26 Configuring RADIUS Authentication
RADIUS is a client/server security protocol widely used to enable remote authentication and access.
- About Configuring RADIUS Authentication
Oracle AI Database supports the RADIUS standard for user authentication. - RADIUS Components
RADIUS has a set of authentication components that enable you to manage configuration settings. - RADIUS Authentication Modes
The RADIUS server can authenticate users using technologies such as FIDO and text message authentication codes. In addition, Oracle Database supports synchronous and challenge-response (async) authentication modes. - RADIUS Parameters
Oracle provides a set of RADIUS-specific parameters. - Enabling RADIUS Authentication, Authorization, and Accounting
You can enable RADIUS authentication, authorization, and accounting from the command line. - Using RADIUS to Log in to a Database
You can use RADIUS to log into a database by using either synchronous authentication mode or challenge-response mode. - Integrating Authentication Devices Using RADIUS
The RADIUS challenge-response user interface further enhances authentication in a RADIUS configuration.
Parent topic: Managing Strong Authentication
26.1 About Configuring RADIUS Authentication
Oracle AI Database supports the RADIUS standard for user authentication.
Note:
Starting with Oracle AI Database 26ai, the older RADIUS API that is based on Request for Comments (RFC) 2138 is deprecated.Oracle AI Database 26ai introduces an updated RADIUS API
based on RFC 6613 and RFC 6614. Oracle recommends that you start planning on
migrating to use the new RADIUS API as soon as possible. The new API is enabled by
default. These parameters associated with the older RADIUS API are also deprecated:
SQLNET.RADIUS_ALTERNATE,
SQLNET.RADIUS_ALTERNATE_PORT,
SQLNET.RADIUS_AUTHENTICATION, and
SQLNET.RADIUS_AUTHENTICATION_PORT. Refer to the Radius API
documentation for information on changing the default to use the older RADIUS
API.
RADIUS is frequently used for multi-factor authentication (MFA) when it is used to access an Oracle AI Database. The specific MFA technologies (such as smart cards or biometric cards) depend on the RADIUS server. The database server and client support asynchronous and synchronous challenges for MFA.
The Oracle AI
Database RADIUS implementation uses the TLS/TCPS standards that are described in RFC 6013 and
6014 and is enabled by default by the Oracle AI
Database. If you want to use the older implementation (before Oracle AI
Database
26ai) using an older RADIUS standard, then you
must enable one or both of the SQLNET.RADIUS_ALLOW_WEAK_CLIENTS and
SQLNET.RADIUS_ALLOW_WEAK_PROTOCOL parameters to use the older
RADIUS implementation.
From an end user's perspective, the entire authentication process is transparent. When the user seeks access to an Oracle AI Database server, the Oracle AI Database server, acting as the RADIUS client, notifies the RADIUS server. The RADIUS server then:
-
Looks up the user's security information
-
Passes authentication and authorization information between the appropriate authentication server or servers and the Oracle AI Database server
-
Grants the user access to the Oracle AI Database server
-
Logs session information, including when, how often, and for how long the user was connected to the Oracle AI Database server
Note:
Oracle AI Database does not support RADIUS authentication over database links.
To configure Oracle AI Database to use RADIUS, you will modify parameters in the
sqlnet.orafile. The settings insqlnet.oraapply to all pluggable databases (PDBs).
Figure 26-1 illustrates the Oracle AI Database-RADIUS environment.
Figure 26-1 RADIUS in an Oracle Environment
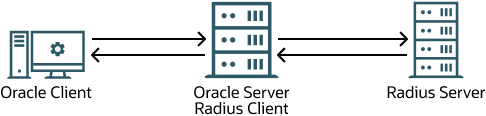
Description of "Figure 26-1 RADIUS in an Oracle Environment"
The Oracle AI Database server acts as the RADIUS client, passing information between the Oracle client and the RADIUS server. Similarly, the RADIUS server passes information between the Oracle AI Databasee server and the appropriate authentication servers.
A RADIUS server vendor is often the authentication server vendor as well. In this case authentication can be processed on the RADIUS server.
Related Topics
Parent topic: Configuring RADIUS Authentication
26.2 RADIUS Components
RADIUS has a set of authentication components that enable you to manage configuration settings.
Table 26-1 lists the authentication components.
Table 26-1 RADIUS Authentication Components
| Component | Stored Information |
|---|---|
|
Oracle client |
Configuration setting for communicating through RADIUS. |
|
Oracle database server/RADIUS client |
Configuration settings for passing information between the Oracle client and the RADIUS server. The secret key file. |
|
RADIUS server |
Authentication and authorization information for all users. Each client's name or IP address. Each client's shared secret. |
|
Authentication server or servers |
User authentication information such as pass codes and PINs, depending on the authentication method in use. Note: The RADIUS server can also be the authentication server. |
Parent topic: Configuring RADIUS Authentication
26.3 RADIUS Authentication Modes
The RADIUS server can authenticate users using technologies such as FIDO and text message authentication codes. In addition, Oracle Database supports synchronous and challenge-response (async) authentication modes.
- Synchronous Authentication Mode
In the synchronous mode, the user enters both the password and the second factor in the password field at the same time. This method is preferable when you use a command line interface when a GUI challenge window cannot be opened. - Challenge-Response (Asynchronous) Authentication Mode
When the system uses the asynchronous mode, the user does not need to enter a user name and password at the SQL*Plus CONNECT string.
Parent topic: Configuring RADIUS Authentication
26.3.1 Synchronous Authentication Mode
In the synchronous mode, the user enters both the password and the second factor in the password field at the same time. This method is preferable when you use a command line interface when a GUI challenge window cannot be opened.
- Sequence for Synchronous Authentication Mode
The sequence of synchronous authentication mode is comprised of six steps. - Example: Synchronous Authentication with Tokens
With token authentication, each user has a token card that displays a dynamic number that changes every sixty seconds.
Parent topic: RADIUS Authentication Modes
26.3.1.1 Sequence for Synchronous Authentication Mode
The sequence of synchronous authentication mode is comprised of six steps.
Figure 26-2 shows the sequence in which synchronous authentication occurs.
Figure 26-2 Synchronous Authentication Sequence
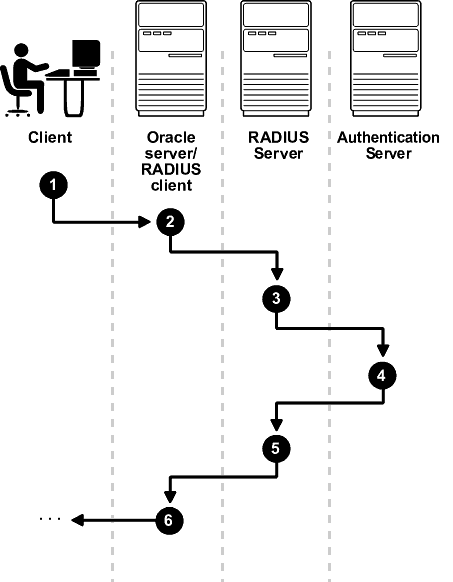
Description of "Figure 26-2 Synchronous Authentication Sequence"
The following steps describe the synchronous authentication sequence:
-
A user logs in by entering a connect string, pass code, or other value. The client system passes this data to the Oracle database server. The pass code is frequently the password followed by the numbers in a token or text. Both credential factors are sent at the same time.
-
The Oracle database server, acting as the RADIUS client, passes the data from the Oracle client to the RADIUS server.
-
The RADIUS server passes the data to the appropriate authentication server.
-
The authentication server sends either an Access Accept or an Access Reject message back to the RADIUS server.
-
The RADIUS server passes this response to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client passes the response back to the Oracle client.
Parent topic: Synchronous Authentication Mode
26.3.1.2 Example: Synchronous Authentication with Tokens
With token authentication, each user has a token card that displays a dynamic number that changes every sixty seconds.
To gain access to the Oracle database server/RADIUS client, the user enters a valid pass code that includes both a personal identification number (PIN) and the dynamic number currently displayed on the user's token. The Oracle database server passes this authentication information from the Oracle client to the RADIUS server, which in this case is the authentication server for validation. The user is now authenticated and able to access the appropriate tables and applications.
Parent topic: Synchronous Authentication Mode
26.3.2 Challenge-Response (Asynchronous) Authentication Mode
When the system uses the asynchronous mode, the user does not need to enter a user name and password at the SQL*Plus CONNECT string.
- Sequence for Challenge-Response (Asynchronous) Authentication Mode
The sequence for challenge-response (asynchronous) authentication mode is comprised of 12 steps. - Example: Asynchronous Authentication with Tokens
One type of token that is used with asynchronous authentication has a keypad and display.
Parent topic: RADIUS Authentication Modes
26.3.2.1 Sequence for Challenge-Response (Asynchronous) Authentication Mode
The sequence for challenge-response (asynchronous) authentication mode is comprised of 12 steps.
Note:
Challenge-response (Asynchronous) authentication mode is not supported with OCI-C client database clients on the Microsoft Windows platform. This includes all thick clients that use OCI-C clients.Figure 26-3 shows the sequence in which challenge-response (asynchronous) authentication occurs. If the RADIUS server is the authentication server, then Steps 3, 4, and 5, and Steps 9, 10, and 11 are combined.
Figure 26-3 Asynchronous Authentication Sequence
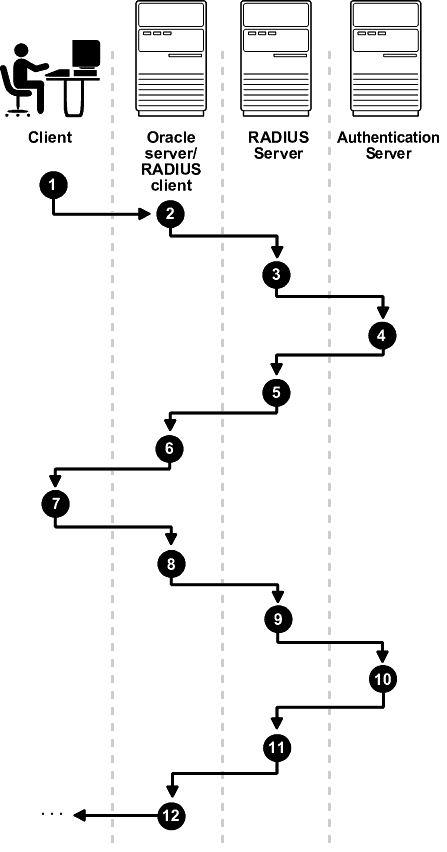
Description of "Figure 26-3 Asynchronous Authentication Sequence"
The following steps describe the asynchronous authentication sequence:
-
A user initiates a connection to an Oracle database server. The client system passes the data to the Oracle database server.
-
The Oracle database server, acting as the RADIUS client, passes the data from the Oracle client to the RADIUS server.
-
The RADIUS server passes the data to the appropriate authentication server or authenticates the user against its own local database.
-
The authentication server sends a challenge, such as a random number, to the RADIUS server.
-
The RADIUS server passes the challenge to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client, in turn, passes it to the Oracle client. A graphical user interface presents the challenge to the user. Oracle provides a JAVA GUI code example that you can modify for your use to present the challenge. See the
netradius.jarandnetradius8.jarfiles in the$ORACLE_HOME/network/jlibdirectory. (Thenetradius8.jarfile is the latest.) -
The user provides a response to the challenge. To formulate a response, the user can, for example, enter the received challenge into the token card. The token card provides a dynamic password that is entered into the graphical user interface. The Oracle client passes the user's response to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client sends the user's response to the RADIUS server.
-
The RADIUS server passes the user's response to the appropriate authentication server for validation.
-
The authentication server sends either an Access Accept or an Access Reject message back to the RADIUS server.
-
The RADIUS server passes the response to the Oracle database server/RADIUS client.
-
The Oracle database server/RADIUS client passes the response to the Oracle client.
Parent topic: Challenge-Response (Asynchronous) Authentication Mode
26.3.2.2 Example: Asynchronous Authentication with Tokens
One type of token that is used with asynchronous authentication has a keypad and display.
When the user seeks access to an Oracle database server by entering a password, the information is passed to the appropriate authentication server by way of the Oracle database server/RADIUS client and the RADIUS server. The authentication server sends back a challenge to the client, by way of the RADIUS server and the Oracle database server. The user types that challenge into the token, and the token displays a number for the user to send in response.
The Oracle client then sends the user's response to the authentication server by way of the Oracle database server and the RADIUS server. If the user has typed a valid number, the authentication server sends an accept packet back to the Oracle client by way of the RADIUS server and the Oracle database server. The user is now authenticated and authorized to access the appropriate tables and applications. If the user has entered an incorrect response, the authentication server sends back a message rejecting the user's access.
Parent topic: Challenge-Response (Asynchronous) Authentication Mode
26.4 RADIUS Parameters
Oracle provides a set of RADIUS-specific parameters.
- RADIUS Parameters for Clients and Servers
Oracle Database provides client and server parameters for using RADIUS authentication. - Minimum RADIUS Parameters
At minimum, you should use theSQLNET.AUTHENTICATION_SERVICESandSQLNET.RADIUS.AUTHENTICATIONparameters. - Initialization File Parameter for RADIUS
For RADIUS, you should set theOS_AUTHENT_PREFIXinitialization parameter.
Parent topic: Configuring RADIUS Authentication
26.4.1 RADIUS Parameters for Clients and Servers
Oracle Database provides client and server parameters for using RADIUS authentication.
The following table lists parameters to insert into the configuration files for clients and servers using RADIUS.
Table 26-2 RADIUS Authentication Parameters
| Parameter | Description |
|---|---|
|
|
Enables one or more authentication services |
|
|
Specifies an alternate RADIUS server if the primary server is unavailable |
|
|
Specifies the listening port of the alternate RADIUS server |
|
|
Specifies the number of times that the database resends messages to alternate RADIUS servers |
|
|
Sets the time for an alternate RADIUS server to wait for a response |
|
|
Specifies a primary RADIUS server location, either by its host name or its IP address |
|
|
Specifies the class that contains the user interface for interacting with users |
|
|
Specifies the listening port of a primary RADIUS server |
|
|
Specifies the number of times the database should resend messages to a primary RADIUS server |
|
|
Specifies the amount of time that the database should wait for a response from a primary RADIUS server |
|
|
Sets the keyword to request a challenge from the RADIUS server |
|
|
Enables or disables challenge responses |
|
|
Sets the path for Java classes and the JDK Java libraries |
|
|
Specifies the location of a RADIUS secret key |
|
|
Enable and disables accounting |
Related Topics
Parent topic: RADIUS Parameters
26.4.2 Minimum RADIUS Parameters
At minimum, you should use the SQLNET.AUTHENTICATION_SERVICES and SQLNET.RADIUS.AUTHENTICATION parameters.
Use the following settings:
sqlnet.authentication_services = (radius) sqlnet.radius.authentication = IP-address-of-RADIUS-server
Parent topic: RADIUS Parameters
26.4.3 Initialization File Parameter for RADIUS
For RADIUS, you should set the OS_AUTHENT_PREFIX initialization parameter.
For example:
OS_AUTHENT_PREFIX=""
Parent topic: RADIUS Parameters
26.5 Enabling RADIUS Authentication, Authorization, and Accounting
You can enable RADIUS authentication, authorization, and accounting from the command line.
- Step 1: Configure RADIUS Authentication
To configure RADIUS authentication, you must first configure it on the Oracle client, then the server. Afterward, you can configure additional RADIUS features. - Step 2: Create a User and Grant Access
After you complete the RADIUS authentication, you must create an Oracle Database user who is responsible for the RADIUS configuration. - Step 3: Configure External RADIUS Authorization (Optional)
You must configure the Oracle server, the Oracle client, and the RADIUS server to RADIUS users who must connect to an Oracle database. - Step 4: Configure RADIUS Accounting
RADIUS accounting logs information about access to the Oracle database server and stores it in a file on the RADIUS accounting server. - Step 5: Add the RADIUS Client Name to the RADIUS Server Database
The RADIUS server that you select must comply with RADIUS standards. - Step 6: Configure the Authentication Server for Use with RADIUS
After you add the RADIUS client name to the RADIUS server database, you can configure the authentication server to use the RADIUS. - Step 7: Configure the RADIUS Server for Use with the Authentication Server
After you configure the authentication server for use with RADIUS, you can configure the RADIUS server to use the authentication server. - Step 8: Configure Mapping Roles
If the RADIUS server supports vendor type attributes, then you can manage roles by storing them in the RADIUS server.
Parent topic: Configuring RADIUS Authentication
26.5.1 Step 1: Configure RADIUS Authentication
To configure RADIUS authentication, you must first configure it on the Oracle client, then the server. Afterward, you can configure additional RADIUS features.
- Step 1A: Configure RADIUS on the Oracle Client
You can usesqlnet.orato configure RADIUS on the Oracle client. - Step 1B: Configure RADIUS on the Oracle Database Server
You must create a file to hold the RADIUS key and store this file on the Oracle database server. Then you must configure the appropriate parameters in thesqlnet.orafile. - Step 1C: Configure Additional RADIUS Features
You can change the default settings, configure the challenge-response mode, and set parameters for an alternate RADIUS server.
26.5.1.1 Step 1A: Configure RADIUS on the Oracle Client
You can use sqlnet.ora to configure RADIUS on the Oracle client.
Parent topic: Step 1: Configure RADIUS Authentication
26.5.1.2 Step 1B: Configure RADIUS on the Oracle Database Server
You must create a file to hold the RADIUS key and store this file on the Oracle database server. Then you must configure the appropriate parameters in the sqlnet.ora file.
- Step 1B (1): Create the RADIUS Secret Key File on the Oracle Database Server
First, you must create the RADIUS secret key file. - Step 1B (2): Configure RADIUS Parameters on the Server (sqlnet.ora file)
After you create RADIUS secret key file, you are ready to configure the appropriate parameters in thesqlnet.orafile. - Step 1B (3): Set Oracle Database Server Initialization Parameters
After you configure thesqlnet.orafile, you must configure theinit.orainitialization file.
Parent topic: Step 1: Configure RADIUS Authentication
26.5.1.2.1 Step 1B (1): Create the RADIUS Secret Key File on the Oracle Database Server
First, you must create the RADIUS secret key file.
Parent topic: Step 1B: Configure RADIUS on the Oracle Database Server
26.5.1.2.2 Step 1B (2): Configure RADIUS Parameters on the Server (sqlnet.ora file)
After you create RADIUS secret key file, you are ready to configure the appropriate parameters in the sqlnet.ora file.
Note:
- Starting with Oracle AI Database 26ai, users authenticating to
the database using the legacy RADIUS API no longer are granted administrative
privileges.
In previous releases, users authenticating with RADIUS API could be granted administrative privileges such as
SYSDBAorSYSBACKUP. In Oracle AI Database 26ai, Oracle introduces a new RADIUS API that uses the latest standards. To grant administrative privileges to users, ensure the database connection to the database uses the new RADIUS API, and that you are using the Oracle AI Database 26ai client to connect to the Oracle AI Database 26ai server. - Starting with Oracle AI Database 26ai, the older RADIUS API that
is based on Request for Comments (RFC) 2138 is deprecated.
Oracle AI Database 26ai introduces an updated RADIUS API based on RFC 6613 and RFC 6614. Oracle recommends that you start planning on migrating to use the new RADIUS API as soon as possible. The new API is enabled by default. These parameters associated with the older RADIUS API are also deprecated:
SQLNET.RADIUS_ALTERNATE,SQLNET.RADIUS_ALTERNATE_PORT,SQLNET.RADIUS_AUTHENTICATION, andSQLNET.RADIUS_AUTHENTICATION_PORT. Refer to the Radius API documentation for information on changing the default to use the older RADIUS API.
Related Topics
Parent topic: Step 1B: Configure RADIUS on the Oracle Database Server
26.5.1.2.3 Step 1B (3): Set Oracle Database Server Initialization Parameters
After you configure the sqlnet.ora file, you must configure the init.ora initialization file.
Related Topics
Parent topic: Step 1B: Configure RADIUS on the Oracle Database Server
26.5.1.3 Step 1C: Configure Additional RADIUS Features
You can change the default settings, configure the challenge-response mode, and set parameters for an alternate RADIUS server.
- Step 1C(1): Change Default Settings
You can edit thesqlnet.orafile to change the default RADIUS settings. - Step 1C(2): Configure Challenge-Response Mode
To configure challenge-response mode, you must specify information such as a dynamic password that you obtain from a token card. - Step 1C(3): Set Parameters for an Alternate RADIUS Server
If you are using an alternate RADIUS server, then you must set additional parameters. - Step 1C(4): Enable Access by Non-TCPS Protocols or Older Clients
If you need to have clients that do not use the TCPS protocol, then you must set additionalsqlnet.oraRADIUS parameters.
Parent topic: Step 1: Configure RADIUS Authentication
26.5.1.3.1 Step 1C(1): Change Default Settings
You can edit the sqlnet.ora file to change the default RADIUS settings.
26.5.1.3.2 Step 1C(2): Configure Challenge-Response Mode
To configure challenge-response mode, you must specify information such as a dynamic password that you obtain from a token card.
Related Topics
Parent topic: Step 1C: Configure Additional RADIUS Features
26.5.1.3.3 Step 1C(3): Set Parameters for an Alternate RADIUS Server
If you are using an alternate RADIUS server, then you must set additional parameters.
Parent topic: Step 1C: Configure Additional RADIUS Features
26.5.1.3.4 Step 1C(4): Enable Access by Non-TCPS Protocols or Older Clients
If you need to have clients that do not use the TCPS protocol, then you must set additional sqlnet.ora RADIUS parameters.
Parent topic: Step 1C: Configure Additional RADIUS Features
26.5.2 Step 2: Create a User and Grant Access
After you complete the RADIUS authentication, you must create an Oracle Database user who is responsible for the RADIUS configuration.
See Also:
Administration documentation for the RADIUS server
26.5.3 Step 3: Configure External RADIUS Authorization (Optional)
You must configure the Oracle server, the Oracle client, and the RADIUS server to RADIUS users who must connect to an Oracle database.
- Step 3A: Configure the Oracle Server (RADIUS Client)
You can edit theinit.orafile to configure an Oracle server for a RADIUS client. - Step 3B: Configure the Oracle Client Where Users Log In
Next, you must configure the Oracle client where users log in. - Step 3C: Configure the RADIUS Server
To configure the RADIUS server, you must modify the RADIUS server attribute configuration file.
26.5.3.1 Step 3A: Configure the Oracle Server (RADIUS Client)
You can edit the init.ora file to configure an Oracle server for a RADIUS client.
init.ora file, restart the database, and the set the RADIUS challenge-response mode.
- Set the RADIUS challenge-response mode to
ONfor the server if you have not already done so. - Add externally identified users and roles.
Related Topics
26.5.3.2 Step 3B: Configure the Oracle Client Where Users Log In
Next, you must configure the Oracle client where users log in.
- Set the RADIUS challenge-response mode to
ONfor the client if you have not already done so.
Related Topics
26.5.4 Step 4: Configure RADIUS Accounting
RADIUS accounting logs information about access to the Oracle database server and stores it in a file on the RADIUS accounting server.
Use this feature only if both the RADIUS server and authentication server support it.
- Step 4A: Set RADIUS Accounting on the Oracle Database Server
You can usesqlnet.orato enable RADIUS accounting on the server. - Step 4B: Configure the RADIUS Accounting Server
RADIUS Accounting Server resides on the same host as the RADIUS authentication server or on a separate host.
26.5.4.1 Step 4A: Set RADIUS Accounting on the Oracle Database Server
You can use sqlnet.ora to enable RADIUS accounting on the server.
Parent topic: Step 4: Configure RADIUS Accounting
26.5.4.2 Step 4B: Configure the RADIUS Accounting Server
RADIUS Accounting Server resides on the same host as the RADIUS authentication server or on a separate host.
- See the administration documentation for the RADIUS server, for information about configuring RADIUS accounting.
Parent topic: Step 4: Configure RADIUS Accounting
26.5.5 Step 5: Add the RADIUS Client Name to the RADIUS Server Database
The RADIUS server that you select must comply with RADIUS standards.
See Also:
Administration documentation for the RADIUS server
26.5.6 Step 6: Configure the Authentication Server for Use with RADIUS
After you add the RADIUS client name to the RADIUS server database, you can configure the authentication server to use the RADIUS.
- Refer to the authentication server documentation for instructions about configuring the authentication servers.
26.5.7 Step 7: Configure the RADIUS Server for Use with the Authentication Server
After you configure the authentication server for use with RADIUS, you can configure the RADIUS server to use the authentication server.
- Refer to the RADIUS server documentation for instructions about configuring the RADIUS server for use with the authentication server.
26.5.8 Step 8: Configure Mapping Roles
If the RADIUS server supports vendor type attributes, then you can manage roles by storing them in the RADIUS server.
CONNECT request using RADIUS.To use this feature, you must configure roles on both the Oracle database server and the RADIUS server.
26.6 Using RADIUS to Log in to a Database
You can use RADIUS to log into a database by using either synchronous authentication mode or challenge-response mode.
Parent topic: Configuring RADIUS Authentication
26.7 Integrating Authentication Devices Using RADIUS
The RADIUS challenge-response user interface further enhances authentication in a RADIUS configuration.
- About the RADIUS Challenge-Response User Interface
You can use third-party authentication vendors to customize the RADIUS challenge-response user interface to fit a particular device. - Customizing the RADIUS Challenge-Response User Interface
You can customizeOracleRadiusInterfaceinterface by creating your own class. - Example: Using the OracleRadiusInterface Interface
You can use the OracleRadiusInterface interface to retrieve a user name and password.
Parent topic: Configuring RADIUS Authentication
26.7.1 About the RADIUS Challenge-Response User Interface
You can use third-party authentication vendors to customize the RADIUS challenge-response user interface to fit a particular device.
You can set up any authentication device that supports the RADIUS standard to authenticate Oracle users. When your authentication device uses the challenge-response mode, a graphical interface prompts the end user first for a password and then for additional information (for example, a dynamic password that the user obtains from a token card). This interface is Java-based to provide optimal platform independence.
Third-party vendors of authentication devices must customize this graphical user interface to fit their particular device. For example, a smart card vendor customizes the Oracle client to issue the challenge to the smart card reader. Then, when the smart card receives a challenge, it responds by prompting the user for more information, such as a PIN.
Related Topics
Parent topic: Integrating Authentication Devices Using RADIUS
26.7.2 Customizing the RADIUS Challenge-Response User Interface
You can customize OracleRadiusInterface interface by creating your own class.
The third party must implement the OracleRadiusInterface interface, which is located in the ORACLE.NET.RADIUS package.
Parent topic: Integrating Authentication Devices Using RADIUS
26.7.3 Example: Using the OracleRadiusInterface Interface
You can use the OracleRadiusInterface interface to retrieve a user name and password.
Example 26-1 shows how to use the OracleRadiusInterface interface.
Example 26-1 Using the OracleRadiusInterface Interface
public interface OracleRadiusInterface {
public void radiusRequest();
public void radiusChallenge(String challenge);
public String getUserName();
public String getPassword();
}
In this specification:
-
radiusRequestprompts the end user for a user name and password, which will later be retrieved throughgetUserNameandgetPassword. -
getUserNameextracts the user name the user enters. If this method returns an empty string, it is assumed that the user wants to cancel the operation. The user then receives a message indicating that the authentication attempt failed. -
getPasswordextracts the password the user enters. IfgetUserNamereturns a valid string, butgetPasswordreturns an empty string, the challenge keyword is replaced as the password by the database. If the user enters a valid password, a challenge may or may not be returned by the RADIUS server. -
radiusChallengepresents a request sent from the RADIUS server for the user to respond to the server's challenge. -
getResponseextracts the response the user enters. If this method returns a valid response, then that information populates theUser-Passwordattribute in the newAccess-Requestpacket. If an empty string is returned, the operation is canceled from both sides by returning the corresponding value.
Parent topic: Integrating Authentication Devices Using RADIUS