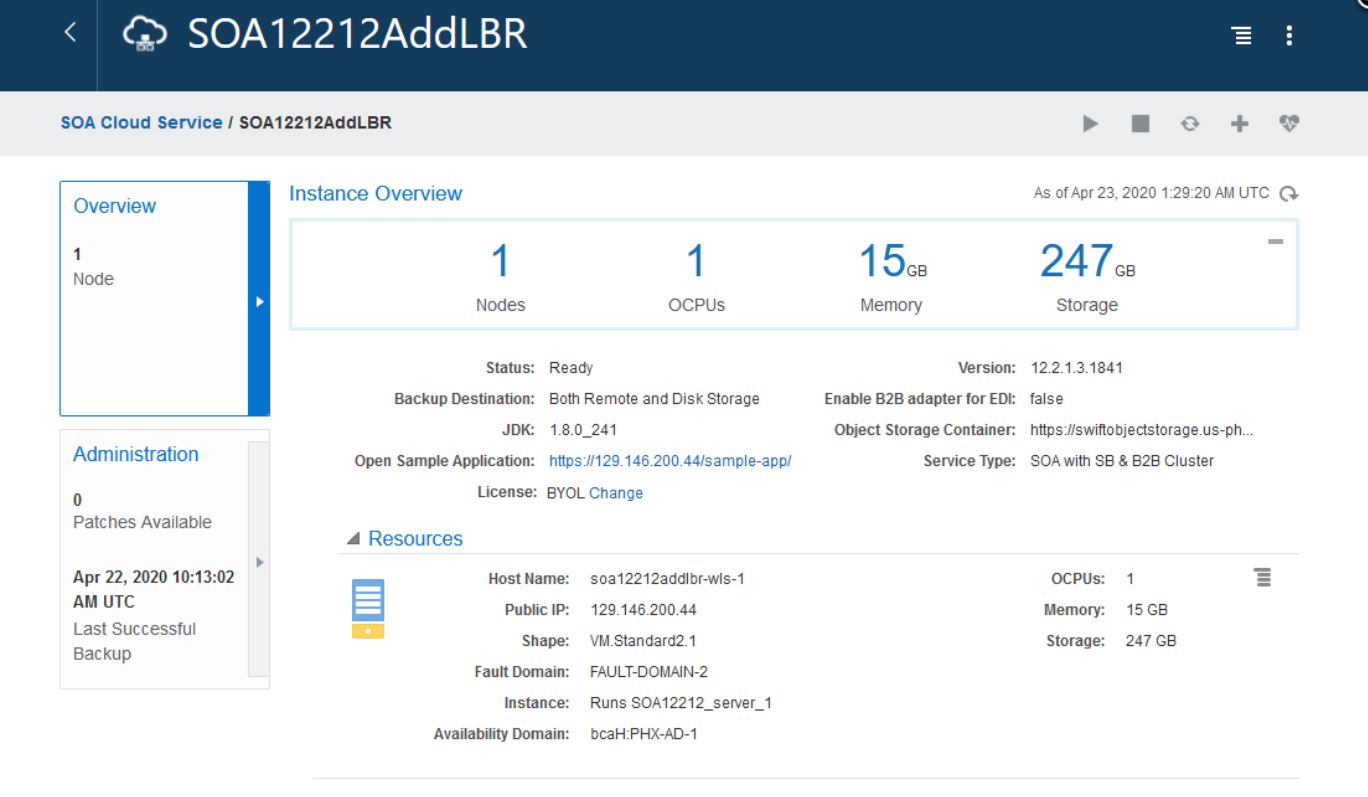
Configure an Oracle Cloud Infrastructure Load Balancer Post-Provisioning
![]() This topic does not apply to Oracle Cloud Infrastructure Classic.
This topic does not apply to Oracle Cloud Infrastructure Classic.
Usage Notes:
- You can configure an Oracle Cloud Infrastructure load balancer post-provisioning for an Oracle SOA Cloud Service instance of service types SOA with SB & B2B Cluster and MFT Cluster.
- If you are provisioning a new Oracle SOA Cloud Service instance, then select None for Load Balancer in the Create Instance Wizard.
- You can configure only one Oracle Cloud Infrastructure load balancer for one Oracle SOA Cloud Service instance.
- The Oracle Cloud
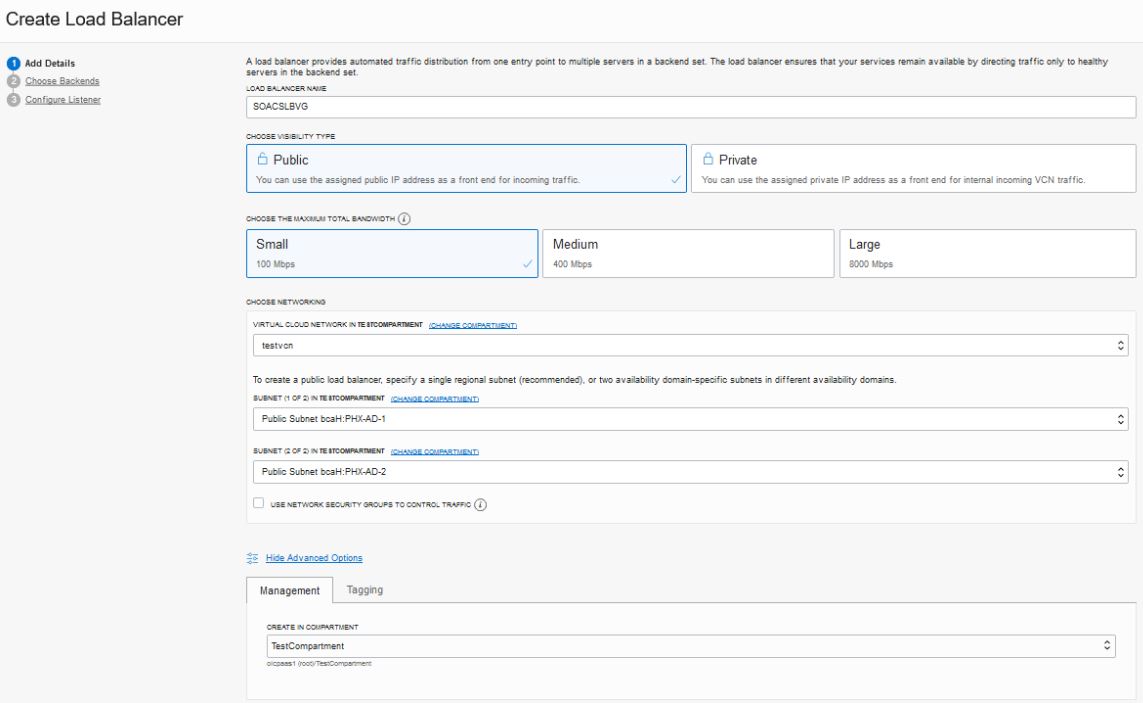
Infrastructure load balancer should be created in custom compartment, not within
ManagedCompartmentForPaaS. - The Oracle Cloud Infrastructure load balancer has high availability (HA) features, spanned across different Availability Domains.
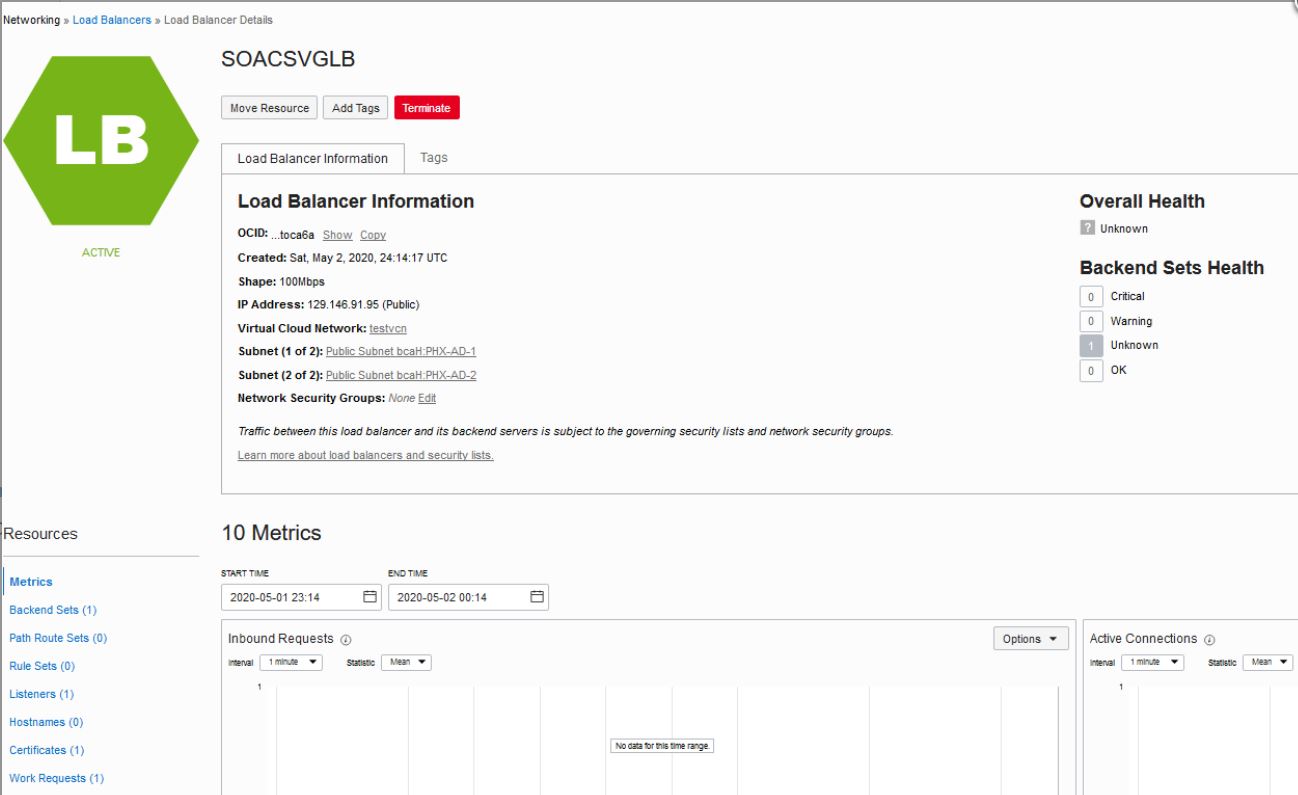
- Unlike OTD, the Oracle SOA Cloud Service Console does not show the Oracle Cloud Infrastructure load balancer on the instance details page.
- For existing Oracle SOA Cloud Service instances
that use OTD:
- If you have manually imported any certificates into Oracle Traffic Director (OTD), you must reimport these certificates into the new load balancer after it is created.
- If provisioned with OTD, then ensure that OTD is in running state and then remove the OTD instance using REST API.
- After completing the steps to add an Oracle Cloud
Infrastructure load balancer:
- If you are not using a DNS name and using an IP address (see Register a Custom Domain Name with a Third-Party Registration Vendor), and you replaced the OTD load balancer with the Oracle Cloud Infrastructure load balancer, make sure your runtime URLs use the Oracle Cloud Infrastructure load balancer IP address instead of the OTD public IP address.
- URLs for all Managed Servers such as b2bconsole, mftconsole, and composer are accessible using the Oracle Cloud Infrastructure load balancer URL using https.
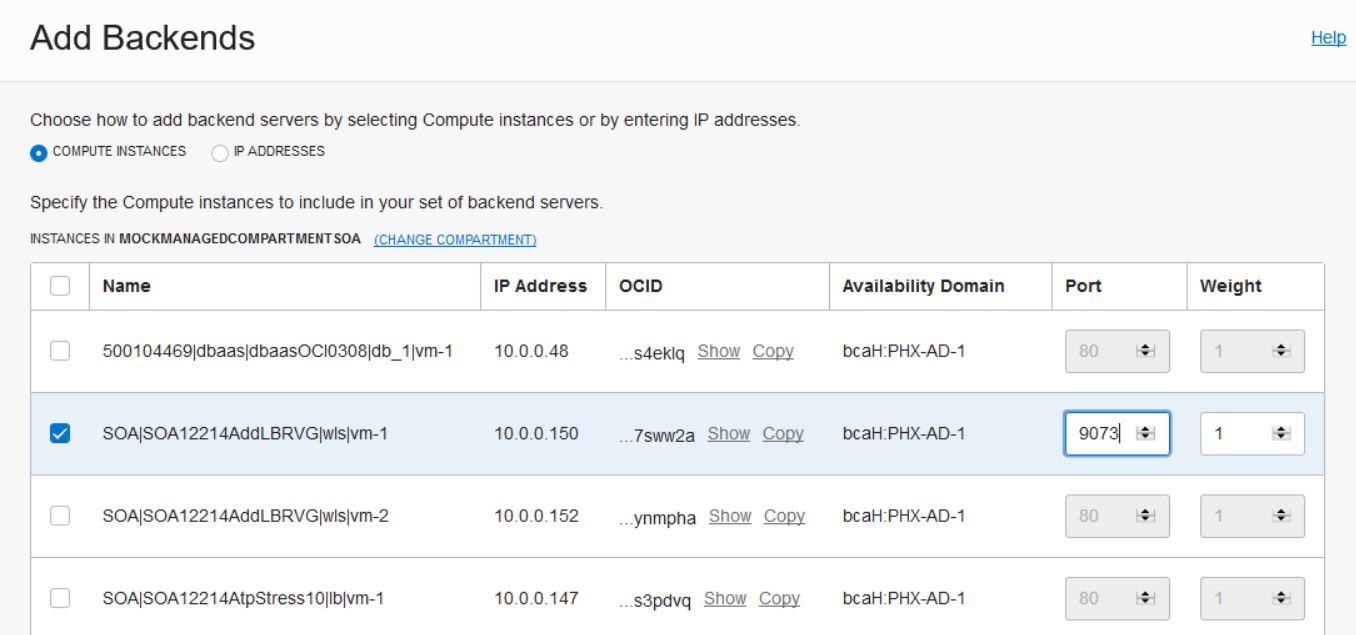
- You must manually add or delete backends in the Oracle Cloud Infrastructure load balancer after scale out and scale in operations.
-
Deprovisioning of the Oracle SOA Cloud Service instance will not delete the Oracle Cloud Infrastructure load balancer. You must manually delete the load balancer from the Oracle Cloud Infrastructure Console.
-
Do not invoke the Add OTD component operation from Oracle SOA Cloud Service Console. If you do so, OTD will override the Oracle Cloud Infrastructure load balancer configuration.
Note:
This procedure uses the following example IP addresses:- WebLogic Server Public IP:
129.146.200.44 - OTD Public IP if available:
129.213.147.163(the steps below replace this OTD load balancer with the Oracle Cloud Infrastructure load balancer) - Oracle Cloud
Infrastructure load balancer Public IP:
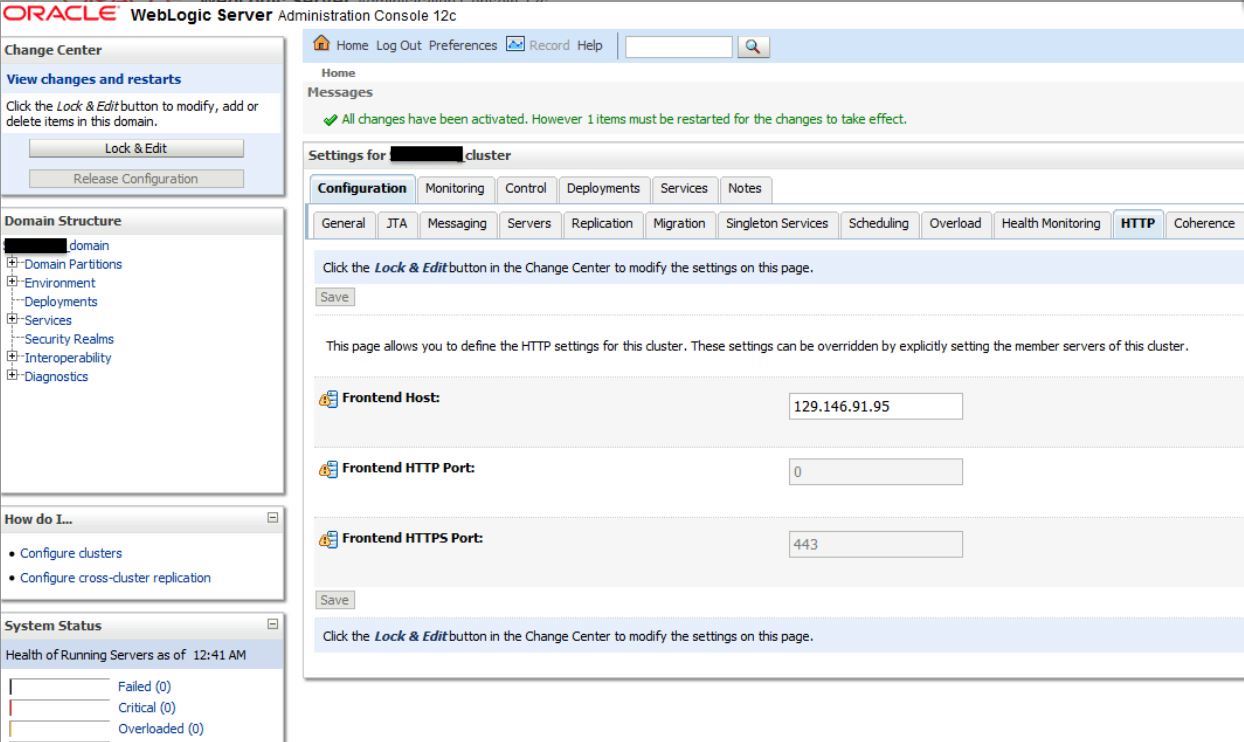
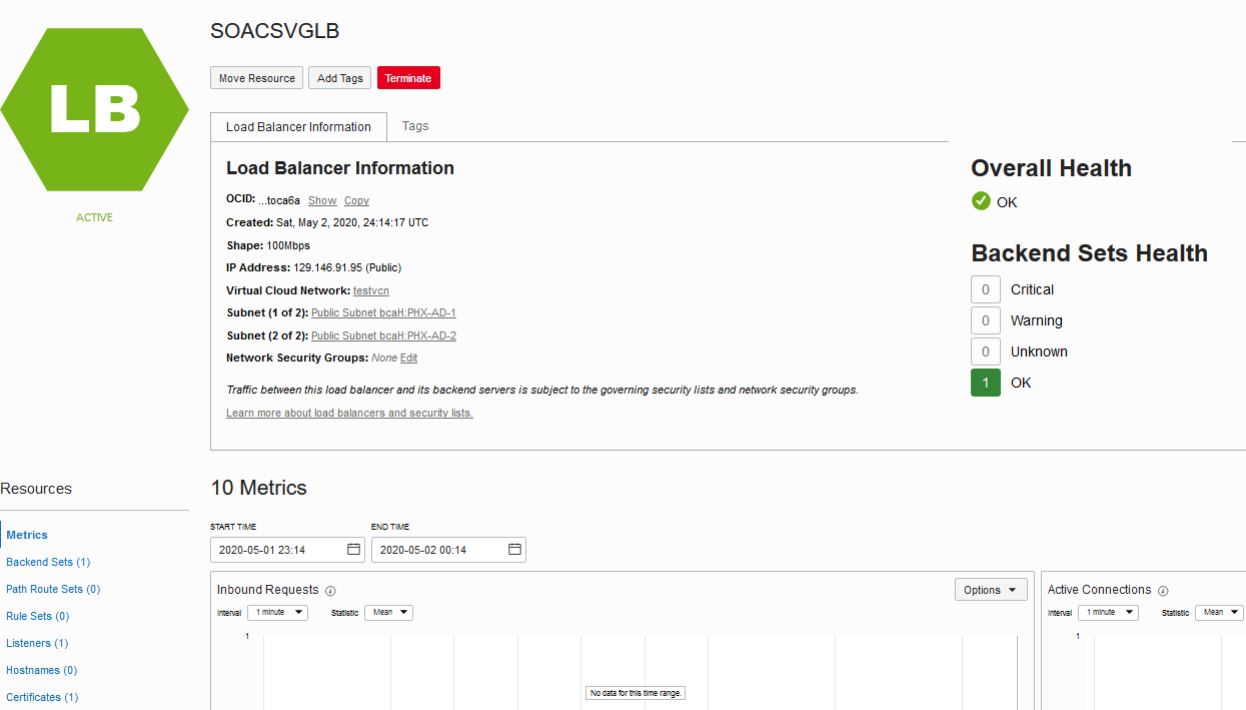
129.146.91.95
To configure an Oracle Cloud Infrastructure load balancer post-provisioning:
Troubleshooting Tips
If any steps in the configuration are missed or incorrectly implemented, the Oracle Cloud Infrastructure load balancer will not generate any error messages to alert you to issues. You can navigate to Oracle Cloud Infrastructure load balancer work requests and make sure the work requests have succeeded to confirm that the load balancer is working.
Use the following checklist to troubleshoot an Oracle Cloud Infrastructure load balancer that is not in Ready state:
-
In the Oracle Cloud Infrastructure Console, verify:
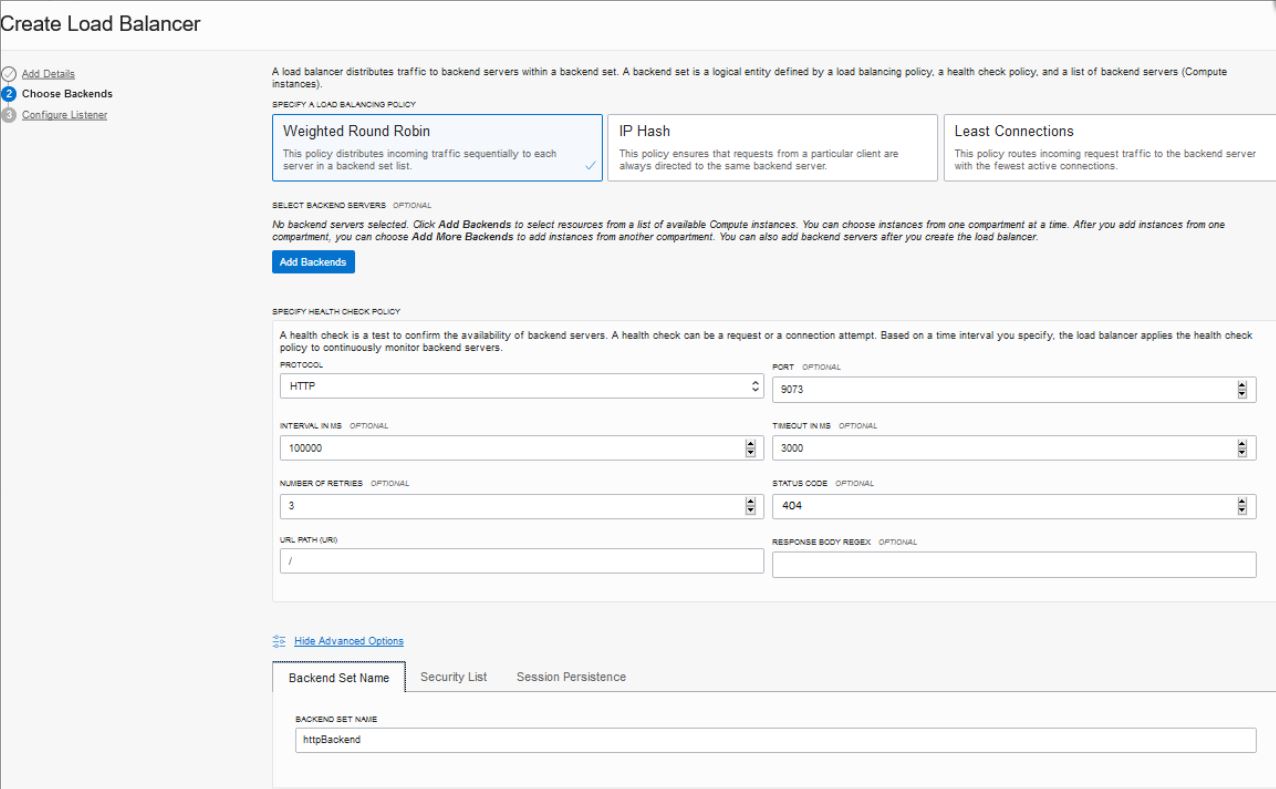
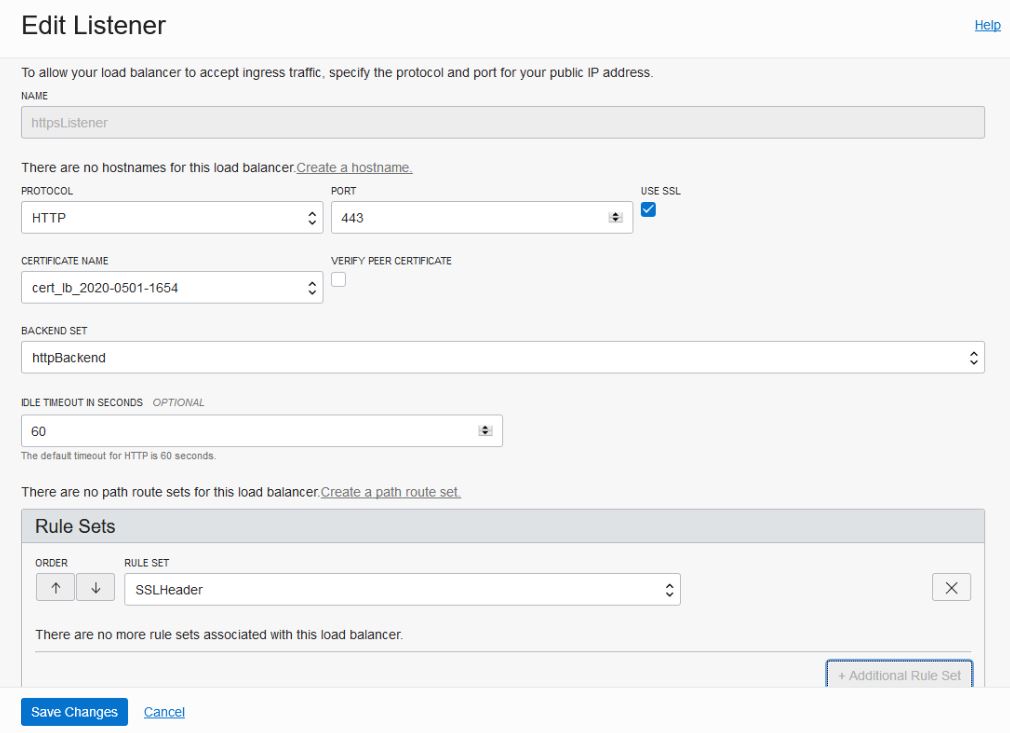
- Healthcheck: port number is
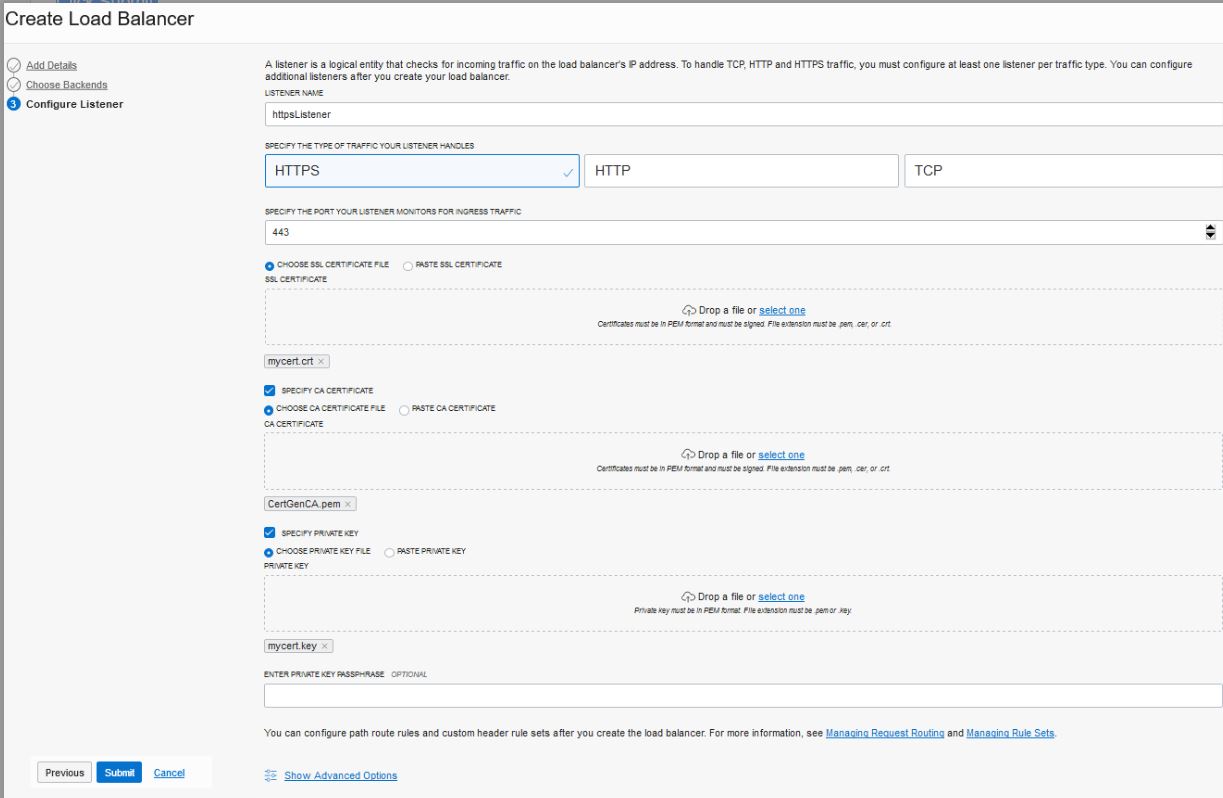
9073and status code is404. - Https Listener: listen port is
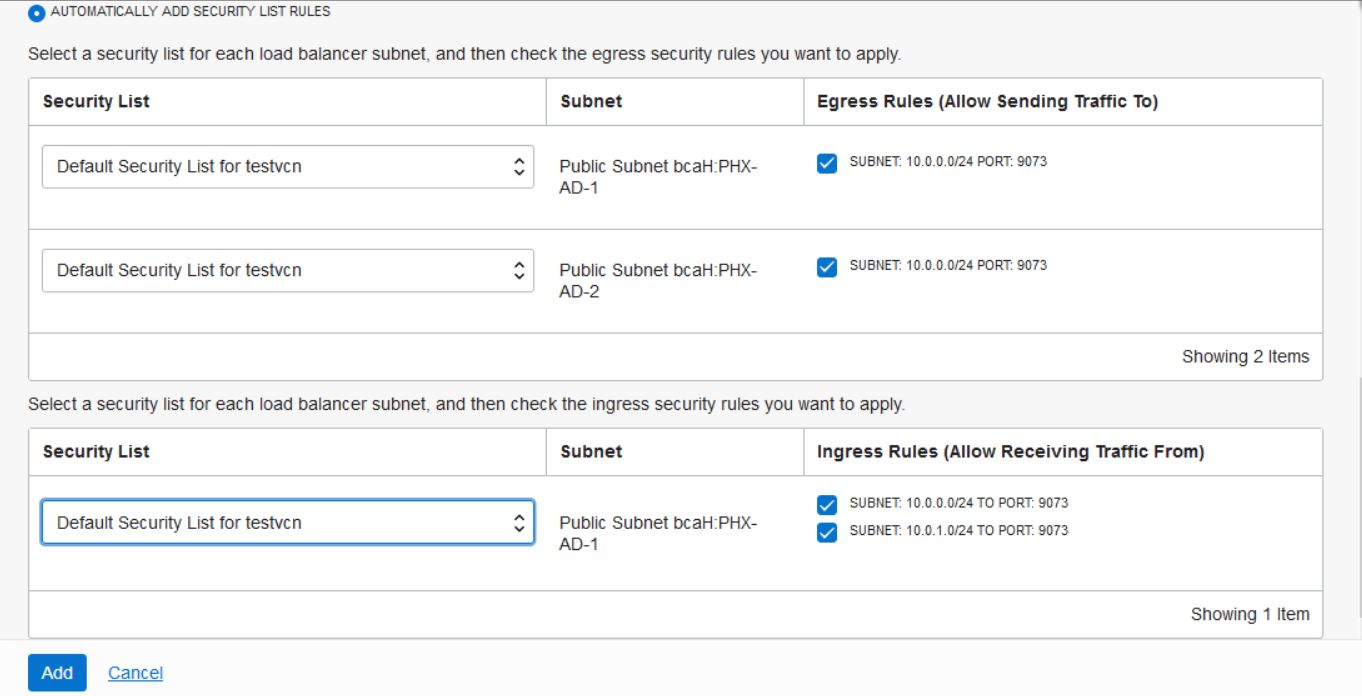
443. - Security lists has rule defined with
0.0.0.0/0for443. - Backends are configured to use port
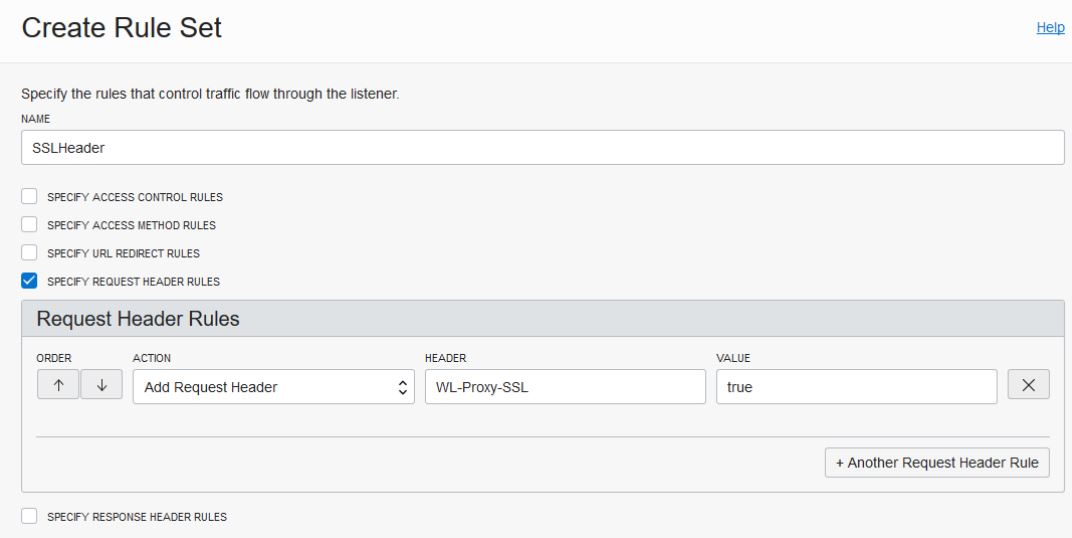
9073. - The
WL-Proxy-SSLheader is added tohttpslistener.
- Healthcheck: port number is
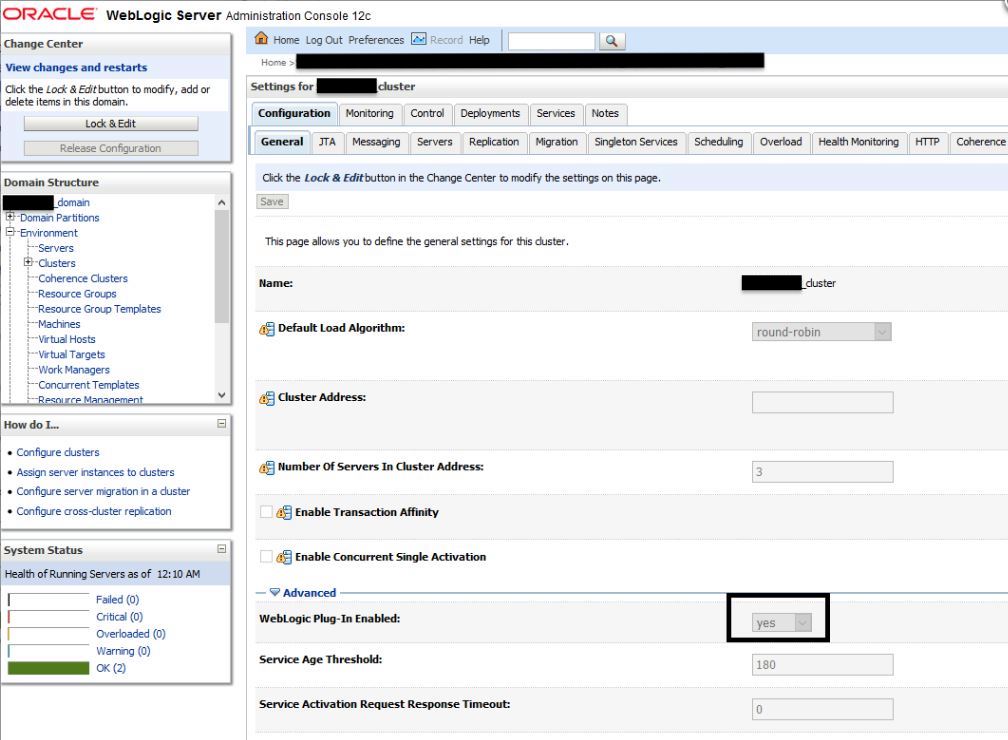
- In the WebLogic Server Administration Console, verify:
Frontendhostandportare configured for the cluster.- The WebLogic Plug-In is enabled.