2 OCCM Architecture
OCCM is a Cloud Native application consisting of a single microservice. OCCM is packaged and delivered as a CSAR or Helm chart.
Figure 2-1 OCCM Architecture
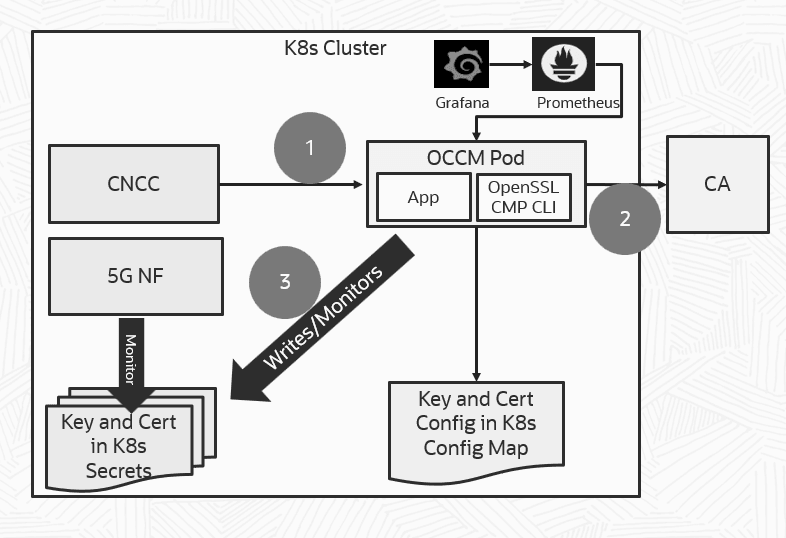
Architecture Description
OCCM is deployed as a single Kubernetes Pod and has a small resource footprint. The OCCM application uses a set of OpenSSL Certificate Management Protocol (CMP) CLI commands based on the provided configuration and the certificate management procedure that needs to be carried out at a point in time. The Output – Key and Certificate – is stored in configuration defined Kubernetes secret.
Operator provides the desired key and certificate configuration through Console. OCCM contacts the CA for certificate signing. After successful Certificate creation, OCCM writes the key and certificate in Kubernetes secrets.
In the diagram above:
- Operator provides the desired Key and Certificate configuration.
- OCCM contacts the CA for certificate signing.
- OCCM writes the key and certificate in Kubernetes Secrets. Starts monitoring of the secret for modification or deletion.
- Dedicated deployment model - OCCM resides in the same Kubernetes namespace as the NF or Components.
- Shared deployment model - OCCM is deployed in a separate Kubernetes namespace and can manage certificates of multiple NFs or components deployed in other Kubernetes namespaces.
Appropriate permissions must be assigned to OCCM using Kubernetes Service Account, Role and Role Binding, based on the selected deployment model.
OCCM provides secret monitoring capabilities, which help the operator to monitor and manage previously created certificates. OCCM identifies and takes necessary action if certificates are modified or deleted manually, without experiencing loss of service.
Certificate monitoring is useful in the following scenarios:
- The certificate or the Kubernetes secret holding the certificate is deleted.
- The certificate is manually updated.
For more information, see "Monitoring Secrets for Manual Update or Delete" in the Oracle Communications Cloud Native Configuration Console User Guide.