21 Configuring Transport Layer Security Encryption
Use Transport Layer Security (TLS), a secure and standard protocol, to encrypt your database client and server connections.
- Transport Layer Security (TLS) and the Oracle Database
TLS secures connections between the Oracle Database client and server. The database server can also connect to other databases and other services using TLS version 1.3 (the default) or 1.2. This chapter will primarily focus on configuring TLS between the Oracle Database client and server. - Configuring TLS for the Oracle Database and Client
This topic describes the three most common TLS configurations. More advanced and optional configurations are described later in this chapter. - Advanced and Optional Configurations
Oracle AI Database 26ai ensures that the default Transport Layer Security configuration is secure and versatile. However, Oracle provides parameters to customize and control this configuration. - TLS and Other Oracle Products
Transport Layer Security (TLS) can be configured when using other Oracle Database products. - Troubleshooting the Transport Layer Security Configuration
Common errors may occur while you use the Oracle Database Transport Layer Security. - Migrating to and Configuring Transport Layer Security Version 1.3
Version 1.3 of Transport Layer Security (TLS) provides stronger security and faster TLS handshakes, when compared to previous versions of TLS.
Parent topic: Securing Data on the Network
21.1 Transport Layer Security (TLS) and the Oracle Database
TLS secures connections between the Oracle Database client and server. The database server can also connect to other databases and other services using TLS version 1.3 (the default) or 1.2. This chapter will primarily focus on configuring TLS between the Oracle Database client and server.
The database client and server can be configured to use TLS depending on your requirements. There are several options to consider which are mentioned below. The primary use cases are discussed in the following topic. Advanced considerations are discussed in Advanced and Optional Configurations.
Configuring a client-server TLS connection requires the database server to have a wallet. The server wallet includes the private key, the signed user certificate, the root of trust certificate and any intermediate certificates for the database server user certificate.
The TLS wallet on the database server must be stored under the
WALLET_ROOT location. (The parameter WALLET_LOCATION is deprecated for
use with Oracle AI Database 26ai for the Oracle Database server. It is not
deprecated for use with the Oracle Database client or listener.) Create a directory for TLS under WALLET_ROOT, so it
looks like WALLET_ROOT/<PDB GUID>/tls. Each
container (including CDB root) will have its own TLS wallet, there's no
configuration to have a single wallet work for more than one or all
containers when using WALLET_ROOT.
When configuring TLS between the database client and server there are several options to consider:
- Self-signed Certificate vs Public Certificate Authority (CA) Signed Certificate
Determine whether a self-signed certificate or a public certificate authority signed certificate is appropriate for your database configuration. - One-way TLS vs Mutual TLS
Determine if one-way TLS or Mutual TLS (mTLS) is appropriate for your database configuration. - TLS With or Without a Client Wallet
Determine if using a client wallet is appropriate for your database configuration. - Certificate DN Matching
Determine if certificate DN matching is appropriate for your database configuration. - Post-Quantum Cryptography
Determine if using post-quantum cryptography (PQC) is appropriate for your database configuration.
Parent topic: Configuring Transport Layer Security Encryption
21.1.1 Self-signed Certificate vs Public Certificate Authority (CA) Signed Certificate
Determine whether a self-signed certificate or a public certificate authority signed certificate is appropriate for your database configuration.
Self-signed certificate: Having a self-signed root certificate is a common practice for internally facing IT resources since you can create these yourself and it's free. The resource (in our case, the database server) will use a self-signed root certificate to sign its own database server certificate. The server certificate and self-signed root certificate are stored in the database server wallet. For the database client to be able to trust the database server certificate, a copy of the self-signed root certificate will also be needed by the client. This self-signed root certificate can be stored in a client-side wallet or installed in the client system default certificate store. The system certificate store locations for all OS are mentioned in Oracle Wallet Search Order.
Before the session is established, the database client will check if the server certificate has been signed by the same root certificate installed on the client. Storing root trust certificate in the client system default certificate store is helpful since it can also be used by other applications and browsers in the client machine. If your company uses self-signed certificates, the root trust certificate may already be installed in all the client default trust stores.
Public certificate authority (CA): A CA-signed certificate is signed by a third-party, publicly trusted certificate authority (CA). Some examples of public certificate authorities are Symantec, DigiCert, Thawte, GeoTrust, GlobalSign, GoDaddy, and Entrust. These entities are responsible for validating the person or organization that requests each certificate.
Using a public root of trust certificate authority has some advantages in that the root trust certificate is most likely already stored in the client system default certificate store. There is no extra step for the client to store the root trust certificate if it is from a public certificate authority. The disadvantage is that this normally has a payment to a third party certificate authority.
Parent topic: Transport Layer Security (TLS) and the Oracle Database
21.1.2 One-way TLS vs Mutual TLS
Determine if one-way TLS or Mutual TLS (mTLS) is appropriate for your database configuration.
One-way TLS: One-way TLS is a server-verified encrypted channel using the TLS protocol. In the standard TLS session, only the server provides a certificate to the client to authenticate itself. The client doesn't need to have a separate client certificate to authenticate itself to the server (similar to how HTTPS sessions are established). While the database server requires a wallet to store the server user certificate and private key, the database client only needs to access the trusted CA root certificate to validate the server user certificate is signed by a trusted CA root certificate. Depending on the OS platform and the database client, the trusted CA root certificate could be in the local default certificate system store or in a client wallet. One-way TLS is the most common TLS configuration and detailed configuration steps can be found in Configuring TLS Using a Public Certificate Authority Root of Trust for the Database Server Certificate.
Two-way TLS (also called Mutual TLS, mTLS): In mTLS, both the client and server present their user certificates to each other. In most cases, the same CA root certificate will have signed both of these certificates so the same root CA certificate can be used with the database server and client to authenticate the other certificate. mTLS when used in this manner is used to encrypt the link between the database and the client, and also validate both the database and the client's certificate. Database user authentication is done separately, for example, using a database username and password to authenticate the user in addition to establishing the mTLS encrypted link. A principal (human or application) can also use the client side user certificate as it's authentication mechanism. This is called PKI certificate authentication and is covered in Configuring PKI Certificate Authentication. In this case, the user certificate does double duty - establish the mTLS connection and PKI certificate authentication to the database. For detailed configuration steps for mTLS see Mutual Transport Layer Security (mTLS).
Parent topic: Transport Layer Security (TLS) and the Oracle Database
21.1.3 TLS With or Without a Client Wallet
Determine if using a client wallet is appropriate for your database configuration.
Client with a wallet: When using mTLS, a client certificate is required. The client certificate must be stored in the client wallet or Microsot Certificate Store (MCS) in Windows. The wallet must also store the trusted CA root certificate along with the required intermediate certificates.
Client without a wallet: Clients can be configured without a wallet when using TLS under these conditions:
- One-way TLS is being configured where the client does not have its own certificate.
- The root certificate that signed the database server certificate is stored in the system default certificate store. If the server certificate is signed by a public certificate authority, the root certificate will most likely already be there. If a self-signed certificate was used to sign the server certificate, this self-signed certificate would need to be installed in the system default certificate store to avoid using a client wallet.
- This is only applicable to Linux and Windows clients. This works natively with Windows MCS and the native Linux keystore. On non-Windows and non-Linux OS clients, the OCI-C client will look for a PEM file stored in several locations described in Oracle Wallet Search Order.
Parent topic: Transport Layer Security (TLS) and the Oracle Database
21.1.4 Certificate DN Matching
Determine if certificate DN matching is appropriate for your database configuration.
Tip:
Oracle recommends using this option when configuring a TLS session.- Partial DN match: In
SQLNET.oraor in the connect string, specifySSL_SERVER_DN_MATCH=YES. Partial DN match will check theHOSTparameter in the connect string to see if there's a match with the CN, DN, or SAN names. There has to be a match for the connection to be successful. - Full DN match: In addition to setting
SSL_SERVER_DN_MATCH=YES, you must also setSSL_SERVER_CERT_DN=<certificate DN>to force a full DN match. This allows you to continue to use DN certificate match when yourHOSTvalue needs to be an IP address or something other than the names available in the certificate.
Parent topic: Transport Layer Security (TLS) and the Oracle Database
21.1.5 Post-Quantum Cryptography
Determine if using post-quantum cryptography (PQC) is appropriate for your database configuration.
Post-Quantum Cryptography (PQC), also known as quantum-resistant or quantum-safe cryptography, is a new class of cryptographic algorithms designed to be secure against attacks by future, large-scale quantum computers.
Current widely used public-key cryptographic methods, such as RSA and Elliptic Curve Cryptography (ECC), rely on mathematical problems that are computationally difficult for classical computers to solve. However, a sufficiently powerful quantum computer, using algorithms like Shor's algorithm, could easily break these systems, compromising the security of sensitive data.
PQC algorithms are based on different mathematical problems—such as those related to lattices, hash functions, or codes—that are believed to be difficult for both classical and quantum computers to solve. The transition to PQC is a critical, proactive measure to protect long-term data, such as medical records and intellectual property, from being harvested today and decrypted in the future once a quantum computer becomes available.
- ML-KEM - A Key Encapsulation Mechanism (KEM) used to securely
establish a shared secret key between two parties. It is a lattice-based
algorithm and is intended to replace classic key exchange methods like
Diffie-Hellman.
ML-KEM and Elliptic Curve Diffie-Hellman Ephemeral (ECDHE) algorithms are only supported in TLS 1.3.
You will need to set the TLS_KEY_EXCHANGE_GROUPS parameter in
sqlnet.ora. If theTLS_KEY_EXCHANGE_GROUPSparameter is not set then the default value ofhybridwill be used. Setting theTLS_KEY_EXCHANGE_GROUPSparameter tohybridproduces a hybrid KEM that combines the key-exchange secrets from both ML-KEM and ECDHE to produce a single shared secret for the TLS session. A hybrid KEM can provide a critical security fallback in case either individual algorithm fails. - ML-DSA - A digital signature algorithm used for authentication and
data integrity. It is also a lattice-based algorithm and is intended to replace
algorithms like RSA and ECDSA.
ML-DSA algorithms for certificate validation are only supported in TLS 1.3. RSA and ECC algorithms are supported for certification validation in TLS 1.3 and TLS 1.2.
orapkisupports creating self-signed ML-DSA, reading ML-DSA certifications, and adding ML-DSA certificates to Oracle wallet with JDK 24 or later.
Note:
The Oracle Net Services parameter SSL_DISABLE_WEAK_EC_CURVES is deprecated in Oracle AI Database 26ai.Related Topics
Parent topic: Transport Layer Security (TLS) and the Oracle Database
21.2 Configuring TLS for the Oracle Database and Client
This topic describes the three most common TLS configurations. More advanced and optional configurations are described later in this chapter.
- About Configuring TLS for the Oracle Database
The three most common TLS configurations are described in detail in this topic. - Configuring TLS Using a Public Certificate Authority Root of Trust for the Database Server Certificate
Before you can configure TLS without using client wallets, you must first create the server wallet and ensure that the database and listener are properly configured. - Configuring TLS with a Self-Signed Root Certificate
Using a self-signed root certificate is very similar to the above use case, except you must create a root wallet and sign the database certificate with the self-signed root certificate. - Configuring TLS Connection With a Client Wallet
A client wallet is sometimes required when configuring TLS with a public or self-signed CA trust certificate. - Enabling Distinguished Name (DN) Matching
DN matching allows a connection to the Oracle Database server when the server certificate name or DN matches what the client expects.
Parent topic: Configuring Transport Layer Security Encryption
21.2.1 About Configuring TLS for the Oracle Database
The three most common TLS configurations are described in detail in this topic.
The first decision is to use a self-signed certificate root of trust or a public CA root of trust. Once you make that decision, Oracle recommends using TLS without a wallet if your environment supports this and is allowed by your security policies. This greatly simplifies managing database clients. Start your configurations with the minimum set of mandatory parameters. And then once you are successful, add the recommended parameters and any optional parameters one by one.
The following parameters are used in the following configurations in this topic.
Table 21-1 Mandatory and Recommended parameters to configure one-way TLS
| Parameter | Description | Server
(Defined in
sqlnet.ora) |
Listener
(Defined in
listener.ora) |
Static
Client
(Defined in
sqlnet.ora) |
Dynamic Client (Defined in the connect string) |
|---|---|---|---|---|---|
WALLET_ROOT |
Database server system parameter
(replaces
WALLET_LOCATION)
|
Required | No | No | No |
WALLET_LOCATION |
Specifies wallet location if required | No | Required | Optional | Optional |
Protocol=tcps |
Enables TLS connection | No | Required | No | Required |
SSL_CLIENT_AUTHENTICATION |
Disable to allow 1-way TLS | Required | Required | Optional | Optional |
SSL_SERVER_DN_MATCH |
Enables partial or full DN matching | No | No | Recommended | Recommended |
SSL_SERVER_CERT_DN |
Use if full DN matching is required | No | No | No | Optional |
WALLET_ROOT and
WALLET_LOCATION Parameters
For Oracle Database server, Oracle recommends that you use the
WALLET_ROOT system parameter instead of using
WALLET_LOCATION.
The parameter WALLET_LOCATION is deprecated for
use with Oracle AI Database 26ai for the Oracle Database server. It is not
deprecated for use with the Oracle Database client or listener. The TLS wallet location for a PDB is WALLET_ROOT/<PDB
GUID>/tls.
WALLET_LOCATION must be used by the listener
to find its wallet. Oracle recommends using the same wallet for the
listener and the server for DN matching. DN matching is used by the
client to verify that it is connecting to the expected server, and
the client checks both the listener and the server certificates.
Protocol Parameter
The Protocol must be set to
tcps with the client and listener. The
listener sets this as part of the service connect string. The client
sets this in the connect string.
SSL_CLIENT_AUTHENTICATON Parameter
SSL_CLIENT_AUTHENTICATON must be set to
FALSE for the database server and the
listener to allow TLS traffic (vs mTLS) to connect to the listener
and the server. This is optional for the client and depends if the
client already has a wallet with a client-side user certificate that
is used for other connections.
DN Matching
Oracle recommends using DN matching. However, add these settings once you have successfully confirmed a TLS connection.
The most common TLS configurations for the Oracle Database are:
Parent topic: Configuring TLS for the Oracle Database and Client
21.2.2 Configuring TLS Using a Public Certificate Authority Root of Trust for the Database Server Certificate
Before you can configure TLS without using client wallets, you must first create the server wallet and ensure that the database and listener are properly configured.
Parent topic: Configuring TLS for the Oracle Database and Client
21.2.2.1 Create the Server and Listener Wallet
21.2.2.5 Client Configuration for TLS
21.2.2.5.1 Configure Client Connect String for TLS
Add the parameter protocol=tcps in the connect string to
enforce TLS from the client. The connection will use TLS from the client to
the listener.
Note:
This parameter is not available insqlnet.ora.(description=
(address=
(protocol=tcps)
(port=1522)
(host=example.com))
(connect_data=
(service_name=dbservicename.example.com)))21.2.2.5.2 (Optional)
Set SSL_CLIENT_AUTHENTICATON for the
Client
- If you have a client-side user certificate, but don't want to use it for mTLS, then you must complete this step.
- If you don't have a client-side user certificate, you can skip this step as the client will go ahead and make a one-way TLS connection regardless of this parameter setting.
21.2.3 Configuring TLS with a Self-Signed Root Certificate
Using a self-signed root certificate is very similar to the above use case, except you must create a root wallet and sign the database certificate with the self-signed root certificate.
Parent topic: Configuring TLS for the Oracle Database and Client
21.2.3.2 Create the Server and Listener Wallet
21.2.3.7 Client Configuration for TLS
21.2.3.7.1 Add the self-signed trusted root certificate to the client system default keystore
The Oracle Database thick clients (OCI-C) work natively with the Windows and Linux system default stores. On other operating systems, the Oracle Database client will search the directory locations listed below for a PEM file. If your PEM file for your OS is in a different location, you can either copy the PEM file to one of the searched locations or create a symlink to a searched location. Follow the directions for your OS to add the new trust certificate to your system certificate store (PEM file). We include the directions for doing that for Microsoft Windows and RHEL/Oracle Linux.
21.2.3.7.2 Configure Client Connect String for TLS
Add the parameter protocol=tcps in the connect string to
enforce TLS from the client. The connection will use TLS from the client to
the listener.
Note:
This parameter is not available insqlnet.ora.(description=
(address=
(protocol=tcps)
(port=1522)
(host=example.com))
(connect_data=
(service_name=dbservicename.example.com)))21.2.3.7.3 (Optional)
Set SSL_CLIENT_AUTHENTICATON for the
Client
- If you have a client-side user certificate, but don't want to use it for mTLS, then you must complete this step.
- If you don't have a client-side user certificate, you can skip this step as the client will go ahead and make a one-way TLS connection regardless of this parameter setting.
21.2.4 Configuring TLS Connection With a Client Wallet
A client wallet is sometimes required when configuring TLS with a public or self-signed CA trust certificate.
A client wallet for a TLS connection includes the trust certificate for the certificate authority that signed the database server certificate. Only the root of trust certificate is required. Intermediate certificates are not required.
Using a client wallet is required if you cannot use the system's default certificate store.
Parent topic: Configuring TLS for the Oracle Database and Client
21.2.4.1 (Optional)
Set SSL_CLIENT_AUTHENTICATON for the
Client
- If you have a client-side user certificate, but don't want to use it for mTLS, then you must complete this step.
- If you don't have a client-side user certificate, you can skip this step as the client will go ahead and make a one-way TLS connection regardless of this parameter setting.
21.2.5 Enabling Distinguished Name (DN) Matching
DN matching allows a connection to the Oracle Database server when the server certificate name or DN matches what the client expects.
Tip:
Oracle strongly recommends using either partial or full DN matching so the client connects to the correct host.When DN matching is enabled, the listener certificate and the database server certificate will both be checked against the certificate expected by the client. Without using DN matching, any server certificate signed by the same or valid public CA will be accepted by the client to establish the TLS session.
It is recommended to first successfully configure TLS in a test environment prior to setting up DN matching. See Configuring TLS Using a Public Certificate Authority Root of Trust for the Database Server Certificate.
To enable DN Matching:
- Set the
SSL_SERVER_DN_MATCHparameter toTRUEin thesqlnet.orafile:SSL_SERVER_DN_MATCH = TRUEThesqlnet.orafile will look similar to:SSL_CLIENT_AUTHENTICATION = FALSE WALLET_LOCATION = (SOURCE= (METHOD=File) (METHOD_DATA= (DIRECTORY=wallet_location))) SSL_SERVER_DN_MATCH = TRUENote:
Only completing this step will result in partial DN matching. Perform step three to establish full DN matching.Partial DN matching will check the host parameter value in the connect string against the certificate's common name (CN). If a match isn't found, the client will then compare the host parameter value against the entries in the certificate's Subject Alternate Name (SAN) field. If there are no matches, the connection will be refused.
- Check the host name parameter in the connect string in
tnsnames.oraagainst the common name (CN) of the certificate DN string and the hostnames listed in the Subject Alternate Name (SAN) field. The connect string host name needs to match for partial DN match to succeed.The
tnsnames.orafile can be located on the client or in the LDAP directory. Thetnsnames.orafile is typically located in the setting specified by theTNS_ADMINenvironment variable. IfTNS_ADMINis not set, thentnsnames.oraresides in the following directory locations:- Linux:
$ORACLE_HOME/network/admin/ - Windows:
ORACLE_BASE\ORACLE_HOME\network\admin\
- Linux:
- If you can't use partial DN matching, then configure full DN matching
by setting the
SSL_SERVER_CERT_DNparameter connection string in thetnsnames.orafile:Note:
If you can't set the host value in
tnsnames.oraorsqlnet.orato the value of the certificate common name (CN) or one of the entries in the SAN field, then consider using full DN matching.Both the listener and server certificate will be checked with both partial and full DN matching. When using full DN matching, while the server and listener certificate can be different, their DN must be the same for the connection to succeed.
Thetnsnames.orafile will look similar to:finance= (DESCRIPTION= (ADDRESS_LIST= (ADDRESS=(PROTOCOL = tcps)(HOST = finance) (PORT = 1575))) (CONNECT_DATA= (SERVICE_NAME= finance.us.example.com)) (SECURITY= (SSL_SERVER_DN_MATCH = TRUE) (SSL_SERVER_CERT_DN="cn=finance,cn=OracleContext,c=us,o=example")))
Parent topic: Configuring TLS for the Oracle Database and Client
21.3 Advanced and Optional Configurations
Oracle AI Database 26ai ensures that the default Transport Layer Security configuration is secure and versatile. However, Oracle provides parameters to customize and control this configuration.
Note:
To ensure secure configuration, Oracle recommends that only mandatory and recommended parameters are configured in your environment. When the Oracle AI Database client and server are configuring a connection, the most secure protocol and cipher suite that is common to both the server and client are selected. Selecting a TLS protocol or cipher suite will block clients that are unable to use that protocol or cipher suite. These configurations need to be checked during database updates and upgrades to make sure the selected values are supported after the database upgrade or update.- Optional Parameters for Transport Layer Security
The server-side TLS configuration is applicable to all connections serviced by the server. These are specified in the server-side configuration files sqlnet.ora for the Database server and listener.ora for the Database listener. - Mutual Transport Layer Security (mTLS)
In traditional Transport Layer Security (TLS), only the server authenticates to the client by presenting its certificate. With mutual Transport Layer Security (mTLS), both the server and the client present their certificates so that they are mutually authenticated. - Oracle Wallet Location
Certificates used for TLS are stored in the Oracle wallet. There are several default locations where the wallet can be placed. The location of the wallet can also be configured with the wallet location parameters on the client and listener. TheWALLET_ROOTsystem parameter should be used for the database server wallet location. - Enable Weak DN Matching
TheSSL_ALLOW_WEAK_DN_MATCHparameter control reverts the DN matching behavior to prior database versions. - Private Key/Certificate Selection
You can have multiple private key/certificate pairs stored in either the Oracle wallet or a system certificate store to use for certificates. This is sometimes necessary when different databases will assign different client credentials for mTLS, such as for Autonomous Database. - Transport Layer Security Encryption Combined with Authentication Methods
You can configure Oracle Database to use TLS concurrently with all authentication mechanisms such as database user names and passwords, RADIUS, Kerberos, PKI certificates, MS-EI, and OCI IAM. - Specifying TLS Protocol and TLS Cipher Suites
Oracle AI Database 26ai supports TLS protocol versions 1.2 and 1.3 and their associated cipher suites for Transport Layer Security (TLS). - Certificate Validation with Certificate Revocation Lists
Oracle provides tools that enable you to validate certificates using certificate revocation lists.
Parent topic: Configuring Transport Layer Security Encryption
21.3.1 Optional Parameters for Transport Layer Security
The server-side TLS configuration is applicable to all connections serviced by the server. These are specified in the server-side configuration files sqlnet.ora for the Database server and listener.ora for the Database listener.
The client-side TLS configuration can be connection-specific or applied to
all connections via sqlnet.ora. There are two ways to configure a
Transport Layer Security (TLS) parameter for clients.
-
Static: these are parameters specified in the configuration file
sqlnet.oraand uniformly applied to all connections made by the client. -
Dynamic: If desired, certain TLS parameters may be specified directly in the TNS connect string to override the same or similar parameter in
sqlnet.ora.
Table 21-2 General TLS Parameters
| Parameter | Description | Server | Listener | Static Client | Dynamic Client |
|---|---|---|---|---|---|
HTTPS_CLIENT_AUTHENTICATION |
Specifies whether a client is authenticated using TLS for HTTPS connections | Yes | Yes | Yes | Yes |
SSL_CLIENT_AUTHENTICATION |
Specifies whether a client is authenticated using TLS or mTLS | Yes | Yes | Yes | Yes |
WALLET_LOCATION |
Specify the TLS wallet location. | Yes* | Yes | Yes | Yes |
*The parameter WALLET_LOCATION is deprecated for
use with Oracle AI Database 26ai for the Oracle Database server. It is not
deprecated for use with the Oracle Database client or listener.
For Oracle Database server, Oracle recommends that you use the
WALLET_ROOT system parameter instead of using
WALLET_LOCATION.
Table 21-3 TLS Parameters For Selecting User Certificate
| Parameter | Description | Server | Listener | Static Client | Dynamic Client |
|---|---|---|---|---|---|
SSL_CERTIFICATE_ALIAS |
Specifies the certificate based on its alias. | Yes | Yes | Yes | Yes |
SSL_EXTENDED_KEY_USAGE |
Specifies the certificate based on its key usage value. | Yes | Yes | Yes | Yes |
SSL_CERTIFICATE_THUMBPRINT |
Specifies the certificate based on its thumbprint. | Yes | Yes | Yes | Yes |
Note:
Selecting a client-side user certificate is only applicable when working with user certificates in Windows MCS and in Oracle wallets.Table 21-4 TLS Certificate DN Matching Parameters
| Parameter | Description | Server | Listener | Static Client | Dynamic Client |
|---|---|---|---|---|---|
SSL_ALLOW_WEAK_DN_MATCH |
Allows the earlier weaker distinguished name (DN) matching behavior during server-side certificate validation | No | No | Yes | Yes |
SSL_SERVER_CERT_DN |
Specifies the distinguished name (DN) of the database server | No | No | No | Yes |
SSL_SERVER_DN_MATCH |
Enforces client-side validation of server through distinguished name (DN) matching | No | No | Yes | Yes |
TLS_CERT_VALIDATION_MODE |
Specifies if stricter checks as per RFC 5280 are enforced. | No | No | Yes | No |
Table 21-5 TLS Protocol and Cipher Suite Selection Parameters
| Parameter | Description | Server | Listener | Static Client | Dynamic Client |
|---|---|---|---|---|---|
SSL_CIPHER_SUITES |
Specifies the TLS cipher suites allowed for TLS connections | Yes | Yes | Yes | Yes |
SSL_ENABLE_WEAK_CIPHERS |
Enables deprecated TLS cipher suites | Yes | Yes | Yes | Yes |
SSL_VERSION |
Specifies the TLS protocol to use in a connection | Yes | Yes | Yes | Yes |
TLS_DISABLE_VERSION |
Specifies what, if any, TLS protocols are disallowed in a connection. | Yes | Yes | Yes | Yes |
Parent topic: Advanced and Optional Configurations
21.3.2 Mutual Transport Layer Security (mTLS)
In traditional Transport Layer Security (TLS), only the server authenticates to the client by presenting its certificate. With mutual Transport Layer Security (mTLS), both the server and the client present their certificates so that they are mutually authenticated.
The SSL_CLIENT_AUTHENTICATION parameter controls
whether the client certificate needs to be authenticated. This doesn't authenticate
or authorize the end user. It authenticates that the certificates used by both the
server and client are valid and signed by a known certificate authority (CA). Configuring PKI Certificate Authentication goes into detail about end-user authentication using PKI certificates.
The default for SSL_CLIENT_AUTHENTICATION is
TRUE for the database server, listener, and client, which will
require mTLS (mutual TLS requiring a client certificate in a client wallet).
Settings are as follows:
OFF/FALSEdisables mTLS, which enables one-way TLS.ON/TRUEenables mTLS. If it is set to On/TRUE on the server, one-way TLS will be disabled. If it is set to On/TRUE on the client, the client will try to establish mTLS; however, one-way TLS is still allowed if the server is configured with one-way TLS.OPTIONAL, server-only configuration value, enables the server to behave as follows:- If the client sends a certificate, the connection will be completed as an mTLS connection after the client certificate is authenticated.
- If the client does not send a certificate, then the connection will be completed as a one-way TLS connection.
- Server Certificate DN Matching
Oracle recommends using Server certificate DN matching, similar to using server DN matching with one-way TLS, to ensure the client is connecting to the intended server.
Parent topic: Advanced and Optional Configurations
21.3.2.1 Create the Server and Listener Wallet
21.3.2.6 Connect to the database
Connect to the database using the connection name with the tcps protocol.
sqlplus <user_name>@<PDB_name>21.3.2.7 Server Certificate DN Matching
Oracle recommends using Server certificate DN matching, similar to using server DN matching with one-way TLS, to ensure the client is connecting to the intended server.
Configure full DN matching by setting the SSL_SERVER_CERT_DN
parameter connection string in the tnsnames.ora
file:
Note:
If you can't set the host value in
tnsnames.ora or sqlnet.ora to
the value of the certificate common name (CN) or one of the entries in the
SAN field, then consider using full DN matching.
Both the listener and server certificate will be checked with both partial and full DN matching. When using full DN matching, while the server and listener certificate can be different, their DN must be the same for the connection to succeed.
tnsnames.ora file will
look similar
to:finance=
(DESCRIPTION=
(ADDRESS_LIST=
(ADDRESS=(PROTOCOL = tcps)(HOST = finance)
(PORT = 1575)))
(CONNECT_DATA=
(SERVICE_NAME= finance.us.example.com))
(SECURITY=
(SSL_SERVER_DN_MATCH = TRUE)
(SSL_SERVER_CERT_DN="cn=finance,cn=OracleContext,c=us,o=example")))Parent topic: Mutual Transport Layer Security (mTLS)
21.3.3 Oracle Wallet Location
Certificates used for TLS are stored in the Oracle wallet. There are several
default locations where the wallet can be placed. The location of the wallet can also be
configured with the wallet location parameters on the client and listener. The
WALLET_ROOT system parameter should be used for the database server
wallet location.
- Configuring Wallet Location for the Client
The client's wallet location can be configured using the parameterWALLET_LOCATION. When theWALLET_LOCATIONparameter is configured insqlnet.ora, it applies to all connections. If a connection-specific wallet is needed,WALLET_LOCATIONfor the connection can be configured in the connect string, which overridesWALLET_LOCATIONinsqlnet.ora. - Configuring Wallet Location for the Listener
Wallet location for the listener can be configured using theWALLET_LOCATIONparameter inlistener.ora. - Configuring PDB Wallet Location for server
The multi-tenant architecture enables an Oracle database to function as a multi-tenant container database (CDB) that includes zero, one, or many customer-created pluggable databases (PDBs). - Oracle Wallet Search Order
Oracle Database provides several routes for finding the wallet on a server in a Transport Layer Security (TLS) environment.
Parent topic: Advanced and Optional Configurations
21.3.3.1 Configuring Wallet Location for the Client
The client's wallet location can be configured using the parameter
WALLET_LOCATION. When the WALLET_LOCATION parameter
is configured in sqlnet.ora, it applies to all connections. If a
connection-specific wallet is needed, WALLET_LOCATION for the connection
can be configured in the connect string, which overrides WALLET_LOCATION in
sqlnet.ora.
On certain platforms, a wallet is not required when setting up a client for one-way TLS authentication, and the wallet location is not required in the configuration. Oracle Database can utilize Trusted CA certificates installed on the system to support one-way TLS. Refer to the earlier topic, “Transport Layer Security Connections without a Client Wallet,” for more details and a list of supported platforms.
(sqlnet.ora)WALLET_LOCATION =
(SOURCE=
(METHOD=File)
(METHOD_DATA=
(DIRECTORY=your_wallet_dir)
)
)(tnsnames.ora)svc_name=(DESCRIPTION=
(ADDRESS=(...))
(CONNECT_DATA=(...))
(SECURITY=
(WALLET_LOCATION=your_wallet_dir)
)
)Parent topic: Oracle Wallet Location
21.3.3.2 Configuring Wallet Location for the Listener
Wallet location for the listener can be configured using the
WALLET_LOCATION parameter in
listener.ora.
WALLET_LOCATION can be specified for each listener in
listener.ora.
LISTENER =
(DESCRIPTION=
(ADDRESS=
(PROTOCOL=tcps)
(HOST=)
(PORT=5678))
(SECURITY=
(WALLET_LOCATION=dir1)))
LISTENER2 =
(DESCRIPTION=
(ADDRESS=
(PROTOCOL=tcps)
(HOST=)
(PORT=5679))
(SECURITY=
(WALLET_LOCATION=dir2)))Parent topic: Oracle Wallet Location
21.3.3.3 Configuring PDB Wallet Location for server
The multi-tenant architecture enables an Oracle database to function as a multi-tenant container database (CDB) that includes zero, one, or many customer-created pluggable databases (PDBs).
CDB$ROOT and each PDB can have its own local wallet which can be configured with the
WALLET_ROOT system parameter defined in the
init.ora file.
WALLET_ROOT/tlsWALLET_ROOT/<pdb_GUID>/tlsNote:
The parameterWALLET_LOCATION is deprecated for
use with Oracle AI Database 26ai for the Oracle Database server. It is not
deprecated for use with the Oracle Database client or listener.For Oracle Database server, Oracle recommends that you use the
WALLET_ROOT system parameter instead of using
WALLET_LOCATION.
Parent topic: Oracle Wallet Location
21.3.3.4 Oracle Wallet Search Order
Oracle Database provides several routes for finding the wallet on a server in a Transport Layer Security (TLS) environment.
How the Oracle Database Server locates wallets for use in TLS
The Oracle Database server locates the wallet by searching in the
following locations in the specified order. If the database has one or more
pluggable databases (PDB), the value for pdb_GUID must be replaced
with the global identifier (GUID) of the PDB.
- Location defined by the
WALLET_ROOTsystem parameter in theinit.orafile:WALLET_ROOT/<pdb_ID>/tlsfor PDBWALLET_ROOT/tlsfor the CDB root container,CDB$ROOT
- Location defined by the
WALLET_LOCATIONin thesqlnet.orafile:WALLET_LOCATIONNote:
The parameterWALLET_LOCATIONis deprecated for use with Oracle AI Database 26ai for the Oracle Database server. It is not deprecated for use with the Oracle Database client or listener.For Oracle Database server, Oracle recommends that you use the
WALLET_ROOTsystem parameter instead of usingWALLET_LOCATION.
- Location defined by the
$TNS_ADMINenvironment variable. This is the only directory location that will be checked, not any sub-directory underneath this location. - Default wallet location:
- Linux:
/etc/ORACLE/WALLETS/user_nameThis is the only directory location that will be checked, not any sub-directory underneath this location.
- Windows:
C:\Users\user_name\ORACLE\WALLETSThis is the only directory location that will be checked, not any sub-directory underneath this location.
- Linux:
- If a single wallet is needed for some or all of the CDB container databases,
then place the wallet in
TNS_ADMINor the default wallet location. Then the PDB will default to that location when it can't find a wallet underWALLET_ROOT.
How the Oracle Database Listener locates wallets for use in TLS
The Oracle Database Listener locates the wallet location by searching in these locations, in the specified order:
- Location defined by the
WALLET_LOCATIONparameter in thelistener.orafile - Location defined by the
$TNS_ADMINenvironment variable - Default wallet location:
- Linux:
/etc/ORACLE/WALLETS/user_name - Windows:
C:\Users\user_name\ORACLE\WALLETS
- Linux:
How the Oracle Database Client locates wallets for use in TLS
Oracle Database Client locates the wallet by searching in these locations, in the specified order:
- Location defined by the
WALLET_LOCATIONparameter in the connection string - Location defined by the
WALLET_LOCATIONparameter in thesqlnet.orafile - Location defined by the
$TNS_ADMINenvironment variable - Default wallet location:
- Linux:
/etc/ORACLE/WALLETS/user_name - Windows:
C:\Users\user_name\ORACLE\WALLETS
- Linux:
- System certificate store
When one-way TLS authentication is desired, Oracle Database Client can use the trusted CA certificates present in the system certificate store. If the client has a need to support client authentication on the connections, it must setup a wallet containing its own certificate along with required trusted CA certificates.
The default certificate store location depends on the platform. At present, Oracle Database supports this method natively on Microsoft Windows and Linux.
For Windows, it is in the Microsoft Certificate Store for Microsoft Windows.
For Linux, its locations are as follows:
- RHEL/Oracle Linux:
/etc/pki/tls/cert.pem - Debian/Ubuntu/Gentoo:
/etc/ssl/certs/ca-certificates.crt - Fedora/RHEL:
/etc/pki/tls/certs/ca-bundle.crt - OpenSUSE:
/etc/ssl/ca-bundle.pem - OpenELEC:
/etc/pki/tls/cacert.pem - CentOS/RHEL7:
/etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem - Alpine Linux:
/etc/ssl/cert.pem
- RHEL/Oracle Linux:
Note:
You cannot change the default location of the certificate store.Parent topic: Oracle Wallet Location
21.3.4 Enable Weak DN Matching
The SSL_ALLOW_WEAK_DN_MATCH parameter control reverts the
DN matching behavior to prior database versions.
Starting in Oracle AI
Database
26ai, the behavior of the
SSL_SERVER_DN_MATCH parameter has changed.
Server-side certificate verification through distinguished name (DN) is changed as follows: Both the listener certificate and the database server certificate are checked. In earlier Oracle Database releases, only the database server certificate was checked. In most production cases, the same certificate is used by the listener and the database. In cases where different certificates are used, DN matching can require new certificates to allow partial DN matching on SAN or hostname certificate information. In addition to checking the listener certificate, when using partial DN matching is used, the SERVICE_NAME parameter will be ignored Only the hostname connect string parameter will be checked against the certificate common name (CN) and subject alternate name (SAN) fields. To revert to the behavior in earlier releases (using the service name in addition to hostname, and only checking the database server certificate), set the new parameter: SSL_ALLOW_WEAK_DN_MATCH=TRUE. The default is FALSE.
You can set SSL_ALLOW_WEAK_DN_MATCH as follows:
TRUEenablesSSL_SERVER_DN_MATCHto check the database server certificate (but not the listener) and enable the service name to be used for partial DN matching. The search order on the client side is as follows: first, the client sqlnet.ora or connect string host name value is compared against the certificate CN, then the list of names in the subject alternative name (SAN) field. Then the client sqlnet.ora or connect string service_name value is compared against the CN and the list of names in the SAN.FALSE(the default) disablesSSL_SERVER_DN_MATCHfrom checking service name matching. Instead, matching on the client side is based on a search for theHOSTvalue in the certificate DN, and if that is not available, then in the subject alternative name (SAN) field (but not the service name). The DN check is performed on the listener and the server certificates.
If you used the service name for partial DN matching previously, then you
must either get a new certificate or set SSL_ALLOW_WEAK_DN_MATCH to
TRUE to revert to the pre-release 26ai behavior. You are most likely using the
same certificate for both the database server and listener, but if you are not, then you
will either need to do one of the following:
- Get a new certificate (use the
orapki wallet addcommand for self-signed certificates). - Change or remove the DN matching strategy.
- Set the
SSL_ALLOW_WEAK_DN_MATCHparameter toTRUEto revertSSL_SERVER_DN_MATCHto its older behavior.
When you set SSL_ALLOW_WEAK_DN_MATCH to TRUE, note the
following:
- When the client performs a full DN match (
SSL_SERVER_MATCH=TRUE,SSL_SERVER_CERT_DN="certificate_DN"), then only the database server certificate DN will need to match theSSL_SERVER_CERT_DNvalue. - When the client performs a partial DN match
(
SSL_SERVER_MATCH=TRUE,SSL_SERVER_CERT_DNis not set), then Oracle AI Database will compare the connect string parameterHOSTto the common name (CN) of the database server certificate DN and the certificate subject alternate names field (SAN). If there is no partial match, then Oracle AI Database will continue and check theSERVICE_NAMEparameter with the CN.
Parent topic: Advanced and Optional Configurations
21.3.5 Private Key/Certificate Selection
You can have multiple private key/certificate pairs stored in either the Oracle wallet or a system certificate store to use for certificates. This is sometimes necessary when different databases will assign different client credentials for mTLS, such as for Autonomous Database.
You can only specify the private key/certificate to be used with Windows MCS and Oracle Wallets.
You will need to specify the correct private key/certificate to use for a database connection. By setting the certificate selection parameters for client authentication on Windows, the MSCAPI certificate selection box will not appear, and the matching certificate is automatically used for Transport Layer Security.
While it is more likely that the client will need to select a specific private key/certificate from MCS or the wallet, the server and listener may also need to select a specific certificate for use if there is more than one in the wallet.
- Setting the SSL_CERTIFICATE_ALIAS Parameter
You can use theSSL_CERTIFICATE_ALIASparameter to specify the alias of the client certificate. - Setting the SSL_CERTIFICATE_THUMBPRINT Parameter
You can use theSSL_CERTIFICATE_THUMBPRINTto specify the thumbprint of the client certificate. - Setting the SSL_EXTENDED_KEY_USAGE Parameter
You can use theSSL_EXTENDED_KEY_USAGEparameter to specify the extended key usage of the client certificate.
Parent topic: Advanced and Optional Configurations
21.3.5.1 Setting the SSL_CERTIFICATE_ALIAS Parameter
You can use the SSL_CERTIFICATE_ALIAS parameter to specify the alias of the client certificate.
-
To get the alias name value, run the following
orapkicommand:orapki wallet display -wallet wallet_directory -pwd wallet_password -complete
The output will look similar to the following. See theAliasfield.User Certificates: Alias: sslClient Subject: CN=ssl ClientIssuer: CN=sslRoot,C=US Not Before: Thu Jul 18 22:29:17 UTC 2024 Not After: Sun Jul 16 22:29:17 UTC 2034 Serial Number: 01 Key Length: 2048 MD5 digest: 06:DD:79:AF:E6:D6:70:CE:C3:98:DE:8C:D7:FC:7E:C2 SHA-256 digest: 09:B2:EC:FE:A1:B8:C3:F3:F5:A7:DC:C6:00:26:86:BE:39:54:16:93:B6:A8:42:CC:69:24:0F:B5:59:43:3F:AA SHA-1 digest: 51:25:6F:45:F8:64:E5:CB:9E:56:D2:F2:0C:5C:A6:D5:61:DA:DB:FE - Set the
Aliasvalue using theSSL_CERTIFICATE_ALIASparameter.For example, for
tnsnames.ora:net_service_name= (DESCRIPTION= (ADDRESS=(PROTOCOL=tcps)(HOST=sales-svr)(PORT=1522)) (SECURITY=(SSL_CERTIFICATE_ALIAS=sslClient)) )This example shows how to set
SSL_CERTIFICATE_ALIASin thesqlnet.orafile:SSL_CERTIFICATE_ALIAS=sslClient
Related Topics
Parent topic: Private Key/Certificate Selection
21.3.5.2 Setting the SSL_CERTIFICATE_THUMBPRINT Parameter
You can use the SSL_CERTIFICATE_THUMBPRINT to specify the thumbprint of the client certificate.
algorithm:hash format
-
To get the thumbprint value, run the following
orapkicommand:orapki wallet display -wallet wallet_directory -pwd wallet_password -complete
The output will look similar to the following. See theSHA-1 digestorSHA-256 digestfield for the thumbprint value.User Certificates: Alias: sslClient Subject: CN=ssl ClientIssuer: CN=sslRoot,C=US Not Before: Thu Jul 18 22:29:17 UTC 2024 Not After: Sun Jul 16 22:29:17 UTC 2034 Serial Number: 01 Key Length: 2048 MD5 digest: 06:DD:79:AF:E6:D6:70:CE:C3:98:DE:8C:D7:FC:7E:C2 SHA-256 digest: 09:B2:EC:FE:A1:B8:C3:F3:F5:A7:DC:C6:00:26:86:BE:39:54:16:93:B6:A8:42:CC:69:24:0F:B5:59:43:3F:AA SHA-1 digest: 51:25:6F:45:F8:64:E5:CB:9E:56:D2:F2:0C:5C:A6:D5:61:DA:DB:FE - Set this value using the
SSL_CERTIFICATE_THUMBPRINTparameter. The following example shows how to set it in thetnsnames.orafile.For example, in the
tnsname.orafile:net_service_name= (DESCRIPTION= (ADDRESS=(PROTOCOL=tcps)(HOST=sales-svr)(PORT=1522)) (SECURITY=(SSL_CERTIFICATE_THUMBPRINT=SHA1:1B:11:01:5A:B1:2C:20:B2:12:34:3E:04:7B:83:47:DE:70:2E:4E:11)) )This example shows how to set
SSL_CERTIFICATE_THUMBPRINTin thesqlnet.orafile:SSL_CERTIFICATE_THUMBPRINT=SHA256:B38A5B1A036383922B5DE15361EE03940A56B456417E4124419B88EBC61E1123
Related Topics
Parent topic: Private Key/Certificate Selection
21.3.5.3 Setting the SSL_EXTENDED_KEY_USAGE Parameter
You can use the SSL_EXTENDED_KEY_USAGE parameter to specify
the extended key usage of the client certificate.
SQLNET.SSL_EXTENDED_KEY_USAGE parameter if you have multiple certificates in the security module, but there is only one certificate with extended key usage field of client authentication, and this certificate is the one you want to use to authenticate to the database.
-
For example, in the
sqlnet.orafile:SSL_EXTENDED_KEY_USAGE = "client authentication"
orapki:orapki cert display -cert <certificate> -completeRelated Topics
Parent topic: Private Key/Certificate Selection
21.3.6 Transport Layer Security Encryption Combined with Authentication Methods
You can configure Oracle Database to use TLS concurrently with all authentication mechanisms such as database user names and passwords, RADIUS, Kerberos, PKI certificates, MS-EI, and OCI IAM.
Architecture: Oracle Database and Transport Layer Security
The Oracle Net Services with Authentication Adapters diagram, displays the Oracle Database implementation of Transport Layer Security architecture, shows that Oracle Databases operates at the session layer on top of TLS and uses TCP/IP at the transport layer. The session layer is a network layer that provides the services needed by the presentation layer entities that enable them to organize and synchronize their dialogue and manage their data exchange. This layer establishes, manages, and terminates network sessions between the client and server. The transport layer is a networking layer that maintains end-to-end reliability through data flow control and error recovery methods.
This separation of functionality lets you employ TLS concurrently with other supported protocols.
Figure 21-1 Oracle Net Services with Authentication Adapters
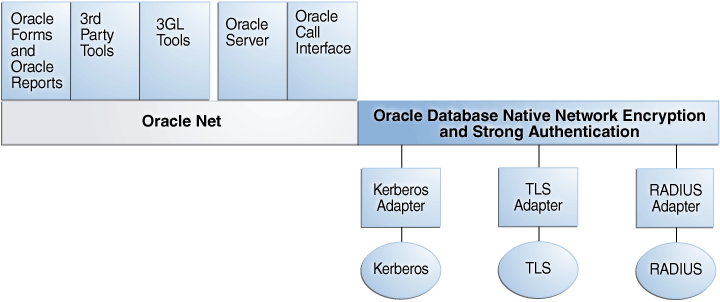
Description of "Figure 21-1 Oracle Net Services with Authentication Adapters"
How Transport Layer Security Works with Other Authentication Methods
Transport Layer Security can be used with other authentication methods that Oracle Database supports.
**INTERNAL XREF ERROR** illustrates a configuration in which Transport Layer Security is used in combination with another authentication method.
Figure 21-2 Transport Layer Security in Relation to Other Authentication Methods
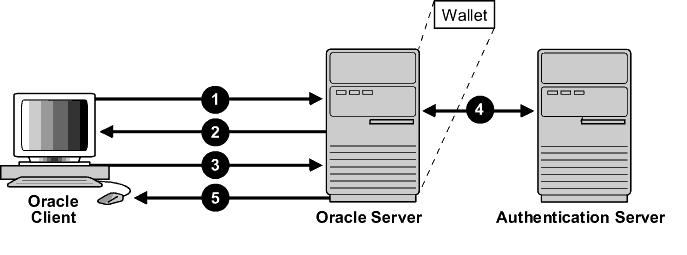
Description of "Figure 21-2 Transport Layer Security in Relation to Other Authentication Methods"
In this example, Transport Layer Security is used to establish an encrypted network connection between the client and server, and an alternative authentication method is used to authenticate the client into the database. The process is as follows:
-
The client seeks to connect to the Oracle database server.
-
Transport Layer Security performs a handshake during which the server authenticates itself to the client and both the client and server establish which cipher suite to use.
-
Once the Transport Layer Security handshake is successfully completed, the user seeks access to the database.
-
The Oracle database server authenticates the user with the authentication server using a non-TLS authentication method such as a password, Kerberos, RADIUS, or a cloud identity token (Oracle Cloud Infrastructure (OCI) Identity and Access Management (IAM), Microsoft Azure AD).
-
Upon validation by the authentication method, the Oracle database server grants access and authorization to the user, and then the user can access the database securely by using TLS.
Related Topics
Parent topic: Advanced and Optional Configurations
21.3.7 Specifying TLS Protocol and TLS Cipher Suites
Oracle AI Database 26ai supports TLS protocol versions 1.2 and 1.3 and their associated cipher suites for Transport Layer Security (TLS).
Oracle provides the configuration parameters SSL_VERSION,
and SSL_CIPHER_SUITE to configure the specific protocol version and
cipher suites. However, Oracle recommends that you do not specify these parameters
unless required. Omitting these values facilitate auto-detection of the strongest common
TLS version (which ensures that the highest available version is selected) and their
associated cipher suites. Oracle AI
Database uses the TLS_AES_256_GCM_SHA384 cipher suite as the default.
- Configuring TLS Protocol Versions
TheSSL_VERSIONandTLS_DISABLE_VERSIONparameters define the protocol version of TLS that is enforced at the end point of the component where they are specified. - Configuring TLS Cipher Suites
A cipher suite is a set of authentication, encryption, and data integrity algorithms used for exchanging messages between network entities. - Allowing Certificates from Earlier Algorithms
You can use certificates that were associated with earlier deprecated (and weaker) algorithms by setting theALLOWED_WEAK_CERT_ALGORITHMSsqlnet.oraorlistener.oraparameter. - Configuring TLS Key Exchange Algorithms
You can specify the TLS key exchange algorithm by setting theTLS_KEY_EXCHANGE_GROUPSparameter insqlnet.oraorlistener.ora.
Parent topic: Advanced and Optional Configurations
21.3.7.1 Configuring TLS Protocol Versions
The SSL_VERSION and TLS_DISABLE_VERSION
parameters define the protocol version of TLS that is enforced at the end point of the
component where they are specified.
SSL_VERSION and TLS_DISABLE_VERSION can be
specified with the database server, the listener, the client, or a combination of these
components. If the TLS protocol version is specified in more than one of these
locations, then at least one version must be common across all of the components.
Otherwise, the connection will be rejected. Also, if a TLS protocol version is specified
that is not supported by another component, then the connection request will also be
rejected.
You can set the SSL_VERSION and
TLS_DISABLE_VERSION parameters in the client or server
sqlnet.ora or the listener.ora file.
SSL_VERSION Parameter
In the server sqlnet.ora file, set the
SSL_VERSION parameter to indicate the supported TLS versions on
the server.
undetermined (the default),
TLSv1.2, and TLSv1.3. Separate multiple
entries with a comma. For
example:SSL_VERSION=(TLSv1.2,TLSv1.3)+ to the values to specify the minimum version. For
example:SSL_VERSION=TLSv1.2+SSL_VERSION and TLS_DISABLE_VERSION
are not set, or SSL_VERSION set to undetermined,
all supported TLS versions are enabled.
Tip:
Oracle recommends that you do not specify these parameters so that the highest version is auto-detected between server and client.For environments where you want to enforce TLSv1.3 explicitly, you may specify the protocol version as follows:
SSL_VERSION = TLSv1.3TLS_DISABLE_VERSION Parameter
In the server sqlnet.ora file, set the
TLS_DISABLE_VERSION parameter to indicate the TLS versions to
not allow on the server.
TLSv1.2 and TLSv1.3.
Separate multiple entries with a comma. For
example:TLS_DISABLE_VERSION=(TLSv1.2,TLSv1.3)Parent topic: Specifying TLS Protocol and TLS Cipher Suites
21.3.7.2 Configuring TLS Cipher Suites
A cipher suite is a set of authentication, encryption, and data integrity algorithms used for exchanging messages between network entities.
During a Transport Layer Security handshake, two entities negotiate to select a cipher suite they will use when transmitting messages to each other through the network.
When you install Oracle Database, the Transport Layer Security cipher suites are set for
you by default and negotiated in the order they are listed from the strongest cipher
suite. You can override the default order by setting the
SSL_CIPHER_SUITES parameter. Ensure that you enclose the
SSL_CIPHER_SUITES parameter setting in parentheses (for example,
SSL_CIPHER_SUITES=(TLS_AES_256_GCM_SHA384)). Otherwise, the cipher
suite setting will not parse correctly.
You can prioritize the cipher suites. When the client negotiates with servers to determine which cipher suite to use, it follows the prioritization you set. When you prioritize the cipher suites, consider the following:
-
Compatibility: The server and client must be configured to use compatible cipher suites for a successful connection.
-
Cipher priority and strength: Prioritize cipher suites starting with the strongest and moving to the weakest to ensure the highest level of security possible.
-
The level of security you want to use: Use this to prevent older clients with weaker cipher suites from connecting to the database
- Strong TLS Cipher Suites
Oracle provides strong Transport Layer Security (TLS) cipher suites by default. Starting with Oracle AI Database 26ai, however, Oracle only supports TLSv1.2 and above. The default ciphers supported by Oracle are shown in the table below. - Deprecated TLS Cipher Suites
To accommodate legacy products, Oracle provides TLS cipher suites which are considered less secure. Those ciphers are deprecated and disabled by default. The deprecated ciphers supported by Oracle are shown in the table below. - Enabling Weak Cipher Suites
You can enable deprecated cipher suites by setting theSSL_ENABLE_WEAK_CIPHERSparameter. For the connections to be successful with the weak cipher suites, all three components (client, listener, and server) need to have the weak cipher suites enabled.
Parent topic: Specifying TLS Protocol and TLS Cipher Suites
21.3.7.2.1 Strong TLS Cipher Suites
Oracle provides strong Transport Layer Security (TLS) cipher suites by default. Starting with Oracle AI Database 26ai, however, Oracle only supports TLSv1.2 and above. The default ciphers supported by Oracle are shown in the table below.
Table 21-6 Approved TLS Cipher Suites
| Cipher Suite | Authentication | Encryption | Data Integrity | TLS Compatibility |
|---|---|---|---|---|
| TLS_AES_128_CCM_SHA256 | ECDHE_RSA, DHE_RSA, ECDHE_ECDSA | AES 128 CCM | SHA256 (SHA 2) | TLS 1.3 |
| TLS_AES_128_GCM_SHA256 | ECDHE_RSA, DHE_RSA, ECDHE_ECDSA | AES 128 GCM | SHA256 (SHA-2) | TLS 1.3 |
| TLS_AES_256_GCM_SHA384 | ECDHE_RSA, DHE_RSA, ECDHE_ECDSA | AES 256 GCM | SHA384 (SHA-2) | TLS 1.3 |
| TLS_CHACHA20_POLY1305_SHA256 (non-FIPS only) | ECDHE_RSA, DHE_RSA, ECDHE_ECDSA | CHACHA20 POLY1305 | SHA256 (SHA-2) | TLS 1.3 |
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 | DHE_RSA | AES 128 GCM | SHA256 (SHA-2) | TLS 1.2 |
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 | DHE_RSA | AES 256 GCM | SHA384 (SHA-2) | TLS 1.2 |
| TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 | ECDHE_ECDSA | AES 128 GCM | SHA256 (SHA-2) | TLS 1.2 |
| TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 | ECDHE_ECDSA | AES 256 GCM | SHA384 (SHA-2) | TLS 1.2 |
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 | ECDHE_RSA | AES 128 GCM | SHA256 (SHA-2) | TLS 1.2 |
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 | ECDHE_RSA | AES 256 GCM | SHA384 (SHA-2) | TLS 1.2 |
Parent topic: Configuring TLS Cipher Suites
21.3.7.2.2 Deprecated TLS Cipher Suites
To accommodate legacy products, Oracle provides TLS cipher suites which are considered less secure. Those ciphers are deprecated and disabled by default. The deprecated ciphers supported by Oracle are shown in the table below.
Table 21-7 Deprecated TLS Cipher Suites
| Cipher Suite | Authentication | Encryption | Data Integrity | TLS Compatibility |
|---|---|---|---|---|
|
TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 |
DHE_RSA |
AES 128 CBC |
SHA256 (SHA-2) |
TLS 1.2 |
|
TLS_DHE_RSA_WITH_AES_256_CBC_SHA |
DHE_RSA |
AES 256 CBC |
SHA (SHA-1) |
TLS 1.2 |
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 |
DHE_RSA |
AES 256 CBC |
SHA256 (SHA-2) |
TLS 1.2 |
|
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA |
ECDHE_ECDSA |
AES 128 CBC |
SHA (SHA-1) |
TLS 1.2 |
|
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA |
ECDHE_ECDSA |
AES 128 CBC |
SHA (SHA-1) |
TLS 1.2 |
|
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 |
ECDHE_ECDSA |
AES 128 CBC |
SHA256 (SHA-2) |
TLS 1.2 |
|
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA |
ECDHE_ECDSA |
AES 256 CBC |
SHA (SHA-1) |
TLS 1.2 |
|
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 |
ECDHE_ECDSA |
AES 256 CBC |
SHA384 (SHA-2) |
TLS 1.2 |
|
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA |
ECDHE_RSA |
AES 128 CBC |
SHA (SHA-1) |
TLS 1.2 |
|
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 |
ECDHE_RSA |
AES 128 CBC |
SHA256 (SHA-2) |
TLS 1.2 |
|
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA |
ECDHE_RSA |
AES 256 CBC |
SHA (SHA-1) |
TLS 1.2 |
|
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 |
ECDHE_RSA |
AES 256 CBC |
SHA384 (SHA-2) |
TLS 1.2 |
|
TLS_RSA_WITH_AES_128_CBC_SHA |
RSA |
AES 128 CBC |
SHA (SHA-1) |
TLS 1.2 |
|
TLS_RSA_WITH_AES_128_CBC_SHA256 |
RSA |
AES 128 CBC |
SHA256 (SHA-2) |
TLS 1.2 |
|
TLS_RSA_WITH_AES_128_GCM_SHA256 |
RSA |
AES 128 GCM |
SHA256 (SHA-2) |
TLS 1.2 |
|
TLS_RSA_WITH_AES_256_CBC_SHA |
RSA |
AES 256 CBC |
SHA (SHA-1) |
TLS 1.2 |
|
TLS_RSA_WITH_AES_256_CBC_SHA256 |
RSA |
AES 256 CBC |
SHA256 (SHA-2) |
TLS 1.2 |
|
TLS_RSA_WITH_AES_256_GCM_SHA384 |
RSA |
AES 256 GCM |
SHA384 (SHA-2) |
TLS 1.2 |
Parent topic: Configuring TLS Cipher Suites
21.3.7.2.3 Enabling Weak Cipher Suites
You can enable deprecated cipher suites by setting the
SSL_ENABLE_WEAK_CIPHERS parameter. For the connections to be successful
with the weak cipher suites, all three components (client, listener, and server) need to
have the weak cipher suites enabled.
In this specification, value can be one of the following:
FALSE(orOFF,NO,0) disables the weak ciphers. The setting is the default. If you try to use a weak cipher, then depending on where you are, the following errors appear:- In the database server:
ORA-28860: Fatal SSL error - In the database client:
ORA-29039: There are no matching cipher suites.
- In the database server:
TRUE(orON,YES,1) enables the weak ciphers.
For example, to enable the deprecated cipher suites,
SSL_ENABLE_WEAK_CIPHERS=TRUEParent topic: Configuring TLS Cipher Suites
21.3.7.3 Allowing Certificates from Earlier Algorithms
You can use certificates that were associated with earlier deprecated (and
weaker) algorithms by setting the ALLOWED_WEAK_CERT_ALGORITHMS
sqlnet.ora or listener.ora parameter.
ALLOWED_WEAK_CERT_ALGORITHMS allows you to explicitly
enable earlier algorithms. However, be aware that earlier algorithms are less secure
than newer algorithms. This parameter replaces the ALLOW_MD5_CERTS and
ALLOW_SHA1_CERTS parameters, which are deprecated starting in Oracle AI
Database release 26ai.
Parent topic: Specifying TLS Protocol and TLS Cipher Suites
21.3.7.4 Configuring TLS Key Exchange Algorithms
You can specify the TLS key exchange algorithm by setting the
TLS_KEY_EXCHANGE_GROUPSparameter in sqlnet.ora or
listener.ora.
The Oracle Net Services parameter
SSL_DISABLE_WEAK_EC_CURVES is deprecated in Oracle AI Database 26ai. As a result, the TLS_KEY_EXCHANGE_GROUPS parameter should be used to
replace it.
- Login to the database server or the client server.
- Edit the
sqlnet.oraorlistener.orafile to include theTLS_KEY_EXCHANGE_GROUPSparameter.The default location of the
sqlnet.orafile is in the$ORACLE_HOME/network/admindirectory.See TLS_KEY_EXCHANGE_GROUPS in Oracle AI Database Net Services Reference for more information.
Related Topics
Parent topic: Specifying TLS Protocol and TLS Cipher Suites
21.3.8 Certificate Validation with Certificate Revocation Lists
Oracle provides tools that enable you to validate certificates using certificate revocation lists.
- About Certificate Validation with Certificate Revocation Lists
The process of determining whether a given certificate can be used in a given context is referred to as certificate validation. - What CRLs Should You Use?
You should have CRLs for all of the trust points that you honor. - How CRL Checking Works
Oracle Database checks the certificate revocation status against CRLs. - Configuring Certificate Validation with Certificate Revocation Lists
You can edit thesqlnet.orafile to configure certificate validation with certificate revocation lists. - Certificate Revocation List Management
Certificate revocation list management entails ensuring that the CRLs are the correct format before you enable certificate revocation checking. - Troubleshooting CRL Certificate Validation
To determine whether certificates are being validated against CRLs, you can enable Oracle Net tracing. - Oracle Net Tracing File Error Messages Associated with Certificate Validation
Oracle generates trace messages that are relevant to certificate validation.
Parent topic: Advanced and Optional Configurations
21.3.8.1 About Certificate Validation with Certificate Revocation Lists
The process of determining whether a given certificate can be used in a given context is referred to as certificate validation.
Certificate validation includes determining that the following takes place:
-
A trusted certificate authority (CA) has digitally signed the certificate
-
The certificate's digital signature corresponds to the independently-calculated hash value of the certificate itself and the certificate signer's (CA's) public key
-
The certificate has not expired
-
The certificate has not been revoked
The Transport Layer Security network layer automatically performs the first three validation checks, but you must configure certificate revocation list (CRL) checking to ensure that certificates have not been revoked. CRLs are signed data structures that contain a list of revoked certificates. They are usually issued and signed by the same entity who issued the original certificate.
Parent topic: Certificate Validation with Certificate Revocation Lists
21.3.8.2 What CRLs Should You Use?
You should have CRLs for all of the trust points that you honor.
The trust points are the trusted certificates from a third party identity that is qualified with a level of trust.
Typically, the certificate authorities you trust are called trust points.
Parent topic: Certificate Validation with Certificate Revocation Lists
21.3.8.3 How CRL Checking Works
Oracle Database checks the certificate revocation status against CRLs.
These CRLs are located in file system directories, Oracle Internet Directory, or downloaded from the location specified in the CRL Distribution Point (CRL DP) extension on the certificate.
Typically, CRL definitions are valid for a few days. If you store your CRLs on the local file system or in the directory, then you must update them regularly. If you use a CRL Distribution Point (CRL DP), then CRLs are downloaded each time a certificate is used, so there is no need to regularly refresh the CRLs.
The server searches for CRLs in the following locations in the order listed. When the system finds a CRL that matches the certificate CA's DN, it stops searching.
-
Local file system
The server checks the
sqlnet.orafile for theSSL_CRL_FILEparameter first, followed by theSSL_CRL_PATHparameter. If these two parameters are not specified, then the server checks the wallet location for any CRLs.Note:
If you store CRLs on your local file system, then you must use theorapkiutility to periodically update them (for example, renaming CRLs with a hash value for certificate validation). -
Oracle Internet Directory
If the server cannot locate the CRL on the local file system and directory connection information has been configured in an
ldap.orafile, then the server searches in the directory. It searches the CRL subtree by using the CA's distinguished name (DN) and the DN of the CRL subtree.The server must have a properly configured
ldap.orafile to search for CRLs in the directory. It cannot use the Domain Name System (DNS) discovery feature of Oracle Internet Directory. Also note that if you store CRLs in the directory, then you must use theorapkiutility to periodically update them. -
CRL DP
If the CA specifies a location in the CRL DP X.509, version 3, certificate extension when the certificate is issued, then the appropriate CRL that contains revocation information for that certificate is downloaded. Currently, Oracle Database supports downloading CRLs over LDAP.
Note the following:
-
For performance reasons, only user certificates are checked.
-
Oracle recommends that you store CRLs in the directory rather than the local file system.
-
21.3.8.4 Configuring Certificate Validation with Certificate Revocation Lists
You can edit the sqlnet.ora file to configure certificate validation with certificate revocation lists.
- About Configuring Certificate Validation with Certificate Revocation Lists
TheSSL_CERT_REVOCATIONparameter must be set toREQUIREDorREQUESTEDin thesqlnet.orafile to enable certificate revocation status checking. - Enabling Certificate Revocation Status Checking for the Client or Server
You can enable certificate revocation status checking for a client or a server. - Disabling Certificate Revocation Status Checking
You can disable certificate revocation status checking.
Parent topic: Certificate Validation with Certificate Revocation Lists
21.3.8.4.1 About Configuring Certificate Validation with Certificate Revocation Lists
The SSL_CERT_REVOCATION parameter must be set to REQUIRED or REQUESTED in the sqlnet.ora file to enable certificate revocation status checking.
By default this parameter is set to NONE indicating that certificate revocation status checking is turned off.
Note:
If you want to store CRLs on your local file system or in Oracle Internet Directory, then you must use the command line utility, orapki, to rename CRLs in your file system or upload them to the directory.
Related Topics
21.3.8.4.2 Enabling Certificate Revocation Status Checking for the Client or Server
You can enable certificate revocation status checking for a client or a server.
21.3.8.5 Certificate Revocation List Management
Certificate revocation list management entails ensuring that the CRLs are the correct format before you enable certificate revocation checking.
- About Certificate Revocation List Management
Oracle Database provides a command-line utility,orapki, that you can use to manage certificate revocation lists (CRL). - Displaying orapki Help for Commands That Manage CRLs
You can display all theorapkicommands that are available for managing CRLs. - Renaming CRLs with a Hash Value for Certificate Validation
When the system validates a certificate, it must locate the CRL issued by the CA who created the certificate. - Uploading CRLs to Oracle Internet Directory
Publishing CRLs in the directory enables CRL validation throughout your enterprise, eliminating the need for individual applications to configure their own CRLs. - Listing CRLs Stored in Oracle Internet Directory
You can display a list of all CRLs stored in the directory withorapki, which is useful for browsing to locate a particular CRL to view or download to your local computer. - Viewing CRLs in Oracle Internet Directory
Oracle Internet Directory CRLs are available in a summarized format; you also can request a listing of revoked certificates for a CRL. - Deleting CRLs from Oracle Internet Directory
The user who deletes CRLs from the directory by usingorapkimust be a member of the directory groupCRLAdmins.
Parent topic: Certificate Validation with Certificate Revocation Lists
21.3.8.5.1 About Certificate Revocation List Management
Oracle Database provides a command-line utility, orapki,
that you can use to manage certificate revocation lists (CRL).
Before you can enable certificate revocation status checking, you must ensure that the CRLs you receive from the CAs you use are in a form (renamed with a hash value) or in a location (uploaded to the directory) where your computer can use them.
You can also use LDAP command-line tools to manage CRLs in Oracle Internet Directory.
Note:
CRLs must be updated at regular intervals (before they expire) for successful validation. You can automate this task by using orapki commands in a script
Parent topic: Certificate Revocation List Management
21.3.8.5.2 Displaying orapki Help for Commands That Manage CRLs
You can display all the orapki commands that are available for managing CRLs.
-
To display all the
orapkiavailable CRL management commands and their options, enter the following at the command line:orapki crl help
Note:
Using the -summary, -complete, or -wallet command options is always optional. A command will still run if these command options are not specified.
Parent topic: Certificate Revocation List Management
21.3.8.5.3 Renaming CRLs with a Hash Value for Certificate Validation
When the system validates a certificate, it must locate the CRL issued by the CA who created the certificate.
The system locates the appropriate CRL by matching the issuer name in the certificate with the issuer name in the CRL.
When you specify a CRL storage location for the Certificate Revocation Lists Path field in Oracle Net Manager, which sets the SSL_CRL_PATH parameter in the sqlnet.ora file, use the orapki utility to rename CRLs with a hash value that represents the issuer's name. Creating the hash value enables the server to load the CRLs.
On UNIX operating systems, orapki creates a symbolic link to the CRL. On Windows operating systems, it creates a copy of the CRL file. In either case, the symbolic link or the copy created by orapki are named with a hash value of the issuer's name. Then when the system validates a certificate, the same hash function is used to calculate the link (or copy) name so the appropriate CRL can be loaded.
-
Depending on the operating system, enter one of the following commands to rename CRLs stored in the file system:
-
To rename CRLs stored in UNIX file systems:
orapki crl hash -crl crl_filename [-wallet wallet_location] -symlink crl_directory [-summary]
-
To rename CRLs stored in Windows file systems:
orapki crl hash -crl crl_filename [-wallet wallet_location] -copy crl_directory [-summary]
-
In this specification, crl_filename is the name of the CRL file, wallet_location is the location of a wallet that contains the certificate of the CA that issued the CRL, and crl_directory is the directory where the CRL is located.
Using -wallet and -summary are optional. Specifying -wallet causes the tool to verify the validity of the CRL against the CA's certificate prior to renaming the CRL. Specifying the -summary option causes the tool to display the CRL issuer's name.
Parent topic: Certificate Revocation List Management
21.3.8.5.4 Uploading CRLs to Oracle Internet Directory
Publishing CRLs in the directory enables CRL validation throughout your enterprise, eliminating the need for individual applications to configure their own CRLs.
All applications can use the CRLs stored in the directory where they can be centrally managed, greatly reducing the administrative overhead of CRL management and use. The user who uploads CRLs to the directory by using orapki must be a member of the directory group CRLAdmins (cn=CRLAdmins,cn=groups,%s_OracleContextDN%). This is a privileged operation because these CRLs are accessible to the entire enterprise. Contact your directory administrator to get added to this administrative directory group.
-
To upload CRLs to the directory, enter the following at the command line:
orapki crl upload -crl crl_location -ldap hostname:ssl_port -user username [-wallet wallet_location] [-summary]
In this specification,
crl_locationis the file name or URL where the CRL is located,hostnameandssl_port(TLS port with no authentication) are for the system on which your directory is installed,usernameis the directory user who has permission to add CRLs to the CRL subtree, andwallet_locationis the location of a wallet that contains the certificate of the CA that issued the CRL.
Using -wallet and -summary are optional. Specifying -wallet causes the tool to verify the validity of the CRL against the CA's certificate prior to uploading it to the directory. Specifying the -summary option causes the tool to print the CRL issuer's name and the LDAP entry where the CRL is stored in the directory.
The following example illustrates uploading a CRL with the orapki utility:
orapki crl upload -crl /home/user1/wallet/crldir/crl.txt -ldap host1.example.com:3533 -user cn=orcladmin
Note:
-
The
orapkiutility will prompt you for the directory password when you perform this operation. -
Ensure that you specify the directory SSL port on which the Diffie-Hellman-based TLS server is running. This is the TLS port that does not perform authentication. Neither the server authentication nor the mutual authentication TLS ports are supported by the
orapkiutility.
Parent topic: Certificate Revocation List Management
21.3.8.5.5 Listing CRLs Stored in Oracle Internet Directory
You can display a list of all CRLs stored in the directory with orapki, which is useful for browsing to locate a particular CRL to view or download to your local computer.
This command displays the CA who issued the CRL (Issuer) and its location (DN) in the CRL subtree of your directory.
-
To list CRLs in Oracle Internet Directory, enter the following at the command line:
orapki crl list -ldap hostname:ssl_port
where thehostnameandssl_portare for the system on which your directory is installed.Note:
This is the directory SSL port with no authentication as described in the preceding section. Uploading CRLs to Oracle Internet Directory
Parent topic: Certificate Revocation List Management
21.3.8.5.6 Viewing CRLs in Oracle Internet Directory
Oracle Internet Directory CRLs are available in a summarized format; you also can request a listing of revoked certificates for a CRL.
Related Topics
Parent topic: Certificate Revocation List Management
21.3.8.5.7 Deleting CRLs from Oracle Internet Directory
The user who deletes CRLs from the directory by using orapki must be a member of the directory group CRLAdmins.
Related Topics
Parent topic: Certificate Revocation List Management
21.3.8.6 Troubleshooting CRL Certificate Validation
To determine whether certificates are being validated against CRLs, you can enable Oracle Net tracing.
When a revoked certificate is validated by using CRLs, then you will see the following entries in the Oracle Net tracing file without error messages logged between entry and exit:
nzcrlVCS_VerifyCRLSignature: entry nzcrlVCS_VerifyCRLSignature: exit nzcrlVCD_VerifyCRLDate: entry nzcrlVCD_VerifyCRLDate: exit nzcrlCCS_CheckCertStatus: entry nzcrlCCS_CheckCertStatus: Certificate is listed in CRL nzcrlCCS_CheckCertStatus: exit
Note:
Note that when certificate validation fails, the peer in the SSL handshake sees an ORA-29024: Certificate Validation Failure.
21.3.8.7 Oracle Net Tracing File Error Messages Associated with Certificate Validation
Oracle generates trace messages that are relevant to certificate validation.
These trace messages may be logged between the entry and exit entries in the Oracle Net tracing file. Oracle SSL looks for CRLs in multiple locations, so there may be multiple errors in the trace.
You can check the following list of possible error messages for information about how to resolve them.
- CRL signature verification failed
-
Cause: The CRL signature cannot be verified.
- CRL date verification failed
-
Cause: The current time is later than the time listed in the next update field. You should not see this error if CRL DP is used. The system searches for the CRL in the following order:
-
File system
-
Oracle Internet Directory
-
CRL DP
The first CRL found in this search may not be the latest.
-
- CRL could not be found
-
Cause: The CRL could not be found at the configured locations. This will return error ORA-29024 if the configuration specifies that certificate validation is required.
- Oracle Internet Directory host name or port number not set
-
Cause: Oracle Internet Directory connection information is not set. Note that this is not an irrecoverable error. The search continues with CRL DP.
- Fetch CRL from CRL DP: No CRLs found
-
Cause: The CRL could not be fetched by using the CRL Distribution Point (CRL DP). This happens if the certificate does not have a location specified in its CRL DP extension, or if the URL specified in the CRL DP extension is incorrect.
Parent topic: Certificate Validation with Certificate Revocation Lists
21.4 TLS and Other Oracle Products
Transport Layer Security (TLS) can be configured when using other Oracle Database products.
- Transport Layer Security Connections in an Oracle Real Application Clusters Environment
You can configure Transport Layer Security (TLS) connections in an Oracle Real Application Clusters (Oracle RAC) environment by using Oracle RAC tools and modifying Oracle Database configuration files.
Parent topic: Configuring Transport Layer Security Encryption
21.4.1 Transport Layer Security Connections in an Oracle Real Application Clusters Environment
You can configure Transport Layer Security (TLS) connections in an Oracle Real Application Clusters (Oracle RAC) environment by using Oracle RAC tools and modifying Oracle Database configuration files.
- Step 1: Configure TCPS Protocol Endpoints
In Oracle Real Application Clusters (Oracle RAC), clients access one of three scan listeners and are then routed to database listeners. To support Transport Layer Security (TLS), all of these listeners must have TCPS protocol endpoints. - Step 2: Ensure That the LOCAL_LISTENER Parameter Is Correctly Set on Each Node
The Oracle Agent automatically sets theLOCAL_LISTENERparameter on each node, but you should double-check to ensure that it is correct. - Step 3: Create Transport Layer Security Wallets and Certificates
You must create Transport Layer Security (TLS) wallets and certificates for the cluster and also for clients that will connect to the cluster over TLS. - Step 4: Create a Wallet in Each Node of the Oracle RAC Cluster
After you have created the cluster wallet, you can copy it to each node of the Oracle Real Applications (Oracle RAC) cluster. - Step 5: Define Wallet Locations in the listener.ora and sqlnet.ora Files
To enable the database server and listeners to access the wallets, you must define the wallet locations in thelistener.oraandsqlnet.orafiles. - Step 6: Restart the Database Instances and Listeners
With the wallets in place and the*.orafiles edited, you must restart the database server and listener processes so that they pick up the new settings. - Step 7: Test the Cluster Node Configuration
To test the cluster node configuration, you can create a connect descriptor for the node and then try to connect to this node. - Step 8: Test the Remote Client Configuration
After you have tested the wallet on the Oracle Real Applications (Oracle RAC) cluster nodes, you are ready to test the remote client configuration.
Parent topic: TLS and Other Oracle Products
21.4.1.1 Step 1: Configure TCPS Protocol Endpoints
In Oracle Real Application Clusters (Oracle RAC), clients access one of three scan listeners and are then routed to database listeners. To support Transport Layer Security (TLS), all of these listeners must have TCPS protocol endpoints.
21.4.1.2 Step 2: Ensure That the LOCAL_LISTENER Parameter Is Correctly Set on Each Node
The Oracle Agent automatically sets the LOCAL_LISTENER parameter on each node, but you should double-check to ensure that it is correct.
21.4.1.3 Step 3: Create Transport Layer Security Wallets and Certificates
You must create Transport Layer Security (TLS) wallets and certificates for the cluster and also for clients that will connect to the cluster over TLS.
- Oracle Real Application Clusters Components That Need Certificates
Specific components in Oracle Real Application Clusters (Oracle RAC) need certificates when you configure Transport Layer Security (TLS) connections. - Creating Transport Layer Security Wallets and Certificates
To create the Transport Layer Security wallets and certificates, you first need to create the root CA certificate, followed by the cluster and client wallets.
21.4.1.3.1 Oracle Real Application Clusters Components That Need Certificates
Specific components in Oracle Real Application Clusters (Oracle RAC) need certificates when you configure Transport Layer Security (TLS) connections.
- Each cluster node (server) and listener must have a wallet with the user certificate and CA certificates.
- The client only needs CA certificates of the listeners and servers (either in wallet or system’s certificate store) if one-way TLS is configured.
- The client needs a wallet with its user certificate and CA certificates of the listeners and servers if mTLS is configured.
21.4.1.4 Step 4: Create a Wallet in Each Node of the Oracle RAC Cluster
After you have created the cluster wallet, you can copy it to each node of the Oracle Real Applications (Oracle RAC) cluster.
21.4.1.5 Step 5: Define Wallet Locations in the listener.ora and sqlnet.ora Files
To enable the database server and listeners to access the wallets, you must define the wallet locations in the listener.ora and sqlnet.ora files.
21.4.1.6 Step 6: Restart the Database Instances and Listeners
With the wallets in place and the *.ora files edited, you must restart the database server and listener processes so that they pick up the new settings.
LOCAL_LISTENER parameter earlier.
21.4.1.7 Step 7: Test the Cluster Node Configuration
To test the cluster node configuration, you can create a connect descriptor for the node and then try to connect to this node.
21.5 Troubleshooting the Transport Layer Security Configuration
Common errors may occur while you use the Oracle Database Transport Layer Security.
A utility is available through My Oracle Support to review and provide feedback on your TLS client and server configuration. See DBSecChk Utility 2.0.0.5 (Doc ID 3066006.1).
It may be necessary to enable Oracle Net tracing to determine the cause of an error. For information about setting tracing parameters to enable Oracle Net tracing, refer to Tracing Error Information for Oracle Net Services in the Oracle AI Database Net Services Administrator's Guide.
- ORA-28759: Failure to Open File
-
Cause: The system could not open the specified file. Typically, this error occurs because the wallet cannot be found.
- ORA-28786: Decryption of Encrypted Private Key Failure
-
Cause: An incorrect password was used to decrypt an encrypted private key. Frequently, this happens because an auto-login wallet is not being used.
- ORA-28858: SSL Protocol Error
-
Cause: This is a generic error that can occur during TLS handshake negotiation between two processes.
- ORA-28859 SSL Negotiation Failure
-
Cause: An error occurred during the negotiation between two processes as part of the TLS protocol. This error can occur when two sides of the connection do not support a common cipher suite.
- ORA-28862: SSL Connection Failed
-
Cause: This error occurred because the peer closed the connection.
- ORA-28865: SSL Connection Closed
-
Cause: The TLS connection closed because of an error in the underlying transport layer, or because the peer process quit unexpectedly.
- ORA-28868: Peer Certificate Chain Check Failed
-
Cause: When the peer presented the certificate chain, it was checked and that check failed. This failure can be caused by a number of problems, including:
-
One of the certificates in the chain has expired.
-
A certificate authority for one of the certificates in the chain is not recognized as a trust point.
-
The signature in one of the certificates cannot be verified.
-
- ORA-28885: No certificate with the required key usage found.
-
Cause: Your certificate was not created with the appropriate X.509 version 3 key usage extension.
- ORA-29019: The Protocol Version is incorrect
-
Cause: There is a protocol version mismatch between the two peers.
- ORA-29024: Certificate Validation Failure
-
Cause: The certificate sent by the other side could not be validated. This may occur if the certificate has expired, has been revoked, or is invalid for any other reason.
- ORA-29223: Cannot Create Certificate Chain
-
Cause: A certificate chain cannot be created with the existing trust points for the certificate being installed. Typically, this error is returned when the peer does not give the complete chain and you do not have the appropriate trust points to complete it.
Parent topic: Configuring Transport Layer Security Encryption
21.6 Migrating to and Configuring Transport Layer Security Version 1.3
Version 1.3 of Transport Layer Security (TLS) provides stronger security and faster TLS handshakes, when compared to previous versions of TLS.
TLS version 1.3 is supported and enabled by default with 26ai when both the database server and client are version 26ai.
If your environment does not specify the SSL_VERSION
parameter in the configuration files, then TLS version 1.3 is enabled by default. If the
SSL_CIPHER_SUITES parameter is not explicitly configured, TLS 1.3
cipher suites get automatically picked. The product is designed to pick the strongest
TLS version and the strongest available cipher in that version.
The enhancements in Transport Layer Security (TLS) version 1.3 may affect current TLS configurations if one or both of the following parameters are specified.
SSL_VERSION: Remove this parameter from the configuration files to enable all supported TLS versions, or include the string "TLSv1.3" in the value specifiedFor example,SSL_VERSION = (TLSv1.3, TLSv1.2)SSL_CIPHER_SUITES: Remove this parameter from the configuration files to enable all supported TLS cipher suites, or include one or more of the TLS version 1.3 cipher suitesFor example,SSL_CIPHER_SUITES = (TLS_AES_256_GCM_SHA384, TLS_AES_128_GCM_SHA256, TLS_AES_128_CCM_SHA256)