How SMIME Security Works
In addition to SSL encryption, Oracle-managed Service mailboxes and general Service mailboxes support S/MIME, an industry standard for ensuring the security of message content through the use of electronic signatures, encryption, or both.
An email address that uses S/MIME has a public certificate as well as a private key that corresponds to the public certificate. The public certificate authenticates the sender and can be used for encryption. The person who replies to the email can use the sender’s public certificate to encrypt the reply, which can then be decrypted only by the original sender using the original sender’s private key.
There are certain situations where S/MIME security options are not available.
- In Outreach and Feedback mailboxes.
- When editing multiple incidents simultaneously. You can send a response to more than one incident at a time, but you cannot use secure mail when doing so.
- When using delayed reporting on the Workspace editor. S/MIME works only if you clear the Delay Report Execution check box in the Report Behavior drop-down list for the Contacts relationship item control on the Workspace editor Design tab. See Overview of Workspace and Script Elements.
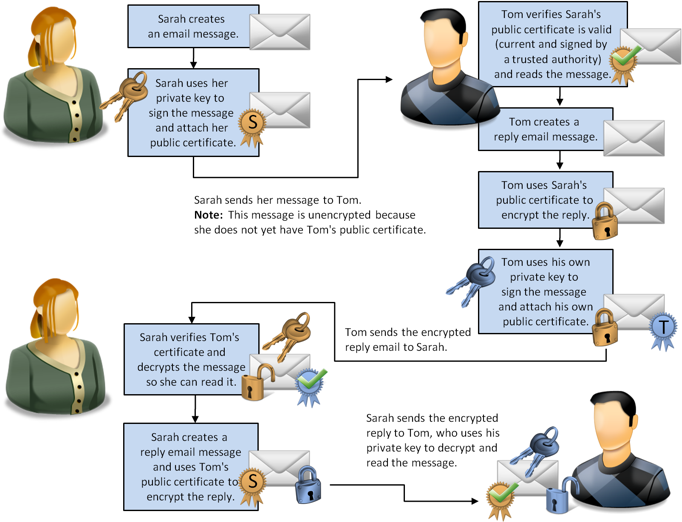
Customers who have S/MIME email can send messages signed with their public certificate to any Oracle-managed Service mailbox or general Service mailbox. When Techmail receives a signed message, it verifies and stores the customer’s certificate and uses it to encrypt any response messages sent to that customer. The customer can then decrypt the response using the private key for the certificate.
Service S/MIME settings also let you set conditions on how strictly Techmail validates a customer’s public certificate for incoming messages. If Techmail cannot verify a customer’s public certificate, it does not update the customer’s contact record with that certificate.
Note that the customer’s original message is not encrypted. In order to encrypt messages sent from a customer to an Oracle-managed Service mailbox or general Service mailbox, the mailbox must be configured with its own certificate and key, as described in the following procedure. Agent response emails are then signed with the mailbox certificate which customers can use to validate the messages and send encrypted replies. Techmail uses the certificate key to decrypt those replies and process the message contents normally.