Manage User Roles and Privileges on Autonomous AI Database
There are several ways to manage user privileges and roles on Autonomous AI Database. You can use Oracle Database Actions Database Users card or client-side tools to connect to the database to mange privileges and roles.
- Manage Users and User Roles on Autonomous AI Database - Connecting with Database Actions
You can manage user roles for Autonomous AI Database users with Oracle Database Actions. The same steps also let you modify account settings for a user. - Manage User Privileges on Autonomous AI Database - Connecting with a Client Tool
Autonomous AI Databases come with a predefined database role namedDWROLE. This role provides the common privileges for Autonomous AI Database users. Depending on the usage requirements you may also need to grant individual privileges to users.
Parent topic: Manage Users
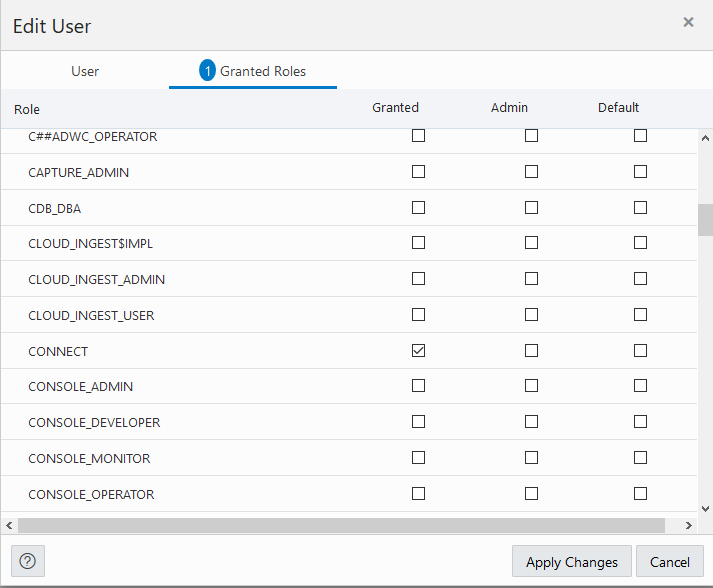
Manage Users and User Roles on Autonomous AI Database - Connecting with Database Actions
You can manage user roles for Autonomous AI Database users with Oracle Database Actions. The same steps also let you modify account settings for a user.
See The Database Users Page for more information on Database Actions Database Users.
See Create Users on Autonomous AI Database with Database Actions for information on using Database Actions.
Manage User Privileges on Autonomous AI Database - Connecting with a Client Tool
Autonomous AI Databases come
with a predefined database role named DWROLE. This role provides the
common privileges for Autonomous AI Database users.
Depending on the usage requirements you may also need to grant individual privileges to
users.
The privileges in
DWROLE are the following:
CREATE ANALYTIC VIEW CREATE ATTRIBUTE DIMENSION ALTER SESSION CREATE HIERARCHY CREATE JOB CREATE MATERIALIZED VIEW CREATE MINING MODEL CREATE PROCEDURE CREATE SEQUENCE CREATE SESSION CREATE SYNONYM CREATE TABLE CREATE TRIGGER CREATE TYPE CREATE VIEW READ,WRITE ON directory DATA_PUMP_DIR EXECUTE privilege on the PL/SQL package DBMS_CLOUD EXECUTE privilege on OCI PL/SQL SDK