Access the WebLogic Console
As an Essbase administrator, when you are managing your Oracle Essbase stack on Oracle Cloud Infrastructure, you may need access to the WebLogic console to perform some administrative tasks.
The Essbase stack on Oracle Cloud Infrastructure runs from a managed WebLogic server. When you start or stop the Essbase stack, it starts and stops the WebLogic server as well as the Essbase applications.
- Essbase instances are configured by default with no access to the administrative T3 WebLogic port. Oracle highly recommends that all access to the T3 port remain disabled, and that you secure it immediately. If necessary for business purposes, access to the T3 port should only be allowed from a certain fixed set of IPs, using SecIPList or a restricted classless inter-domain routing block (CIDR); for example, xx.xx.0.0/16.
- ALL ports should be closed to the public internet. There should be only two network options:
- VPN - You open ports in your private network.
- Public access - ssh (port 22) through bastion (service instance), 443 through Load Balancer, host ports should not be open to the public internet.
The WebLogic AdminServer runs on port 7002. To access it,
-
Expose the port on the target compute node. To do this, SSH into the target machine as the opc user and run the following commands:
[opc@essbase-1 ~]$ sudo firewall-cmd --add-port=7002/tcp --zone=public # To make this survive restarts of the firewall service [opc@essbase-1 ~]$ sudo firewall-cmd --add-port=7002/tcp --zone=public --permanent [opc@essbase-1 ~]$ sudo systemctl restart firewalld [opc@essbase-1 ~]$ sudo firewall-cmd --list-all public target: default icmp-block-inversion: no interfaces: sources: services: sshdhcpv6-client http https ports: 7002/tcp protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: -
Enable the security list for the subnet to allow limited access to the port from a source network. The quick start creates a virtual cloud network (VCN) named
<prefix>-vcn, and a security list named<prefix>-app-security-list. Add an ingress rule as shown below. Enter an IP address in the Source CIDR field that only your admin users are allowed to access from their client laptop or desktop.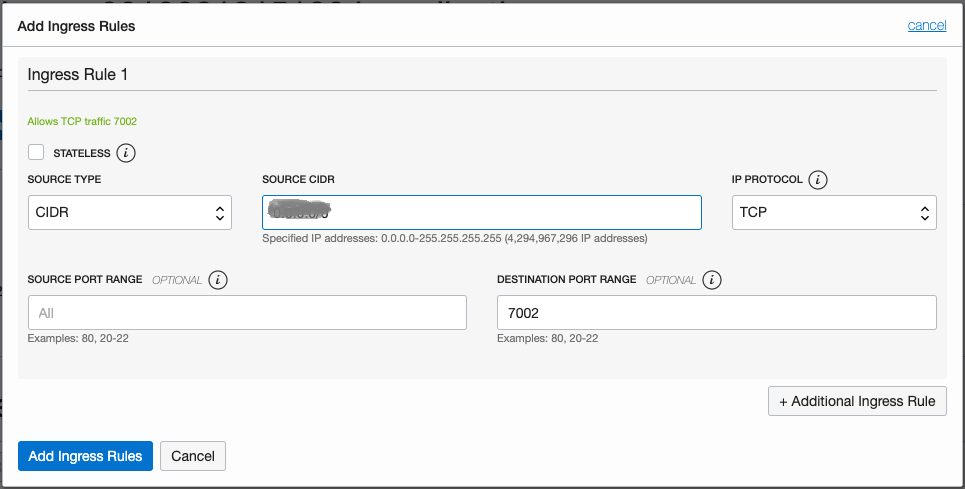
-
Log in to the target machine using the Console URL
https://<Essbase IP address>:7002/console, with the same Essbase administrator login that you used during configuration of the stack.