22 Monitoring and Auditing Oracle Key Vault
Oracle Key Vault administrators can monitor and audit the Oracle Key Vault system, configure alerts and use reports.
- Managing System Monitoring
System monitoring refers to tasks such as configuring SNMP connections, email notifications, the syslog destination, and system diagnostics. - Configuring Oracle Key Vault Alerts
You can select the type of alerts that you want to see in the Oracle Key Vault dashboard. - Managing System Auditing
Auditing entails tasks such as capturing audit records in a syslog file or downloading the audit records to a local file. - Using Oracle Key Vault Reports
Oracle Key Vault collects statistical information on a range of activities that impact Key Vault operations.
22.1 Managing System Monitoring
System monitoring refers to tasks such as configuring SNMP connections, email notifications, the syslog destination, and system diagnostics.
- Configuring Remote Monitoring to Use SNMP
With Simple Network Management Protocol (SNMP) enabled, system administrators can remotely monitor the Oracle Key Vault appliance and its services. - Configuring Email Notification
You can use email notifications to directly notify administrators of Key Vault status changes without logging into the Oracle Key Vault management console. - Configuring the Syslog Destination for Individual Multi-Master Cluster Nodes
On each node, you can forward syslog entries to a remote service such as Splunk or SIEM. - Capturing System Diagnostics
To troubleshoot problems that may arise, you can generate a diagnostics package. - Monitoring System Metrics
You can use the System Metrics Monitoring feature to view and collect data for key system resource usage including CPU and Memory Usage in Oracle Key Vault.
Parent topic: Monitoring and Auditing Oracle Key Vault
22.1.1 Configuring Remote Monitoring to Use SNMP
With Simple Network Management Protocol (SNMP) enabled, system administrators can remotely monitor the Oracle Key Vault appliance and its services.
The collected data can be further processed and presented for the needs of the enterprise.
- About Using SNMP for Oracle Key Vault
You can use the Simple Network Management Protocol (SNMP) to monitor devices on a network for resource usage. - Granting SNMP Access to Users
You can grant any user, including users who are not Oracle Key Vault administrators, access to SNMP data. - Changing the SNMP User Name and Password
You can change the SNMP user name and password for a node at any time. - Changing SNMP Settings on the Standby Server
You change the SNMP settings from the command line on the standby server. - Remotely Monitoring Oracle Key Vault Using SNMP
SNMP enables you to monitor the vital components of Oracle Key Vault remotely without having to install new software in Oracle Key Vault. - SNMP Management Information Base Variables for Oracle Key Vault
Oracle Key Vault provides a set of SNMP Management Information Base (MIB) variables that you can track. - Example: Simplified Remote Monitoring of Oracle Key Vault Using SNMP
In Linux, you can simplify the SNMP commands you manually enter to find Oracle Key Vault information, yet still have useful and detailed output.
Parent topic: Managing System Monitoring
22.1.1.1 About Using SNMP for Oracle Key Vault
You can use the Simple Network Management Protocol (SNMP) to monitor devices on a network for resource usage.
Monitoring Oracle Key Vault is an important aspect how critical Oracle Key Vault's availability is when hundreds or thousands of Oracle and MySQL databases store their TDE master encryption keys in an Oracle Key Vault multi-master cluster. The types of resource usage that you should monitor include memory, CPU utilization, and processes. Even though Oracle Key Vault provides continuous key availability by allowing up to 16 (geographically distributed) instances to be connected to a single cluster, the health of each individual node contributes to the performance and availability of the entire cluster.
You can use Simple Network Management Protocol (SNMP) third-party tool to monitor remote systems that access Oracle Key Vault. The benefits of using SNMP to monitor Oracle Key Vault are as follows:
- There is no need to allow SSH access to Oracle Key Vault. (SSH access should only be enabled for the window of time in which it is being used.)
- You do not need to install additional tools to perform an SNMP monitoring operation.
Oracle Key Vault uses SNMP version 3 for user authentication and data encryption features. Unlike SNMP versions 1 and 2 that communicate in readable, insecure plaintext, SNMP 3 authenticates users and encrypts data on the communication channel between the monitoring server and the target. The information from Oracle Key Vault is unreadable to an intruder, even if the communication channel is intercepted.
In addition, with SNMP enabled on Oracle Key Vault, you can determine whether the key management server (KMIP daemon) is running. To track this information, you must use a third-party SNMP client to poll the Oracle Key Vault instance, because Oracle Key Vault does not provide SNMP client software.
Oracle Key Vault audits the creation and modification of SNMP credentials.
You must be a user with the System Administrator role to configure the SNMP account with a user name and password. These SNMP credentials are needed to access SNMP data.
In a multi-master cluster, the SNMP account with a user name and password can be set for all nodes of the cluster at once. It can also be set for each individual node.
Note:
You must ensure that the SNMP username and password is not the same username and password as any of the Oracle Key Vault administrative user accounts with the System Administrator, Key Administrator, or Audit Manager role.
Parent topic: Configuring Remote Monitoring to Use SNMP
22.1.1.2 Granting SNMP Access to Users
You can grant any user, including users who are not Oracle Key Vault administrators, access to SNMP data.
Parent topic: Configuring Remote Monitoring to Use SNMP
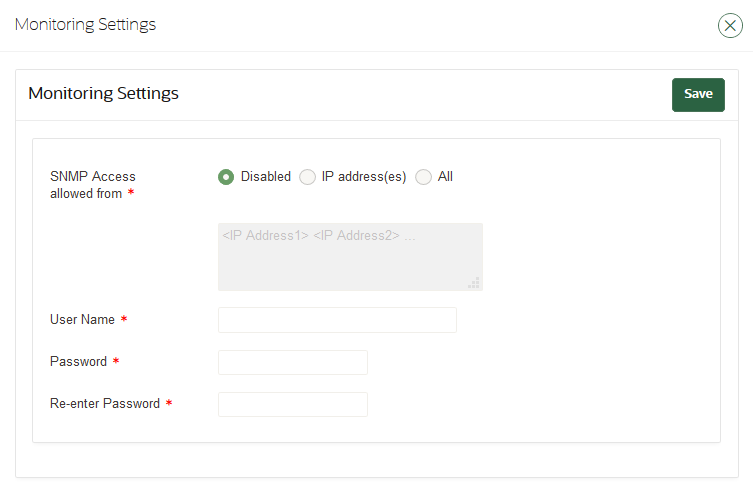
22.1.1.3 Changing the SNMP User Name and Password
You can change the SNMP user name and password for a node at any time.
- Log in to the Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then select Settings from the left navigation bar.
- In the Monitoring and Alerts area, click SNMP.
- In the User Name, Password, and Re-enter Password fields, enter the user name and password information.
- Click Save.
Parent topic: Configuring Remote Monitoring to Use SNMP
22.1.1.4 Changing SNMP Settings on the Standby Server
You change the SNMP settings from the command line on the standby server.
To add SNMP support in a primary-standby environment, you should configure SNMP on both the primary and standby servers before pairing them. This is because the standby server is no longer accessible from the Oracle Key Vault management console because all requests are forwarded to the primary server. However, you can change SNMP settings on the standby server in a primary-standby environment.
The following examples show how to change SNMP settings on a standby server:
snmpuser and password password:./stdby_snmp_enable -a "all" -u "snmpuser" -p "password"./stdby_snmp_enable -a "disabled"./stdby_snmp_enable -a "192.0.2.1 192.0.2.2 192.0.2.3" -u "snmpuser" -p "password"Parent topic: Configuring Remote Monitoring to Use SNMP
22.1.1.5 Remotely Monitoring Oracle Key Vault Using SNMP
SNMP enables you to monitor the vital components of Oracle Key Vault remotely without having to install new software in Oracle Key Vault.
snmpwalk and snmpget from the command line on a remote computer that has a network connection into the SNMP account in Oracle Key Vault.
Parent topic: Configuring Remote Monitoring to Use SNMP
22.1.1.6 SNMP Management Information Base Variables for Oracle Key Vault
Oracle Key Vault provides a set of SNMP Management Information Base (MIB) variables that you can track.
The following table lists the MIB variables that are supported.
Table 22-1 MIBs That SNMP Tracks for Oracle Key Vault
| MIB Variable | Object ID | Description |
|---|---|---|
|
|
1.3.6.1.2.1.25.1.1 |
Tracks the amount of time that an Oracle Key Vault instance has been running |
|
|
1.3.6.1.2.1.2.2.1.7 |
Tracks if the Oracle Key Vault network interface (
|
|
|
1.3.6.1.4.1.2021.4.6 |
Tracks the available RAM |
|
|
1.3.6.1.4.1.2021.4.5 |
Tracks the total amount of RAM being used |
|
|
1.3.6.1.4.1.2021.11.53 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent idle |
|
|
1.3.6.1.4.1.2021.11.56 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent processing hardware interrupts |
|
|
1.3.6.1.4.1.2021.11.55 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent processing kernel-level code |
|
|
1.3.6.1.4.1.2021.11.51 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent processing reduced-priority code |
|
|
1.3.6.1.4.1.2021.11.52 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent processing system-level code |
|
|
1.3.6.1.4.1.2021.11.50 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent processing user-level code |
|
|
1.3.6.1.4.1.2021.11.54 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent waiting for input-output (IO) |
|
|
1.3.6.1.4.1.2021.2 |
Tracks the number of processes running under a certain name. Names we monitor are
|
nsExtendOutputFull |
1.3.6.1.4.1.8072.1.3.2.3.1.2 |
For monitoring Fast Recovery Area Space utilization; displays the size, used and free space. The alert also shows the CA and the server certificate expiration date and time, as well as the status of the Oracle Audit Vault agent and the Apache Tomcat Web server. For the certificate expiration, the time zone that is shown for the date and time is in UTC. The output may be inconsistent if Oracle Key Vault is in the middle of a certification rotation. |
sysDescr |
1.3.6.1.2.1.1.1 |
Represents the product name and version identification of Oracle Key Vault. |
sysUpTime |
1.3.6.1.2.1.1.3 |
Represents the time (in hundredths of a second) since the network management portion of the system was last re-initialized. |
sysName |
1.3.6.1.2.1.1.5 |
Represents an administratively-assigned name. By convention, this is the node's fully-qualified domain name. |
See Also:
For more information refer to the Net-SNMP documentation at http://www.net-snmp.org
Parent topic: Configuring Remote Monitoring to Use SNMP
22.1.1.7 Example: Simplified Remote Monitoring of Oracle Key Vault Using SNMP
In Linux, you can simplify the SNMP commands you manually enter to find Oracle Key Vault information, yet still have useful and detailed output.
The configuration in this section assumes that you have granted SNMP access to a trusted user. It also assumes that the you have installed the SNMP Management Information Base (MIB) variables on the remote host that will monitor Oracle Key Vault.
For example, a lengthy version of the snmpwalk command for an SNMP user named snmp_admin is as follows:
snmpwalk -v3 OKV_IP_address -n "" -l authPriv -u snmp_admin -a SHA -A snmp_user_password -x AES -X snmp_user_password
This command lists the vital services that are running on Oracle Key Vault. However, you can modify the command (and other SNMP commands) to be not only shorter, but to show additional information, such as whether the services are running or not running.
To simplify this type of command, you can edit the /etc/snmp/snmp.conf configuration file so that the SNMP commands you enter will automatically include commonly used settings, such as the default user or the default security level. The example in this topic omits password parameters so that users can enter the password at the command line interactively.
- Log in to the remote host that will monitor Oracle Key Vault.
- Edit the
/etc/snmp/snmp.conf, which appears as follows:# As the snmp packages come without MIB files due to license reasons, # loading MIBs is disabled by default. If you added the MIBs you # can reenable loading them by commenting out the following line. mibs :
- Comment out the
# mibs :line and then add the following lines, as follows:# loading MIBs is disabled by default. If you added the MIBs you # can reenable loading them by commenting out the following line. # mibs : defSecurityName snmp_admin defSecurityLevel authPriv defAuthType SHA1 defPrivType AES128
In this example:
defSecurityName: Enter the name of the user to whom you granted SNMP access. This example usessnmp_admin.defSecurityLevel: Enter the default security level to use. This example usesauthPriv, which enables communication with authentication and privacy.defAuthType: Enter the default authorization type. This example usesSHA1.defPrivType: Enter the default privilege type. This example usesAES128.
- Restart
snmpdto load the configuration file.For example, for Linux 7 and later:
systemctl restart snmpd
For Linux 6:
service snmpd restart
- To run the simplified version of the
snmpwalkcommand that was shown earlier, enter the following command:snmpwalk okv_ip_address prNames -A snmp_user_pwd -X snmp_user_pwd
In this command,
prNamesrefers to "process names", which displays the names of processes instead of numbers. For example:$ snmpwalk 192.0.2.254 prNames -A snmp_user_pwd -X snmp_user_pwd UCD-SNMP-MIB::prNames.1 = STRING: httpd UCD-SNMP-MIB::prNames.2 = STRING: kmipd UCD-SNMP-MIB::prNames.3 = STRING: kmipusd UCD-SNMP-MIB::prNames.4 = STRING: ora_pmon_dbfwdb UCD-SNMP-MIB::prNames.5 = STRING: ServiceManager UCD-SNMP-MIB::prNames.6 = STRING: adminsrvr UCD-SNMP-MIB::prNames.7 = STRING: distsrvr UCD-SNMP-MIB::prNames.8 = STRING: recvsrvr UCD-SNMP-MIB::prNames.9 = STRING: av_agent_monitor
snmptable command now becomes the following. snmptable okv_ip_address prTable -A snmp_user_pwd -X snmp_user_pwd
Output similar to the following appears.
$ snmptable 192.168.1.181 -A Manager_1 -X Manager_1 prTable
SNMP table: UCD-SNMP-MIB::prTable
prIndex prNames prMin prMax prCount prErrorFlag prErrMessage prErrFix prErrFixCmd
1 httpd 1 20 8 noError noError
2 kmipd 1 2 2 noError noError
3 kmipusd 1 2 2 noError noError
4 ora_pmon_dbfwdb 1 1 1 noError noError
5 ServiceManager 1 1 1 noError noError
6 adminsrvr 1 1 1 noError noError
7 distsrvr 1 1 1 noError noError
8 recvsrvr 1 1 1 noError noError
9 av_agent_monitor 1 1 0 error No av_agent_monitor process running noError
The next example shows how you would now run the snmpdf command:
snmpdf okv_ip_address -A snmp_user_pwd -X snmp_user_pwd
Output similar to the following appears.
Description Size (kB) Used Available Used% / 20027260 7247856 12779404 36% /usr/local/dbfw/tmp 6932408 15764 6916644 0% /var/log 5932616 19932 5912684 0% /tmp 1999184 3072 1996112 0% /var/lib/oracle 143592160 35023900 108568260 24%
Parent topic: Configuring Remote Monitoring to Use SNMP
22.1.2 Configuring Email Notification
You can use email notifications to directly notify administrators of Key Vault status changes without logging into the Oracle Key Vault management console.
- About Email Notification
Email notifications alert users of status changes and are used to complete the processes of endpoint enrollment and user password reset operations. - Configuring Email Settings
You can configure the Simple Mail Transfer Protocol (SMTP) server properties to receive email notifications from Oracle Key Vault. - Testing the Email Configuration
Oracle Key Vault management console enables you to send test emails to test the email configuration. - Disabling Email Notifications for a User
You can use the Oracle Key Vault management console to enable or disable email notifications.
Parent topic: Managing System Monitoring
22.1.2.1 About Email Notification
Email notifications alert users of status changes and are used to complete the processes of endpoint enrollment and user password reset operations.
To enable email notification you must set your email preferences in Oracle Key Vault. You can choose the events that you want updates to. The events include Oracle Key Vault system status like disk utilization, backup, and primary-standby, or user and endpoint status like expiration of user passwords, endpoint certificates, and keys, or cluster status like the heartbeat lag, naming conflicts, cluster-wide HSM status, and others.
In cluster deployments, you must configure and validate email settings on all nodes of the cluster. Email settings of a cluster node are local to that node.
Configuring Email Settings is driven by the SMTP provider. Once you confirm that the SMTP server is reachable from the Oracle Key Vault server. You need to follow the required setting from the SMTP provider.
You can modify the SMTP server configuration at any time. If a custom SMTP certificate was used initially, and you later decide to use the default, you can modify the trust store setting to default, instead of custom.
For example:
-
The enrollment token generated during endpoint enrollment can be mailed directly to the endpoint administrator from Oracle Key Vault.
-
An Oracle Key Vault system administrator can send the random temporary password directly to the user when the user password is reset.
To enable email notifications successfully, there must be a connection between Oracle Key Vault and the SMTP server.
You can disable email notifications at any time.
Note:
If you are using Oracle Key Vault in an Oracle Cloud Infrastructure (OCI) environment, then see My Oracle Support note 2501601.1 for information about how to configure Postfix to use email delivery on the Oracle Linux 6 and 7 platforms. After you complete the configuration, ensure that you populate theFrom Address field with the approved sender from OCI.
Parent topic: Configuring Email Notification
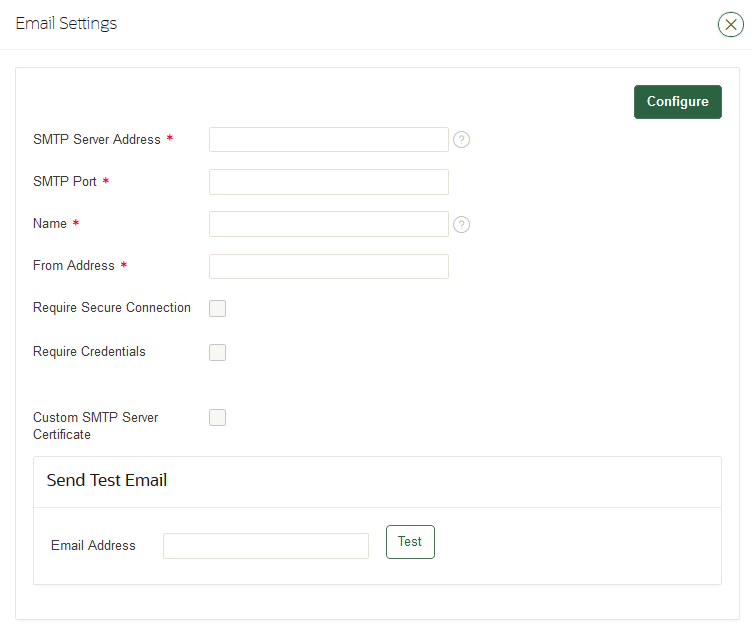
22.1.2.2 Configuring Email Settings
You can configure the Simple Mail Transfer Protocol (SMTP) server properties to receive email notifications from Oracle Key Vault.
Parent topic: Configuring Email Notification
22.1.2.3 Testing the Email Configuration
Oracle Key Vault management console enables you to send test emails to test the email configuration.
Related Topics
Parent topic: Configuring Email Notification
22.1.2.4 Disabling Email Notifications for a User
You can use the Oracle Key Vault management console to enable or disable email notifications.
Parent topic: Configuring Email Notification
22.1.3 Configuring the Syslog Destination for Individual Multi-Master Cluster Nodes
On each node, you can forward syslog entries to a remote service such as Splunk or SIEM.
- Setting the Syslog Destination Setting for the Node
You can set the syslog destination to use either Transmission Control Protocol (TCP) or User Datagram Protocol (UDP). - Clearing the Syslog Destination Setting for the Node
You can clear the syslog destination setting for the node and then reset the node to the cluster setting.
Parent topic: Managing System Monitoring
22.1.3.1 Setting the Syslog Destination Setting for the Node
You can set the syslog destination to use either Transmission Control Protocol (TCP) or User Datagram Protocol (UDP).
22.1.3.2 Clearing the Syslog Destination Setting for the Node
You can clear the syslog destination setting for the node and then reset the node to the cluster setting.
- Log into the Oracle Key Vault management console for the node as a user who has the System Administrator role.
- Select the System tab, and then Settings from the left navigation bar.
- In the Monitoring and Alerts area, click Syslog.
- In the Syslog window, click Delete.
22.1.4 Capturing System Diagnostics
To troubleshoot problems that may arise, you can generate a diagnostics package.
- About Capturing System Diagnostics
The Oracle Key Vault diagnostics file provides advanced debugging and troubleshooting information for problems that you may encounter while using Oracle Key Vault. - Configuring the Oracle Key Vault Application Tracing Level
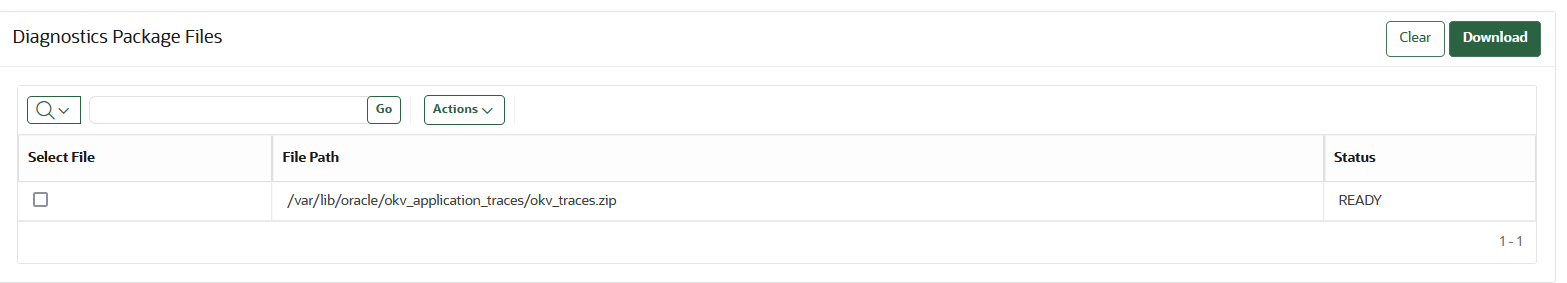
The System Administrator can configure the tracing level for the unified application tracing from the configure diagnostics page. - Downloading the Diagnostics Package
The system administrator can download the diagnostic files using the Oracle Key Vault management console. - Unpacking the Diagnostics Package
When the generated diagnostics bundle file size is smaller than the partition size, the diagnostics package is available in a singular.zipfile. Otherwise, the diagnostics bundle is split into and is available in parts with the extension.zip-partXX. - Deleting Trace Files
You can delete the old tracing files after they are downloaded to free up the disk space.
Parent topic: Managing System Monitoring
22.1.4.1 About Capturing System Diagnostics
The Oracle Key Vault diagnostics file provides advanced debugging and troubleshooting information for problems that you may encounter while using Oracle Key Vault.
You can download diagnostics file and provide it to Oracle support for further analysis and debugging.
By default, diagnostics reporting is enabled on Oracle Key Vault. With the simplified diagnostics collection, system administrators are able to select which diagnostics components are to be packaged for the downloadable diagnostics bundle. Be aware that the first time you run the diagnostic utility or after the Oracle Key Vault system’s internal database has been restarted, it can take longer to produce the bundle compared to subsequent runs because it must gather all the diagnostic information of the system.
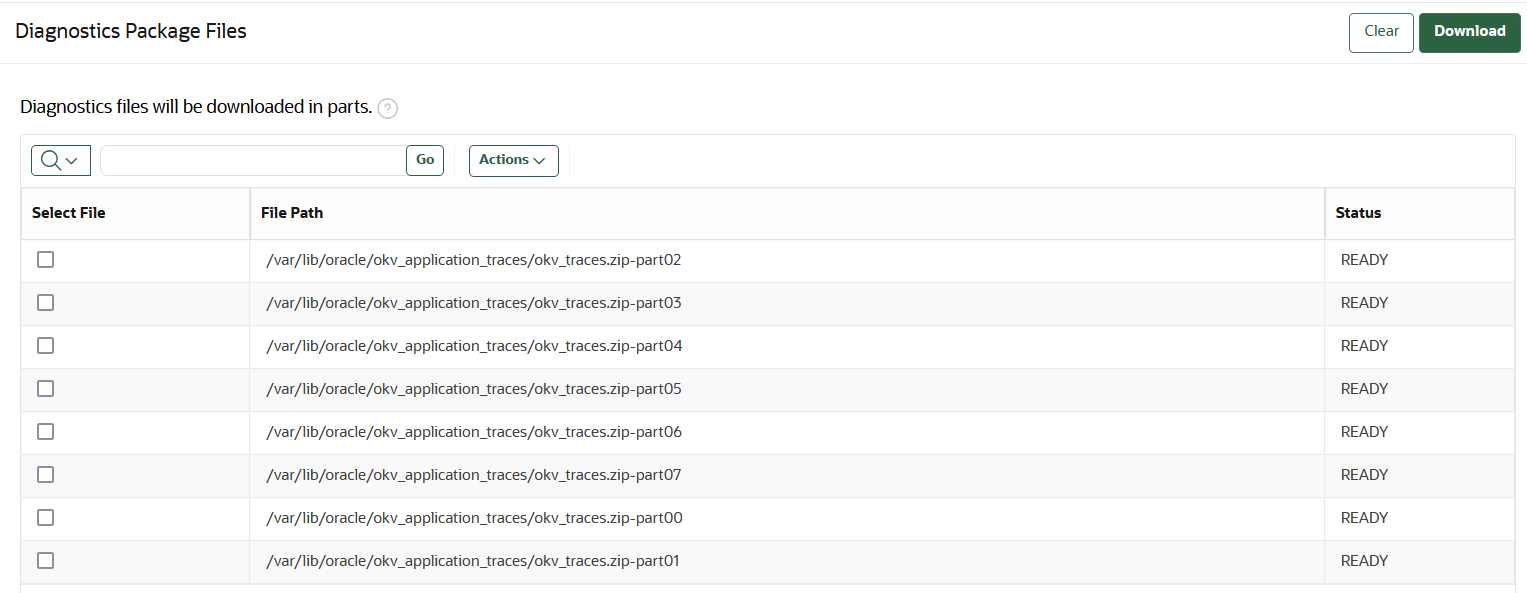
If you plan to perform an upgrade of the Oracle Key Vault server, then disable the diagnostics packaging utility by ensuring that there are no files available to download. This can be confirmed by checking if the Diagnostics page has a section called Diagnostics Package Files. If it does, click Clear to disable the utility.
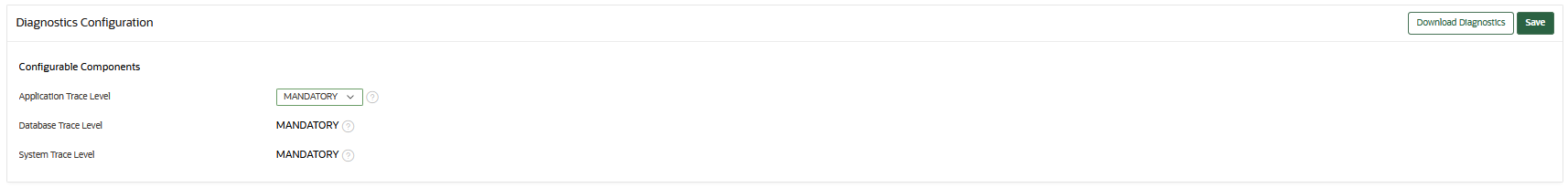
During upgrades, the current trace level for each component will reset to the Mandatory trace level.
Parent topic: Capturing System Diagnostics
22.1.4.2 Configuring the Oracle Key Vault Application Tracing Level
The System Administrator can configure the tracing level for the unified application tracing from the configure diagnostics page.
Parent topic: Capturing System Diagnostics
22.1.4.3 Downloading the Diagnostics Package
The system administrator can download the diagnostic files using the Oracle Key Vault management console.
Parent topic: Capturing System Diagnostics
22.1.4.4 Unpacking the Diagnostics Package
When the generated diagnostics bundle file size is smaller than the
partition size, the diagnostics package is available in a singular .zip
file. Otherwise, the diagnostics bundle is split into and is available in parts with the
extension .zip-partXX.
Related Topics
Parent topic: Capturing System Diagnostics
22.1.4.5 Deleting Trace Files
You can delete the old tracing files after they are downloaded to free up the disk space.
Parent topic: Capturing System Diagnostics
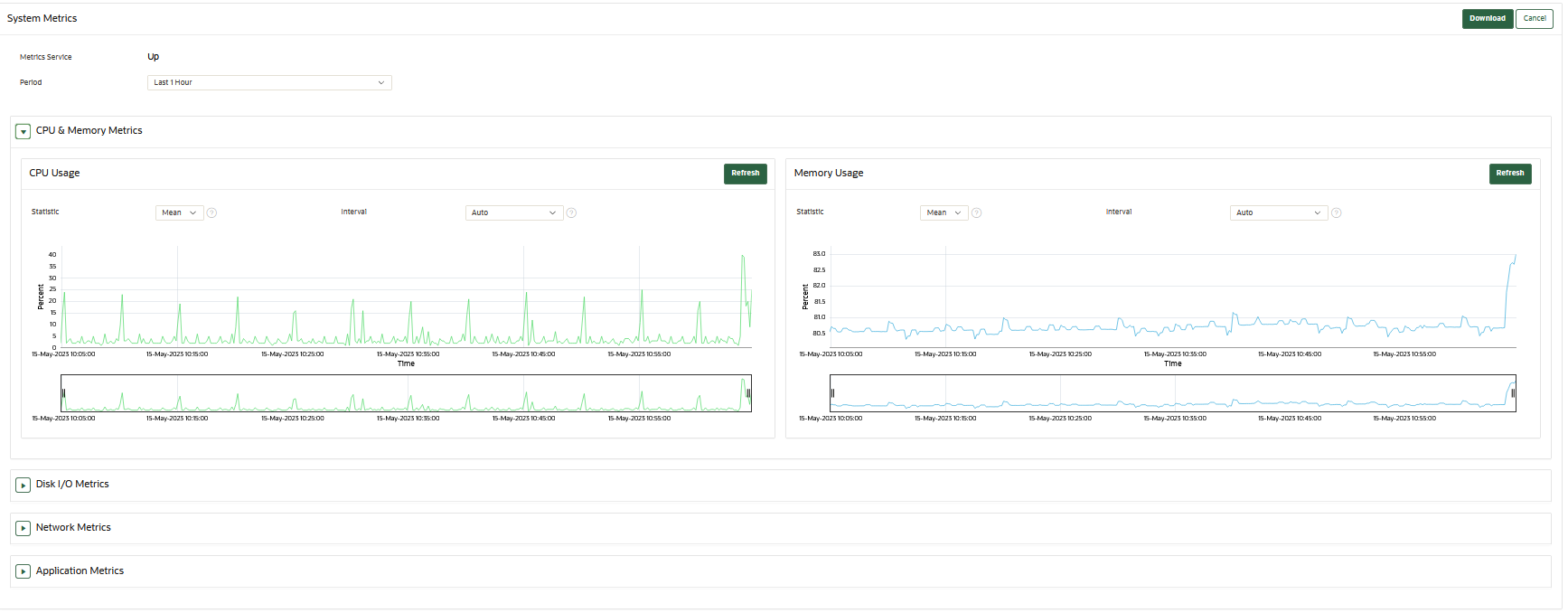
22.1.5 Monitoring System Metrics
You can use the System Metrics Monitoring feature to view and collect data for key system resource usage including CPU and Memory Usage in Oracle Key Vault.
- About Capturing System Metrics
The System Metrics Monitoring feature provide resource monitoring capabilities using the Oracle Key Vault management console. - Viewing System Metrics
You can use the Oracle Key Vault management console to view and download the system monitoring data.
Parent topic: Managing System Monitoring
22.1.5.1 About Capturing System Metrics
The System Metrics Monitoring feature provide resource monitoring capabilities using the Oracle Key Vault management console.
Oracle Key Vault periodically collects CPU and Memory Usage, Disk I/O, Network and Application Metrics. You can view and collect system metrics data using the Oracle Key Vault management console. The Oracle Key Vault System Metrics Monitoring eliminates the need to first login to Oracle Key Vault server and then monitor the system manually.
Parent topic: Monitoring System Metrics
22.1.5.2 Viewing System Metrics
You can use the Oracle Key Vault management console to view and download the system monitoring data.
Parent topic: Monitoring System Metrics
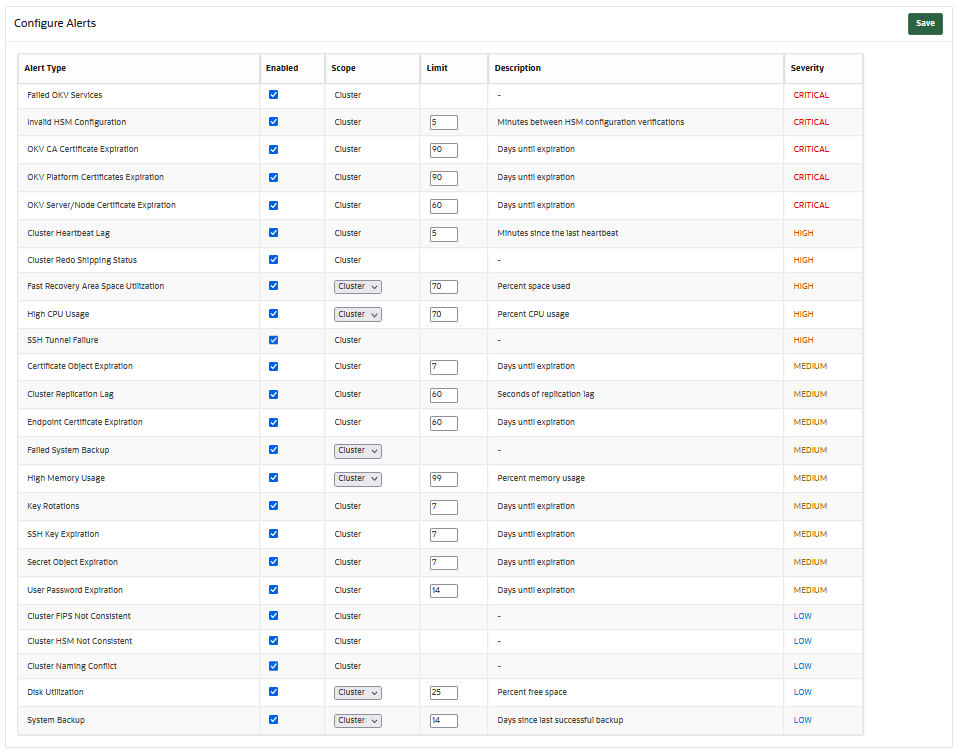
22.2 Configuring Oracle Key Vault Alerts
You can select the type of alerts that you want to see in the Oracle Key Vault dashboard.
- About Configuring Alerts
System administrators can configure alerts from the Oracle Key Vault dashboard, but all users can see alerts for the security objects to which they have access. - Configuring Alerts
You can configure alerts in the Reports page of the Oracle Key Vault management console. - Viewing Open Alerts
Users can view alerts depending on their privileges.
Parent topic: Monitoring and Auditing Oracle Key Vault
22.2.1 About Configuring Alerts
System administrators can configure alerts from the Oracle Key Vault dashboard, but all users can see alerts for the security objects to which they have access.
Email notifications must be enabled for users to receive alerts.
The Oracle Key Vault dashboard is the first page you see on logging into the management console. You can navigate to this page by clicking the Home tab. All users can see the alerts on security objects they have access to, but only users with the System Administrator role can configure alerts.
Oracle Key Vault offers several types of alerts that you can configure with appropriate thresholds according to your requirements. The alert types that appear are based on the type of environment that you are using: standalone, primary-standby, or multi-master cluster. You can also configure alerts for an HSM-enabled Oracle Key Vault server.
Oracle Key Vault alerts are categorized to one of the severity levels: CRITICAL, HIGH, MEDIUM, and LOW. You should resolve the higher severity alerts first.
- Fast Recovery Area Space Utilization
- High CPU Usage
- Failed System Backup
- High Memory Usage
- Disk Utilization
- System Backup
You can configure the following alerts, which are listed in ascending order:
Table 22-3 Available Alerts
| Alert Type | Severity | Environment | Multi-master Cluster Applicability | Purpose of Alert | When Alert Is Deleted |
|---|---|---|---|---|---|
|
|
HIGH |
Standalone, primary-standby, and multi-master cluster environments |
Cluster-wide |
Raised when a certificate object's deactivation date is within the threshold value (default 7 days). This alert is raised only if the certificate object is
in the When an expiration alert is within its threshold, an email notification is sent once every 24 hours until the certificate object expires. |
Deleted if the certificate object is no longer expiring within the threshold value as a result of changes to either object's deactivation date or the configured threshold value. This alert is also deleted when a certificate object is revoked or destroyed. |
|
|
MEDIUM |
Multi-master cluster only |
Cluster-wide |
Raised when at least one, but not all,
|
Deleted when all cluster nodes are in FIPS mode or all nodes are not in FIPS mode |
|
|
HIGH |
Multi-master cluster only |
Node specific |
Raised when a node has not received a heartbeat from
another |
Deleted when a node has once again received a heartbeat from the other node in the configured threshold period, as long as the node had received a heartbeat from the other node within the last Maximum Disable Node Duration period of time. This alert is also deleted when a node involved has been deleted from the cluster. |
|
|
MEDIUM |
Multi-master cluster only |
Cluster-wide |
Raised when at least one, but not all,
|
Deleted when all nodes are HSM-enabled or all nodes are not HSM-enabled |
|
|
LOW |
Multi-master cluster only |
Cluster-wide |
Raised when a naming conflict has been automatically resolved by Oracle Key Vault |
Deleted when the object is deleted or renamed, or has had the new name explicitly accepted |
|
|
HIGH |
Multi-master cluster only |
Node specific |
Raised when a read-write node is unable to ship redo to its read-write peer, and as a result, is in read-only restricted mode. In addition to redo-shipping inactive status information, the alert indicates that the node in the cluster is operating in read-only mode. |
Deleted when a read-write node is once again able to ship redo to its read-write peer, or when the node is deleted. The email notification states that the redo-shipping status is back up and the node in the cluster is no longer operating in read-only mode. |
|
|
HIGH |
Multi-master cluster only |
Node specific |
Raised when incoming replication lag is greater than the threshold value (default 60 seconds) |
Deleted when replication lag falls below the threshold value, or when any node in the replication link is deleted. |
|
|
MEDIUM |
Standalone, primary-standby, and multi-master cluster environments |
Node specific |
Raised when the free disk space percentage of the
|
Deleted when free disk space is once again higher than the threshold |
|
|
HIGH |
Standalone, primary-standby, and multi-master cluster environments |
Cluster-wide |
Raised when an endpoint's certificate is expiring within the threshold value (default 30 days). When an expiration alert is within its threshold, an email notification is sent once every 24 hours until the endpoint's certificate expires. |
Deleted when the endpoint's certificate is no longer expiring within the threshold value or when the endpoint is deleted |
|
|
MEDIUM |
Standalone, primary-standby, and multi-master cluster environments |
Node specific |
Raised when the last backup did not complete successfully |
Deleted when the most recent backup completed successfully |
|
|
CRITICAL |
Standalone, primary-standby, and multi-master cluster environments |
Node Specific |
Raised when DB, KMIP, REST, Email, Cluster, or Audit Vault service stops because of a failure. |
Deleted when all of the failed services start running successfully. |
|
|
HIGH |
Standalone, primary-standby, and multi-master cluster environments |
Node specific |
Raised when Fast Recovery Area Space utilization of Oracle Key Vault's embedded database exceeds the configured threshold value (default 70 percent). To remedy this problem, try the following: Reduce the Maximum Disable Node Duration setting of the cluster node. Minimize the duration when peer node is not available. Consider deleting the node from the cluster and adding it back later. |
Deleted when Fast Recovery Area Space utilization of Oracle Key Vault's embedded database is once again within the configured threshold |
High CPU Usage |
HIGH |
Standalone, primary-standby, and multi-master cluster environments |
Node Specific |
Raised when average memory usage is greater than the threshold in last 5 minutes. Default value of threshold is 99%. Setting a threshold above 90% takes memory swapping into consideration along with memory usage for raising an alert. |
Deleted when 24 hours are passed since the first alert is raised and the CPU utilization is less than the threshold in last 5 minutes. |
|
|
HIGH |
Standalone, primary-standby, and multi-master cluster environments |
Node Specific |
Raised when average memory usage is greater than the threshold in last 5 minutes. Default value of threshold is 99%. |
Deleted when 24 hours are passed since the first alert is raised and the memory usage is less than the threshold in the last 5 minutes. |
|
|
CRITICAL |
Standalone, primary-standby, and multi-master cluster environments |
Node specific |
Raised when there is an error in the HSM configuration (checked by default every 5 minutes) |
Deleted when there is no longer an error in the HSM configuration |
|
|
HIGH |
Standalone, primary-standby, and multi-master cluster environments |
Cluster-wide |
Raised when a key's deactivation date is within the threshold value (default 7 days) This alert is raised only if the key object is in the
When an expiration alert is within its threshold, an email notification is sent once every 24 hours until the certificate object expires. |
Deleted if the key object is no longer expiring within the threshold value as a result of changes to either object's deactivation date or the configured threshold value. This alert is also deleted when a key object is revoked or destroyed. |
OKV CA Certificate Expiration |
CRITICAL |
Standalone, primary-standby, and multi-master cluster environments |
Node specific |
Raised when the Oracle Key Vault CA certificate is expiring within the threshold value (default 90 days). When an expiration alert is within its threshold, an email notification is sent once every 24 hours until the CA certificate expires.Be aware that if the CA certificate expires, then endpoints will no longer be able to communicate with Oracle Key Vault. This will result in downtime. |
Deleted when the CA certificate is no longer expiring within the threshold value |
OKV Server/Node Certificate
Expiration |
CRITICAL |
Standalone, primary-standby, and multi-master cluster environments |
Node specific |
|
Deleted when the server or node certificate is no longer expiring within the threshold value. |
OKV Platform Certificates
Expiration |
CRITICAL |
Standalone, primary-standby, and multi-master cluster environments |
Node specific |
Raised when the Oracle Key Vault platform certificates
are expiring within the threshold value (default 90 days). When an
expiration alert is within its threshold, an email notification is
sent once every 24 hours. The platform certificates are used when a
new node is added to the cluster. The node whose platform
certificates have expired cannot add any new node. Platform
certificates are also used when shipping redo between read/write
nodes of a cluster. The expired platform certificates may cause the
redo shipping to fail resulting in read/write nodes of a cluster to
go in read-only restricted mode.
Note: Although expired platform certificates may impact communication between a node and its read/write peer, they do not impact endpoint communications with Oracle Key Vault. |
Deleted when the platform certificates are no longer expiring within the threshold value. |
|
|
Standalone, primary-standby, and multi-master cluster environments |
Node specific |
Raised when the Oracle Key Vault server certificate is expiring within the threshold value (default 90 days). When an expiration alert is within its threshold, an email notification is sent once every 24 hours until the certificate expires. Be aware that if the server certificate expires, then endpoints will no longer be able to communicate with the Oracle Key Vault server. This will result in downtime. |
Deleted when the server certificate is no longer expiring within the threshold value |
|
|
|
HIGH |
Primary-standby only |
- |
Raised when the Oracle Data Guard Broker status is not
|
Deleted when the broker status is once again
|
|
|
MEDIUM |
Primary-standby only |
- |
Raised when the fast-start failover status is not
|
Deleted when the fast-start failover status is once again
|
|
|
HIGH |
Primary-standby only |
- |
Raised when the switchover status is |
Deleted when the switchover status is no longer
|
|
|
HIGH |
Primary-standby only |
- |
Raised when in primary-standby environment and the primary is running in read-only restricted mode |
Deleted when the primary is no longer in read-only restricted mode or when Oracle Key Vault is no longer in a primary-standby configuration |
|
|
LOW |
Primary-standby only |
- |
Raised when there is a role change |
Deleted when Oracle Key Vault is no longer in a primary-standby configuration |
|
|
HIGH |
Standalone, primary-standby, and multi-master cluster environments |
Cluster-wide |
Raised when a secret object's deactivation date is within
the threshold value (default 7 days). This alert is raised only if
the object is in the When an expiration alert is within its threshold, an email notification is sent once every 24 hours until the secret object expires. |
Deleted if the secret object is no longer expiring within the threshold value as a result of changes to either object's deactivation date or the configured threshold value. This alert is also deleted when a secret object is revoked or destroyed. |
|
|
HIGH |
Standalone, primary-standby, and multi-master cluster environments |
Node specific |
Raised when an SSH tunnel is not available |
Deleted when the SSH tunnel is once again available or when the SSH tunnel is deleted |
|
|
MEDIUM |
Standalone, primary-standby, and multi-master cluster environments |
Node specific |
Raised when the last successful backup is over the threshold value (default 14 days) |
Deleted when the last successful backup was within the threshold value |
|
|
MEDIUM |
Standalone, primary-standby, and multi-master cluster environments |
Cluster-wide |
Raised when a user's password expires within the threshold value (default 14 days). When an expiration alert is within its threshold, an email notification is sent once every 24 hours until the password expires. If the user password expires, user cannot login and Administrative tasks cannot be performed. |
Deleted when a user's password no longer expire within the threshold value, or when the user is deleted |
22.2.2 Configuring Alerts
You can configure alerts in the Reports page of the Oracle Key Vault management console.
- Guidance for Configuring Alerts
You must consider the following guidelines before configuring the Alerts.
Related Topics
Parent topic: Configuring Oracle Key Vault Alerts
22.2.2.1 Guidance for Configuring Alerts
You must consider the following guidelines before configuring the Alerts.
For the alerts which support a configurable alert scope, following is the behavior when either the Cluster or the Node scope is selected.
- On changing the alert configuration, the changes are applied to all nodes which have the scope set to Cluster.
- When an alert is disabled, all previously generated alerts, for selected alert, are deleted from all nodes which have the scope set to Cluster.
- On changing the alert configuration, the changes are applied to the current node only.
- When an alert is generated on a node where the Node scope is set, the alert message has a post fix "node configuration in effect".
- When an alert is disabled, the previously generated alert, for selected alert, is deleted from the current node.
For the alerts which support a configurable alert scope, following is the behavior when the scope is changed from Cluster to Node or vice versa.
- When the selected scope for an alert is changed from Cluster to Node or vice versa, then the previously generated alert, for selected alert, is deleted from the current node.
- When the selected scope for an alert is changed from Node to Cluster, then the node specific alert configuration is deleted.
- When the selected scope for an alert is changed from Cluster to Node, the Enabled column and Limit column, for selected alert, on Configure Alerts page get populated with corresponding values from cluster alert configuration.
Parent topic: Configuring Alerts
22.2.3 Viewing Open Alerts
Users can view alerts depending on their privileges.
- Log in to the Oracle Key Vault management console as a user who has the System Administrator role.
- Access the Alerts page by using one of the following methods:
- Select the System tab, then Settings, and in the Monitoring and Alerts area, click Alerts.
- Select the Reports tab, and then select Alerts from the left navigation bar.
- On the Home page, expand Alerts at the top of the page, and then click All Alerts.
The Home page is also a convenient way to go immediately to how to solve a problem that an alert raises. Under Alerts, click Show Details, and then in the listing of alert types, click the appropriate link. For example, alerts describing upcoming key expirations will take you to the Alerts configuration page, where only alerts for key rotations are displayed. From there, you can examine the details of keys that are expiring.
The Alerts page appears, displaying all the unresolved alerts. Alerts are listed in the order of their severity and severity based color code scheme. The alerts with higher severity should be resolved first.
When you resolve the issue stated in the alert message, the alerts are automatically removed. To delete an alert message, select it and then click Delete. If the issue that caused the alert still exists, then the alert will be regenerated and appear again in this list.
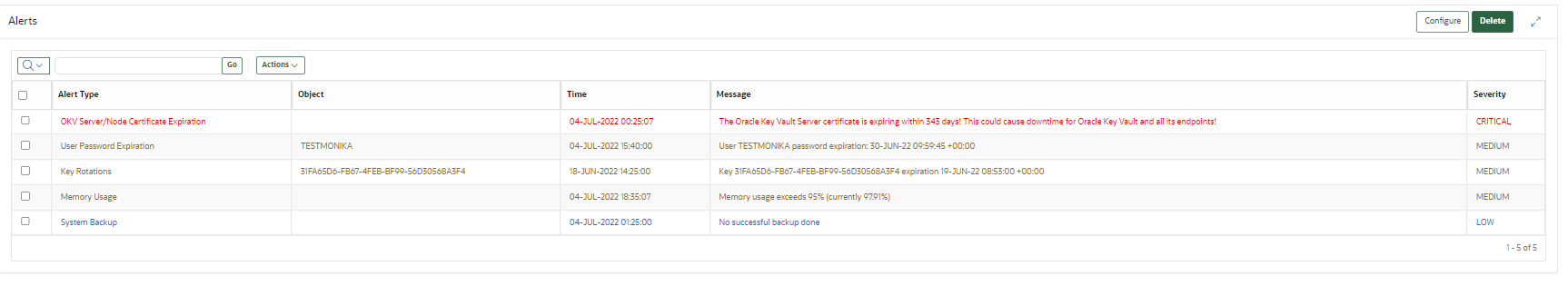
Description of the illustration 21.5_view_alerts.png
Oracle Key Vault sends all system alerts to the syslog. The following is an example of a system alert in syslog:
Mar 29 18:36:29 okv080027361e7e logger[13171]: No successful backup done for 4 day(s)
The following table lists the conditions that trigger alerts, and the accompanying system alert message:
| Condition | System Alert Message |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
The label |
|
|
Any of the following messages:
|
|
|
|
|
|
When Cluster scope is set:
|
|
|
|
Failed OKV Services |
service_name service is failed or
service_name1, service_name2 services are
failed. |
|
|
When Cluster scope is set:
When Node scope is set:
|
|
|
When Cluster scope is set:
When Node scope is set:
|
High CPU usage |
When Cluster scope is set:
When Node scope is set:
|
High Memory Usage |
When Cluster scope is set:
When Node scope is set:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
When Cluster scope is set:
When Node scope is set:
|
|
|
|
Parent topic: Configuring Oracle Key Vault Alerts
22.3 Managing System Auditing
Auditing entails tasks such as capturing audit records in a syslog file or downloading the audit records to a local file.
- About Auditing in Oracle Key Vault
Oracle Key Vault records and time-stamps all endpoint and user activity. - Oracle Key Vault Audit Trail
The Oracle Key Vault audit trail captures information about activities that are performed in Oracle Key Vault, such as the name of an action and who performed it. - Viewing Audit Records
To view audit records, access the Oracle Key Vault management console Audit Trail page. - Exporting and Deleting Audit Records Manually
Oracle Key Vault audit records are stored in a.csvfile. - Deleting Audit Records Automatically
You can configure Oracle Key Vault to automatically delete or purge the audit records that are older than the specified retention period. - Oracle Key Vault Audit Event IDs
Oracle Key Vault Audit Event ID identifies the audit operation type. - Configuring Oracle Key Vault with Oracle Audit Vault
A user who has the Audit Manager role can configure Oracle Key Vault to send audit records to Oracle Audit Vault for centralized audit reporting and alerting.
Parent topic: Monitoring and Auditing Oracle Key Vault
22.3.1 About Auditing in Oracle Key Vault
Oracle Key Vault records and time-stamps all endpoint and user activity.
The audit records include endpoint groups and user groups, from endpoint enrollment and user password reset, to the management of keys and wallets, and changes to system settings and SNMP credentials. The audit trail captures details on who initiated which action, with what keys and tokens, and the result of the action. In addition, it records the success or failure of each action.
Only a user who has the Audit Manager role can manage the audit trail for Oracle Key Vault activity. Each user can see audit records of the objects that the user can access.
Auditing in Oracle Key Vault is enabled by default.
A user with the Audit Manager role can see and manage all the audit records. Other users can see only those audit records that pertain to security objects that they have created, or have been granted access to.
The audit manager can export audit records to view system activity off line. After exporting the records, the audit manager can delete them from the system to free up resources.
Related Topics
Parent topic: Managing System Auditing
22.3.2 Oracle Key Vault Audit Trail
The Oracle Key Vault audit trail captures information about activities that are performed in Oracle Key Vault, such as the name of an action and who performed it.
The following lists the contents of the Oracle Key Vault audit trail.
Table 22-4 Oracle Key Vault Audit Trail
| Column Name | Description |
|---|---|
Event ID |
ID to identify each audit operation type uniquely. |
|
|
The IP address of the client host or the IP address of the proxy server between the client and the Oracle Key Vault server that is making its IP address available to Oracle Key Vault |
|
|
ID of the Oracle Key Vault cluster node on which the operation was performed |
|
|
IP address of the Oracle Key Vault cluster node on which the operation was performed |
|
|
Name of the Oracle Key Vault cluster node on which the operation was performed |
|
|
Captures the name of object on which the operation is performed |
|
|
Type of object on which the operation is performed
(for example, |
|
|
Name of the operation performed |
|
|
Result of the operation indicating whether it was successful or failure |
|
|
Captures the name of entity that performed the operation |
|
|
Type of entity, |
|
|
Timestamp of the operation |
- Enabling Auditing and Configuring Syslog to Store Audit Records
You can enable or disable auditing and then configure the Oracle Key Vault syslog to store audit records if the System Administrator has enabled this functionality.
Parent topic: Managing System Auditing
22.3.2.1 Enabling Auditing and Configuring Syslog to Store Audit Records
You can enable or disable auditing and then configure the Oracle Key Vault syslog to store audit records if the System Administrator has enabled this functionality.
Parent topic: Oracle Key Vault Audit Trail
22.3.3 Viewing Audit Records
To view audit records, access the Oracle Key Vault management console Audit Trail page.
Parent topic: Managing System Auditing
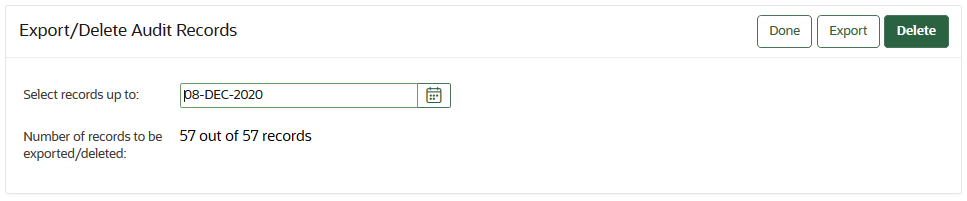
22.3.4 Exporting and Deleting Audit Records Manually
Oracle Key Vault audit records are stored in a .csv file.
.csv file that can be downloaded to the user's local system. The .csv file contains the same details found in the audit trail on the Reports page. The timestamp in the .csv file reflects the time zone of the particular Oracle Key Vault server whose records were exported. After you export the records, you can delete them from the Oracle Key Vault server to free up space.
Parent topic: Managing System Auditing
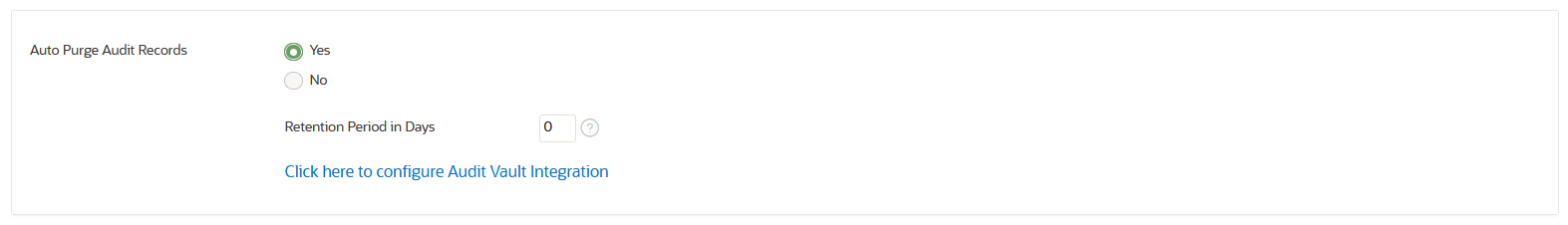
22.3.5 Deleting Audit Records Automatically
You can configure Oracle Key Vault to automatically delete or purge the audit records that are older than the specified retention period.
Related Topics
Parent topic: Managing System Auditing
22.3.6 Oracle Key Vault Audit Event IDs
Oracle Key Vault Audit Event ID identifies the audit operation type.
The Event ID in Oracle Key Vault audit records represents a stable identity that is uniquely associated with an audit operation type.
Table 22-5 Oracle Key Vault Audit Event IDs
| Event ID | Operation |
|---|---|
| 1000 | Login Attempted |
| 1001 | Login Attempted and Succeeded |
| 1002 | Logout |
| 1003 | Logout on Console Timeout |
| 1100 | System Recovery: Initiate Recovery Passphrase Change |
| 1101 | System Recovery: Reset Recovery Passphrase Change |
| 1102 | System Recovery: Change Recovery Passphrase |
| 1103 | System Recovery: Reset Administrative Accounts |
| 1104 | System Recovery: Manage Administrator |
| 1105 | System Recovery: Modify User Account Profile Parameters |
| 1106 | System Recovery: Reset User Account Profile Parameters |
| 1107 | System Recovery: Modify Enforce Separation of Administrator Roles Parameter |
| 1200 | Add User |
| 1201 | Delete User |
| 1202 | Modify User Attributes |
| 1203 | Reset User Password |
| 1204 | Change User Password |
| 1205 | Password Email Sent |
| 1300 | Add Endpoint |
| 1301 | Delete Endpoint |
| 1302 | Modify Endpoint Attributes |
| 1303 | Enroll Endpoint |
| 1304 | Enrollment Token Email Sent |
| 1305 | Get Enrollment Token |
| 1306 | Reenroll Endpoint |
| 1307 | Suspend Endpoint |
| 1308 | Resume Endpoint |
| 1309 | Rotate Endpoint Certificate |
| 1310 | Endpoint Certificate Rotation Initiated |
| 1311 | Endpoint Certificate Rotation Completed |
| 1312 | Modify Endpoint Configuration Parameters |
| 1313 | Reset Endpoint Configuration Parameters |
| 1314 | Clear Endpoint Configuration Parameters |
| 1315 | Modify Endpoint Settings for Keys & Secrets |
| 1316 | Reset Endpoint Settings for Keys & Secrets |
| 1317 | Clear Endpoint Settings for Keys & Secrets |
| 1400 | Modify Endpoint Self Enrollment Setting |
| 1401 | Modify Global Endpoint Configuration Parameters |
| 1402 | Reset Global Endpoint Configuration Parameters |
| 1403 | Modify Global Endpoint Settings for Keys & Secrets |
| 1404 | Reset Global Endpoint Settings for Keys & Secrets |
| 2000 | Add User Group |
| 2001 | Delete User Group |
| 2002 | Modify User Group Attributes |
| 2003 | Add User Group Member(s) |
| 2004 | Drop User Group Member(s) |
| 2005 | Add User Group Membership |
| 2006 | Drop User Group Membership |
| 2100 | Add Endpoint Group |
| 2101 | Delete Endpoint Group |
| 2102 | Modify Endpoint Group Attributes |
| 2103 | Add Endpoint Group Member(s) |
| 2104 | Drop Endpoint Group Member(s) |
| 2105 | Add Endpoint Group Membership |
| 2106 | Drop Endpoint Group Membership |
| 2200 | Create Wallet |
| 2201 | Delete Wallet |
| 2202 | Modify Wallet |
| 2203 | Add Wallet Membership |
| 2204 | Drop Wallet Membership |
| 2205 | Add Wallet Member(s) |
| 2206 | Remove Wallet Member(s) |
| 2207 | Add Access Mapping |
| 2208 | Delete Access Mapping |
| 2209 | Modify Access Mapping |
| 2210 | Assign Default Wallet |
| 2211 | Grant Endpoint Management Privilege |
| 2212 | Revoke Endpoint Management Privilege |
| 2213 | Grant Endpoint Group Management Privilege |
| 2214 | Revoke Endpoint Group Management Privilege |
| 3000 | Convert Server to First Cluster Node |
| 3001 | Convert Server to Candidate Node |
| 3002 | Add Candidate Node |
| 3003 | Abort Conversion of Candidate Node |
| 3004 | Abort Candidate Node |
| 3005 | Add Node to Cluster |
| 3006 | Abort Addition of Node to Cluster |
| 3007 | Finish Pairing on Candidate Node |
| 3008 | Initiate Delete Node |
| 3009 | Initiate Force Delete Node |
| 3010 | Cleanup Deleted Node |
| 3011 | Finish Delete Node |
| 3012 | Initiate Enable Node |
| 3013 | Finish Enable Node |
| 3014 | Initiate Disable Node |
| 3015 | Finish Disable Node |
| 3016 | Cancel Disable Node |
| 3017 | Edit Cluster Subgroup |
| 3018 | Start Replication for Node |
| 3019 | Stop Replication for Node |
| 3020 | Start Cluster Services |
| 3021 | Stop Cluster Services |
| 3022 | User Name Conflict Resolution |
| 3023 | User Group Name Conflict Resolution |
| 3024 | Endpoint Name Conflict Resolution |
| 3025 | Endpoint Group Name Conflict Resolution |
| 3026 | Wallet Name Conflict Resolution |
| 3027 | KMIP Attribute Name Conflict Resolution |
| 3900 | Initiate Primary-Standby Pairing |
| 3901 | Initiate Primary-Standby Unpairing |
| 3902 | Primary-Standby Role Switch |
| 4000 | Discover Versions |
| 4001 | Query |
| 4002 | Create |
| 4003 | Create Key Pair |
| 4004 | Register |
| 4005 | Delete |
| 4006 | Add Attribute(s) |
| 4007 | Delete Attribute(s) |
| 4008 | Modify Attribute(s) |
| 4009 | Get Attribute(s) |
| 4010 | Get Attribute List |
| 4011 | Check Object Status |
| 4012 | Activate |
| 4013 | Revoke |
| 4014 | Destroy |
| 4015 | Check |
| 4016 | Locate |
| 4017 | Get |
| 4018 | Rekey |
| 4019 | Store Endpoint Metadata |
| 4020 | Encrypt |
| 4021 | Decrypt |
| 4022 | Sign |
| 4023 | Signature Verify |
| 5000 | Power Off |
| 5001 | Reboot System |
| 5002 | Rebooting the Server Operating with FIPS Mode Enabled |
| 5003 | Rebooting the Server Operating with FIPS Mode Disabled |
| 5100 | Modify Trace Levels |
| 5101 | Download Diagnostics |
| 5200 | Configure Alerts |
| 5201 | Delete Alert(s) |
| 5202 | Critical Alert(s) Ignored |
| 5203 | Critical Alert(s) Viewed |
| 5300 | Modify Monitoring Settings |
| 5301 | Modify Monitoring Settings for Cluster |
| 5302 | Clear Monitoring Settings for Node |
| 5303 | Modify SNMP Credentials |
| 5400 | Enable Auditing |
| 5401 | Disable Auditing |
| 5402 | Enable Auditing in Cluster |
| 5403 | Disable Auditing in Cluster |
| 5404 | Modify Audit Settings |
| 5405 | Modify Audit Settings for Cluster |
| 5406 | Clear Audit Settings for Node |
| 5407 | Enable Audit Replication |
| 5408 | Disable Audit Replication |
| 5409 | Enable Audit Replication in Cluster |
| 5410 | Disable Audit Replication in Cluster |
| 5411 | Clear Audit Replication Settings for Node |
| 5412 | Start Sending Audit Records to SYSLOG |
| 5413 | Stop Sending Audit Records to SYSLOG |
| 5414 | Start Sending Audit Records to SYSLOG in Cluster |
| 5415 | Stop Sending Audit Records to SYSLOG in Cluster |
| 5416 | Clear Send Audit Records to SYSLOG Settings for Node |
| 5417 | Enable Audit Records Auto Purge |
| 5418 | Disable Audit Records Auto Purge |
| 5419 | Clear Audit Records Auto Purge Settings for Node |
| 5420 | Delete Audit Records |
| 5600 | Modify System Settings |
| 5601 | Modify Network Details |
| 5602 | Modify DNS Settings |
| 5603 | Modify DNS Settings for Cluster |
| 5604 | Clear DNS Settings for Node |
| 5605 | Modify System Time Settings |
| 5606 | Modify NTP Settings |
| 5607 | Modify NTP Settings for Cluster |
| 5608 | Clear NTP Settings for Node |
| 5609 | Modify Web Access |
| 5610 | Modify SSH Access |
| 5611 | Modify Management Console Timeout Settings |
| 5612 | Enable FIPS Mode |
| 5613 | Disable FIPS Mode |
| 5614 | Enable RESTful Services |
| 5615 | Disable RESTful Services |
| 5616 | Modify Syslog Settings |
| 5617 | Modify Syslog Settings for Cluster |
| 5618 | Clear Syslog Settings for Node |
| 5619 | Configure SMTP |
| 5620 | Unconfigure SMTP |
| 5621 | Modify SMTP Settings |
| 5622 | Modify Maximum Disable Node Duration Settings for Cluster |
| 5623 | Add SSH Tunnel |
| 5624 | Delete SSH Tunnel |
| 5625 | Enable SSH Tunnel |
| 5626 | Disable SSH Tunnel |
| 5627 | Tunnel Cleanup on Failover |
| 5628 | Delete Cloud IP Reservation |
| 6000 | Restore |
| 6001 | Create Backup |
| 6002 | Delete Backup |
| 6003 | Edit Backup |
| 6004 | Backup Initiated |
| 6005 | Backup Completed |
| 6006 | Pause Backup |
| 6007 | Resume Backup |
| 6008 | Purge Backup |
| 6009 | Create Backup Destination |
| 6010 | Delete Backup Destination |
| 6011 | Edit Backup Destination |
| 6012 | Reset Backup Host Public Key |
| 6013 | Create Backup Destination Policy |
| 6014 | Delete Backup Destination Policy |
| 6015 | Edit Backup Destination Policy |
| 6016 | Suspend Backup Destination Policy |
| 6017 | Resume Backup Destination Policy |
| 6100 | Generate New Server Certificate |
| 6101 | Generate New Node Certificate |
| 6102 | Modify Server Certificate Details |
| 6103 | Modify Server Certificate Alternate Name and IP Address Details |
| 6104 | Modify CA Certificate Details |
| 6105 | Generate and Download Intermediate CA Certificate Request |
| 6106 | Abort Generation of Intermediate CA Certificate |
| 6107 | Download Intermediate CA Certificate Request |
| 6108 | Upload Intermediate CA Certificate |
| 6109 | Upload Intermediate CA Trust Chain |
| 6110 | Generate New CA Certificate |
| 6111 | Unpack New CA Certificate Bundle |
| 6112 | Abort CA Certificate Rotation |
| 6113 | Activate New CA Certificate |
| 6114 | Update Endpoint Certificate Rotation Window Size |
| 6115 | Update Cluster Subgroup Order |
| 6116 | Remove Cluster Subgroup Order |
| 6117 | Update Endpoint Group Order |
| 6118 | Check Expired CA Certificate Rotation State |
| 6119 | Generate New CA Certificate for Manual Recovery |
| 6120 | Upload CA Certificate Bundle |
| 6121 | CA Certificate Rotation Manual Recovery Completed |
| 6122 | CA Certificate Rotation Manual Recovery Verified |
| 6123 | Abort CA Certificate Rotation Manual Recovery |
| 6180 | Generate Console Certificate |
| 6181 | Upload Console Certificate |
| 6182 | Remove Console Certificate |
| 6183 | Restore Console Certificate |
| 8000 | Add LDAP Configuration |
| 8001 | Delete LDAP Configuration |
| 8002 | Force Delete LDAP Configuration |
| 8003 | Test LDAP Configuration |
| 8004 | Edit LDAP Configuration |
| 8005 | Enable LDAP Configuration |
| 8006 | Disable LDAP Configuration |
| 8007 | Add LDAP Server |
| 8008 | Delete LDAP Server(s) |
| 8009 | Test LDAP Server |
| 8010 | Test LDAP Connections |
| 8011 | Add LDAP Group Access Mapping |
| 8012 | Delete LDAP Group Access Mapping |
| 8013 | Edit LDAP Group Access Mapping |
| 8014 | Remove User Group from LDAP Group Access Mapping |
| 8015 | Validate LDAP Group(s) for LDAP Configuration |
| 8016 | Validate LDAP User(s) for LDAP configuration |
| 8018 | Delete LDAP User |
| 8019 | Delete Stale LDAP User |
| 8020 | Modify LDAP User Attributes |
| 8021 | Download LDAP Log |
| 8100 | Add Single Sign-On Configuration |
| 8101 | Delete Single Sign-On Configuration |
| 8104 | Edit Single Sign-On Configuration |
| 8105 | Enable Single Sign-On Configuration |
| 8106 | Disable Single Sign-On Configuration |
| 8200 | Enable Audit Vault Integration |
| 8201 | Disable Audit Vault Integration |
| 8202 | Suspend Audit Vault Audit Record Collection |
| 8203 | Resume Audit Vault Audit Record Collection |
| 8300 | HSM Initialize |
| 8301 | HSM Set Credential |
| 8302 | HSM Create Bundle |
| 8303 | HSM Apply Bundle |
| 8304 | HSM Reverse Migrate |
Parent topic: Managing System Auditing
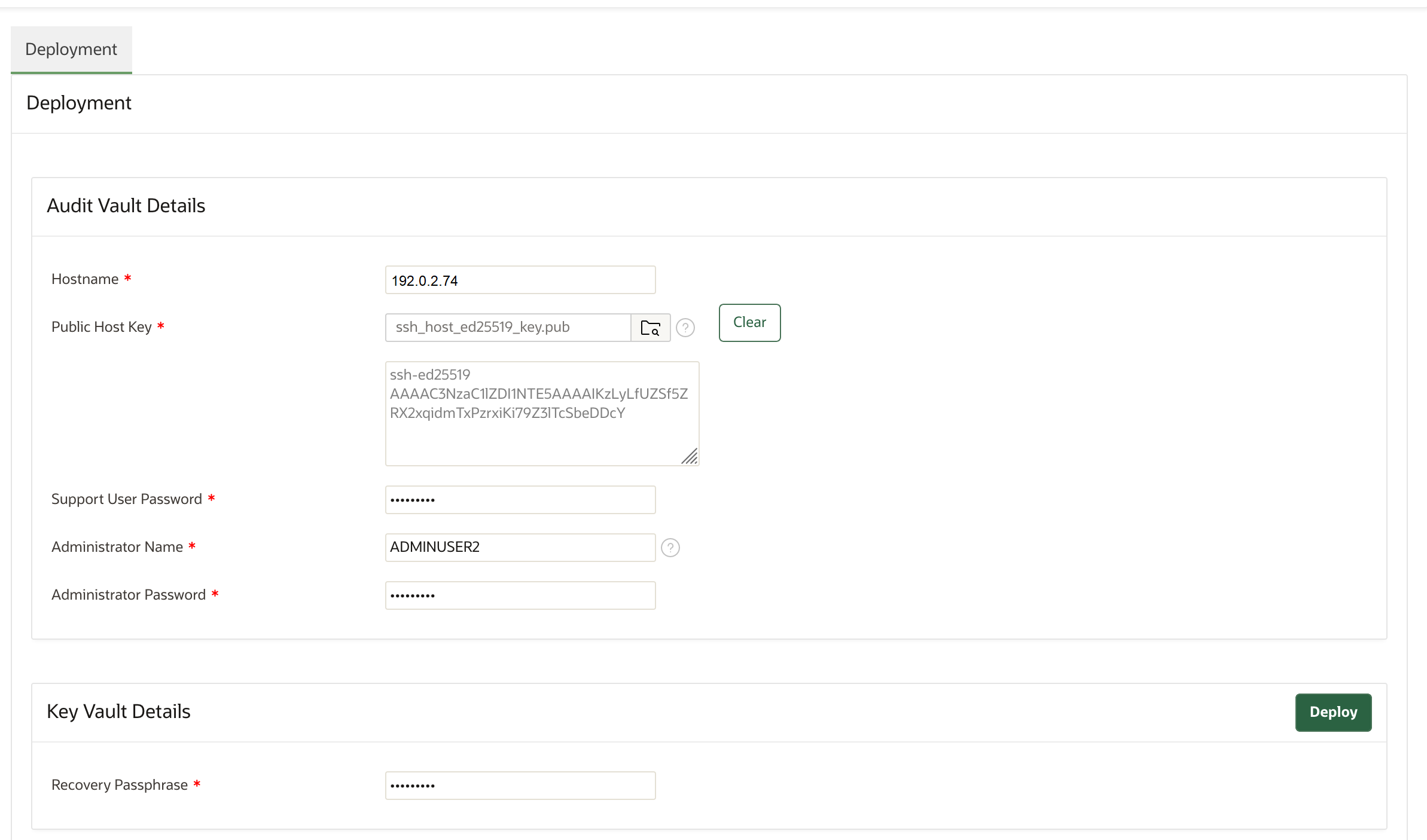
22.3.7 Configuring Oracle Key Vault with Oracle Audit Vault
A user who has the Audit Manager role can configure Oracle Key Vault to send audit records to Oracle Audit Vault for centralized audit reporting and alerting.
- Integrating Oracle Audit Vault with Oracle Key Vault
You can perform this integration from the Oracle Key Vault management console. - Viewing Oracle Key Vault Audit Data Collected by Oracle Audit Vault
You can use the Oracle Audit Vault Server console to view data that is collected by Oracle Key Vault and Oracle Audit Vault. - Suspending an Oracle Audit Vault Monitoring Operation
You can suspend an Oracle Audit Vault monitoring operation from the Oracle Key Vault management console. - Resuming an Oracle Audit Vault Monitoring Operation
You can resume a suspended Oracle Audit Vault monitoring operation from the Oracle Key Vault management console. - Deleting an Oracle Audit Vault Integration
You can delete an Oracle Audit Vault integration by using the Oracle Key Vault management console. - Guidance for Integrating Oracle Audit Vault in a Multi-Master Cluster or Primary-Standby Environment
You must follow special guidelines to integrate Oracle Audit Vault with Oracle Key Vault in a multi-master cluster or primary-standby environment.
Parent topic: Managing System Auditing
22.3.7.1 Integrating Oracle Audit Vault with Oracle Key Vault
You can perform this integration from the Oracle Key Vault management console.
- Step 1: Check the Environment
Before you begin the integration, you should ensure that the required components are all in place. - Step 2: Configure Oracle Key Vault as a Registered Host and a Secured Target with Oracle Audit Vault
A user who has the Audit Manager role must configure the Oracle Key Vault server as a secured target on the Oracle Audit Vault server. - Aborting an Oracle Audit Vault Integration
You can abort an Oracle Audit Vault integration by using the Oracle Key Vault management console.
Parent topic: Configuring Oracle Key Vault with Oracle Audit Vault
22.3.7.1.1 Step 1: Check the Environment
Before you begin the integration, you should ensure that the required components are all in place.
Parent topic: Integrating Oracle Audit Vault with Oracle Key Vault
22.3.7.1.2 Step 2: Configure Oracle Key Vault as a Registered Host and a Secured Target with Oracle Audit Vault
A user who has the Audit Manager role must configure the Oracle Key Vault server as a secured target on the Oracle Audit Vault server.
Parent topic: Integrating Oracle Audit Vault with Oracle Key Vault
22.3.7.1.3 Aborting an Oracle Audit Vault Integration
You can abort an Oracle Audit Vault integration by using the Oracle Key Vault management console.
Parent topic: Integrating Oracle Audit Vault with Oracle Key Vault
22.3.7.2 Viewing Oracle Key Vault Audit Data Collected by Oracle Audit Vault
You can use the Oracle Audit Vault Server console to view data that is collected by Oracle Key Vault and Oracle Audit Vault.
Parent topic: Configuring Oracle Key Vault with Oracle Audit Vault
22.3.7.3 Suspending an Oracle Audit Vault Monitoring Operation
You can suspend an Oracle Audit Vault monitoring operation from the Oracle Key Vault management console.
Parent topic: Configuring Oracle Key Vault with Oracle Audit Vault
22.3.7.4 Resuming an Oracle Audit Vault Monitoring Operation
You can resume a suspended Oracle Audit Vault monitoring operation from the Oracle Key Vault management console.
Parent topic: Configuring Oracle Key Vault with Oracle Audit Vault
22.3.7.5 Deleting an Oracle Audit Vault Integration
You can delete an Oracle Audit Vault integration by using the Oracle Key Vault management console.
Parent topic: Configuring Oracle Key Vault with Oracle Audit Vault
22.3.7.6 Guidance for Integrating Oracle Audit Vault in a Multi-Master Cluster or Primary-Standby Environment
You must follow special guidelines to integrate Oracle Audit Vault with Oracle Key Vault in a multi-master cluster or primary-standby environment.
Multi-Master Cluster Environments
- If Oracle Key Vault is configured to use multi-master clusters, then you must perform the Oracle Audit Vault integration individually on each node. Each node will send audit records that are generated only on that node to Oracle Audit Vault irrespective of whether audit record replication is enabled.
Primary-Standby Environments
- Perform the integration only on the primary server, not the standby server.
- If you must perform a switchover operation, then note the following:
- You must switch back to the primary server if you want to suspend, resume, or delete the integration. You do not need to perform additional steps.
- To integrate the new primary server with Oracle Audit Vault, optionally, ensure that you use the same Oracle Audit Vault host name and administrator credentials that were used in the old primary server.
- If you perform an unpair operation after performing a switchover operation, then you must perform a new Oracle Audit Vault integration with the new primary server.
- If you delete the new integration, then the old integration becomes non-functional. You must then delete this old integration by switching back to the old primary server.
- If a failover operation occurs and the original primary server is no longer available, then you must perform a new Oracle Audit Vault integration with the new primary server.
- However, if the original primary server is not lost and it is possible to bring back the original primary server as the new standby server, then you do not need to perform additional steps.
Parent topic: Configuring Oracle Key Vault with Oracle Audit Vault
22.4 Using Oracle Key Vault Reports
Oracle Key Vault collects statistical information on a range of activities that impact Key Vault operations.
- About Oracle Key Vault Reports
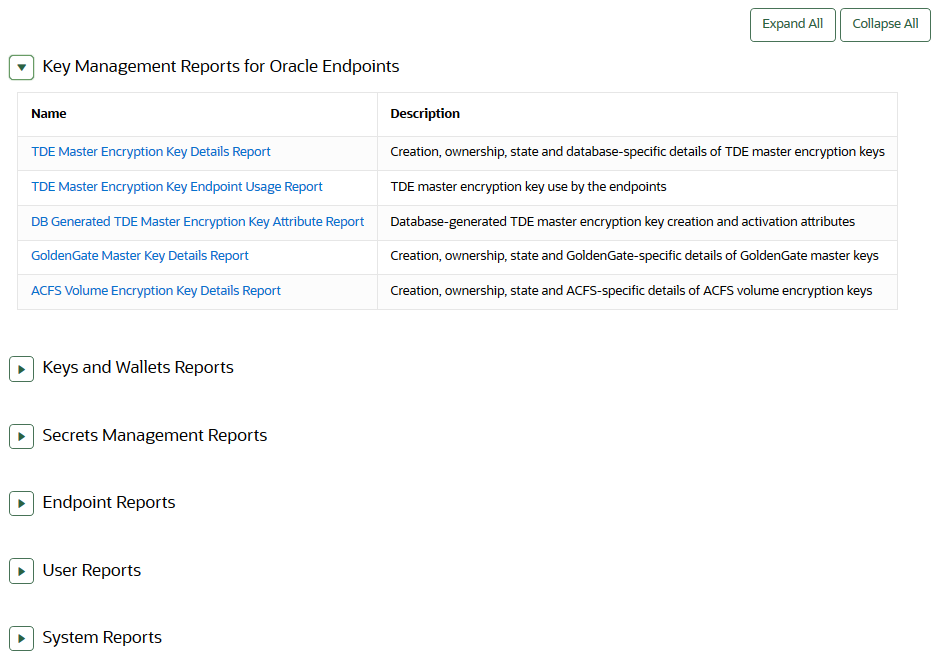
The reports cover system activity, certificate expiration, keys, passwords, entitlement status, extraction status, and metadata. - Viewing Key Management Reports for Oracle Endpoints
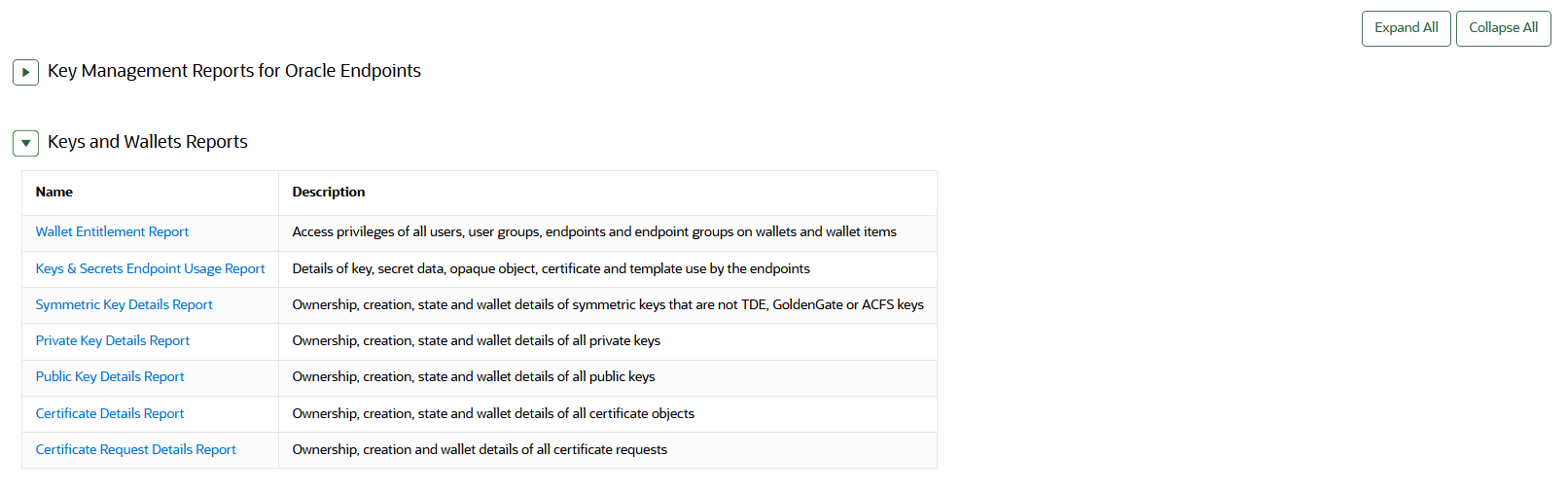
All users can view the key management reports for Oracle endpoints. - Viewing Keys and Wallets Reports
The keys and wallets reports require different privileges for viewing, depending on the report. - Viewing Secrets Management Reports
All users can view the secrets management reports. - Viewing SSH Reports
All users can view the SSH reports. - Viewing Endpoint Reports
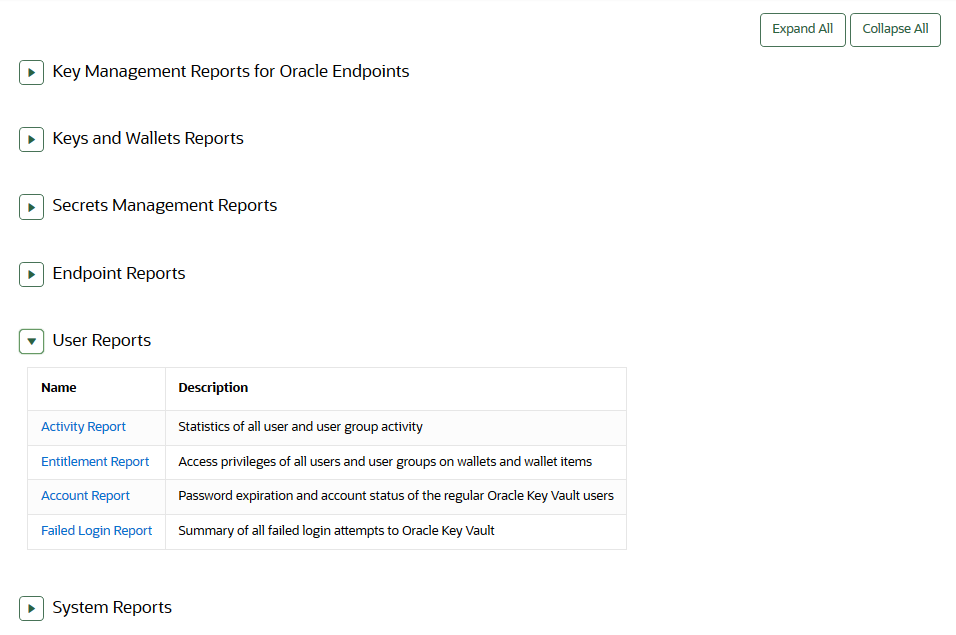
You must have the System Administrator role or the Audit Manager role to view the five categories of endpoint reports. - Viewing User Reports
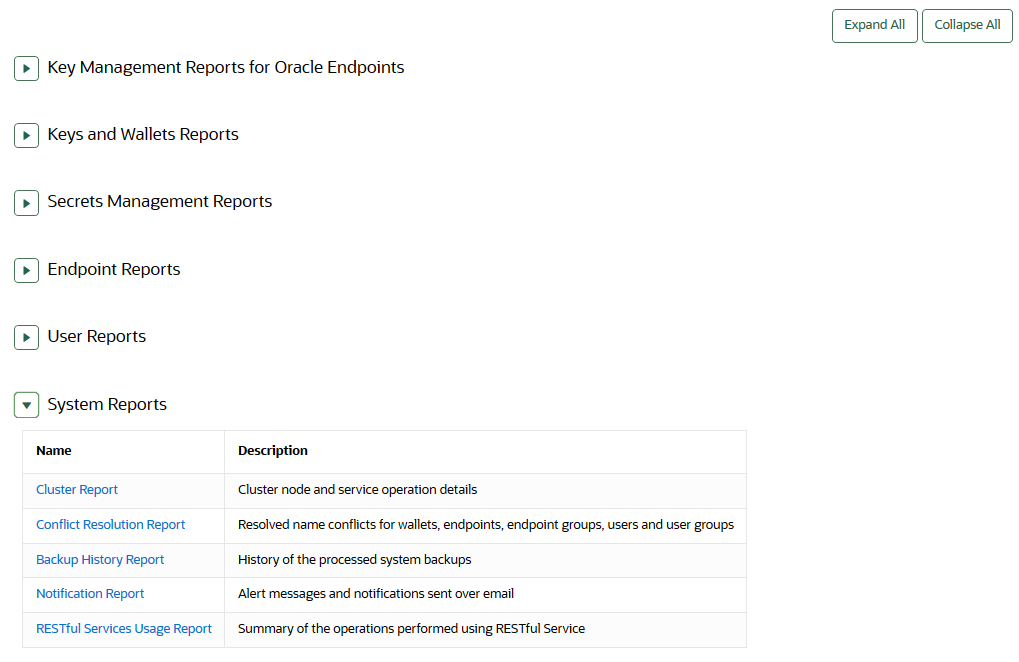
You must have the System Administrator role, the Key Management role, or the Audit Manager role to view the four categories of user reports. - Viewing System Reports
You must have the System Administrator role or the Audit Manager role to view the system reports.
Parent topic: Monitoring and Auditing Oracle Key Vault
22.4.1 About Oracle Key Vault Reports
The reports cover system activity, certificate expiration, keys, passwords, entitlement status, extraction status, and metadata.
Oracle Key Vault provides seven types of reports for endpoints, users, keys and wallets, SSH keys configuration and usage, and system. In a multi-master cluster, some reports contain additional information, such as the node ID, node name, and IP address.
The seven report types are as follows:
-
Key management reports for Oracle endpoints, which includes information about TDE master encryption keys, GoldenGate master keys, and ACFS volume encryption key details
-
Keys and wallets reports list the access privileges granted to all keys and wallets, and the details of TDE master encryption keys managed by Oracle Key Vault
-
Secrets management reports for database passwords, secret data, and opaque objects
-
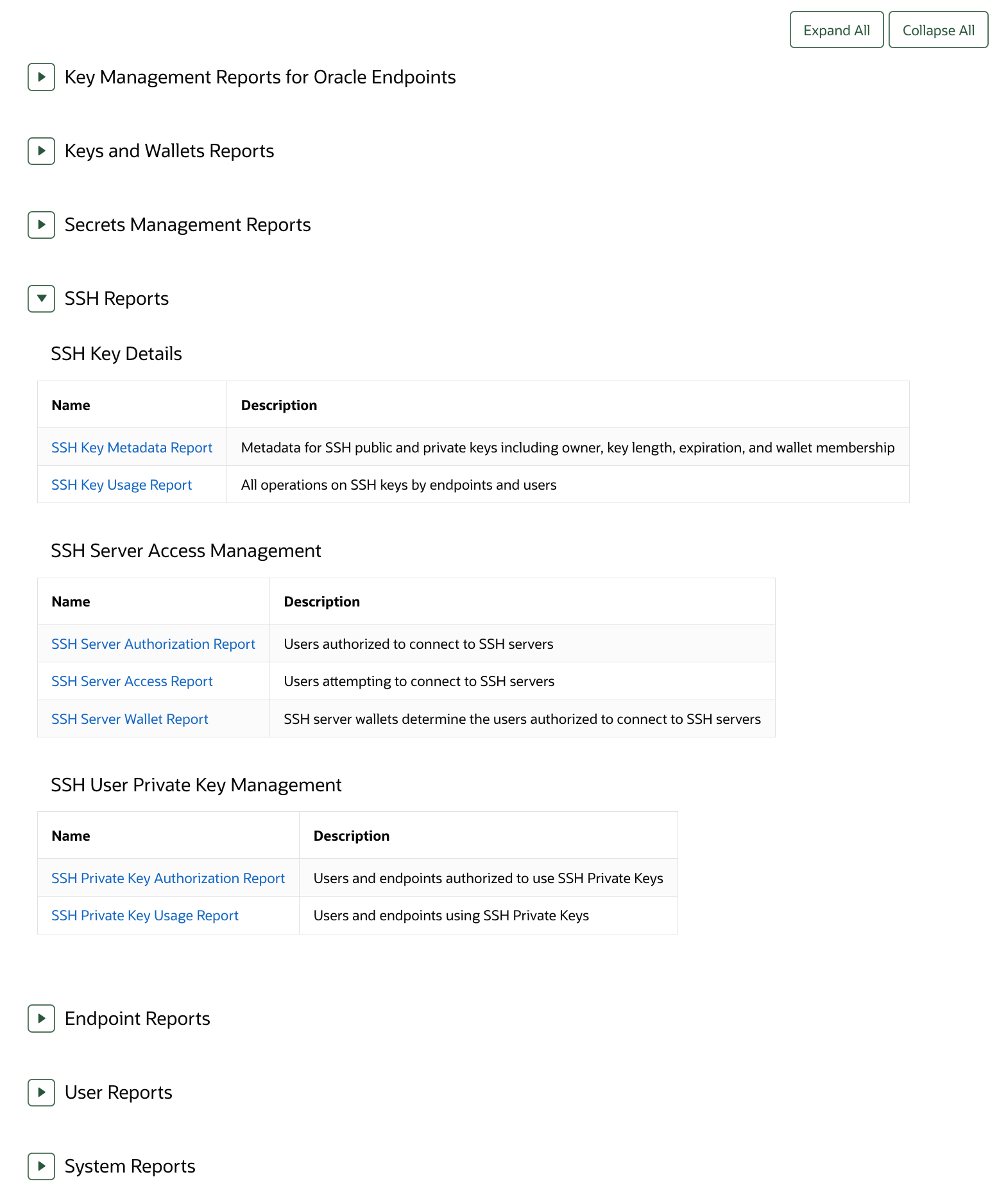
SSH reports for SSH user key management, SSH server access management and detailed information on SSH user keys inventory, authorization, and usage.
-
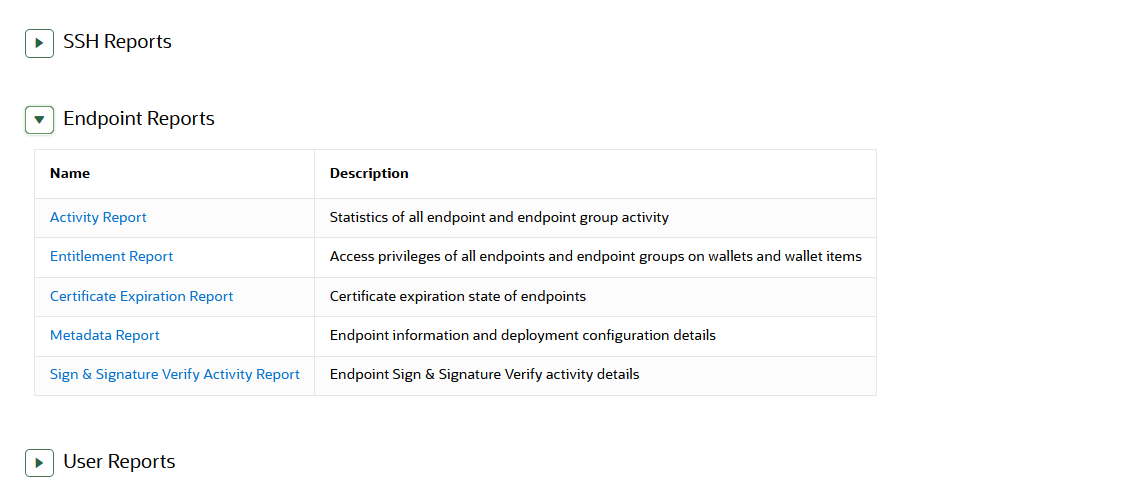
Endpoint reports contain details of all endpoint and endpoint group activity, certificate and password expiration, and access privileges
-
User reports contain details of all user and user group activity, their certificate and password expiration, and access privileges
-
System reports contain a history of system backups taken and scheduled, details of remote restoration points, and RESTful command-line interface usage
A user who has the Audit Manager role can view all reports, including reports that are accessible from the Audit Trail pages in the Oracle Key Vault management console. A user with the Key Administrator role can view user reports and keys and wallets reports. Users with the System Administrator role can view endpoint, user, and system reports.
Reports may include additional columns that are hidden by default. To include such columns in the displayed report, Click on Actions, then on Select Columns. The Select Columns dialog box appears. Select the columns that you want to include in the report from the list shown under Do Not Display section and move them to the list shown under Display In Report section by clicking on Move button (shown as >). Likewise, you can also remove columns from the report.
- Log in to the Oracle Key Vault management console.
- Click the Reports tab and then Reports from left navigation bar.
- Expand the report type to see the corresponding reports.
Related Topics
Parent topic: Using Oracle Key Vault Reports
22.4.2 Viewing Key Management Reports for Oracle Endpoints
All users can view the key management reports for Oracle endpoints.
Parent topic: Using Oracle Key Vault Reports
22.4.3 Viewing Keys and Wallets Reports
The keys and wallets reports require different privileges for viewing, depending on the report.
Parent topic: Using Oracle Key Vault Reports
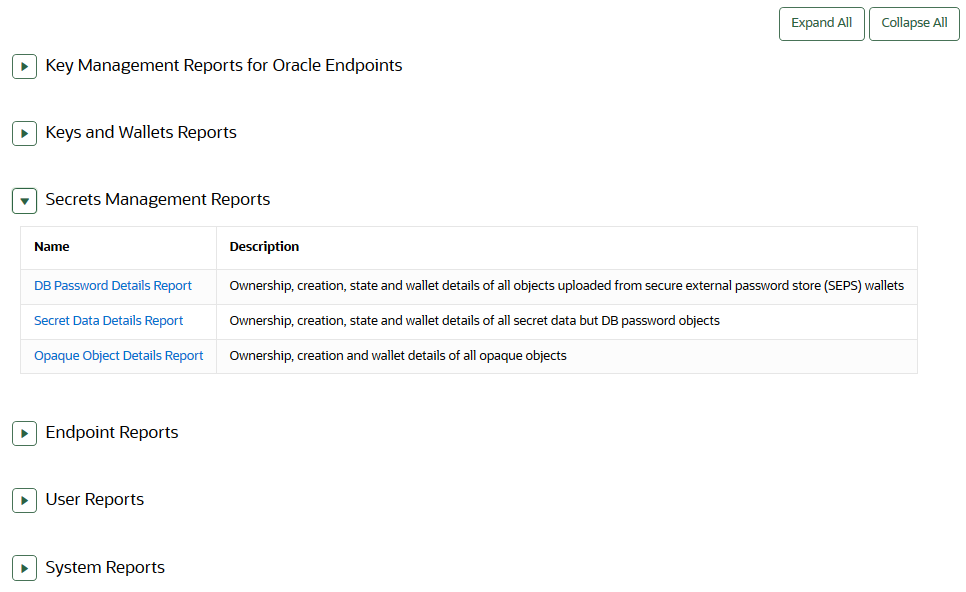
22.4.4 Viewing Secrets Management Reports
All users can view the secrets management reports.
Parent topic: Using Oracle Key Vault Reports
22.4.5 Viewing SSH Reports
All users can view the SSH reports.
Parent topic: Using Oracle Key Vault Reports
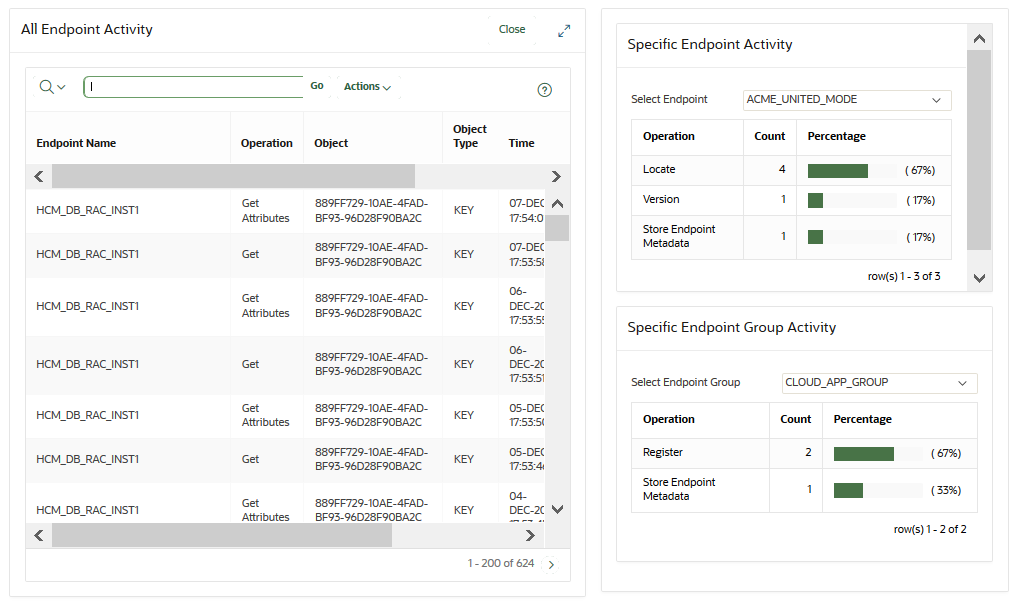
22.4.6 Viewing Endpoint Reports
You must have the System Administrator role or the Audit Manager role to view the five categories of endpoint reports.
Parent topic: Using Oracle Key Vault Reports
22.4.7 Viewing User Reports
You must have the System Administrator role, the Key Management role, or the Audit Manager role to view the four categories of user reports.
Parent topic: Using Oracle Key Vault Reports
22.4.8 Viewing System Reports
You must have the System Administrator role or the Audit Manager role to view the system reports.
Parent topic: Using Oracle Key Vault Reports