8 Authenticating and Authorizing Microsoft Azure Users for Oracle Databases
An Oracle database can be configured for Microsoft Azure users of Microsoft Entra ID (previously called Microsoft Azure AD) to connect using single sign-on authentication.
Note:
Microsoft recently changed the name of Microsoft Azure AD to Microsoft Entra ID. This name change is used in the current Oracle Database documentation. Earlier Oracle Database releases use the name Azure AD.- Introduction to Oracle Database Integration with Microsoft Entra ID
Before you begin configuring Microsoft Entra AD to access an Oracle database, you must understand the overall process. - Configuring the Oracle Database for Microsoft Entra ID Integration
The Microsoft Entra ID integration with the Oracle Database instance requires the database to be registered with Entra ID. - Mapping Oracle Database Schemas and Roles
Azure users will be mapped to one database schema and optionally to one or more database roles. - Configuring Entra ID Client Connections to the Oracle Database
You can configure client connections to connect with the registered database. - Configuring Microsoft Entra ID Proxy Authentication
Proxy authentication allows an Azure user to proxy to a database schema for tasks such as application maintenance. - Troubleshooting Microsoft Entra ID Connections
You can use trace files to diagnose problems with Microsoft Entra ID connections. You also can easily remedyORA-12599andORA-03114errors.
Parent topic: Managing User Authentication and Authorization
8.1 Introduction to Oracle Database Integration with Microsoft Entra ID
Before you begin configuring Microsoft Entra AD to access an Oracle database, you must understand the overall process.
- About Integrating Oracle Database with Microsoft Entra ID
Oracle Database and Microsoft Entra ID can be configured to allow users and applications to connect to the database using their Entra ID credentials. - Architecture of Oracle Database Integration with Microsoft Entra ID
Microsoft Azure Active Directory access tokens follow the OAuth 2.0 standard with extensions. - Azure Users Mapping to an Oracle Database Schema and Roles
Microsoft Azure users must be mapped to an Oracle Database schema and have the necessary privileges (through roles) before being able to authenticate to the Oracle Database instance. - Use Cases for Connecting to an Oracle Database Using Entra ID
Oracle Database supports several use cases for connecting to the database. - General Process of Authenticating Microsoft Entra ID Identities with Oracle Database
The Oracle Database administrator and the Microsoft Entra ID administrator play roles to allow Azure users to connect to the database using Entra IDOAuth2access tokens.
8.1.1 About Integrating Oracle Database with Microsoft Entra ID
Oracle Database and Microsoft Entra ID can be configured to allow users and applications to connect to the database using their Entra ID credentials.
Azure users and applications can log in with Entra ID Single Sign On (SSO) credentials to access the database. This is done with an Entra ID OAuth2 access token that the user or application first requests from Entra ID. This OAuth2 access token contains the user identity and database access information and is then sent to the database. Refer to Refer to the Microsoft article Passwordless authentication options for Azure Active Directory for information about configuring multi-factor and passwordless authentication.
You can perform this integration in the following Oracle Database environments:
- On-premises Oracle Database release 19.18 and later
- Oracle Autonomous Database Serverless
- Oracle Autonomous Database on Dedicated Exadata Infrastructure
- Oracle Base Database Service
- Oracle Exadata Cloud Service (Oracle ExaCS)
- All Oracle Database server platforms: Linux, Windows, AIX, Solaris, and HPUX
The instructions for configuring Entra ID use the term "Oracle Database" to encompass these environments.
This type of integration enables the Azure user to access an Oracle Database instance. Azure users and applications can log in with Entra ID Single Sign On (SSO) credentials to get an Entra ID OAuth2 access token to send to the database.
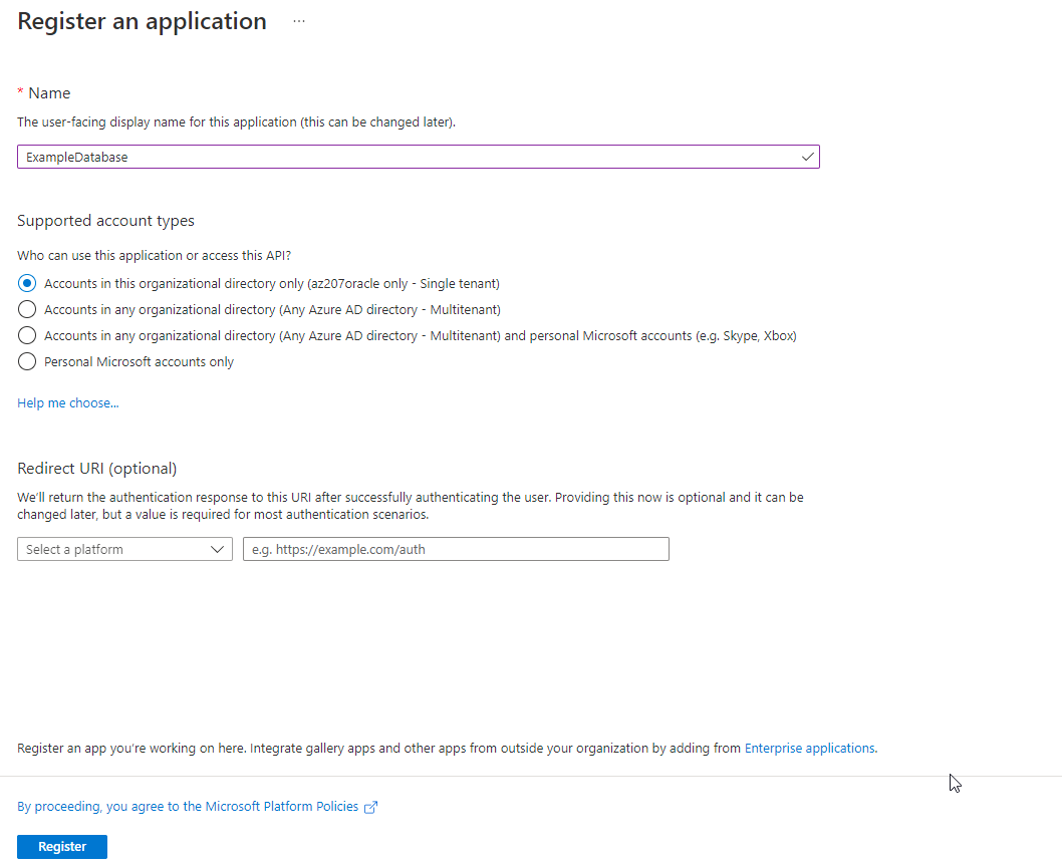
The Entra ID administrator creates and registers Oracle Database with Entra ID. Within Entra ID, this is called an app registration, which is short for application registration. This is the digital information that Entra ID must know about the software that is using Entra ID. The Entra ID administrator also creates application (app) roles for the database app registration in Entra ID. App roles connect Azure users, groups, and applications to database schemas and roles. The Entra ID administrator assigns Azure users, groups, or applications to the app roles. These app roles are mapped to a database global schema or a global role or to both a schema and a role. An Azure user, group, or application that is assigned to an app role will be mapped to a database global schema, global role, or to both a schema and a role. An Oracle global schema can also be mapped exclusively to an Azure user. An Azure guest user (non-organization user) or an Entra ID service principal (application) can only be mapped to a database global schema through an Entra ID app role. An Oracle global role can only be mapped from an Azure app role and cannot be mapped from an Azure user.
Tools and applications that are updated to support Entra ID tokens can authenticate users directly with Entra ID and pass the database access token to the Oracle Database instance. You can configure existing database tools such as SQL*Plus to use an Entra ID token from a file location. In these cases, Entra ID tokens can be retrieved using tools like Microsoft PowerShell or Azure CLI and put into a file location. An Entra ID OAuth2 database access tokens are issued with an expiration time. The Oracle Database client driver will ensure that the token is in a valid format and that it has not expired before passing it to the database. The token is scoped for the database, which means that there is information in the token about the database where the token will be used. The app roles the Entra ID principal was assigned to in the database Entra ID app registration are included as part of the access token. The directory location for the Entra ID token should only have enough permission for the user to write the token file to the location and the database client to retrieve these files (for example, just read and write by the user). Because the token allows access to the database, it should be protected within the file system.
Azure users can request a token from Entra ID using a number of methods to open an Azure login window to enter their Entra ID credentials.
Oracle Database accepts tokens representing the following Entra ID principals:
- Azure user, who is registered user in the Entra ID tenancy
- Guest user, who is registered as a guest user in the Entra ID tenancy
- Service, which is the registered application connecting to the database as itself with the client credential flow (connection pool use case)
Oracle Database supports the following Entra ID authentication flows:
- Interactive flow (also called authorization code flow) using Proof Key for Code Exchange (PKCE), most commonly used for human users (not applications) to authenticate to Entra ID in a client environment with a browser
- Client credentials, which are for database applications that connect as themselves (and not the end-user)
- On-Behalf-Of (OBO), where an application requests an access token on behalf of a logged-in user to send to the database
- Resource owner password credential (ROPC), which is not recommended for production use, but can be used in test environments where a pop-up browser user authentication would be difficult to incorporate. ROPC needs the Entra ID user name and password credential to be part of the token request call.
8.1.2 Architecture of Oracle Database Integration with Microsoft Entra ID
Microsoft Azure Active Directory access tokens follow the OAuth 2.0 standard with extensions.
The Entra ID access token will be needed before you access the database from the database client (for example, with SQLPlus or SQLcl). The Oracle clients (for example, OCI, JDBC, and ODP) can be configured to pick up an Entra ID token from a file location or the token can be passed to the client through the database client API. An Azure user can use a script (examples available from Microsoft) to retrieve a token and put it into a file location for the database client to retrieve. Applications can use the Azure SDK to get an access token and pass the token through the database client API. Command-line tools such as Microsoft PowerShell or the Azure command-line interface can be used to retrieve the Entra ID token if the application cannot directly get the token.
The following diagram is a generalized flow diagram for OAuth 2.0 standard, using the OAuth2 token. See Authentication flow support in MSAL in the Microsoft Entra ID documentation for more details about each supported flow.
Figure 8-1 Azure User Accessing the Database with the Interactive Authorization Code Flow
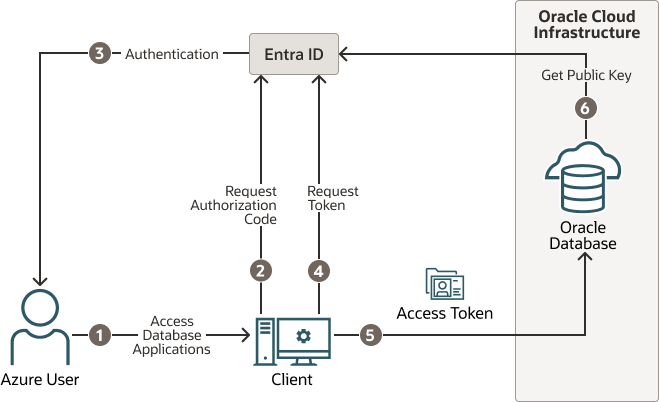
Description of "Figure 8-1 Azure User Accessing the Database with the Interactive Authorization Code Flow"
The authorization code flow is an OAuth2 standard and is described in detail as part of the standards. There are two steps in the flow. The first step authenticates the user and retrieves the authorization code. The second step uses the authorization code to get the database access token.
- The Azure user requests access to the resource, the Oracle Database instance.
- The database client or application requests an authorization code from Entra ID.
- Entra ID authenticates the Azure user and returns the authorization code.
- The helper tool or application uses the authorization code with Entra ID to exchange it for the
OAuth2token. - The database client sends the
OAuth2access token to the Oracle database. The token includes the database app roles the user was assigned to in the Entra ID app registration for the database. - The Oracle Database instance uses the Entra ID public key to verify that the access token was created by Entra ID.
Both the database client and the database server must be registered with the app registrations feature in the Azure Active Directory section of the Azure portal. The database client must be registered with Entra ID app registration. Permission must also be granted to allow the database client to get an access token for the database.
8.1.3 Azure Users Mapping to an Oracle Database Schema and Roles
Microsoft Azure users must be mapped to an Oracle Database schema and have the necessary privileges (through roles) before being able to authenticate to the Oracle Database instance.
In Microsoft Azure, an Entra ID administrator can assign users, groups, and applications to the database app roles.
Exclusively mapping an Entra ID user to a database schema requires the database administrator to create and manage a database schema for the lifecycle of the user (joining, moving, leaving). The database administrator must create the schema when the user joins the organization. The database administrator must also modify the privileges and roles that are granted to the database schema to align them with the tasks the Azure user is assigned to. When the Azure user leaves the organization, the database administrator must drop the database schema so that an unused account is not left on the database. Using the database app roles enables the Entra ID administrator to control access and roles by assigning users to app roles that are mapped to global schemas and global roles. This way, user access to the database is managed by Entra ID administrators and database administrators do not need to create, manage, and drop schemas for every user.
An Azure user can be mapped to a database schema (user) either exclusively or through an app role.
- Creating an exclusive mapping between an Azure user and an Oracle Database schema. In this type of mapping, the database schema must be created for the Azure user. Database privileges and roles that are needed by the Azure user must be granted to the database schema. The database schema not only must be created when the Azure user is authorized to the database, but the granted privileges and roles must be modified as the Entra ID roles and tasks change. Finally, the database schema must be dropped when the Azure user leaves the organization.
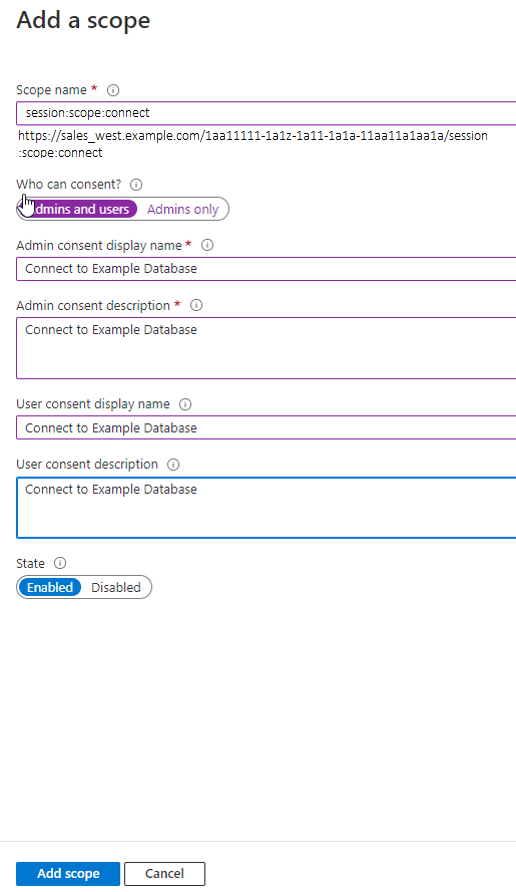
- Creating a shared mapping between an Entra ID app role and an Oracle Database schema. This type of mapping, which is more common than exclusive mappings, is for Azure users who have been assigned directly to the app role or is a member of an Entra ID group that is assigned to the app role. The app role is mapped to an Oracle Database schema (shared schema mapping). Shared schema mapping allows multiple Azure users to share the same Oracle Database schema so a new database schema is not required to be created every time a new user joins the organization. This operational efficiency allows database administrators to focus on database application maintenance, performance, and tuning tasks instead of configuring new users, updating privileges and roles, and removing accounts.
In addition to database roles and privileges being granted directly to the mapped global schema, additional roles and privileges can be granted through mapped global roles. Different Azure users mapped to the same shared global schema may need different privileges and roles. Azure app roles can be mapped to Oracle Database global roles. Azure users who are assigned to the app role or are a member of an Entra ID group that is assigned to the app role will be granted the Oracle Database global role when they access the database.
The following diagram illustrates the different types of assignments and mappings that are available.
Figure 8-2 Assignments and Mappings Between Entra ID and Oracle Database
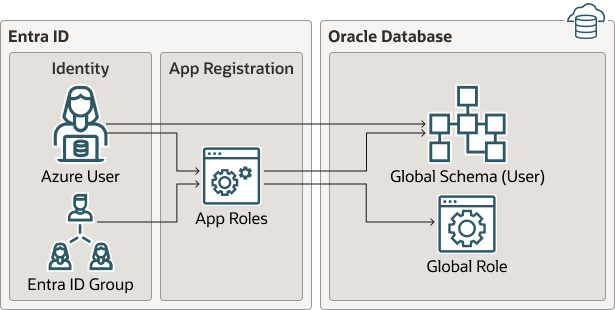
Description of "Figure 8-2 Assignments and Mappings Between Entra ID and Oracle Database"
These mappings are as follows:
- An Azure user can be mapped directly to an Oracle Database global schema (user).
- An Azure user, Entra ID group, or application is assigned to an app role, which is then mapped to either an Oracle Database global schema (user) or a global role.
8.1.4 Use Cases for Connecting to an Oracle Database Using Entra ID
Oracle Database supports several use cases for connecting to the database.
- OAuth2 authorization code flow: This is the most common flow for human users. The client directs the Azure user to Entra ID to get the authorization code. This code is used to get the database access token. See the Microsoft Azure article Microsoft identity platform and OAuth 2.0 authorization code flow.
- Resource owner password credentials (ROPC): This flow is not recommended for production servers. It is useful for test software that cannot work with a pop-up authentication window. It is used in non-graphic user interface environments when a pop-up window cannot be used to authenticate a user.
- Client credentials: This flow is used for applications to connect with the database. The application must register with Entra ID app registration and needs a client ID and client password. These client credentials must be used to get the database access token from Entra ID when the application connects to the database. The application can pass the token through the file system or through the database client API.
- On-behalf-of (OBO) token: An Azure application requests an OBO token for a logged in user. The OBO token will also be an access token for the database with the Azure user identity and assigned app roles for the database. This enables the Azure user to log in to the database as the user and not the application. Only an application can request an OBO token for its Azure user and pass it to the database client through the API.
8.1.5 General Process of Authenticating Microsoft Entra ID Identities with Oracle Database
The Oracle Database administrator and the Microsoft Entra ID administrator play roles to allow Azure users to connect to the database using Entra ID OAuth2 access tokens.
The general process is as follows:
- The Oracle Database administrator ensures that the Oracle Database environment meets the requirements for the Microsoft Entra ID integration. See Oracle Database Requirements for the Microsoft Entra ID Integration.
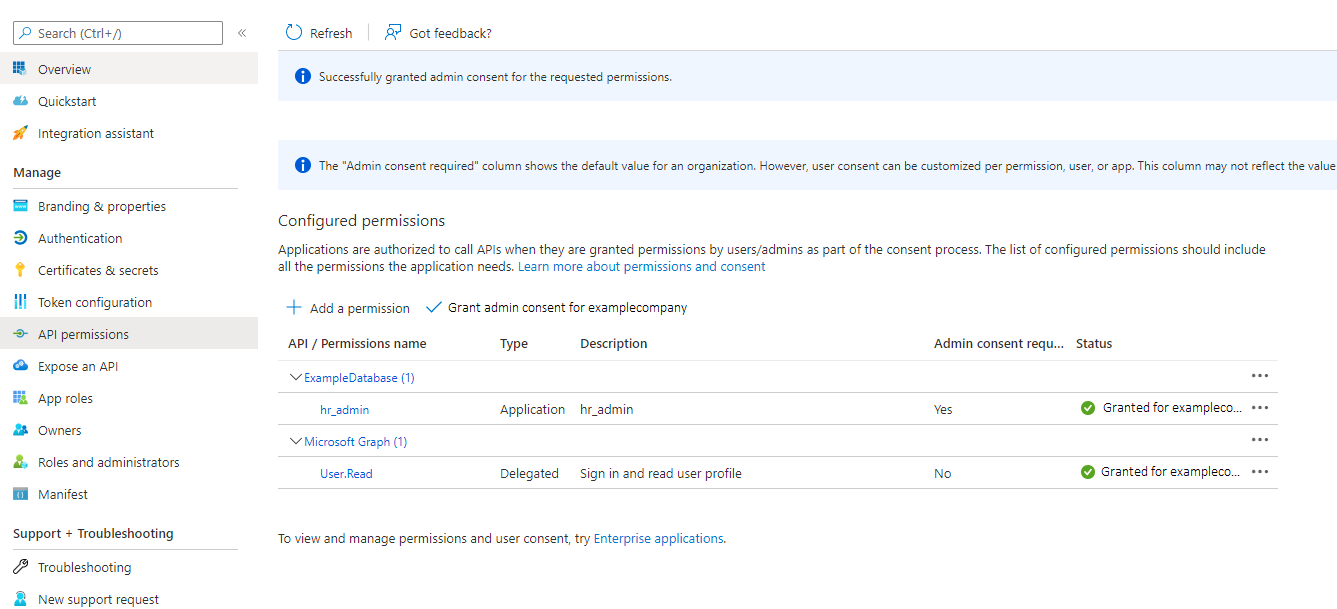
- The Entra ID administrator creates an Entra ID app registration for the database and the Oracle Database administrator enables the database to use Entra ID tokens for database access.
As part of the app registration process, the Entra ID administrator creates Azure app roles to be used for the mappings between the Azure users, groups, and applications to the Oracle Database schemas and roles.
- The Oracle Database administrator creates and maps global schemas to either an Azure user (exclusive schema mapping) or to an Azure app role (shared schema mapping). The Azure user or application must be mapped to one schema.
- Optionally, the Oracle administrator creates and maps global Oracle Database roles to Azure app roles.
- The Azure end user who wants to connect with the Oracle Database instance registers the client application as an Entra ID client (similar to how the Oracle database is registered).
The Entra ID client will have a client identification and a client secret, unless the application client is public. If the application client is public, then only the application client identification is necessary.
- The Azure user (who can be a database administrator) connects using an utility such as PowerShell or the Azure command-line interface to retrieve the
OAuth2database access token and store it in a local file directory. An application can also request an Entra IDOAuth2access token directly from Entra ID and pass it through a database client API. Refer to the following Oracle Database client documentation for information about passing Entra IDOAuth2tokens:- JDBC-thin clients: Oracle Database JDBC Developer’s Guide
- Oracle Call Interface (OCI): Oracle Call Interface Developer's Guide
- Oracle Data Provider for .NET (ODP): Oracle Data Provider for .NET Developer's Guide.Connecting to Oracle Database
- Once connected to the Oracle Database instance, the Azure end user performs database operations as needed.
8.2 Configuring the Oracle Database for Microsoft Entra ID Integration
The Microsoft Entra ID integration with the Oracle Database instance requires the database to be registered with Entra ID.
- Oracle Database Requirements for the Microsoft Entra ID Integration
Before you can configure an Oracle Database instance with Microsoft Entra ID, you must ensure that your environment meets special requirements. - Registering the Oracle Database Instance with a Microsoft Entra ID Tenancy
A user with Entra ID administrator privileges uses Microsoft Entra ID to register the Oracle Database instance with the Microsoft Entra ID tenancy. - Enabling Microsoft Entra ID v2 Access Tokens
To enable the Microsoft Entra ID v2 access token, you must configure it to use theupnattribute from the Azure portal. - Managing App Roles in Microsoft Entra ID
In Entra ID, you can create and manage app roles that will be assigned to Azure users and groups and also be mapped to Oracle Database global schemas and roles. - Enabling Entra ID External Authentication for Oracle Database
You need to enable Microsoft Entra ID external authentication with Oracle Database. - Disabling Entra ID External Authentication for Oracle Database
To disable Entra ID External authentication for an Oracle Database instance, you must use theALTER SYSTEMstatement.
8.2.1 Oracle Database Requirements for the Microsoft Entra ID Integration
Before you can configure an Oracle Database instance with Microsoft Entra ID, you must ensure that your environment meets special requirements.
Note the following:
- The Oracle Database server must be able to request the Entra ID public key. Depending on the enterprise network connectivity setup, you may need to configure a proxy setting.
- Users and applications that need to request an Entra ID token must also be able to have network connectivity to Entra ID. You may need to configure a proxy setting for the connection.
- You must configure Transport Layer Security (TLS) between the Oracle Database client and the Oracle Database server so that the token can be transported securely. This TLS connection can be either one-way or mutual.
- You can create the TLS server certificate to be self-signed or be signed by a well known certificate authority. The advantage of using a certificate that is signed by a well known Certificate Authority (CA) is that the database client can use the system default certificate store to validate the Oracle Database server certificate instead of having to create and maintain a local wallet with the root certificate. Note that this applies to Linux and Windows clients only.
8.2.2 Registering the Oracle Database Instance with a Microsoft Entra ID Tenancy
A user with Entra ID administrator privileges uses Microsoft Entra ID to register the Oracle Database instance with the Microsoft Entra ID tenancy.
8.2.3 Enabling Microsoft Entra ID v2 Access Tokens
To enable the Microsoft Entra ID v2 access token, you must configure it to use the upn attribute from the Azure portal.
- Check the version of the Entra ID access token that you are using.
- Log in to the Microsoft Entra ID portal.
- Search for and select Entra ID.
- Under Manage, select App registrations.
- Choose the application for which you want to configure optional claims based on your scenario and desired outcome.
- Under Manage, select Token configuration.
- Click Add optional claim and select upn.
Related Topics
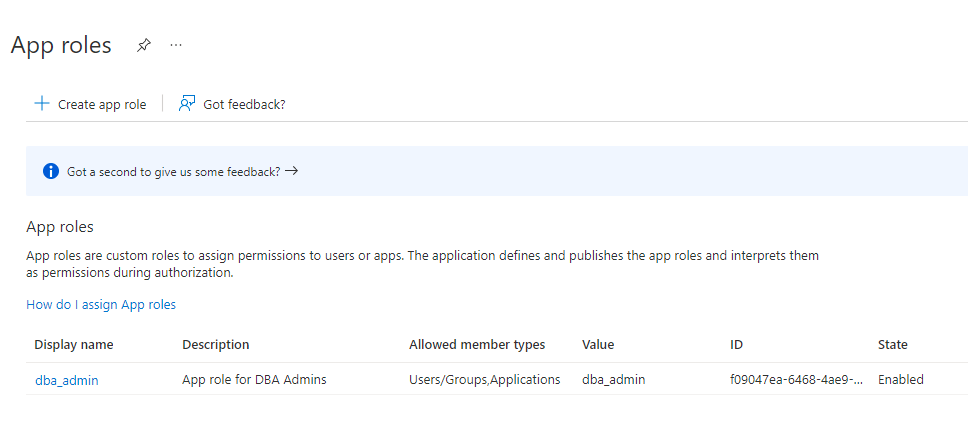
8.2.4 Managing App Roles in Microsoft Entra ID
In Entra ID, you can create and manage app roles that will be assigned to Azure users and groups and also be mapped to Oracle Database global schemas and roles.
- Creating a Microsoft Entra ID App Role
Azure users, groups, and applications that need to connect to the database will be assigned to the database app roles. - Assigning Users and Groups to the Microsoft Entra ID App Role
Before Microsoft Azure users can have access to the Oracle database, they must first be assigned to the app roles that will be mapped to Oracle Database schema users or roles. - Assigning an Application to an App Role
An application that must connect to the database using the client credential flow must to be assigned to an app role.
8.2.4.1 Creating a Microsoft Entra ID App Role
Azure users, groups, and applications that need to connect to the database will be assigned to the database app roles.
Parent topic: Managing App Roles in Microsoft Entra ID
8.2.4.2 Assigning Users and Groups to the Microsoft Entra ID App Role
Before Microsoft Azure users can have access to the Oracle database, they must first be assigned to the app roles that will be mapped to Oracle Database schema users or roles.
- Log in to Entra ID as an administrator who has privileges for assigning Azure users and Entra ID groups to app roles.
- In enterprise applications, find the name of the Oracle Database app registration that you created. This is automatically created when you create an app registration.
- Use the Directory + subscription filter to locate the Azure Active Directory tenant that contains the Oracle connection.
- Select Azure Active Directory.
- Under Manage, select Enterprise applications, and then select the Oracle Database app registration name that you registered earlier.
- Under Getting Started, select Assign users and groups.
- Select Add user/group.
- In the Add assignment window, select Users and groups to display a list of users and security groups.
- From this list, select the users and groups that you want to assign to the app role, and then click Select.
- In the Add assignment window, select Select a role to display a list of the app roles that you have created.
- Select the app role and then select Select.
- Click Assign.
Parent topic: Managing App Roles in Microsoft Entra ID
8.2.4.3 Assigning an Application to an App Role
An application that must connect to the database using the client credential flow must to be assigned to an app role.
Related Topics
Parent topic: Managing App Roles in Microsoft Entra ID
8.2.5 Enabling Entra ID External Authentication for Oracle Database
You need to enable Microsoft Entra ID external authentication with Oracle Database.
See the following platform-specific documentation for information about enabling Oracle Database for Entra ID external authentication, in addition to the information detailed in this document for on-premises (non-cloud) Oracle databases.
8.2.6 Disabling Entra ID External Authentication for Oracle Database
To disable Entra ID External authentication for an Oracle Database instance, you must use the ALTER SYSTEM statement.
To disable Entra ID from Oracle Autonomous Database Serverless, see Using Oracle Autonomous Database Serverless. The following procedure applies to all other platforms:
8.3 Mapping Oracle Database Schemas and Roles
Azure users will be mapped to one database schema and optionally to one or more database roles.
- Exclusively Mapping an Oracle Database Schema to a Microsoft Azure User
You can exclusively map an Oracle Database schema to a Microsoft Azure user. - Mapping a Shared Oracle Schema to an App Role
In this mapping, an Oracle schema is mapped to an app role. Therefore, anyone who has that app role would get the same shared schema. - Mapping an Oracle Database Global Role to an App Role
Oracle Database global roles that are mapped to Entra ID app roles give Azure users and applications additional privileges and roles above those that they have been granted through their login schemas.
8.3.1 Exclusively Mapping an Oracle Database Schema to a Microsoft Azure User
You can exclusively map an Oracle Database schema to a Microsoft Azure user.
Parent topic: Mapping Oracle Database Schemas and Roles
8.3.2 Mapping a Shared Oracle Schema to an App Role
In this mapping, an Oracle schema is mapped to an app role. Therefore, anyone who has that app role would get the same shared schema.
Parent topic: Mapping Oracle Database Schemas and Roles
8.3.3 Mapping an Oracle Database Global Role to an App Role
Oracle Database global roles that are mapped to Entra ID app roles give Azure users and applications additional privileges and roles above those that they have been granted through their login schemas.
Parent topic: Mapping Oracle Database Schemas and Roles
8.4 Configuring Entra ID Client Connections to the Oracle Database
You can configure client connections to connect with the registered database.
- About Configuring Client Connections to Entra ID
There are three different ways for an Oracle Database client to use an Entra IDOAuth2token to send to the database for access. - Operational Flow for SQL*Plus Client Connection to Oracle Database Using Microsoft Entra ID OAuth2 Token
The connection between the Azure user, Entra ID, and an Oracle database relies on the passing of theOAuth2token throughout these three components. - Supported Client Drivers for Entra ID Connections
Oracle Database supports several types of client drivers for Entra ID connections. - Registering a Client with Entra ID Application Registration
This type of registration is similar to registering Oracle Database with Entra ID app registration. - Configuration of Clients to Work with Microsoft Entra ID Tokens
Depending on the Oracle Database client, you can configure the client to either directly request the token from Entra ID or retrieve it from a file location. - Examples of Retrieving Entra ID OAuth2 Tokens Outside an Oracle Database Client
These examples show different ways that you can retrieve Entra IDOAuth2token separately from the database client if you are not using the database client to retrieve the tokens directly. - Creating a Network Proxy for the Database to Connect with the Internet
This network proxy will enable the Oracle database to reach the Entra ID endpoint. - Using Centralized Entra ID Services for Net Naming and Secrets
You can use the Azure app configuration and Azure Vault to centrally store net names and secrets.
8.4.1 About Configuring Client Connections to Entra ID
There are three different ways for an Oracle Database client to use an Entra ID OAuth2 token to send to the database for access.
-
Connect to Entra ID endpoint directly and retrieve the token for the user (interactive flow).
-
Retrieve the token from a file location (all supported Entra ID flows).
-
Pass the token to the client by using the client API (all supported Entra ID flows).
Oracle Database supports several Entra ID flows for different use cases. You should review the details of each flow in the Microsoft documentation. Each database client can support different flows with different versions. Details of these types are available in the JDBC, ODP.NET, and other platform-specific client documentation for the supported Entra ID flows for the client. This section focuses on the use of the OCI and Instant Clients, which are also called thick clients.
The types of available flows are as follows:
-
The interactive flow (also known as the OAuth2 authz flow) is the primary flow used by human actors. This flow requires an environment that can open a browser so that the user to enter their Entra ID credentials.
-
The device code flow is supported by some clients, but not currently with the OCI and Instant Clients. This type of flow is also for human actors but for environments that cannot open a browser.
-
The managed identity flow (supported by some clients, but not the OCI and Instant Clients) is for applications that run on Azure compute nodes and have access to the managed identity for the node.
-
The client credential flow is designed for applications, especially if they are not running in an Azure environment.
-
The Resource Owner Password Credential (ROPC) flow is not recommended for production use.
When a user must access the database as a human actor, Oracle recommends that you configure the interactive flow and configure the database client to retrieve the token directly from Entra ID. An application will need to use the client credential flow. Commonly, the application will use a script that is run periodically to retrieve a token from Entra ID and place it into a file location for the database client to use. If the application can be modified to integrate with the Entra ID SDK, then it can alternatively use the SDK to retrieve the token and pass it to the client using the client API.
You should choose the client connection method that works best with your use case. This guide provides examples of connecting SQL*Plus with different methods of getting an Entra ID OAuth2 access token. All Oracle Database release 19c clients can accept a token that is passed as a file or through the client API. The JDBC-thin, Instant Client, and ODP.net drivers also accept the token through the database client API from an application. Tools such as PowerShell or Azure CLI can retrieve the Entra ID OAuth2 access token for use by the client driver. To retrieve an Entra ID token, the client must be registered through the Entra ID app (application) registration process. Registering the client is similar to registering the Oracle Database server with Entra ID using the app registration. Both the database and client must be registered with Entra ID.
The database must be registered so the client can get permission to get an access token for the database. The client must be registered so that Entra ID can recognize a trusted client is asking for an access token.
See the following Microsoft Azure articles for more information about connecting clients to Entra ID:
8.4.2 Operational Flow for SQL*Plus Client Connection to Oracle Database Using Microsoft Entra ID OAuth2 Token
The connection between the Azure user, Entra ID, and an Oracle database relies on the passing of the OAuth2 token throughout these three components.
There are three ways for an Oracle Database client to send an Entra ID OAuth2 token to an Oracle database.
- Through the Oracle Database client
- By specifying a file location
- Using the the Oracle Database client API
Using an Oracle Database Client to Send the Entra ID OAuth2 Token to the Oracle Database
The Oracle Database client can request an OAuth2 token directly from the Entra ID endpoint. This method simplifies the required configuration. The following diagram shows the use of the interactive flow with a public client. The interactive flow is also called the OAuth2 authorization flow. See the Microsoft identity platform and OAuth2.0 authorization code flow Microsoft article for detailed information about the authorization flow.
Figure 8-3 Entra ID OAuth2 Tokens Sent to the Oracle Database Using Client
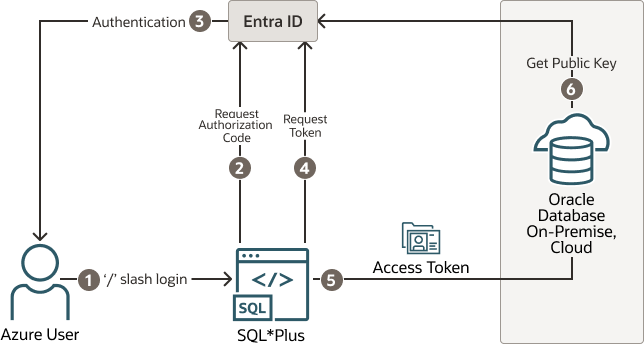
Description of "Figure 8-3 Entra ID OAuth2 Tokens Sent to the Oracle Database Using Client"
- The user uses a
/slash login to use the Azure SSO login. The connect string (orsqlnet.ora) includes all the parameters that are required for the Oracle Database client to get a token for the user. - The Oracle Database client connects with the Entra ID endpoint to request an authorization code.
- If the user has not logged in with Entra ID, then a browser window opens and requests the user to enter their Azure SSO credentials.
- The Oracle Database client requests an
OAuth2access token using the authorization code. - When the Oracle Database client receives the
OAuth2access token, it sends this token to the Oracle database. - The Oracle database verifies that the access token came from Entra ID (using the Entra ID public key) and then checks the token for additional claims. Next, the database finds the schema mapping (exclusive or shared) and creates the session. The database will also grant any global roles that the Azure user is also assigned to through an app role.
Specifying a File Location to Send the Entra ID OAuth2 Token to the Oracle Database
The following diagram illustrates how a file location can be used to send the Entra ID OAuth2 token to an Oracle database.
Figure 8-4 Entra ID OAuth2 Tokens Sent to the Oracle Database Using File Location
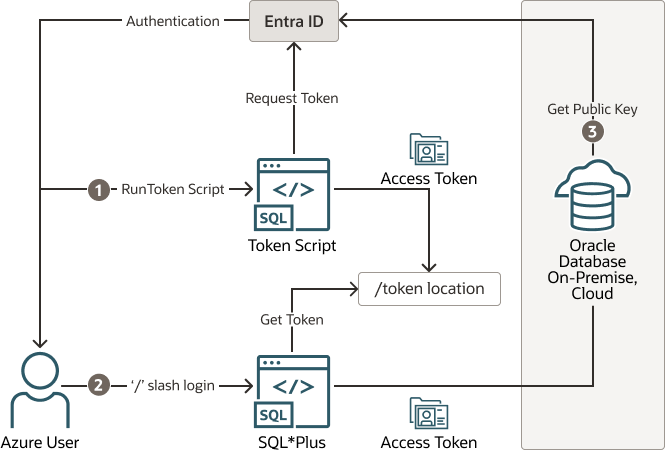
Description of "Figure 8-4 Entra ID OAuth2 Tokens Sent to the Oracle Database Using File Location"
- The Azure user requests an Entra ID access token for the database using a script and the returned token is written into a file called
tokenat a file location. The Azure user may be requested to authenticate with Entra ID at this time. - The Azure user connects to the database using the
/slash login. Either thesqlnet.oraortnsnames.oraconnection string tells the Oracle Instant Client that an Entra IDOAuth2token is needed and to retrieve it from a specified file location. The access token is then sent to the Oracle database. - The Oracle database verifies that the access token came from Entra ID (using the Entra ID public key) and then checks the token for additional claims. The database then finds the schema mapping (exclusive or shared) and creates the database session. The database will also grant any global roles that the Azure user is also assigned to through an app role.
Using the Oracle Database Client API to Send the Entra ID OAuth2 Token to the Oracle Database
The following diagram illustrates how the Oracle Database Client API can be used to send the Entra ID OAuth2 Token to the Oracle database.
Figure 8-5 Entra ID OAuth2 Tokens Sent to the Oracle Database Using the Client API
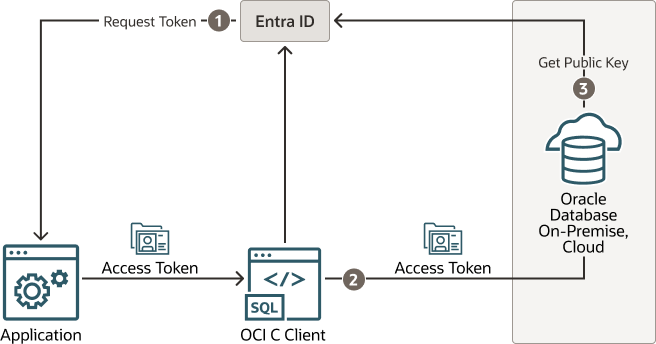
Description of "Figure 8-5 Entra ID OAuth2 Tokens Sent to the Oracle Database Using the Client API"
- The application requests an Entra ID access token for the Oracle database using a script. The returned token is then sent to the database client using the client API. The token can represent the user (on-behalf-of token flow) or the application (client credential flow)
- The Oracle Database client sends the access token to the Oracle database.
- The Oracle database verifies that the access token came from Entra ID (using the Entra ID public key) and then checks the token for additional claims. The database finds the schema mapping (exclusive or shared) and creates the session. The database will also grant any global roles that the application or user is assigned to through an app role.
8.4.3 Supported Client Drivers for Entra ID Connections
Oracle Database supports several types of client drivers for Entra ID connections.
Oracle recommends that you use the latest quarterly patch for the supported versions because enhancements are added with the quarterly releases. In addition, some features will only exist in the Oracle Database 23ai version and will not be backported.
- Thick clients (OCI C driver, Oracle Instant Client, Oracle Data Provider - Unmanaged (ODP.NET-Unmanaged), JDBC-thick, and others based on OCI C driver): Oracle Database 19.16 (July 2022) and above, not supported with 21c, fully supported with Database 23ai
- JDBC-thin: Oracle Database 19.16 (July 2022), Oracle Database 21.8 (October 2022)
- Oracle Data Provider (ODP.NET core, managed): Oracle Database 19.16, Oracle Database 21.7
- Python-thin: 1.1.0+
- Node.js-thin: v6.3+
8.4.4 Registering a Client with Entra ID Application Registration
This type of registration is similar to registering Oracle Database with Entra ID app registration.
- Confidential and Public Client Registration
You can register the database client with Entra ID as either confidential or public depending on your use case. - Registering a Database Client App with Entra ID
Creating the client app registration is similar to creating the Oracle Database instance with the Microsoft Entra ID tenancy.
8.4.4.1 Confidential and Public Client Registration
You can register the database client with Entra ID as either confidential or public depending on your use case.
See the Microsoft Azure article Authentication flows and application scenarios for detailed information about authentication flows and application scenarios.
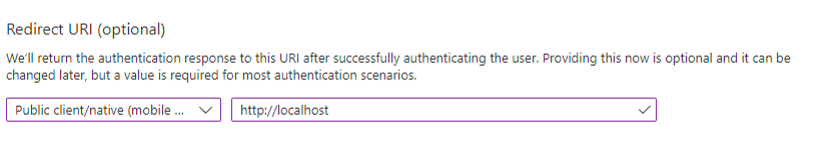
Registering a confidential client app requires that the client have a secret, in addition to the client ID. The confidential client app uses both the client ID and the secret when it makes Entra ID requests. However, in an enterprise, it is not practical for every SQL*Plus and SQLcl user to create a separate app registration with its own secret. In addition, a secret is no longer a secret when you start to share it within an organization. It is far better to just create a public client app. A public client app does not have a secret; it only has a client ID. All database tool users can use the public client ID when they connect to Entra ID to get an access token. The Azure user still needs to authenticate to Entra ID with their own user credential.
8.4.5 Configuration of Clients to Work with Microsoft Entra ID Tokens
Depending on the Oracle Database client, you can configure the client to either directly request the token from Entra ID or retrieve it from a file location.
- Configuring Clients to Work with Microsoft Entra ID Tokens
There are different ways to configure your database client to work with Entra IDOAuth2access tokens. - Enabling Clients to Directly Retrieve Entra ID Tokens
You can set parameters to enable clients to directly retrieve Entra ID tokens on their own. - Enabling Clients to Retrieve Entra ID Tokens from a File Location
If you choose to retrieve the Entra ID location from a file location when you use the/slash login, then you will need to configure your client.
8.4.5.1 Configuring Clients to Work with Microsoft Entra ID Tokens
There are different ways to configure your database client to work with Entra ID OAuth2 access tokens.
OAuth2 token from the Entra ID endpoint. In other cases, a separate utility will need to be run to get the token and put it into a file location for use by the database client. An application can also use the Azure SDK to get a token and send it through the database client API. Refer to the database client specific documentation for using the client API and for client configuration information. Before you can request a token from Entra ID, you must perform the following configuration.
OAuth2 tokens. You can use TLS (server authentication) or mTLS (client and server authentication). If your database client and platform support it, then you can simply use your system default certificate store when using TLS and not use a wallet. In addition to using TLS, you must specify either partial or full DN matching (SSL_SERVER_DN_MATCH = ON).
8.4.5.2 Enabling Clients to Directly Retrieve Entra ID Tokens
You can set parameters to enable clients to directly retrieve Entra ID tokens on their own.
Oracle Database clients differ by platform and version for what flows they support. The following table shows what each client can support.
Table 8-1 Parameters to Directly Retrieve Tokens
| Database Clients | Passing Using Client API | Using File Location | Database Client Direct Support |
|---|---|---|---|
|
Thick clients (OCI C driver, Instant Clients Along with platform specific drivers that use the thick client (for example, JDBC-thick, ODP.NET unmanaged, Python-thick) |
Client versions 19.16+, not 21c, all 23ai Supported for all flows (interactive, client credential, OBO, ROPC) |
Client versions 19.16+, not 21c, all 23ai Supported for all flows (interactive, client credential, OBO, ROPC) |
Client version 23.4+ Interactive flow support only |
|
JDBC-thin |
Client versions 19.16+, 21.7+, all 23ai Supported for all flows (interactive, client credential, OBO, ROPC) |
Client versions 19.16+, 21.7+, all 23ai Supported for all flows (interactive, client credential, OBO, ROPC) |
Client version 23ai Supports the following flows (interactive, device code, client credential, managed identity, OBO, ROPC) |
|
ODP.NET core, managed |
Client versions 19.16+, 21.7+, all 23ai Supported for all flows (interactive, client credential, OBO, ROPC) |
Client versions 19.16+, 21.7+, all 23ai Supported for all flows (interactive, client credential, OBO, ROPC) |
Client version 23ai Supports the following flows (interactive, device code, client credential, managed identity, OBO, ROPC) |
|
Python-thin |
Not supported |
Not supported |
Not supported |
|
Node.js |
Not supported. |
Not supported |
Not supported |
The connect string parameters are common across the database clients. Refer to each database client documentation (JDBC-thin, ODP.NET core, managed) for more specific information regarding this feature with those drivers. The following information is specifically for the OCI thick client/Instant client. However, the information about connect string parameters will remain consistent across the drivers.
To enable this feature in the client to get a token directly from Entra ID for a supported flow, you must set the following parameters in either the client's sqlnet.ora file or in a connect string. The connect string takes precedence over sqlnet.ora.
Table 8-2 Parameters to Directly Retrieve Tokens
| Parameter | Description |
|---|---|
|
|
Sets the token authentication. This parameter is mandatory when you are asking the database client to get the database token or pick it up from a file location. This parameter is not required when you are passing the token through the client API. Enter one of the following values:
|
|
|
The unique application (client) ID assigned to your app by Entra ID when the app was registered. This app is your database client that will request to get an access token for the database for the user. This is not the client ID for the database server. |
|
|
The application ID URI is a URI that uniquely identifies the database in your Entra ID. You get this value from the overview screen of your database Entra ID app registration. |
|
|
Specifies the Azure tenancy ID of the database. |
|
|
Optional parameter for setting the port number for the HTTP server. This URL obtains the authorization code from the Entra authentication endpoint and determines which port to use to receive the authorization code. If |
See Oracle Database Net Services Reference for specific information about each parameter. The following is an example of specifying use of interactive flow to get a token.
conn /@(DESCRIPTION=(ADDRESS=(PROTOCOL=tcps)(HOST=example.us-phoenix-1.oraclecloud.com)(PORT=6010))
(SECURITY=(SSL_SERVER_DN_MATCH=YES)
(AZURE_DB_APP_ID_URI=https://oracledevelopment.onmicrosoft.com/11111111-11a1-1a11-111a-a11a11111111)
(TENANT_ID=1a111aa1-a1a1-1a11-a1a1-a11aaaaa1111)
(CLIENT_ID=aa11a111-111a-1a11-1aa1-1aa1a1aa1111)
(TOKEN_AUTH=AZURE_INTERACTIVE))(CONNECT_DATA=(SERVICE_NAME=cdb1_pdb3.regress.rdbms.dev.us.oracle.com)))8.4.5.3 Enabling Clients to Retrieve Entra ID Tokens from a File Location
If you choose to retrieve the Entra ID location from a file location when you use the / slash login, then you will need to configure your client.
sqlnet.ora file or the tnsnames.ora file.
- On the client, set or check the following parameters in the
tnsnames.oraconnect string or in thesqlnet.orafile:SSL_SERVER_DN_MATCH: Ensure that this parameter is set toONso that DN matching is enabled.TOKEN_AUTH: Set this parameter toOAUTH.TOKEN_LOCATION: Set this parameter to the file location of the token. There is no default location for the token. If the token is namedtoken, then you only need to specify the file directory (for example,/test/oracle/aad-token). If the token name is different fromtoken(for example,azure.token), then you must include this name in the path (for example,/test/oracle/aad-token/azure.token).
The parameter values in the tnsnames.ora connect string take precedence over the sqlnet.ora settings for that connection. The following code is an example of a tnsnames.ora entry. In this case, SSL_SERVER_DN_MATCH is specified in sqlnet.ora and will not appear in the connect string:
(description=
(retry_count=20)(retry_delay=3)
(address=(protocol=tcps)(port=1522)
(host=example.us-phoenix-1.oraclecloud.com))
(connect_data=(service_name=aaabbbccc_exampledb_high.example.oraclecloud.com))
(security=(ssl_server_cert_dn="CN=example.uscom-east-1.oraclecloud.com,
OU=Oracle BMCS US, O=Example Corporation,
L=Redwood City, ST=California, C=US")
(TOKEN_AUTH=OAUTH)(TOKEN_LOCATION="/oracle/tokens/aad-token"))
After the connect string is updated with these parameters, the Azure user can log in to the Oracle Database instance by first running the external utility to get the token and then running the following command to start SQL*Plus. You can include the connect descriptor itself or use the name of the descriptor from the tnsnames.ora file.
connect /@exampledb_highThe database client is already configured to get an Azure OAuth2 token because TOKEN_AUTH has already been set, either through the connect string or the sqlnet.ora file. The database client gets the OAuth2 token and then sends the token to the Oracle Database instance.
8.4.6 Examples of Retrieving Entra ID OAuth2 Tokens Outside an Oracle Database Client
These examples show different ways that you can retrieve Entra ID OAuth2 token separately from the database client if you are not using the database client to retrieve the tokens directly.
- About Examples of Retrieving Microsoft Entra ID OAuth2 Tokens Outside of an Oracle Database Client
Oracle Database clients have differing abilities in directly retrieving an Entra IDOAuth2token. - Example: Requesting a Token Using a Python Script for the Interactive (Authorization) Flow
The interactive (authorization) flow is the most common for human users to access the database. - Example: Requesting a Token Using Azure CLI for the Interactive (Authorization) Flow
This example shows how to use the Azure CLI to retrieve an access token and then write the token to a file. - Requesting a Token Using the Azure CLI for the Client Credential Flow
The client credential flow is used for applications that need to use an Entra IDOAuth2token to access the database.
8.4.6.1 About Examples of Retrieving Microsoft Entra ID OAuth2 Tokens Outside of an Oracle Database Client
Oracle Database clients have differing abilities in directly retrieving an Entra ID OAuth2 token.
Review the specific client documentation for configuring the database client to retrieve tokens for different flows. The other two ways to work with Entra ID tokens are as follows:
- Passing tokens by using the client API
- Passing tokens through the file system
Review the client documentation on using the API. A utility or script is used to request a token from Entra ID and store it in a file location for the database client to pick up. Using a script or utility to request and store the token is outside Oracle Database. There are many examples available from Microsoft and others on the internet on how to get an Entra ID token. (Also search for Azure AD OAuth2 token). The samples in this section are just some examples and not supported by Oracle.
8.4.6.2 Example: Requesting a Token Using a Python Script for the Interactive (Authorization) Flow
The interactive (authorization) flow is the most common for human users to access the database.
OAuth2 access token. This example with the Microsoft Authentication Library (MSAL) is in Python and can be run on a variety of platforms such as Windows PowerShell and Linux. Because the authorization flow requires two round trips to Azure AD, it is best handled using the MSAL. See the Microsoft article Get Entra ID tokens by using the Microsoft Authentication Library for how to use a python script with MSAL. These instructions are for the Databricks service, but the scope is changed to the database App ID URI and scope instead of the Databricks scope.
8.4.6.3 Example: Requesting a Token Using Azure CLI for the Interactive (Authorization) Flow
This example shows how to use the Azure CLI to retrieve an access token and then write the token to a file.
8.4.6.4 Requesting a Token Using the Azure CLI for the Client Credential Flow
The client credential flow is used for applications that need to use an Entra ID OAuth2 token to access the database.
Because applications are "headless" and do not have a user to authenticate interactively with the Azure portal, the interactive flow cannot be used with applications. The client credential flow is designed for applications. In these flows, the application app registration requires a client secret along with the client ID. These are used to retrieve the Entra ID OAuth2 database access token.
After the script gets the token, this token will need to be written to a file (as shown in the examples in this section) so that the database client can access it. Microsoft provides several examples for a service principal to request a token. See then Microsoft article Get Microsoft Entra ID (formerly Azure Active Directory) tokens for service principals.
8.4.7 Creating a Network Proxy for the Database to Connect with the Internet
This network proxy will enable the Oracle database to reach the Entra ID endpoint.
- About Creating a Network Proxy for the Database to Connect with the Internet
The Oracle database must connect to Entra ID endpoints and it may require network configuration and default trust store access. - Testing the Accessibility of the Entra ID Endpoint
You must ensure that your Oracle Database instance can access the Entra ID endpoint. - Creating the Network Proxy for the Default Oracle Database Environment
To create the network proxy, you must set environment variables and then restart the listener. - Creating the Network Proxy for an Oracle Real Application Clusters Environment
To create the network proxy, you must set an environment variable and then restart the database. - Creating the Network Proxy in the Windows Registry Editor
To create the network proxy in a Windows environment, you must update the Registry Editor (regedit).
8.4.7.1 About Creating a Network Proxy for the Database to Connect with the Internet
The Oracle database must connect to Entra ID endpoints and it may require network configuration and default trust store access.
You can configure the database when HTTP network proxy is in place in an enterprise, for a default Oracle Database environment and for an Oracle Real Applications Clusters environment. The database establishes a Transport Layer Security (TLS) link to Entra ID, so it also needs access to the default trust store on the database server. To enable this, ensure that the database server has access to the system default certificate store.
Related Topics
8.4.7.2 Testing the Accessibility of the Entra ID Endpoint
You must ensure that your Oracle Database instance can access the Entra ID endpoint.
OAuth2 tokens, the database must request the public key from the Microsoft Entra ID endpoint.
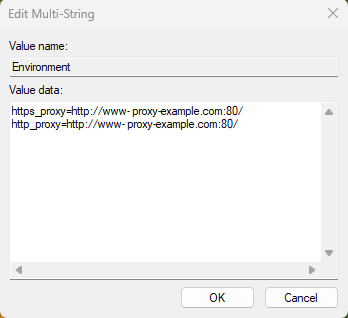
HTTP_PROXY package for your database. Review the topics listed in Related Topics, depending if you are using a default Oracle Database environment or an Oracle Real Application Clusters RAC environment. Your network administrator should be able to tell you what the correct HTTP_PROXY setting should be.
8.4.7.3 Creating the Network Proxy for the Default Oracle Database Environment
To create the network proxy, you must set environment variables and then restart the listener.
8.4.7.4 Creating the Network Proxy for an Oracle Real Application Clusters Environment
To create the network proxy, you must set an environment variable and then restart the database.
8.5 Configuring Microsoft Entra ID Proxy Authentication
Proxy authentication allows an Azure user to proxy to a database schema for tasks such as application maintenance.
- About Configuring Microsoft Entra ID Proxy Authentication
Azure users can connect to Oracle Autonomous Database by using proxy authentication. - Configuring Proxy Authentication for the Azure User
To configure proxy authentication for an Azure user, this user must already have a mapping to a global schema (exclusive or shared mapping). A separate database schema for the Azure user to proxy to must also be available. - Validating the Azure User Proxy Authentication
You can validate the Azure user proxy configuration for token authentication.
8.5.1 About Configuring Microsoft Entra ID Proxy Authentication
Azure users can connect to Oracle Autonomous Database by using proxy authentication.
Proxy authentication is typically used to authenticate the real user and then authorize them to use a database schema with the schema privileges and roles in order to manage an application. Alternatives such as sharing the application schema password are considered insecure and unable to audit which actual user performed an action.
A use case can be in an environment in which a named Azure user who is an application database administrator can authenticate by using their credentials and then proxy to a database schema user (for example, hrapp). This authentication enables the Entra ID administrator to use the hrapp privileges and roles as user hrapp in order to perform application maintenance, yet still use their Entra ID credentials for authentication. An application database administrator can sign in to the database and then proxy to an application schema to manage this schema.
Parent topic: Configuring Microsoft Entra ID Proxy Authentication
8.5.2 Configuring Proxy Authentication for the Azure User
To configure proxy authentication for an Azure user, this user must already have a mapping to a global schema (exclusive or shared mapping). A separate database schema for the Azure user to proxy to must also be available.
CONNECT [hrapp]/@connect_stringParent topic: Configuring Microsoft Entra ID Proxy Authentication
8.5.3 Validating the Azure User Proxy Authentication
You can validate the Azure user proxy configuration for token authentication.
Parent topic: Configuring Microsoft Entra ID Proxy Authentication
8.6 Troubleshooting Microsoft Entra ID Connections
You can use trace files to diagnose problems with Microsoft Entra ID connections. You also can easily remedy ORA-12599 and ORA-03114 errors.
- Trace Files for Troubleshooting Oracle Database Client Connections with Entra ID
You can use trace files to troubleshoot the Oracle Database integration with Entra ID. - ORA-12599 and ORA-03114 Errors Caused When Trying to Access a Database Using a Token
TheORA-12599: TNS: cryptographic checksum mismatchandORA-03114: not connected to ORACLEerrors indicate that the database to which you are trying to connect is protected by native network encryption. - Checking the Entra ID Access Token Version
You can check the version of the Entra ID access token that your site uses by using the JSON Web Tokens web site.
8.6.1 Trace Files for Troubleshooting Oracle Database Client Connections with Entra ID
You can use trace files to troubleshoot the Oracle Database integration with Entra ID.
- About Trace Files Used for Troubleshooting Connections
You can generate two levels of trace files to troubleshoot Entra ID connections on client side. - Setting Client Tracing for Token Authentication
You can addEVENTsettings to the client-sidesqlnet.orafile to control client tracing.
Parent topic: Troubleshooting Microsoft Entra ID Connections
8.6.1.1 About Trace Files Used for Troubleshooting Connections
You can generate two levels of trace files to troubleshoot Entra ID connections on client side.
The two levels of trace files that you can generate are as follows:
- Low level tracing prints traces in case of failures:
- If TCPS is not set up for the Entra ID connection, then it prints a message that the protocol has to be TCPS.
- If
SSL_SERVER_DN_MATCHis not set toTRUE, then it prints a message that the value isFALSE. - If
TOKEN_LOCATIONhas not been specified, then it prints a message that the token location does not exist. - If the token is not present at the specified
TOKEN_LOCATION, then it prints a message. - If the application has passed in the token without setting
OCI_ATTR_TOKEN_ISBEARERto true, it prints a message for the missing attribute. - If the application has set
OCI_ATTR_TOKEN_ISBEARERtoTRUEand not passed in the token, it prints a message for the missing attribute. - If the token has expired, then it prints a message.
- If the token is a Microsoft Entra ID v2.0 token and it does not contain upn claim or roles claim, then it prints out a message that the needed claim is missing.
- High level tracing prints traces in case of failure as mentioned above. In addition, it prints traces in case of success, as follows:
- It prints where
SSL_SERVER_DN_MATCHis present,tnsnames.oraorsqlnet.ora. It also prints the value asTRUEif set toTRUE. - If both the token and
OCI_ATTR_TOKEN_ISBEARER=trueare set by the application, then it prints a message. - If
TOKEN_AUTHhas the correct valueOAUTH, then it prints the value. - If the token is not expired, then it prints a message.
- If the token is a Microsoft Entra ID v2.0 token and the upn claim or roles claim exist, then it prints out a message that the needed claim exists.
- It prints where
8.6.2 ORA-12599 and ORA-03114 Errors Caused When Trying to Access a Database Using a Token
The ORA-12599: TNS: cryptographic checksum mismatch and ORA-03114: not connected to ORACLE errors indicate that the database to which you are trying to connect is protected by native network encryption.
When tokens are being used to access an Oracle database, a Transport Layer Security (TLS) connection must be established, not network native encryption. To remedy these errors, ensure that TLS is properly configured for your database. You should test the configuration with a local database user name and password and check the following SYSCONTEXT USERENV parameters:
-
NETWORK_PROTOCOL -
TLS_VERSION
Related Topics
Parent topic: Troubleshooting Microsoft Entra ID Connections
8.6.3 Checking the Entra ID Access Token Version
You can check the version of the Entra ID access token that your site uses by using the JSON Web Tokens web site.
Related Topics
Parent topic: Troubleshooting Microsoft Entra ID Connections