5 Configuring OCI IAM
5.1 OCI SAML Integration
Overview
SAML (Security Assertion Markup Language) enables applications to authenticate a user using an identity provider. The identity provider authenticates the user and returns the assertion information about the authenticated user and the authentication event to the application. If the user tries to access any other application that uses the same identity provider for user authentication, the user doesn't need to log in a second time, and will be granted access. This is the principle of SSO (Single Sign On).
Adding a SAML Identity Provider in OCI IAM
OCI IAM Console allows adding a SAML 2.0 identity provider (IdP) to an identity domain, so that authenticated users from the IdP can access Oracle Cloud Infrastructure resources and cloud applications.
For more information, see the Managing a SAML Identity Provider section in Oracle Cloud Infrastructure Documentation.Note:
- After following the steps from the above guide, the SAML IdP is configured, but any user created in SAML IdP must be created in OCI IAM to allow a successful login.
- To directly log in to CNC Console Core using SAML IdP, SAML JIT (Just-In-Time) must be configured.
- Role Mappings are also configured as a part of JIT (Just-In-Time).
JIT (Just-In-Time) Configuration in OCI IAM
OCI IAM allows setting up a SAML identity provider (IdP) that uses Just-In-Time (JIT) provisioning for an identity domain.
For information on assigning identity providers to policy, see the Adding a SAML Just-in-Time Identity Provider section in Oracle Cloud Infrastructure Documentation.
Figure 5-1 JIT Provisioning
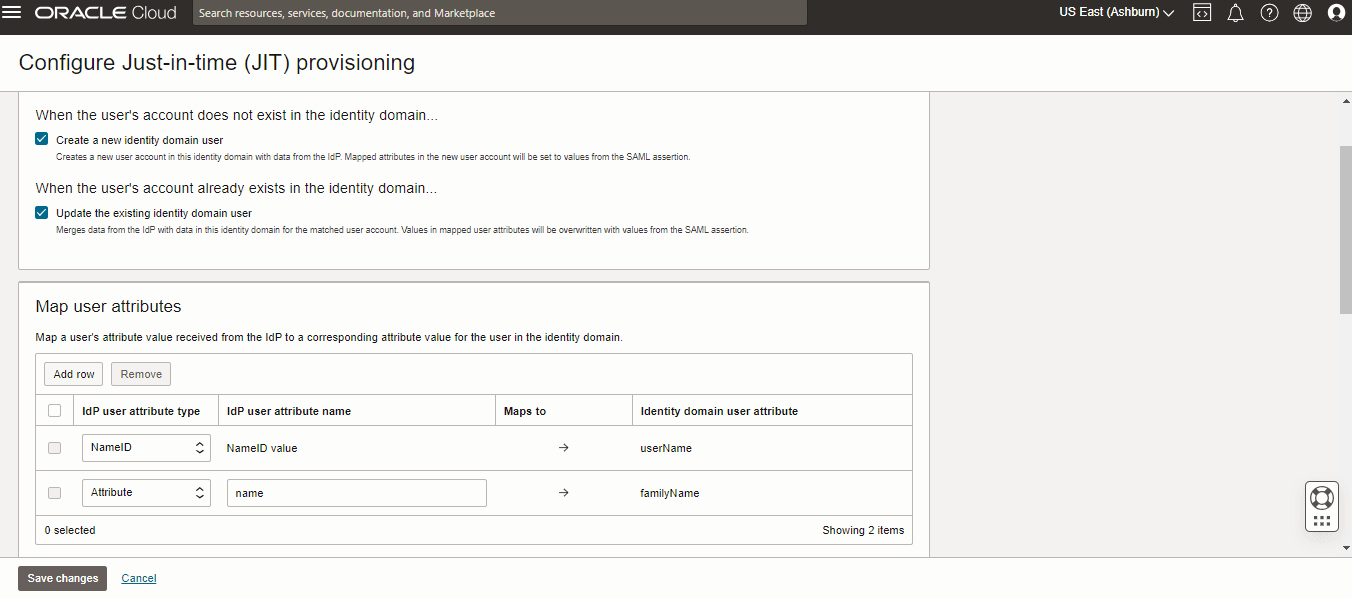
Configuration Example:
The NameID value to the userName is the default mapping, and the name to familyName mapping is configured by the user.
curl --location --request PUT 'http://{host}:{port}/occm-config/v1/occm/logging' \
--header 'oc-cncc-id: Cluster1' \
--header 'oc-cncc-instance-id: Cluster1-occm-instance1' \
--header 'Authorization: Bearer eyJhbG...Yh8bJI_Owc_nb_hA' \
--header 'Content-Type: application/json' \
--data-raw '{
"appLogLevel":"INFO",
"packageLogLevel":[
{
"packageName":"root",
"logLevelForPackage":"ERROR"
}
]
}'<saml:AttributeStatement>
<saml:Attribute FriendlyName="name"
Name="name"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string">SamlUser</saml:AttributeValue>
</saml:Attribute>Note:
The user must ensure that the SAML IdP is populating these attributes in the assertions, otherwise JIT configuring will not work, and the SAML SSO Authentication will fail.
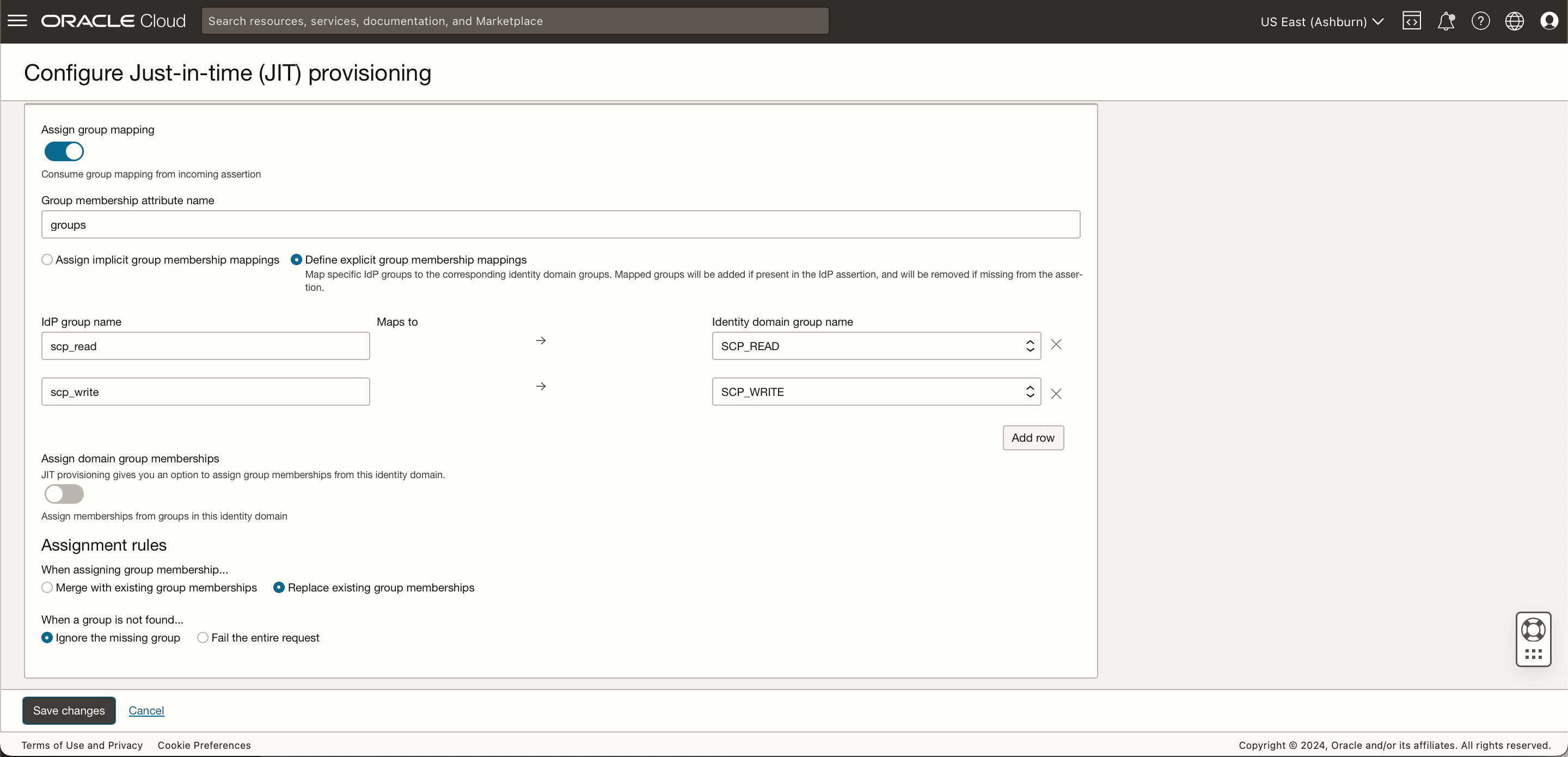
In role mapping, since OCI IAM reads roles as groups, we have assigned 'Group membership attribute name' as groups.
Figure 5-2 Sample Role Mapping
Activating or Deactivating an Identity Provider
For information on activating or deactivating an identity provider, see the Activating or Deactivating an Identity Provider section in Oracle Cloud Infrastructure Documentation.
Assigning Identity Providers to the Policy
For information on assigning identity providers to policy, see the Assigning Identity Providers to the Policy section in Oracle Cloud Infrastructure Documentation.
Testing an Identity Provider
For information on testing an identity provider, see the Testing an Identity Provider section in Oracle Cloud Infrastructure Documentation.
Updating an Identity Provider
For information on updating an identity provider, see the Updating an Identity Provider section in Oracle Cloud Infrastructure Documentation.
5.2 OCI Password Policy
Overview
Password policies let you define a set of criteria for user passwords in an identity domain in IAM. The criteria are enforced when a user creates their password for an identity domain.
These password policies govern the passwords associated with the users created in a particular identity domain, or the passwords of users present in a user group of a particular domain.
Managing Password Policies in OCI IAM
For information on managing password policies in OCI IAM, see the Managing Password Policies section in Oracle Cloud Infrastructure Documentation.
Default Password Policy
If no custom policy is defined, then OCI default password policy (Custom) will be applied.
Note:
If required, OCI recommends the user to review each and every criteria, and modify the existing or create new password policy according to their own requirements.| Policy Criteria | Description | Value | |
| Password length (minimum) | The minimum number of characters that the password must contain. | 12 | |
| Password length (maximum) | The maximum number of characters a password can contain. A password can’t exceed 500 characters. | 40 | |
| Expires after (days) | The number of days until the password expires. Setting this option to 0 means that the password never expires. | 120 | |
| Account lock threshold | The number of consecutive, unsuccessful login attempts into the identity domain after which the user account is locked. If you enter 0, then the user's account is never locked. | 5 | |
| Enable automatic account unlock | Automatically unlocks the locked user accounts after the configured duration has passed. | Enabled | |
| Automatically unlock account after (minutes) | The amount of time (in minutes), after which locked user accounts unlock automatically. You can set a value ranging between 5 minutes and 24 hours. | 30 | |
| Previous passwords remembered | The number of unique new passwords that a user must use before a previously used password can be reused. | 4 | |
| Alphabetic (minimum) | The number of alphabetical characters that the password must contain. | 0 | |
| Numeric (minimum) | The number of numeric characters that the password must contain. | 1 | |
| Special (minimum) | The number of special characters that the password must contain. | 0 | |
| Lowercase (minimum) | The number of lowercase characters that the password must contain. | 1 | |
| Uppercase (minimum) | The number of uppercase characters that the password must contain. | 1 | |
| Unique (minimum) | The number of unique characters that the password must contain. Increasing the number of unique characters in a password can increase password strength by avoiding repetitive sequences that are easily guessed. | 0 | |
| Repeated (maximum) | The number of repeated characters that are allowed for the password. Limiting the use of repeating characters in a password provides extra security by preventing users from creating passwords that are easy to guess, such as the same character repeated several times. | 0 | |
| Starts with an alphanumeric character | Select this checkbox to force the first character of all passwords to be an alphanumeric character. | No | |
| Required characters | The alphanumeric or special characters that the password must contain are separated by commas. | None | |
| Password must not contain | The user's first name | Prevents the user's first name from being used as all or part of the password. | Enabled |
| The user's last name | Prevents the user's last name from being used as all or part of the password. | Enabled | |
| The username | Prevents the username from being used as all or part of the password. | Enabled | |
| Characters not allowed | The alphanumeric or special characters that aren’t allowed in the password are separated by commas. | None | |
| Whitespaces | Prevents whitespace characters from being used as part of a password. A whitespace character is a character that represents horizontal space. For example, for the display name of John Smith, the space between “John” and “Smith” is a whitespace character. | None | |
| Dictionary words | Screens all passwords for words that can be found in a dictionary and prohibits those words. | None | |
5.3 OCI Groups
Overview
Access management for resources is a critical function for any organization. Role-based access control (RBAC) helps you manage who has access to resources, what they can do with those resources, and the areas they can access.
Role-based access control (RBAC)
RBAC restricts network access based on a person's role within an organization, and has become one of the main methods for advanced access control. The roles in RBAC refer to the levels of access that employees have to the network.
Role
A role is a collection of permissions that you can apply to users. Using roles makes it easier to add, remove, and adjust permissions, than assigning permissions to users individually. As your user base increases in scale and complexity, roles become particularly useful.
Note:
Role(s) are referred as Group(s) in OCI IAM.5.3.1 CNC Console Groups
In CNC Console, RBAC is controlled by Oracle Cloud Infrastructure Identity Access Management (OCI IAM).
Groups related to CNC Console applications are defined in OCI IAM.
NF Level Groups
NF level groups are divided further into:
- <NF>_READ
- <NF>_WRITE
<NF> is placeholder. For example, if CNC Console supports POLICY and SCP NFs, then POLICY_READ, POLICY_WRITE, SCP_READ and SCP_WRITE groups would be defined for CNC Console application in OCI IAM.
Users that are assigned this group can read configurations from all Managed Objects (MOs) within an NF.
Allowed Operations: READ
NFs: One particular NF
For example, if user has POLICY_READ, then
- they can read configurations of any MOs within an NF.
- they cannot write, update, or delete any record.
Users that are assigned this group can access one particular NF, and perform CREATE, DELETE, and UPDATE operations.
Note:
READ operation is not allowed with <NF>_WRITE group. To update any MO's configuration, the user must be assigned both <NF>_READ and <NF>_WRITE groups.Allowed Operations: CREATE, UPDATE, and DELETE
NFs: One particular NF
For example, if a user is assigned POLICY_WRITE group, then they can create, update, and delete any MO's configurations within the NF, as long as the user is also assigned the POLICY_READ group.
5.3.2 Managing Groups in OCI IAM
For information on managing groups in OCI IAM, see the Managing Groups section in Oracle Cloud Infrastructure Documentation.
5.3.3 Import and Export of Groups in OCI IAM
Note:
For information on transferring data, see the Transferring Data section in Oracle Cloud Infrastructure Documentation.5.3.3.1 Import Groups
For information on importing groups, see the Importing Groups section in Oracle Cloud Infrastructure Documentation.
Note:
Use the oci_occncc_groups_<version>.csv file
provided with the CNC Console release package for importing Groups.
5.3.3.2 Export Groups
For information on exporting groups, see the Exporting Groups section in Oracle Cloud Infrastructure Documentation.
5.3.4 View Groups
To view groups:
- Log in to OCI Console.
- Open the navigation menu and click Identity & Security.
Under Identity, click Groups. A list of the groups in your tenancy
appears.
Figure 5-3 View Groups
5.3.5 Assigning Groups to User Using CSV
The following prerequisites are required for assigning groups to users using CSV:
- CNC Groups must be created within OCI IAM.
- Users must be present within the OCI IAM.
Perform the following procedure to assign groups to users using CSV:
- Export the existing groups.
- Update the users in User Members column in the
groups.csvfile.Note:
For multiple users use semi-colons (;) to separate the users.For example. Robin; David
- Save the CSV file.
- Import the groups using
groups.csv.
5.4 OCI Users
5.4.1 Managing Users
For information on managing users in OCI deployment, see the Managing Users section in Oracle Cloud Infrastructure Documentation.
5.4.2 Managing User Credentials in OCI IAM
For information on managing user credentials, see the Changing Users Password section in Oracle Cloud Infrastructure Documentation.
5.4.3 Import and Export of User in OCI IAM
This section describes the procedure import and export users in OCI IAM.
Note:
For more details, see the Transferring Data section in Oracle Cloud Infrastructure Documentation.
5.4.3.1 Import Users
For information on importing users, see the Importing Users section in Oracle Cloud Infrastructure Documentation.
5.4.3.2 Export User
For information on exporting users, see the Exporting Users section in Oracle Cloud Infrastructure Documentation.
5.5 OCI Active Directory Integration
Overview
Active Directory (AD) stores information about objects on the network and makes this information easy for administrators and users to find and use. Active Directory uses a structured data store as the basis for a logical and hierarchical organization of directory information.
Prerequisites
- Running Active Directory.
- Groups must be created in Active Directory following the CNC Console group name format, and user's must beassigned to the groups.
Note:
To create CNC Console groups, see OCI Groups.5.5.1 Setting Up a Microsoft Active Directory Bridge
For information on how to install active directory bridge, see the Setting Up a Microsoft Active Directory Bridge section in the Oracle Cloud Infrastructure Documentation.
5.5.2 Setting Up A Microsoft Active Directory Bridge With SSL Enabled
For information on setting up a microsoft active directory bridge with SSL enabled, see the Setting Up a Microsoft Active Directory Bridge section in the Oracle Cloud Infrastructure Documentation.
Note:
You must enable the Use SSL flag while providing the active directory credentials.5.5.3 Importing Users and Groups From Active Directory
- Active Directory Bridge must be configured.
- Active Directory Bridge must be in active state.
Figure 5-5 Directory integration in cncc-iam Domain

Note:
If active directory bridge is not configure or the status is inactive, see the Setting Up a Microsoft Active Directory Bridge section in the Oracle Cloud Infrastructure Documentation.
To import users from active directory, see the Importing Users from Active Directory section in the Oracle Cloud Infrastructure Documentation.
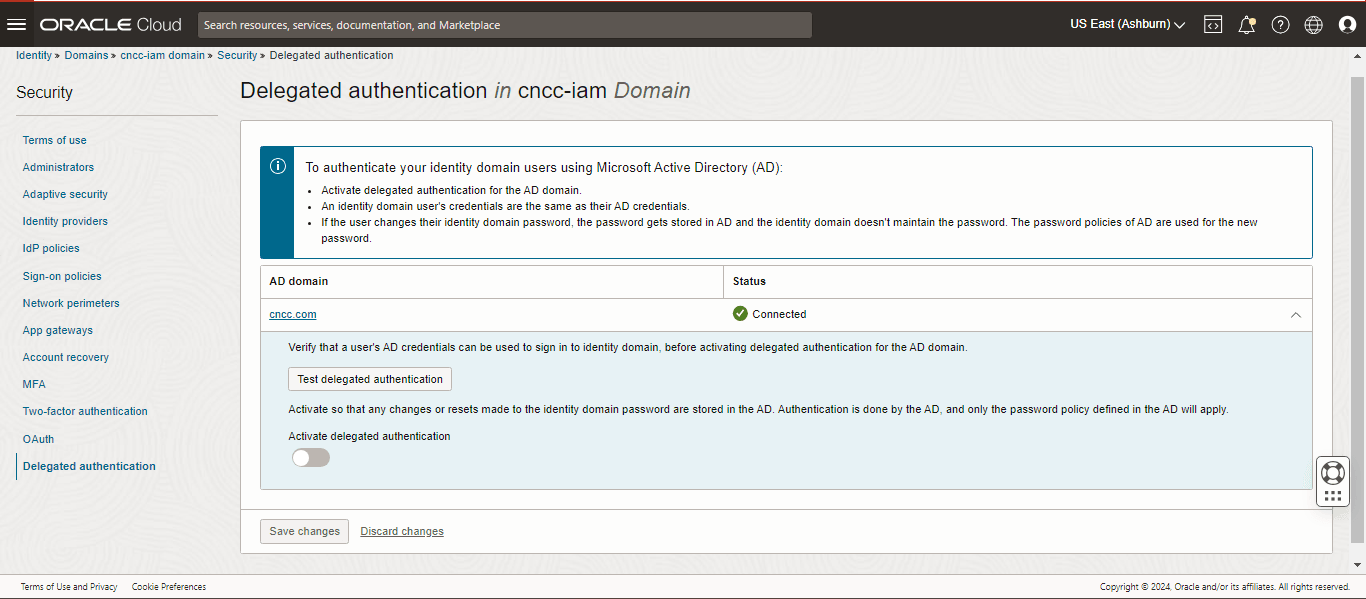
5.5.4 Setting up Delegated Authentication
- Log in To OCI Console.
- Open the navigation menu and click Identity & Security. Under Identity, click Domains.
- Click Security.
- Click Delegated Authentication.
- Click Test Delegated Authentication.
- Provide active directory user credentials.
- Enable Activate Delegate Authentication.
Figure 5-6 Delegated Authentication in CNC Console IAM Domain