Secure a Domain Using Identity Cloud Service
Use Oracle Identity Cloud Service to protect applications and restrict administrative access for an Oracle WebLogic Server domain that you created with Oracle WebLogic Server for OCI.
By default, a domain is configured to use the local WebLogic Server identity store to maintain administrators, application users, groups, and roles. These security elements are used to authenticate users, and to also authorize access to your applications and to tools like the WebLogic Server Administration Console.
When you create a domain running WebLogic Server, you can also choose to enable Oracle Identity Cloud Service for authentication. The following diagram illustrates this configuration.
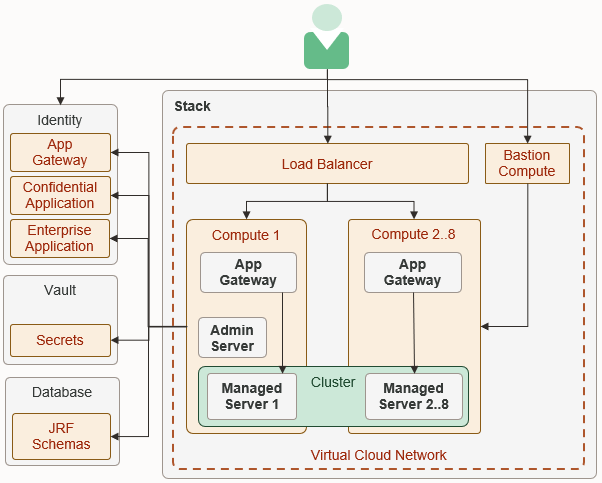
Description of the illustration architecture_idcs_diagram.png
See About Oracle Identity Cloud Service Concepts in Administering Oracle Identity Cloud Service.
Create WebLogic Administrator Groups
Create groups in Oracle Identity Cloud Service to grant users administrative access to your domain.
Global roles in WebLogic Server control the administrative operations that a user can perform in the domain. For example, users with the Deployer role can deploy Java applications to the domain. By default, these roles are assigned to group names like Deployers. After creating these groups in Oracle Identity Cloud
Service, you can add users to them.
When you create a domain, you specify a default administrative user. This user is configured in the default WebLogic Server identity store. You can use standard WebLogic Server tools like the Administration Console in order to modify this user or to change its password.
See these topics in Administering Oracle Identity Cloud Service:
Update WebLogic Administrator Roles
Map groups in Oracle Identity Cloud Service to the administrator roles in your domain.
By default, the global administrator roles in a domain are mapped to these groups.
AdministratorsDeployersOperatorsMonitors
If you do not modify the administrator roles in a domain, members of these groups in Oracle Identity Cloud Service will have access to all domains that you create with Oracle WebLogic Server for OCI and that you configure to use Oracle Identity Cloud Service.
Sign in to the WebLogic Server Administration Console for your domain. See Access the WebLogic Server Administration Console.
Note:
As of release 14c (14.1.2.0.0), the WebLogic Server Administration Console has been removed. For comparable functionality, you should use the WebLogic Remote Console. For more information, see Oracle WebLogic Remote Console.
- From the WebLogic Server Administration Console, click Security Realms.
- Click the default realm.
- Click the Roles and Policies tab.
- From the Roles table, expand Global Roles, and then expand Roles.
- Click View Role Conditions for the
Adminrole. - Click the group name assigned to this role. The default is Administrators.
- Enter the name of the Oracle Identity Cloud Service group to which you want to map to this role.
- Click OK, and then click Save.
- From the breadcrumb links at the top of the page, click Realm Roles.
- Repeat from step 4 for each administrator role that you want to update.
Update Protected Application Resources
Configure the URL patterns that Oracle Identity Cloud Service uses to determine which application requests require authentication for your domain.
Oracle WebLogic Server for OCI provisions each compute instance in the domain with the App Gateway software appliance. The App Gateway acts as a reverse proxy, intercepts HTTP requests to the domain, and ensures that the users are authenticated with Oracle Identity Cloud Service.
Oracle WebLogic Server for OCI also creates an enterprise application in Oracle Identity Cloud Service for the domain. The enterprise application defines which resources require the user to be authenticated, and which resources don't require authentication.
By default, all requests whose URI begins with
/__protected (two underscore characters followed by the word
"protected") are protected. For example, a client request to the URL
https://<lb_host>/__protected/myapp/doaction
requires authentication, while a request to https://<lb_host>/myapp/doaction does not.
Note:
Any changes to the Oracle Identity Cloud Service applications configuration take an hour to be propagated to the App Gateway running on the compute instances.See About Enterprise Applications in Administering Oracle Identity Cloud Service.
Update Application Deployment Descriptors
Secure a Java application that's deployed to your domain by updating the application’s context path, security constraints, and role assignments.
Oracle WebLogic Server supports the Java Enterprise Edition declarative model for securing web applications with XML deployment descriptors.
Let's assume that you have created a managed resource with Forms or Access
Token. Then, to ensure that the identity is propagated to the web application,
complete the following steps: