Integrate with Oracle Content Management Using OAuth
Developer access to Oracle Content Management (OCM) REST APIs for administering system or managing assets, files, or other resources is supported only via token-based authorization. To access the OCM REST APIs, you need an OAuth 2 access token to use for authorization.
You need to create an OAuth client application to be able to request the access token. OAuth client is simply an HTTP client that must be registered as an OAuth 2 client using the Oracle Identity Cloud Service (IDCS) or Identity and Access Management (IAM) with Identity Domains administration console.
If single sign-on (SSO) is already established with IDCS (the same that OCM points to), then we do not need OAuth. The SSO should be sufficient since OCM REST APIs support SSO as well. If the UI will not have an active SSO session, then OAuth should be used.
- Client Credentials: When using the Client Credentials grant
type, the client authenticates with the OAuth service and then requests an
access token. With this grant type, the OAuth client application presents its
own credentials to obtain an access token for the client-initiated requests to
access a protected resource. This access token is either associated with the
client’s own resources, and not a particular resource owner, or is associated
with a resource owner for whom the client is otherwise authorized to act.
Trusted applications (such as back-end services) may request access tokens directly on behalf of users. This is an OAuth two-legged authorization flow. Another use case of this flow or grant type is when integrating application users are not users of OCM, (i.e. they reside in a different identity store other than OCM service’s identity store and hence OAuth application client credentials are used to make API calls to OCM).
To know more about Client Credentials grant type, see Client Credentials Grant Type.
- Authorization Code: The OAuth web applications typically
need to first validate the user's identity and optionally obtain the user's
consent. This is an OAuth three-legged authorization flow and in this case, the
Authorization Code grant type is used.
In this case, you want to obtain an authorization code first by using an authorization server as an intermediary between the client application and the resource owner. An authorization code is returned to the client through a browser redirect after the resource owner gives consent to the authorization server. The client then exchanges the authorization code for an access (and often a refresh) token. The resource owner credentials are never exposed to the client. To know more about Authorization Code grant type, see Authorization Code Grant Type.
- Resource Owner: When using the Resource Owner grant type,
the resource owner's password credentials (user name and password) can be used
directly as an authorization grant to obtain an access token. Therefore, this
grant type is used when the resource owner has a trust relationship with the
client, such as a computer operating system or a highly privileged application,
because the client must discard the password after obtaining the access token.
To know more about Resource Owner grant type, see Resource Owner Password Credentials Grant Type.
- Log in to the Oracle Identity Cloud Service (IDCS) or IAM with Identity Domains administration console.
- Create an OAuth client application and make note of the client ID and client secret.
- Use the client ID and client secret to request an access token from the Oracle Identity Cloud Service OAuth Service.
- Include the access token in the appropriate HTTP header when you make REST API calls.
For content management and sites management REST APIs, you acquire the client ID and secret required to get the access token from Oracle Identity Cloud Service (IDCS) or IAM with Identity Domains. For the two-legged OAuth, you use client credentials to acquire the client ID and secret. For the three-legged OAuth, you use an authorization code to acquire the client ID and secret.
Note:
The Oracle Cloud Console is merging IDCS into Identity and Access Management (IAM) with Identity Domains. You can check if your cloud account is using identity domain or not.Sign in to the Oracle Cloud Console. In the navigation menu, click Identity & Security. Under Identity, check for Domains. If you see Domains, then your cloud account has been updated. For details, see Oracle Cloud Infrastructure Documentation.
Cloud Account Using IAM Identity Domain
Access OCM Using Client Credentials (Two-Legged OAuth in Identity Domain)
For this OAuth flow, the token is requested for the client application and calls to Oracle Content Management (OCM) APIs are made using this client application’s token. This OAuth client application needs to be added to the OCM roles to have appropriate OCM access.
The Identity Domain Administrator or Application Administrator of the tenant creates an OAuth client for the developer with the required privileges.
The Identity Domain Administrator performs the following steps to get an access token:
Create an OAuth Client and Acquire a Client ID and Secret
The Identity Domain Administrator or an Application Administrator of the tenant creates an OAuth client for the developer with the required privileges. To do this, perform the following steps:
- Sign in to the Oracle Cloud
Console.
https://cloud.oracle.comNavigate to Identity & Security. Under Identity, check for Domains. Select the domain (default or newly created) while creating an application, you will see the Applications option in the left menu as shown in the figure below.
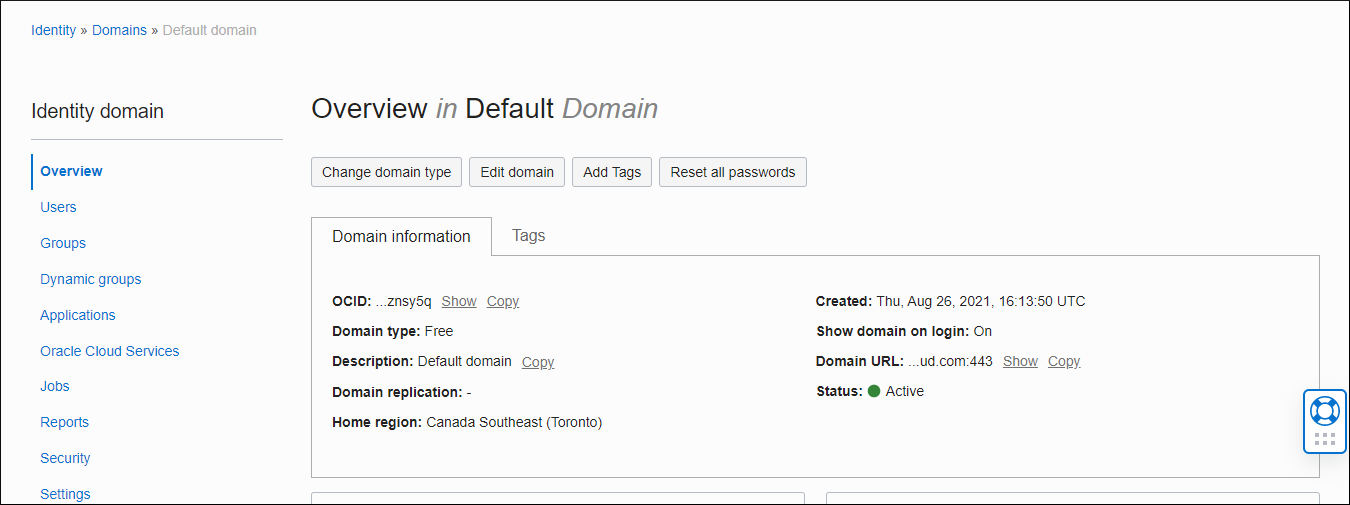
Description of the illustration identity-domain.png - Click to add a new application in the Applications section.
- Select Confidential Application. The Confidential Applications use OAuth 2.0 and can protect their OAuth client ID and client secret. To know more about Confidential Applications, see Add a Confidential Application.
- Give the application a name and, optionally, a description, and click Next.
- Choose to configure this application as a client.
- Select the client credentials grant type on the Authorization screen.
- Scroll down to the Token Issuance Policy section and, under Resources, click add scope to give the application access to the required Oracle Content Management instance.
- Click the right arrow to select the scope.
The only scope required is the one ending in
urn:opc:cec:all.Select the checkbox next to it and then click Add.
- Click Next until the end of the
train.
The Resources, Web Tier Policy, and Authorization stops are related to applications that have some resource authenticated or authorized by Identity Domain; for example, a web application. This isn’t relevant in the case of a simple server-server client, which is discussed here.
- Click Finish.
- Note the Client ID and Client Secret values because you’ll need those to get a token later.
- Check Activate and then click Save to enable the application.
You can decide how to handle the client ID and secret.
Note:
Just as a regular user, an OAuth client with the client credentials requires relevant permission on objects in your Oracle Content Management instance to be able to perform actions using REST API for Content Management. For example, it needs to be a repository member with Contributor permission to create assets in it, or a Manager on the repository to modify its settings. In the Oracle Content Management web UI, you can use the Members dialog to find your OAuth client by name and add it to the required object. A newly created OAuth client will appear in search only after the next hourly Identity Domain sync is complete.Grant the Required Oracle Content Management Roles to the Client
You can grant the required roles through the Oracle Cloud administration console.
- Sign in to the Oracle Cloud administration console.
- Click Oracle Cloud Services.
- Select the Oracle Content Management service instance for which you need privileges. This instance name would have been provided by your account administrator.
- Click Application Roles and then right-click the burger menu on the right.
- Choose Assign Applications.
- Assign the client application to the roles based on the access that is required to OCM objects. For OCM application roles, see Application Roles.
- Save the changes.
Acquire an Access Token from Identity Domain for the Required Resource
Use the client ID and secret obtained earlier from the OAuth client to get an AccessToken for the resource.
A sample curl command to acquire an access token follows:
AccessToken Request
curl -X POST \
https://<idcs tenantname that is protecting this service>/oauth2/v1/token \
-H 'Authorization: Basic <Base64 encoded clientID:clientSecret>' \
-d 'grant_type=client_credentials&scope=<scope string>'curl -X POST 'https://idcs-99463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/token' \
-H 'Authorization: Basic Y2RlNGQyMDZjYTE1NGM2Yjg2NGMyMTJiMjVmMTY3MmE6MWM0ZTAyNGQtZDU4MC00MzEzLWJkZjMtZTQyMGQzMzgzZTY2' \
-d'grant_type=client_credentials&scope=https://50B904E53A6F4EA1B45F30E225EA99B.cec.ocp.oc-test.com:443/urn:opc:cec:all'Identity Domain returns the key and value for an access token:
{"access_token":"<access-token-value>}"You can copy the access token value.
Note:
The refresh token is not included in the Client Credentials grant type flow.Use the Access Token to Access the Oracle Content Management Resource
Once the access token is acquired, call the Oracle Content Management endpoint to access the resource.
A sample curl command follows.
curl -X GET <Oracle-Content-Management-URL>/sites/management/api/v1/sites \
-H 'Authorization: Bearer <Access Token acquired from previous step>'\
-H 'Content-Type: application/json'Access OCM Using Authorization Code (Three-Legged OAuth Flow in Identity Domain)
In this flow, a client application is created to acquire the client ID and secret, which are used by the client browser. The client browser then redirects the user to Identity Domain to log in with the username and password. Upon successful authentication, an authorization code is sent with the redirect URL. An access token is requested from Identity Domain using this authorization code. Thus, the resource owner credentials are never exposed to the client in this flow.
Because this is a user token, the user requesting the token needs to have relevant Oracle Content Management roles as the user’s access to the OCM objects will be checked against assigned roles.
The Identity Domain Administrator performs the following steps to get an access token:
Create an OAuth Client and Acquire a Client ID and Secret
The Identity Domain Administrator or an Application Administrator of the tenant creates an OAuth client for the developer with the required privileges. To do this, perform the following steps:
- Sign in to the Oracle Cloud
Console.
https://cloud.oracle.comNavigate to Identity & Security. Under Identity, check for Domains. Select the domain (default or newly created) while creating an application, you will see the Applications option in the left menu as shown in the figure below.

Description of the illustration identity-domain.png - Click to add a new application in the Applications section.
- Select Confidential Application. The Confidential Applications use OAuth 2.0 and can protect their OAuth client ID and client secret. To know more about Confidential Applications, see Add a Confidential Application.
- Give the application a name and, optionally, a description, and click Next.
- Choose to configure this application as a client.
- Select the Authorization code grant type on the Authorization screen.
- Enter a redirect URL value to point to the URL where the user needs to be redirected after authorization.
- Enter a Post logout URL value to
point to the Oracle Content Management service administration
console.
Note:
It is not a mandatory field while creating a client application with the Authorization Code grant type. As mentioned in the IDCS documentation (see Using OpenID Connect for Log Out), this could be again any client-specific URL to where the redirection happens after logout. - Scroll down to the Token Issuance Policy section and, under Resources, click add scope to give the application access to the required Oracle Content Management instance.
- Click the right arrow to select the scope.
The only scope required is the one ending in
urn:opc:cec:all.Select the checkbox next to it and then click Add (note down the scope string as it will be used later on while requesting the access token).
- Click Next until the end of the
train.
The Resources, Web Tier Policy, and Authorization stops are related to applications that have some resource authenticated or authorized by Identity Domain; for example, a web application. This isn’t relevant in the case of a simple server-server client, which is discussed here.
- Click Finish.
- Note the Client ID and Client Secret values because you’ll need those to get a token later.
- Check Activate and then click Save to enable the application.
The client can store the Client ID and Client Secret values securely in a credential store.
Grant the Required Oracle Content Management Roles to the Client
You can grant the required OCM roles to the user through the Oracle Cloud administration console.
- Sign in to the Oracle Cloud administration console.
- Click Oracle Cloud Services.
- Select the Oracle Content Management service instance for which you need privileges. This instance name would have been provided by your account administrator.
- Click Application Roles.
- Right-click the burger menu on the right. Choose Assign Users.
- Assign the user to the roles based on the access that is required to OCM objects. For information about OCM application roles, see Application Roles.
- Save the changes.
Acquire an Access Token from Identity Domain for the Required Resource
Acquisition of the access token consists of multiple steps:
- The UI of the customer’s application makes authorization code requests
for the user to Identity Domain.
- The UI makes a GET call to Identity Domain
with the URL given below. No authorization is
required (this needs to be accessed via browser as
this will open login UI, Postman will not work in
this
case).
Where nonce-value and state are optional.https://<IDCS-service-instance>/oauth2/v1/authorize?client_id=<clientid>&response_type=code&redirect_uri=<client-redirect-uri>&scope=<scope string from Step 9 of Create oauth client>&nonce=<nonce-value>&state=1234Example:
https://idcs-4c463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/authorize?client_id=51d06799e2aa4c749a79276cf7d24ca7&response_type=code&redirect_uri=https://p2qaextradp1srvc1-qucm2019927ac99.cec.ocp.oc-test.com/documents&scope=https://50B904E53A6F4EA1B45F30E225E6C99B.cec.ocp.oc-test.com:443/urn:opc:cec:all&nonce=12345&state=12345 - Identity Domain shows the login UI.
- The user logs in to the login UI. The
Identity Domain redirects to redirect URL with the
Authorization code as shown
below:
<redirection_url>?code=<auth_code>&state=12345Example:
https://p2qaextradp1srvc1-qucm2019927ac99.cec.ocp.oc-test.com/documents?code=AgAgZTM5MGMzODVjNzY3NGZhNzgzMmExMTI0YmU1ZDBiOTYIABC_fyt25KEcHP9-Hmjkh9y1AAAAMPia8fMCbuzkdk10_CzsrqZ-EtGwsI_MCPFr1Y3gt25EhrhYH65mb7vkJmPvUeKdTg&state=12345
- The UI makes a GET call to Identity Domain
with the URL given below. No authorization is
required (this needs to be accessed via browser as
this will open login UI, Postman will not work in
this
case).
- The UI makes a call to Identity Domain to get the user
token, passing
auth_codeobtained in the previous step with the following payload:Authorization: Basic <Base64 encoded clientID:clientSecret> Method: Post URL: https://<IDCS-service-instance>/oauth2/v1/token BODY (as form data): grant_type=authorization_code&code=<auth_code>Example:
curl -X POST 'https://idcs-4c463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/token' \ -H 'Authorization: Basic NTFkMDY3OTllMmFhNGM3NDlhNzkyNzZjZjdkMjRjYTY6YjZhMzc4ZmQtZjk2Mi00MTg3LWE2NzctYTBmMGI3NmEzODhj' \ -d 'grant_type=authorization_code&code=AgAgZTM5MGMzODVjNzY3NGZhNzgzMmExMTI0YmU1ZDBiOTYIABC_fyt25KEcHP9-Hmjkh9y1AAAAMPia8fMCbuzkdk10_CzsrqZ-EtGwsI_MCPFr1Y3gt25EhrhYH65mb7vkJmPvUeKdTg'Identity Domain returns the key and value for an access token:{"access_token":"<access-token-value>"}You can copy the access token value (the expiry of the access token is set to 7 days and refresh token’s to 14 days).
Note:
If one desires to create a refresh token along with access token, two additional tasks need to be performed:- While creating OAuth client, in addition to selecting grant type Authorization Code (see step 5 in Create an OAuth Client and Acquire a Client ID and Secret), you will also have to choose Refresh.
- While requesting for authorization
code, you will have to specify the additional
scope
offline_accessalong withurn:opc:cec:all(scopes are space separated) as shown below:https://idcs-4c463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/authorize?client_id=51d06799e2aa4c749a79276cf7d24ca7&response_type=code&redirect_uri=https://p2qaextradp1srvc1-qucm2019927ac99.cec.ocp.oc-test.com/documents&scope=https://50B904E53A6F4EA1B45F30E225E6C99B.cec.ocp.oc-test.com:443/urn:opc:cec:all offline_access&nonce=12345&state=12345Then using this authorization code in
/oauth2/v1/tokenwill return refresh token along with access token.
Use the Access Token to Access the Oracle Content Management Resource
Once the access token is acquired, call the Oracle Content Management endpoint to access the resource.
A sample curl command follows.
curl -X GET <Oracle-Content-Management-URL>/content/management/api/v1.1/channels \
-H 'Authorization: Bearer <Access Token acquired from previous step>'\
-H 'Content-Type: application/json'Access OCM Using Resource Owner (Identity Domain)
In this flow, the resource owner credentials are exposed to the
client. The credentials are passed in /oauth2/v1/token API to get
the token so it is important that the resource owner has a trust relationship with
the client making this API call as the client must discard the password after
obtaining the access token.
As this is a user token, the user requesting the token needs to have relevant OCM roles as the user’s access to the OCM objects will be checked against assigned roles.
To configure a confidential application to authorize a Resource Owner grant:
- Sign in to the Oracle Cloud admin console:
https://cloud.oracle.com - Click to add a new application in the Applications section.
- Select Confidential Application. Confidential Applications use OAuth 2.0 and can protect their OAuth client ID and client secret. To know more about Confidential Applications, see Add a Confidential Application.
- Give the application a name and, optionally, a description, and click Next.
- Choose to configure this application as a client.
- Select the Resource Owner grant type on the Authorization screen.
- Scroll down to the Token Issuance Policy section and, under Resources, click Add Scope to give the application access to the Oracle Content Management instance required.
- Select the correct instance.
- Click the right arrow to select the scope. The one ending in
urn:opc:cec:allis the only scope required. Select the checkbox next to it and then click Add (note down the scope string as it will be used later on while requesting the access token). - Click Next until the end of the train. The Resources, Web Tier Policy, and Authorization stops are related to applications that have some resource authenticated or authorized by Identity Domain; for example, a web application. In the case of a simple server-server client, which is discussed here, this isn’t relevant.
- Click Finish.
- Note the Client ID and Client Secret values because you’ll need those to get a token later.
- Check Activate and then click Save to enable the application.
To request a token:
- Make a form post to
<domain URL>. For Domain URL, see the figure given below.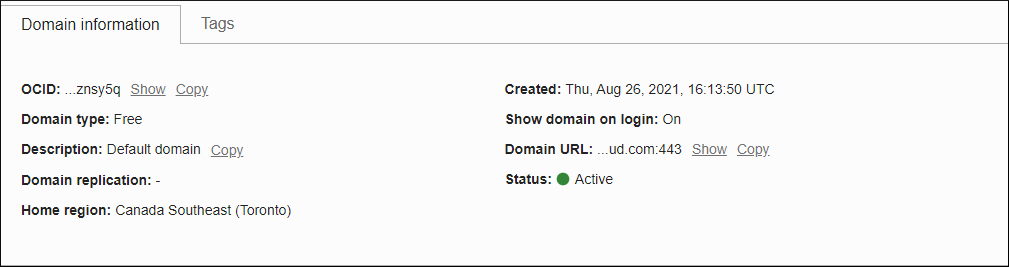
- The following table describes the fields.
Field Value grant_type password scope A scope you added previously, in step 9; for example: https:// 1DF8AB52D0FF48F6992EEA3A5715B66F.cec.dev.ocp.octest. com:443/urn:opc:cec:allusername The user name to generate the token for. password The password for the user name in the preceding field. POST /oauth2/v1/token HTTP/1.1 Host: <iam-domain-host> Authorization: Basic NTZkZWJjY2EzYjc0NDRlMWFhNjg4OGQ0ZTYzY2Y1M2Y6NDYxYzM5YjctMzJiZC00NGE0LTk4NTc tN WM1NzAyMWMzNDg4 Accept: */* Content-Type: application/x-www-form-urlencoded Content-Length: 162 grant_type=password&scope=https%3A%2F %2F1DF8AB52D0FF48F6992EEA3A5715B66F.cec. dev.ocp.octest. com%3A443%2Furn%3Aopc%3Acec%3Aall&username=<user-name>&password=<password>This results in JSON text where the token is the value of theaccess_tokenfield:{ "access_token": "eyJ4NXQjUzI1NiI6IkhoRktIMFFGeHR1UDkxLWg3QlJKSUFDMU50V2R...HUQmto_oELyjRaBp qhI75hQJYLWRKm6ozPS57tR1EYHmWABgYw_XALMT1kMuIuRxpGB2ozngpajzNNBBu2qtKg10- RzBTulKaxD25vKK1rznQ3p_XAOLK4CUUM-uG_PUOk49- JDgJjuSI74hLC1kagIlM93A2jUG3g3gdUpUCZPg", "token_type": "Bearer", "expires_in": 604800 }The token expiration time is given in seconds and is typically 7 days.
To use the token and access REST API endpoints, use the Bearer Authorization header as before.
Note:
If one desires to create a refresh token along with access token, two additional tasks need to be performed:- While creating OAuth client, in addition to selecting grant type Resource Owner (See step 6 in Create an OAuth Client and Acquire a Client ID and Secret), you will also have to choose Refresh Token.
- While requesting for token, you will have to specify
additional scope
offline_accessalong withurn:opc:cec:all(scopes are space separated) as shown below:curl -X POST 'https://idcs-4c463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/token' \ -H 'Authorization: Basic NTFkMDY3OTllMmFhNGM3NDlhNzkyNzZjZjdkMjRjYTY6YjZhMzc4ZmQtZjk2Mi00MTg3LWE2NzctYTBmMGI3NmEzODhj' \ -d 'grant_type=password&scope=https://50B904E53A6F4EA1B45F30E225EA99B.cec.ocp.oc-test.com:443/urn:opc:cec:all offline_access&username=John.Doe@test.com&password=johndoepassword#3’
This will return a refresh token along with access token.
Cloud Account Using Oracle Identity Cloud Service
The following sections describe how to use your cloud account:
Access OCM Using Client Credentials (Two-Legged OAuth Flow)
For this OAuth flow, the token is requested for the client application and calls to Oracle Content Management (OCM) APIs are made using this client application’s token. This OAuth client application needs to be added to OCM roles in Oracle Identity Cloud Service (IDCS) to have appropriate OCM access.
The Identity Domain Administrator or Application Administrator of the tenant creates an OAuth client for the developer with the required privileges and performs the following steps to get an access token:
Create an OAuth Client and Acquire a Client ID and Secret
The Identity Domain Administrator or an Application Administrator of the tenant creates an OAuth client for the developer with the required privileges. To do this, perform the following steps:
-
Go to the IDCS administration console:
https://<IDCS BaseURL>/ui/v1/adminconsole - Click to add a new application in the Applications section.
- Select Confidential Application. The Confidential Applications use OAuth 2.0 and can protect their OAuth client ID and client secret. To know more about Confidential Applications, see Add a Confidential Application.
- Give the application a name and, optionally, a description, and click Next.
- Choose to configure this application as a client.
- Select the client credentials grant type on the Authorization screen.
- Scroll down to the Token Issuance Policy section and, under Resources, click add scope to give the application access to the required Oracle Content Management instance.
- Click the right arrow to select the scope.
The only scope required is the one ending in
urn:opc:cec:all.Select the checkbox next to it and then click Add.
- Click Next until the end of the
train.
The Resources, Web Tier Policy, and Authorization stops are related to applications that have some resource authenticated or authorized by IDCS; for example, a web application. This isn’t relevant in the case of a simple server-server client, which is discussed here.
- Click Finish.
- Note the Client ID and Client Secret values because you’ll need those to get a token later.
- Check Activate and then click Save to enable the application.
Note:
Just as a regular user, an OAuth client with the client credentials requires relevant permission on objects in your Oracle Content Management instance to be able to perform actions using REST API for Content Management. For example, it needs to be a repository member with Contributor permission to create assets in it, or a Manager on the repository to modify its settings. In the Oracle Content Management web UI, you can use the Members dialog to find your OAuth client by name and add it to the required object. A newly created OAuth client will appear in search only after the next hourly IDCS sync is complete.Grant the Required Oracle Content Management Roles to the Client
You can grant the required roles through the Oracle Identity Cloud Service (IDCS) administration console.
- Log in to the IDCS administration console.
- Click Oracle Cloud Services.
- Select the Oracle Content Management service instance for which you need privileges. This instance name would have been provided by your account administrator.
- Click Application Roles and then right-click the burger menu on the right.
- Choose Assign Applications.
- Assign the client application to the roles based on the
access privilege that is required for OCM objects. For OCM
application roles, see Application
Roles.
- Save the changes.
Acquire an Access Token from Oracle Identity Cloud Service (IDCS) for the Required Resource
Use the client ID and secret obtained earlier from the OAuth client to get an AccessToken for the resource.
A sample curl command to acquire an access token follows:
AccessToken Request
curl -X POST \
https://<idcs tenantname that is protecting this service>/oauth2/v1/token \
-H 'Authorization: Basic <Base64 encoded clientID:clientSecret>' \
-d 'grant_type=client_credentials&scope=<scope string>'curl -X POST 'https://idcs-99463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/token' \
-H 'Authorization: Basic Y2RlNGQyMDZjYTE1NGM2Yjg2NGMyMTJiMjVmMTY3MmE6MWM0ZTAyNGQtZDU4MC00MzEzLWJkZjMtZTQyMGQzMzgzZTY2' \
-d'grant_type=client_credentials&scope=https://50B904E53A6F4EA1B45F30E225EA99B.cec.ocp.oc-test.com:443/urn:opc:cec:all'IDCS returns the key and value for an access token (access token expiry is set to 7 days):
{"access_token":"<access-token-value>}"You can copy the access token value.
Note:
The refresh token is not included in the Client Credentials grant type flow.Use the Access Token to Access the Oracle Content Management Resource
Once the access token is acquired, call the Oracle Content Management endpoint to access the resource.
A sample curl command follows.
curl -X GET <Oracle-Content-Management-URL>/sites/management/api/v1/sites \
-H 'Authorization: Bearer <Access Token acquired from previous step>'\
-H 'Content-Type: application/json'Access OCM Using Authorization Code (Three-Legged OAuth Flow)
In this flow, a client application is created to acquire the client ID and secret, a client browser uses these and redirects the user to IDCS to login with their username and password and on successful authentication, an authorization code is sent on the redirect URL. An access token is requested from IDCS using this authorization code. Thus, the Resource owner credentials are never exposed to the client in this flow.
As this is a user token, the user requesting the token needs to have relevant OCM roles as the user’s access to the OCM objects will be checked against assigned roles.
The Identity Domain Administrator performs the following steps to get an access token:
Create an OAuth Client and Acquire a Client ID and Secret
The Identity Domain Administrator or an Application Administrator of the tenant creates an OAuth client for the developer with the required privileges. To do this, perform the following steps:
-
Go to the IDCS administration console:
https://<IDCS BaseURL>/ui/v1/adminconsole - Click to add a new application in the Applications section.
- Select Confidential Application. The Confidential Applications use OAuth 2.0 and can protect their OAuth client ID and client secret. To know more about Confidential Applications, see Add a Confidential Application.
- Give the application a name and, optionally, a description, and click Next.
- Choose to configure this application as a client.
- Select the Authorization code grant type on the Authorization screen.
- Enter a redirect URL value to point to the URL where the user needs to be redirected after authorization. It can be any URL pointing to customer’s application.
- Enter a Post logout URL value to
point to the Oracle Content Management service administration
console.
Note:
It is not a mandatory field while creating a client application with the Authorization Code grant type. As mentioned in the IDCS documentation (see Using OpenID Connect for Log Out), this could be again any client-specific URL to where the redirection happens after logout. - Scroll down to the Token Issuance Policy section and, under Resources, click add scope to give the application access to the required Oracle Content Management instance.
- Click the right arrow to select the scope.
The only scope required is the one ending in
urn:opc:cec:all.Select the checkbox next to it and then click Add (note down the scope string as it will be used later on while requesting the access token).
- Click Next until the end of the
train.
The Resources, Web Tier Policy, and Authorization stops are related to applications that have some resource authenticated or authorized by IDCS; for example, a web application. This isn’t relevant in the case of a simple server-server client, which is discussed here.
- Click Finish.
- Note the Client ID and Client Secret values because you’ll need those to get a token later.
- Check Activate and then click Save to enable the application.
The client can store the Client ID and Client Secret values securely in a credential store.
Grant the Required Oracle Content Management Roles to the Client
You can grant the required OCM roles to the user through the Oracle Identity Cloud Service (IDCS) administration console.
- Log in to the IDCS administration console.
- Click Oracle Cloud Services.
- Select the Oracle Content Management service instance for which you need privileges. This instance name would have been provided by your account administrator.
- Click Application Roles.
- Right-click the burger menu on the right.
Description of the illustration access-rest-apis.png - Choose Assign Users.
- Assign the user to the roles based on the access level that is required for OCM objects. For information about OCM application roles, see Application Roles.
- Save the changes.
Acquire an Access Token from Oracle Identity Cloud Service (IDCS) for the Required Resource
Acquisition of the access token consists of multiple steps:
- The UI of the customer’s application makes authorization code requests
for the user to IDCS.
- The UI makes a GET call to IDCS with the URL given below. No
authorization is required (this needs to be accessed via browser as this
will open IDCS login UI, Postman will not work in this
case).
Where nonce-value and state are optional.https://<IDCS-service-instance>/oauth2/v1/authorize?client_id=<clientid>&response_type=code&redirect_uri=<client-redirect-uri>&scope=<scope string from Step 9 of Create oauth client>&nonce=<nonce-value>&state=1234Example:
https://idcs-4c463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/authorize?client_id=51d06799e2aa4c749a79276cf7d24ca7&response_type=code&redirect_uri=https://p2qaextradp1srvc1-qucm2019927ac99.cec.ocp.oc-test.com/documents&scope=https://50B904E53A6F4EA1B45F30E225E6C99B.cec.ocp.oc-test.com:443/urn:opc:cec:all&nonce=12345&state=12345 - IDCS shows the login UI.
- The user logs in to the login UI. IDCS redirects to redirect
URL with the Authorization code as shown
below:
<redirection_url>?code=<auth_code>&state=12345Example:
https://p2qaextradp1srvc1-qucm2019927ac99.cec.ocp.oc-test.com/documents?code=AgAgZTM5MGMzODVjNzY3NGZhNzgzMmExMTI0YmU1ZDBiOTYIABC_fyt25KEcHP9-Hmjkh9y1AAAAMPia8fMCbuzkdk10_CzsrqZ-EtGwsI_MCPFr1Y3gt25EhrhYH65mb7vkJmPvUeKdTg&state=12345
- The UI makes a GET call to IDCS with the URL given below. No
authorization is required (this needs to be accessed via browser as this
will open IDCS login UI, Postman will not work in this
case).
- The UI makes a call to IDCS to get the user token, passing
auth_codeobtained in the previous step with the following payload:Authorization: Basic <Base64 encoded clientID:clientSecret> Method: Post URL: https://<IDCS-service-instance>/oauth2/v1/token BODY (as form data): grant_type=authorization_code&code=<auth_code>Example:
curl -X POST 'https://idcs-4c463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/token' \ -H 'Authorization: Basic NTFkMDY3OTllMmFhNGM3NDlhNzkyNzZjZjdkMjRjYTY6YjZhMzc4ZmQtZjk2Mi00MTg3LWE2NzctYTBmMGI3NmEzODhj' \ -d 'grant_type=authorization_code&code=AgAgZTM5MGMzODVjNzY3NGZhNzgzMmExMTI0YmU1ZDBiOTYIABC_fyt25KEcHP9-Hmjkh9y1AAAAMPia8fMCbuzkdk10_CzsrqZ-EtGwsI_MCPFr1Y3gt25EhrhYH65mb7vkJmPvUeKdTg'IDCS returns the key and value for an access token:{"access_token":"<access-token-value>"}You can copy the access token value (the expiry of the access token is set to 7 days and refresh token is set to 14 days).
Note:
If one desires to create a refresh token along with an access token, two additional tasks need to be performed:- While creating an OAuth client, in addition to selecting grant type Authorization Code (see step 5 in Create an OAuth Client and Acquire a Client ID and Secret), you will also have to choose Refresh.
- While requesting for authorization code, you will have to
specify the additional scope
offline_accessalong withurn:opc:cec:all(scopes are space separated) as shown below:https://idcs-4c463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/authorize?client_id=51d06799e2aa4c749a79276cf7d24ca7&response_type=code&redirect_uri=https://p2qaextradp1srvc1-qucm2019927ac99.cec.ocp.oc-test.com/documents&scope=https://50B904E53A6F4EA1B45F30E225E6C99B.cec.ocp.oc-test.com:443/urn:opc:cec:all offline_access&nonce=12345&state=12345Then using this authorization code in
/oauth2/v1/tokenwill return refresh token along with access token.
Use the Access Token to Access the Oracle Content Management Resource
Once the access token is acquired, call the Oracle Content Management endpoint to access the resource.
A sample curl command follows.
curl -X GET <Oracle-Content-Management-URL>/content/management/api/v1.1/channels \
-H 'Authorization: Bearer <Access Token acquired from previous step>'\
-H 'Content-Type: application/json'Access OCM Using Resource Owner
In this flow, the resource owner credentials are exposed to the client. The
credentials are passed in /oauth2/v1/token API to get the token. So
it is important that the resource owner has a trust relationship with the client
making this API call, since the client must discard the password after obtaining the
access token.
Because this is a user token, the user requesting the token needs to have relevant OCM roles as the user’s access to the OCM objects will be checked against assigned roles.
To configure a confidential application to authorize a Resource Owner grant:
- Go to the IDCS admin console:
https://<IDCS BaseURL>/ui/v1/adminconsole - Click to add a new application in the Applications section.
- Select Confidential Application. Confidential Applications use OAuth 2.0 and can protect their OAuth client ID and client secret. To know more about Confidential Applications, see Add a Confidential Application.
- Give the application a name and, optionally, a description, and click Next.
- Choose to configure this application as a client.
- Select the Resource Owner grant type on the Authorization screen.
- Scroll down to the Token Issuance Policy section and, under Resources, click Add Scope to give the application access to the Oracle Content Management instance required.
- Select the correct instance.
- Click the right arrow to select the scope. The one ending in
urn:opc:cec:allis the only scope required. Select the checkbox next to it and then click Add (note down the scope string as it will be used later on while requesting the access token). - Click Next until the end of the train. The Resources, Web Tier Policy, and Authorization stops are related to applications that have some resource authenticated or authorized by IDCS; for example, a web application. In the case of a simple server-server client, which is discussed here, this isn’t relevant.
- Click Finish.
- Note the Client ID and Client Secret values because you’ll need those to get a token later.
- Check Activate and then click Save to enable the application.
To request a token:
- Get the token by making POST to
<idcs-base-url>/oauth2/v1/tokenusing client application's client ID and secret with basic auth. Following is the payload:Authorization: Basic <Base64 encoded clientID:clientSecret> Method: Post URL: <idcs-base-url>/oauth2/v1/token BODY (as form data): grant_type=password&scope==<scope string from Step 7 above>&username=<user name>&password=<password> - The following table describes the fields.
Field Value grant_type password scope A scope you added previously, in step 7; for example: https:// 1DF8AB52D0FF48F6992EEA3A5715B66F.cec.dev.ocp.octest. com:443/urn:opc:cec:allusername The user name to generate the token for. password The password for the user name in the preceding field. Example:curl -X POST 'https://idcs-4c463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/token' \ -H 'Authorization: Basic NTFkMDY3OTllMmFhNGM3NDlhNzkyNzZjZjdkMjRjYTY6YjZhMzc4ZmQtZjk2Mi00MTg3LWE2NzctYTBmMGI3NmEzODhj' \ -d 'grant_type=password&scope=https://50B904E53A6F4EA1B45F30E225EA99B.cec.ocp.oc-test.com:443/urn:opc:cec:all&username=John.Doe@test.com&password=johndoepassword#3’This results in JSON text where the token is the value of theaccess_tokenfield:{ "access_token": "eyJ4NXQjUzI1NiI6IkhoRktIMFFGeHR1UDkxLWg3QlJKSUFDMU50V2R...HUQmto_oELyjRaBp qh I75hQJYLWRKm6ozPS57tR1EYHmWABgYw_XALMT1kMuIuRxpGB2ozngpajzNNBBu2qtKg10- RzBTulKaxD25vKK1rznQ3p_XAOLK4CUUM-uG_PUOk49- JDgJjuSI74hLC1kagIlM93A2jUG3g3gdUpUCZPg", "token_type": "Bearer", "expires_in": 604800 }The token expiration time is given in seconds and is typically 7 days.
To use the token and access REST API endpoints, use the Bearer Authorization as before.
Note:
If one desires to create a refresh token along with access token, two additional tasks need to be performed:- While creating OAuth client, in addition to selecting grant type Resource Owner (See step 6 in Create an OAuth Client and Acquire a Client ID and Secret), you will also have to choose Refresh Token.
- While requesting for token, you will have to specify additional
scope
offline_accessalong withurn:opc:cec:all(scopes are space separated) as shown below:curl -X POST 'https://idcs-4c463010b1bb495d8db89fd05ebe1d99.identity.dev99.testdev.com/oauth2/v1/token' \ -H 'Authorization: Basic NTFkMDY3OTllMmFhNGM3NDlhNzkyNzZjZjdkMjRjYTY6YjZhMzc4ZmQtZjk2Mi00MTg3LWE2NzctYTBmMGI3NmEzODhj' \ -d 'grant_type=password&scope=https://50B904E53A6F4EA1B45F30E225EA99B.cec.ocp.oc-test.com:443/urn:opc:cec:all offline_access&username=John.Doe@test.com&password=johndoepassword#3’
This will return a refresh token along with access token.