4 Oracle Key Vault Installation and Configuration
Installing Oracle Key Vault entails ensuring that the environment meets the necessary requirements before you begin the installation and configuration.
- About Oracle Key Vault Installation and Configuration
Oracle Key Vault is a software appliance that is delivered as an ISO image. - Oracle Key Vault Installation Requirements
The Oracle Key Vault installation requirements cover system requirements such as CPU, memory, disk space, network interfaces, and supported endpoint platforms. - Installing and Configuring Oracle Key Vault
You must download the Oracle Key Vault application software, and then you can perform the installation. - Logging In to the Oracle Key Vault Management Console
To use Oracle Key Vault, you can log in to the Oracle Key Vault management console. - Upgrading the Oracle Key Vault Server Software
The upgrade includes the Oracle Key Vault server software and utilities that control the associated endpoint software. - Overview of the Oracle Key Vault Management Console
The Oracle Key Vault management console provides a graphical user interface for System Administrators, Key Administrators, and Audit Managers. - Performing Actions and Searches
The Oracle Key Vault management console enables you to perform standard actions and search operations, as well as get help information.
4.1 About Oracle Key Vault Installation and Configuration
Oracle Key Vault is a software appliance that is delivered as an ISO image.
The software appliance consists of a pre-configured operating system, an Oracle database, and the Oracle Key Vault application. You must install Oracle Key Vault onto its own dedicated server.
Parent topic: Oracle Key Vault Installation and Configuration
4.2 Oracle Key Vault Installation Requirements
The Oracle Key Vault installation requirements cover system requirements such as CPU, memory, disk space, network interfaces, and supported endpoint platforms.
- System Requirements
System requirements include CPU, memory, disk, network interface, hardware compatibility, and RESTful services client. - Network Port Requirements
Network port requirements includes requirements for SSH/SCP, SNMP, HTTPS, listeners, KMIP, and TCP ports. - Supported Endpoint Platforms
Oracle Key Vault supports both UNIX and Windows endpoint platforms. - Endpoint Database Requirements
For endpoints, Oracle Key Vault supports Oracle Database release 10 and later.
Parent topic: Oracle Key Vault Installation and Configuration
4.2.1 System Requirements
System requirements include CPU, memory, disk, network interface, hardware compatibility, and RESTful services client.
The Oracle Key Vault installation removes existing software on a server.
Deployment on virtual machines is not recommended for production systems. However, virtual machines are useful for testing and proof of concept purposes.
The minimum hardware requirements for deploying the Oracle Key Vault software appliance are:
-
CPU: Minimum: x86-64 16 cores. Recommended: 24-48 cores with cryptographic acceleration support (Intel AESNI).
-
Memory: Minimum 16 GB of RAM. Recommended: 32–64 GB.
-
Disk: Minimum 2 TB. Recommended: 4 TB.
-
Network interface: One network interface.
-
Hardware Compatibility: Refer to the hardware compatibility list (HCL) for Oracle Linux Release 6 Update 10 at the link in the Related Topics section.
Note:
You can find the supported hardware from the hardware certification list for Oracle Linux and Oracle VM. Filter the results by selecting All Operating Systems and choosing Oracle Linux 6.10.Oracle Key Vault release 18.1 supports both Legacy BIOS and UEFI BIOS boot modes. The support for UEFI BIOS mode allows the installation of Oracle Key Vault on servers that exclusively support UEFI BIOS only, such as Oracle X7-2 Server. Oracle Key Vault can be installed on Oracle X7–2 servers as a standalone server, a primary-standby configuration, or a multi-master cluster configuration.
-
RESTful Services Client: If RESTful Services are enabled, then each endpoint that connects to the Oracle Key Vault management console must have at least Java 1.7.0.21 installed.
The REST API requires the cURL utility. Ensure that you have installed a cURL version that supports Transport Layer Security (TLS) 1.2 or later on the endpoint before using the REST API to provision endpoints.
Note:
For deployment with a large number of endpoints, the hardware requirement may need to scale to meet the workload.Related Topics
Parent topic: Oracle Key Vault Installation Requirements
4.2.2 Network Port Requirements
Network port requirements includes requirements for SSH/SCP, SNMP, HTTPS, listeners, KMIP, and TCP ports.
Oracle Key Vault and its endpoints use a set of specific ports for communication. Network administrators must ensure that these ports are open in the network firewall.
The following table lists the required network ports for Oracle Key Vault:
Table 4-1 Ports Required for Oracle Key Vault
| Port Number | Protocol | Descriptions |
|---|---|---|
|
|
SSH/SCP port |
Used by Oracle Key Vault administrators and support personnel to remotely administer Oracle Key Vault |
|
|
SNMP port |
Used by monitoring software to poll Oracle Key Vault for system information |
|
|
HTTPS port |
Used by web clients such as browsers and RESTful Services to communicate with Oracle Key Vault |
|
|
Database TCPS listener port |
Listener port used in a primary-standby configuration by Oracle Data Guard to communicate between the primary and standby server |
|
|
Database TCPS listener port |
Listener port used in a primary-standby configuration to run OS commands like synchronizing wallets and configuration files through HTTPS. This port is also used when you add a new node to a cluster. |
|
|
KMIP port |
Used by Oracle Key Vault endpoints and third party KMIP clients to communicate with the Oracle Key Vault KMIP Server |
|
|
TCP port |
Used by Oracle GoldenGate for transmitting data in a Multi-Master Cluster configuration. |
Parent topic: Oracle Key Vault Installation Requirements
4.2.3 Supported Endpoint Platforms
Oracle Key Vault supports both UNIX and Windows endpoint platforms.
Oracle supports both 32-bit and 64-bit Linux endpoints. However, only 64-bit endpoints are supported for Oracle databases that use the online master key. The operating systems on which the endpoint runs must be compatible with Transport Layer Security (TLS) 1.2, either directly or with appropriate patches.
The supported endpoint platforms in this release are as follows:
-
Oracle Linux (6 and 7)
-
Oracle Solaris (10 and 11)
-
Oracle Solaris Sparc (10 and 11)
-
RHEL 6 and 7
-
IBM AIX (6.1, and 7.1) and AIX 5.3 in a limited capacity
-
HP-UX (IA) (11.31)
-
Windows Server 2008
-
Windows Server 2012
Parent topic: Oracle Key Vault Installation Requirements
4.2.4 Endpoint Database Requirements
For endpoints, Oracle Key Vault supports Oracle Database release 10 and later.
Administrators who manage endpoints that are Oracle Database 10g release 2 and later can use the okvutil upload command to upload Oracle wallets to Oracle Key Vault. Administrators who manage endpoints that are Oracle Database 11g release 2 and later can use the online master key to manage TDE master encryption keys.
Administrators who manage endpoints that are Oracle Database may need to set the COMPATIBLE initialization parameter.
For an endpoint that is Oracle Database release 11.2 or 12.1, set the COMPATIBLE initialization parameter to 11.2.0.0 or later. For example:
SQL> ALTER SYSTEM SET COMPATIBLE = 11.2.0.0 SCOPE=SPFILE;
This applies to an Oracle Database endpoint that use the online master key to manage TDE master encryption keys. This compatibility mode setting is not required for Oracle wallet upload or download operations.
Also note that after setting the COMPATIBLE parameter to 11.2.0.0, you cannot set it to a lower value such as 10.2. After you set the COMPATIBLE parameter, you must restart the database.
Related Topics
Parent topic: Oracle Key Vault Installation Requirements
4.3 Installing and Configuring Oracle Key Vault
You must download the Oracle Key Vault application software, and then you can perform the installation.
- Downloading the Oracle Key Vault Appliance Software
You can download executables for both a fresh Oracle Key Vault installation or an upgrade. - Installing the Oracle Key Vault Appliance Software
The Oracle Key Vault installation process installs all the required software components onto a dedicated server. - Performing Post-Installation Tasks
After you install Oracle Key Vault, you must complete a set of post-installation tasks.
Parent topic: Oracle Key Vault Installation and Configuration
4.3.1 Downloading the Oracle Key Vault Appliance Software
You can download executables for both a fresh Oracle Key Vault installation or an upgrade.
For a fresh installation, you can download the Oracle Key Vault appliance software from Software Delivery Cloud. You cannot use this package to upgrade Oracle Key Vault. For an upgrade, you can download the Oracle Key Vault upgrade software from the My Oracle Support website.
Parent topic: Installing and Configuring Oracle Key Vault
4.3.2 Installing the Oracle Key Vault Appliance Software
The Oracle Key Vault installation process installs all the required software components onto a dedicated server.
The installation process may take from 30 minutes or longer to complete, depending on the server resources where you are installing Oracle Key Vault.
Caution:
The Oracle Key Vault installation wipes the server and installs a customized Oracle Linux 6 Update 10. The installation erases existing software and data on the server.
-
Ensure that the server meets the recommended requirements.
-
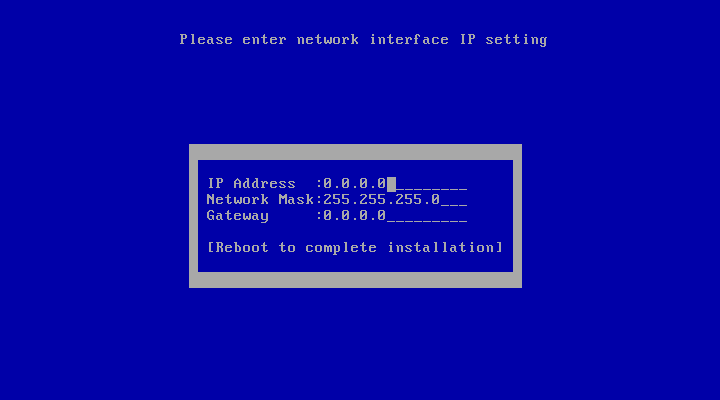
Request a fixed IP address, network mask, and gateway address from your network administrator for the dedicated server. You will need this information to configure the network.
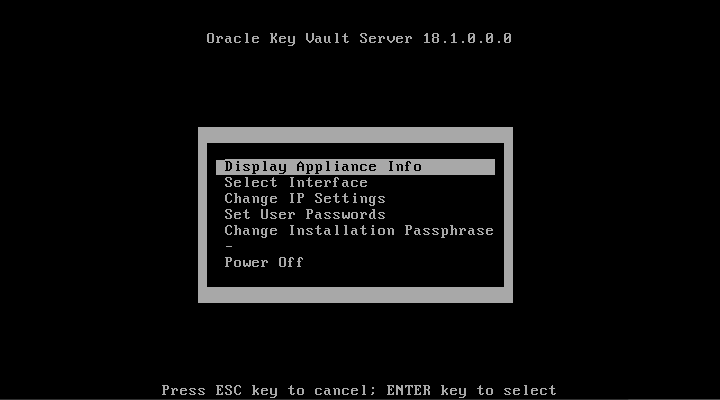
To install the Oracle Key Vault appliance:
Parent topic: Installing and Configuring Oracle Key Vault
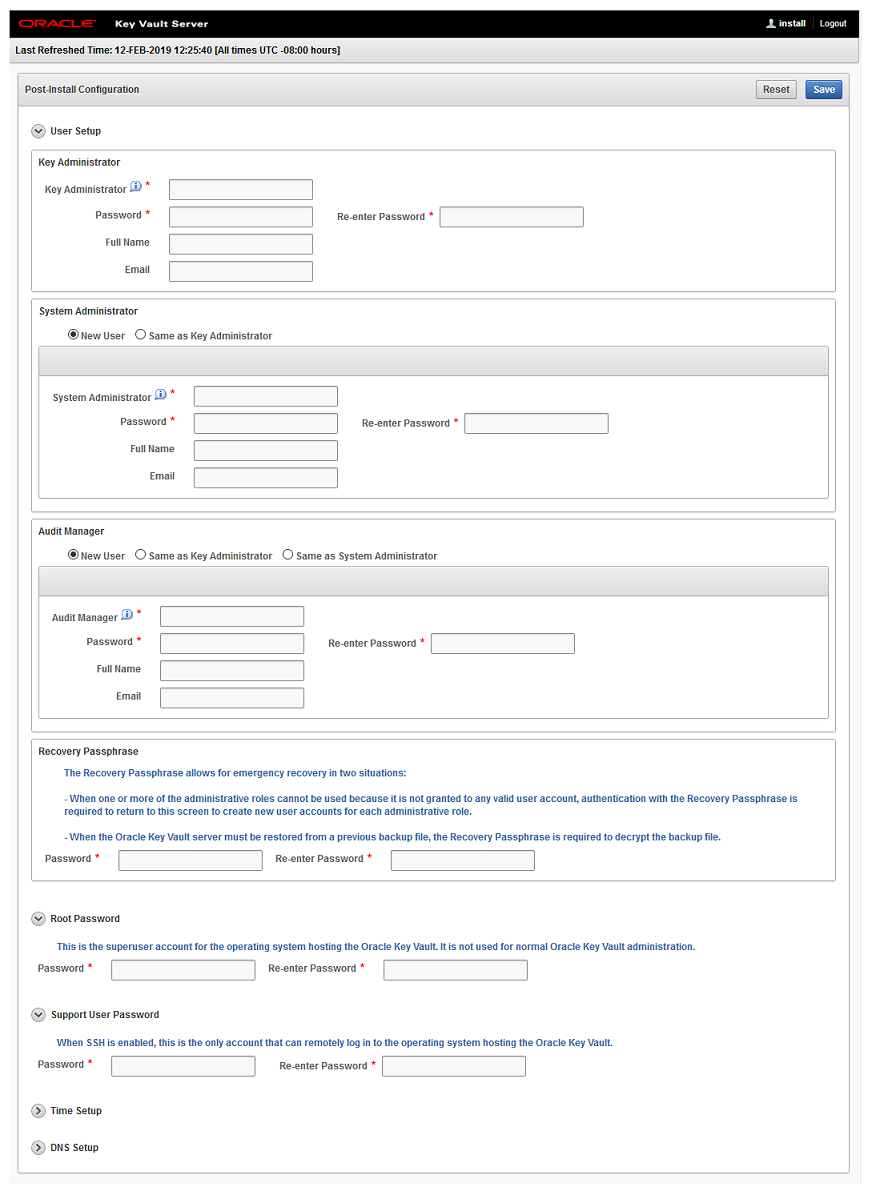
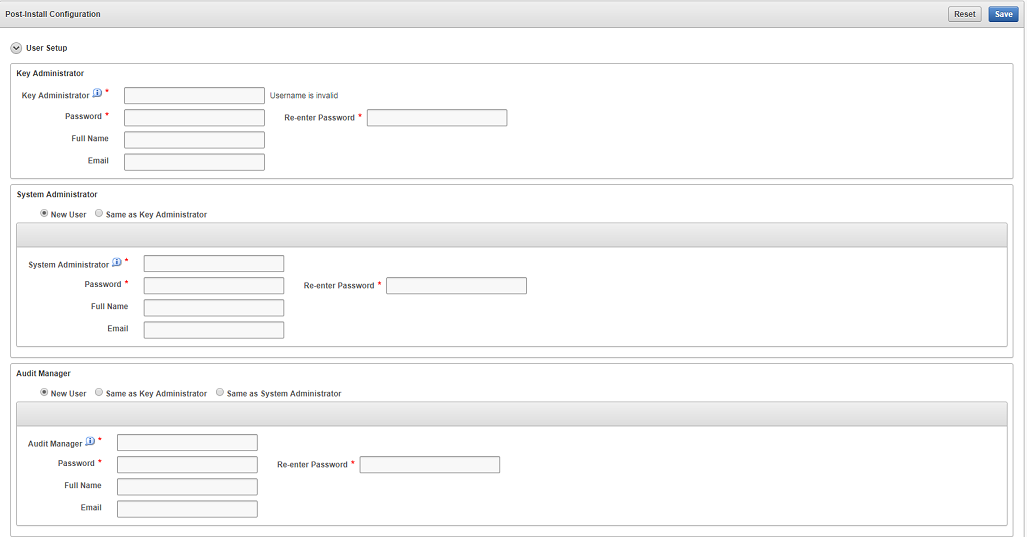
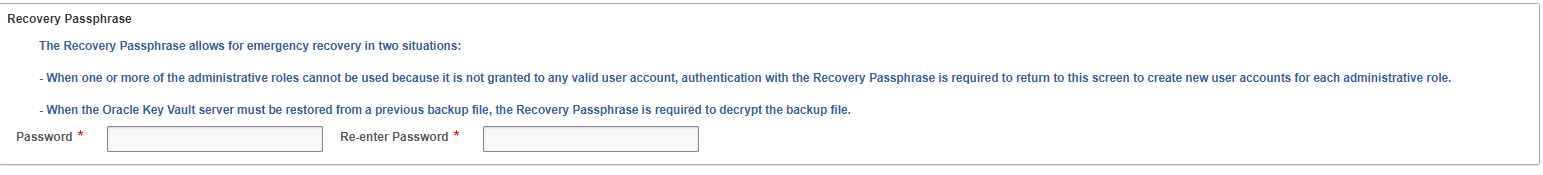
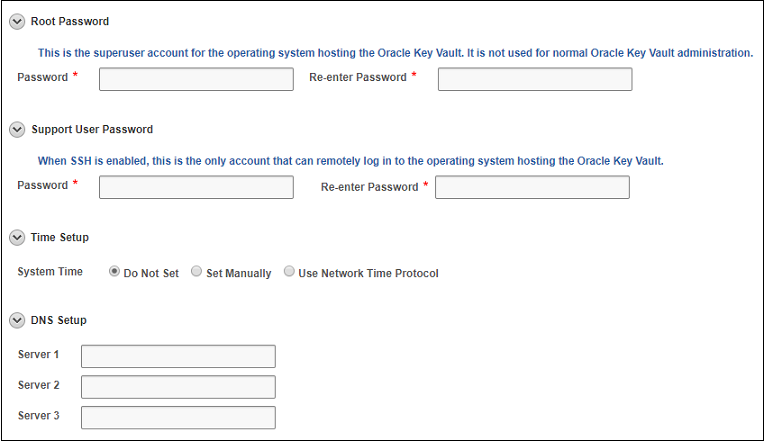
4.3.3 Performing Post-Installation Tasks
After you install Oracle Key Vault, you must complete a set of post-installation tasks.
These tasks include configuring the administrative user accounts and passwords for recovery, and operating system accounts and passwords for root and support.
Related Topics
Parent topic: Installing and Configuring Oracle Key Vault
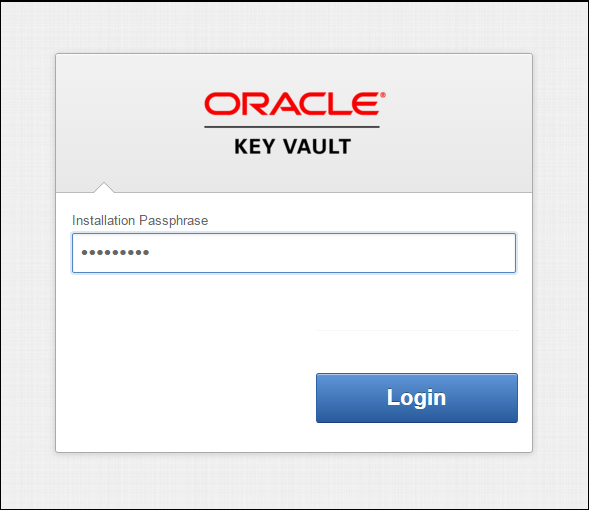
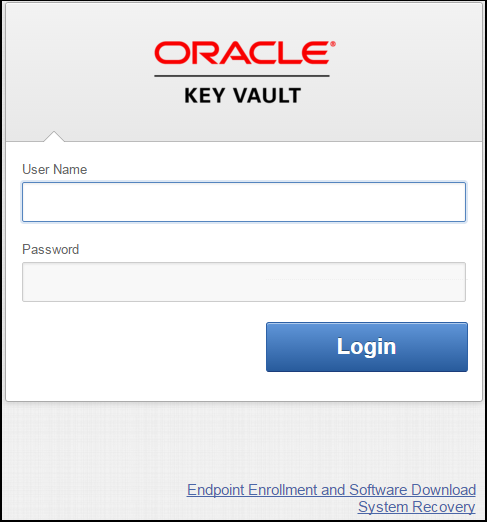
4.4 Logging In to the Oracle Key Vault Management Console
To use Oracle Key Vault, you can log in to the Oracle Key Vault management console.
Parent topic: Oracle Key Vault Installation and Configuration
4.5 Upgrading the Oracle Key Vault Server Software
The upgrade includes the Oracle Key Vault server software and utilities that control the associated endpoint software.
- About Upgrading the Oracle Key Vault Server Software
When you upgrade the Oracle Key Vault server software appliance, also upgrade the endpoint software to get access to the latest enhancements. - Step 1: Back Up the Server Before You Upgrade
Before you upgrade the Oracle Key Vault server, back up this server so that you can recover data in case the upgrade fails. - Step 2: Perform Pre-Upgrade Tasks
To ensure a smooth upgrade to Oracle Key Vault, you should prepare the server you are upgrading. - Step 3: Upgrade the Oracle Key Vault Server or Server Pair
You can upgrade a standalone Oracle Key Vault server or a pair of Oracle Key Vault servers in a primary-standby deployment. - Step 4: Upgrade the Endpoint Software
As part of the upgrade, you must reenroll endpoints created in earlier releases of Oracle Key Vault, or update the endpoint software. - Step 5: If Necessary, Remove Old Kernels
Oracle recommends that you clean up the older kernels that were left behind after the upgrade. - Step 6: If Necessary, Add Disk Space to Extend Swap Space
If you upgraded from an earlier release, you should extend swap space to accommodate the new Oracle Key Vault software. - Step 7: If Necessary, Remove SSH-Related DSA Keys
You should remove SSH-related DSA keys left behind after the upgrade, because they can cause problems with some code analysis tools. - Step 8: Back Up the Upgraded Oracle Key Vault Server
You must perform server backup and user password tasks after completing a successful upgrade.
Parent topic: Oracle Key Vault Installation and Configuration
4.5.1 About Upgrading the Oracle Key Vault Server Software
When you upgrade the Oracle Key Vault server software appliance, also upgrade the endpoint software to get access to the latest enhancements.
However, the endpoint software downloaded from the previous Oracle Key Vault release will continue to function with the upgraded Oracle Key Vault server.
You must upgrade in the order shown: first perform a full backup of Oracle Key Vault, upgrade the Oracle Key Vault server or server pair in the case of a primary-standby deployment, the endpoint software, and last, perform another full backup of the upgraded server. Note that upgrading requires a restart of the Oracle Key Vault server.
The Oracle Key Vault server is not available to endpoints for a limited duration during the upgrade. You can enable the persistent cache feature to enable endpoints to continue operation during the upgrade process.
Before you begin the upgrade, refer to Oracle Key Vault Release Notes for additional information about performing upgrades.
Related Topics
Parent topic: Upgrading the Oracle Key Vault Server Software
4.5.2 Step 1: Back Up the Server Before You Upgrade
Before you upgrade the Oracle Key Vault server, back up this server so that you can recover data in case the upgrade fails.
Caution:
Do not bypass this step. Back up the server before you perform the upgrade so that your data is safe and recoverable.
Related Topics
Parent topic: Upgrading the Oracle Key Vault Server Software
4.5.3 Step 2: Perform Pre-Upgrade Tasks
To ensure a smooth upgrade to Oracle Key Vault, you should prepare the server you are upgrading.
Parent topic: Upgrading the Oracle Key Vault Server Software
4.5.4 Step 3: Upgrade the Oracle Key Vault Server or Server Pair
You can upgrade a standalone Oracle Key Vault server or a pair of Oracle Key Vault servers in a primary-standby deployment.
- About Upgrading an Oracle Key Vault Server or Server Pair
You can deploy Oracle Key Vault as a standalone server in test and development environments or in a primary-standby configuration in production environments. - Upgrading a Standalone Oracle Key Vault Server
A single Oracle Key Vault server in a standalone deployment is the most typical deployment in test and development environments. - Upgrading a Pair of Oracle Key Vault Servers in a Primary-Standby Deployment
You should allocate several hours to upgrade the primary server after upgrading the standby.
Parent topic: Upgrading the Oracle Key Vault Server Software
4.5.4.1 About Upgrading an Oracle Key Vault Server or Server Pair
You can deploy Oracle Key Vault as a standalone server in test and development environments or in a primary-standby configuration in production environments.
In a standalone deployment you must upgrade a single Oracle Key Vault server, but in a primary-standby deployment you must upgrade both primary and standby Oracle Key Vault servers. Note that persistent caching enables endpoints to continue to be operational during the upgrade process.
Note:
If you are upgrading from a system with 4 GB memory, first add an additional 12 GB memory to the system before upgrading.Related Topics
4.5.4.2 Upgrading a Standalone Oracle Key Vault Server
A single Oracle Key Vault server in a standalone deployment is the most typical deployment in test and development environments.
4.5.4.3 Upgrading a Pair of Oracle Key Vault Servers in a Primary-Standby Deployment
You should allocate several hours to upgrade the primary server after upgrading the standby.
4.5.5 Step 4: Upgrade the Endpoint Software
As part of the upgrade, you must reenroll endpoints created in earlier releases of Oracle Key Vault, or update the endpoint software.
-
Ensure that you have upgraded the Oracle Key Vault servers. If you are upgrading the endpoint software for an Oracle database configured for direct-connect, then shut down the database.
-
Download the endpoint software (
okvclient.jar) for your platform from the Oracle Key Vault server as follows:-
Go to the Oracle Key Vault management console login screen.
-
Click the Endpoint Enrollment and Software Download link.
-
In the Download Endpoint Software Only section, select the appropriate platform from the drop-down list.
-
Click the Download button.
-
-
Identify the path to your existing endpoint installation that you are about to upgrade (for example,
/home/oracle/okvutil). -
Install the endpoint software by executing the following command:
java -jar okvclient.jar -dexisting_endpoint_directory_pathFor example:
java -jar okvclient.jar -d /home/oracle/okvutil
- Install the updated PKCS#11 library file.
This step is needed only for online TDE master encryption key management by Oracle Key Vault.
- On UNIX/Linux platforms: Run
root.shfrom thebindirectory of endpoint installation directory to copy the latestliborapkcs.sofile for Oracle Database endpoints.$ sudo $OKV_HOME/bin/root.sh
Or
$ su - # bin/root.sh
- On Windows platforms: Run
root.batfrom thebindirectory of endpoint installation directory to copy the latestliborapkcs.dllfile for Oracle Database endpoints. You will be prompted for the version of the database in use.bin\root.bat
- On UNIX/Linux platforms: Run
-
Restart the endpoint if it was shut down.
Related Topics
Parent topic: Upgrading the Oracle Key Vault Server Software
4.5.6 Step 5: If Necessary, Remove Old Kernels
Oracle recommends that you clean up the older kernels that were left behind after the upgrade.
Parent topic: Upgrading the Oracle Key Vault Server Software
4.5.7 Step 6: If Necessary, Add Disk Space to Extend Swap Space
If you upgraded from an earlier release, you should extend swap space to accommodate the new Oracle Key Vault software.
Parent topic: Upgrading the Oracle Key Vault Server Software
4.5.8 Step 7: If Necessary, Remove SSH-Related DSA Keys
You should remove SSH-related DSA keys left behind after the upgrade, because they can cause problems with some code analysis tools.
Parent topic: Upgrading the Oracle Key Vault Server Software
4.5.9 Step 8: Back Up the Upgraded Oracle Key Vault Server
You must perform server backup and user password tasks after completing a successful upgrade.
-
Take a full backup of the upgraded Oracle Key Vault Server Database to a new remote destination. Avoid using the old backup destination for the new backups.
-
Schedule a new periodic incremental backup to the new destination defined in the step above.
-
Password hashing has been upgraded to a more secure standard than in earlier releases. This change affects the operating system passwords,
supportandroot. You must change Oracle Key Vault administrative passwords after the upgrade to take advantage of the more secure hash.
Related Topics
Parent topic: Upgrading the Oracle Key Vault Server Software
4.6 Overview of the Oracle Key Vault Management Console
The Oracle Key Vault management console provides a graphical user interface for System Administrators, Key Administrators, and Audit Managers.
The Oracle Key Vault management console is a browser-based console that connects to the server using the https secure communication channel. It provides the graphical user interface for Oracle Key Vault, where users can perform tasks such as the following:
-
Setting up and managing the cluster
-
Creating and managing users, endpoints, and their respective groups
-
Creating and managing virtual wallets and security objects
-
Setting system settings, like network and other services
-
Setting up primary-standby
-
Performing backups
Parent topic: Oracle Key Vault Installation and Configuration
4.7 Performing Actions and Searches
The Oracle Key Vault management console enables you to perform standard actions and search operations, as well as get help information.
Many of the tab and menu pages contain an Actions menu or Search bars that allow you to search and perform actions on lists and the results of searches. The Help selection of the Actions list provides detailed help for using these features.
- Actions Menus
The actions available from an Actions drop-down menu can vary but typically include a set of standard menu items. - Search Bars
Along with Actions menus, many tabs in the Oracle Key Vault management console contain search bars.
Parent topic: Oracle Key Vault Installation and Configuration
4.7.1 Actions Menus
The actions available from an Actions drop-down menu can vary but typically include a set of standard menu items.
These items are as follows:
-
Select Columns: Select which column should be displayed.
-
Filter: Filter by column or row and a user-defined expression.
-
Rows Per Page: Choose how many rows you want to view .
-
Format: Choose formatting such as Sort, Control Break, Highlight, Compute, Aggregate, Chart, and Group By.
-
Save Report: Save reports.
-
Reset: Reset the report settings, removing any customizations.
-
Help: Get information about these actions.
-
Download: Download the result set in CSV or HTML.
Parent topic: Performing Actions and Searches
4.7.2 Search Bars
Along with Actions menus, many tabs in the Oracle Key Vault management console contain search bars.
Parent topic: Performing Actions and Searches