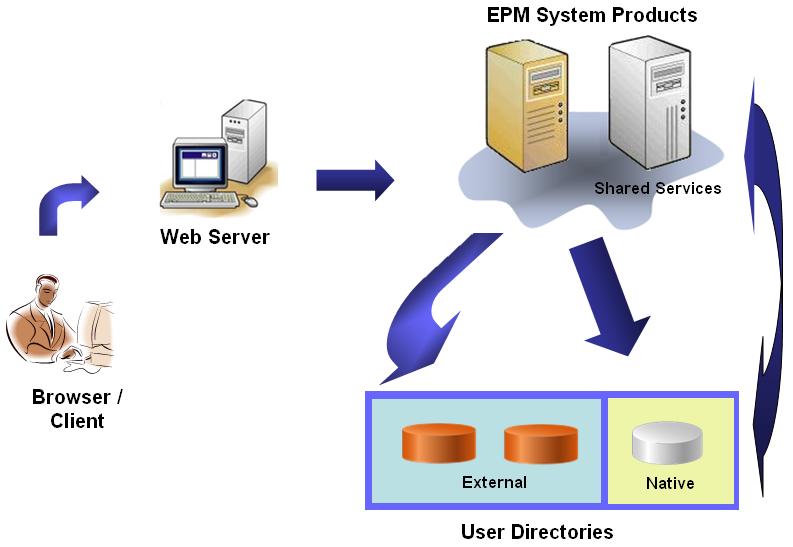
-
Through a browser, users access an EPM System component login screen and enter a user name and password.
The EPM System component queries the configured user directories (including Native Directory) to verify user credentials. Upon finding the matching user account in a user directory, the search is terminated, and the user's information is returned to the EPM System component.
Access is denied if no user account is found in any configured user directory.
-
Using the retrieved user information, the EPM System component queries Native Directory to obtain provisioning details for the user.
-
EPM System component checks the Access Control List (ACL) in the component to determine the application artifacts that the user can access.
Upon receiving provisioning information from Native Directory, the EPM System component is made available to the user. At this point, SSO is enabled for all EPM System components for which the user is provisioned.
Single Sign-on from Access Management Systems
To further secure EPM System components, you can implement a supported access management system such as Oracle Access Manager or SiteMinder, which can provide authenticated user credentials to EPM System components and control access based on predefined access privileges.
SSO from security agents is available for EPM System web applications only. In this scenario, EPM System components use the user information provided by the security agent to determine access permissions of users. To enhance security, Oracle recommends that direct access to servers be blocked by firewalls so all requests are routed through an SSO portal.
SSO from access management systems is supported by accepting authenticated user credentials through an acceptable SSO mechanism. See Supported SSO Methods. The access management system authenticates users and passes the login name to EPM System. EPM System verifies the login name against configured user directories.
See these topics.
The illustrated concept:
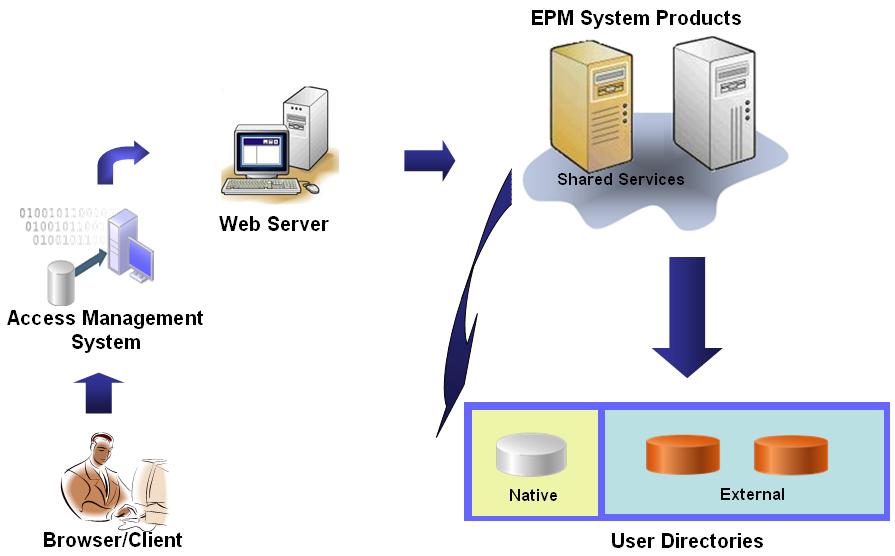
-
Using a browser, users request access to a resource protected by an access management system, for example; Oracle Access Manager, or SiteMinder.
Note:
EPM System components are defined as resources protected by the access management system.
The access management system intercepts the request and presents a login screen. Users enter a user name and password, which are validated against configured user directories in the access management system to verify user authenticity. EPM System components are also configured to work with these user directories.
Information about the authenticated user is passed to the EPM System component, which accepts the information as valid.
The access management system passes the user's login name (value of
Login Attribute) to the EPM System component using an acceptable SSO mechanism. See Supported SSO Methods. -
To verify user credentials, the EPM System component tries to locate the user in a user directory. If a matching user account is found, then user information is returned to the EPM System component. EPM System security sets the SSO token that enables SSO across EPM System components.
-
Using the retrieved user information, the EPM System component queries Native Directory to obtain provisioning details for the user.
Upon receiving user provisioning information, the EPM System component is made available to the user. SSO is enabled for all EPM System components for which the user is provisioned.