Configure Security Rules for the Network
If your instance communicates with other resources in Oracle Cloud or on the Internet, create or update the security lists for your target Oracle Cloud Infrastructure network.
A security list is assigned to subnets within your virtual cloud network (VCN). It includes ingress and egress rules that specify the types of traffic allowed in and out of the instances within the subnet. You can update an existing security list, or create a new one and assign it to a subnet.
- JavaMail Session
- Foreign Java Naming and Directory Interface (JNDI) Provider
- Foreign Java Message Service (JMS) Server
- Messaging Bridge
- Store-and-Forward
- WebLogic Diagnostic Framework (WLDF) REST Action
Oracle recommends that you create a private subnet for Oracle WebLogic Server for OCI in the VCN used by Oracle Java Cloud Service.
Set up a private subnet that can be used for creating your Oracle WebLogic Server for OCI instance in the same VCN as the Oracle Java Cloud Service instance. This allows you to quickly set up a connection to the same database that Oracle Java Cloud Service uses and allow ssh connectivity between the Oracle WebLogic Server for OCI instance VMs and the Oracle Java Cloud Service VMs, so files can be transferred between them.
Recommended simplified network configurations
Note:
Public subnets are allowed for Oracle WebLogic Server for OCI instances, but not recommended.Oracle Java Cloud Service with OTD
There is no Oracle Traffic Director (OTD) option in Oracle WebLogic Server for OCI. Instead, the OCI load balancer must be used to route traffic to the WebLogic managed servers.
Figure 2-1 Oracle Java Cloud Service with OTD
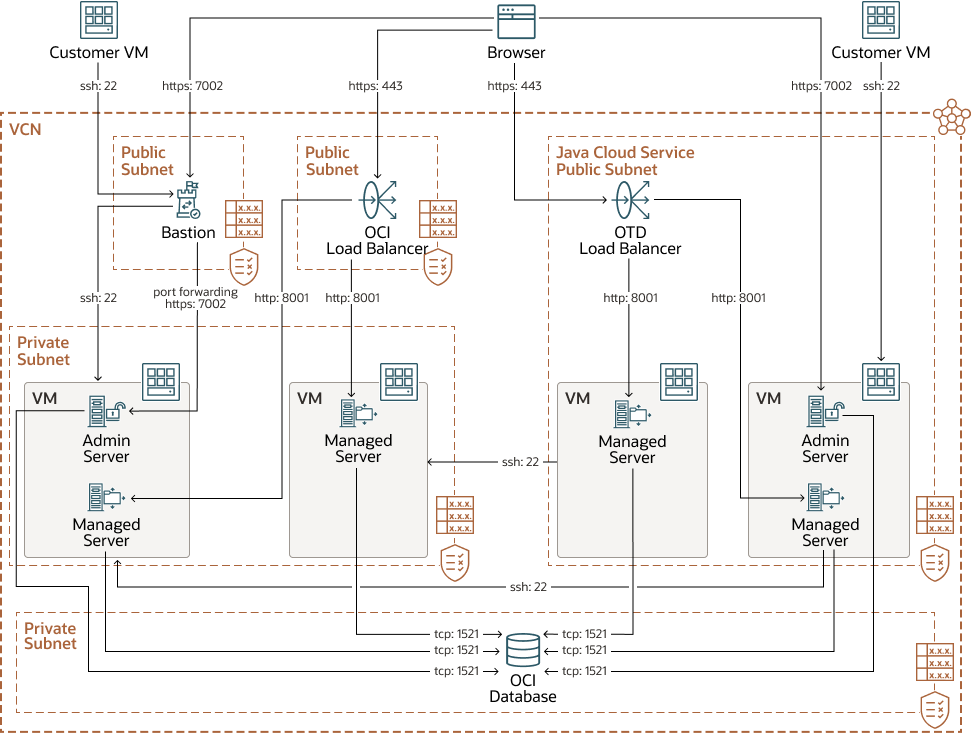
The private subnet for the OCI database and the public subnet for JCS must already exist. The Oracle WebLogic Server for OCI private subnet, OCI load balancer public subnet, and bastion host public subnet must be created.
Table 2-1 Oracle WebLogic Server for OCI Private Subnet
| Rule Type | Source CIDR and Protocol | Default Destination Port | Description |
|---|---|---|---|
|
Stateful Ingress |
Bastion public subnet, TCP |
22 |
SSH access |
|
Stateful Ingress |
Bastion public subnet, TCP |
7002 |
Administration server SSL port |
|
Stateful Ingress |
OCI load balancer public subnet, TCP |
8001 |
Managed server port |
|
Stateful Ingress |
Oracle Java Cloud Service public subnet, TCP |
22 |
SSH access, so domain and binaries can be copied over |
|
Stateful Ingress |
Oracle WebLogic Server for OCI private subnet (self), TCP |
22 |
SSH access between the compute instances of Oracle WebLogic Server for OCI |
|
Stateful Ingress |
Oracle WebLogic Server for OCI private subnet (self), TCP |
9071 |
Used for provisioning and scaling |
|
Stateful Ingress |
Oracle WebLogic Server for OCI private subnet (self), TCP |
9073 |
Used for WebLogic health check |
|
Stateful Ingress |
Oracle WebLogic Server for OCI private subnet (self), TCP |
5556 |
Used for accessing node manager |
Table 2-2 OCI Load Balancer Public Subnet
| Rule Type | Source CIDR and Protocol | Default Destination Port | Description |
|---|---|---|---|
|
Stateful Ingress |
Internet (0.0.0.0/0), TCP |
443 |
SSL access |
Table 2-3 Bastion Public Subnet
| Rule Type | Source CIDR and Protocol | Default Destination Port | Description |
|---|---|---|---|
|
Stateful Ingress |
Hosts with access to bastion, TCP |
22 |
SSH access, port forwarding |
Table 2-4 Access to OCI Database Public Subnet
| Rule Type | Source CIDR and Protocol | Default Destination Port | Description |
|---|---|---|---|
|
Stateful Ingress |
WLS for OCI private subnet, TCP |
1521 |
DB access |
Oracle Java Cloud Service with IDCS
Figure 2-2 Oracle Java Cloud Service with IDCS
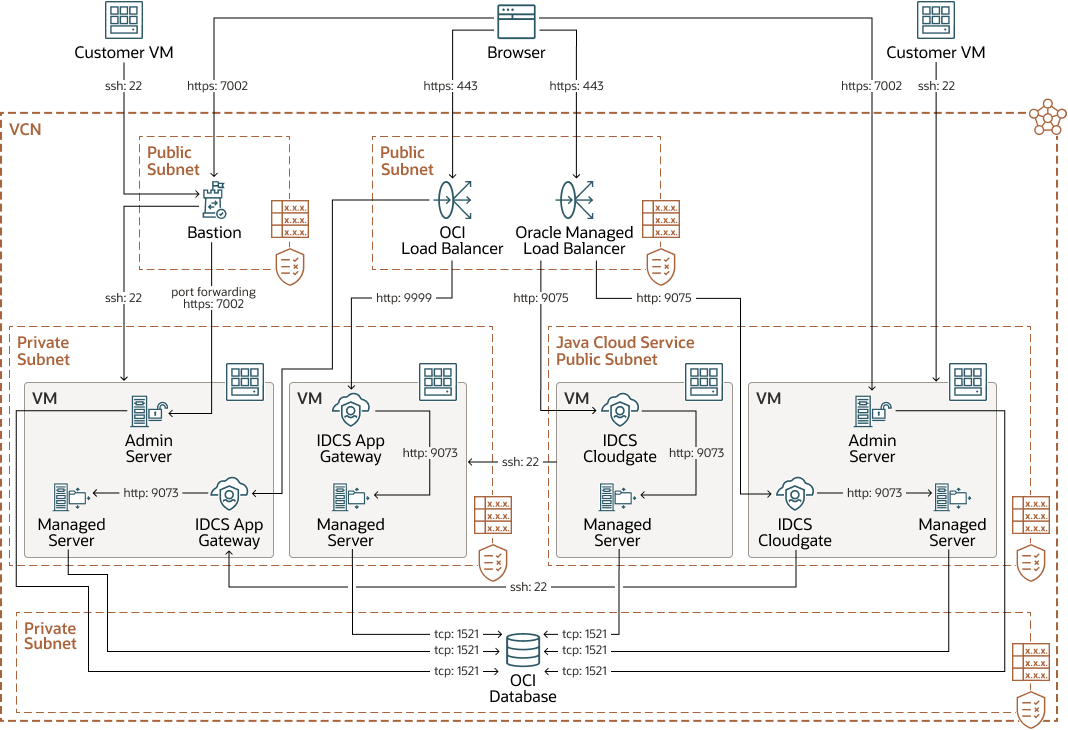
The private subnet for the OCI database, the public subnet for the OCI load balancer, and the public subnet for JCS must already exist. The Oracle WebLogic Server for OCI private subnet and bastion host public subnet must be created.
Table 2-5 Oracle WebLogic Server for OCI Private Subnet
| Rule Type | Source CIDR and Protocol | Default Destination Port | Description |
|---|---|---|---|
|
Stateful Ingress |
Bastion public subnet, TCP |
22 |
SSH access |
|
Stateful Ingress |
Bastion public subnet, TCP |
7002 |
Administration server SSL port |
|
Stateful Ingress |
OCI load balancer public subnet, TCP |
9999 |
IDCS app gateway port |
|
Stateful Ingress |
Oracle Java Cloud Service public subnet, TCP |
22 |
SSH access, so domain and binaries can be copied over |
|
Stateful Ingress |
Oracle WebLogic Server for OCI private subnet (self), TCP |
22 |
SSH access between the compute instances of Oracle WebLogic Server for OCI |
|
Stateful Ingress |
Oracle WebLogic Server for OCI private subnet (self), TCP |
9071 |
Used for provisioning and scaling |
|
Stateful Ingress |
Oracle WebLogic Server for OCI private subnet (self), TCP |
9073 |
IDCS app gateway for accessing the managed server |
|
Stateful Ingress |
Oracle WebLogic Server for OCI private subnet (self), TCP |
5556 |
Used for accessing node manager |
Table 2-6 Bastion Public Subnet
| Rule Type | Source CIDR and Protocol | Default Destination Port | Description |
|---|---|---|---|
|
Stateful Ingress |
Hosts with access to bastion, TCP |
22 |
SSH access, port forwarding |
Table 2-7 Access to OCI Database Public Subnet
| Rule Type | Source CIDR and Protocol | Default Destination Port | Description |
|---|---|---|---|
|
Stateful Ingress |
WLS for OCI private subnet, TCP |
1521 |
DB access |