Use OAuth 2.0 Grants in Oracle Identity Cloud Service Environments
To use an OAuth 2.0 grant type with this adapter in an Oracle Identity Cloud Service environment of Oracle Integration, you must perform the following prerequisites.
Note:
The following instructions apply only to cloud tenancies that still use Oracle Identity Cloud Service. Most cloud tenancies have been migrated to identity domains, which require different configuration instructions. See Use OAuth 2.0 Grants in Identity Domain Environments. If you are unsure of your environment, check with your administrator.Prerequisites for All Grants
Perform the following tasks for each grant type you use.
- Obtain the Oracle Identity Cloud
Service URL.
- Go to the URL for your Oracle Integration instance.
For example, if your Oracle Integration instance is
https://myhost.example.com/ic/home, when you go to that URL, you are redirected to a URL such as:https://idcs-c2881.identity.myhost.example.com/ui/v1/signin - Replace
/signinwith/adminconsoleto access Oracle Identity Cloud Service.For example:https://idcs-c2881.identity.myhost.example.com/ui/v1/adminconsoleYou'll be prompted to sign in again to the Oracle Identity Cloud Service Console.
- Log in to the Oracle Identity Cloud Service Console with your identity domain administrator credentials.
- Go to the URL for your Oracle Integration instance.
- Check the Oracle Integration application in Oracle Identity Cloud
Service.
When an Oracle Integration instance is provisioned, an Oracle Identity Cloud Service application is created for that Oracle Integration instance. The application name is
OICINST_service_instance_name.- Log in to the Oracle instance to get the service instance
name.
https://myhost.example.com/ic/home - Log in to Oracle Identity Cloud Service to get the application.
- Go to Applications and find the application with the above name to access the application.
Alternatively, you can find the application through the Oracle Cloud Dashboard. When you click the IDCS Application link on the details page of the Oracle Integration instance (for this example, named OIC), it opens the Oracle Identity Cloud Service application for Oracle Integration that is already created.
- Log in to the Oracle instance to get the service instance
name.
Prerequisites for JWT User Assertion
Perform the following tasks.
- Validate the Oracle Integration application and user roles.
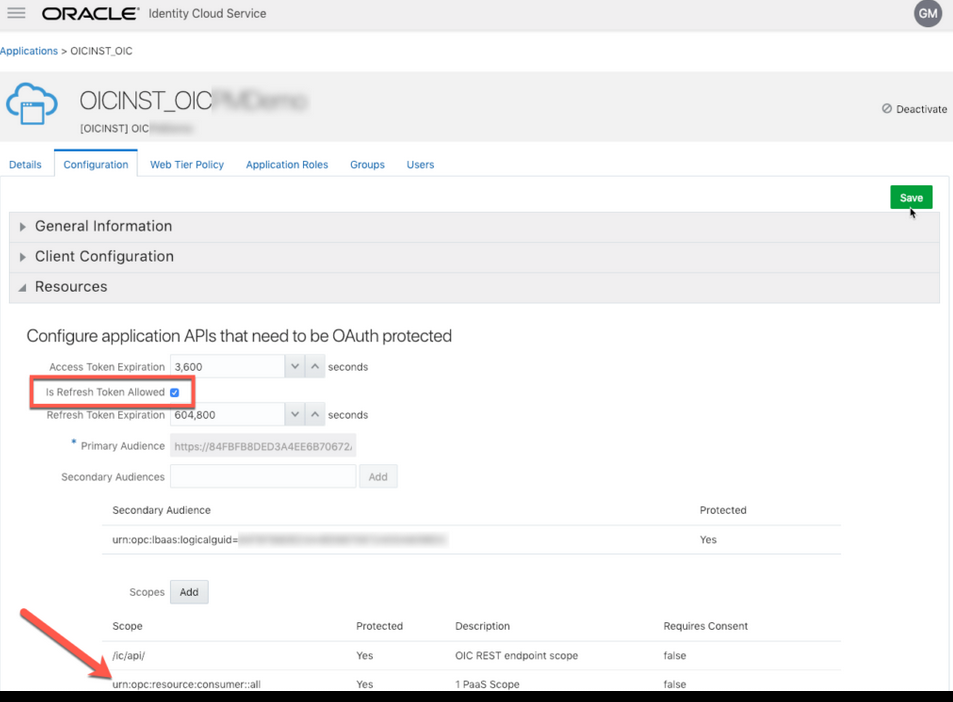
- Verify that the Is Refresh Token Allowed option is enabled for the Oracle Identity Cloud Service application.
- Check under the Configuration >
Resources section of the application. Note
also that there is a special scope predefined
(urn:opc:resource:consumer::all), which can
trigger integrations using OAuth.
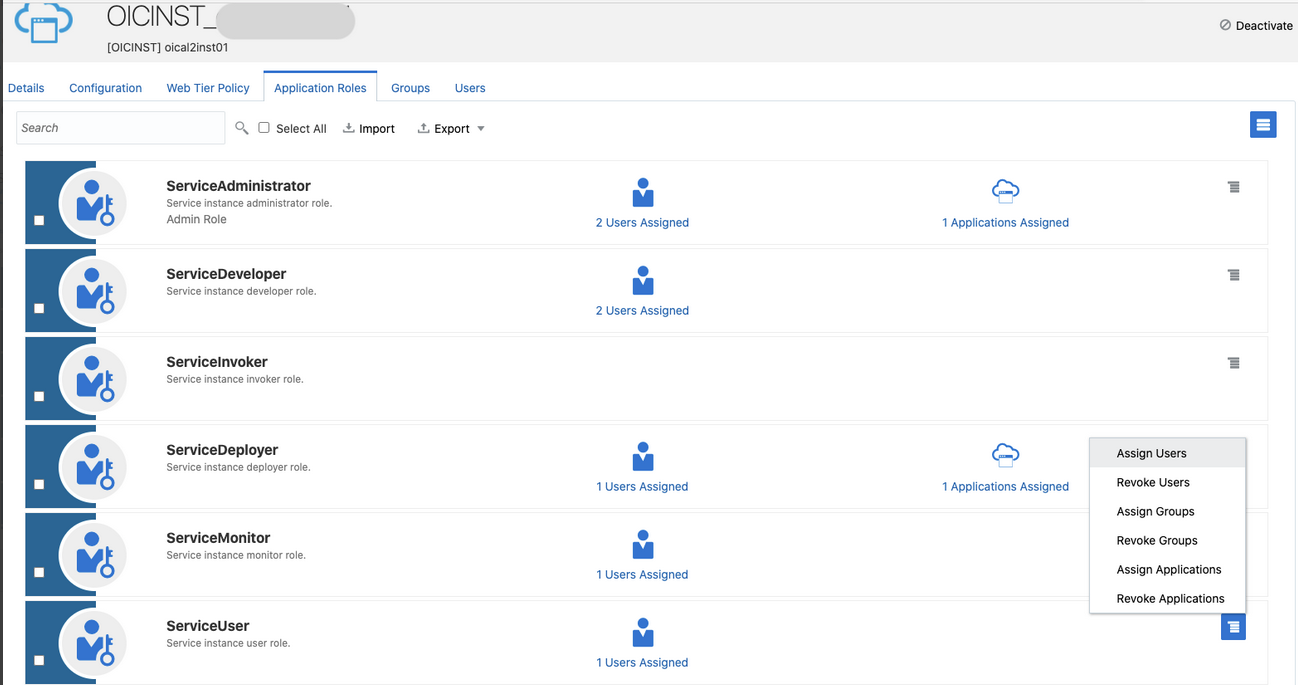
- Add the appropriate users to the various Oracle Integration roles. For standard/production configurations, use the ServiceUser role. (See Oracle Integration Service Roles in Provisioning and Administering Oracle Integration 3.)
- To assign the user, go to the Application
Roles section of the application.
- Generate the key:
- Generate the self-signed key pair.
keytool -genkey -keyalg RSA -alias <your_alias> -keystore <keystore_file> -storepass <password> -validity 365 -keysize 2048 ##example keytool -genkey -keyalg RSA -alias assert -keystore sampleKeystore.jks -storepass samplePasswd -validity 365 -keysize 2048 - Export the public key for signing the JWT
assertion.
keytool -exportcert -alias <your_alias> -file <filename> -keystore <keystore_file> -storepass <password> ##example keytool -exportcert -alias assert -file assert.cer -keystore sampleKeystore.jks -storepass samplePasswd ## This should show a success message e.g. Certificate stored in file <assert.cer> - Convert the keystore to P12
format.
keytool -importkeystore -srckeystore <filename> -srcstorepass <password> -srckeypass <password> -srcalias <your_alias> -destalias <your_alias> -destkeystore <destFileName> -deststoretype PKCS12 -deststorepass <password> -destkeypass <password> ##example keytool -importkeystore -srckeystore sampleKeystore.jks -srcstorepass samplePasswd -srckeypass samplePasswd -srcalias assert -destalias assert -destkeystore assert.p12 -deststoretype PKCS12 -deststorepass samplePasswd -destkeypass samplePasswd ## This should show a success message e.g. Importing keystore sampleKeystore.jks to assert.p12... - Export the private key from the P12
keystore.
openssl pkcs12 -in <destFileName> -nodes -nocerts -out <pem_file> ##example openssl pkcs12 -in assert.p12 -nodes -nocerts -out private_key.pem ## This should show a success message: MAC verified OK
- Generate the self-signed key pair.
- Configure the client application:
To trigger the integration with OAuth, a client application is required.
- In the Oracle Identity Cloud
Service Console, go to the
Applications section to create a new
application that allows you to trigger an integration with OAuth.
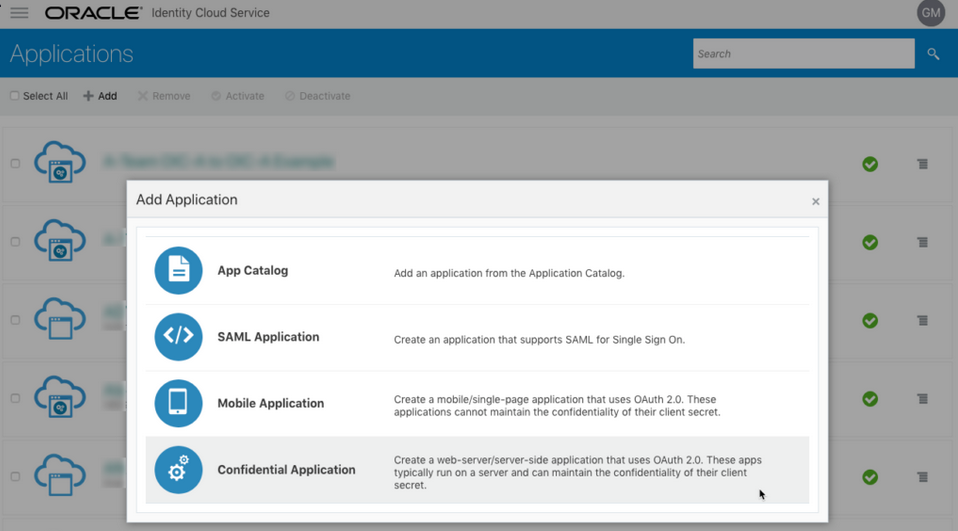
- Click Add.
- Select Confidential Application.
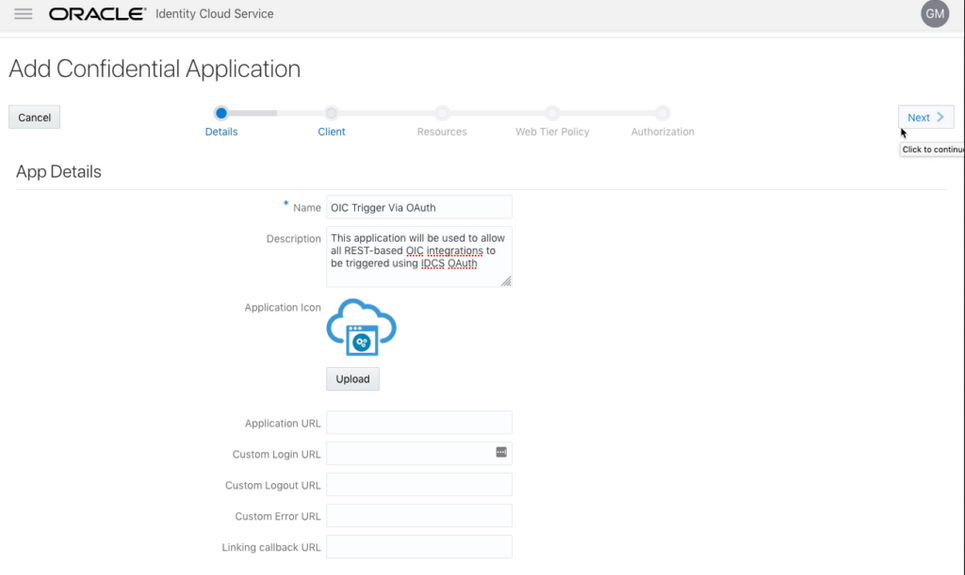
- Complete the Details page, and go to
the Client page.
- On the Client page, select
Configure this application as a client now
and add the following.
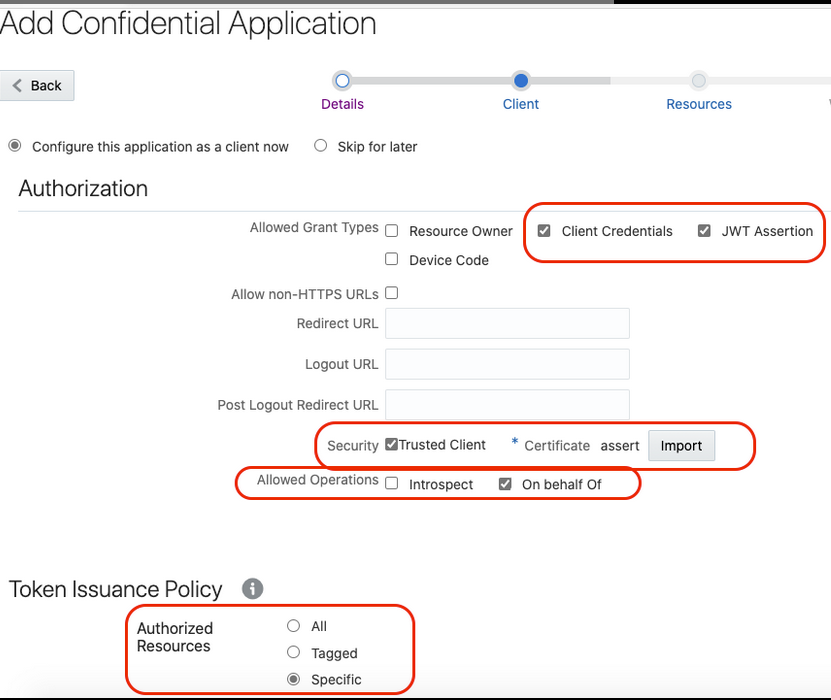
- Select Client Credentials and JWT Assertion for the Allowed Grant Types.
- In the Security section, select Trusted Client and upload the certificate created in the previous section (Generate the key - Step 2).
- Select Specific in the
Authorized Resources section.
- Click Add Scope under the
Resources section.
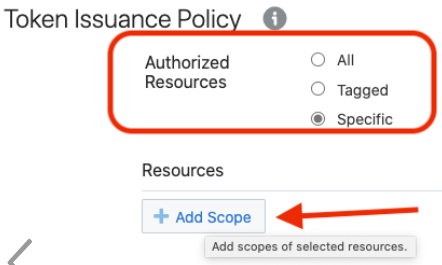
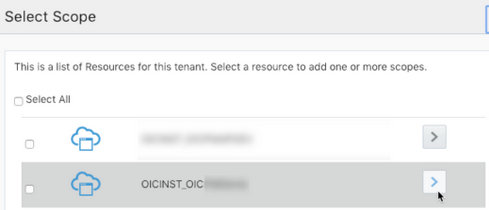
- Find the Oracle Integration application, and click
>.
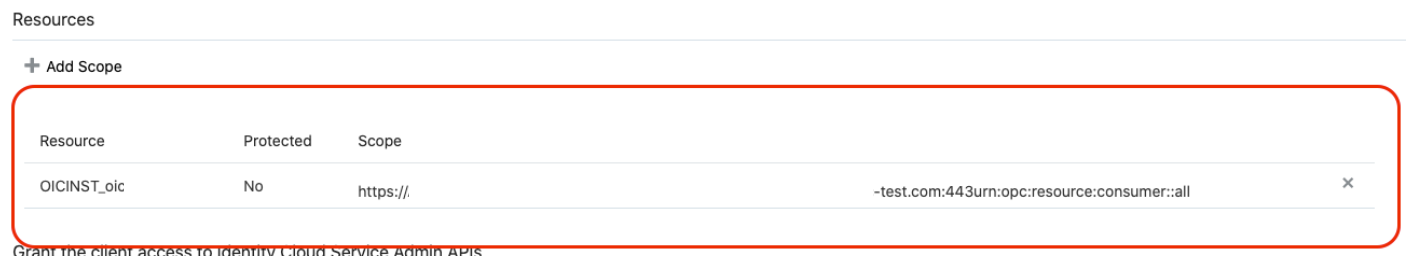
- Add the scope containing
urn:opc:resource:consumer::all, and
click >.
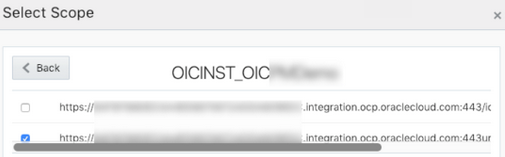
The scope containing urn:opc:resource:consumer::all is added.
- Save your changes.
- Click through the remaining wizard pages without making changes and save the application.
- Activate the application for use.
- In the Oracle Identity Cloud
Service Console, go to the
Applications section to create a new
application that allows you to trigger an integration with OAuth.
- Add a certificate as a trusted partner:
Even though you imported the signing certificate in the application, Oracle Identity Cloud Service requires you to also have the certificate as a trusted partner certificate. Upload the certificate created in the previous section. (See Generate the key - Step 2.)
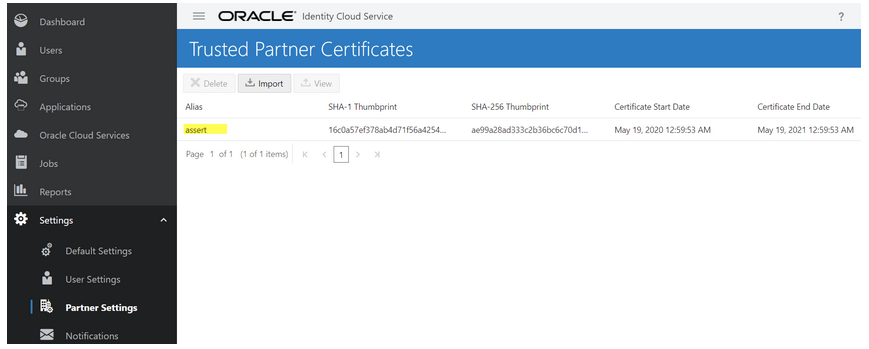
Description of the illustration trusted_partner_cert.png - Generate the JWT user assertion:
- Generate the JWT user assertion using the generated private
key and simple Java code.
Note:
You can use the https://github.com/jwtk/jjwt library to generate the user assertion. There are many libraries listed at https://jwt.io/ for multiple technologies.Sample: header: { "alg": "RS256", "typ": "JWT", "kid": "assert" } payload: { "sub": "ssaInstanceAdmin", "jti": "8c7df446-bfae-40be-be09-0ab55c655436", "iat": 1589889699, "exp": 1589909699, "iss": "d702f5b31ee645ecbc49d05983aaee54", "aud": "https://identity.oraclecloud.com/" }
Where:subspecifies the user name for whom user assertion is generated.jtiis a unique identifieriatis issued (epoch seconds).expis the token expiry (epoch seconds).issis the client ID.audmust include the Oracle Identity Cloud Service audiencehttps://identity.oracle.com/. The signing algorithm must be RS256.kidspecifies the key to use to verify the signature. Therefore, it must match with the uploaded certificate alias in Oracle Identity Cloud Service.
- Generate the JWT user assertion using the generated private
key and simple Java code.
- Validate the client application:
- Once you generate the JWT user assertion, generate the Oracle Identity Cloud
Service access token as
follows.
##Syntax curl -i -H 'Authorization: Basic <base64Encoded clientid:secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=urn%3Aietf%3Aparams%3Aoauth%3Agrant-type%3Ajwt-bearer&assertion=<user assertion>&scope=<app_scope>' ###where #### grant type - urn:ietf:params:oauth:grant-type:jwt-bearer #### <base64-clientid-secret> - Base 64 encode clientId:ClientSecret #### <user assertion> - User assertion generated #### <app scope> - Scope added while creating application in client configuration section (Ends with urn:opc:resource:consumer::all) - Capture the
access_tokenfrom the response.{ "access_token": "eyJ4NXQjG...dfsdfsFgets2ed", "token_type": "Bearer", "expires_in": 3600 } - Use an
access_tokenin the authorization header to invoke the Oracle Integration trigger endpoint.curl --location --request GET 'https://OIC host/OIC endpoint' \ --header 'Authorization: Bearer eyJ4NXQjG...dfsdfsFgets2ed'
- Once you generate the JWT user assertion, generate the Oracle Identity Cloud
Service access token as
follows.
Prerequisites for Authorization Code
Perform the following tasks.
- Validate the Oracle Integration application and user roles:
- Verify that the Is Refresh Token Allowed option is enabled for the Oracle Identity Cloud Service application.
- Check the Configuration >
Resources section of the application. Note
also that there is a special predefined scope
(urn:opc:resource:consumer::all) that permits
triggering of the Oracle Integration integrations using OAuth.
- Add the appropriate users to the various Oracle Integration roles. For standard/production configurations, use the ServiceUser role. (See Oracle Integration Service Roles in Provisioning and Administering Oracle Integration 3.)
- To assign the user, go to the Application Roles
section of the application.
- Configure the client application:
To allow you to trigger the Oracle Integration integration with OAuth, the client application is required.
- In the Oracle Identity Cloud
Service Console, go to the
Applications section to create a new
application that allows you to trigger the Oracle Integration
integration with OAuth.

- Select Confidential Application.
- Complete the Details page, and go to
the Client page.
- On the Client page, select
Configure this application as a client now
and add the following.
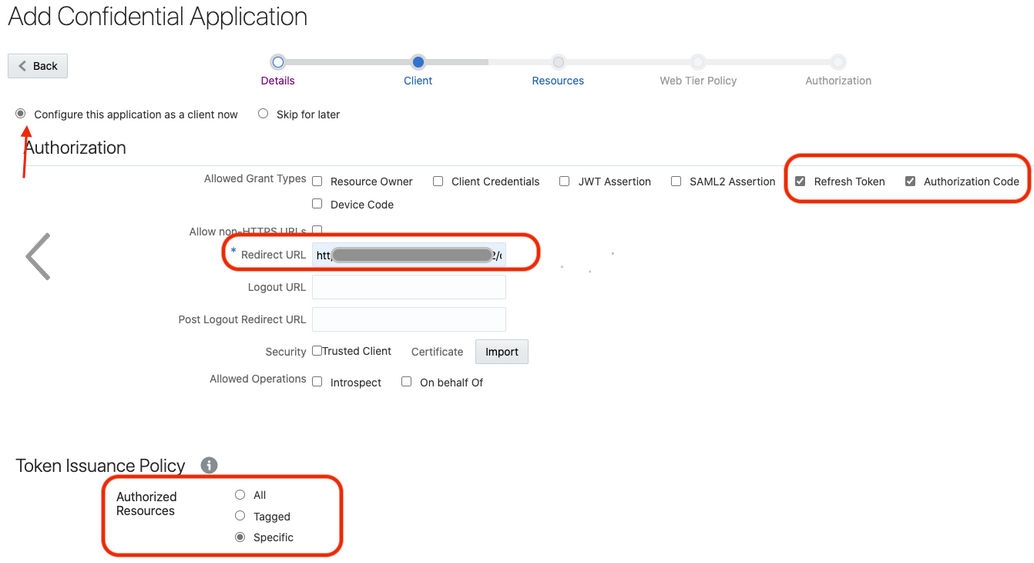
- Select Refresh Token and Authorization Code for Allowed Grant Types.
- Set the redirect URL to the URL of the client
application. After user login, Oracle Identity Cloud
Service
redirects to this URL with the authorization code.
Note:
If you don't know the following information, check with your administrator:
- If your instance is new or upgraded from Oracle Integration Generation 2 to Oracle Integration 3.
- The complete instance URL with the region included (required for new instances).
For Connections… Include the Region as Part of the Redirect URL? Example of Redirect URL to Specify… Created on new Oracle Integration 3 instances Yes. https://OIC_instance_URL.region.ocp.oraclecloud.com/icsapis/agent/oauth/callbackCreated on instances upgraded from Oracle Integration Generation 2 to Oracle Integration 3
No. This applies to both:
- New connections created after the upgrade
- Existing connections that were part of the upgrade
https://OIC_instance_URL.ocp.oraclecloud.com/icsapis/agent/oauth/callback - Select Specific in the
Authorized Resources section.
- Click Add Scope under the
Resources section.

- Find the Oracle Integration application, and click
>.

- Add the scope containing
urn:opc:resource:consumer::all, and
click >.

The scope containing urn:opc:resource:consumer::all is added.

- Save your changes.
- Click through the remaining wizard pages without making changes and save the application.
- Activate the application for use.
- In the Oracle Identity Cloud
Service Console, go to the
Applications section to create a new
application that allows you to trigger the Oracle Integration
integration with OAuth.
- Validate the client application:
- To fetch the authorization code, make the following request
from the
browser.
##Syntax GET https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/authorize?client_id=<client-id>&response_type=code&redirect_uri=<client-redirect-uri>&scope=<app_scope>%20offline_access&nonce=<nonce-value>&state=<unique_value> ###where #### <client-id> - ID of Client application generated. #### <client-redirect-uri> - Redirect URI, in client application. #### <app_scope> - scope added while creating application in client configuration. (Ends with urn:opc:resource:consumer::all) #### nonce - Optional, unique value to mitigate replay attacks #### state - Recommended, Opaque to IDCS. Value used to maintain state between the request and the callback ##Example GET https://<idcs-host>/oauth2/v1/authorize?client_id=<clientID>&response_type=code&redirect_uri=https://app.getpostman.com/oauth2/callback&scope=https://<Resource_APP_Audience>urn:opc:resource:consumer::all%20offline_access&nonce=121&state=12345544 - If the user is not already logged in, Oracle Identity Cloud
Service challenges the user to authenticate. Oracle Identity Cloud
Service checks the user's credentials. (For
authentication, the user assigned the ServiceUser
role must be used.)
After authentication is successful, Oracle Identity Cloud Service redirects back to the client redirect URL with the authorization code and state added to the URL.
##Response URL https://<redirect_URL>?code=<code_value>=&state=<state_value> ###Client should validate state received is same as one sent in request. - Capture the code value from the above response and make the
following request to Oracle Identity Cloud
Service to get the access
token.
##Syntax curl -i -H 'Authorization: Basic <base64-clientid-secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=authorization_code&code=<authz-code>&redirect_uri=<client-redirect-uri> ###where #### <base64-clientid-secret> - BAse 64 encode clientId:ClientSecret #### <authz-code> - code value received as response on redirect. #### <client-redirect-uri> - Redirect URI, in client application. ##Example curl -i -H 'Authorization: Basic MDMx..NGY1' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<idcs_host>/oauth2/v1/token -d 'grant_type=authorization_code&code=AQAg...3jKM4Gc=&redirect_uri=https://app.getpostman.com/oauth2/callback - Capture the
access_tokenandrefresh_tokenfrom the response.{ "access_token": "eyJ4NXQjG...dfsdfsFgets2ed", "token_type": "Bearer", "expires_in": 3600, "refresh_token": "AQAgY2MzNjVlOTVhOTRh...vM5S0MkrFSpzc=" } - Use the
access_tokenin the authorization header to invoke the Oracle Integration trigger endpoint.curl --location --request GET 'https://OIC host/OIC endpoint' \ --header 'Authorization: Bearer eyJ4NXQjG...dfsdfsFgets2ed' - To update the access token, use the refresh token and make the request to Oracle Identity Cloud Service.
- Capture the
access_tokenandrefresh_tokenfrom a response for further use.curl -i -H 'Authorization: Basic <base64-clientid-secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=refresh_token&refresh_token=<refresh_token>' ##Example curl -i -H 'Authorization: Basic OGQyM...ZDA0Mjcz' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://IDCS-Service-Instance.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=refresh_token&refresh_token=AQAgY2MzNjVlOTVhOTRh...vM5S0MkrFSpzc='
- To fetch the authorization code, make the following request
from the
browser.
Prerequisites for Resource Owner Password Credentials
Perform the following tasks.
- Validate the Oracle Integration application and user roles:
- Verify that the Is Refresh Token Allowed option is enabled for the Oracle Integration Oracle Identity Cloud Service application.
- Check under the Configuration >
Resources section of
Applications. Note also that there is a
special predefined scope
(urn:opc:resource:consumer::all) that allows
the triggering of integrations with OAuth.
- Add the appropriate users to the various Oracle Integration roles. For standard/production configurations, use the ServiceUser role. (See Oracle Integration Service Roles in Provisioning and Administering Oracle Integration 3.)
- To assign the user, go to the Application
Roles section of the application.
- Configure the client application:
To trigger the integration with OAuth, a client application is required.
- In the Oracle Identity Cloud
Service Console, go to the
Applications section to create a new
application that allows you to trigger an integration with OAuth.

- Click Add.
- Select Confidential
Application.
- Complete the Details page, and go to
the Client page.
- On the Client page, select
Configure this application as a client now
and add the following.
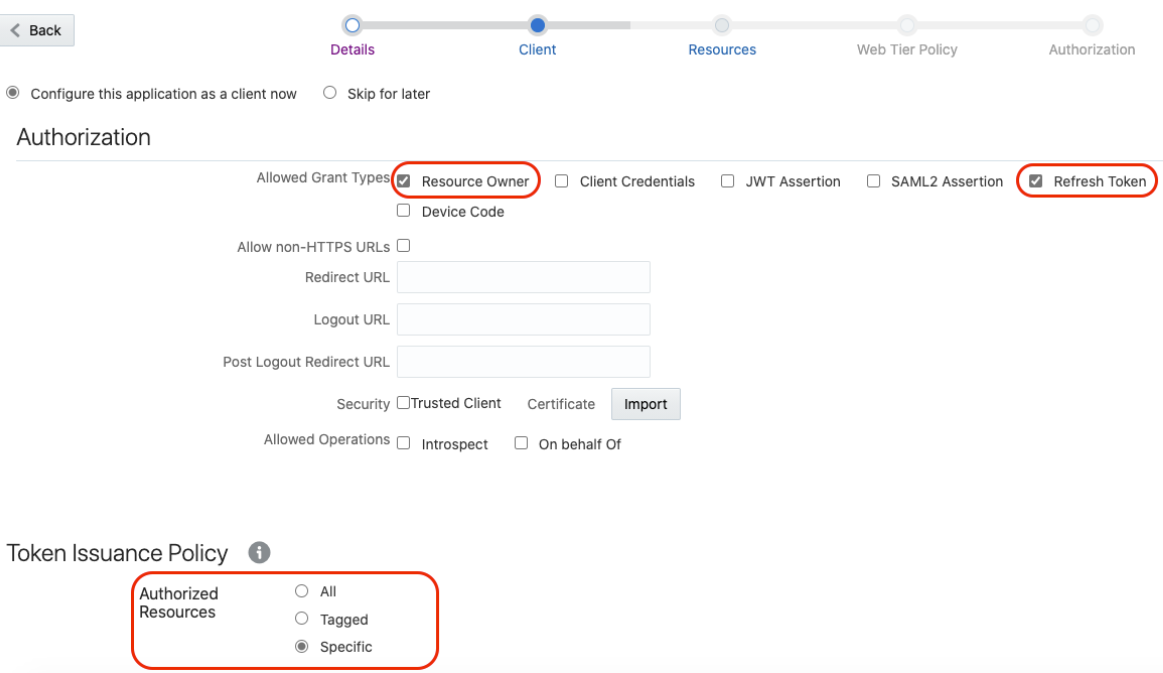
- Select Resource Owner and Refresh Token for Allowed Grant Types.
- Select Specific in the
Authorized Resources section.
- Click Add Scope under the
Resources section.

- Find the Oracle Integration application.

- Add the scope containing
urn:opc:resource:consumer::all, and
click >.

The scope containing urn:opc:resource:consumer::all is added.

- Save your changes.
- Click through the remaining wizard pages without making changes and save the application.
- Activate the application for use.
- In the Oracle Identity Cloud
Service Console, go to the
Applications section to create a new
application that allows you to trigger an integration with OAuth.
- Validate the client application:
- To fetch the access client, make a request to Oracle Identity Cloud
Service with the user name and password in the
payload.
##Syntax curl -i -H 'Authorization: Basic <base64Encoded_clientid:secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=password&username=<user-name>&password=<password>&scope=<App_Scope>%20offline_access' ###where #### <base64-clientid-secret> - Base 64 encode clientId:ClientSecret #### <username> - user for token needs to be issued (must be in serviceuser role). #### <password> - password for above user #### <app_scope> - Scope added while creating application in client configuration section (Ends with urn:opc:resource:consumer::all) ##Example curl -i -H 'Authorization: Basic OGQyM...ZDA0Mjcz' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<idcs_host>/oauth2/v1/token -d 'grant_type=password&username=sampleUser&password=SamplePassword&scope=https://<Resource_APP_Audience>urn:opc:resource:consumer::all%20offline_access' - Capture the
access_tokenandrefresh_tokenfrom the response.{ "access_token": "eyJ4NXQjG...dfsdfsFgets2ed", "token_type": "Bearer", "expires_in": 3600, "refresh_token": "AQAgY2MzNjVlOTVhOTRh...vM5S0MkrFSpzc=" } - Use the
access_tokenin the authorization header to invoke the Oracle Integration trigger endpoint.curl --location --request GET 'https://OIC host/OIC endpoint' \ --header 'Authorization: Bearer eyJ4NXQjG...dfsdfsFgets2ed' - To update the access token, use the refresh token and make a request to Oracle Identity Cloud Service.
- Capture the
access_tokenandrefresh_tokenfrom the response for further use.curl -i -H 'Authorization: Basic <base64-clientid-secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=refresh_token&refresh_token=<refresh_token>' ##Example curl -i -H 'Authorization: Basic OGQyM...ZDA0Mjcz' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=refresh_token&refresh_token=AQAgY2MzNjVlOTVhOTRh...vM5S0MkrFSpzc='
- To fetch the access client, make a request to Oracle Identity Cloud
Service with the user name and password in the
payload.
Prerequisites for Client Credentials
- Configure the client application.
- In the Oracle Identity Cloud
Service Console, go to the
Applications section to create a new
application that allows you to trigger an integration with OAuth.

- Click Add.
- Select Confidential Application.
- Complete the Details page, and click Next.
- On the Client page,
select Configure this application as a client
now, and complete the following:
- Select Client Credentials from the Allowed Grant Types list.
- Select Specific in the Authorized Resources area of the Token Issuance Policy section.
- Click Add Scope under the Resources section.
- Find the Oracle Integration application, and click
>.
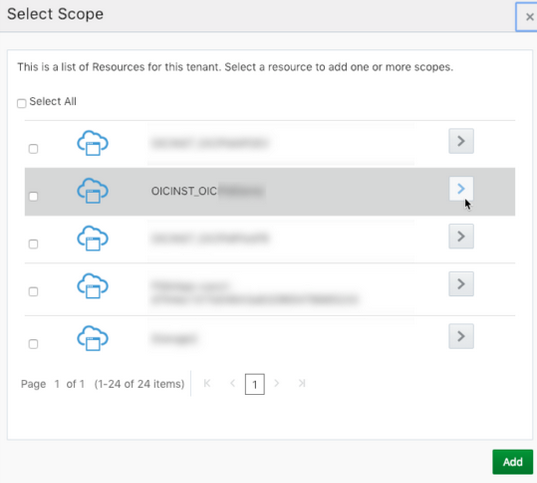
- Add the scope containing urn:opc:resource:consumer::all.
- Save your changes.
- Click through the remaining wizard pages without making changes and save the application.
- Activate the application for use.
- In the Oracle Identity Cloud
Service Console, go to the
Applications section to create a new
application that allows you to trigger an integration with OAuth.
- Add roles to the client application.
- Go to the Application Roles tab of the Oracle Identity Cloud Service application.
- Select Assign Applications for the
ServiceUser role.
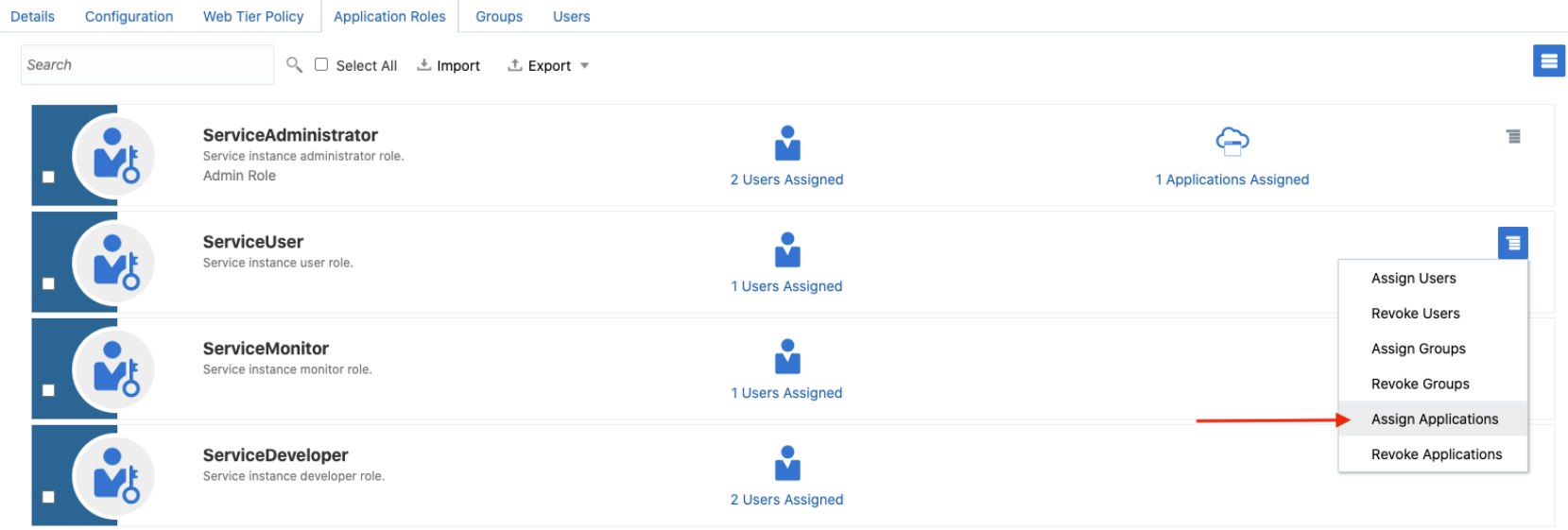
- Validate the client application.
- Fetch the access client to make an access token request to
Oracle Identity Cloud
Service with the client
credentials.
##Syntax curl -i -H 'Authorization: Basic <base64Encoded clientid:secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=client_credentials&scope=<app scope>' ###where #### <base64-clientid-secret> - Base 64 encode clientId:ClientSecret #### <app scope> - Scope added while creating application in client configuration section (Ends with urn:opc:resource:consumer::all) ##Example curl -i -H 'Authorization: Basic OGQyM...ZDA0Mjcz' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<idcs_host>/oauth2/v1/token -d 'grant_type=client_credentials&scope=https://<Resource APP Audience>urn:opc:resource:consumer::all' - Capture the
access_tokenfrom the response.{ "access_token": "eyJ4NXQjG...dfsdfsFgets2ed", "token_type": "Bearer", "expires_in": 3600 } - Use the
access_tokenin the authorization header to invoke the trigger endpoint.curl --location --request GET 'https://OIC host/OIC endpoint' \ --header 'Authorization: Bearer eyJ4NXQjG...dfsdfsFgets2ed'
- Fetch the access client to make an access token request to
Oracle Identity Cloud
Service with the client
credentials.