12 Managing Oracle Key Vault Endpoints
Oracle Key Vault endpoints are computer systems like database or application servers, where keys and credentials are used to access data.
- Overview of Managing Endpoints
You can manage endpoints in standalone, primary-standby and multi-master clusters in mostly the same way, except that multi-master clusters have more restrictions. - Managing Endpoints
You can enroll, reenroll, suspend, rotate, and delete endpoints. - Managing Endpoint Details
Endpoint details refers to endpoint name, type, description, platform, and email, and adding the endpoint to a group, or upgrading the endpoint software. - Managing Global and Per-Endpoint Configuration Parameters and Settings
Oracle Key Vault provides global and per-endpoint configuration parameters and settings that you can set in the Oracle Key Vault management console. - Default Wallets and Endpoints
You can use a default wallet, which is a type of virtual wallet, with an endpoint. - Managing Endpoint Access to a Virtual Wallet
You can grant an endpoint access to a virtual wallet, and revoke or modify access when it is no longer necessary. - Managing Endpoint Groups
An endpoint group is a named group of endpoints that share a common set of wallets.
12.1 Overview of Managing Endpoints
You can manage endpoints in standalone, primary-standby and multi-master clusters in mostly the same way, except that multi-master clusters have more restrictions.
- About Managing Endpoints
You must register and enroll an endpoint to communicate with an Oracle Key Vault server. - How a Multi-Master Cluster Affects Endpoints
You should be aware of how a multi-master cluster affects endpoints, both in the way an endpoint connects to it and with restrictions.
Parent topic: Managing Oracle Key Vault Endpoints
12.1.1 About Managing Endpoints
You must register and enroll an endpoint to communicate with an Oracle Key Vault server.
Afterward, keys in the endpoint can be uploaded to Oracle Key Vault and be shared with other endpoints and then downloaded from these endpoints so that users can access their data. Only a user with the System Administrator role or the Create Endpoint privilege can add an endpoint to Oracle Key Vault. After the endpoint is added, the endpoint administrator can enroll the endpoint by downloading and installing the endpoint software at the endpoint. The endpoint can then use the utilities packaged with the endpoint software to upload and download security objects to and from Oracle Key Vault.
All users can create virtual wallets but only a user with the Key Administrator role can grant endpoints access to security objects contained in virtual wallets. A Key Administrator user can grant access on any wallet to an endpoint. A user with the Key Administrator role or Create Endpoint Group privilege can also Create Endpoint Groups to enable shared access to virtual wallets. Any user (including users who created the endpoint) who has the manage wallet permission on a wallet can grant access to that wallet to an endpoint. When you grant an endpoint group access to a virtual wallet, all the member endpoints will have access to the virtual wallet. For example, you can grant all the nodes in an Oracle Real Application Clusters (Oracle RAC) database access to a virtual wallet by putting them in an endpoint group. This saves you the step of granting each node access to the virtual wallet. As an added layer of security, the Key Administrator user can enable or disable the extraction of symmetric keys from Oracle Key Vault.
If you have a large deployment, Oracle recommends that you install at least four Oracle Key Vault servers, and when you enroll the endpoints, balance them across these four servers to ensure high availability. For example, if a data center has 1000 database endpoints to register, and you have four Oracle Key Vault servers to accommodate them, then enroll 250 endpoints across each of the four servers.
When you name an endpoint, you cannot use an Oracle Key Vault server user name as the endpoint name.
Note:
Ensure that the system time on the endpoint host and the Oracle Key Vault server is in sync for successful endpoint enrollment.When a user with Create Endpoint or Endpoint Group privilege creates an endpoint or endpoint group, Oracle Key Vault indirectly grants the Manage Endpoint or Endpoint Group to the user.
The administrative roles and privileges as they pertain to endpoints are as follows:
- Endpoint creation: A user with either the System Administrator role or the Create Endpoint privilege can create endpoints in Oracle Key Vault. A user with the Create Endpoint privilege is automatically granted the Manage Endpoint privilege on any endpoints that they create.
- Endpoint management: A user with the System Administrator role can
Manage Endpoints anywhere in the Oracle Key Vault system. A user with the Manage Endpoint
privilege can manage only his or her own endpoints. This includes endpoints that the user
was explicitly granted the Manage Endpoint privilege on, or endpoints that the user created
and continues to have the Manage Endpoint privilege on. This management includes the
following duties:
- Managing the endpoint metadata such as the name, type, platform, description, and email notifications
- Managing the endpoint life cycle, which consists of enrolling, suspending, re-enrolling, rotating, and deleting endpoints
- Endpoint group creation: A user with the Key Administrator role or Create Endpoint Group privilege can create endpoint groups in Oracle Key Vault. A user with the Create Endpoint Group privilege is automatically granted the Manage Endpoint Group privilege on any endpoint groups that they create.
- Endpoint group management: A user with the Key Administrator role can
manage endpoint groups anywhere in the Oracle Key Vault system. A user with the manage
endpoint group privilege can manage only his or her own endpoint groups. The endpoint groups
that a user can manage include those that the user was explicitly granted the manage
endpoint group privilege on, or those that the user created and continues to have the manage
endpoint group privilege on. This management includes the following duties:
- Managing the endpoint group lifecycle, which consists of creating, modifying, and deleting endpoint groups
- Managing the life cycle of security objects, which consists of creating, modifying and deleting security objects
Related Topics
Parent topic: Overview of Managing Endpoints
12.1.2 How a Multi-Master Cluster Affects Endpoints
You should be aware of how a multi-master cluster affects endpoints, both in the way an endpoint connects to it and with restrictions.
In a multi-master configuration, when an endpoint attempts to make a connection to Oracle Key Vault, it performs the following actions:
- First, it obtains the list of server IPs from its configuration file (
okvclient.ora). - Next, it picks one at random, preferentially from those in the same cluster subgroup as the endpoint.
Be aware of the following restrictions with how endpoints work in multi-master clusters:
- An endpoint can only be enrolled from the same node where it was most recently created or reenrolled.
- You can assign a default wallet to an endpoint if one or both of them (wallet and
endpoint) is in the
PENDINGstate, but not if the assignment is attempted from a non-creator node. After both the endpoint and wallet are in theACTIVEstate, this restriction ends.
Parent topic: Overview of Managing Endpoints
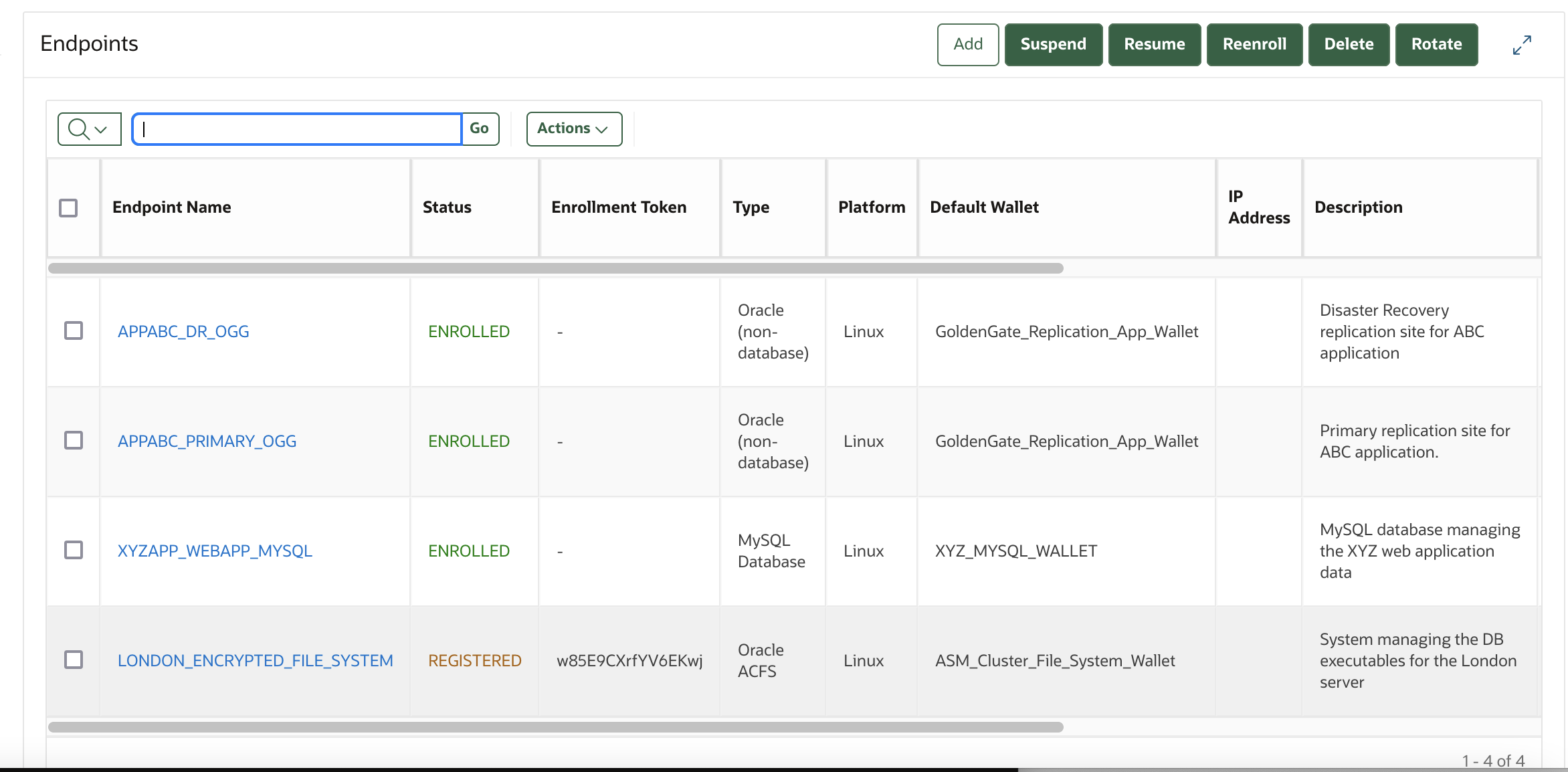
12.2 Managing Endpoints
You can enroll, reenroll, suspend, rotate, and delete endpoints.
- Types of Endpoint Enrollment
The first step in enrolling an endpoint is to add the endpoint to Oracle Key Vault. - Endpoint Enrollment in a Multi-Master Cluster
Endpoints of a cluster are the client systems of the multi-master cluster. - Adding an Endpoint as an Oracle Key Vault System Administrator or Create Endpoint User
A user who has been granted the System Administrator role or the Create Endpoint privilege can add an endpoint by using the Endpoints tab. - Adding Endpoints Using Self-Enrollment
The self-enrollment process immediately sends the endpoint to the Enrolled status without the intermediate Registered status. - Deleting, Suspending, Reenrolling, or Rotating Endpoints
When endpoints no longer use Oracle Key Vault to store security objects, you can delete them. You can also suspend, and later resume them when they are needed. You can also re-enroll or rotate endpoints when necessary.
Parent topic: Managing Oracle Key Vault Endpoints
12.2.1 Types of Endpoint Enrollment
The first step in enrolling an endpoint is to add the endpoint to Oracle Key Vault.
There are two methods for adding, also known as registering, an endpoint:
- Initiated by an administrator
An Oracle Key Vault user who has the System Administrator role initiates the enrollment from the Oracle Key Vault side by adding the endpoint to Oracle Key Vault. When the endpoint is added, a one-time enrollment token is generated. This token can be communicated to the endpoint administrator in two ways:
- Directly from Oracle Key Vault by email. To use email notification you must configure SMTP in email settings.
- Out-of-band method, such as email or telephone.
The endpoint administrator uses the enrollment token to download the endpoint software and complete the enrollment process. In a multi-master cluster, the same node that is used to add the endpoint must be used to enroll the endpoint.
After the enrollment token is used to enroll an endpoint, it cannot be used again for another enrollment. If you are reenrolling an endpoint, then the reenrollment process will generate a new one-time enrollment token for this purpose.
- Self-enrolled
Endpoints may enroll themselves during specific times without human administrative intervention. Endpoint self-enrollment is useful when the endpoints do not share security objects, and use Oracle Key Vault primarily to store and restore their own security objects. Another use for endpoint self-enrollment is testing.
A self-enrolled endpoint is created with a generic endpoint name in this format:
ENDPT_001. In a cluster, a self-enrolled endpoint is created with a generic endpoint name in this format:ENDPT_xx_001, wherexxis a 2-digit node identifier or node number. Initially, a self-enrolled endpoint has access only to the security objects that it uploads or creates. It does not have access to any virtual wallets. You can later grant the endpoint access to virtual wallets after verifying its identity.Endpoint self-enrollment is disabled by default, and must be enabled by a user with the System Administrator role. Oracle recommends that you enable self-enrollment for short periods, when you expect endpoints to self enroll, and then disable it when the self-enrollment period ends.
Related Topics
Parent topic: Managing Endpoints
12.2.2 Endpoint Enrollment in a Multi-Master Cluster
Endpoints of a cluster are the client systems of the multi-master cluster.
Endpoint enrollment is divided into two steps. First you create the endpoint and then you enroll it.
The Oracle Key Vault server that becomes the controller node can have endpoints already enrolled, especially if it was upgraded from a previous release. These existing endpoints initialize, or seed, the cluster. During induction, information about the endpoints that were enrolled in the cluster is replicated to the newly added node. Oracle Key Vault also removes information about the endpoints that were previously enrolled in all candidate nodes added to the cluster.
Endpoints can only be enrolled on a read-write node.
Note:
An endpoint must be enrolled on the same node where it was most recently added or reenrolled.New endpoints added concurrently to the multi-master cluster on different nodes could have name conflicts. Oracle Key Vault automatically resolves the endpoint name conflicts, and then displays the conflicts in a Conflicts Resolution page. From here, a system administrator can choose to rename them.
Related Topics
Parent topic: Managing Endpoints
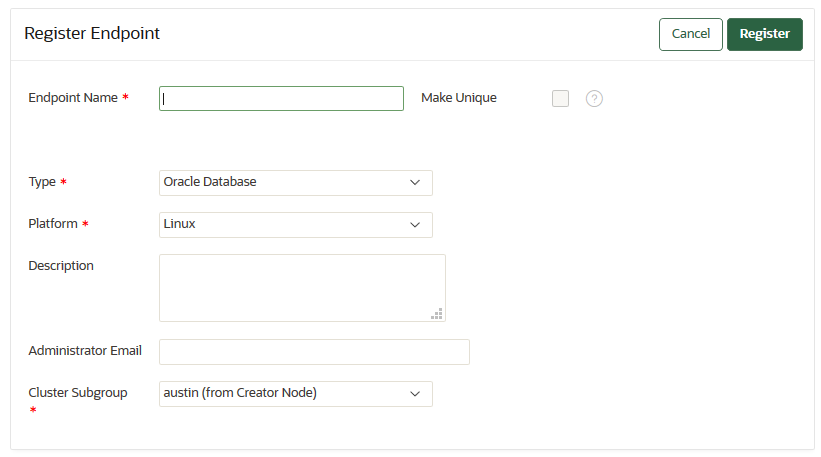
12.2.3 Adding an Endpoint as an Oracle Key Vault System Administrator or Create Endpoint User
A user who has been granted the System Administrator role or the Create Endpoint privilege can add an endpoint by using the Endpoints tab.
Parent topic: Managing Endpoints
12.2.4 Adding Endpoints Using Self-Enrollment
The self-enrollment process immediately sends the endpoint to the Enrolled status without the intermediate Registered status.
- About Adding Endpoints Using Self-Enrollment
Oracle Key Vault associates a self-enrolled attribute with all endpoints that are enrolled through endpoint self-enrollment. - Adding an Endpoint Using Self-Enrollment
You can configure the self-enrollment process for endpoints from the Oracle Key Vault management console.
Parent topic: Managing Endpoints
12.2.4.1 About Adding Endpoints Using Self-Enrollment
Oracle Key Vault associates a self-enrolled attribute with all endpoints that are enrolled through endpoint self-enrollment.
Self-enrolled endpoints go directly to Enrolled status without the intermediate Registered status when a user downloads the endpoint software. You can recognize self-enrolled endpoints by their system generated names in the format ENDPT_001. In a multi-master cluster, system generated endpoint names are in the format ENDPT_node_id_sequential_number, where node_id is a value such as 01 or 02. For example, ENDPT_01_001 can be the generated name of an endpoint.
Endpoint self-enrollment is disabled by default and must be enabled by a user who has the System Administrator role.
A best practice is to enable endpoint self-enrollment for limited periods when you expect endpoints to enroll. After the expected endpoints have been enrolled, you should disable endpoint self-enrollment.
Parent topic: Adding Endpoints Using Self-Enrollment
12.2.4.2 Adding an Endpoint Using Self-Enrollment
You can configure the self-enrollment process for endpoints from the Oracle Key Vault management console.
Related Topics
Parent topic: Adding Endpoints Using Self-Enrollment
12.2.5 Deleting, Suspending, Reenrolling, or Rotating Endpoints
When endpoints no longer use Oracle Key Vault to store security objects, you can delete them. You can also suspend, and later resume them when they are needed. You can also re-enroll or rotate endpoints when necessary.
- About Deleting Endpoints
Deleting an endpoint removes it permanently from Oracle Key Vault. - Deleting One or More Endpoints
The Endpoints page enables you to delete a group of endpoints from Oracle Key Vault at one time. - Deleting One Endpoint (Alternative Method)
The Endpoint Details page provides a consolidated view for the selected endpoint including a mechanism to delete the endpoint from Oracle Key Vault. - Suspending an Endpoint
You can suspend an endpoint temporarily for security reasons, and then reinstate the endpoint once the threat has passed. You can choose to suspend unused endpoints during the CA certificate rotation process to allow the CA certificate rotation process to complete. - Reenrolling an Endpoint
When you reenroll an endpoint, the enrollment process automatically upgrades the endpoint software and also generates new endpoint certificates. - Rotating Endpoint Certificates
Rotating an endpoint's certificate extends its certificate validity without incurring downtime for the endpoint.
Parent topic: Managing Endpoints
12.2.5.1 About Deleting Endpoints
Deleting an endpoint removes it permanently from Oracle Key Vault.
However, security objects that were previously created or uploaded by that endpoint will remain in Oracle Key Vault. Similarly, security objects that are associated with that endpoint also remain. To permanently delete or reassign these security objects, you must be a user with the Key Administrator role or authorized to merge these objects by managing wallet privileges. The endpoint software previously downloaded at the endpoint also remains on the endpoint until the endpoint administrator removes it.
You cannot delete an endpoint that is in the PENDING state unless you are the user who created it. You must delete it on the node on which it was created.
Parent topic: Deleting, Suspending, Reenrolling, or Rotating Endpoints
12.2.5.2 Deleting One or More Endpoints
The Endpoints page enables you to delete a group of endpoints from Oracle Key Vault at one time.
Related Topics
Parent topic: Deleting, Suspending, Reenrolling, or Rotating Endpoints
12.2.5.3 Deleting One Endpoint (Alternative Method)
The Endpoint Details page provides a consolidated view for the selected endpoint including a mechanism to delete the endpoint from Oracle Key Vault.
Related Topics
Parent topic: Deleting, Suspending, Reenrolling, or Rotating Endpoints
12.2.5.4 Suspending an Endpoint
You can suspend an endpoint temporarily for security reasons, and then reinstate the endpoint once the threat has passed. You can choose to suspend unused endpoints during the CA certificate rotation process to allow the CA certificate rotation process to complete.
PENDING state unless you are the user who created it.
The following rules apply to suspending an endpoint in a multi-master cluster:
- For regular endpoints, the endpoint will continue to operate until all suspend operation requests have reached all nodes in the cluster.
- You can suspend the endpoint on any node.
- For cloud-based endpoints, the endpoint will continue to operate until the suspend operation has reached all nodes from where the reverse SSH tunnel is established.
- You can potentially suspend the endpoint on any node from the cloud-based endpoint from where the reverse SSH tunnel is established.
Related Topics
Parent topic: Deleting, Suspending, Reenrolling, or Rotating Endpoints
12.2.5.5 Reenrolling an Endpoint
When you reenroll an endpoint, the enrollment process automatically upgrades the endpoint software and also generates new endpoint certificates.
okvclient.jar and deploy it in a directory that is separate from the existing deployment. When you deploy the software, use the -o option to overwrite the symbolic link pointing to the old okvclient.ora. You cannot reenroll an endpoint that is in the PENDING state unless you are the user who created the endpoint.
Related Topics
Parent topic: Deleting, Suspending, Reenrolling, or Rotating Endpoints
12.2.5.6 Rotating Endpoint Certificates
Rotating an endpoint's certificate extends its certificate validity without incurring downtime for the endpoint.
Note:
You can determine the remaining time to expiration of the endpoint certificate from the Oracle Key Vault Management console, by navigating to the Endpoints page and checking the Endpoint Certificate Expiration field.See Also:
Configuring Oracle Key Vault AlertsIf an endpoint is not rotated before its certificate expires, it will experience downtime. You must re-enroll the endpoint when that happens. You can rotate a single endpoint, or multiple endpoints at once. Rotating an endpoint generates a new certificate on Oracle Key Vault. The endpoint must then reach out to Oracle Key Vault to receive this new certificate, and subsequently acknowledge receipt of the certificate back to Oracle Key Vault to fully complete the certificate rotation.
To rotate the endpoint certificates, perform the following steps.
- Guidelines for Rotating Endpoint Certificates
Consider these Oracle Key Vault guidelines before you rotate an endpoint certificate.
Related Topics
Parent topic: Deleting, Suspending, Reenrolling, or Rotating Endpoints
12.2.5.6.1 Guidelines for Rotating Endpoint Certificates
Consider these Oracle Key Vault guidelines before you rotate an endpoint certificate.
Guidelines for Endpoint Certificate Rotation
- Do not rotate an endpoint certificate while a CA certificate rotation is in progress.
- Do not rotate an endpoint certificate rotation while a server or node certificate rotation is in progress.
- Do not alter the Endpoint Certificate Validity parameter while an endpoint certificate rotation is in progress.
- Consider rotating an endpoint from a node in the cluster subgroup that the endpoint is associated with.
- Do not rotate an endpoint if its certificate has already expired. Consider re-enrolling it instead.
- Consider re-enrolling an endpoint if it does not receive its new certificate due to network or other issues.
- Ensure that the endpoint software has been upgraded to version 21.5.0.0.0 or later before rotating the endpoint.
Related Topics
Parent topic: Rotating Endpoint Certificates
12.3 Managing Endpoint Details
Endpoint details refers to endpoint name, type, description, platform, and email, and adding the endpoint to a group, or upgrading the endpoint software.
- About Endpoint Details
The Endpoint Details page provides a consolidated view of the endpoint. - Modifying Endpoint Details
You can modify the endpoint name, endpoint type, description, platform, and email.
Parent topic: Managing Oracle Key Vault Endpoints
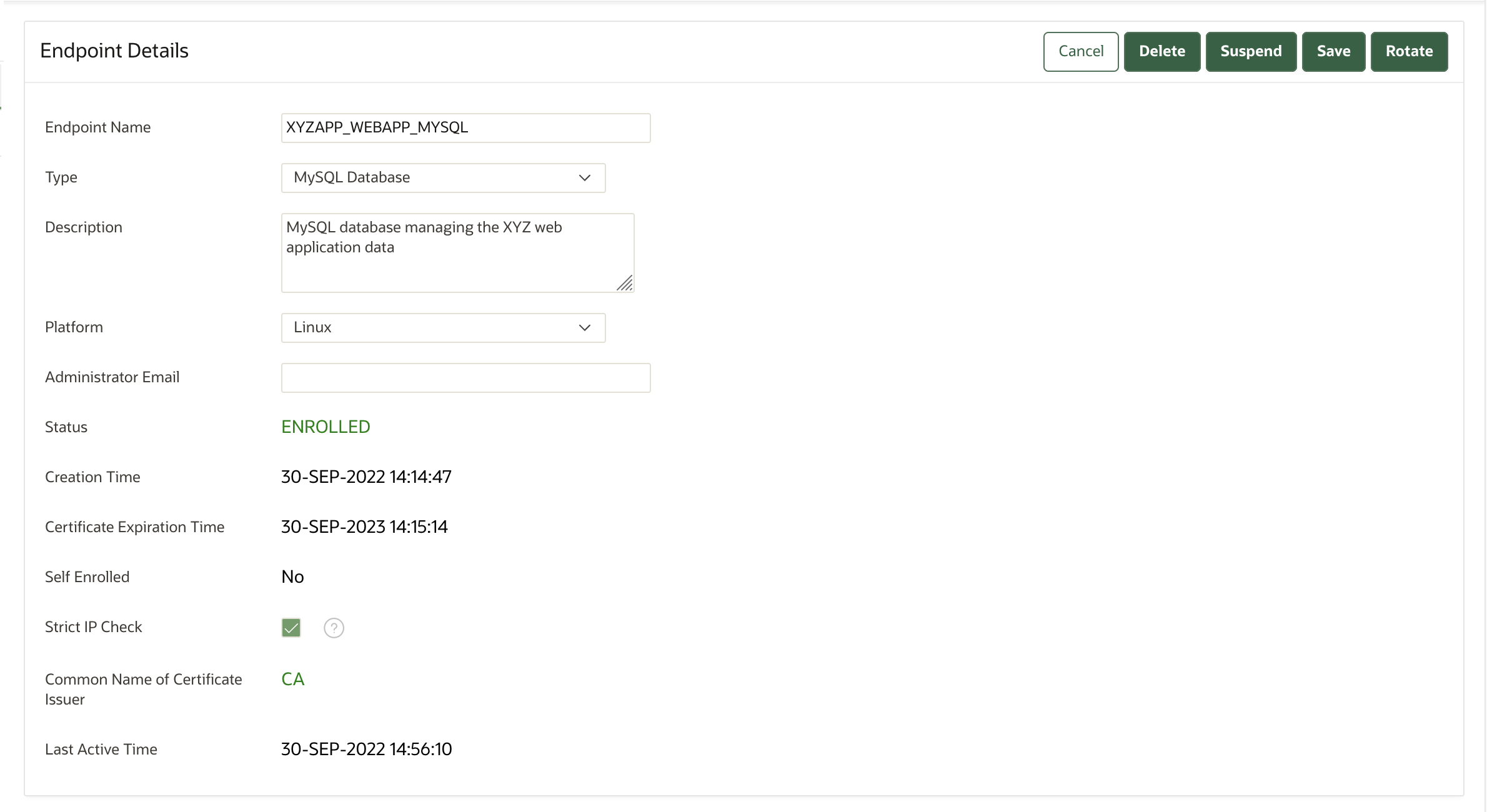
12.3.1 About Endpoint Details
The Endpoint Details page provides a consolidated view of the endpoint.
To access this page, you can select the Endpoints tab and then click the name of an endpoint. From here you can modify endpoint details and complete endpoint management tasks. (The following screen shows a partial view.)
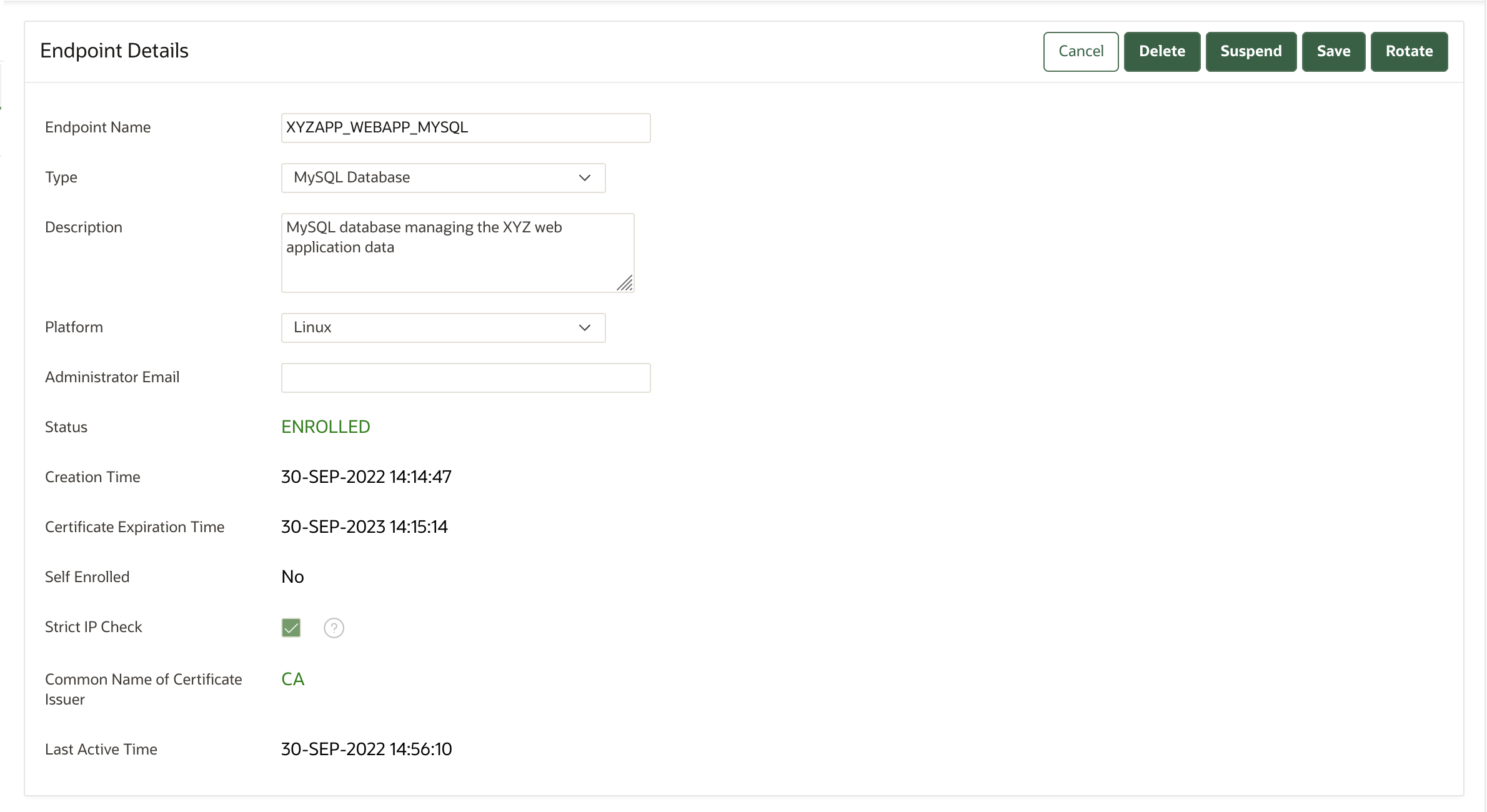
Description of the illustration 21.5_endpoint_details.png
Parent topic: Managing Endpoint Details
12.3.2 Modifying Endpoint Details
You can modify the endpoint name, endpoint type, description, platform, and email.
PENDING state by the creator on the node on which it was created.
Parent topic: Managing Endpoint Details
12.4 Managing Global and Per-Endpoint Configuration Parameters and Settings
Oracle Key Vault provides global and per-endpoint configuration parameters and settings that you can set in the Oracle Key Vault management console.
- About Managing Global and Per-Endpoint Configuration Parameters and Settings
Users who have the System Administrator role or the Key Administrator role can centrally update certain endpoint configuration parameters and settings in the Oracle Key Vault management console. - Global Endpoint Configuration Parameters and Settings
You can set endpoint configuration parameters and settings globally for all endpoints in the Oracle Key Vault management console. - Per-Endpoint Configuration Parameters and Settings
You can set different endpoint configuration parameters and settings for individual endpoints in the Oracle Key Vault management console.
Parent topic: Managing Oracle Key Vault Endpoints
12.4.1 About Managing Global and Per-Endpoint Configuration Parameters and Settings
Users who have the System Administrator role or the Key Administrator role can centrally update certain endpoint configuration parameters and settings in the Oracle Key Vault management console.
Setting endpoint configuration parameters and settings globally (for all endpoints) or on a per-endpoint basis simplifies the process of managing multiple endpoints for system and key administrators.
You can perform the following types of global endpoint and per-endpoint settings:
- Endpoint configuration parameters: These include settings that control features such as the length of time that a certificate is valid, timeouts for various PKCS 11 settings, and the timeout in seconds for a client's attempt to connect to an Oracle Key Vault server. Only a user who has the System Administrator role or the Manage Endpoint privilege for a specific endpoint can modify these parameters. Users who have the System Administrator role can modify endpoint configuration parameters for all endpoints. Users who have the Manage Endpoint privilege can modify the configuration parameters individually for each endpoint to which they have access. To do so, this user must go to the Details page for the endpoint, scroll to the bottom, and then modify the endpoints from there.
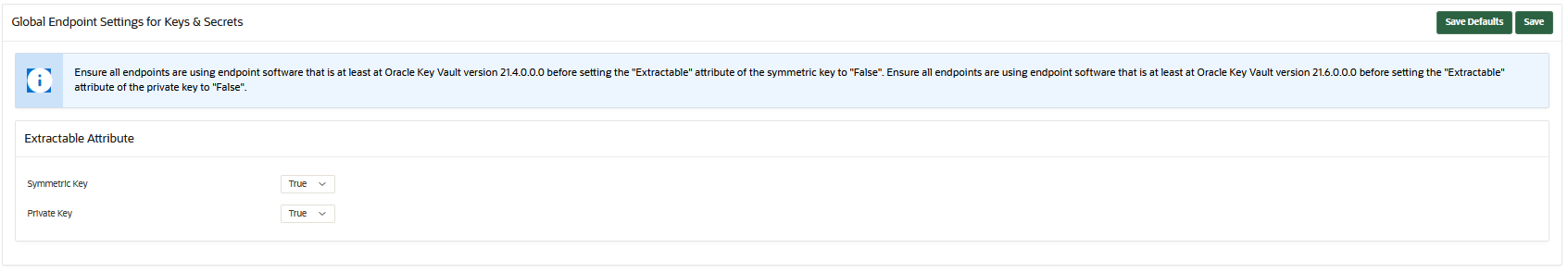
- Keys and secrets: This includes setting the extractable attribute value for symmetric keys. Only a user who has the Key Administrator role can modify this setting.
When Changes in Global and Per-Endpoint Values Take Effect
The configuration parameter values that are set in the Oracle Key Vault management console are applied to endpoints dynamically. The next time that the endpoint contacts Oracle Key Vault server, the updated configuration parameters are applied to the endpoint. If there is an error, then the update is not applied.
If you use the RESTful services utility, then Oracle Key Vault does not update the
endpoint configuration. In this case, use okvutil, C SDK, JAVA SDK,
or the PKCS11 library to apply the endpoint configuration updates.
In a multi-master cluster, replication of configuration parameters and settings depends on the replication lag. It is possible that an endpoint will not be able to get an update immediately because the node to which it is connected may not yet have received the new values of the parameters or settings. The endpoint will refresh its configuration when it connects to a node that has new values or if it has not refreshed its configuration in the past hour.
Precedence and Inheritance of Global and Per-Endpoint Values
Values that are set for an individual endpoint take precedence over the same values that are set globally. Global parameters and settings take effect when endpoint-specific parameters and settings are cleared. Oracle Key Vault uses the default system parameters and settings if both the global and endpoint specific parameters are cleared or not set from Oracle Key Vault management console.
In the case of keys and secrets, suppose you create a new symmetric key or private key but do not specify an extractable attribute value at the time of the symmetric or private key's creation. The key will inherit the default value that has been set for the individual endpoint in which the symmetric or private key was created. If the default extractable attribute value has not been set for this endpoint, then the key will inherit the global endpoint value for the extractable attribute. If this global endpoint value has not been set, then the extractable attribute value defaults to true. Suppose later on, you change the global endpoint extractable attribute value so that future endpoints will use this value. Similar to configuration parameters, the values set in the individual endpoint that already exists take precedence over the same value that is set globally.
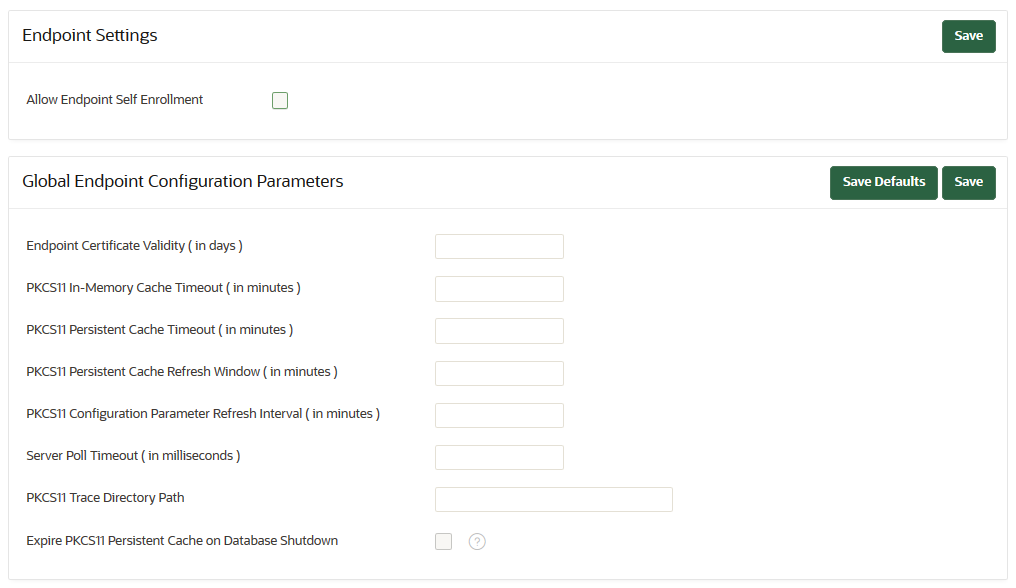
12.4.2 Global Endpoint Configuration Parameters and Settings
You can set endpoint configuration parameters and settings globally for all endpoints in the Oracle Key Vault management console.
- Setting Global Endpoint Configuration Parameters
You can set global endpoint configuration parameters in the Oracle Key Vault management console. - Configuring Global Endpoint Settings for Keys and Secrets
You can set the default extractable attribute value for new symmetric keys that you create or register in the endpoint configuration.
12.4.2.1 Setting Global Endpoint Configuration Parameters
You can set global endpoint configuration parameters in the Oracle Key Vault management console.
Related Topics
- PKCS11_CACHE_TIMEOUT Parameter
- PKCS11_PERSISTENT_CACHE_TIMEOUT Parameter
- PKCS11_PERSISTENT_CACHE_REFRESH_WINDOW Parameter
- PKCS11_CONFIG_PARAM_REFRESH_INTERVAL Parameter
- EXPIRE PKCS11 PERSISTENT CACHE ON DATABASE SHUTDOWN Parameter
- About Configuring Certificate Validity Period for Endpoint Certificates
Parent topic: Global Endpoint Configuration Parameters and Settings
12.4.2.2 Configuring Global Endpoint Settings for Keys and Secrets
You can set the default extractable attribute value for new symmetric keys that you create or register in the endpoint configuration.
Parent topic: Global Endpoint Configuration Parameters and Settings
12.4.3 Per-Endpoint Configuration Parameters and Settings
You can set different endpoint configuration parameters and settings for individual endpoints in the Oracle Key Vault management console.
- Modifying Configuration Parameters for an Individual Endpoint
A user who has the System Administrator role or the Manage Endpoint privilege can set configuration parameters for individual endpoints. - Configuring Endpoint Settings for Keys and Secrets for an Individual Endpoint
A user who has the Key Administrator role can set values for keys and secrets in an individual endpoint.
12.4.3.1 Modifying Configuration Parameters for an Individual Endpoint
A user who has the System Administrator role or the Manage Endpoint privilege can set configuration parameters for individual endpoints.
Parent topic: Per-Endpoint Configuration Parameters and Settings
12.4.3.2 Configuring Endpoint Settings for Keys and Secrets for an Individual Endpoint
A user who has the Key Administrator role can set values for keys and secrets in an individual endpoint.
Related Topics
Parent topic: Per-Endpoint Configuration Parameters and Settings
12.5 Default Wallets and Endpoints
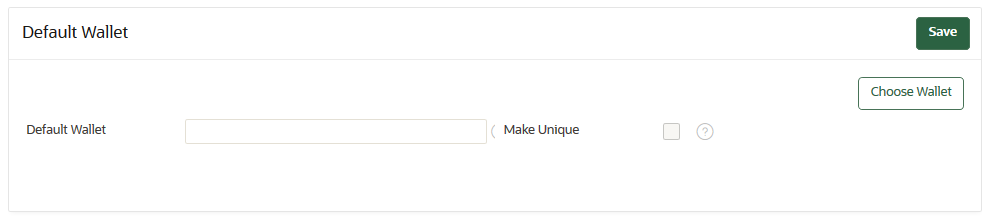
You can use a default wallet, which is a type of virtual wallet, with an endpoint.
- Associating a Default Wallet with an Endpoint
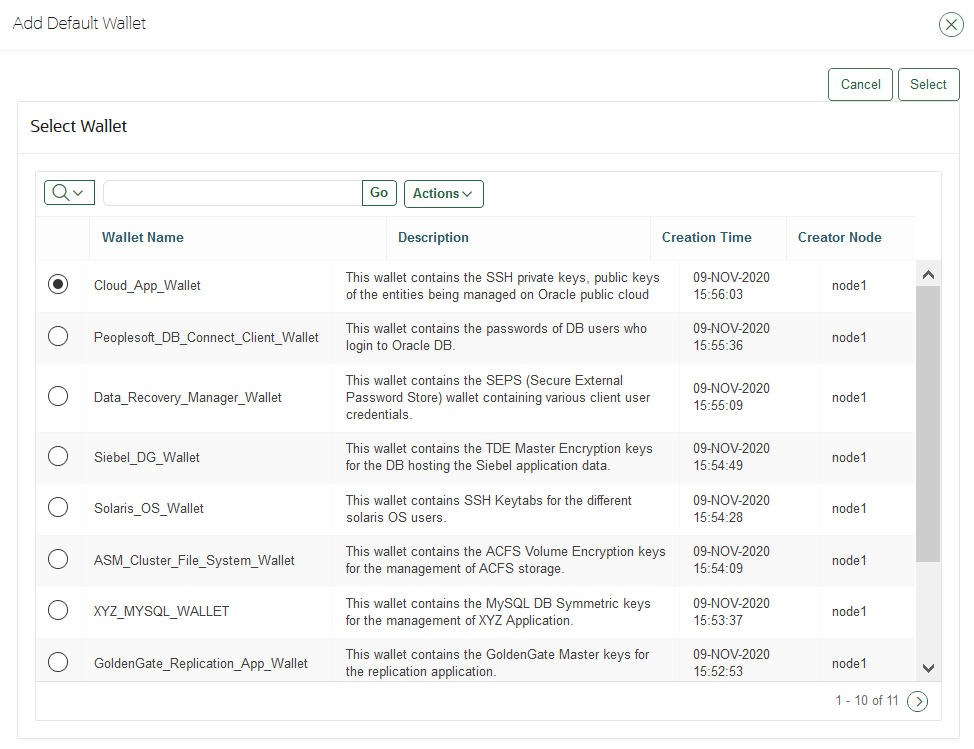
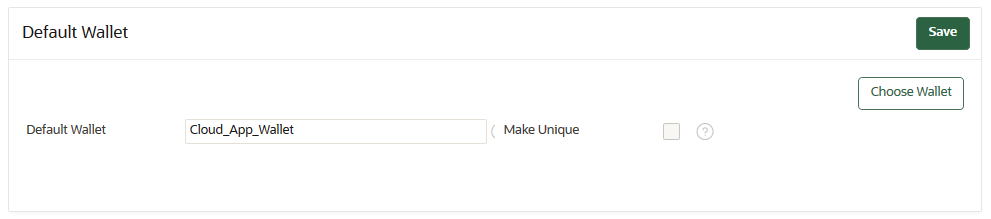
A default wallet is a type of virtual wallet to which security objects are uploaded when a wallet is not explicitly specified. - Setting the Default Wallet for an Endpoint
Setting a default wallet for an endpoint automatically uploads the endpoint's security objects to the wallet if another wallet is not explicitly specified.
Parent topic: Managing Oracle Key Vault Endpoints
12.5.1 Associating a Default Wallet with an Endpoint
A default wallet is a type of virtual wallet to which security objects are uploaded when a wallet is not explicitly specified.
Default wallets are useful for sharing with other endpoints such as nodes in an Oracle Real Application Clusters (Oracle RAC), or primary and standby nodes in Oracle Data Guard by having all endpoints use the same default wallet.
If you want to use the default wallet, then you must set this wallet after you register the endpoint before you enroll it. If you decide to use a default wallet after enrollment, then you must remove the default wallet and subsequently reenroll the endpoint.
An enrollment status of registered means that the endpoint has been added to Oracle Key Vault, but the endpoint software has not yet been downloaded and installed. When the status is registered, then you must associate the default wallet with the endpoint.
The endpoint's enrollment status becomes enrolled when you download and install the endpoint software to the endpoint. If you set the default wallet after you enroll the endpoint, then you must reenroll the endpoint to ensure that all future security objects created by the endpoint are automatically associated with that wallet.
In a multi-master cluster, you can only assign the default wallet on the same node where the endpoint and wallet were created when either are still in the PENDING state. After both are in the ACTIVE state, then there are no restrictions. After the default wallet is assigned and the endpoint is enrolled, the default wallet can be accessed from any node, as long as both are in the ACTIVE state and the information has been replicated to that node.
Parent topic: Default Wallets and Endpoints
12.5.2 Setting the Default Wallet for an Endpoint
Setting a default wallet for an endpoint automatically uploads the endpoint's security objects to the wallet if another wallet is not explicitly specified.
Parent topic: Default Wallets and Endpoints
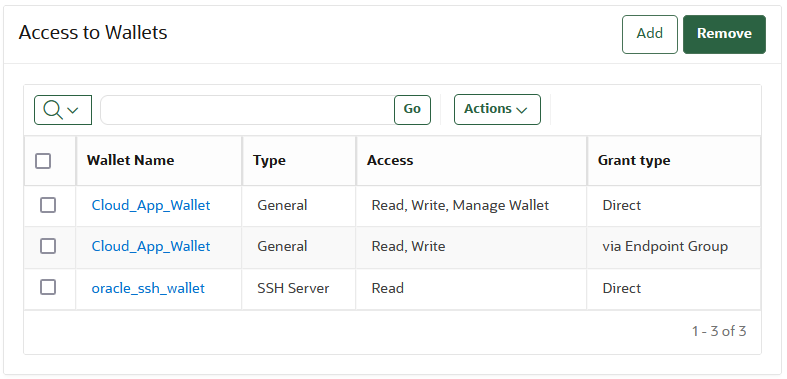
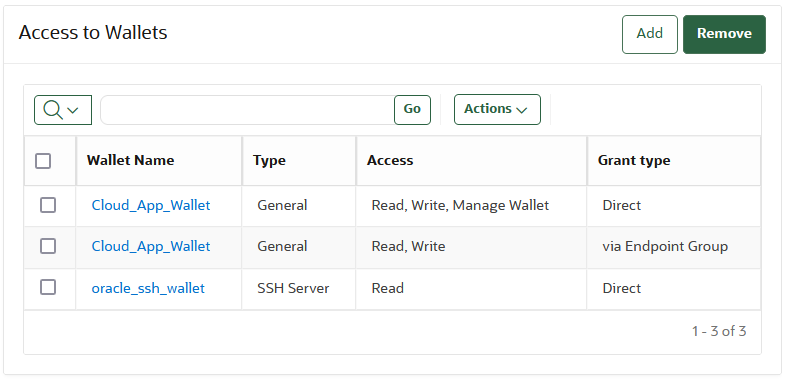
12.6 Managing Endpoint Access to a Virtual Wallet
You can grant an endpoint access to a virtual wallet, and revoke or modify access when it is no longer necessary.
- Granting an Endpoint Access to a Virtual Wallet
An endpoint must have the Read, Modify, and Manage Wallet privileges on the wallet before security objects can be uploaded or downloaded. - Revoking Endpoint Access to a Virtual Wallet
You can revoke access to a virtual wallet for an endpoint by using the Endpoints tab. - Viewing Wallet Items Accessed by Endpoints
The term wallet items refers to the security objects to which the endpoint has access.
Parent topic: Managing Oracle Key Vault Endpoints
12.6.1 Granting an Endpoint Access to a Virtual Wallet
An endpoint must have the Read, Modify, and Manage Wallet privileges on the wallet before security objects can be uploaded or downloaded.
Related Topics
Parent topic: Managing Endpoint Access to a Virtual Wallet
12.6.2 Revoking Endpoint Access to a Virtual Wallet
You can revoke access to a virtual wallet for an endpoint by using the Endpoints tab.
Parent topic: Managing Endpoint Access to a Virtual Wallet
12.6.3 Viewing Wallet Items Accessed by Endpoints
The term wallet items refers to the security objects to which the endpoint has access.
Parent topic: Managing Endpoint Access to a Virtual Wallet
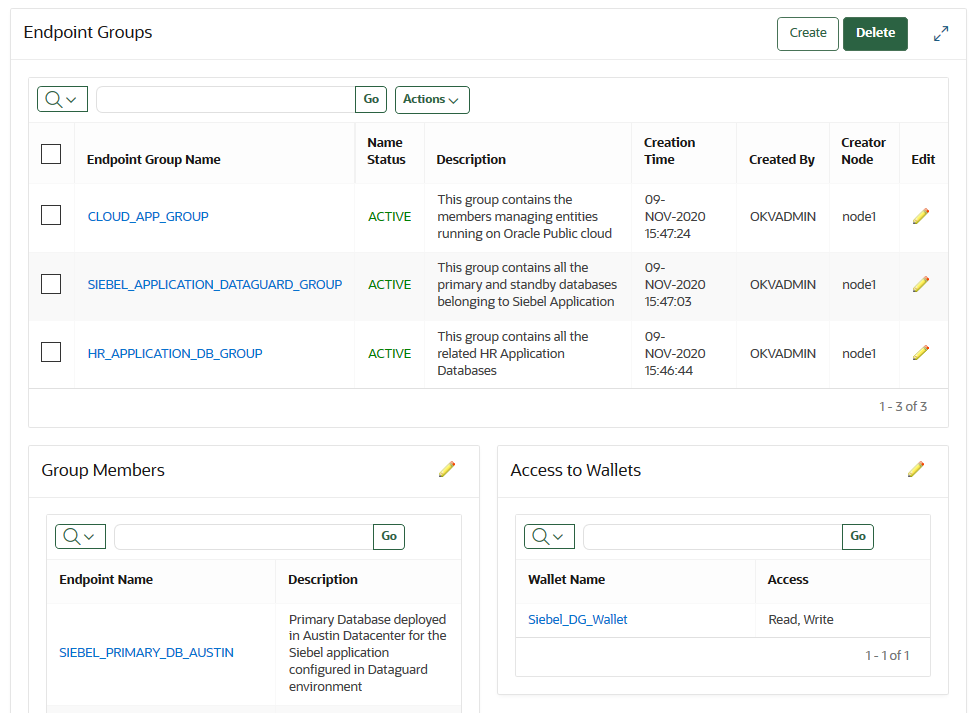
12.7 Managing Endpoint Groups
An endpoint group is a named group of endpoints that share a common set of wallets.
- How a Multi-Master Cluster Affects Endpoint Groups
You can create endpoint groups on any node and they will have a cluster-wide presence. - Creating an Endpoint Group
Endpoints that must share a common set of security objects stored in wallets can be grouped into an endpoint group. - Modifying Endpoint Group Details
You can add endpoints and access mappings to an endpoint group after creating the endpoint group. - Granting an Endpoint Group Access to a Virtual Wallet
You can grant an endpoint group access to a virtual wallet. - Adding an Endpoint to an Endpoint Group
You can add an endpoint to a named endpoint group. - Removing an Endpoint from an Endpoint Group
When you remove an endpoint from an endpoint group, this removes access to wallets that are associated with that endpoint group. - Deleting Endpoint Groups
You can delete endpoint groups if their member endpoints no longer require access to the same virtual wallets.
Parent topic: Managing Oracle Key Vault Endpoints
12.7.1 How a Multi-Master Cluster Affects Endpoint Groups
You can create endpoint groups on any node and they will have a cluster-wide presence.
You can add, update, or delete endpoint groups in any node, but in read-write mode only.
The Oracle Key Vault server that becomes the initial node can have endpoint groups already created. These endpoint groups are used to initialize, or seed, the cluster. During induction, the endpoint groups in the cluster are replicated to a newly added node. Endpoint groups previously created in all other nodes added to the cluster will be removed during induction.
New endpoint groups added concurrently to the multi-master cluster on different nodes may have name conflicts. Oracle Key Vault automatically resolves any endpoint group name conflicts. These conflicts are displayed in a Conflicts Resolution page and key administrators can choose to rename them.
Related Topics
Parent topic: Managing Endpoint Groups
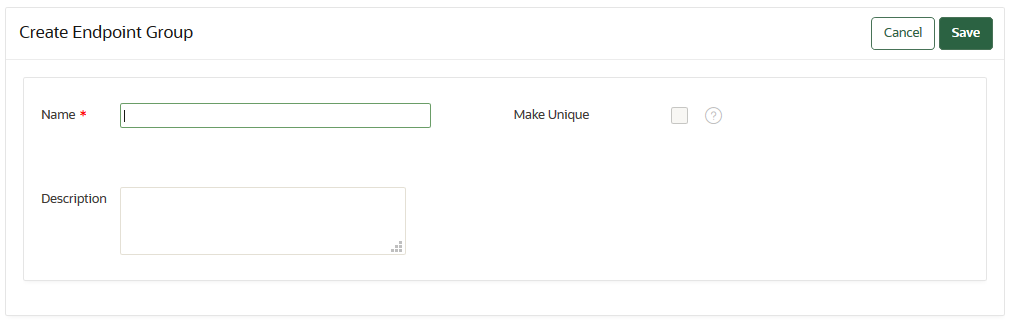
12.7.2 Creating an Endpoint Group
Endpoints that must share a common set of security objects stored in wallets can be grouped into an endpoint group.
Related Topics
Parent topic: Managing Endpoint Groups
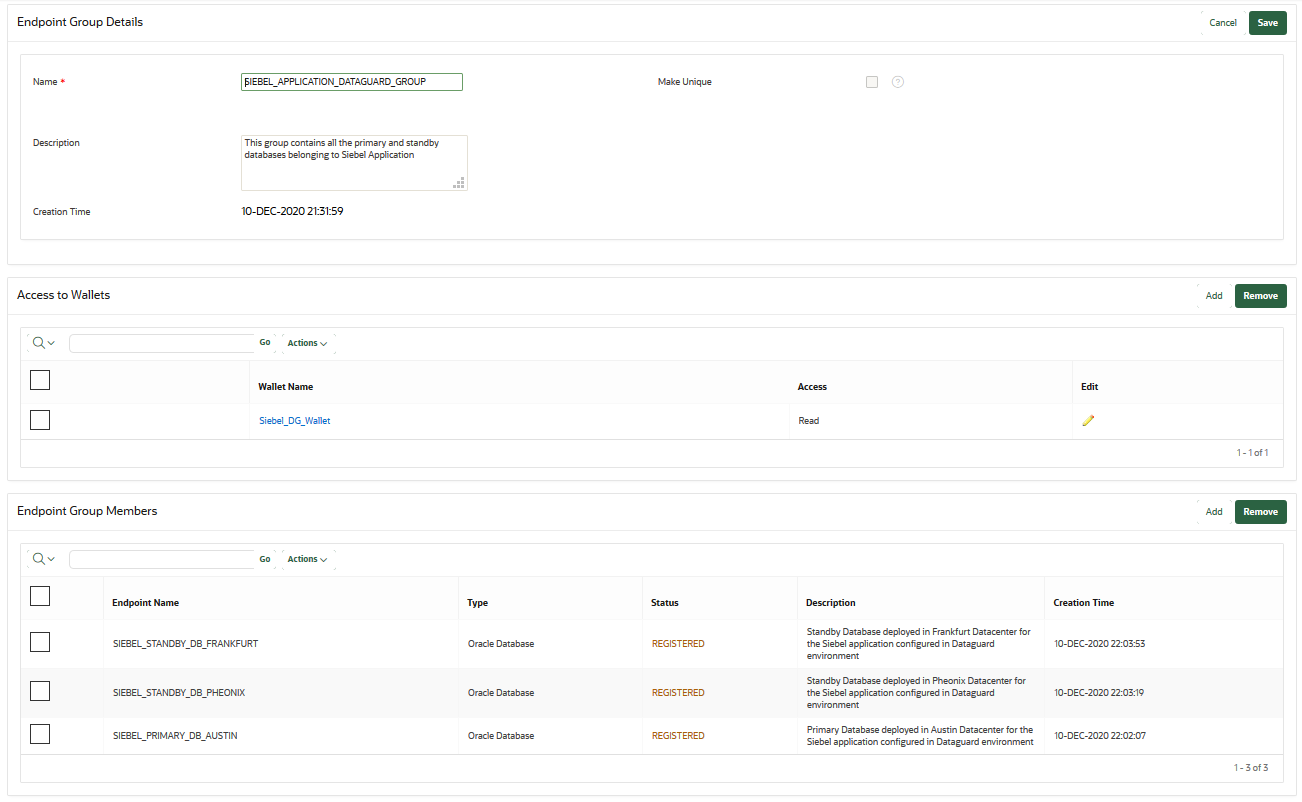
12.7.3 Modifying Endpoint Group Details
You can add endpoints and access mappings to an endpoint group after creating the endpoint group.
Parent topic: Managing Endpoint Groups
12.7.4 Granting an Endpoint Group Access to a Virtual Wallet
You can grant an endpoint group access to a virtual wallet.
PENDING state to a virtual wallet.
Related Topics
Parent topic: Managing Endpoint Groups
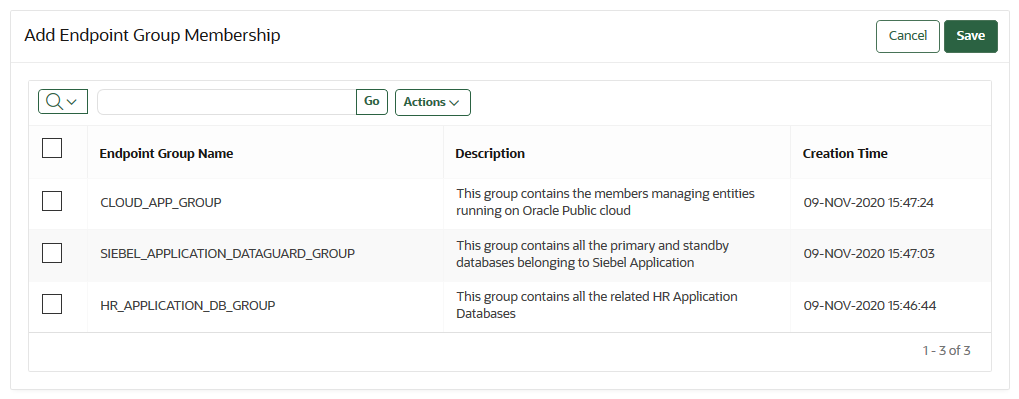
12.7.5 Adding an Endpoint to an Endpoint Group
You can add an endpoint to a named endpoint group.
PENDING state to an endpoint group. Also, you cannot add an endpoint to an endpoint group that is in the PENDING state.
Related Topics
Parent topic: Managing Endpoint Groups
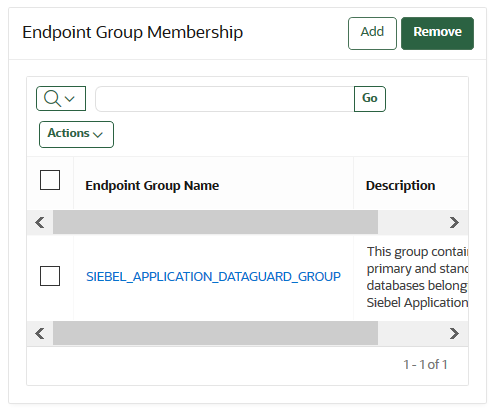
12.7.6 Removing an Endpoint from an Endpoint Group
When you remove an endpoint from an endpoint group, this removes access to wallets that are associated with that endpoint group.
PENDING state.
Parent topic: Managing Endpoint Groups
12.7.7 Deleting Endpoint Groups
You can delete endpoint groups if their member endpoints no longer require access to the same virtual wallets.
PENDING state if it has no members or access to wallets.
Parent topic: Managing Endpoint Groups