B Installing Oracle AVDF on Oracle Database Appliance (ODA)
Learn how to install Audit Vault Server or Database Firewall on Oracle Database Appliance.
The Oracle Database Appliance (ODA) is a database server appliance. It is the easiest and most affordable way to run Oracle Databases and applications in remote and edge computing environments. It reduces Oracle Database deployment time and management workload using a pre-built integrated system with management automation.
Oracle AVDF comprises of Audit Vault Server and Database Firewall. They are delivered as software appliance images that can be deployed on physical machines or virtual machines (VM). Audit Vault Server and Database Firewall can be deployed on Oracle Database Appliance by creating a KVM (Kernel-based Virtual Machine) guest instance on ODA.
This appendix contains an overview for installing Audit Vault Server and Database Firewall on Oracle Database Appliance.
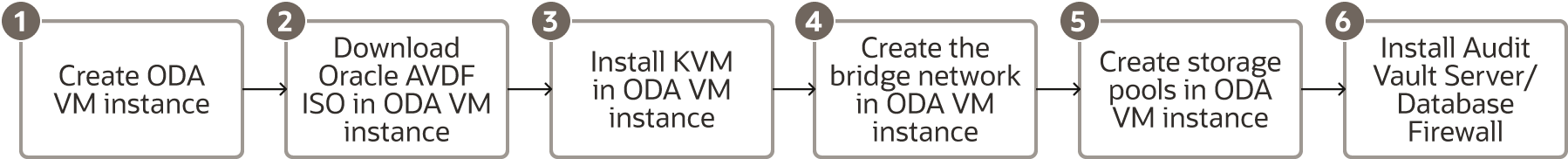
At the high level, below would be the flow of installation.
Follow these steps at a high level:
-
Prerequisites
- Create an ODA VM instance
- Download Oracle AVDF ISO files within the ODA VM instance
-
Install KVM on ODA VM instance
-
Install Audit Vault Server
- Create a storage pool for ISO files and Audit Vault Server installation
- Create a KVM guest instance
- Install Audit Vault Server or Database Firewall
-
Configure Audit Vault Server
- Deploy Audit Vault Agents
- Register the target database instance in the Audit Vault Server
- Start the Audit Vault Agent
- Configure the database instance as a target using the Audit Vault Server console
- Configure Auditing
- Provision Audit Policies
- Monitor Database Activity in Audit Vault Server
B.1 Completing the Installation Prerequisites
Learn about the prerequisites before the installation of Oracle AVDF on ODA.
B.2 Download the Oracle AVDF ISO Files
Learn about downloading and verifying the software to install Oracle AVDF on ODA.
Download Oracle AVDF ISO files using the VNC console for the ODA VM instance. Refer to Downloading and Verifying Oracle AVDF Software for detailed steps for complete information.
Here are high level steps to follow:
B.3 Installing KVM on ODA VM Instance for Running Oracle AVDF
Learn how to install KVM on ODA VM instance for running Oracle AVDF appliances.
Follow these steps to install KVM on the ODA VM instance, refer to the OS documentation about installing KVM hypervisor:
B.4 Configuring the Network on ODA VM Instance
Learn how to configure a bridge network on ODA VM instance to be used by the Oracle AVDF VM instance.
The purpose of this section is to create a bridge network for ODA VM instance, attach the virtual interface to the bridge, and plumb IP to the bridge.
Refer to the Oracle Linux documentation for more details about how to configure the network.
Follow these steps:
- From the bare metal host, access the ODA VM by
using:
virsh <ODA VM name> --console - Create the bridge
network:
< delete the existing ens3 configuration from network manager> # nmcli connection down ens3 # nmcli connection delete ens3 <create a bridge br0 and add port ens3 to the bridge br0> # nmcli connection add type bridge con-name br0 ifname br0 # nmcli connection add type ethernet slave-type bridge con-name br0-port1 ifname ens3 master br0 <configure IP, gateway, dns to the bridge> # nmcli connection modify br0 ipv4.addresses 'x.x.x.x/xx' # nmcli connection modify br0 ipv4.gateway 'y.y.y.y' # nmcli connection modify br0 ipv4.dns 'x.x.x.x' # nmcli connection modify br0 ipv4.dns-search 'example.com' # nmcli connection modify br0 ipv4.method manual
B.5 Installing the Audit Vault Server on the ODA VM Instance
Learn how to install the Audit Vault Server or Database Firewall on the ODA VM instance.
The ODA VM instance was installed following the steps in the previous topic.
Follow these steps on a high level to install Audit Vault Server or Database Firewall on the ODA VM instance
- Create a storage pool to upload ISO files.
- Create a storage pool for installing Audit Vault Server
- Create a KVM guest instance
- Install the Audit Vault Server
Follow these steps to create a storage pool in the ODA VM instance to upload Oracle AVDF ISO files:
- Connect to the Virtual Machine using the VNC Viewer as root user.
- Open a terminal and launch the virt-manager.
- Right click on QEMU/KVM. Choose Details, and then select the Storage tab.
- In the Storage tab of the virt-manager, click the plus button in the bottom left corner.
- Provide a Name from which you can quickly identify that it is for the installable ISO file.
- Select the Type of the storage pool.
For example:
dir: Filesystem Directory. - Provide the Target Path. It is the directory where
the Audit Vault Server ISO files will be stored. For example:
/u01/source/av. - Click Finish.
- The newly created storage pool appears on the left hand side. Select the pool.
- Copy or move the ISO file to this storage pool.
Follow these steps to create a storage pool for installing Audit Vault Server or Database Firewall. The appliance is installed on the storage pool.
- Connect to the Virtual Machine with VNC Viewer as the root user.
- Open a terminal and launch virt-manager.
- Right-click on QEMU/KVM. Then choose Details and select the Storage tab.
- Click the plus button in the bottom left corner.
- Provide a Name.
- Select the Type of the storage pool. For example:
dir: Filesystem Directory. - Provide the Target Path. It is the directory
where Audit Vault Server files are stored. For example:
/u01/kvm/av. - Click Finish.
- The new directory created appears on the left-hand side. Select the directory and then click the plus button next to Volumes.
- Enter the Name.
- Select the Format as
qcow2. - Specify the size in the Max Capacity field. This is for installing Audit Vault Server, which requires a minimum of 256 GB.
- Click Finish.
- The newly created entry appears in the table below the Volumes field. Verify the same.
Follow these steps to create a KVM guest instance. KVM can be managed through the command line or GUI tools. In this document, the focus is on using the GUI tools. Use VNC console to connect to the ODA VM instance. Open the gnome-terminal and follow the steps or commands.
- Connect to the Virtual Machine with VNC Viewer as the root user.
- Open a terminal and launch virt-manager.
- Select File and select New Virtual Machine.
- Select the
Local install media (ISO image or CDROM)option. - In the next few steps, choose the options based on the configuration,
which may differ. Select the
Use ISO imageoption and click Browse to select the first ISO file. - Deselect the checkbox Automatically detect operating system based on install media.
- Select
Linuxas the OS Type. - Choose the Version. For example,
Oracle Linux 7.7. - Choose Memory and CPU
settings based on the workload of the service
used on this KVM guest virtual machine. For example,
16384MB as Memory (RAM) and CPUs as4. - Click Forward.
- Select the radio button Select or create custom storage.
- Enter the path of the storage pool created earlier. For example:
/u01/kvm/av/av191.qcow2. - In the New VM dialog, enter the Name.
- Select the Customize configuration before install field.
- Expand the Network selection area, and select the previously created bridge.
- Select
virtioin the Device model field. - Add the MAC address of the vNIC, and click Apply.
- Click VirtIO Disk1 on the left, and expand Advanced Options.
- Select
SATAin the Disk bus field. - Click IDE CDROM 1 on the left, and ensure the Source path has the correct ISO file.
- Select
SATAin the Disk bus field.21. Click VirtIO Disk1 on the left, and expand Advanced Options. - Click Begin Installation in the top left corner of the dialog.
The virtual machine starts the installation and detects the vNIC network device attached to the virtual machine. The installation takes approximately one hour to complete. See Installing Audit Vault Server or Database Firewall for more information.
- The system boots, and the initial splash screen appears. This indicates the Oracle AVDF release is being installed.
- Enter the new root user password when prompted for change. Enter the same password when prompted for confirmation.
- See Post-Install Configuration Tasks for more information on the installation passphrase used for initial log in to the Audit Vault Server console.
- When prompted to insert the installation ISO again to continue, go to the KVM console.
- Click View and then Details.
- Click IDE CDROM1 on the left. In the Source path field, click Connect to specify the ISO file path.
- Select the
Image Locationoption and click Browse to navigate and select the ISO file. - Click Choose Volume.
- Click the terminal icon to switch to the installation console.
- Log in as root user to continue with the installation.
- Select the default network interface. Ensure the MAC address is correct.
-
Set up the network configuration by entering the following fields:
-
IP address: Enter the IP address that is used for Audit Vault Server installation.
-
Network mask
-
Gateway: Enter the IP address of the network interface if a gateway is required. Else, clear the field before saving.
-
- Press the Tab key to navigate to the OK button, and press the Enter button. The installation begins and may take up to two hours to complete.
- A confirmation message is displayed on the screen after the installation is completed. Click OK.
- In the host VM instance, open a web browser. Enter
https://<VM Private IP address of the vNIC assigned to Oracle AVDF VM>/console. - Choose to accept and continue to connect to the Audit Vault Server console.
- Enter the password chosen earlier to log in.
- When prompted, enter the user name of the super administrator and super auditor. Set the repository encryption password, support user password (for SSH access to VM), root user password (for root privilege on the VM). See Accessing the Audit Vault Server Post-Install Configuration Page for more information.
-
Expand the Time Setup region, and select
Use NTP. Enter Server 1 IP address and click Test Server.Note: Time difference between the Audit Vault Server and target negatively impacts the audit collection.
- Check the network connectivity between the Audit Vault Server and targets by using ICMP ping. If all the previous steps were correctly performed, the Audit Vault Server and targets will connect with each other.
B.6 Installing the Database Firewall on the ODA VM Instance
Learn how to install the Database Firewall on ODA (Oracle Database Appliance) VM instance.
Follow the same steps documented in the previous section Installing the Audit Vault Server on the ODA VM Instance pointing to the Database Firewall ISO.
After the Database Firewall VM is ready, you need to follow additional steps to register the Database Firewall.
Additionally, follow these steps: