1 Prerequisites
The following sections provide information about the tasks that you need to perform before connecting your Java applications to Oracle Autonomous Database using Oracle JDBC driver and Universal Connection Pool.
1.1 Prerequisites (one-way TLS)
This section lists prerequisites for one-way TLS authentication.
1.1.1 Provisioning an Oracle Autonomous Database Instance
This section describes how to provision an Oracle Autonomous Database Instance if you have not provisioned it already.
Click these links to walk through the steps to provision an Oracle Autonomous Database Instance.
Remember the password that you set while provisioning the Autonomous Database for the ADMIN user. For demonstration purposes, the ADMIN user is used, but it is recommended to create other database users either using Oracle SQL Developer or Database Actions.
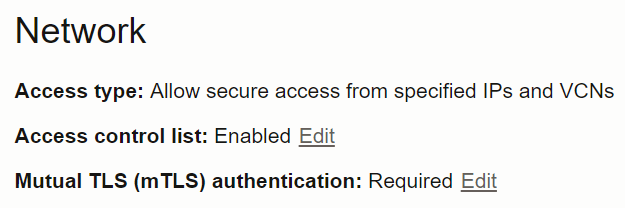
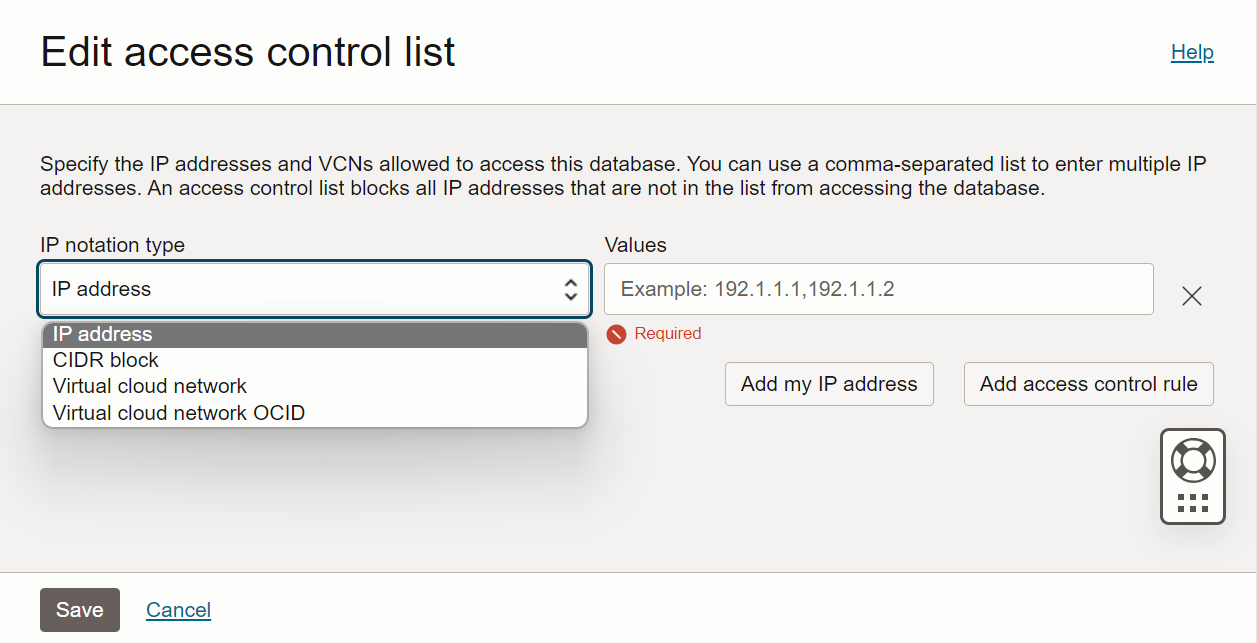
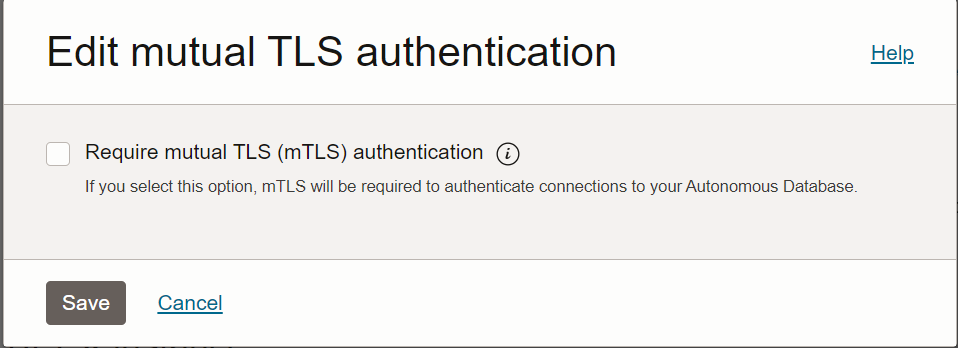
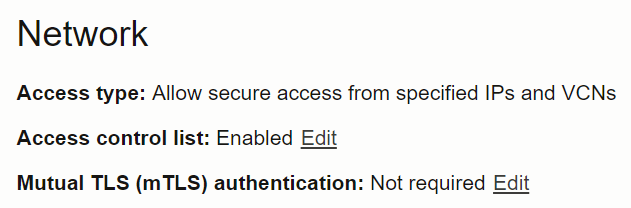
1.1.2 Disabling Mutual TLS (mTLS) Requirement
This section lists the steps to disable the mutual TLS (mTLS) requirement and to enable both mTLS and one-way TLS connections.
See Also:
Using Oracle Autonomous AI Database Serverless for more information.1.1.3 Installing JDK 8
This section lists the step to install JDK 8.
Note:
Ensure that you useJDK8u162 or a later version. Use java -version to check the JDK version that you have installed. To check the JDBC driver version, type java -jar ojdbc8.jar.
1.1.4 Downloading a Sample Program from Github
This section lists the steps to download a sample program from Github.
1.1.5 Recent Changes to Database Connectivity
This section lists different versions of JDBC-thin that support host name-based matching.
DigiCert retired the Organizational Unit (OU) field for all public TLS/SSL certificates to comply with industry standards as of August 2022 per their announcement. This means that the public TLS/SSL certificates issued by DigiCert will no longer have an OU field.
See Also:
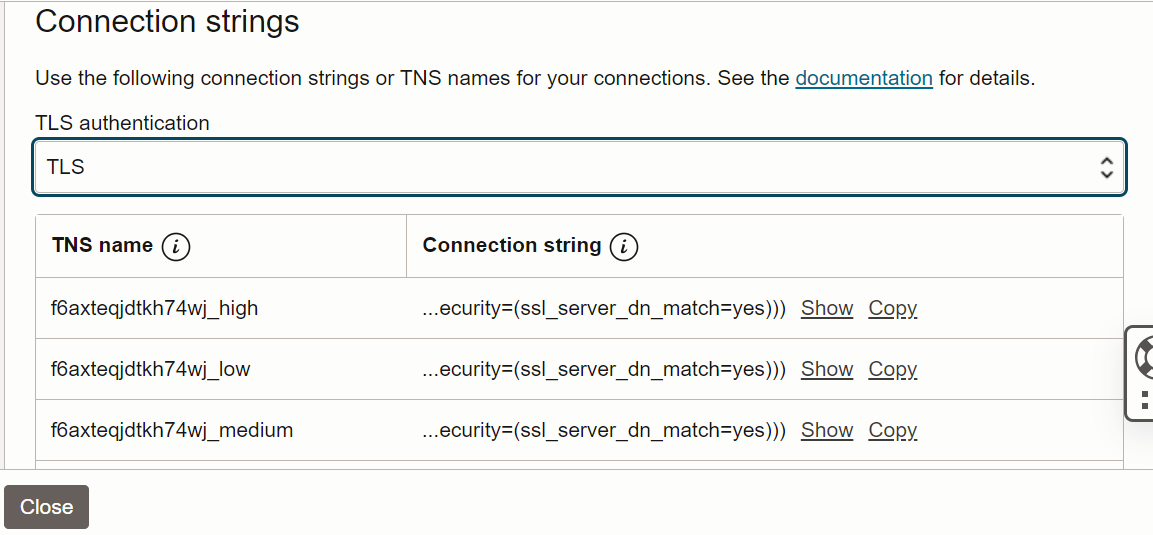
MOS Note 2911553.1To avoid disruption to applications connecting to Oracle Autonomous Database Serverless during the server side certificate change while preserving security, you must use host name-based matching (Domain Name (DN) matching) of the server certificate (for TLS server-authentication).
- 21.6 (or later) or 19.15 (or later). These are the recommended versions that support
(security=(ssl_server_dn_match=yes))in the TNS connection string. - Other versions that require turning on host name-based matching explicitly are:
- 21.5 (or before) and 19.14 (or before)
- 18.21.0.0-patched-for-bug-28492769 and 12.2.0.1-Patched-for-bug-28492769
- 12.1.0.2 and 11.2.0.4 with patch for bugs 28492769 and 19030178 (for host name-based matching and TLS v1.2 support)
- You must also explicitly turn on DN matching using one of the following methods:
- Using a program:
prop.setProperty("oracle.net.ssl_server_dn_match", "true") - Setting a Java system property:
-Doracle.net.ssl_server_dn_match=true
- Using a program:
See Also:
Oracle JDBC Drivers Archive Page1.2 Prerequisites (mutual TLS)
This section lists prerequisites for mutual TLS authentication.
1.2.1 Provisioning an Oracle Autonomous Database Instance
This section describes how to provision an Oracle Autonomous Database Instance if you have not provisioned it already.
Click these links to walk through the steps to provision an Oracle Autonomous Database Instance.
Remember the password that you set while provisioning the Autonomous Database for the ADMIN user. For demonstration purposes, the ADMIN user is used, but it is recommended to create other database users either using Oracle SQL Developer or Database Actions.
1.2.2 Obtaining Client Credentials
This section lists the steps to obtain client credentials.
wallet_[dbname].zip) contain the required wallet files and the tnsnames.ora file that allows you to connect using a mTLS connection, providing enhanced security for authentication and encryption.
1.2.3 Installing JDK 8
This section lists the step to install JDK 8.
Note:
Ensure that you useJDK8u162 or a later version. Use java -version to check the JDK version that you have installed. To check the JDBC driver version, type java -jar ojdbc8.jar.
1.3 Additional Step for Changed Connection String
This section includes an additional step that is required to be performed when you change the Autonomous Database Serverless connection string.
Autonomous Database Serverless connect strings contain the host name ...(HOST=xyz)..., which depends on the region. For example, in the Chicago region, the host name would be adb.us-chicago-1.oraclecloud.com. If you have replaced the default host name with an IP address or a custom host name, then host name-based DN matching will fail.
The solution is to add a new entry to your /etc/hosts file using the original Autonomous Database Serverless domain suffix. Your connection string should then use this new name. For example, add an entry localtunnel.adb.us-chicago-1.oraclecloud.com that resolves to your custom IP address and use that name in the JDBC connection string.