Discover Cloud Services
Oracle Management Cloud’s Monitoring Cloud services capability gives you an easy way to obtain monitoring data from Cloud service entities such as Amazon Web Services or Microsoft Azure. By defining a monitoring Discovery Profile that is used to access the desired service, you can monitor Cloud services with minimal setup.
About Monitoring Cloud Services
To monitor a Cloud service, you first create a Cloud Discovery Profile. This profile defines Cloud service account information required to discover services and monitor them as entities. Monitoring of Cloud services automatically starts as soon as the services are discovered. Every 15 minutes, Oracle Management Cloud automatically checks for new services and also automatically polls metric data from your monitored services. Once the Cloud services are discovered, and status and performance metrics have been collected, monitoring features such as alerting and notifications will be automatically applied to the Cloud services.
Adding a Cloud Service
You add Cloud services by defining a Cloud Discovery Profile.
-
Navigate to the Cloud Discovery Profiles page (Administration—>Discovery—>Cloud Discovery Profiles).
-
Click Add Profile. The Add Discovery Profile page displays.
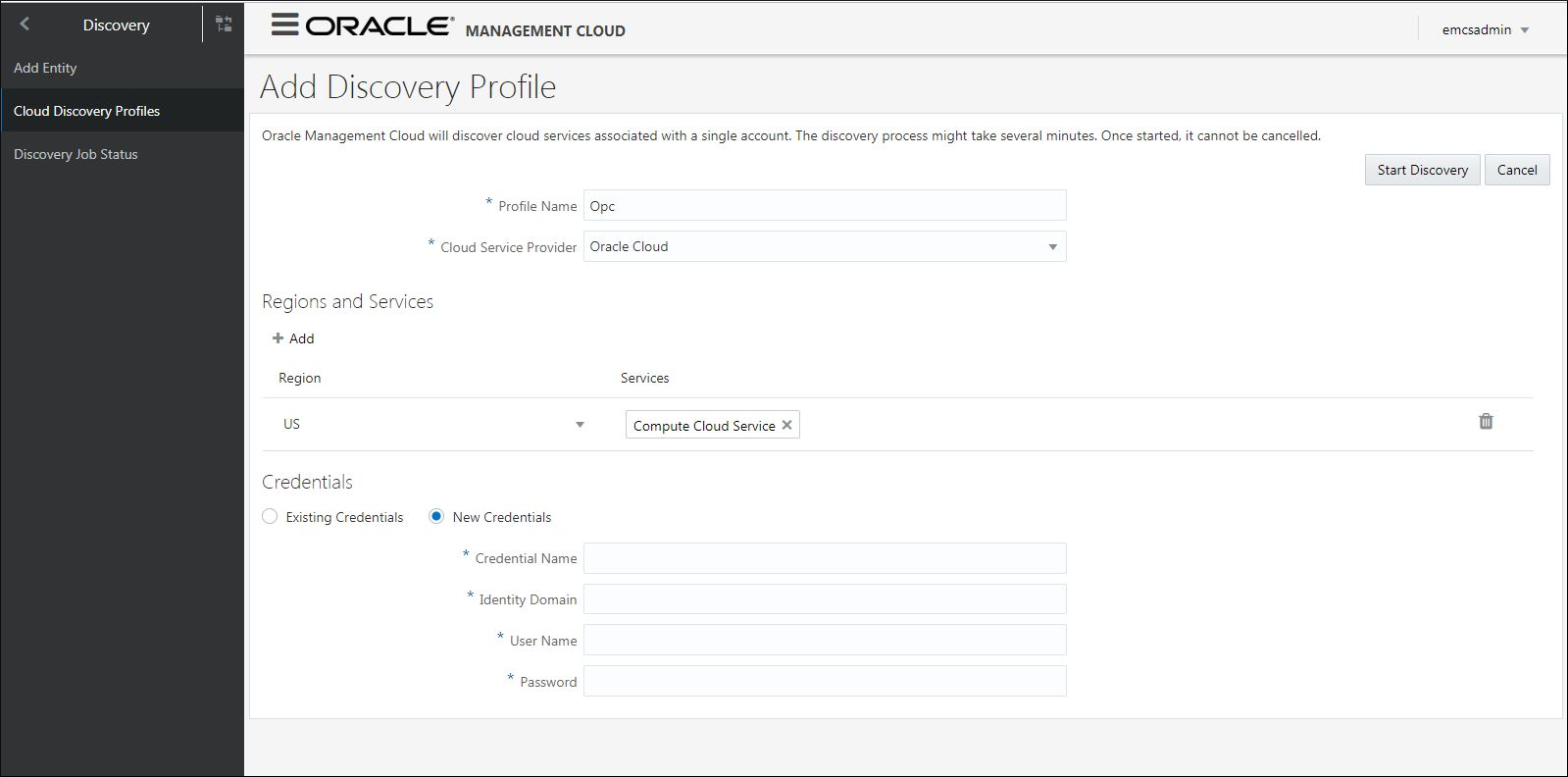
-
Enter a Profile Name and select a Cloud Service Provider. Based on the Cloud Service Provider you will create a profile that encapsulates all information required to connect to the Cloud vendor.
Note:
Required discovery profile information changes according to the Cloud Service Provider you select. See the following section for discovery information required for each service provider. -
Click Start Discovery.
Cloud Service Entity Type Discovery Information
Oracle Cloud
-
Regions and Services
-
Region: Region in which your services are enabled. US or Europe
-
Service: Services enrolled in Oracle Public Cloud that are to be monitored by Oracle Management Cloud.
-
-
Credentials
-
Credential Name: Any name for the credentials account.
-
Identity Domain: If you are using the traditional account, specify the Identity Domain. If you are using an Identity Cloud Service (IDCS)-based account, specify the Identity Service ID. This would be of the form
idcs-<GUID>. -
Username: Username from Oracle Public Cloud.
-
Password: Password from Oracle Public Cloud.
-
Note:
For monitoring via cloud profiles, only Oracle Compute is supported. Database Cloud Service and Java Cloud Service can be discovered via Cloud profiles but they are only supported for Compliance Service. To monitor (unmanaged) DBCS and JCS, you should use the cloud agent to monitor it like an Oracle database and WebLogic Server.If IDCS single sign-on has been enabled, you will need to perform the following procedures in order to enable monitoring using these IDCS-based accounts.
-
Log in and navigate to the MyServices page https://myservices-<tenant id>..console.oraclecloud.com/mycloud/cloudportal/dashboard
-
Click Customize Dashboard and select Identity Cloud from the drop-down list.
-
In the overview page, search for Identity Service Id. This corresponds to the IDCS GUID that should be used when creating OPC cloud profiles.
For an IDCS-based user account, grant the Monitoring_ApiAcess privilege to the user:
-
Log in and navigate to the MyServices page
https://myservices-<tenant id>.console.oraclecloud.com/mycloud/cloudportal/dashboard -
At the upper-right corner, click Users.
-
Navigate to the tab Groups.
-
Click Add and create a group with name Monitoring_ApiAccess (if the group does not exist already)
-
Click on the created group.
-
Navigate to the tab Users.
-
Click Add To Group at the right side. This lists all the existing users. Select the user for which you want to grant access to this group and click Add.
For a traditional account, perform the following steps to grant Monitoring_ApiAccess privilege to the user:
-
Connect to https://myservices.us.oraclecloud.com/mycloud/faces/cloudHome.jspx
-
Scroll down the page and click MyServices.
-
Click Users. https://myservices.us.oraclecloud.com/mycloud/faces/security.jspx
-
Create a Custom Role as shown in http://docs.oracle.com/en/cloud/get-started/subscriptions-cloud/ramoc/QuickStart.html. with the Role name
Monitoring _ApiAccessand the display nameMonitoring API Access. -
After creating the Role assign it to the user.:
Note:
The role needs to be created by the identity domain administrator.Amazon Web Services
Note:
The AWS permissions should be assigned to the user or the group to which the user belongs. Role-based access is currently not supported.| AWS Service | AWS Entity | Function | Required for |
|---|---|---|---|
|
DynamoDB |
omc_aws_dynamodb_table |
ListTables |
Discovery |
|
EC2 |
omc_aws_ec2_instance |
DescribeInstances |
Discovery |
|
omc_aws_ebs |
DescribeVolumes |
Discovery |
|
|
omc_aws_elastic_ip |
DescribeAddresses |
Discovery |
|
|
omc_aws_security_group |
DescribeSecurityGroups |
Discovery |
|
|
omc_aws_customer_gateway |
DescribeCustomerGateways |
Discovery |
|
|
omc_aws_internet_gateway |
DescribeInternetGateways |
Discovery |
|
|
omc_aws_route_table |
DescribeRouteTables |
Discovery |
|
|
omc_aws_subnet |
DescribeSubnets |
Discovery |
|
|
omc_aws_vpc |
DescribeVpcs |
Discovery |
|
|
omc_aws_vpn_connection |
DescribeVpnConnections |
Discovery |
|
|
omc_aws_vpn_gateway |
DescribeVpnGateways |
Discovery |
|
|
Elastic Load Balancer |
omc_aws_elb_instance |
DescribeLoadBalancers |
Discovery |
|
omc_aws_elb_application_instance |
DescribeLoadBalancers |
Discovery |
|
|
Lambda |
omc_aws_lambda_function |
ListFunctions |
Discovery |
|
RDS |
omc_aws_rds_instance |
DescribeDBInstances |
Discovery |
|
Redshift |
omc_aws_redshift_cluster |
DescribeClusters |
Discovery |
|
S3 |
omc_aws_s3_bucket |
ListAllMyBuckets |
Discovery |
|
SNS |
omc_aws_sns_topic |
ListTopics |
Discovery |
|
SQS |
omc_aws_sqs_queue |
ListQueues |
Discovery |
|
CloudWatch |
. |
GetMetricStatistics |
Performance collection for all the entities. |
-
AWS Account Number: Amazon Identity and Access Management (IAM) user name.
-
Regions and Services
Most Amazon Web Services offer a regional endpoint to make your requests. An endpoint is a URL that is the entry point for a web service. For example, https://dynamodb.us-west-2.amazonaws.com is an entry point for the Amazon DynamoDB service.
-
Credentials
-
Credential Name: Any name for the credentials account.
-
AWS User Access Key: Access keys consist of an access key ID (Example: AKIAIOSFODNN7EXAMPLE)
-
AWS User Secret Key: A secret access key consisting of a secret key ID (Example, wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY)
-
Microsoft Azure
-
Azure Subscription ID: An Azure GUID (subscription ID).
-
Regions and Services
-
Region: All Regions - Microsoft Azure endpoints are global. Because selection of resources to be monitored by region is not supported,, all resources for given subscription ID will be monitored.
-
Services: Currently, only monitoring of Azure VM instances is supported.
-
-
Credentials
Azure Monitoring is done through Azure Resource Manager and Azure Monitor APIs using an App account within the specified Azure Active Directory and has read permission for the specified subscription(s). The App account can have read permission for multiple subscriptions; therefore credentials can be reused.
For information on setting up Azure monitoring from Oracle Management Cloud, see Microsoft Azure.
-
Credential Name: Name given to credentials.
-
Microsoft Active Directory ID: Azure Active Directory –> Properties –> Directory ID (Example: cafe8c3d-c91a-4405-a43b-01efee6d2fbc)
-
Microsoft Active Directory Application ID: Azure Active Directory –> App registrations –> App / APPLICATION ID (Example: cafef0f5-f431-4c8b-9ee3-22524407ce69)
-
Microsoft Active Directory Application Key: Displayed on the registration of the App in the Azure Active Directory
-
Supported Cloud Entity Types
| Cloud Vendor | Cloud Service | Monitored by REST APIs | Monitored by Cloud Agent |
|---|---|---|---|
|
Oracle Cloud |
Compute (General Purpose and Dedicated Compute) (OCI Classic only) |
Yes
Note: To monitor Compute via REST APIs, you must have the Monitoring_apiAccess role. There are two ways to perform this action depending on whether you are using a traditional account or a IDCS-based account. For more information, see Quick Start: Obtain Account Information. |
Yes (agent is local to Compute) |
|
. |
Database Cloud Service (11g and 12c) |
No |
Yes (agent can be local or remote) |
|
. |
Java Cloud Service (WebLogic Server 11g and 12c) |
No |
Yes (agent can be remote) |
|
. |
Exadata Cloud Service |
No |
Yes: Oracle DB, Listener, Host/VM components |
|
Amazon |
Elastic Compute Cloud (EC2) |
Yes |
Yes (agent is local) |
|
. |
Relational Database (RDS) - Oracle |
Yes |
Yes |
|
. |
RDS (all database engines) |
Yes |
No |
|
. |
Simple Storage Service (S3) |
Yes |
No |
|
. |
Elastic Block Store (EBS) |
Yes |
No |
|
. |
Redshift |
Yes |
No |
|
. |
Elastic Load Balancer (ELB) – Classic Load Balancer and Application Load Balancer |
Yes |
No |
|
. |
Lambda |
Yes |
No |
|
. |
Simple Notification Service (SNS) |
Yes |
No |
|
. |
Simple Queue Service SQS |
Yes |
No |
|
Microsoft Azure |
Virtual Machines |
Yes |
No |
| . | Logic Application Service | Yes | No |
| . | VM Scale Set | Yes | No |
| . | API Application Service | Yes | No |
| . | Application Service Plan | Yes | No |
| . | Application Gateway Service | Yes | No |
| . | Event Hub Namespace Service | Yes | No |
| . | Functions Application Service | Yes | No |
| . | Mobile Application Service | Yes | No |
| . | Web Application Service | Yes | No |
| . | SQL Database | Yes | No |
| . | SQL Data Warehouse | Yes | No |
Support for OCI Compute
OCI Comput is currently supported and monitored like a host entity using the cloud agent. Once you deploy the cloud agent, the underlying host should be discovered and monitored like an host entity.
Support for Autonomous Database in OCI
For information about Autonomous Database in OCI, see Discover Autonomous Databases in Using Oracle Database Management for Autonomous Databases.