18 Oracle Key Vault General System Administration
General system administration refers to system management tasks for the Oracle Key Vault server, such as configuring network details and services.
- Overview of Oracle Key Vault General System Administration
System administrators can perform most general administration tasks in the Oracle Key Vault management console, including finding the current status of the overall system. - Configuring Oracle Key Vault in a Non-Multi-Master Cluster Environment
On the system Settings page, you can configure settings for either a standalone environment or a primary-standby environment. - Configuring Oracle Key Vault in a Multi-Master Cluster Environment
When you configure Oracle Key Vault in a multi-master cluster environment, you can configure either individual nodes or the entire multi-master cluster environment. - Managing System Recovery
System recovery includes tasks such as recovering lost administrative passwords. - Support for a Primary-Standby Environment
To ensure that Oracle Key Vault can always access security objects, you can deploy Oracle Key Vault in a primary-standby (highly available) configuration. - Commercial National Security Algorithm Suite Support
You can use scripts to perform Commercial National Security Algorithm (CNSA) operations for Oracle Key Vault HSM backup and upgrade operations. - Minimizing Downtime
Business-critical operations require data to be accessible and recoverable with minimum downtime.
18.1 Overview of Oracle Key Vault General System Administration
System administrators can perform most general administration tasks in the Oracle Key Vault management console, including finding the current status of the overall system.
- About Oracle Key Vault General System Administration
System administrators configure the Oracle Key Vault system settings. - Viewing the Oracle Key Vault Dashboard
The dashboard presents the current state of the Oracle Key Vault at a high level and is visible to all users. - Using the Status Panes in the Dashboard
The status panes on the dashboard provide a high-level overview of the current state of Oracle Key Vault, including outstanding alerts, aggregated summary of managed contents, and also the state and status of various objects, entities and services.
Parent topic: Oracle Key Vault General System Administration
18.1.1 About Oracle Key Vault General System Administration
System administrators configure the Oracle Key Vault system settings.
The Oracle Key Vault system settings include administration, local and remote monitoring, email notification, backup and recovery operations, and auditing. You must have the appropriate role for performing these tasks. Users who have the System Administrator role can perform most of the administrative tasks, and users with the Audit Manager role can configure audit settings, export audit records, and integrate Oracle Key Vault with Oracle Audit Vault. In most cases, you will perform these tasks in the Oracle Key Vault management console.
To quickly find information about the current state of the Oracle Key Vault system at a high level, you can view the Oracle Key Vault dashboard.
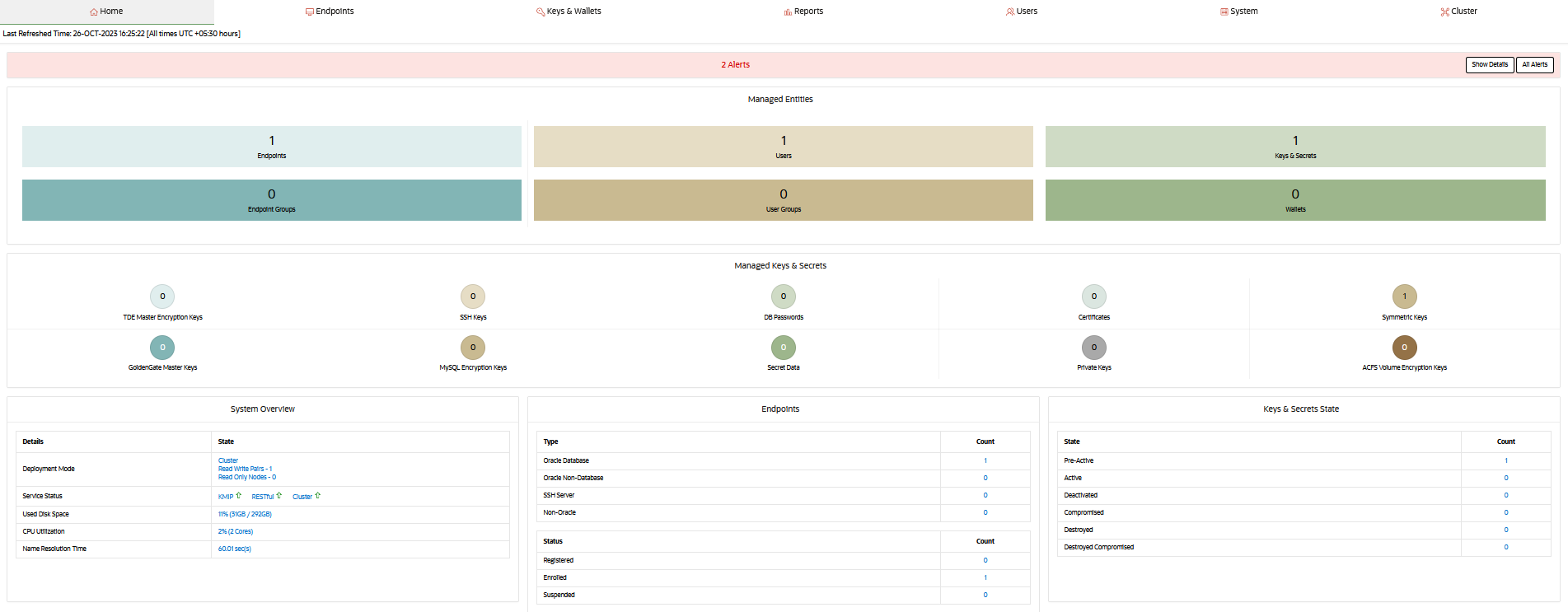
18.1.2 Viewing the Oracle Key Vault Dashboard
The dashboard presents the current state of the Oracle Key Vault at a high level and is visible to all users.
18.1.3 Using the Status Panes in the Dashboard
The status panes on the dashboard provide a high-level overview of the current state of Oracle Key Vault, including outstanding alerts, aggregated summary of managed contents, and also the state and status of various objects, entities and services.
Log in to the Oracle Key Vault management console.
The dashboard appears in the Home tab.
The dashboard is organized into different panes. These dashboard panes display aggregated information about alerts, managed entities, security objects, and overall system overview of Oracle Key Vault.
In the home page, the item type and item state are displayed as of the last time refreshed. The number and count of entities and objects displayed may vary for different users depending upon their authorization.
Related Topics
18.2 Configuring Oracle Key Vault in a Non-Multi-Master Cluster Environment
On the system Settings page, you can configure settings for either a standalone environment or a primary-standby environment.
- Configuring the Network Details
Learn how to configure the network details from the Oracle Key Vault management console. - Configuring Network Access
In a non-multi-master cluster, you can configure the network services from the Oracle Key Vault management console. - Configuring DNS
You can configure up to three domain name service (DNS) servers with IP addresses that Oracle Key Vault will use to resolve host names. - Configuring the System Time
Oracle strongly recommends that you synchronize Oracle Key Vault with an NTP time source. - Configuring FIPS Mode
You can either enable or disable FIPS mode for Oracle Key Vault. - Configuring Syslog
You can enable syslog for specific destinations and transmit the records either using Transmission Control Protocol (TCP) or User Datagram Protocol (UDP). - Changing the Network Interface Mode
You can switch between dual NIC mode and classic mode for the network interface. - Configuring RESTful Services Utility
RESTful services utility allows you to automate the management of endpoints, wallets, security objects, deployment operations, and backup operations. - Checking the Oracle Audit Vault Integration Status
Oracle Key Vault can send audit records to Oracle Audit Vault for centralized audit reporting and alerting. - Configuring the Oracle Key Vault Management Console Web Session Timeout
You can configure a timeout value in minutes for the Oracle Key Vault management console Web session. - Restarting or Powering Off Oracle Key Vault
You can manually restart or power off Oracle Key Vault as required for maintenance or for patch and upgrade procedures.
Parent topic: Oracle Key Vault General System Administration
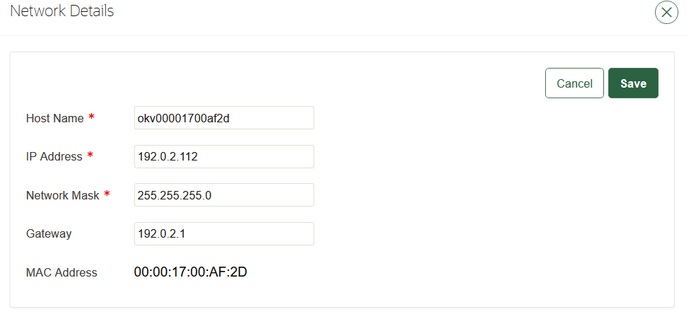
18.2.1 Configuring the Network Details
Learn how to configure the network details from the Oracle Key Vault management console.
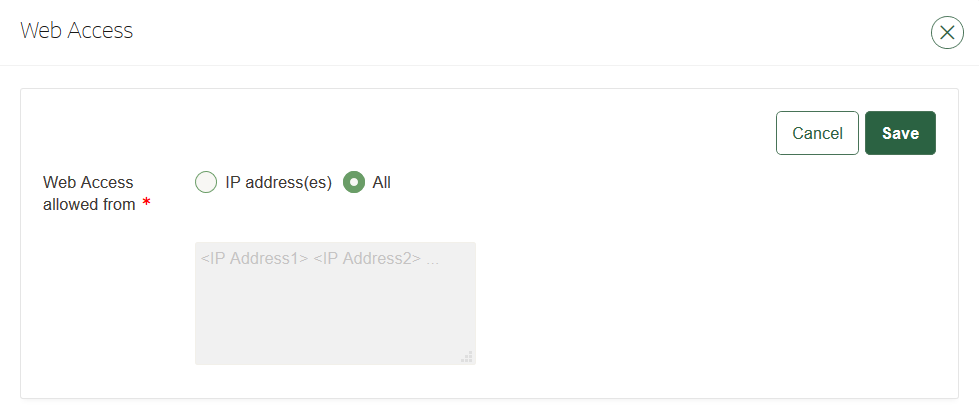
18.2.2 Configuring Network Access
In a non-multi-master cluster, you can configure the network services from the Oracle Key Vault management console.
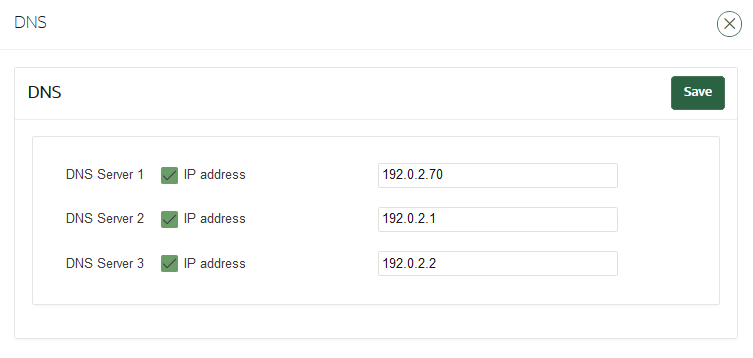
18.2.3 Configuring DNS
You can configure up to three domain name service (DNS) servers with IP addresses that Oracle Key Vault will use to resolve host names.
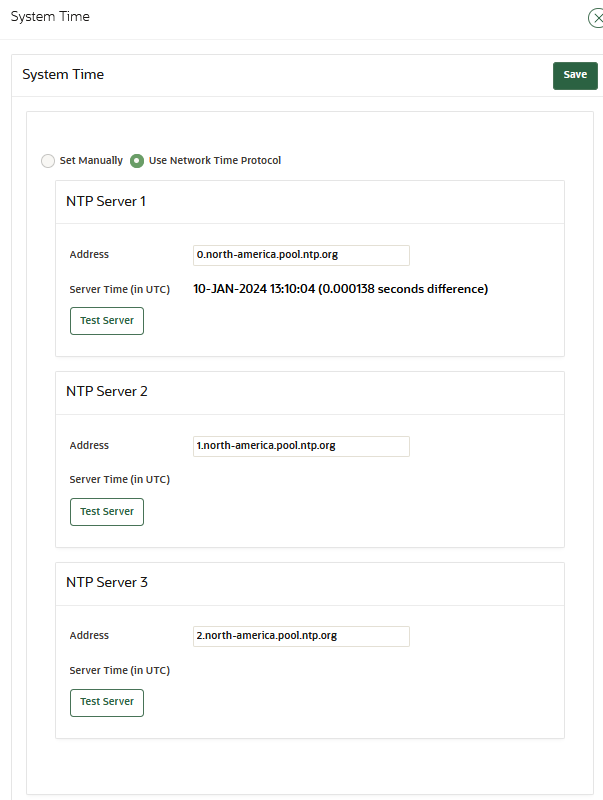
18.2.4 Configuring the System Time
Oracle strongly recommends that you synchronize Oracle Key Vault with an NTP time source.
You can configure Oracle Key Vault to synchronize its system time with the NTP servers. Oracle Key Vault provides fields to enter information for up to three NTP servers. If an NTP server is not available, then set the current time manually. Use the calendar icon to set the date and time so that these values are stored in the correct format.
Related Topics
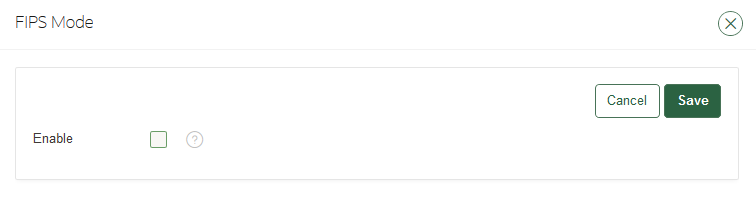
18.2.5 Configuring FIPS Mode
You can either enable or disable FIPS mode for Oracle Key Vault.
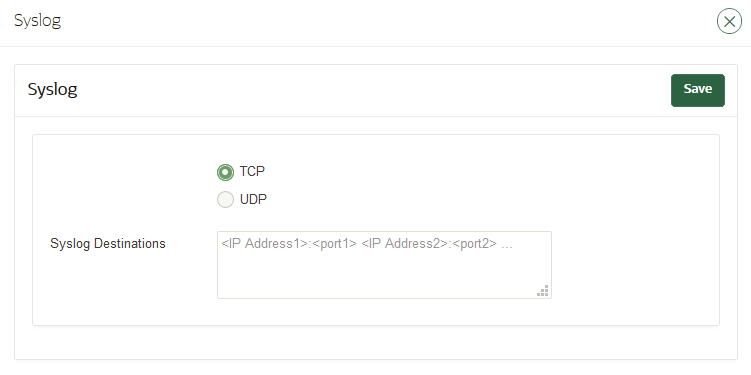
18.2.6 Configuring Syslog
You can enable syslog for specific destinations and transmit the records either using Transmission Control Protocol (TCP) or User Datagram Protocol (UDP).
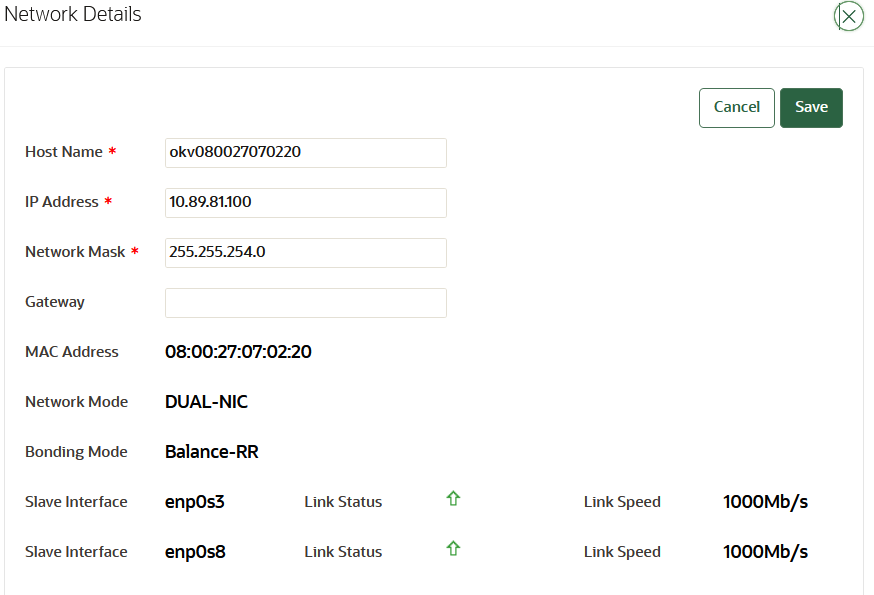
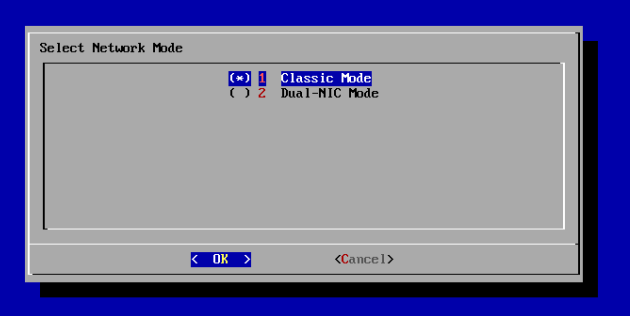
18.2.7 Changing the Network Interface Mode
You can switch between dual NIC mode and classic mode for the network interface.
18.2.8 Configuring RESTful Services Utility
RESTful services utility allows you to automate the management of endpoints, wallets, security objects, deployment operations, and backup operations.
Oracle Key Vault provides the management of endpoint operations, virtual wallet operations, downloading and provisioning operations as RESTful services.
Click Download to download the Oracle Key Vault RESTful Service Utility, okvrestclipackage.zip, to use these services. Click Download Classic Utility to download the classic utility, okvrestservices.jar.
18.2.9 Checking the Oracle Audit Vault Integration Status
Oracle Key Vault can send audit records to Oracle Audit Vault for centralized audit reporting and alerting.
18.2.10 Configuring the Oracle Key Vault Management Console Web Session Timeout
You can configure a timeout value in minutes for the Oracle Key Vault management console Web session.
20 minutes, then the user can extend the session for another 20 minutes.
18.3 Configuring Oracle Key Vault in a Multi-Master Cluster Environment
When you configure Oracle Key Vault in a multi-master cluster environment, you can configure either individual nodes or the entire multi-master cluster environment.
- About Configuring Oracle Key Vault in a Multi-Master Cluster Environment
You have the option of configuring settings for individual nodes or the entire multi-master cluster. - Configuring System Settings for Individual Multi-Master Cluster Nodes
You set or change the settings for an individual multi-master cluster node from the Oracle Key Vault management console for that node. - Configuring System Settings for an Entire Oracle Key Vault Multi-Master Cluster
You can set or change the settings for the entire multi-master cluster from the Oracle Key Vault management console of any node.
Parent topic: Oracle Key Vault General System Administration
18.3.1 About Configuring Oracle Key Vault in a Multi-Master Cluster Environment
You have the option of configuring settings for individual nodes or the entire multi-master cluster.
Some settings are same for the entire multi-master cluster and they apply to all the cluster nodes. For such settings, you cannot configure different values for different nodes. Examples of such settings include Console Timeout and Maximum Disable Node Duration.
You can configure some settings only at the individual cluster node level. You must configure such settings on each cluster node individually. Examples of such settings include Network Info, and SSH Access.
You can configure some settings at both the individual cluster node level and the entire cluster level. If you configure the settings at both levels, values set at the cluster node level are effective. Examples of such settings include DNS, NTP, and SNMP
When you set a value for the entire cluster, it may take several minutes for changes to propagate to other nodes.
When you start the configuration from the Settings page, you can select the following View Settings menu options to filter the settings based on whether they can be set at the node level only, cluster level only, or both:
-
Node only Shows settings that can only be configured at the individual node level. You configure such settings on each node individually. Examples of such settings include Network Info, and SSH Access.
-
Cluster only Shows settings that are cluster-wide and updating them will change the settings for all cluster nodes. Examples of such settings include Alerts, Console Timeout, and Maximum Disable Node Duration.
-
Both Shows settings that can be set at both the node level and the cluster level. If you configure the settings at both levels, values set at the node level are effective for that node. Examples of such settings include DNS, NTP, and SNMP.
You can navigate these settings between node and cluster settings using the right arrow button in the respective setting page. For example, if you select DNS, then you can configure DNS settings for either current node, or for the entire cluster, or both.
-
All shows all the available settings without any filter.
18.3.2 Configuring System Settings for Individual Multi-Master Cluster Nodes
You set or change the settings for an individual multi-master cluster node from the Oracle Key Vault management console for that node.
These include settings that can be set at the:
- individual node level only
-
individual node level as well as the entire-cluster level.
Values set for the individual node override the values set at the cluster level. You can clear any individual node level setting to revert to the cluster level setting.
Examples of these settings are network details, network access, system time, FIPS mode, syslog, and Oracle Audit Vault integration.
- Configuring the Network Details for the Node
In a multi-master cluster, you can change the host name for a node. - Configuring Network Access for the Node
In a multi-master cluster, you can configure network access for a node. - Configuring DNS for the Node
When you configure the DNS for a multi-master cluster node, you should enter more than one DNS IP address. - Configuring the System Time for the Node
In a multi-master cluster, you must synchronize Oracle Key Vault with an NTP time source. All nodes of the cluster should operate on the same system time (or coordinated system time) for the inter node replication to work correctly. - Configuring the FIPS Mode for the Node
All multi-master cluster nodes must use the same FIPS mode setting or you will receive an alert. - Configuring Syslog for the Node
In a multi-master cluster node, you can enable syslog for specific destinations and transmit the records either using Transmission Control Protocol (TCP) or User Datagram Protocol (UDP). - Changing the Network Interface Mode for the Node
You can switch between dual NIC mode and classic mode for the network interface for a node in a multi-master cluster environment. - Configuring Auditing for the Node
You can enable or disable audit settings for a node. - Configuring SNMP Settings for the Node
You can enable or disable SNMP access for a multi-master cluster node. - Checking the Oracle Audit Vault Integration for the Node
Oracle Key Vault can send audit records from a node to Oracle Audit Vault for centralized audit reporting and alerting. - Restarting or Powering Off Oracle Key Vault from a Node
You can manually restart or power off an Oracle Key Vault node as required for maintenance or for patch and upgrade procedures.
18.3.2.1 Configuring the Network Details for the Node
In a multi-master cluster, you can change the host name for a node.
18.3.2.2 Configuring Network Access for the Node
In a multi-master cluster, you can configure network access for a node.
18.3.2.3 Configuring DNS for the Node
When you configure the DNS for a multi-master cluster node, you should enter more than one DNS IP address.
18.3.2.4 Configuring the System Time for the Node
In a multi-master cluster, you must synchronize Oracle Key Vault with an NTP time source. All nodes of the cluster should operate on the same system time (or coordinated system time) for the inter node replication to work correctly.
18.3.2.5 Configuring the FIPS Mode for the Node
All multi-master cluster nodes must use the same FIPS mode setting or you will receive an alert.
18.3.2.6 Configuring Syslog for the Node
In a multi-master cluster node, you can enable syslog for specific destinations and transmit the records either using Transmission Control Protocol (TCP) or User Datagram Protocol (UDP).
Related Topics
18.3.2.7 Changing the Network Interface Mode for the Node
You can switch between dual NIC mode and classic mode for the network interface for a node in a multi-master cluster environment.
18.3.2.8 Configuring Auditing for the Node
You can enable or disable audit settings for a node.
Related Topics
18.3.2.9 Configuring SNMP Settings for the Node
You can enable or disable SNMP access for a multi-master cluster node.
18.3.2.10 Checking the Oracle Audit Vault Integration for the Node
Oracle Key Vault can send audit records from a node to Oracle Audit Vault for centralized audit reporting and alerting.
18.3.2.11 Restarting or Powering Off Oracle Key Vault from a Node
You can manually restart or power off an Oracle Key Vault node as required for maintenance or for patch and upgrade procedures.
- Log into the Oracle Key Vault management console for the node as a user who has the System Administrator role.
- Select the System tab, and then Status from the left navigation bar.
- At the top of the Status page, do one of the following to restart or power off the node:
- To restart, click Reboot.
- To power off, click Power Off.
18.3.3 Configuring System Settings for an Entire Oracle Key Vault Multi-Master Cluster
You can set or change the settings for the entire multi-master cluster from the Oracle Key Vault management console of any node.
These include settings that can be set at the:
- Entire cluster level only.
-
Individual node-level and the entire cluster level.
Values set at the cluster level do not override the values set the node level. To use cluster level setting, you need to clear any individual node level settings.
Example of these settings are console timeout, SNMP, system time, DNS, and auditing.
- Configuring the System Time for the Cluster
In a multi-master cluster, you can synchronize Oracle Key Vault with an NTP time source. - Configuring DNS for the Cluster
When you configure the DNS for a cluster, you can enter up to three DNS server IP addresses. - Configuring the Maximum Disable Node Duration for the Cluster
You can set the maximum disable node duration time for the cluster in hours. - Configuring Syslog for the Cluster
In a multi-master cluster environment, you can enable syslog for specific destinations and transmit the records either using Transmission Control Protocol (TCP) or User Datagram Protocol (UDP). - Configuring RESTful Services for the Cluster
You can enable or disable RESTful Services for the cluster. - Configuring Auditing for the Cluster
You can enable or disable audit settings for the cluster. - Configuring SNMP Settings for the Cluster
You can enable or disable SNMP access for a multi-master cluster. - Configuring the Oracle Key Vault Management Console Web Session Timeout for the Cluster
You can configure a timeout value in minutes for the Oracle Key Vault management console for all nodes in a multi-master cluster.
18.3.3.1 Configuring the System Time for the Cluster
In a multi-master cluster, you can synchronize Oracle Key Vault with an NTP time source.
18.3.3.2 Configuring DNS for the Cluster
When you configure the DNS for a cluster, you can enter up to three DNS server IP addresses.
18.3.3.3 Configuring the Maximum Disable Node Duration for the Cluster
You can set the maximum disable node duration time for the cluster in hours.
18.3.3.4 Configuring Syslog for the Cluster
In a multi-master cluster environment, you can enable syslog for specific destinations and transmit the records either using Transmission Control Protocol (TCP) or User Datagram Protocol (UDP).
Related Topics
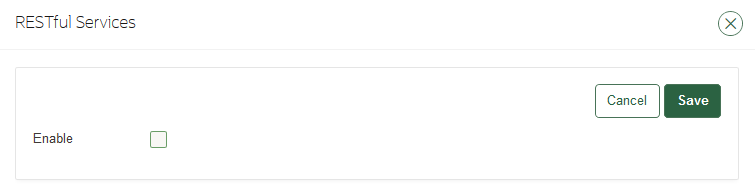
18.3.3.5 Configuring RESTful Services for the Cluster
You can enable or disable RESTful Services for the cluster.
- Log into any Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then Settings from the left navigation bar.
- In the System Configuration area, click RESTful Services.
- In the RESTful Services window, select the Enable check box.
- Click Save.
- Click Download to download the Oracle Key Vault RESTful
Service Utility,
okvrestclipackage.zip, to use these services. - Click Download Classic Utility to download the classic
utility,
okvrestservices.jar.
18.3.3.6 Configuring Auditing for the Cluster
You can enable or disable audit settings for the cluster.
Related Topics
18.3.3.7 Configuring SNMP Settings for the Cluster
You can enable or disable SNMP access for a multi-master cluster.
18.3.3.8 Configuring the Oracle Key Vault Management Console Web Session Timeout for the Cluster
You can configure a timeout value in minutes for the Oracle Key Vault management console for all nodes in a multi-master cluster.
20 minutes, then the user can extend the session for another 20 minutes.
18.4 Managing System Recovery
System recovery includes tasks such as recovering lost administrative passwords.
- About Managing System Recovery
To perform system recovery, you use the recovery passphrase. - Recovering Credentials for Administrators
You can recover the system by adding credentials for administrative users. - Changing the Recovery Passphrase in a Non-Multi-Master Cluster Environment
Periodically changing the recovery passphrase is a good security practice. - Changing the Recovery Passphrase in a Multi-Master Cluster
Changing the recovery passphrase in a multi-master cluster is a two-step process.
Parent topic: Oracle Key Vault General System Administration
18.4.1 About Managing System Recovery
To perform system recovery, you use the recovery passphrase.
In an emergency when no administrative users are available, or you must change the password of administrative users, you can recover the system with the current recovery passphrase of Oracle Key Vault. In addition, you can change the recovery passphrase to keep up with security best practices.
Parent topic: Managing System Recovery
18.4.2 Recovering Credentials for Administrators
You can recover the system by adding credentials for administrative users.
Parent topic: Managing System Recovery
18.4.3 Changing the Recovery Passphrase in a Non-Multi-Master Cluster Environment
Periodically changing the recovery passphrase is a good security practice.
Parent topic: Managing System Recovery
18.4.4 Changing the Recovery Passphrase in a Multi-Master Cluster
Changing the recovery passphrase in a multi-master cluster is a two-step process.
- About Changing the Recovery Passphrase for a Multi-Master Cluster
To change the recovery passphrase for a multi-master cluster, you must first initiate the recovery passphrase change from one of the cluster node. Other cluster nodes are notified of the impending passphrase change. - Step 1: Initiate the Recovery Passphrase Change Across the Nodes
You must initiate the change for the recovery passphrase so that all nodes in the multi-master cluster will be notified of the impending change. - Step 2: Change the Recovery Passphrase
After the multi-master cluster nodes have been notified of the impending recovery passphrase change, you can change the recovery passphrase.
Parent topic: Managing System Recovery
18.4.4.1 About Changing the Recovery Passphrase for a Multi-Master Cluster
To change the recovery passphrase for a multi-master cluster, you must first initiate the recovery passphrase change from one of the cluster node. Other cluster nodes are notified of the impending passphrase change.
Before changing the Recovery Passphrase, ensure that the node is ready to accept the new passphrase. The presence of the fields on the System Recovery page indicates that the node is ready to accept the new password on the Recovery Passphrase tab. Set the new recovery passphrase on each node in below order:
- Set the new recovery passphrase on all nodes other than the one which initiated the recovery passphrase change.
- After the new recovery passphrase change on other nodes has been set, set the new recovery passphrase for the node that initiated the recovery passphrase change.
- Set the same passphrase on every node.
18.4.4.2 Step 1: Initiate the Recovery Passphrase Change Across the Nodes
You must initiate the change for the recovery passphrase so that all nodes in the multi-master cluster will be notified of the impending change.
Related Topics
18.4.4.3 Step 2: Change the Recovery Passphrase
After the multi-master cluster nodes have been notified of the impending recovery passphrase change, you can change the recovery passphrase.
- The new recovery passphrase is set on each node.
- The new recovery passpharse is set on all the nodes first other than the initiator node, that is, the node that has initiated the recovery passphrase change.
- Set the new recovery passphrase on the initiator node in the end.
- All the nodes are using the same Recovery passphrase.
Before changing the Recovery Passphrase, ensure that the node is ready to accept the new passphrase. This is indicated by the presence of the fields to accept the new password on the Recovery Passphrase tab of the System Recovery page.
18.5 Support for a Primary-Standby Environment
To ensure that Oracle Key Vault can always access security objects, you can deploy Oracle Key Vault in a primary-standby (highly available) configuration.
This configuration also supports disaster recovery scenarios.
You can deploy two Oracle Key Vault servers in a primary-standby configuration. The primary server services the requests that come from endpoints. If the primary server fails, then the standby server takes over after a configurable preset delay. This configurable delay ensures that the standby server does not take over prematurely in case of short communication gaps.
The primary-standby configuration was previously known as the high availability configuration. The primary-standby configuration and the multi-master cluster configuration are mutually exclusive.
Oracle Key Vault supports primary-standby read-only restricted mode. When the primary server is affected by server, hardware, or network failures, primary-standby read-only restricted mode ensures that an Oracle Key Vault server is available to service endpoints, thus ensuring operational continuity. However, key and sensitive operations, such as generation of keys are disabled, while operations such as generation of audit logs are unaffected.
When an unplanned shutdown makes the standby server unreachable, the primary server is still available to the endpoints in read-only mode.
Related Topics
Parent topic: Oracle Key Vault General System Administration
18.6 Commercial National Security Algorithm Suite Support
You can use scripts to perform Commercial National Security Algorithm (CNSA) operations for Oracle Key Vault HSM backup and upgrade operations.
- About Commercial National Security Algorithm Suite Support
You can configure Oracle Key Vault for compliance with the Commercial National Security Algorithm (CNSA) Suite. - Running the Commercial National Security Algorithm Scripts
You configure Oracle Key Vault to use the Commercial National Security Algorithm (CNSA) suite by running CNSA scripts. - Performing Backup Restore Operations with CNSA
After you restore a backup of the Oracle Key Vault that was configured to use the enhanced Commercial National Security Algorithm (CNSA) Suite, use/usr/local/okv/bin/okv_cnsato reconfigure CNSA compliance. - Upgrading a Standalone Oracle Key Vault Server with CNSA
You can upgrade a standalone Oracle Key Vault while using Commercial National Security Algorithm (CNSA) compliance by upgrading and then executing theokv_cnsascript. - Upgrading Primary-Standby Oracle Key Vault Servers to Use CNSA
You can upgrade Oracle Key Vault primary-standby servers while using Commercial National Security Algorithm (CNSA) compliance by upgrading and then executing theokv_cnsascript.
Parent topic: Oracle Key Vault General System Administration
18.6.1 About Commercial National Security Algorithm Suite Support
You can configure Oracle Key Vault for compliance with the Commercial National Security Algorithm (CNSA) Suite.
This compliance applies to TLS connections to and from the Oracle Key Vault appliance.
The CNSA suite is a list of strong encryption algorithms and key lengths, that offer greater security and relevance into the future.
Oracle Key Vault release 12.2 BP3 or later do not provide complete compliance across every component in the system. You will be able to switch to the CNSA algorithms, where available by means of the following scripts that are packaged with the Oracle Key Vault ISO:
-
/usr/local/okv/bin/okv_cnsamakes configuration file changes to update as many components as possible to use the enhanced algorithms. -
/usr/local/okv/bin/okv_cnsa_certregenerates CNSA compliant public key pairs and certificates.Note:
The/usr/local/okv/bin/okv_cnsaand/usr/local/okv/bin/okv_cnsa_certscripts are both disruptive because they replace the old key pairs with new ones. This has consequences for the following operations:-
Endpoint Enrollment: Enroll endpoints after running this script when possible. If you had endpoints enrolled before running the CNSA script, you must reenroll them so that fresh CNSA compliant keys are generated using CNSA algorithms.
-
Primary-Standby: Run the CNSA scripts on both Oracle Key Vault instances before pairing them in a primary-standby configuration when possible. If you had primary-standby before you run the CNSA scripts, then you must re-configure primary-standby as follows: unpair the primary and standby servers, reinstall the standby server, run the CNSA scripts individually on each server, and then pair them again.
-
Limitations:
-
CNSA compliance is not supported for all components in the Oracle Key Vault infrastructure (for example, SSH or Transparent Data Encryption (TDE)).
-
The Firefox browser is not supported for use with the Oracle Key Vault management console when CNSA is enabled. This is because the Firefox browser does not support CNSA-approved cipher suites.
Parent topic: Commercial National Security Algorithm Suite Support
18.6.2 Running the Commercial National Security Algorithm Scripts
You configure Oracle Key Vault to use the Commercial National Security Algorithm (CNSA) suite by running CNSA scripts.
/usr/local/okv/etc/okv_security.conf with the following line:USE_ENHANCED_ALGORITHMS_ONLY="1"
Related Topics
Parent topic: Commercial National Security Algorithm Suite Support
18.6.3 Performing Backup Restore Operations with CNSA
After you restore a backup of the Oracle Key Vault that was configured to use the enhanced Commercial National Security Algorithm (CNSA) Suite, use /usr/local/okv/bin/okv_cnsa to reconfigure CNSA compliance.
Related Topics
Parent topic: Commercial National Security Algorithm Suite Support
18.6.4 Upgrading a Standalone Oracle Key Vault Server with CNSA
You can upgrade a standalone Oracle Key Vault while using Commercial National Security Algorithm (CNSA) compliance by upgrading and then executing the okv_cnsa script.
18.6.5 Upgrading Primary-Standby Oracle Key Vault Servers to Use CNSA
You can upgrade Oracle Key Vault primary-standby servers while using Commercial National Security Algorithm (CNSA) compliance by upgrading and then executing the okv_cnsa script.
Related Topics
Parent topic: Commercial National Security Algorithm Suite Support
18.7 Minimizing Downtime
Business-critical operations require data to be accessible and recoverable with minimum downtime.
You can configure Oracle Key Vault to ensure minimum downtime in the following ways:
-
Configuring a multi-master cluster: You can configure a multi-master cluster by adding redundancy in the form of additional nodes. The client can access any available node. In the event of a failure of any node, a client will automatically connect to another node in the endpoint node scan list. This reduces and potentially eliminates downtime.
-
Configuring a primary-standby environment: A primary-standby environment is configured by adding redundancy in the form of a standby server. The standby server takes over from the primary server in the event of a failure, thus eliminating single points of failure, and minimizing downtime.
-
Enabling read-only restricted mode: Primary-standby read-only restricted mode ensures endpoint operational continuity when primary or standby Oracle Key Vault servers are affected by server, hardware, or network failures. When an unplanned shutdown causes the standby server to become unreachable, the primary server is still available to the endpoints.
If primary-standby read-only restricted mode is disabled, then the primary server will become unavailable and stop accepting requests in the event of a standby failure. Endpoints connected to Oracle Key Vault are unable to retrieve keys until connectivity is restored between primary and standby servers.
To ensure endpoint operational continuity in the event of a primary or standby server failure, enable read-only restricted mode.
-
Enabling persistent master encryption key cache: The persistent master encryption key cache ensures that the endpoints can access keys in the event of a primary or standby server failure. While the surviving server is taking over from the failed peer, the endpoints can retrieve keys from the persistent cache and continue operations normally.
-
Apply the TDE heartbeat database patch on endpoints: Apply the database patch for Bug 22734547 to tune the Oracle Key Vault heartbeat.
Oracle strongly recommends that you back up Oracle Key Vault data regularly on a schedule. This practice ensures that backups are current and hold the most recent data. You can use this backup to restore a new or existing Oracle Key Vault server and enable it to be fully operational with minimum downtime and data loss.
If the Oracle Key Vault installation uses an online master encryption key (formerly known as TDE direct connect), then during an upgrade, ensure that you upgrade database endpoints in parallel to reduce total downtime.
Related Topics
Parent topic: Oracle Key Vault General System Administration