6 Managing an Oracle Key Vault Primary-Standby Configuration
You can deploy Oracle Key Vault in a primary-standby server configuration.
- Overview of the Oracle Key Vault Primary-Standby Configuration
The Oracle Key Vault primary-standby configuration provides benefits based on the type of deployment your site needs. - Configuring the Primary-Standby Environment
To configure a primary-standby environment, you must have the System Administrator role and have access to the two servers (one primary and one standby). - Switching the Primary and Standby Servers
You can switch the roles of the primary and standby server for situations such as maintenance periods. - Restoring Primary-Standby After a Failover
A failover takes place if the primary server fails. - Disabling (Unpairing) the Primary-Standby Configuration
You can disable the primary-standby configuration by unpairing the primary and standby servers. - Read-Only Restricted Mode in a Primary-Standby Configuration
The read-only restricted mode is the default mode in a primary-standby configuration. - Best Practices for Using Oracle Key Vault in a Primary-Standby Configuration
Oracle provides guidelines for ensuring operational continuity and minimal downtime of Oracle Key Vault.
6.1 Overview of the Oracle Key Vault Primary-Standby Configuration
The Oracle Key Vault primary-standby configuration provides benefits based on the type of deployment your site needs.
- About the Oracle Key Vault Primary-Standby Configuration
You configure a primary-standby environment by providing the primary and standby servers with each other's IP address and certificate, and then pairing them. - Benefits of an Oracle Key Vault Primary-Standby Configuration
The benefits of an Oracle Key Vault primary-standby configuration include high availability, necessary for business-critical operations. - Difference Between Primary-Standby Configuration and Multi-Master Cluster
One server will always operate in read-write mode. - Primary Server Role in a Primary-Standby Configuration
A primary-standby deployment consists of two Oracle Key Vault servers operating in a primary-standby configuration. - Standby Server Role in a Primary-Standby Configuration
In a primary-standby environment, one server runs in the standby server role.
6.1.1 About the Oracle Key Vault Primary-Standby Configuration
You configure a primary-standby environment by providing the primary and standby servers with each other's IP address and certificate, and then pairing them.
While pairing the primary and standby servers, you can select one as the primary server, and the other as the standby. A failover timeout that you set determines when the standby starts to take over as the primary server.
Note:
Oracle strongly recommends that you keep the primary and standby systems as identical as possible, because their roles can be reversed in maintenance periods and failure situations. These include the following:
-
Oracle Key Vault software versions
-
Disk size
-
RAM size
-
System clocks on both systems must be synchronized
WARNING:
Configure primary-standby deployments before adding endpoints to ensure that the endpoints know about both nodes.If you want to add SNMP support in a primary-standby environment, then ideally, configure SNMP on both the primary and the standby servers before pairing them. This is because the standby server is no longer accessible from the Oracle Key Vault management console, because all requests are forwarded to the primary server. However you can also add SNMP support to the standby after pairing the servers by accessing the standby using SSH.
If you want to use a third-party certificate in a primary-standby configuration, then you must install it on the primary and standby servers first, and then pair them.
If you want to enable FIPS mode in a primary-standby environment, then you must ensure that both the primary and standby servers use the same FIPS mode: either both are enabled, or both are disabled for FIPS mode. This is because the standby server is no longer accessible from the Oracle Key Vault management console, because all requests are forwarded to the primary server.
With persistent cache enabled, both the primary and the standby will cache the master encryption keys from Oracle Key Vault independently. Ensure that TDE operations have executed on the primary and standby servers after these servers have started to verify the persistent cache. The persistent cache feature also enables endpoints to be operational during primary-standby operations, such as configuration, switchovers, and failovers.
If enabled, read-only restricted mode ensures endpoint operational continuity (such as enabling the endpoints to fetch keys) if either the standby or primary server is not available. For example, if the standby shuts down, then the primary will go into read-only restricted mode and enable the endpoints to fetch keys and continue operations.
A primary-standby configuration is characterized by continuous synchronization between the primary server and the standby server. When synchronization is lost between the primary and standby servers, it is possible to encounter a split-brain scenario where two primary servers might be active simultaneously. In such a scenario, both servers record new data that diverges from the last synchronized state. When connectivity is restored between the primary and standby servers, it may not be possible to reconcile the changes on the two servers and data loss may occur.
You can enable or disable restricted mode when configuring the primary-standby environment by selecting the Allow Read-Only Restricted Mode option to Yes or No on the Configure Primary-Standby page.
When read-only restricted mode is enabled, the primary server enters read-only restricted mode if the standby server is unavailable. In read-only restricted mode, the primary server allows keys to be retrieved, but does not allow keys to be modified or new keys to be added. This ensures that endpoints still have access to their keys, and key data or metadata is not lost due to a split-brain scenario. However, the primary server still writes audit records, which may be lost if a split-brain scenario occurs with the standby server.
When read-only restricted mode is disabled, the primary server becomes unavailable and stops accepting new requests if the standby server is unavailable. Endpoints connected to Oracle Key Vault will be unable to retrieve keys from the server until connectivity is restored between primary and standby servers. You can use the persistent master encryption key cache feature to avoid endpoint downtime. With this feature, data integrity is ensured by allowing endpoints to communicate with one primary server at any given time. This avoids split-brain situations, and the risk of data loss associated with such situations.
Related Topics
6.1.2 Benefits of an Oracle Key Vault Primary-Standby Configuration
The benefits of an Oracle Key Vault primary-standby configuration include high availability, necessary for business-critical operations.
Users performing business-critical operations must have data to be accessible and recoverable with minimum downtime. These requirements are met in a primary-standby configuration.
You achieve high availability by adding redundancy in the form of a standby server that can take over the functions of the primary server in case of failure. The standby server helps you eliminate single points of failure and reduce server downtime. This is a significant reason to deploy Oracle Key Vault in a primary-standby configuration. In a classic primary-standby configuration, the emphasis is on key preservation. In a multi-master cluster, emphasis is on both key preservation and availability of the keys.
You can create a cluster of Oracle Key Vault server nodes for greater availability and redundancy. A primary-standby configuration is limited to two servers, whereas a multi-master cluster can have up to 16 geographically distributed nodes. The primary-standby configuration and the multi-master configuration are mutually exclusive.
Related Topics
6.1.3 Difference Between Primary-Standby Configuration and Multi-Master Cluster
One server will always operate in read-write mode.
In a primary-standby configuration, when both servers are available, one of the servers operates in read-write mode in the primary server role, and the other operates in the standby server role. The endpoints only connect to the server running in the primary server role. The roles can be switched manually to support maintenance operations, or automatically due to server or connectivity failure. If either the primary or standby server becomes unavailable, then the remaining server operates in a read-only restricted mode, limiting normal updates while allowing audits and other internal updates.
In a multi-master cluster, the endpoints can connect to any Oracle Key Vault server. Some servers are configured as bi-directional read-write pairs in which information updated in either node must be successfully replicated to the other node immediately. If one of the nodes in a read-write pair becomes unavailable, the surviving node operates in read-only restricted mode until the other node is restored and synchronization resumes. A fully functional multi-master cluster must have at least one read-write pair.
When a successful update occurs in a read-write pair, the update is propagated to all other nodes in the cluster.
A primary-standby configuration and a multi-master cluster configuration are mutually exclusive and incompatible configurations. The specific configuration of an Oracle Key Vault deployment has no ramification on the endpoint side configuration.
6.1.4 Primary Server Role in a Primary-Standby Configuration
A primary-standby deployment consists of two Oracle Key Vault servers operating in a primary-standby configuration.
By default, endpoints only connect to the primary server until is becomes unavailable. At any time, only one server operates in the primary server role and that server actively accepts client connections. The other server operates in the standby server role, which receives updates from the primary server. On failure of the server running in the primary server role, the standby assumes the primary role. There may be restrictions in operations if the primary-standby pair is not fully available and operational.
6.1.5 Standby Server Role in a Primary-Standby Configuration
In a primary-standby environment, one server runs in the standby server role.
This standby server does not accept client connections while in that role. The server receives updates only from the paired server running in primary server role. If the primary server is no longer available, including being available to the administrator, then the server running in the standby role switches to assume the primary server role. There may be restrictions in operations if the primary-standby pair is not fully available and operational.
6.2 Configuring the Primary-Standby Environment
To configure a primary-standby environment, you must have the System Administrator role and have access to the two servers (one primary and one standby).
- Step 1: Configure the Primary Server
To configure the primary server, you must enable it to connect to the standby server. - Step 2: Configure the Standby Server
To configure the standby server, you must enable it to connect to the primary server. - Step 3: Complete the Configuration on the Primary Server
After you configure the primary and standby servers, you can enable the primary-standby on the designated primary server.
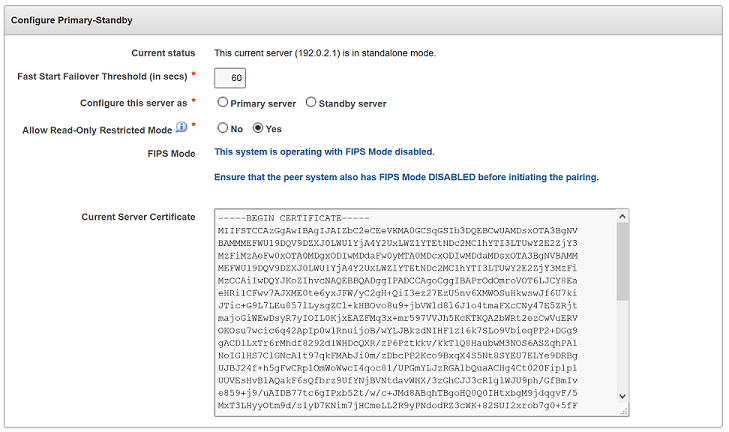
6.2.1 Step 1: Configure the Primary Server
To configure the primary server, you must enable it to connect to the standby server.
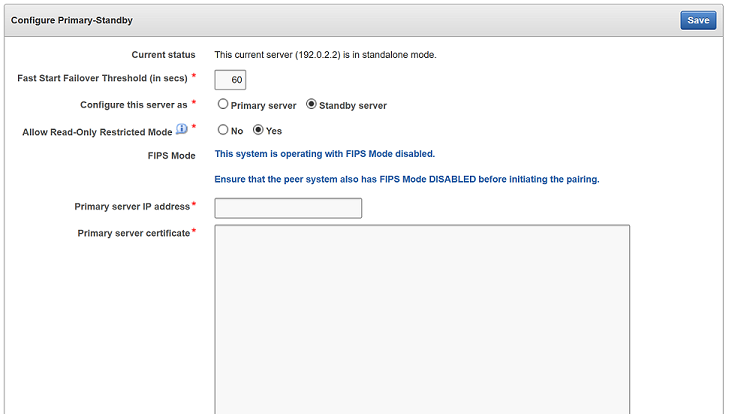
6.2.2 Step 2: Configure the Standby Server
To configure the standby server, you must enable it to connect to the primary server.
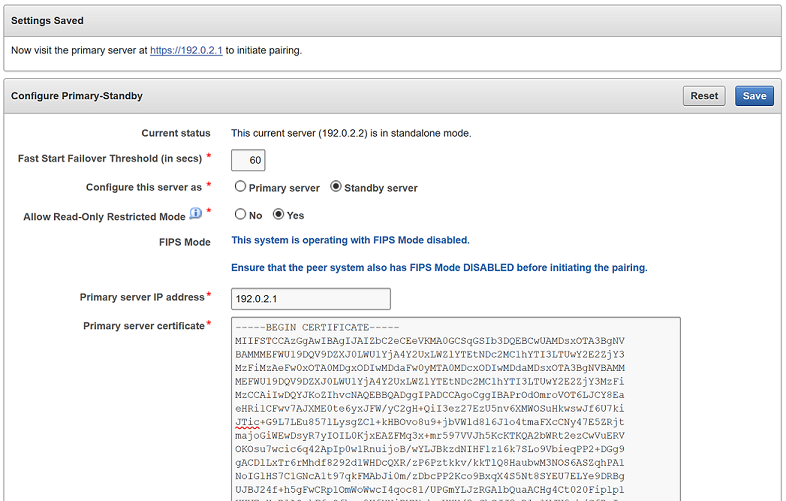
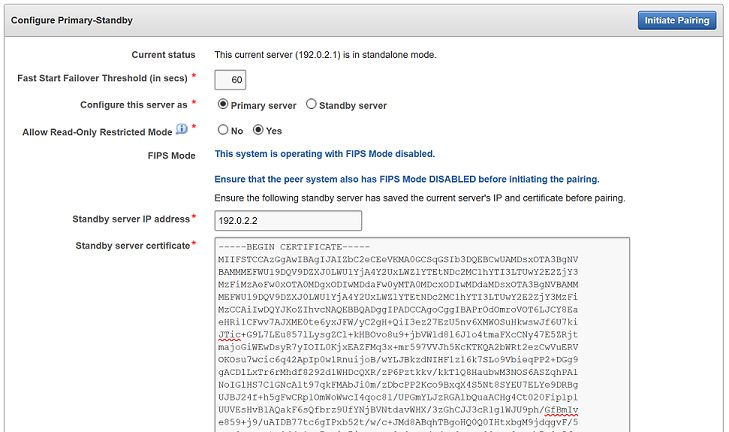
6.2.3 Step 3: Complete the Configuration on the Primary Server
After you configure the primary and standby servers, you can enable the primary-standby on the designated primary server.
-
When the primary-standby configuration is complete, you cannot log in to the standby server using a web browser because all configuration is propagated from the primary.
-
To manage the primary-standby deployment, log in to the primary server using a web browser.
Caution:
Ensure that you leave read-only restricted mode enabled while configuring primary-standby. Enabling it later requires a reinstall of the Oracle Key Vault server software on the standby server.
After configuring the primary-standby environment, do not change the system time on the primary server. The changed system time causes the standby server to go down, thus disrupting the functioning of the primary-standby configuration.
Parent topic: Configuring the Primary-Standby Environment
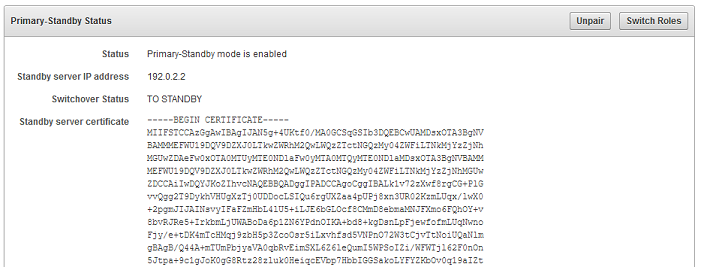
6.3 Switching the Primary and Standby Servers
You can switch the roles of the primary and standby server for situations such as maintenance periods.
6.4 Restoring Primary-Standby After a Failover
A failover takes place if the primary server fails.
Note:
When read-only restricted mode is disabled, the primary server's failover status goes into suspended state causing the standby server to wait indefinitely for the primary server to come back up. This is expected behavior to avoid a split-brain scenario where two primary servers are simultaneously active.
When read-only restricted mode is enabled, a primary or standby server failure causes the operational peer to enter read-only restricted mode, thus ensuring endpoint operational continuity.
Related Topics
6.5 Disabling (Unpairing) the Primary-Standby Configuration
You can disable the primary-standby configuration by unpairing the primary and standby servers.
/var/lib/oracle/diag/rdbms/dbfwdb/dbfwdb/metadata_pv directory beforehand. Check the Release Notes for additional issues related to unpair operations.
Related Topics
6.6 Read-Only Restricted Mode in a Primary-Standby Configuration
The read-only restricted mode is the default mode in a primary-standby configuration.
- About Read-Only Restricted Mode in a Primary-Standby Configuration
Primary-standby read-only restricted mode ensures endpoint operational continuity. - Primary-Standby with Read-Only Restricted Mode
Read-only restricted mode is the default primary-standby mode in Oracle Key Vault. - Primary-Standby without Read-Only Restricted Mode
When a primary-standby environment is configured without read-only restricted mode, the impact on endpoint operations differs. - States of Read-Only Restricted Mode
A server using read-only restricted mode is affected by the failure in a primary server, a standby server, and the network. - Enabling Read-Only Restricted Mode
Read-only restricted mode is enabled by default when primary-standby is configured. - Disabling Read-Only Restricted Mode
Read-only restricted mode is enabled by default when primary-standby is configured. - Recovering from Read-Only Restricted Mode
To recover an instance from read-only restricted mode after a network failure or standby server failure, manual intervention may be required. - Read-Only Restricted Mode Notifications
When the primary or standby server enters read-only restricted mode, an alert is generated.
6.6.1 About Read-Only Restricted Mode in a Primary-Standby Configuration
Primary-standby read-only restricted mode ensures endpoint operational continuity.
This endpoint operational continuity is essential when the primary or standby Oracle Key Vault servers are affected by server, hardware, or network failures.
When an unplanned shutdown makes the primary or standby server offline, the endpoints can still connect to the surviving peer server to perform critical operations. Primary-standby read-only restricted mode ensures that operations that replicate data are blocked. Operations that replicate data are allowed when both primary and standby servers are back online, thus ensuring that no critical data is lost.
In a primary-standby Oracle Key Vault configuration, the single point of failure is eliminated when you replicate the primary server’s data to the standby server. Read-only restricted mode enables the generation of non-critical data such as audit records. However, generation of critical data such as keys is disabled. When the primary server is down, operations that generate new critical data on the standby are disabled. The reverse is also true. When the standby server is down, operations that attempt to modify or create any data on the primary server are disabled.
In a primary-standby deployment without read-only restricted mode, most endpoint operations are blocked because endpoint operations generate audit records, which is data that needs replication, thus disrupting operational continuity.
The following are the benefits of using read-only restricted mode:
-
Enables endpoint operational continuity when the primary or standby server is offline
-
Ensures symmetrical behavior when the primary or standby server is offline
The following sections describe the behavior of:
6.6.2 Primary-Standby with Read-Only Restricted Mode
Read-only restricted mode is the default primary-standby mode in Oracle Key Vault.
Note:
You can disable read-only restricted mode during the primary-standby configuration. Oracle recommends that you configure primary-standby with read-only restricted mode enabled, which is the default mode. While configuring primary-standby, ensure that Yes is selected in the Allow Read-Only Restricted Mode field on the Configure Primary-Standby page.Read-only restricted mode ensures endpoint operational continuity as well as symmetrical behavior when the primary or standby server is offline. Symmetrical behavior ensures that the online server seamlessly takes over from its failed peer, and continues to service the endpoints without any disruption. For more information about primary-standby failover situations with read-only restricted mode, see Failover Situations with Read-Only Restricted Mode.
In read-only restricted mode, the surviving Oracle Key Vault server operates with limited functionality. Endpoint operations that add or modify critical data on the Oracle Key Vault server are blocked. However, endpoint operations that involve fetching of data are allowed. This ensures endpoint operational continuity and data integrity. For more information about blocked and allowed operations, see About the States of Read-Only Restricted Mode.
For more information about read-only restricted mode, see States of Read-Only Restricted Mode.
Note:
Read-only restricted mode has no impact on a standalone server.6.6.3 Primary-Standby without Read-Only Restricted Mode
When a primary-standby environment is configured without read-only restricted mode, the impact on endpoint operations differs.
This impact depends on the type of failure encountered: primary failure, standby failure, or a network failure that prevents communication between the primary and standby servers. The following are the possible scenarios:
-
Primary server failure: The standby server will failover and take over from the affected primary server. This allows the Oracle Key Vault service to remain operational. Data modifications are stored on the primary server until they can be replicated to the standby server. This ensures endpoint operational continuity when the primary server goes offline due to an unplanned shutdown.
-
Standby server failure: The primary server is unavailable to the endpoints, because it is not possible to distinguish a standby server failure from a network failure that prevents communication between the primary and standby servers.
-
Power loss or network connectivity failure: The primary and standby servers are unable to communicate. The standby server will failover and take over from the primary server. To avoid a split-brain scenario, only one of the servers is allowed to service the endpoints.
Note:
A split-brain scenario in Oracle Key Vault occurs when the primary server fails, causing the standby server to failover and take over from the primary server. This causes a situation where the primary and standby servers are available to service the endpoints, and create new data. A split-brain scenario causes data on the primary and standby servers to go out of sync. This can lead to data loss and corruption, as well as loss of operational continuity. To avoid a split-brain scenario, only one of the servers is allowed to service the endpoints after a failover occurs.In primary-standby without read-only restricted mode, one of the following situations is triggered when a failure occurs:
-
Endpoints suffer a temporary operational disruption to avoid a split-brain scenario.
-
The standby server accepts new requests and generates new data without attempting to synchronize the data with the failed primary server. Replication of data is temporarily disabled until the primary server is online, thus ensuring operational continuity.
6.6.4 States of Read-Only Restricted Mode
A server using read-only restricted mode is affected by the failure in a primary server, a standby server, and the network.
- About the States of Read-Only Restricted Mode
Read-only restricted mode puts the Oracle Key Vault instance into the read-only restricted mode state. - Read-Only Restricted State Functionality During a Primary Server Failure
You can set a failover threshold value to determine when a standby server takes over for a failed primary server. - Read-Only Restricted Mode Functionality During a Standby Server Failure
If a standby fails, the primary server waits for the duration in the Fast Start Failover Threshold field on the Configure Primary-Standby page. - Read-Only Restricted State Functionality During a Network Failure
When a network failure affects communication between primary and standby servers, communication between certain endpoints and the primary server may also be affected.
6.6.4.1 About the States of Read-Only Restricted Mode
Read-only restricted mode puts the Oracle Key Vault instance into the read-only restricted mode state.
However, read-only restricted mode does not put the embedded Oracle Key Vault database into the read-only restricted mode state. In read-only restricted mode, the following behavior occurs when a primary or a standby server is unavailable:
-
When the primary server is down, data cannot be replicated and so the standby server will failover and disable all operations that generate new data. However, the standby can fetch existing data.
-
When the standby server is down, data cannot be replicated and so the primary server disables all operations that generate new data. However, the primary can fetch existing data.
Read-only restricted mode introduces the following deviations from normal functionality:
-
All operations that generate new data are blocked. Operations that fetch existing data are allowed. Audit records for endpoint operations are generated as in normal operation. Internal system operations of the Oracle Key Vault database are not impacted. Functionality such as alerts continue to work normally.
-
Endpoints are allowed to fetch keys from the Oracle Key Vault server. Endpoints cannot create new keys or modify existing keys.
-
Administrators can log in to the Oracle Key Vault management console. Creation of an endpoint or a wallet, deletion of keys, and operations that modify or delete data are blocked.
-
Unpairing of primary and standby Oracle Key Vault servers running in read-only restricted mode are allowed.
-
Backup operations are blocked to avoid data mismatches between backups.
Table 6-1 Allowed and Blocked Operations in Read-Only Restricted Mode
| Operation | Allowed or Blocked |
|---|---|
| Log in to Oracle Key Vault | Allowed |
| Endpoint operations such as fetching keys from the cache | Allowed |
| Endpoint operations that add, modify, or delete data such as rotation of keys on the database | Blocked |
| System operations such as enabling SSH access | Allowed |
| System operations that write data such as setting up a REST server and creating virtual wallets | Blocked |
| Oracle Key Vault management console access | Allowed |
| All Administrator and endpoint operations that add new data or modify existing data | Blocked |
| Backup operations | Blocked |
In read-only restricted mode, if you attempt to execute operations that generate new data or modify existing data on the Oracle Key Vault server, the Key Vault Server in read-only restricted Mode error is displayed.
If you attempt to upload a wallet to the Java keystore, then you are prompted for the source Java keystore password. After entering the password, the Key Vault Server in read-only restricted Mode error is displayed.
Parent topic: States of Read-Only Restricted Mode
6.6.4.2 Read-Only Restricted State Functionality During a Primary Server Failure
You can set a failover threshold value to determine when a standby server takes over for a failed primary server.
In the event of a primary server failure, the standby server waits for the duration specified in the Fast Start Failover Threshold (in secs) field on the Configure Primary-Standby page. If the primary server is not reachable after the specified duration has elapsed, the standby server enters read-only restricted mode. In read-only restricted mode, only operations that fetch data are allowed. Endpoint operations that add new data or modify existing data on the Oracle Key Vault server are blocked.
Related Topics
Parent topic: States of Read-Only Restricted Mode
6.6.4.3 Read-Only Restricted Mode Functionality During a Standby Server Failure
If a standby fails, the primary server waits for the duration in the Fast Start Failover Threshold field on the Configure Primary-Standby page.
If the standby server is not reachable after the specified duration has elapsed, the primary server enters read-only restricted mode. In read-only restricted mode, only operations that fetch data are allowed. Endpoint operations that add new data or modify existing data on the Oracle Key Vault server are blocked.
The primary server continues to provide limited service to the endpoints.
Related Topics
Parent topic: States of Read-Only Restricted Mode
6.6.4.4 Read-Only Restricted State Functionality During a Network Failure
When a network failure affects communication between primary and standby servers, communication between certain endpoints and the primary server may also be affected.
The primary server waits for the duration specified in the Fast Start Failover Threshold field on the Configure Primary-Standby page. If the standby server is not reachable after the specified duration has elapsed, the primary server enters read-only restricted mode.
The standby server will also wait for the same duration. If the primary server is not reachable after the specified duration has elapsed, the standby server enters read-only restricted mode. The standby server takes over as the new primary server, and provides service to endpoints that cannot communicate with the affected primary server.
Related Topics
Parent topic: States of Read-Only Restricted Mode
6.6.5 Enabling Read-Only Restricted Mode
Read-only restricted mode is enabled by default when primary-standby is configured.
6.6.6 Disabling Read-Only Restricted Mode
Read-only restricted mode is enabled by default when primary-standby is configured.
6.6.7 Recovering from Read-Only Restricted Mode
To recover an instance from read-only restricted mode after a network failure or standby server failure, manual intervention may be required.
You will need to unpair and reset the surviving instance, reinstate a new Oracle Key Vault server, and pair it as the new standby to the surviving server. The following are the possible scenarios:
-
Primary server failure: Depending on the operational state of the primary server at the time of failure, it could be restarted and some functionality may be available. However, due to possible corruption of the embedded Oracle Key Vault database, recovery may not be possible. You would then need to reinstate the Oracle Key Vault instance because of the partial failure. If the failed server is unable to again pair with the peer server within 20 minutes, then you must reinstantiate the server.
Even though the endpoint processes communicating with the Oracle Key Vault servers retain the IP address of the last known reachable server, they must determine the IP address of the new Oracle Key Vault server when spawned. The endpoint processes attempt to communicate with the Oracle Key Vault server configured as the primary server in the configuration scripts, and then wait for a response before trying to reach the server configured as the standby server in the configuration scripts. To minimize downtime, Oracle recommends that you initiate a switchover after reinstating the failed primary server.
-
Standby server failure: The primary server will run in the read-only restricted mode if there is a standby server failure. Reinstate the standby server if it does not automatically pair with the primary server.
-
Power loss or network connectivity failure: When a network failure occurs, the primary and standby servers are unable to communicate, and both servers enter read-only restricted mode. The standby also attempts to failover to the primary server. Once communication is re-established between the primary and standby servers, the old primary server is automatically converted to the new standby. The data from the new primary server overwrites the old primary server’s data, resulting in the loss of audit records from the old primary server. It is recommended that you enable syslog auditing to preserve the audit records that were overwritten on the old primary. Similar to recovering from primary server failure, Oracle recommends that you perform a switchover after recovery. You should also not enroll any new endpoints before the switchover.
Related Topics
6.7 Best Practices for Using Oracle Key Vault in a Primary-Standby Configuration
Oracle provides guidelines for ensuring operational continuity and minimal downtime of Oracle Key Vault.
-
Configure your Transparent Data Encryption (TDE)-enabled databases to have an auto-login connection into Oracle Key Vault. Oracle Database Advanced Security Guide describes how to configure auto-login keystores.
-
Apply the database patch for Bug 22734547 to tune the Oracle Key Vault heartbeat.
-
Ensure that read-only restricted mode is enabled in primary-standby Oracle Key Vault deployments.
-
Set the duration in the Fast Start Failover Threshold field on the Configure Primary-Standby page to a value that avoids unnecessary failover due to transient network interruptions.
-
Configure syslog auditing to capture audit records in read-only restricted mode.
-
Switch over to the original primary server in case the primary server is reinstated.
- Before attempting any unpair operations, check Oracle Key Vault Release Notes for known issues.