5 Enabling Secure Communication
By default, the Event Connector Web Service uses insecure communication. You can configure secure communication between the OMS and the Event Connector Web Service, the Event Connector Web Service and the Microsoft SCOM Web Service, or both. The appropriate setup for your environment depends on your network topology.
Configuration Scenario: Enabling SSL/TLS Between the OMS and the Event Connector Web Service

- Navigate to
<ECWS_HOME>/config/. - Create a keystore with a valid server certificate to be presented by the Event Connector Web Service. The keystore must include the following attributes:
- Type:
PKCS12 - Filename:
OemScomKeystore.p12 - Keystore location:
<ECWS_HOME>/config/directory - Certificate alias:
oemscomconnector
Note:
If any of the above attributes are missing or incorrect when secure communication is expected, the web service will fail to start and a message will be generated toecws.log.Although the approach for obtaining this may vary, the following is an example command:
"%JAVA_HOME%\bin\keytool" -importkeystore ^ -srckeystore scom_server.pfx -srcstoretype PKCS12 -srcstorepass "<password>" -srcalias "scomserver" -destkeystore OemScomKeystore.p12 -deststoretype PKCS12 -deststorepass "<password>" -destalias oemscomconnector - Type:
- Import the certificate into the OMS truststore. For information, see Importing the Server Certificate in Oracle Enterprise Manager.
Configuration Scenario: Enabling SSL/TLS Between the Event Connector Web Service and the Microsoft SCOM Web Service
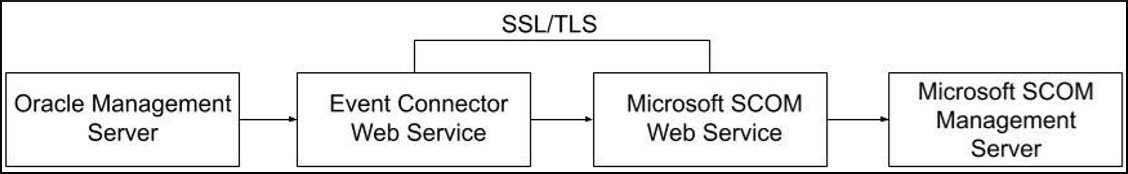
- Navigate to the
config/directory that was populated when first executingWebService.jar. - Create a truststore and import the valid server certificate from the Microsoft SCOM Web Service. The truststore must include the following attributes:
- Type:
PKCS12 - Filename:
OemScomTruststore.p12 - Truststore location:
<ECWS_HOME>/config/directory
Note:
If any of the above attributes are missing or incorrect when secure communication is expected, the web service will fail to start and a message will be generated toecws.log.Although the approach for obtaining this may vary, the following is an example command:
keytool -importcert -alias scomserver -file scom_server.crt -keystore OemScomTruststore.p12 -storetype PKCS12 -storepass <password> - Type: