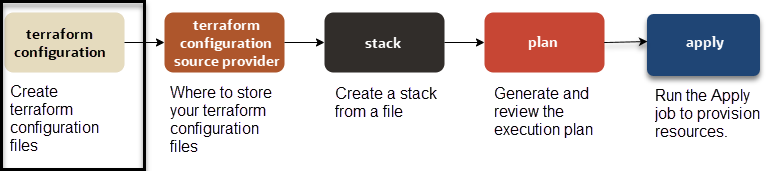Deploying Oracle NoSQL Table Using Terraform and OCI Resource Manager
It’s easy to deploy NDCS tables on OCI (Oracle Cloud Infrastructure) using Terraform and Resource Manager’s Stack. We are going to use the OCI Resource Manager CLI to deploy NDCS Tables on Oracle Cloud. Before we proceed with this article, it is assumed that you are aware of NoSQL Cloud Service and know its basics, along with Terraform.
Terraform uses providers to interface between the Terraform engine and the supported cloud platform. The Oracle Cloud Infrastructure (OCI) Terraform provider is a component that connects Terraform to the OCI services that you want to manage. You can use the OCI Terraform provider, including Terraform Cloud and the OCI Resource Manager.
The OCI Resource Manager is an Oracle-managed service based on Terraform that uses Terraform configuration files to automate deployment and operations for the OCI resources supported by the OCI Terraform provider. Resource Manager allows you to share and manage infrastructure configurations and state files across multiple teams and platforms.

- To create resources in OCI, we need to configure terraform. Create the basic terraform configuration files for terraform provider definition, NoSQL resource definitions, authentication, and input variables.
- Decide where to store the terraform configuration files. You can store these files in different sources, such as local folder or zip, Object Storage bucket, and source control systems, such as GitHub or GitLab.
- Run the Resource Manager CLI commands to perform the following tasks:
- Create a stack.
- Generate and review the execution plan.
- Run the Apply job to provision NoSQL resources.
- Review log files, as needed.
Note:
We’re going to be working with the Oracle Cloud Infrastructure (OCI) Resource Manager Command Line Interface (CLI) and executing these commands in the Cloud Shell using Console. This means you will need some information about your cloud tenancy and other items such as public or private key pairs handy. If you want to configure the OCI CLI on your local machine, refer to this documentation.This article has the following topics:
Prerequisites
- Basic understanding of Terraform. Read the brief introduction here.
- An Oracle Cloud account and a subscription to the Oracle NoSQL Database Cloud Service. If you do not already have an Oracle Cloud account you can start here.
- OCI Terraform provider installed and configured.
Substep 1.1: Create OCI Terraform provider configuration
Create a new file named "provider.tf" that contains the OCI Terraform provider definition, and also associated variable definitions. The OCI Terraform provider requires ONLY the region argument.
- API Key Authentication
- Instance Principal Authorization
- Security Token Authentication
region argument specifies the geographical region in which your provider resources are created. To target multiple regions in a single configuration, you simply create a provider definition for each region and then differentiate by using a provider alias, as shown in the following example. Notice that only one provider, named "oci" is defined, and yet the oci provider definition is entered twice, once for the us-phoenix-1 region (with the alias "phx"), and once for the region us-ashburn-1 (with the alias "iad").provider "oci" {
region = "us-phoenix-1"
alias = "phx"
}
provider "oci" {
region = "us-ashburn-1"
alias = "iad"
}region argument is required for the OCI Terraform provider. tenancy_ocid, user_ocid, private_key_path, and fingerprint arguments are required for API Key authentication. You can provide the value for region and API Key Authentication keys (tenancy_ocid, user_ocid, private_key_path, and fingerprint) as Environment Variables or within Terraform configuration variables (as mentioned in Substep 1.3: Loading Terraform Configuration Variables).variable "tenancy_ocid" {
}
variable "user_ocid" {
}
variable "fingerprint" {
}
variable "private_key_path" {
}
variable "region" {
}
provider "oci" {
region = var.region
tenancy_ocid = var.tenancy_ocid
user_ocid = var.user_ocid
fingerprint = var.fingerprint
private_key_path = var.private_key_path
}tenancy_ocid, user_ocid, private_key_path, and fingerprint attributes in your provider definition.
Note:
Instance principal authorization applies only to instances that are running in Oracle Cloud Infrastructure.region argument is required for the OCI Terraform provider, and an auth argument is required for Instance Principal Authorization. You can provide the value for region argument as Environment Variables or within Terraform configuration variables (as mentioned in Substep 1.3: Loading Terraform Configuration Variables).variable "region" {
}
provider "oci" {
auth = "InstancePrincipal"
region = var.region
}Note:
This token expires after one hour. Avoid using this authentication method when provisioning of resources takes longer than one hour. See Refreshing a Token for more information.region an argument is required for the OCI Terraform provider. The auth and config_file_profile arguments are required for Security Token authentication.
variable "region" {
}
variable "config_file_profile" {
}
provider "oci" {
auth = "SecurityToken"
config_file_profile = var.config_file_profile
region = var.region
}Substep 1.2: Create NoSQL Terraform configuration
Create a new file named "nosql.tf" that contains the NoSQL terraform configuration resources for creating NoSQL Database Cloud Service tables or indexes. For more information about the NoSQL Database resources and data sources, see oci_nosql_table.
compartment_ocid argument is required for NoSQL Database resources such as tables and indexes. You can provide the value for compartment_ocid as Environment Variables or within Terraform configuration variables (as mentioned in Substep 1.3: Loading Terraform Configuration Variables).variable "compartment_ocid" {
}
resource "oci_nosql_table" "nosql_demo" {
compartment_id = var.compartment_ocid
ddl_statement = "CREATE TABLE if not exists demo (ticketNo INTEGER, fullName STRING, contactPhone STRING, confNo STRING, gender STRING, bagInfo JSON, PRIMARY KEY (ticketNo))"
name = "demo"
table_limits {
max_read_units = var.table_table_limits_max_read_units
max_storage_in_gbs = var.table_table_limits_max_storage_in_gbs
max_write_units = var.table_table_limits_max_write_units
}
}
resource "oci_nosql_table" "nosql_demoKeyVal" {
compartment_id = var.compartment_ocid
ddl_statement = "CREATE TABLE if not exists demoKeyVal (key INTEGER GENERATED ALWAYS AS IDENTITY (START WITH 1 INCREMENT BY 1 NO CYCLE), value JSON, PRIMARY KEY (key))"
name = "demoKeyVal"
table_limits {
max_read_units = var.table_table_limits_max_read_units
max_storage_in_gbs = var.table_table_limits_max_storage_in_gbs
max_write_units = var.table_table_limits_max_write_units
}
}Substep 1.3: Loading Terraform Configuration Variables
The next step is to create a file named "terraform.tfvars" and provide values for the required OCI Terraform provider arguments based on the authentication method.
Provide values for your IAM access and secret keys (tenancy_ocid, user_ocid, private_key_path, and fingerprint), region, and compartment_ocid arguments. You should already have an OCI IAM user with secret and access keys having sufficient permissions on NoSQL Database Cloud Service. Get those keys and store them in the file.
tenancy_ocid = "ocid1.tenancy.oc1..aaaaaaaaqljdu37xcfoqvyj47pf5dqutpxu4twoqc7hukwgpbavpdwkqxc6q"
user_ocid = "ocid1.user.oc1..aaaaaaaafxz473ypsc6oqiespihan6yi6obse3o4e4t5zmpm6rdln6fnkurq"
fingerprint = "2c:9b:ed:12:81:8d:e6:18:fe:1f:0d:c7:66:cc:03:3c"
private_key_path = "~/NoSQLLabPrivateKey.pem"
compartment_ocid = "ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya"
region = "us-phoenix-1"Provide values for region and compartment_ocid arguments.
region = "us-phoenix-1"
compartment_ocid = "ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya"Provide values for the region, compartment_ocid, and config_file_profile arguments.
region = "us-phoenix-1"
compartment_ocid = "ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya"
config_file_profile = "PROFILE"Substep 1.4: Declaring Input Variables
variables.tf" and assign values to input variables in it. Click here to refer to Terraform documentation to check for the valid arguments or properties available for NoSQL Database. In the example, the default value of the read, write, and storage units for NoSQL table are set to 10, 10, and 1 respectively.variable "table_table_limits_max_read_units" {
default = 10
}
variable "table_table_limits_max_write_units" {
default = 10
}
variable "table_table_limits_max_storage_in_gbs" {
default = 1
}Using Cloud Shell from the Console, we have created all the required terraform configuration files for provider definition, NoSQL database resources, authentication values, and input variables.
Step 2: Where to Store Your Terraform Configurations
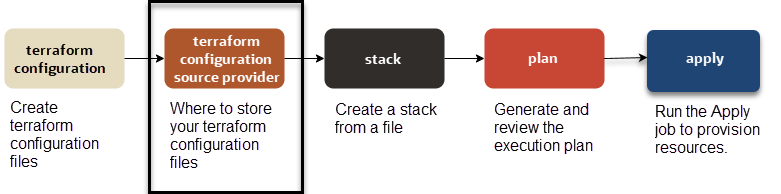
When creating a stack with Resource Manager, you can select your Terraform configuration from the following sources.
- Local .zip file
- Local folder
- Object Storage bucket
The most recent contents of the bucket are automatically used by any job running on the associated stack.
- Source code control systems, such as GitHub and GitLab
The latest version of your configuration is automatically used by any job running on the associated stack.
- Template (pre-built Terraform configuration from Oracle or a private template)
- Existing compartment (Resource Discovery)
Substep 2.1: Create Configuration Source Providers for Remote Terraform Configurations
You need to create a source configuration provider in case you want to use the remote terraform configurations that are hosted on a source control system, such as GitHub and GitLab.
For more information on how to create configuration source providers for remote Terraform configurations, see Managing Configuration Source Providers.
Step 3: Create a Stack from a File
Use the command related to your file location. For Terraform configuration sources supported with Resource Manager, see Where to Store Your Terraform Configurations.
terraform.zip. The terraform.zip file contains the following files:
provider.tfnosql.tfterraform.tfvarsvariables.tf
Note:
In this tutorial, we are using OCI Resource Manager CLI commands to create a stack. You can perform the same task using OCI Resource Manager Console.oci resource-manager stack create-from-git-provider
--compartment-id ocid1.tenancy.oc1..uniqueid
--config-source-configuration-source-provider-id ocid.ormconfigsourceprovider.oc1..uniqueid
--config-source-repository-url https://github.com/user/repo.git
--config-source-branch-name mybranch
--display-name "My Stack from Git"
--description "Create NoSQL Table"
--variables file://variables.json
--working-directory ""oci resource-manager stack create-from-object-storage
--compartment-id ocid1.tenancy.oc1..uniqueid
--config-source-namespace MyNamespace
--config-source-bucket-name MyBucket
--config-source-region PHX
--display-name "My Stack from Object Storage"
--description "Create NoSQL Table"
--variables file://variables.jsonoci resource-manager stack create
--compartment-id ocid1.tenancy.oc1..uniqueid
--config-source vcn.zip
--variables file://variables.json
--display-name "My Example Stack"
--description "Create NoSQL Table"
--working-directory ""--compartment-idis the OCID of the compartment where you want to create the stack.--config-sourceis the name of a .zip file that contains one or more Terraform configuration files.- (Optional)
--variablesis the path to the file specifying input variables for your resources.The Oracle Cloud Infrastructure Terraform provider requires additional parameters when running Terraform locally (unless you are using instance principals). For more information on using variables in Terraform, see Input Variables. See also Input Variable Configuration.
- (Optional)
--display-nameis the friendly name for the new stack. - (Optional)
--descriptionis the description for the new stack. - (Optional)
--working-directoryis the root configuration file in the directory. If not specified, or if null as in this example, then the service assumes that the top-level file in the directory is the root configuration file.
oci resource-manager stack create
--compartment-id ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya
--config-source terraform.zip{
"data": {
"compartment-id": "ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya",
"config-source": {
"config-source-type": "ZIP_UPLOAD",
"working-directory": null
},
"defined-tags": {},
"description": null,
"display-name": "ormstack20220117104810",
"freeform-tags": {},
"id": "ocid1.ormstack.oc1.phx.aaaaaaaa7jrci2s5iav5tdxpl6ucwo2dwazzrdkfhs6bxiohgcpkscmr57bq",
"lifecycle-state": "ACTIVE",
"stack-drift-status": "NOT_CHECKED",
"terraform-version": "1.0.x",
"time-created": "2022-01-17T10:48:10.878000+00:00",
"time-drift-last-checked": null,
"variables": {}
},
"etag": "dd62ace0b9e9d825d825c05d4588b73fede061e55b75de6436b84fb2bb794185"
}"id": "ocid1.ormstack.oc1.phx.aaaaaaaa7jrci2s5iav5tdxpl6ucwo2dwazzrdkfhs6bxiohgcpkscmr57bq"Step 4: Generate an Execution Plan

Note:
In this tutorial, we are using OCI Resource Manager CLI commands to generate an execution plan. You can perform the same task using OCI Resource Manager Console.oci resource-manager job create-plan-job
–-stack-id <stack_OCID>
--display-name "<friendly_name>"oci resource-manager job create-plan-job
--stack-id ocid1.ormstack.oc1.phx.aaaaaaaa7jrci2s5iav5tdxpl6ucwo2dwazzrdkfhs6bxiohgcpkscmr57bq{
"data": {
"apply-job-plan-resolution": null,
"cancellation-details": {
"is-forced": false
},
"compartment-id": "ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya",
"config-source": {
"config-source-record-type": "ZIP_UPLOAD"
},
"defined-tags": {},
"display-name": "ormjob20220117104856",
"failure-details": null,
"freeform-tags": {},
"id": "ocid1.ormjob.oc1.phx.aaaaaaaacrylnpglae4yvwo4q2r2tk5z5x5v6bwjsoxgn26moyg3eqwnt2aq",
"job-operation-details": {
"operation": "PLAN",
"terraform-advanced-options": {
"detailed-log-level": null,
"is-refresh-required": true,
"parallelism": 10
}
},
"lifecycle-state": "ACCEPTED",
"operation": "PLAN",
"resolved-plan-job-id": null,
"stack-id": "ocid1.ormstack.oc1.phx.aaaaaaaa7jrci2s5iav5tdxpl6ucwo2dwazzrdkfhs6bxiohgcpkscmr57bq",
"time-created": "2022-01-17T10:48:56.324000+00:00",
"time-finished": null,
"variables": {},
"working-directory": null
},
"etag": "a6f75ec1e205cd9105705fd7c8d65bf262159a7e733b27148049e70ce6fc14fe"
}"id": "ocid1.ormjob.oc1.phx.aaaaaaaacrylnpglae4yvwo4q2r2tk5z5x5v6bwjsoxgn26moyg3eqwnt2aq",
"job-operation-details": {
"operation": "PLAN"
...
}Substep 4.1: Review the Execution Plan
oci resource-manager job get-job-logs
--job-id <plan_job_OCID>oci resource-manager job get-job-logs
--job-id ocid1.ormjob.oc1.phx.aaaaaaaacrylnpglae4yvwo4q2r2tk5z5x5v6bwjsoxgn26moyg3eqwnt2aq...
{
"level": "INFO",
"message": "Terraform used the selected providers to generate the following execution",
"timestamp": "2022-01-17T10:49:21.634000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": "plan. Resource actions are indicated with the following symbols:",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + create",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": "Terraform will perform the following actions:",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " # oci_nosql_table.nosql_demo will be created",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + resource \"oci_nosql_table\" \"nosql_demo\" {",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + compartment_id = \"ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya\"",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + ddl_statement = \"CREATE TABLE if not exists demo (ticketNo INTEGER, fullName STRING, contactPhone STRING, confNo STRING, gender STRING, bagInfo JSON, PRIMARY KEY (ticketNo))\"",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + is_auto_reclaimable = true",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + name = \"demo\"",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + table_limits {",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_read_units = 10",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_storage_in_gbs = 1",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_write_units = 10",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " # oci_nosql_table.nosql_demoKeyVal will be created",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + resource \"oci_nosql_table\" \"nosql_demoKeyVal\" {",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + compartment_id = \"ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya\"",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + ddl_statement = \"CREATE TABLE if not exists demoKeyVal (key INTEGER GENERATED ALWAYS AS IDENTITY (START WITH 1 INCREMENT BY 1 NO CYCLE), value JSON, PRIMARY KEY (key))\"",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + is_auto_reclaimable = true",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + name = \"demoKeyVal\"",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + table_limits {",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_read_units = 10",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_storage_in_gbs = 1",
"timestamp": "2022-01-17T10:49:21.635000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_write_units = 10",
"timestamp": "2022-01-17T10:49:21.636000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": "Plan: 2 to add, 0 to change, 0 to destroy.",
"timestamp": "2022-01-17T10:49:21.636000+00:00",
"type": "TERRAFORM_CONSOLE"
},
...demo and demoKeyVal.{
...
"message": "Plan: 2 to add, 0 to change, 0 to destroy.",
...
}Step 5: Run an Apply Job

- To specify a plan job ("apply" an execution plan), use
FROM_PLAN_JOB_ID:oci resource-manager job create-apply-job --stack-id <stack_OCID> --execution-plan-strategy FROM_PLAN_JOB_ID --execution-plan-job-id <plan_job_OCID> --display-name "Example Apply Job" - To automatically approve the apply job (no plan job specified), use
AUTO_APPROVED:oci resource-manager job create-apply-job --stack-id <stack_OCID> --execution-plan-strategy AUTO_APPROVED --display-name "Example Apply Job"
oci resource-manager job create-apply-job
--stack-id ocid1.ormstack.oc1.phx.aaaaaaaa7jrci2s5iav5tdxpl6ucwo2dwazzrdkfhs6bxiohgcpkscmr57bq
--execution-plan-strategy AUTO_APPROVED
--display-name "Create NoSQL Tables Using Terraform"{
"data": {
"apply-job-plan-resolution": {
"is-auto-approved": true,
"is-use-latest-job-id": null,
"plan-job-id": null
},
"cancellation-details": {
"is-forced": false
},
"compartment-id": "ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya",
"config-source": {
"config-source-record-type": "ZIP_UPLOAD"
},
"defined-tags": {},
"display-name": "Create NoSQL Tables Using Terraform",
"failure-details": null,
"freeform-tags": {},
"id": "ocid1.ormjob.oc1.phx.aaaaaaaaqn4nsnfgi3th4rxolwqn3kftzzdpsw52pnfeyphi5dsxd6fhescq",
"job-operation-details": {
"execution-plan-job-id": null,
"execution-plan-strategy": "AUTO_APPROVED",
"operation": "APPLY",
"terraform-advanced-options": {
"detailed-log-level": null,
"is-refresh-required": true,
"parallelism": 10
}
},
"lifecycle-state": "ACCEPTED",
"operation": "APPLY",
"resolved-plan-job-id": null,
"stack-id": "ocid1.ormstack.oc1.phx.aaaaaaaa7jrci2s5iav5tdxpl6ucwo2dwazzrdkfhs6bxiohgcpkscmr57bq",
"time-created": "2022-01-17T10:54:46.346000+00:00",
"time-finished": null,
"variables": {},
"working-directory": null
},
"etag": "4042a300e8f678dd6da0f49ffeccefed66902b51331ebfbb559da8077a728126"
}"id": "ocid1.ormjob.oc1.phx.aaaaaaaaqn4nsnfgi3th4rxolwqn3kftzzdpsw52pnfeyphi5dsxd6fhescq",
"job-operation-details": {
"operation": "APPLY"
...
}Note:
If you are using a dedicated host environment, set the environment variable CLIENT_HOST_OVERRIDES to specify the custom endpoint before you run the job. Example:export CLIENT_HOST_OVERRIDES=<oci_nosql.NosqlClient=https://ndcs.us-ashburn-1.oci.oc-test.com>Substep 5.1: Verify the Status of Job
oci resource-manager job get
--job-id <job_OCID>oci resource-manager job get
--job-id ocid1.ormjob.oc1.phx.aaaaaaaaqn4nsnfgi3th4rxolwqn3kftzzdpsw52pnfeyphi5dsxd6fhescq{
"data": {
"apply-job-plan-resolution": {
"is-auto-approved": true,
"is-use-latest-job-id": null,
"plan-job-id": null
},
"cancellation-details": {
"is-forced": false
},
"compartment-id": "ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya",
"config-source": {
"config-source-record-type": "ZIP_UPLOAD"
},
"defined-tags": {},
"display-name": "Create NoSQL Tables Using Terraform",
"failure-details": null,
"freeform-tags": {},
"id": "ocid1.ormjob.oc1.phx.aaaaaaaaqn4nsnfgi3th4rxolwqn3kftzzdpsw52pnfeyphi5dsxd6fhescq",
"job-operation-details": {
"execution-plan-job-id": null,
"execution-plan-strategy": "AUTO_APPROVED",
"operation": "APPLY",
"terraform-advanced-options": {
"detailed-log-level": null,
"is-refresh-required": true,
"parallelism": 10
}
},
"lifecycle-state": "SUCCEEDED",
"operation": "APPLY",
"resolved-plan-job-id": null,
"stack-id": "ocid1.ormstack.oc1.phx.aaaaaaaa7jrci2s5iav5tdxpl6ucwo2dwazzrdkfhs6bxiohgcpkscmr57bq",
"time-created": "2022-01-17T10:54:46.346000+00:00",
"time-finished": "2022-01-17T10:55:28.853000+00:00",
"variables": {},
"working-directory": null
},
"etag": "9e9f524b87e3c47b3f3ea3bbb4c1f956172a48e4c2311a44840c8b96e318bcaf--gzip"
}{
...
"lifecycle-state": "SUCCEEDED",
...
}Substep 5.2: View the Log for a Job
oci resource-manager job get-job-logs-content
--job-id <job_OCID>oci resource-manager job get-job-logs-content
--job-id ocid1.ormjob.oc1.phx.aaaaaaaaqn4nsnfgi3th4rxolwqn3kftzzdpsw52pnfeyphi5dsxd6fhescq...
{
"level": "INFO",
"message": "Terraform will perform the following actions:",
"timestamp": "2022-01-17T10:55:05.580000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": "",
"timestamp": "2022-01-17T10:55:05.580000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " # oci_nosql_table.nosql_demo will be created",
"timestamp": "2022-01-17T10:55:05.580000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + resource \"oci_nosql_table\" \"nosql_demo\" {",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + compartment_id = \"ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya\"",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + ddl_statement = \"CREATE TABLE if not exists demo (ticketNo INTEGER, fullName STRING, contactPhone STRING, confNo STRING, gender STRING, bagInfo JSON, PRIMARY KEY (ticketNo))\"",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + is_auto_reclaimable = true",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + name = \"demo\"",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + table_limits {",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_read_units = 10",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_storage_in_gbs = 1",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_write_units = 10",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " # oci_nosql_table.nosql_demoKeyVal will be created",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + resource \"oci_nosql_table\" \"nosql_demoKeyVal\" {",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + compartment_id = \"ocid1.compartment.oc1..aaaaaaaawrmvqjzoegxbsixp5k3b5554vlv2kxukobw3drjho3f7nf5ca3ya\"",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + ddl_statement = \"CREATE TABLE if not exists demoKeyVal (key INTEGER GENERATED ALWAYS AS IDENTITY (START WITH 1 INCREMENT BY 1 NO CYCLE), value JSON, PRIMARY KEY (key))\"",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + is_auto_reclaimable = true",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + name = \"demoKeyVal\"",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + table_limits {",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_read_units = 10",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_storage_in_gbs = 1",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": " + max_write_units = 10",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": "Plan: 2 to add, 0 to change, 0 to destroy.",
"timestamp": "2022-01-17T10:55:05.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": "oci_nosql_table.nosql_demoKeyVal: Creating...",
"timestamp": "2022-01-17T10:55:06.581000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": "oci_nosql_table.nosql_demo: Creating...",
"timestamp": "2022-01-17T10:55:06.582000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": "oci_nosql_table.nosql_demoKeyVal: Creation complete after 6s [id=ocid1.nosqltable.oc1.phx.amaaaaaau7x7rfyaqgpbjucp3s6jjzpnar4lg5yudxhwlqrlbd54l3wdo7hq]",
"timestamp": "2022-01-17T10:55:12.582000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": "oci_nosql_table.nosql_demo: Creation complete after 9s [id=ocid1.nosqltable.oc1.phx.amaaaaaau7x7rfyasvdkoclhgryulgzox3nvlxb2bqtlxxsrvrc4zxr6lo4a]",
"timestamp": "2022-01-17T10:55:15.583000+00:00",
"type": "TERRAFORM_CONSOLE"
},
{
"level": "INFO",
"message": "Apply complete! Resources: 2 added, 0 changed, 0 destroyed.",
"timestamp": "2022-01-17T10:55:15.583000+00:00",
"type": "TERRAFORM_CONSOLE"
},
...demo and demoKeyVal.{
...
"message": "Apply complete! Resources: 2 added, 0 changed, 0 destroyed.",
...
}We have covered a lot of details in this tutorial. We created terraform configuration files required for deployment of NoSQL database tables on OCI cloud and then configured the source location for these files. We then used the OCI Resource Manager CLI to create a stack, generate an execution plan, and run apply job on the execution plan.
Deploying Oracle NoSQL Table Using Terraform and OCI Resource Manager