7 Managing Oracle Key Vault Users
Oracle Key Vault users administer the system, enroll endpoints, manage users and endpoints, control access to security objects, and grant other users administrative roles.
- Managing User Accounts
You can create Oracle Key Vault user accounts, grant these users Key Vault administrative roles, and add the users to user groups. - Managing Administrative Roles and Privileges
Oracle Key Vault has predefined roles that you can grant to (or change) or revoke from users. - Managing User Passwords
You or the user can change the user's password. You also can have passwords reset automatically. - Managing User Email
Oracle Key Vault users should have their current email on file so that they can receive alerts such as system changes. - Managing User Groups
You can organize users who have a common purpose into a named user group.
7.1 Managing User Accounts
You can create Oracle Key Vault user accounts, grant these users Key Vault administrative roles, and add the users to user groups.
- About Oracle Key Vault User Accounts
Oracle Key Vault users fulfill multiple functions. - How a Multi-Master Cluster Affects User Accounts
An Oracle Key Vault multi-master cluster environment affects users in various ways. - Creating an Oracle Key Vault User Account
A user with the System Administrator role can create user accounts from the Oracle Key Vault management console. - Viewing User Account Details
All administrative users can view the list of Oracle Key Vault user accounts and their details. - Deleting an Oracle Key Vault User Account
Deleting an Oracle Key Vault user removes the user from any user groups the user was part of in Oracle Key Vault.
Parent topic: Managing Oracle Key Vault Users
7.1.1 About Oracle Key Vault User Accounts
Oracle Key Vault users fulfill multiple functions.
An important user function is to register and enroll Oracle Key Vault endpoints, enabling the user to manage his or her security objects by using Oracle Key Vault.
There are two types of Oracle Key Vault users:
-
Administrative users who have one or more of the three administrative roles: System Administrator, Key Administrator, or Audit Manager
-
Ordinary users who have none of the administrative roles, but who have access to security objects
Separation of duties in Oracle Key Vault means that users with an administrative role have access to functions pertaining to their role, but not other roles. For example, only a user with the System Administrator role has access to the full System tab, not users with the Key Administrator or Audit Manager roles. Similarly, a system administrator can add endpoints, but cannot create endpoint groups. The user interface elements needed to create endpoint groups are visible only to the key administrator.
Users who have no administrative role can be granted access to security objects that are specific to their function. For example, you can grant a user access to a specific virtual wallet. This user can log into the Oracle Key Vault management console and add, manage, and delete his or her own security objects, but he or she cannot see system menus, details of other users and endpoints, their wallets, or audit reports.
Although the separation of user duties is recommended, you can have a single user perform all the administrative functions by granting that user all the administrative roles.
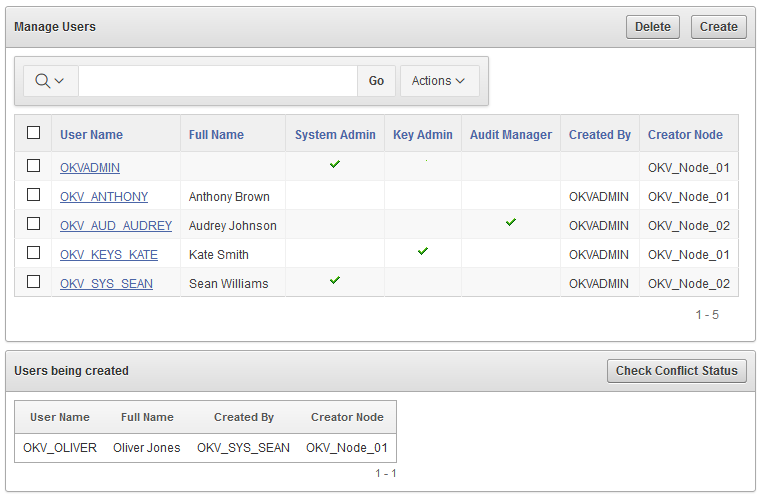
Oracle Key Vault does not permit the user name to be the same as the name of another user or an endpoint. If you are creating users in a multi-master cluster environment, there is a chance that user with the same name will be created in another node at the same time. In that case, Oracle Key Vault checks for naming conflicts and will automatically rename the user account that was created after the first user account of that name. You must drop the second user and then recreate it with a different name.
Parent topic: Managing User Accounts
7.1.2 How a Multi-Master Cluster Affects User Accounts
An Oracle Key Vault multi-master cluster environment affects users in various ways.
These can include expanding the activities that they can perform and ensuring that their names do not conflict with other objects in the cluster environment.
- Multi-Master Cluster Effect on System Administrator Users
The user who is granted the System Administrator role is responsible for managing the cluster configuration. - Multi-Master Cluster Effect on Key Administrator Users
The user who is granted the Key Adminstrator role manages endpoint groups, user groups, wallets, and objects. - Multi-Master Cluster Effect on Audit Manager Users
The user who is granted the Audit Manager role is responsible for configuring audit settings. - Multi-Master Cluster Effect on Administration Users
Administrative users can have any combination of the administration roles, including the System Administrator, Key Administrator, and Audit Manager roles. - Multi-Master Cluster Effect on System Users
System users are responsible for the operating system of each Oracle Key Vault appliance, server, and node.
Parent topic: Managing User Accounts
7.1.2.1 Multi-Master Cluster Effect on System Administrator Users
The user who is granted the System Administrator role is responsible for managing the cluster configuration.
The System Administrator role in a multi-master cluster includes the following responsibilities:
- All system administrator responsibilities for a single Oracle Key Vault server
- Cluster initialization, converting the first Oracle Key Vault server to the initial node
- Adding and removing nodes from the cluster
- Disabling and enabling nodes in the cluster
- Managing cluster-wide system settings
- Monitoring cluster operations and cluster health indicators
- Enabling and disabling replication between nodes
- Monitoring and resolving data and naming conflicts
- Monitoring and reacting to cluster alerts
- Managing cluster settings
Parent topic: How a Multi-Master Cluster Affects User Accounts
7.1.2.2 Multi-Master Cluster Effect on Key Administrator Users
The user who is granted the Key Adminstrator role manages endpoint groups, user groups, wallets, and objects.
In a multi-master cluster, when these items are uploaded in separate nodes and in separate data centers, name conflicts can occur. The key administrator provides input to the system administrator to resolve these conflicts for wallets, KMIP objects, endpoint groups, and user groups.
Related Topics
Parent topic: How a Multi-Master Cluster Affects User Accounts
7.1.2.3 Multi-Master Cluster Effect on Audit Manager Users
The user who is granted the Audit Manager role is responsible for configuring audit settings.
In a multi-master cluster environment, this user can configure audit settings for the entire cluster and for individual nodes. The audit manager user can use different setting for different nodes, if necessary. However, this user can also unify audit settings across the entire cluster.
The audit manager can replicate audit trails between nodes, if necessary. However, this can result in significant traffic between nodes, so the audit manager can turn on or off the audit trail replication. By default, the audit trails replication is turned off.
Parent topic: How a Multi-Master Cluster Affects User Accounts
7.1.2.4 Multi-Master Cluster Effect on Administration Users
Administrative users can have any combination of the administration roles, including the System Administrator, Key Administrator, and Audit Manager roles.
Administrative user information created in the Oracle Key Vault server that is used as the initial node seeds the cluster.
New servers added to a cluster will get administrative user information from the cluster. Administrator information that is created on the server for the purpose of inducting the server into the cluster will be removed.
Administrative users that are created in a node after the node joins an Oracle Key Vault cluster will have a cluster-wide presence. New administrative users that are added to the Oracle Key Vault cluster on different Oracle Key Vault nodes may have name conflicts. When the user account is created, Oracle Key Vault automatically resolves the administrative user name conflicts. User and endpoint conflicts will displayed in the Conflicts Resolution page and administrators can choose to rename endpoint conflicts. If there is a user name conflict, then you must either accept the automatically generated user name, or delete and recreate the user. User accounts will not be available for use and will be placed in a PENDING state until the name resolution is completed.
Related Topics
Parent topic: How a Multi-Master Cluster Affects User Accounts
7.1.2.5 Multi-Master Cluster Effect on System Users
System users are responsible for the operating system of each Oracle Key Vault appliance, server, and node.
Oracle Key Vault servers are first installed and later configured to become nodes of an Oracle Key Vault cluster. As part of the server configuration, the operating system users (support and root) are created. Those users will remain unchanged after the server joins a cluster.
The same support and root passwords should be used for all the Oracle Key Vault nodes. Unlike Oracle Key Vault administrative accounts that are replicated, the support and root accounts are operating system users, and their passwords are not automatically synchronized across the cluster. Therefore, each node can potentially have a different support or root user password, making it difficult to manage multiple nodes of the cluster.
Parent topic: How a Multi-Master Cluster Affects User Accounts
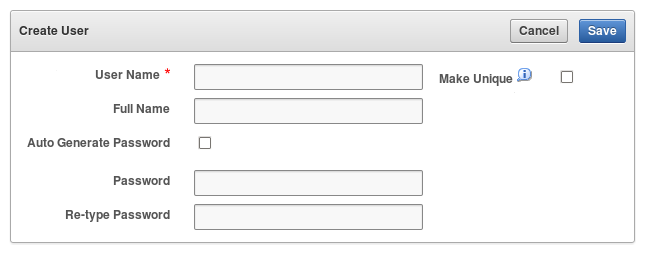
7.1.3 Creating an Oracle Key Vault User Account
A user with the System Administrator role can create user accounts from the Oracle Key Vault management console.
Related Topics
Parent topic: Managing User Accounts
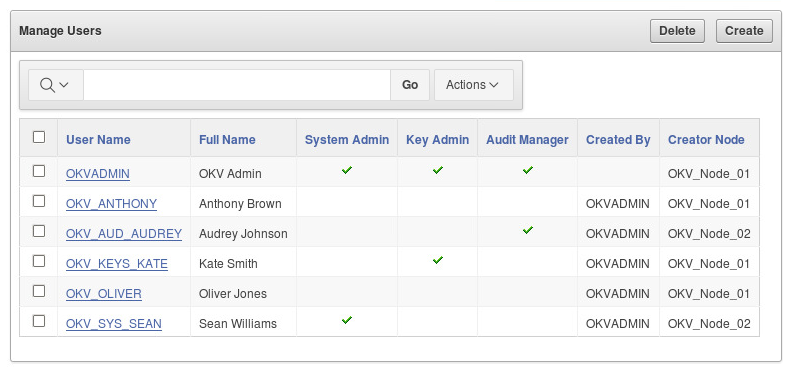
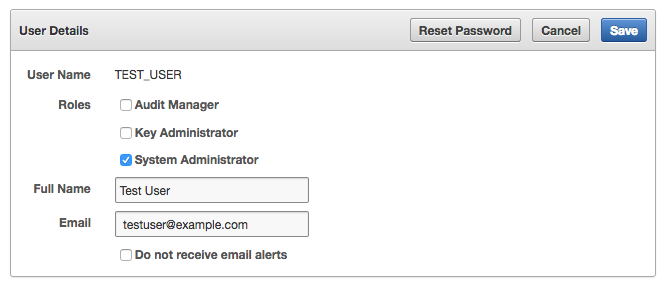
7.1.4 Viewing User Account Details
All administrative users can view the list of Oracle Key Vault user accounts and their details.
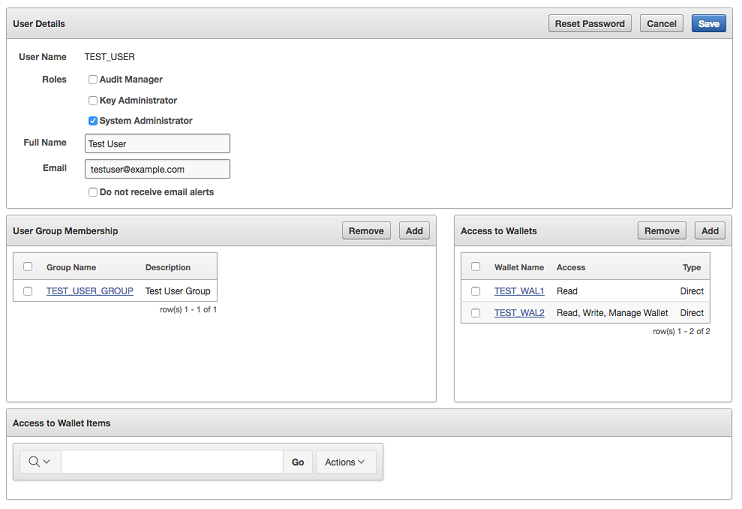
Users without any of the three administrative roles can only see their own user details. The User Details page provides a consolidated view of the Oracle Key Vault user. This is the page where all user management tasks are performed.
Parent topic: Managing User Accounts
7.1.5 Deleting an Oracle Key Vault User Account
Deleting an Oracle Key Vault user removes the user from any user groups the user was part of in Oracle Key Vault.
PENDING state.
Parent topic: Managing User Accounts
7.2 Managing Administrative Roles and Privileges
Oracle Key Vault has predefined roles that you can grant to (or change) or revoke from users.
- About Managing Administrative Roles
You can grant or change an administrative role for a user account that you have added. - Granting or Changing an Administrative Role of a User
You can use the Manage Users page to grant or change a user administrative role. - Granting a User Access to a Virtual Wallet
A user with the Key Administrator role controls access to security objects for users, endpoints, and their respective groups. - Revoking an Administrative Role from a User
You can use the Manage User page to revoke a role from a user.
Parent topic: Managing Oracle Key Vault Users
7.2.1 About Managing Administrative Roles
You can grant or change an administrative role for a user account that you have added.
You must be a user with the administrative role to grant it to other users. You can also revoke the administrative role when it is no longer needed. You cannot add, change, or delete these roles.
If you are using a multi-master cluster environment, then you can not grant, change, and revoke administrative roles for users in the PENDING state.
Parent topic: Managing Administrative Roles and Privileges
7.2.2 Granting or Changing an Administrative Role of a User
You can use the Manage Users page to grant or change a user administrative role.
Parent topic: Managing Administrative Roles and Privileges
7.2.3 Granting a User Access to a Virtual Wallet
A user with the Key Administrator role controls access to security objects for users, endpoints, and their respective groups.
Any user can be granted access to security objects in Oracle Key Vault at a level that is appropriate to their function in the organization.
You cannot grant access to a virtual wallet if the wallet is in the PENDING state.
7.2.4 Revoking an Administrative Role from a User
You can use the Manage User page to revoke a role from a user.
Parent topic: Managing Administrative Roles and Privileges
7.3 Managing User Passwords
You or the user can change the user's password. You also can have passwords reset automatically.
- About Changing User Passwords
Any valid Oracle Key Vault user can change his or her own password. - Changing Your Own Password
Any user can change his or her own Oracle Key Vault account password. - Changing Another User's Password
You can change another user's password if you have the identical administrative role (at minimum) as the user whose password you want to reset. - Controlling the Use of Password Reset Methods
You can restrict the ability of users to reset another user's password manually so that only password reset operations through email notifications are allowed.
Parent topic: Managing Oracle Key Vault Users
7.3.1 About Changing User Passwords
Any valid Oracle Key Vault user can change his or her own password.
You can reset the password of another user if you have at minimum the same administrative role as that user. For example, if you want to change the password of a user who has the Audit Manager role, then you also must have the Audit Manager role before you can change the password.
Consider the following users and roles:
| User | System Admin | Key Admin | Audit Manager |
|---|---|---|---|
|
|
Yes |
Yes |
Yes |
|
|
Yes |
Yes |
- |
|
|
Yes |
- |
- |
|
|
- |
Yes |
- |
|
|
- |
- |
Yes |
|
|
- |
- |
- |
Suppose that user OKV_SYS_KEYS_JOE, who has the System Administrator and Key Administrator roles, is logged in and wants to change the other users' passwords. The following happens:
-
OKV_KEYS_KATE:OKV_SYS_KEYS_JOEcan change the password forOKV_KEYS_KATEbecause they have the Key Administrator role in common. -
OKV_AUD_AUDREY:OKV_SYS_KEYS_JOEcannot changeOKV_AUD_AUDREY's password becauseOKV_SYS_KEYS_JOEdoes not have the Audit Manager role. -
OKV_ALL_JANE:OKV_SYS_KEYS_JOEcannot change the password for userOKV_ALL_JANEbecause he does not have the Audit Manager role. -
OKV_OLIVER:OKV_SYS_KEYS_JOEcan change the password for userOKV_OLIVER, who has no roles at all.
Any user can change his or her own password.
Assuming you have privileges to do so, you can change the password of another user by using either of the following methods:
- Specify a new password for the other user and then notify this user of the new password by using any out-of-band method.
- Send the user a randomly generated one-time password to their email account.
Related Topics
Parent topic: Managing User Passwords
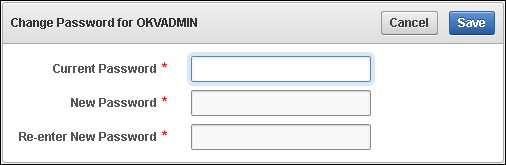
7.3.2 Changing Your Own Password
Any user can change his or her own Oracle Key Vault account password.
Parent topic: Managing User Passwords
7.3.3 Changing Another User's Password
You can change another user's password if you have the identical administrative role (at minimum) as the user whose password you want to reset.
- Changing a Password Manually
You can change the password manually for a user and then use any out-of-band method to notify the user of the new password. - Changing a Password Through Email Notification
You can change a user's password by sending them a randomly generated one-time password to their email account. - Changing Operating System User Account Passwords
Before you perform the post-installation configuration task after the Oracle Key Vault installation, you can change the passwords for therootandsupportaccounts in the server terminal console.
Related Topics
Parent topic: Managing User Passwords
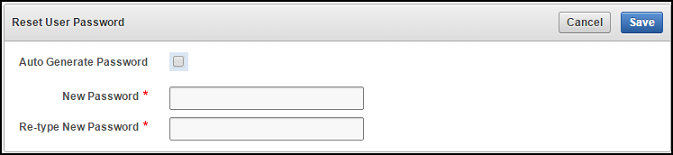
7.3.3.1 Changing a Password Manually
You can change the password manually for a user and then use any out-of-band method to notify the user of the new password.
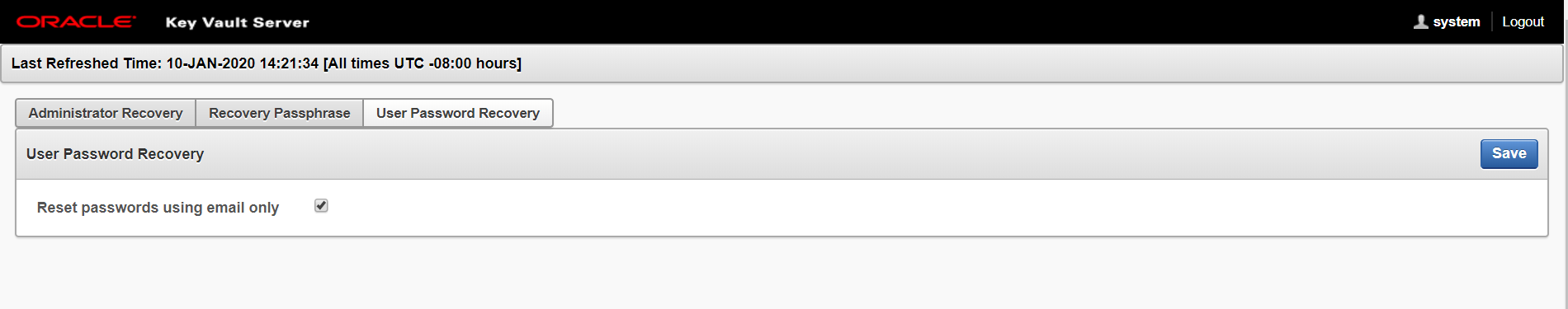
Reset passwords using email only option in the User Password Recovery tab of the System Recovery page is not checked.
Related Topics
Parent topic: Changing Another User's Password
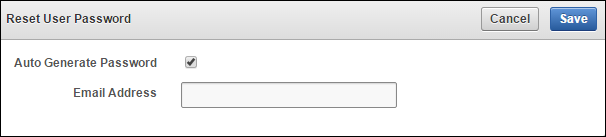
7.3.3.2 Changing a Password Through Email Notification
You can change a user's password by sending them a randomly generated one-time password to their email account.
Reset passwords using email only option in the User Password Recovery tab of the System Recovery page.
If you check Auto Generate Password without configuring SMTP, a link to Email Settings appears. Click the link to configure email settings and repeat the steps in this topic.
Parent topic: Changing Another User's Password
7.3.3.3 Changing Operating System User Account Passwords
Before you perform the post-installation configuration task after the Oracle Key Vault installation, you can change the passwords for the root and support accounts in the server terminal console.
root and support passwords. (When you install Oracle Key Vault, you create these accounts as part of the process.) The root and support users will be prompted to change their password when the next time they log in is past the expiration time of their passwords. The expiration times are 365 days with a warning at 120 days, and with STIG it is 60 days with a warning at 60 days.
Parent topic: Changing Another User's Password
7.3.4 Controlling the Use of Password Reset Methods
You can restrict the ability of users to reset another user's password manually so that only password reset operations through email notifications are allowed.
- About Controlling the Use of Password Reset Methods
You can configure Oracle Key Vault to only allow users to change another user's password by sending them a randomly generated one-time password through email. - Configuring the Use of Password Reset Operations
A user who has access to the system recovery passphrase can configure the use of password reset operations
Related Topics
Parent topic: Managing User Passwords
7.3.4.1 About Controlling the Use of Password Reset Methods
You can configure Oracle Key Vault to only allow users to change another user's password by sending them a randomly generated one-time password through email.
The user performing a password change for another user must be either an Oracle Key Vault administrator or have the same or higher privileges as the user whose password needs to be reset.
By default, there are two ways to change another user's password:
- Manually, in which you create a new password for the user. In this scenario, both you and the user will know the password (until this user manually changes his or her own password)
- Automatically, in which you trigger an automatically-generated password for the user, who is then emailed the new password on a one-time basis. In this scenario, only the user knows his or her new password.
You can enable only automatic password generation through email notification and disable manual password reset operations. The email notification uses the email ID that is associated with the user's account. The benefit of this feature is that the newly generated password is known only to the user whose password needed to be reset, not to the user who initiated the user's password change. Users can still change their own passwords when this feature is enabled.
When this feature is disabled, then both methods of user creation are allowed: manual password reset operations, and automatic password reset operations.
Parent topic: Controlling the Use of Password Reset Methods
7.3.4.2 Configuring the Use of Password Reset Operations
A user who has access to the system recovery passphrase can configure the use of password reset operations
Related Topics
Parent topic: Controlling the Use of Password Reset Methods
7.4 Managing User Email
Oracle Key Vault users should have their current email on file so that they can receive alerts such as system changes.
- Changing the User Email Address
After creating a user account, you can add or change the user's email address. - Disabling Email Notifications for a User
You can disable email notifications for a user on the User Details page.
Parent topic: Managing Oracle Key Vault Users
7.4.1 Changing the User Email Address
After creating a user account, you can add or change the user's email address.
Parent topic: Managing User Email
7.4.2 Disabling Email Notifications for a User
You can disable email notifications for a user on the User Details page.
Parent topic: Managing User Email
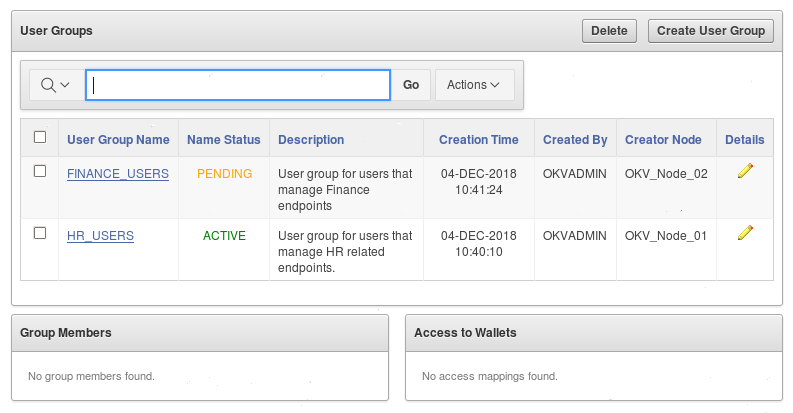
7.5 Managing User Groups
You can organize users who have a common purpose into a named user group.
- About Managing User Groups
Users who have the Key Administrator role can create, modify, and delete user groups. - How a Multi-Master Cluster Affects User Groups
User groups are used at the Oracle Key Vault server and cluster level to group user roles and permissions. - Creating a User Group
You can create a user group when a set of users must manage a set of common security objects. - Adding a User to a User Group
You can add an existing user to a user group if that user must manage the same security objects as the group. - Granting a User Group Access to a Virtual Wallet
You can modify the access level to a virtual wallet for a user group as functional needs change. - Renaming a User Group
Depending on its status, you can change the name of a user group. - Changing a User Group Description
A group description is useful for identifying the purpose of the group. - Removing a User from a User Group
Depending on the circumstances, you can remove a user from a user group. - Deleting a User Group
You can delete a user group when the users in the group do not need to access the same security objects.
Parent topic: Managing Oracle Key Vault Users
7.5.1 About Managing User Groups
Users who have the Key Administrator role can create, modify, and delete user groups.
This enables them to manage their access to virtual wallets. After a user group is created, you can modify its details.
The main purpose of a user group is simplify access control to security objects. If a set of users need access to a common set of security objects, then you can assign these users to a group and grant the group access instead of granting access to each user or based on each security object. When certain users do not need access to the security objects any longer, you can remove them from the group. You can add new users to the group. You can modify the group's access level to security objects at any time.
Parent topic: Managing User Groups
7.5.2 How a Multi-Master Cluster Affects User Groups
User groups are used at the Oracle Key Vault server and cluster level to group user roles and permissions.
When new servers are inducted into the cluster, Oracle Key Vault replaces any user group information that is in the cluster. You can create new user groups in the cluster from a read-write pair.
User groups created in a node after the node is added to an Oracle Key Vault cluster will have a cluster-wide presence. User groups created on two different nodes could have name conflicts. Oracle Key Vault automatically resolves the user group name conflicts. These conflicts will be displayed in the Conflicts Resolution page and administrators can choose to rename them.
Note the following:
- You cannot change membership by adding or removing users when the user group is in a
PENDINGstate. Similarly, users in a pending state cannot be added to, or removed from a user group in theACTIVEstate. - You cannot change access mapping for users and user groups if a wallet is in the
PENDINGstate. Similarly, users and user groups in a pending state cannot be added to, or removed from a wallet access mapping even when the wallet is in theACTIVEstate.
Related Topics
Parent topic: Managing User Groups
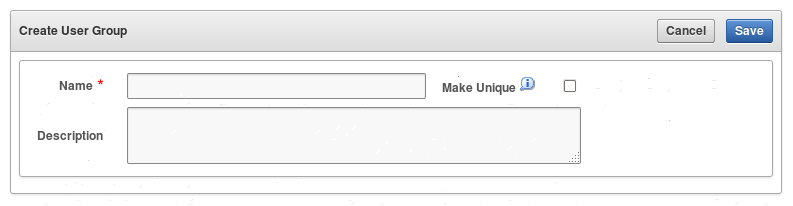
7.5.3 Creating a User Group
You can create a user group when a set of users must manage a set of common security objects.
You can add users to the group when you create the group or later after creating the group.
Related Topics
Parent topic: Managing User Groups
7.5.4 Adding a User to a User Group
You can add an existing user to a user group if that user must manage the same security objects as the group.
ACTIVE state, then you can add users to a group when you create the group or later after creating the groups.
Parent topic: Managing User Groups
7.5.5 Granting a User Group Access to a Virtual Wallet
You can modify the access level to a virtual wallet for a user group as functional needs change.
ACTIVE state.
Related Topics
Parent topic: Managing User Groups
7.5.6 Renaming a User Group
Depending on its status, you can change the name of a user group.
PENDING state, then only the creator user can rename the user group.
Parent topic: Managing User Groups
7.5.7 Changing a User Group Description
A group description is useful for identifying the purpose of the group.
PENDING state, then only the creator can modify the user group description.
Parent topic: Managing User Groups
7.5.8 Removing a User from a User Group
Depending on the circumstances, you can remove a user from a user group.
ACTIVE state, then you can remove users from a user group. You may want to remove these users when their function in the organization changes, and they no longer need to manage the same security objects as the group.
Parent topic: Managing User Groups
7.5.9 Deleting a User Group
You can delete a user group when the users in the group do not need to access the same security objects.
PENDING state, then only the creator can delete it.
Parent topic: Managing User Groups