1 Introduction to Oracle Key Vault
Oracle Key Vault is a full-stack, security-hardened software appliance built to centralize the management of keys and security objects within the enterprise.
- About Oracle Key Vault and Key Management
Oracle Key Vault is a fault-tolerant, highly available and scalable, secure and standards-compliant key and secrets management tool, where you can store, manage, and share your security objects. - Benefits of Using Oracle Key Vault
Oracle Key Vault helps you to fight security threats, centralize key storage, and centralize key lifecycle management. - Oracle Key Vault Use Cases
The most typical use cases for Oracle Key Vault are centralized storage and management of security objects. - Who Should Use Oracle Key Vault
Oracle Key Vault is designed for users who are responsible for deploying, maintaining, and managing security within the enterprise. - Major Features of Oracle Key Vault
Oracle Key Vault enhances security in key management with a wide range of features that support different database deployments. - Oracle Key Vault Interfaces
Oracle Key Vault provides both a graphical user interface and command-line interfaces. - Overview of an Oracle Key Vault Deployment
There are three different Oracle Key Vault deployment options.
1.1 About Oracle Key Vault and Key Management
Oracle Key Vault is a fault-tolerant, highly available and scalable, secure and standards-compliant key and secrets management tool, where you can store, manage, and share your security objects.
A security object contains critical data that is provided by a user. Security objects that you can manage with Oracle Key Vault include encryption keys, Oracle wallets, Java keystores (JKS), Java Cryptography Extension keystores (JCEKS), and credential files. Credential files can include SSH private keys (used for public key authentication to remote servers (for example OCI compute instances)) or database account passwords for unattended execution of regularly scheduled maintenance scripts.
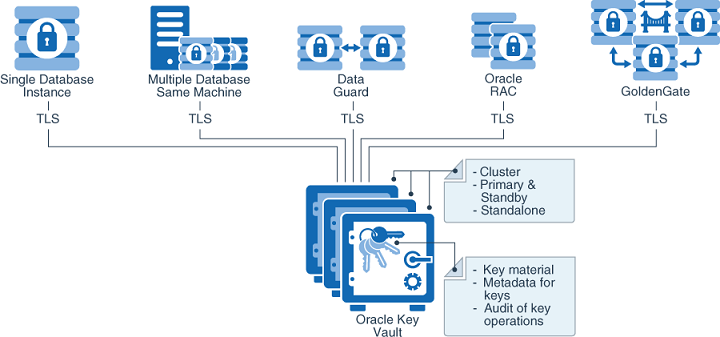
To increase key and secret availability, you can install Oracle Key Vault as a multi-master cluster with up to 16 (geographically distributed) nodes.
Oracle Key Vault centralizes encryption key storage across your organization quickly and efficiently. Built on Oracle Linux, Oracle Database, Oracle Database security features like Oracle Transparent Data Encryption, Oracle Database Vault, Oracle Virtual Private Database, and Oracle GoldenGate technology, Oracle Key Vault's centralized, highly available, and scalable security solution helps to overcome the biggest key-management challenges facing organizations today. With Oracle Key Vault you can retain, back up, and restore your security objects, prevent their accidental loss, and manage their lifecycle in a protected environment.
Oracle Key Vault is optimized for the Oracle Stack (database, middleware, systems), and Advanced Security Transparent Data Encryption (TDE). In addition, it complies with the industry standard OASIS Key Management Interoperability Protocol (KMIP) for compatibility with KMIP-based clients.
Oracle Key Vault works with endpoints, which it treats as clients to store and manage security objects, share them with trusted peers, and retrieve them. An endpoint is a computer system such as a database server, an application server, and other information systems, where keys are used to access encrypted data and credentials are used to authenticate to other systems. You can use Oracle Key Vault to manage a variety of other endpoints, such as master encryption keys for Oracle Golden Gate encrypted trail files, MySQL TDE, encrypted ACFS file systems, ZDLRA, and many more KMIP-compliant endpoints. The Java and C software development kits make it easy to integrate other endpoints as well.
Parent topic: Introduction to Oracle Key Vault
1.2 Benefits of Using Oracle Key Vault
Oracle Key Vault helps you to fight security threats, centralize key storage, and centralize key lifecycle management.
Deploying Oracle Key Vault in your organization will help you accomplish the following:
-
Manage the lifecycle for endpoint security objects and keys, which includes key creation, rotation, deactivation, and removal.
-
Prevent the loss of keys and wallets due to forgotten passwords or accidental deletion.
-
Share keys securely between authorized endpoints across the organization.
-
Enroll and provision endpoints easily using a single software package that contains all the necessary binaries, configuration files, and endpoint certificates for mutually authenticated connections (TLS 1.2) between endpoints and Oracle Key Vault.
-
Work with other Oracle products and features in addition to Transparent Data Encryption (TDE), such as Oracle Real Application Clusters (Oracle RAC), Oracle Data Guard, pluggable databases, and Oracle GoldenGate. Oracle Key Vault facilitates the movement of encrypted data using Oracle Data Pump and transportable tablespaces, a key feature of Oracle Database.
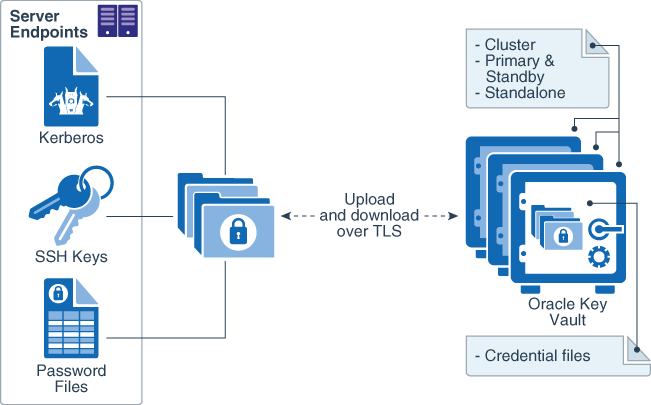
Figure 1-1 The Centralized Key-Management Platform of Oracle Key Vault
Description of "Figure 1-1 The Centralized Key-Management Platform of Oracle Key Vault "
This figure illustrates a typical deployment of Oracle Key Vault from a location central to the enterprise.
It interacts with the following components:
-
Transparent Data Encryption refers to Oracle databases protected with TDE.
-
Oracle wallets and Java keystores are containers for keys and sensitive objects that you upload and download between Oracle Key Vault and endpoints.
-
Other Keystore Files are security objects like certificates, and credential files like Kerberos keytab files, SSH key files, and server password files, that you upload to Oracle Key Vault from endpoints.
-
Oracle Key Vault Management Console refers to the Oracle Key Vault graphical user interface, where you can log in to manage your security objects and administer the Oracle Key Vault system.
-
Oracle Key Vault Backup refers to a backup device, where security objects in Oracle Key Vault can be backed up on-demand or on-schedule.
Oracle Key Vault multi-master cluster provides additional benefits, such as:
- Maximum key availability by providing multiple Oracle Key Vault nodes from which data may be retrieved
- Zero endpoint downtime during Oracle Key Vault multi-master cluster maintenance
Parent topic: Introduction to Oracle Key Vault
1.3 Oracle Key Vault Use Cases
The most typical use cases for Oracle Key Vault are centralized storage and management of security objects.
- Centralized Storage of Oracle Wallet Files and Java Keystores
You can store security objects centrally in Oracle Key Vault, and manage them with automatic mechanisms for tracking, backup, and recovery. - Centralized Management of TDE Master Encryption Keys Using Online Master Keys
You can use an online master key to centralize the management of TDE master encryption keys over a direct network connection. - Storage of Credential Files
Oracle Key Vault can back up credential files other than Oracle wallets and Java keystores for long-term retention and recovery. - Online Management of Endpoint Keys and Secret Data
You can use the RESTful key management interface to manage the storage and retrieval of keys.
Parent topic: Introduction to Oracle Key Vault
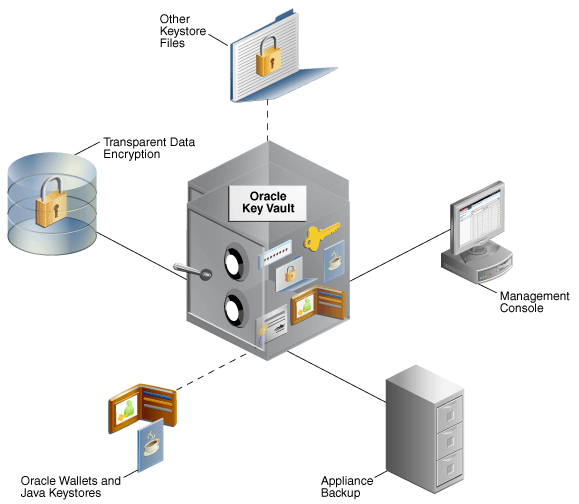
1.3.1 Centralized Storage of Oracle Wallet Files and Java Keystores
You can store security objects centrally in Oracle Key Vault, and manage them with automatic mechanisms for tracking, backup, and recovery.
This will help you address many operational and security challenges posed by the manual tracking and management of security objects dispersed widely across multiple servers.
Oracle Key Vault stores copies of Oracle wallet files, Java keystores, and other security objects in a centralized location for long-term retention and recovery. These security objects can later be downloaded to a new wallet or keystore file and shared with trusted server peer endpoints.
The Oracle Key Vault endpoint software can read the format of Oracle wallet files and Java keystores to store their contents at the granularity of individual security objects. You can upload both password-protected and auto-login wallets, and then download the wallet contents to a new wallet of either type. This enables users to manage security objects individually and add them to virtual wallets for sharing.
Oracle Key Vault can individually store and manage the security objects contained in:
-
Oracle wallet files
Symmetric keys used for encryption (including TDE master encryption keys), passwords (Secure External Password Store), and X.509 certificates (network encryption).
Oracle Key Vault supports wallet files from all supported releases of the Oracle Database.
-
Java keystores
Symmetric keys, asymmetric keys such as private keys, and X.509 certificates.
Oracle Key Vault supports both JKS and JCEKS types of Java keystores.
The following figure illustrates the centralized storage of Oracle wallet files and Java keystores.
Figure 1-2 Centralized Storage of Oracle Wallet Files and Java Keystores
Description of "Figure 1-2 Centralized Storage of Oracle Wallet Files and Java Keystores"
Parent topic: Oracle Key Vault Use Cases
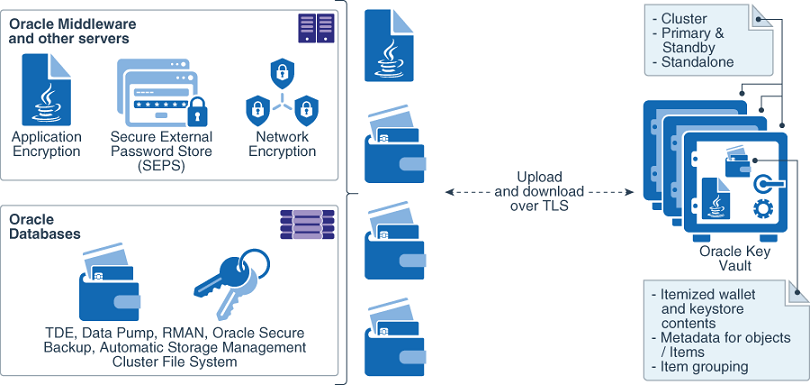
1.3.2 Centralized Management of TDE Master Encryption Keys Using Online Master Keys
You can use an online master key to centralize the management of TDE master encryption keys over a direct network connection.
This feature applies only to Oracle databases that use Transparent Data Encryption (TDE). The term online master key replaces the previous term TDE direct connection.
Online master keys enable you to centrally manage Transparent Data Encryption (TDE) master encryption keys over a network connection as an alternative to using local Oracle wallet files. The connection configuration entails using a PKCS#11 library to connect to Oracle Key Vault. After you perform the configuration, all future TDE master encryption keys will be stored and managed in Oracle Key Vault. There are two scenarios that you can use:
-
If the database does not yet have TDE wallets
-
If the database has already been configured for TDE
The online master key feature works as follows: TDE generates the master encryption key and stores it in Oracle Key Vault. Oracle Key Vault administrators have full control of the TDE master encryption keys. They can revoke access of the keys from certain endpoints, share the keys with other endpoints, and perform other operations. The online master key is also a convenient alternative to copying local wallet files to multiple endpoints manually. Sharing TDE master encryption keys, rather than maintaining local wallet copies, is especially useful when TDE is running on database clusters such as Oracle Real Application Clusters (Oracle RAC) or Oracle Data Guard. The following comparison illustrates the difference:
-
Local wallet copy
In a Data Guard scenario, re-key operations on the primary database cause the managed recovery process on the standby databases to fail. You must copy the wallet to the standby database, and then an administrator must open the wallet (if the wallet is not an auto-login wallet). Afterward, you must restart the managed recovery process.
-
Shared TDE key in a virtual wallet in Oracle Key Vault
In a database cluster, after a key rotation operation, Oracle Key Vault immediately shares the new TDE master encryption key with other nodes in the cluster. There is no need to copy the wallet manually to the other nodes. In a Data Guard configuration, after key rotation, the new keys are immediately available to the standby databases, making the key management operations seamless.
Centralized management facilitates copying encrypted data between databases using Oracle Data Pump export, import, and the transportable tablespaces features of Oracle Database when master encryption keys are stored in the wallet.
-
In non-centralized management the wallet must be manually copied from source to target databases.
-
In centralized management these master encryption keys are easily shared when you place them in a virtual wallet in Oracle Key Vault, and then grant each endpoint access to the virtual wallet.
You must open the wallet before encryption and decryption. After you close the wallet, then encrypted data in tables and tablespaces is unavailable to you. You should rotate the TDE master encryption key regularly to remain in compliance with the applicable regulations.
Oracle Key Vault supports the SQL statements that were used to administer earlier TDE releases, specifically the use of the ALTER SYSTEM and ADMINISTER KEY MANAGEMENT SQL statements.
Online master keys are supported on Oracle Database 11g release 2 or later versions.
The following figure illustrates the centralized management of online master keys.
Figure 1-3 Centralized Management of Online Master Keys
Description of "Figure 1-3 Centralized Management of Online Master Keys"
Parent topic: Oracle Key Vault Use Cases
1.3.3 Storage of Credential Files
Oracle Key Vault can back up credential files other than Oracle wallets and Java keystores for long-term retention and recovery.
Oracle Key Vault does not interpret the actual content of a credential file. It simply stores the entire file as an opaque object (a file designed to prevent tools such as Oracle Key Vault from interpreting its contents) and provides a handle to the endpoint for retrieval at a later time. A credential file contains security objects such as keys, passwords, SSH keys, Kerberos keytab files, and X.509 certificates.
You can directly upload credential files to Oracle Key Vault, consolidate them in a central repository, and share them across endpoints in a trusted group. Oracle Key Vault backs up all credential files for continued and secure access at any time. Access control to credential files is managed by Oracle Key Vault endpoint administrators.
The following figure illustrates how credential files are backed up in Oracle Key Vault.
Related Topics
Parent topic: Oracle Key Vault Use Cases
1.3.4 Online Management of Endpoint Keys and Secret Data
You can use the RESTful key management interface to manage the storage and retrieval of keys.
Applications, scripts, and third-party software can use the new interfaces to manage their keys and secrets in the Oracle Key Vault. They can retrieve the secrets or keys at run time and also generate and store new secrets or keys in Oracle Key Vault at run time. All objects managed by the user or operations executed by the user using the RESTful utility have the same security and availability attributes and the same access control as those created by other Oracle Key Vault endpoint utilities such as okvutil.
Parent topic: Oracle Key Vault Use Cases
1.4 Who Should Use Oracle Key Vault
Oracle Key Vault is designed for users who are responsible for deploying, maintaining, and managing security within the enterprise.
These users can be database, system, or security administrators, indeed any information security personnel responsible for protecting enterprise data in database servers, application servers, operating systems, and other information systems. They manage encryption keys, Oracle wallets, Java keystores, and other security objects on a regular basis.
Other users can include personnel responsible for Oracle databases, and servers that interact with Oracle Database, because Oracle Key Vault provides inherently tighter integration with Oracle database. These systems often deploy encryption on a large scale and may have a need to simplify key and wallet management.
Parent topic: Introduction to Oracle Key Vault
1.5 Major Features of Oracle Key Vault
Oracle Key Vault enhances security in key management with a wide range of features that support different database deployments.
- Centralized Storage and Management of Security Objects
You can store and manage security objects, such as TDE master encryption keys, wallets and keystores, and certificates, using Oracle Key Vault. - Management of Key Lifecycle
The management of the key lifecycle is critical for maintaining security and regulatory compliance, and consists of creation, backup, rotation, and expiration. - Reporting and Alerts
Oracle Key Vault provides reports and alerts to track system activity in depth. - Separation of Duties for Oracle Key Vault Users
Oracle Key Vault provides for separation of duties in the form of three console user roles and four endpoint privileges. - Persistent Master Encryption Key Cache
The persistent master encryption key cache feature of the endpoint software enables databases to operate when the Oracle Key Vault server is unavailable. - Backup and Restore Functionality for Security Objects
Oracle Key Vault enables you to back up all security objects including keys, certificates, and passwords. - Management of Oracle Key Vault Using RESTful Service
You can use Oracle Key Vault RESTful services to automate many of the configuration, deployment, and administration tasks at scale. - Support for OASIS Key Management Interoperability Protocol (KMIP)
You can use Oracle Key Vault with a range of OASIS KMIP Version 1.1 profiles. - Database Release and Platform Support
Oracle Key Vault supports both full Oracle Database releases and bundle patches of Oracle Database. - Integration with External Audit and Monitoring Services
You can use Oracle Key Vault with Oracle Audit Vault and Database Firewall and Simple Network Management Protocol (SNMP). - Integration of MySQL with Oracle Key Vault
Oracle Key Vault can manage MySQL TDE encryption keys. - Automatic Storage Management Cluster File System (ACFS) Encryption
Oracle Key Vault supports key management for Automatic Storage Management (ASM) cluster file system (ACFS) encryption. - Support for Oracle Cloud Database as a Service Endpoints
An Oracle Key Vault on-premises server can manage Transparent Data Encryption (TDE) master encryption keys for Oracle Cloud Database as a Service instance. - Oracle Key Vault Hardware Security Module Integration
Oracle Key Vault can use a hardware security module (HSM) as a Root of Trust (RoT) that protects encryption keys. - Support for a Primary-Standby Environment
To ensure that Oracle Key Vault can always access security objects, you can deploy Oracle Key Vault in a primary-standby (highly available) configuration.
Related Topics
Parent topic: Introduction to Oracle Key Vault
1.5.1 Centralized Storage and Management of Security Objects
You can store and manage security objects, such as TDE master encryption keys, wallets and keystores, and certificates, using Oracle Key Vault.
-
TDE master encryption keys
For Oracle databases that use Transparent Data Encryption (TDE), Oracle Key Vault manages master encryption keys over a direct network connection using an online master encryption key as an alternative to using local wallet files. The keys stored in Oracle Key Vault can be shared across databases according to endpoint access control settings. This method of sharing keys without local wallet copies is useful when TDE is running on database clusters such as Oracle Real Application Clusters (Oracle RAC), Oracle Data Guard, or Oracle GoldenGate. You can easily migrate master encryption keys from Oracle wallets to Oracle Key Vault. Direct connections between TDE and Oracle Key Vault are supported for Oracle Database 11g release 2 or later.
-
Oracle wallets and Java keystores
Oracle wallets and Java keystores are often widely distributed across servers and server clusters, with backup and distribution of these files performed manually. Oracle Key Vault itemizes and stores contents of these files in a master repository, yet allows server endpoints to continue operating with their local copies, while being disconnected from Oracle Key Vault. After you have archived wallets and keystores, you can recover them to their servers if their local copies are mistakenly deleted or their passwords are forgotten. Oracle Key Vault streamlines the sharing of wallets across database clusters such as Oracle RAC, Oracle Active Data Guard, and Oracle GoldenGate. Sharing wallets also facilitates the movement of encrypted data using Oracle Data Pump and the transportable tablespaces feature of Oracle Database, or when migrating (unplugging or plugging) a PDB. You can use Oracle Key Vault with Oracle wallets from all supported releases of Oracle middleware products and Oracle Database.
-
Credential files
Applications store keys, passwords, and other types of sensitive information in credential files that are often widely distributed without appropriate protective mechanisms. Secure Shell (SSH) key files and Kerberos keytabs are examples of credential files. Oracle Key Vault backs up credential files for long-term retention and recovery, audits access to them, and shares them across trusted server endpoints.
-
Certificate files
X.509 certificate files (common file extensions include
.pem,.cer,.crt,.der,.p12) used to authenticate and validate user identities and encrypt data on communication channels may also be stored, shared, and managed in Oracle Key Vault.
Parent topic: Major Features of Oracle Key Vault
1.5.2 Management of Key Lifecycle
The management of the key lifecycle is critical for maintaining security and regulatory compliance, and consists of creation, backup, rotation, and expiration.
Oracle Key Vault provides mechanisms for facilitating periodic key rotations, backup, and recovery, which ensure that you can stay in regulatory compliance, unlike other systems that create keys and passwords. You can create policies to track the key lifecycle, and configure Oracle Key Vault to report key lifecycle changes as they happen. In this manner, you will know when keys are due to expire, and can ensure that they are properly rotated and backed up.
Key lifecycle tracking is very important to maintain compliance with industry and governmental standards, such as the Payment Card Industry Data Security Standard (PCI DSS), which deal with highly sensitive data, and therefore have stringent requirements regarding the maximum lifetime of encryption keys and passwords.
Parent topic: Major Features of Oracle Key Vault
1.5.3 Reporting and Alerts
Oracle Key Vault provides reports and alerts to track system activity in depth.
-
Reports
The Oracle Key Vault audit and management reports provide detailed statistics on system, user, and endpoint activity, certificate, key and password expiry, entitlement and metadata of security objects. Audit reports capture all user and endpoint actions, the objects of the actions, and their final result.
-
Alerts
You can configure the types of alerts that you want to receive. These include alerts for the expiration of keys, endpoint certificates, and user passwords, disk utilization, system backup, and primary-standby events. You can choose to send alerts to syslog to allow for external monitoring.
Parent topic: Major Features of Oracle Key Vault
1.5.4 Separation of Duties for Oracle Key Vault Users
Oracle Key Vault provides for separation of duties in the form of three console user roles and four endpoint privileges.
The roles are System Administrator, Key Administrator, and Audit Manager. The endpoint privileges are Create Endpoint, Manage Endpoint, Create Endpoint Group, and Manage Endpoint Group.
Each user role possesses privileges for a type of task and may be assigned to one user (for a strict separation of duties) or combined so a single user performs multiple user roles according to the needs of the organization.
The user who is responsible for uploading and downloading security objects between Oracle Key Vault and the endpoint is referred to as the endpoint administrator. Only endpoint administrators can directly access security objects provided they have been granted access and only through installing the endpoint software. You cannot retrieve security objects using the Oracle Key Vault management console.
Parent topic: Major Features of Oracle Key Vault
1.5.5 Persistent Master Encryption Key Cache
The persistent master encryption key cache feature of the endpoint software enables databases to operate when the Oracle Key Vault server is unavailable.
The TDE master encryption key is cached in the persistent master encryption key cache in addition to the in-memory cache, to make the master encryption key available across database processes. It eliminates the need for databases to contact the Oracle Key Vault server for every new process, redo log switch, or database start-up operations.
The persistent master encryption key cache is not necessary in a multi-master cluster deployment. It is primarily used for standalone or primary-standby Oracle Key Vault deployments.
Related Topics
Parent topic: Major Features of Oracle Key Vault
1.5.6 Backup and Restore Functionality for Security Objects
Oracle Key Vault enables you to back up all security objects including keys, certificates, and passwords.
It encrypts backups for better protection of the sensitive keys and security objects and supports storing them securely at a remote destination.
This feature prevents loss of your sensitive data in the case of server failure, because you can restore a new Oracle Key Vault server to a previous state from a backup.
Oracle Key Vault can transfer backup files to any remote location that implements the Secure Copy Protocol (SCP) or SSH Secure File Transfer Protocol (SFTP).
Users with the System Administrator role can perform the following backup and restore tasks in Oracle Key Vault:
- Managing incremental and full backups
- Creating, deleting, and modifying remote backup locations
- Setting up, modifying, or disabling the current backup schedule
- Initiating an immediate one-time backup
- Scheduling a future one-time backup
Oracle Key Vault performs hot backup operation which means that the system is not interrupted while the backup is being created.
Parent topic: Major Features of Oracle Key Vault
1.5.7 Management of Oracle Key Vault Using RESTful Service
You can use Oracle Key Vault RESTful services to automate many of the configuration, deployment, and administration tasks at scale.
A large distributed enterprise deployment often requires automation through scripting to enable mass endpoint deployments, apply configuration changes, and perform routine management operations. The Oracle Key Vault RESTful services utility enables you perform all of these tasks in a way that facilitates faster deployment with less human intervention. You can use Oracle Key Vault RESTful services to automate the management of endpoints, wallets, access control, deployment operations, and backup operations at scale.
The Oracle Key Vault RESTful services utility also enables the automation of most key management functions at scale by providing a simplified interface to Key Management Interoperability Protocol (KMIP) operations. The RESTful services utility allows operations on managed objects such as keys, certificates, and other objects in a simple manner without requiring any client side development.
Related Topics
Parent topic: Major Features of Oracle Key Vault
1.5.8 Support for OASIS Key Management Interoperability Protocol (KMIP)
You can use Oracle Key Vault with a range of OASIS KMIP Version 1.1 profiles.
OASIS Key Management Interoperability Protocol (KMIP) standardizes key management operations between key management servers and endpoints provided by different vendors.
Oracle Key Vault implements the following OASIS KMIP Version 1.1 profiles:
-
Basic Discover Versions Server Profile: Provides the server version to endpoints.
-
Basic Baseline Server KMIP Profile: Provides core functionality to retrieve objects from the server.
-
Basic Secret Data Server KMIP Profile: Provides endpoints the ability to create, store, and retrieve secret data (typically passwords) on the server.
-
Basic Symmetric Key Store and Server KMIP Profile: Provides endpoints the ability to store and retrieve symmetric encryption keys on the server.
-
Basic Symmetric Key Foundry and Server KMIP Profile: Provides endpoints the ability to create new symmetric encryption keys on the server.
Parent topic: Major Features of Oracle Key Vault
1.5.9 Database Release and Platform Support
Oracle Key Vault supports both full Oracle Database releases and bundle patches of Oracle Database.
Oracle Key Vault supports Oracle Database releases 11g release 2 or later on Oracle Linux x86-64, Solaris, AIX, and HP-UX (IA) as endpoints without patching. Oracle Key Vault also supports the bundle patches of Oracle Database release 11g release 2 and 12c release 1 (12.1.0.2) or later on Windows Server 2012.
Related Topics
Parent topic: Major Features of Oracle Key Vault
1.5.10 Integration with External Audit and Monitoring Services
You can use Oracle Key Vault with Oracle Audit Vault and Database Firewall and Simple Network Management Protocol (SNMP).
Oracle Key Vault supports integration with Oracle Audit Vault and Database Firewall for central storage of audit records generated. Oracle Key Vault also supports use of SNMP version 3 to monitor the health and availability of the system.
Parent topic: Major Features of Oracle Key Vault
1.5.11 Integration of MySQL with Oracle Key Vault
Oracle Key Vault can manage MySQL TDE encryption keys.
Note:
MySQL Windows databases are not supported.Related Topics
Parent topic: Major Features of Oracle Key Vault
1.5.12 Automatic Storage Management Cluster File System (ACFS) Encryption
Oracle Key Vault supports key management for Automatic Storage Management (ASM) cluster file system (ACFS) encryption.
Parent topic: Major Features of Oracle Key Vault
1.5.13 Support for Oracle Cloud Database as a Service Endpoints
An Oracle Key Vault on-premises server can manage Transparent Data Encryption (TDE) master encryption keys for Oracle Cloud Database as a Service instance.
Related Topics
Parent topic: Major Features of Oracle Key Vault
1.5.14 Oracle Key Vault Hardware Security Module Integration
Oracle Key Vault can use a hardware security module (HSM) as a Root of Trust (RoT) that protects encryption keys.
HSMs are built with specialized tamper-resistant hardware which is harder to access than normal servers. This protects the RoT and makes it difficult to extract, lowering the risk of compromise. In addition, you can use HSMs in FIPS 140-2 Level 3 mode which can help meet certain compliance requirements.
Related Topics
Parent topic: Major Features of Oracle Key Vault
1.5.15 Support for a Primary-Standby Environment
To ensure that Oracle Key Vault can always access security objects, you can deploy Oracle Key Vault in a primary-standby (highly available) configuration.
This configuration also supports disaster recovery scenarios.
You can deploy two Oracle Key Vault servers in a primary-standby configuration. The primary server services the requests that come from endpoints. If the primary server fails, then the standby server takes over after a configurable preset delay. This configurable delay ensures that the standby server does not take over prematurely in case of short communication gaps.
The primary-standby configuration was previously known as the high availability configuration. The primary-standby configuration and the multi-master cluster configuration are mutually exclusive.
Oracle Key Vault supports primary-standby read-only restricted mode. When the primary server is affected by server, hardware, or network failures, primary-standby read-only restricted mode ensures that an Oracle Key Vault server is available to service endpoints, thus ensuring operational continuity. However, key and sensitive operations, such as generation of keys are disabled, while operations such as generation of audit logs are unaffected.
When an unplanned shutdown makes the standby server unreachable, the primary server is still available to the endpoints in read-only mode.
Related Topics
Parent topic: Major Features of Oracle Key Vault
1.6 Oracle Key Vault Interfaces
Oracle Key Vault provides both a graphical user interface and command-line interfaces.
- Oracle Key Vault Management Console
The Oracle Key Vault management console is a browser-based graphical user interface that Key Vault administrators use to perform day-to-day tasks. - Oracle Key Vault okvutil Endpoint Utility
Endpoint administrators can use theokvutilcommand-line utility to upload and download security objects between Oracle Key Vault and endpoints. - Oracle Key Vault RESTful Services
You can use the Oracle Key Vault RESTful Services utility to automate processes for a large distributed enterprise deployment. - Oracle Key Vault Client SDK
Parent topic: Introduction to Oracle Key Vault
1.6.1 Oracle Key Vault Management Console
The Oracle Key Vault management console is a browser-based graphical user interface that Key Vault administrators use to perform day-to-day tasks.
It enables Oracle Key Vault administrators to manage keys and sensitive objects, wallets, endpoints, and users. The console can also configure settings for individual Oracle Key Vault servers, as well as multi-master clusters, primary-standby environments, backup, and recovery.
Related Topics
Parent topic: Oracle Key Vault Interfaces
1.6.2 Oracle Key Vault okvutil Endpoint Utility
Endpoint administrators can use the okvutil command-line utility to upload and download security objects between Oracle Key Vault and endpoints.
The okvutil utility communicates with Oracle Key Vault over a mutually authenticated secure connection.
Related Topics
Parent topic: Oracle Key Vault Interfaces
1.6.3 Oracle Key Vault RESTful Services
You can use the Oracle Key Vault RESTful Services utility to automate processes for a large distributed enterprise deployment.
This utility enables you to automate the management of endpoints, wallets, security objects, deployment operations, and backup operations using RESTful services that are JSON compliant.
Related Topics
Parent topic: Oracle Key Vault Interfaces
1.6.4 Oracle Key Vault Client SDK
Various Oracle and non-Oracle products can use the Oracle Key Vault client SDK to integrate directly with Oracle Key Vault.
The client SDK is available in both Java and C. It has a comprehensive set of high-level and low-level APIs and sample programs.
Related Topics
Parent topic: Oracle Key Vault Interfaces
1.7 Overview of an Oracle Key Vault Deployment
There are three different Oracle Key Vault deployment options.
- A multi-master cluster configuration allows for up to 16 nodes and is recommended for deployments requiring high availability. This is the recommended deployment.
- A standalone deployment is simplest to deploy. However, it does not provide continuous availability of the key service in the event an Oracle Key Vault server becomes unavailable.
- A primary-standby configuration enables the deployment of a second Oracle Key Vault server as a passive standby to an active primary server. If a primary server becomes unavailable, then the standby server becomes the new primary Oracle Key Vault server to service read and write requests from the endpoints. This is the high availability mode that was introduced in Oracle Key Vault release 12.2.
You can use the following steps as a guideline to deploying Oracle Key Vault within your organization:
-
Understand important concepts described in Oracle Key Vault Concepts and Oracle Key Vault Multi-Master Cluster Concepts.
-
Install and configure Oracle Key Vault as described in Oracle Key Vault Installation and Configuration.
-
Create a multi-master cluster by adding up to 16 Oracle Key Vault servers for maximum redundancy and reliability. This is described in Managing Oracle Key Vault Multi-Master Clusters.
You must have a separate license for each Oracle Key Vault server installation in a multi-master cluster environment.
-
As an alternative to a multi-master cluster deployment, create a primary-standby configuration by adding a second Oracle Key Vault server. Enable primary-standby read-only restricted mode to ensure operational continuity of the endpoints. This is described in Managing an Oracle Key Vault Primary-Standby Configuration.
You must have a separate license for each Oracle Key Vault server installation in a primary-standby environment.
-
Create users to manage the day-to-day tasks for Oracle Key Vault as described in Managing Oracle Key Vault Users.
-
Register endpoints so that they can use Oracle Key Vault to store and manage their security objects described in Managing Oracle Key Vault Endpoints.
-
Register endpoints in the cloud described in Oracle Database Instances in Oracle Cloud Infrastructure.
-
Enroll endpoints so that you can upload or download security objects between the endpoints and Oracle Key Vault described in Enrolling and Upgrading Endpoints for Oracle Key Vault.
-
Upload or add virtual wallets to Oracle Key Vault described in Managing Oracle Key Vault Master Encryption Keys.
-
Use automating endpoint enrollment and provisioning for large-scale deployments in Oracle Key Vault RESTful Services Administrator's Guide .
-
Read about using Oracle Key Vault with other features, such as Oracle GoldenGate, in Managing Keys for Oracle Products.
-
Automate key management to perform online key management with other software using RESTful services and client SDK, as described in Oracle Key Vault RESTful Services Administrator's Guide .
-
Learn how to perform periodic maintenance tasks such as administering and monitoring the system, as described in Oracle Key Vault General System Administration.
- Learn how to monitor Oracle Key Vault by performing tasks such as creating alerts, as described in Monitoring and Auditing Oracle Key Vault.
Parent topic: Introduction to Oracle Key Vault