25 Configuring PKI Certificate Authentication
You can configure Oracle AI Database to use PKI certificates for end-user authentication.
- How Oracle Database Uses Transport Layer Security for Authentication
Transport Layer Security works with the core Oracle Database features such as encryption and data access controls. - Enabling Oracle Internet Directory to Use Transport Layer Security Authentication
To enable Oracle Internet Directory (OID) to use Transport Layer Security (TLS), create a wallet and certificates, and modifytnsnames.oraandsqlnet.ora. - Configuring User Authentication with Transport Layer Security
Both the client and server side can authenticate administrative users with Transport Layer Security (TLS). - Configuring Transport Layer Security for Client Authentication and Encryption with X.509 Certificates
You must perform this type of configuration on the server first, then the client. - Configuring Email over Transport Layer Security with an Oracle Wallet
You can use an Oracle wallet, PL/SQL packages, and security access control lists (ACLs) to configure email over a Transport Layer Security (TLS) connection. - Troubleshooting Transport Layer Security Errors
Oracle provides a utility to help troubleshoot PKI certificate configurations as well as additional guidance below. A utility is available through the support website to review and provide feedback on your PKI certificate authentication client and server configuration.
Parent topic: Managing Strong Authentication
25.1 How Oracle Database Uses Transport Layer Security for Authentication
Transport Layer Security works with the core Oracle Database features such as encryption and data access controls.
By using Oracle Database TLS functionality to secure communications between clients and servers, you can
-
Use TLS to encrypt the connection between clients and servers
-
Authenticate any client or server, such as Oracle Application Server 10g, to any Oracle database server that is configured to communicate over TLS
You can use TLS features by themselves or in combination with other authentication methods supported by Oracle Database. For example, you can use the encryption provided by TLS in combination with the authentication provided by Kerberos. TLS supports any of the following authentication modes:
-
Only the server authenticates itself to the client
-
Both client and server authenticate themselves to each other
Parent topic: Configuring PKI Certificate Authentication
25.2 Enabling Oracle Internet Directory to Use Transport Layer Security Authentication
To enable Oracle Internet Directory (OID) to use Transport Layer Security (TLS), create a wallet and certificates, and modify tnsnames.ora and sqlnet.ora.
Parent topic: Configuring PKI Certificate Authentication
25.3 Configuring User Authentication with Transport Layer Security
Both the client and server side can authenticate administrative users with Transport Layer Security (TLS).
CONNECT statement in SQL*Plus. For example, to log on as SYSDBA if the net service name is orcl:CONNECT /@orcl AS SYSDBA
25.4 Configuring Transport Layer Security for Client Authentication and Encryption with X.509 Certificates
You must perform this type of configuration on the server first, then the client.
- About Configuring TLS for Client Authentication and Encryption with X.509 Certificates
You can enable Public Key Infrastructure (PKI) authentication between Oracle Database clients and an Oracle database with X.509 certificates. - Configuring the Server for Authentication and Encryption with X.509 Certificates
You must configure the server'slistener.ora,sqlnet.ora, and initialization files and create a database user account for authentication and encryption with X.509 certificates. - Configuring the Client for Authentication and Encryption with X.509 Certificates
You must configure the client'ssqlnet.ora,tnsnames.oralistener.orafiles, and configure the Microsoft Certificate Store (MCS) for authentication and encryption with X.509 certificates.
Parent topic: Configuring PKI Certificate Authentication
25.4.1 About Configuring TLS for Client Authentication and Encryption with X.509 Certificates
You can enable Public Key Infrastructure (PKI) authentication between Oracle Database clients and an Oracle database with X.509 certificates.
The configuration entails having to enable Public Key Infrastructure (PKI) authentication between Oracle Database clients and an Oracle database. It can be used with U.S. Federal Government Personal Identity Verification (PIV) and Department of Defense Common Access Card (CAC) cards as external keystores with the Microsoft Certificate Store (MCS) on the Windows operating system. In addition, the configuration enables Java-based Oracle Database clients to authenticate against the Oracle Database through use of client certificates stored in an Oracle wallet.
Before you begin the configuration process, note the following:
- TLS communications must run on a separate network port from normal database connections. This may affect requirements for firewall exceptions.
- TLS connections can take a longer time to establish than connections with native encryption or without any encryption, because the key exchange process introduces additional overhead.
25.4.2 Configuring the Server for Authentication and Encryption with X.509 Certificates
You must configure the server's listener.ora, sqlnet.ora, and initialization files and create a database user account for authentication and encryption with X.509 certificates.
- Step 1: Create and Configure the Server Wallet for the X.509 Certificate
You can use theorapkiutility to perform this configuration. - Step 2: Shut Down the Oracle Listener on the Server
You use different methods to shut down the Oracle listener on the server. - Step 3: Configure the sqlnet.ora File on the Server
You must add or modify severalsqlnet.oraparameters on the server. - Step 4: For Logical Volume Management, Configure the Server listener.ora File
A logical volume management environment requires special settings for thelistener.orafile on the server. - Step 5: For Grid Infrastructure, Configure the Server Listener Process
A Grid Infrastructure environment requires special settings for thelistener.orafile on the server. - Step 6: Set Initialization Parameters on the Server
To avoid problems with prefixed user names, you may need to set some Oracle database initialization parameters on the server. - Step 7: Create an External Database User on the Server
You must create the database user by specifying the distinguished name (DN) of the user's client certificate. - Step 8: Restart and Check the Listener Process on the Server
If the Oracle database does not use Grid Infrastructure, then you must restart the listener on the server and check its process.
25.4.2.1 Step 1: Create and Configure the Server Wallet for the X.509 Certificate
You can use the orapki utility to perform this configuration.
wallet_file_directory to be readable by the grid user. Additionally, if it is an Oracle RAC database, then make the Oracle wallet available in a similar manner on all supporting database nodes.
25.4.2.2 Step 2: Shut Down the Oracle Listener on the Server
You use different methods to shut down the Oracle listener on the server.
- If the Oracle database does not use Oracle Real Applications (Oracle RAC) or Oracle Grid Infrastructure Storage Management, then as the
oracleuser, use the followinglsnrctlcommand:lsnrctl stop - If the Oracle database uses Oracle Grid Infrastructure Storage Management, then as the grid user, use the following
lsnrctlcommand:srvctl stop listener - If the Oracle database is an Oracle RAC database, as the grid user, then use the following
srvctlcommand:srvctl stop scan_listener
25.4.2.3 Step 3: Configure the sqlnet.ora File on the Server
You must add or modify several sqlnet.ora parameters on the server.
25.4.2.4 Step 4: For Logical Volume Management, Configure the Server listener.ora File
A logical volume management environment requires special settings for the listener.ora file on the server.
listener.ora file. However, it also possible to configure a newly created listener by using Net Manager (netmgr) as well. Oracle recommends that you use a standard TCPS port setting of 2484, but you can still use another port number. Your firewalls, security lists, and network security groups must be configured to allow traffic from your clients to the TCPS port that you specify.
25.4.2.5 Step 5: For Grid Infrastructure, Configure the Server Listener Process
A Grid Infrastructure environment requires special settings for the listener.ora file on the server.
25.4.2.6 Step 6: Set Initialization Parameters on the Server
To avoid problems with prefixed user names, you may need to set some Oracle database initialization parameters on the server.
25.4.2.7 Step 7: Create an External Database User on the Server
You must create the database user by specifying the distinguished name (DN) of the user's client certificate.
SYSDBA that require credentials to be stored in the database password file.
25.4.2.8 Step 8: Restart and Check the Listener Process on the Server
If the Oracle database does not use Grid Infrastructure, then you must restart the listener on the server and check its process.
- If the Oracle database does not use Oracle Real Applications (Oracle RAC) or Oracle Grid Infrastructure Storage Management, then as the
oracleuser, use the followinglsnrctlcommands:lsnrctl start lsnrctl status - If the Oracle database uses Oracle Grid Infrastructure Storage Management, then as the grid user, use the following
lsnrctlcommands:srvctl start listener srvctl status listener - If the Oracle database is an Oracle RAC database, as the grid user, then use the following
srvctlcommands:srvctl start scan_listener srvctl status scan_listener
25.4.3 Configuring the Client for Authentication and Encryption with X.509 Certificates
You must configure the client's sqlnet.ora, tnsnames.oralistener.ora files, and configure the Microsoft Certificate Store (MCS) for authentication and encryption with X.509 certificates.
- Step 1: Configure the sqlnet.ora File on the Client
You must add or modify severalsqlnet.oraparameters on the client. - Step 2: Configure the tnsnames.ora File on the Client
You must modify thetnsnames.orafile on the client. - Step 3: Configure Microsoft Certificate Store on the Client
The Microsoft Certificate Store (MCS), which enables you to store and manage certificates locally, can be configured on an Oracle Database Windows client.
25.4.3.1 Step 1: Configure the sqlnet.ora File on the Client
You must add or modify several sqlnet.ora parameters on the client.
25.4.3.2 Step 2: Configure the tnsnames.ora File on the Client
You must modify the tnsnames.ora file on the client.
25.4.3.3 Step 3: Configure Microsoft Certificate Store on the Client
The Microsoft Certificate Store (MCS), which enables you to store and manage certificates locally, can be configured on an Oracle Database Windows client.
- About Configuring Microsoft Certificate Store on the Client
Before you configure Microsoft Certificate Store (MCS) on the client, you should ensure that your client environment is properly set up. - Setting the TNS_ADMIN Environment Variable
TheTNS_ADMINenvironment variable must be set in a special way to facilitate the MCS operation. - Configuring Microsoft Certificate Store on the Client
For the mTLS configuration to work, the certificates for the root and intermediate CAs that signed the certificate that the database server used must be added to the MCS. - Testing the Microsoft Certificate Store Configuration Using tnsping
Thetnspingutility determines whether an Oracle service can be successfully reached. - Testing the Microsoft Certificate Store Configuration Using SQL*Plus
SQL*Plus is the most basic Oracle Database utility commonly used by users, administrators, and programmers that can be used to confirm mTLS and user authentication to the database.
25.4.3.3.1 About Configuring Microsoft Certificate Store on the Client
Before you configure Microsoft Certificate Store (MCS) on the client, you should ensure that your client environment is properly set up.
These instructions assume the following:
- The Oracle Database client has been installed and configured to communicate with the Oracle Database server.
- All clients have the latest patches installed.
- You have installed the appropriate hardware and software to enable MCS to read the certificates from the X509 smart cards (Common Access Card (CAC), Personal Identity Verification (PIV)
You can also configure MCS to work on the client with SQL Developer and with Java using JDBC Type 4 Drivers. See My Oracle Support note 2959952.1.
The following diagram illustrates a smart card and MCS in an Oracle Database environment.
Figure 25-1 Smart Card and MCS in an Oracle Database Environment
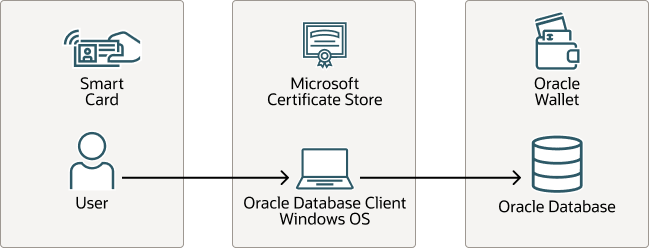
Description of "Figure 25-1 Smart Card and MCS in an Oracle Database Environment"
In this diagram:
- A user logs in to the Oracle database. The user's user certificate, private key, and other necessary certificates are on the smart card.
- The database connection from the client is configured to use MCS.
- The wallet in the Oracle database is a PKCS11 wallet with a private key an certificate. The Oracle Database wallet holds the server private key and the trusted root certificate.
25.4.3.3.2 Setting the TNS_ADMIN Environment Variable
The TNS_ADMIN environment variable must be set in a special way to facilitate the MCS operation.
*.ora files within their own user profile where they have ownership and control. It also allows each user of a system to have individual, personalized configurations.
25.4.3.3.3 Configuring Microsoft Certificate Store on the Client
For the mTLS configuration to work, the certificates for the root and intermediate CAs that signed the certificate that the database server used must be added to the MCS.
- Download the certificates for the root and intermediate CAs that were used to sign the database server certificate when you created and configured the server wallet.
- Start the MCS Certificate Import wizard.
- In the Welcome to the Certificate Import Wizard page, select the Current User option, and then click Next.
- On the Certificate Store page, select the Automatically select the certificate store based on the type of certificate option, and then click Next.
- In the Completing the Certificate Import Wizard page, check the settings that you made, and then click Finish. Click OK in the Certificate Import Wizard confirmation window.
- Confirm that the CAs have successfully been loaded into MCS.
- In the Console Root tree on the left, under Certificates - Current User, expand the Trusted Root Certificates folder.
- Select the Certificates folder to display the Certificate window.
- Check the contents. The window will describe the purpose of the certificate, who it was issued to, who issued it, and the dates the certificate will be valid for. Click OK to dismiss the window.
25.4.3.3.4 Testing the Microsoft Certificate Store Configuration Using tnsping
The tnsping utility determines whether an Oracle service can be successfully reached.
Related Topics
25.5 Configuring Email over Transport Layer Security with an Oracle Wallet
You can use an Oracle wallet, PL/SQL packages, and security access control lists (ACLs) to configure email over a Transport Layer Security (TLS) connection.
Parent topic: Configuring PKI Certificate Authentication
25.6 Troubleshooting Transport Layer Security Errors
Oracle provides a utility to help troubleshoot PKI certificate configurations as well as additional guidance below. A utility is available through the support website to review and provide feedback on your PKI certificate authentication client and server configuration.
- Step 1: Check the TLS Connection with the tnsping Utility
A successful connection using thetnspingutility shows that the database service has been registered to the listener on the TCPS endpoint. - Step 2: Check the SSL_VERSION Parameter
An incorrectly setSSL_VERSIONparameter can cause Transport Layer Security (TLS) problems. - Step 3: Check the Wallet File Permissions
The Transport Layer Security (TLS) connection requires the database and listener to have access to the auto-login wallet file (cwallet.sso). - Step 4: Check the Wallet Settings in the sqlnet.ora and listener.ora Files
Transparent Layer Security (TLS) problems can arise from wallet and certificate configuration errors in thesqlnet.oraandlistener.orafiles. - Step 5: Enable Tracing for the SQL*Net and Listener Connections
In thesqlnet.orafile, you can enable tracing for SQL*Net and listener connections.
Parent topic: Configuring PKI Certificate Authentication
25.6.1 Step 1: Check the TLS Connection with the tnsping Utility
A successful connection using the tnsping utility shows that the database service has been registered to the listener on the TCPS endpoint.
Parent topic: Troubleshooting Transport Layer Security Errors
25.6.2 Step 2: Check the SSL_VERSION Parameter
An incorrectly set SSL_VERSION parameter can cause Transport Layer Security (TLS) problems.
You should ensure that the SSL_VERSION parameter in the server and client sqlnet.ora file is set to the correct version of TLS, so that connections can be established. For example:
SSL_VERSION= TLSv1.3By default, Oracle Database uses the most secure protocol that is available when SSL_VERSION is not set.
See Oracle AI Database Net
Services Reference to learn more about how to set the SSL_VERSION parameter for the correct version of TLS.
Parent topic: Troubleshooting Transport Layer Security Errors
25.6.3 Step 3: Check the Wallet File Permissions
The Transport Layer Security (TLS) connection requires the database and listener to have access to the auto-login wallet file (cwallet.sso).
In the case of an Oracle Real Application Clusters (Oracle RAC) database, both the Grid Infrastructure Oracle Home owner and the Database Oracle Home owner must have access to the contents of a cwallet.sso file containing the correct certificates. Quite often the configuration implies the usage of the same cwallet.sso file for both environments, in which case the permissions should be set appropriately so that both users can have access to the file no matter who is the owner of the file.
By default, the wallet permissions are as follows:
$ ls -ltr
-rw-------. 1 ewallet.p12
-rw-------. 1 cwallet.sso If the cwallet.sso file will be used by the Grid Infrastructure Oracle Home owner (usually grid) then user grid must be a member of the oinstall group. You can change the permissions as follows:
$ chmod 640 cwallet.sso
$ ls -ltr
-rw-------. 1 oracle oinstall 75 Mar 6 10:47 ewallet.p12
-rw-r-----. 1 oracle oinstall 120 Mar 6 10:47 cwallet.ssoParent topic: Troubleshooting Transport Layer Security Errors
25.6.4 Step 4: Check the Wallet Settings in the sqlnet.ora and listener.ora Files
Transparent Layer Security (TLS) problems can arise from wallet and certificate configuration errors in the sqlnet.ora and listener.ora files.
These settings enable you to encrypt the connections between the database and its clients. (Another way to handle this encryption is with the external network services PL/SQL packages, UTL_SMTP, UTL_HTTP, and UTL_TCP.)
Note the following:
- For the server: Set the
WALLET_ROOTparameter. (TheWALLET_LOCATIONparameter can still be used.) Both trusted certificate and server certificate are required. - For the client: Set the
WALLET_LOCATIONinsqlnet.ora. Only trusted certificates are required if one-way TLS is configured. If mTLS is configured, then both trusted certificate and server certificate are required. - For the listener: Set the
WALLET_LOCATIONparameter in thelistener.orafile. Both trusted certificate and server certificate are required.
An example WALLET_LOCATION parameter setting is as follows:
WALLET_LOCATION =
(SOURCE =
(METHOD = FILE)
(METHOD_DATA =
(DIRECTORY = wallet_location)
)
)The certificates can be self-signed or they can be signed by a third-party authority.
You can use the orapki wallet display -wallet command to view the contents of a wallet to find if it has self-signed certificates. For example:
$ orapki wallet display -wallet .
Requested Certificates:
User Certificates:
Subject: C=US,CN=MYROOT
Trusted Certificates:
Subject: C=US,CN=MYROOT
The following example shows the output for a wallet that has wallet that has certificates that were provided by a third-party authority:
Requested Certificates:
User Certificates:
Subject: CN=*.us.example.com,O=Example Corporation,L=Redwood City,ST=California,C=US
Trusted Certificates:
Subject: CN=DigiCert Global Root CA,O=DigiCert Inc,C=US
Subject: CN=DigiCert TLS RSA SHA256 2020 CA1,O=DigiCert Inc,C=USParent topic: Troubleshooting Transport Layer Security Errors
25.6.5 Step 5: Enable Tracing for the SQL*Net and Listener Connections
In the sqlnet.ora file, you can enable tracing for SQL*Net and listener connections.
For example, to enabling tracing for SQL*Net:
TRACE_LEVEL_CLIENT=SUPPORT
TRACE_DIRECTORY_CLIENT=trace_dir
TRACE_LEVEL_SERVER=SUPPORT
TRACE_DIRECTORY_SERVER=trace_dir
DIAG_ADR_ENABLED=OFFFor the listener, you can set the following tracing parameters:
TRACE_FILE_LISTENER = LISTENER.TRC
TRACE_DIRECTORY_LISTENER = trace_dir
TRACE_LEVEL_LISTENER = SUPPORT
TRACE_FILELEN_LISTENER = 10240
TRACE_FILENO_LISTENER=10The following output indicates that the TLS connection failed because the wrong TLS protocol was used. To find how to address these errors, see My Oracle Support note 244527.1.
[<DATE AND TIME>] ntzdosecneg: entry
[<DATE AND TIME>] nttrd: entry
[<DATE AND TIME>] nttrd: socket 13 had bytes read=11
[<DATE AND TIME>] nttrd: exit
[<DATE AND TIME>] ntzdosecneg: SSL handshake failed with error 29019.
[<DATE AND TIME>] ntzdosecneg: exit
[<DATE AND TIME>] ntzcontrol: failed with error 542
[<DATE AND TIME>] ntzcontrol: exit
[<DATE AND TIME>] nserror: entry
[<DATE AND TIME>] nserror: nsres: id=0, op=79, ns=12561, ns2=0; nt[0]=0, nt[1]=0, nt[2]=0; ora[0]=0, ora[1]=0, ora[2]=0
[<DATE AND TIME>] nsclose: entry
[<DATE AND TIME>] nsvntx_dei: entry
[<DATE AND TIME>] nsvntx_dei: exitSee Troubleshooting the Transport Layer Security Configuration for information about common error codes.
See also Oracle AI Database Net Services Administrator's Guide for more information about using trace settings to track connections.
Parent topic: Troubleshooting Transport Layer Security Errors