Setting Up VPN
![]() This topic does not apply to Oracle Cloud at Customer.
This topic does not apply to Oracle Cloud at Customer.
Topics
- About Setting Up VPN
- Creating a Cloud Gateway
- Registering a Third-Party VPN Device
- Connecting the Cloud Gateway with the Third-Party Device
Note:
You must have the Compute_Operations role to access the pages under the VPN tab. If you don’t have this role, you won’t be able to view these pages.
About Setting Up VPN
![]() This topic does not apply to Oracle Cloud at Customer.
This topic does not apply to Oracle Cloud at Customer.
Considerations for Setting Up a Single-Homed or Dual-Homed VPN Gateway
While setting up a VPN connection to yourCompute Classic instances, consider whether the instances that you want to access will be on IP networks or on the shared network.
-
Using IP networks allows you to define IP subnets in your account and isolate or enable traffic between subnets. By adding instances to IP networks, you can control the IP address assigned to each instance and you can also assign static IP addresses to each instance. See About IP Networks.
If you want to access instances that are added to IP networks, you can create a dual-homed VPN gateway, which has one interface on the shared network and one interface on an IP network. With this gateway, you can use VPN to access all instances that are on the same IP network as the gateway instance.
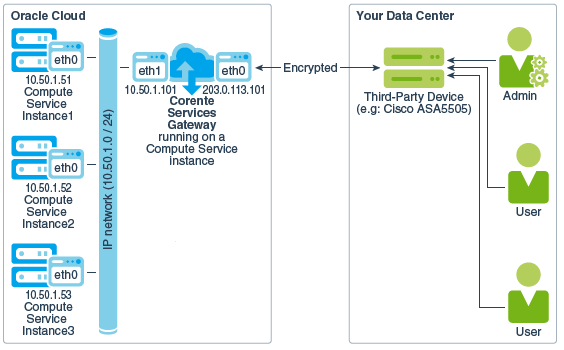
The following figure shows a VPN connection between a third-party VPN device and a dual-homed cloud gateway. This gateway allows VPN access to instances on the same IP network.
Note:
You can also extend VPN access to instances on other IP networks. However, if you want access to a large number of instances, it is recommended that you avoid setting up numerous IP networks with a /32 subnet. Instead, use a smaller number of IP networks with larger subnets. If you create a very large number of IP networks, a large number of IPSec security associations are required, which could cause performance degradation on some third-party devices. See Workflow for Adding IP Networks to an Existing VPN Connection.
-
If you don’t need to set up IP networks and the instances that you want to access over VPN all have an interface on the shared network, then you can create a single-homed VPN gateway. After you’ve set up the VPN connection, you must configure a Generic Routing Encapsulation (GRE) tunnel from each instance to the gateway.
The following figure shows a VPN connection between a third-party VPN device and a single-homed cloud gateway. This gateway allows VPN access to instances on the shared network with a GRE tunnel between each instance and the gateway.

VPN Scenarios Not Supported by the Compute Classic Web Console
-
Connect a Corente Services Gateway instance in the cloud with a Corente Services Gateway instance in your data center. To do this, see About Setting Up VPN Using Corente Services Gateway in Setting Up VPN from Corente Services Gateway On-Premises to the Shared Network or Solution Overview in Setting Up VPN from a Corente Services Gateway to an IP Network in Oracle Cloud.
-
Configure failover between two Corente Services Gateway instances to provide high availability. To do this, see Configuring Active-Active HA in Setting Up VPN from a Third-Party Gateway to an IP Network in Oracle Cloud.
-
If you want to add an IP network to an existing VPN connection, you can create the IP network and add it to an IP network exchange using the web console. However, you can’t complete the steps to update user groups for your Corente Services Gateway and add a route on the gateway to the subnet of the newly added IP network using the web console. To complete these steps, you must use App Net Manager. See Adding IP Networks to an Existing VPN Connection in Setting Up VPN from a Third-Party Gateway to an IP Network in Oracle Cloud.
Workflow for Setting Up VPN
-
Configure a supported third-party VPN device at your data center. Device configuration varies depending on the type and model of your device. For supported configurations, see Third-Party VPN Device Configuration.
-
Create a Corente Services Gateway instance in Compute Classic. See Creating a Cloud Gateway.
-
Add information about your third-party VPN device. See Registering a Third-Party VPN Device.
-
Create a connection between your Corente Services Gateway and your third-party device. See Connecting the Cloud Gateway with the Third-Party Device.
-
If you created a single-homed VPN gateway instance, on each instance that you want to access, configure a GRE tunnel to the gateway. See Configuring a GRE Tunnel on a Guest Instance in Oracle Cloud in Setting Up VPN From a Third-Party Gateway On-Premises to the Shared Network.
Third-Party VPN Device Configuration
You can set up a VPN connection to any certified third-party device that allows interoperability with Corente Services Gateway. Devices must be configured for policy-based VPN.
The following table lists the certified third-party VPN device configurations.
| Certified Configurations | Devices |
|---|---|
|
Cisco 2921 Cisco ISR 4331 Checkpoint 3200 Palo Alto 3020 FortiGate-200D |
|
Cisco 2921 Cisco ISR 4331 Checkpoint 3200 Palo Alto 3020 FortiGate-200D |
|
Cisco 2921 Cisco ISR 4331 Checkpoint 3200 Palo Alto 3020 FortiGate-200D |
|
Cisco ASA5505 |
|
Cisco ISR 4331 Checkpoint 3200 Palo Alto 3020 FortiGate-200D |
Other devices may work if they are configured with the certified configurations. Consider the following information while configuring your third-party device for a VPN connection.
-
Configuration Information
-
The Corente Services Gateway uses IPSec and is behind a NAT, so network address translation traversal (NAT-T) is required. Ensure that the third-party device in your data center supports NAT-T. NAT-T requires UDP port 4500 to be open.
-
Devices must support and be configured for policy-based VPN.
-
Authentication: Pre-shared keys
-
Encryption: 3DES, AES-128, AES-192, AES-256
-
Hash: MD5, SHA-1, SHA-2
-
Policy Group: Diffie-Hellman groups supported are 2, 5, 14, 15, 16, 17, 18, 22, 23, 24
-
ISAKMP: IKEv1 only. If IKEv2 is enabled by default, turn it off.
-
Exchange type: Main Mode (The cloud gateway uses main mode in phase one negotiations)
-
IPSec protocol: ESP, tunnel-mode
-
PFS: Enabled
-
It is highly recommended that the third-party device be configured to be responder-only.
-
Ensure the IKE and IPSec timeouts on the Corente Services Gateway and the third-party device are the same.
-
For Phase 1, ensure that the IKE ID on the Corente Services Gateway and the third-party device match.
-
-
HA Information
-
When HA is configured, Dead Peer Detection (DPD) must be enabled to detect when a tunnel is down.
-
When HA is configured, asymmetric routing across the tunnels that make up the VPN connection will occur. Ensure that your firewall is configured to support this. If not, traffic will not be routed reliably.
-
Switching tunnels might take 30–40 seconds.
-
Creating a Cloud Gateway
![]() This topic does not apply to Oracle Cloud at Customer.
This topic does not apply to Oracle Cloud at Customer.
Prerequisites
- You must have already reserved the public IP address that you want to use with your gateway instance. See Reserving a Public IP Address.
- If you want to add your VPN gateway instance to an IP network, you must create the IP network first. See Creating an IP Network.
-
To complete this task, you must have the
Compute_Operationsrole. If this role isn’t assigned to you or you’re not sure, then ask your system administrator to ensure that the role is assigned to you in Oracle Cloud Infrastructure Classic Console. See Modifying User Roles in Managing and Monitoring Oracle Cloud.
Procedure
- Sign in to the Compute Classic console. If your domain spans multiple sites, select the appropriate site. To change the site, click the Site menu near the top of the page.
- Click the Network tab.
- In the Network drop-down list, expand VPN, expand Corente, and then click VPN Gateways.
- Click Create VPN Gateway.
- Select or enter the required information:
- Name: Enter a name for the Corente Services Gateway instance.
- IP Reservation: Select the IP reservation that you want to use with this instance. This is the public IP address of your VPN gateway.
- Image: Select the machine image that you want to use to create the instance. You must select the most recent Corente Gateway image.
-
Interface Type: Select Dual-homed if you want to use this VPN gateway to connect to instances on an IP network. If you haven’t set up IP networks or if you want to use this gateway to connect to instances on the shared network only, then select Single-homed.
If you select Single-homed, you must configure GRE tunnels between the Corente Services Gateway instance and each Compute Classic instance that you want to access using VPN. See Configuring a GRE Tunnel on a Guest Instance in Oracle Cloud in Setting Up VPN From a Third-Party Gateway On-Premises to the Shared Network.
If you select Dual-homed, all instances that are on the same IP network as the Corente Services Gateway instance can be accessed using VPN.
- IP Network: This field is displayed when you select the Dual-homed interface type. Select the IP network that you want to add the Corente Services Gateway instance to.
- IP Network Address: This field is displayed when you select the Dual-homed interface type. Select the IP address for your gateway instance. The IP address you specify must belong to the subnet of the specified IP network. An available IP address is allocated by default. You can specify a different LAN IP address, if required.
- Subnets: Enter a comma-separated list of subnets (in CIDR format) that should be reachable using this gateway. If you selected the Dual-homed interface type, you can enter the subnets of your IP networks. Ensure that all the IP networks you specify here belong to the same IP network exchange. The subnet of the IP network specified in the IP Network field is added by default. Don’t modify or delete this subnet in this field.
- Add reachable IP networks: (Optional) This field is displayed when you select the Dual-homed interface type. You can select additional IP networks that should be reachable using this gateway. Ensure that the IP networks that you specify here, and the IP network that the Corente Services Gateway is added to, all belong to the same IP network exchange. See Adding an IP Network to an IP Network Exchange.
You must also add a route on the gateway to the subnet of each additional IP network. You can’t do this using the web console. Use App Net Manager to add this route. See Adding IP Networks to an Existing VPN Connection in Setting Up VPN from a Third-Party Gateway to an IP Network in Oracle Cloud.
Note:
You must also add the subnets that you specify here to the list of destination IP addresses that you specify in your third-party device.
- Click Create.
A Corente Services Gateway instance is created. The required orchestrations are created and started automatically. For example, if you specified the name of the Corente Gateway instance as CSG1, then the following orchestrations are created:
-
vpn–CSG1–launchplan: This orchestration creates the instance using the specified image, and associates the instance interfaces with the shared network and, for a dual-homed gateway, with the specified IP network.
-
vpn–CSG1–bootvol: This orchestration creates the persistent bootable storage volume.
-
vpn–CSG1–secrules: This orchestration creates the required security list, security applications, and security rules.
-
vpn–CSG1–master: This orchestration specifies relationships between each of the nested orchestrations and starts each orchestration in the appropriate sequence.
While the Corente Services Gateway instance is being created, the instance status displayed in the Instance column on the VPN Gateways page is Starting. When the instance is created, its status changes to Ready.
To use this gateway in a VPN connection, add a third-party device and then create a connection. See Registering a Third-Party VPN Device and Connecting the Cloud Gateway with the Third-Party Device.
Note:
You can list the gateway instance and view details on the Instances page, or view the corresponding orchestrations on the Orchestrations page. However, it is recommended that you always use the VPN Gateways page to manage your gateway instances.
Registering a Third-Party VPN Device
![]() This topic does not apply to Oracle Cloud at Customer.
This topic does not apply to Oracle Cloud at Customer.
To complete this task, you must have the Compute_Operations role. If this role isn’t assigned to you or you’re not sure, then ask your system administrator to ensure that the role is assigned to you in Oracle Cloud Infrastructure Classic Console. See Modifying User Roles in Managing and Monitoring Oracle Cloud.
Connecting the Cloud Gateway with the Third-Party Device
![]() This topic does not apply to Oracle Cloud at Customer.
This topic does not apply to Oracle Cloud at Customer.
Prerequisites
-
You must have already created the cloud gateway that you want to use. See Creating a Cloud Gateway.
-
You must have already configured your third-party VPN device in your data center. See Third-Party VPN Device Configuration.
-
You must have already added the third-party VPN device that you want to connect to in your data center. See Registering a Third-Party VPN Device.
-
To complete this task, you must have the
Compute_Operationsrole. If this role isn’t assigned to you or you’re not sure, then ask your system administrator to ensure that the role is assigned to you in Oracle Cloud Infrastructure Classic Console. See Modifying User Roles in Managing and Monitoring Oracle Cloud.
Procedure