Configure a Microsoft SharePoint Online Content Connector
Microsoft SharePoint Online is a web-based document management and storage system. After you configure and enable a Microsoft SharePoint Online content connector, you can connect to it and pull content from Microsoft SharePoint Online into Oracle Content Management.
A Microsoft SharePoint Online content connector enables you to import assets from the Microsoft SharePoint Online repository into Oracle Content Management. As an Administrator or Developer, you can configure a Microsoft SharePoint Online Content Connector from the Integrations menu in an Oracle Content Management instance.
To configure a Microsoft SharePoint Online content connector:
- Get the Oracle Content Management host name and authorization URL
details.
- Sign in to Oracle Content Management as an Administrator or Developer.
- Click Integrations in the Administration area of the navigation menu on the left.
- In the Integrations menu, choose Content Connectors.
- Click the check box next to the Microsoft SharePoint Online content connector.
- Click Edit, or you can click the link to get to the Edit page.
- On the General tab, note the Redirect
URL, which will be in this
format:
https://<hostname>.<domainname>.com:<port>/documents/web/AR_COMPLETE_AUTHORIZATIONThe Redirect URL field is truncated. Double-click the field to copy the value to your clipboard. You'll need to provide this value later on the Azure app registration page.
- Create a SharePoint Online app:
- Sign in to Microsoft Azure at https://portal.azure.com/:
- Pick an account that has your Microsoft user name.
- Enter your Microsoft password.
- Choose Office365.
- Click Sign in.
- Click Yes to stay signed in and reduce multiple sign-ins.
- On the Azure services page, click App registrations.
- On the App registrations page, click New registration.
- On the Register an application page, enter a name and choose the account types that can use the application. At the bottom, paste a redirect URL and then click Register.
- On your application's page, click Certificates & secrets in the left menu, and then click the New client secret button on the page.
- Under Add a client secret, enter a description for your client secret, select Never under Expires, and then click Add.
- Click the Copy to clipboard icon on the bottom right to record the secret. You'll need to enter it later in the Client Secret field on the Additional Fields page for the content connector. Also click Copy to clipboard to record other details.
- On the API permissions page, click Add a
permission to add a SharePoint Online permission, such as
User.Read, a Delegated
permission for SharePoint Online to sign in as the user and access an API.
Another permission you might want to add is off-line
access, which enables the refresh token.
In addition to User permissions, you can grant AllSites, Myfiles, Sites, and TermStore permissions.
- Sign in to Microsoft Azure at https://portal.azure.com/:
- Add the SharePoint Online connector to a repository.
- In Oracle Content Management, select Integrations on the left navigation menu.
- On the Integrations page, choose Content Connectors from the drop-down menu.
- In the list of content connectors, click the name of the SharePoint Online content connector.
- Configure the Microsoft SharePoint Online content connector in Oracle Content Management.
- On the General tab:
- The Name, Description, Connector service URL, and Redirect URL fields are prepopulated.
- In the Connector tags field, you can assign tags that will be applied to assets pulled from the content connector (for example, the content connector name). This lets you search for all items from that content connector in an asset repository.
- Make sure Enabled for end users
is selected.
You can review the Terms of use and Privacy Policy below the Enable for end users button.
- Click the Additional Fields tab.
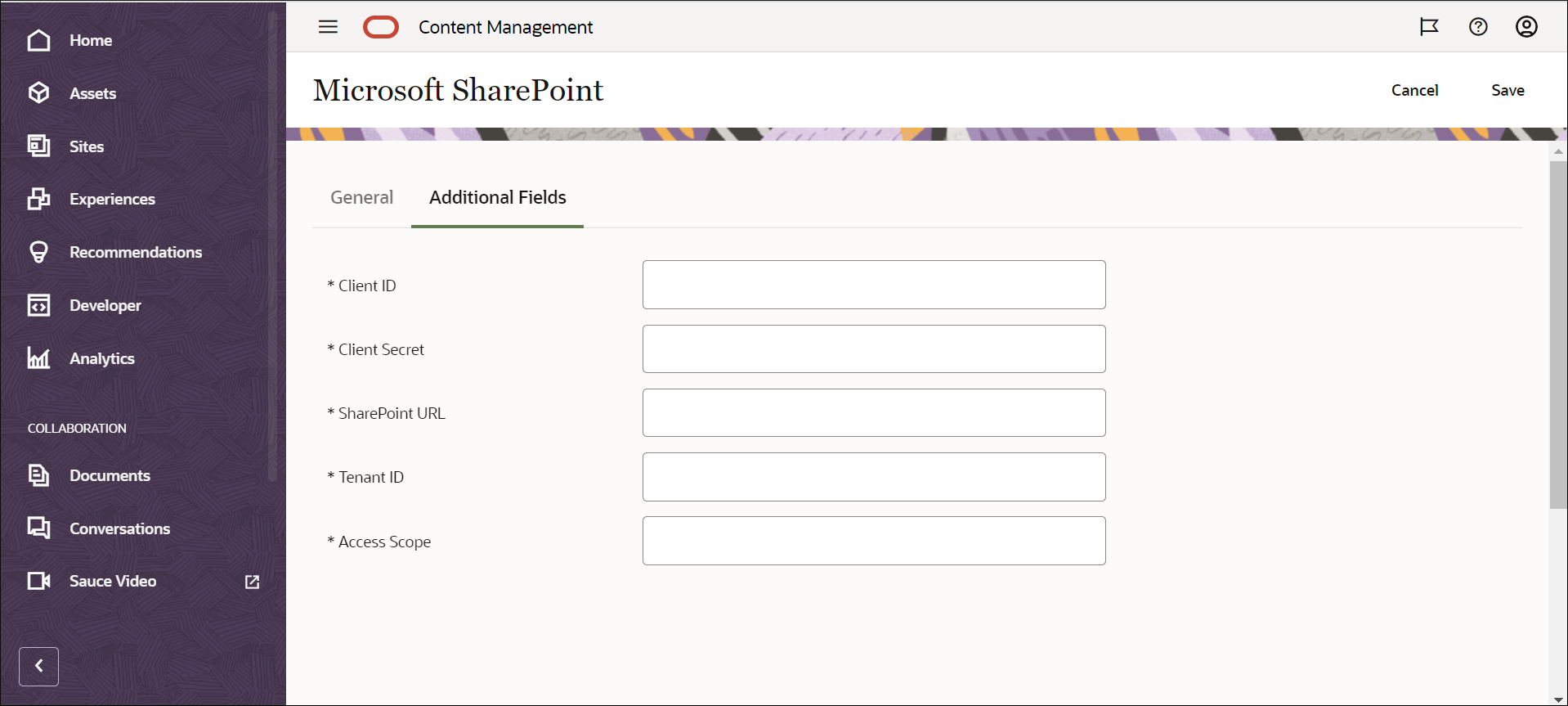
Description of the illustration sharepoint-connector-custom-fields.png
Enter the values for the following fields, some of which you recorded earlier:
- Client ID: the value of the Application ID from the Azure app registration.
- Client Secret: the value of the client secret generated in the Azure app registration.
- SharePoint URL:
https://<company name>.sharepoint.com, this is the SharePoint URL, URL of your tenant, and URL of site collection. - Tenant ID: the Directory (tenant) ID from the Azure app registration.
- Access Scope: offline_access
https://<company name>.sharepoint.com/AllSites.Read
- When you're done, click Save.
- On the General tab:
- Add the connector to a repository.
- Click Content in the Administration area of the navigation menu on the left.
- Open an existing repository or click Create to create a new one.
- If you're creating a new repository, specify the repository name, publishing channels, languages, and other options.
- Under Content Connectors, select one or
more connectors to associate with the repository.
This menu lists all the content connectors that have been configured and enabled in your Oracle Content Management instance.
If any of the connectors you select have content types associated with them, the types appear under Content Types.
After a Microsoft SharePoint Online content connector is configured, enabled, and associated with a repository, it's available in the asset repository for Oracle Content Management users to download content, through the Add drop-down menu Import from Microsoft SharePoint option on the Assets page.
Note:
An authorized application for a Microsoft SharePoint Online content connector must provide a link tohttps://account.live.com/consent/Manage, or to another location
specified for a SharePoint Online content connector, with a clear indication that end
users can go to that Microsoft site to revoke permissions at any time. If end users must
take additional steps to disable the authorized application's access to end-user
information, then the application must clearly indicate to end users the additional
steps required to disable access. These requirements do not apply where Microsoft
provides the end-user web interface.