2SSO Authentication
SSO Authentication
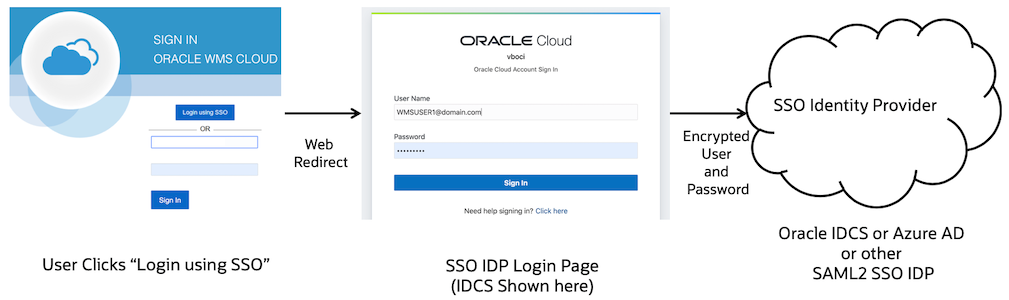
SAML2 SSO works a bit differently. The username and password are not entered in the WMS Cloud login page. The user instead clicks the “Login using SSO” button (which will be available after the SSO configuration has been setup by following SR process mentioned earlier). The page gets redirected to the Identity Provider’s login page where the user will login using their username linked to the IDP (this is stored in the “Alternate username” field in WMS Cloud). If the authentication succeeds, a token is returned back to the WMS Cloud and the user is logged in to the application.
Technical Configuration for SSO
For SAML2 SSO setup, the customer and Oracle exchange certain technical information needed to configure both systems.
| Customer Provides | Oracle provides |
|---|---|
|
|
Customer provided information:
The customer configures their IDP for Cloud WMS authentication, generates the SAML2 Metadata file, and sends it to Oracle. IDPs that support SAML2 SSO will have a mechanism to generate this file, including Oracle IDCS and Azure AD.
SAML2.0 MetaData - Customer must provide IDP metadata for SAML2.0, it can be provided in a metadata.xml file or a URL allowing Oracle to download the IDP metadata from customer site.
The specific fields that are used by Oracle are explained below. In addition, for IDCS, the MyApp URL is also needed (details below) and has to be sent separately as its not part of the metadata file.
IDCS SSO Information
| Item | Description |
|---|---|
| Issuer ID | Unique identifier of the IDP |
| MyApp URL | The binding that is used to send the response to the Identity provider. NOTE: IDCS also has an SSO_URL which is different. The Metadata does not include the MyApp URL |
| Response signature certificate (X509 Certificate) – PEM format |
Will verify tokens signed by IDCS |
| Domain name | Used to link WMS username with the SSO username, using "Alternate username" For example if the username is "jdoe"@somedomain.com, then domain name is somedomain.com. NOTE: Customers need to provide ALL domains that they need for WMS. We don’t support generic consumer domains (for example: @yahoo.com @gmail.com) |
Azure AD SSO Authentication
| Item | Description |
|---|---|
| Issuer ID | Unique identifier of the IDP
|
| Single Sign-On URL | The binding that is used to send the response to the Identity provider. |
| Response signature certificate (X509 Certificate) – PEM format |
Will verify tokens signed by the IDP |
| Domain name | Used to link WMS username with the SSO username, using "Alternate username" For example: if the username is jdoe @somedomain.com, then the domain name is somedomain.com. NOTE: Customers need to provide ALL domains that they need for WMS. We don’t support generic consumer domains (for example: @yahoo.com @gmail.com) |
<saml:Assertion xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ...> ... <saml:Subject> <saml:NameID>username@domain</saml:NameID> ... </saml:Subject> ... </saml:Assertion>