4 Configuring Service Communication Proxy using the CNC Console
This chapter provides information about how to configure and modify different services in Service Communication Proxy (SCP) using the Oracle Communications Cloud Native Configuration Console (CNC Console).
The REST API configurations can also be performed using the CNC Console.
4.1 Support for Multicluster Deployment
The CNC Console supports both single and multiple cluster deployments.
In a single cluster deployment, the CNC Console can manage NFs and Oracle Communications Cloud Native Environment (OCCNE) common services deployed in the local Kubernetes clusters.
In a multicluster deployment, the CNC Console can manage NFs and OCCNE common services deployed in the remote Kubernetes clusters. For more information about single and multiple cluster deployments, see Oracle Communications Cloud Native Configuration Console Installation, Upgrade, and Fault Recovery Guide .
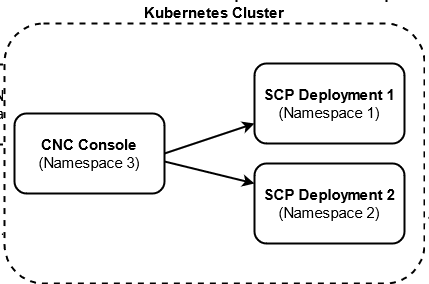
With the support of multicluster deployment, a single instance of the CNC Console can configure two or multiple instances of SCP deployments if both CNC Console and SCP instances are deployed in the same Kubernetes cluster with different namespaces.
The following image represents a Kubernetes cluster with one instance of CNC Console and two instances of SCP. The single instance of the CNC Console is configuring two instances of SCP with different namespaces.
Figure 4-1 Support for Multicluster Deployment
4.2 CNC Console Interface
This section provides an overview of the CNC Console to configure SCP features.
C:\Windows\System32\drivers\etc location.
-
In the Windows system, open the hosts file in the notepad as an Administrator and append the following set of lines at the end:
<CNCC Node IP> cncc-iam-ingress-gateway.cncc.svc.cluster.local <CNCC Node IP> cncc-core-ingress-gateway.cncc.svc.cluster.localExample:10.75.212.88 cncc-iam-ingress-gateway.cncc.svc.cluster.local 10.75.212.88 cncc-core-ingress-gateway.cncc.svc.cluster.localNote:
The IP Address in the above lines may change when deployment cluster changes. - Save and close the hosts file.
Before logging in to the CNC Console, create a CNC user and password. Log in to the CNC Console using the same credentials. For information about creating a CNC Console user and password, see Oracle Communications Cloud Native Configuration Console Installation, Upgrade, and Fault Recovery Guide .
Logging in to the CNC Console and Selecting an SCP Instance
Perform the following procedure to log in to the CNC Console and select the required SCP instance to configure SCP features.
- Open any web browser.
- Enter the URL:
http://<host name>:<port number>.Where,
<host name>is cncc-iam-ingress-ip and<port number>is cncc-iam-ingressport. - Enter the login credentials.
- Click Log
in.
The CNC Console Home page appears.
Figure 4-2 CNC Console Welcome Screen
- In the upper pane, from the Please Select
Instance drop-down list, select the required SCP
instance.
The SCP tab appears in the left navigation pane.
Figure 4-3 Select NF Instance
 The Please Select Instance drop-down list provides NF instances to configure corresponding NF features. You must select an appropriate SCP instance to configure SCP features. Alternatively, you can click one of the following interface elements on the Welcome screen:
The Please Select Instance drop-down list provides NF instances to configure corresponding NF features. You must select an appropriate SCP instance to configure SCP features. Alternatively, you can click one of the following interface elements on the Welcome screen:- About: This element provides the CNC Console product name and version.
- Sign Out: This element exits the CNC Console.
Note:
In all the Query Parameters fields, do not enter keys or values in single or double quotes. For example, the "nfType"="UDM" query parameter must be entered as nfType=UDM.4.2.1 Configuring SCP Features
Note:
You must log in to the CNC Console while performing the procedures described in the subsequent subsections.- Configuring Enhanced NF Status Processing
- Configuring Global Egress Rate Limiting
- Configuring Support for 5G SBI Roaming
- Configuring Mediation
- Configuring Model D Indirect 5G SBI Communication
- Configuring SCP User Agent Info
- Configuring Message Feed
- Configuring Load Control Information (LCI)
- Configuring Host Preference for Egress Message Requests
- Configuring CCA Header Validation
- Configuring Location Header Update for Host Mismatch
- Configuring Support for OAuth2.0
- Configuring SCP Health Check API
- NRF Configuration using DNS SRV Resolution
- Configuring Overload Control Based on the Overload Control Information Header
- Configuring Enhanced NFProfile Processing
- Configuring Error Response Enhancement
- Enhanced Notifications Handling
- Ingress Rate Limiting
- Egress Rate Limiting
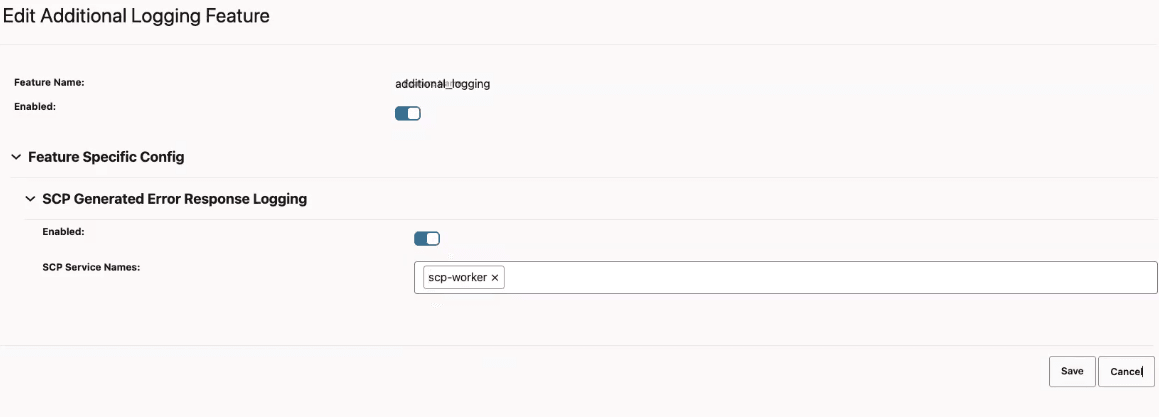
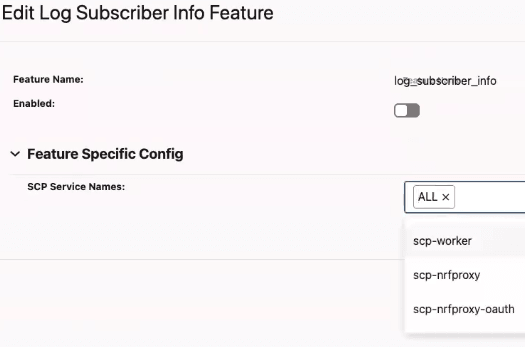
4.2.1.1 Configuring the Log Enhancement Feature
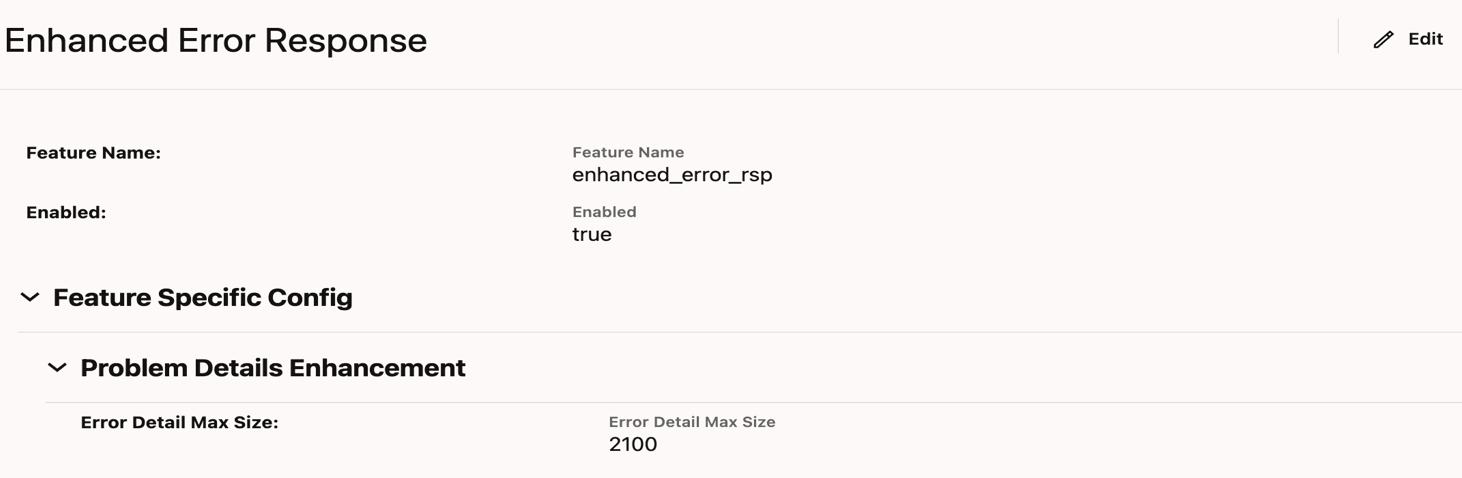
4.2.1.2 Configuring Error Response Enhancement
4.2.1.3 Configuring Enhanced NF Status Processing
Perform the following procedure to enable the support for creating or retaining SCP routing rules for NF Profiles with NF Status as SUSPENDED.
Note:
The Enhanced NF Status Processing feature is applicable only when nnrf-nfm (NRF Management) service is used as an audit service for SCP.- In the left navigation pane, click the SCP tab, and then click the SCP Features tab.
- From the SCP Features list, click Enhanced Nf Status Processing.
- In the Enhanced NF Status section, click
Edit.
Figure 4-7 Editing Enhanced Nf Status Processing
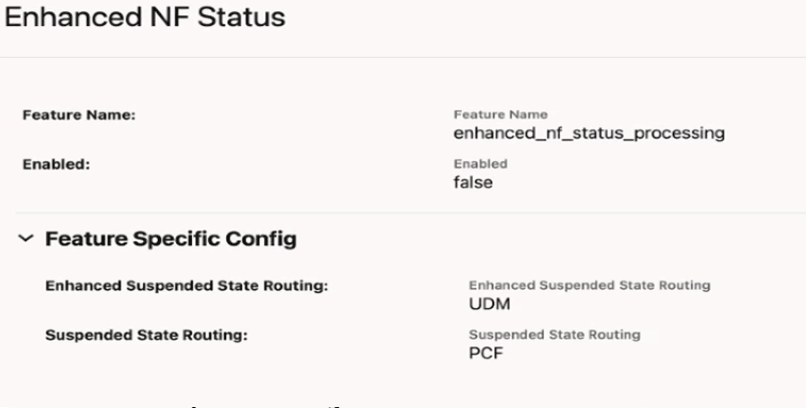
- Set Enabled to true.
By default, this option is set to false.
- In the Feature Specific Config section, configure the
following fields as required:
- Enhanced Suspended State Routing: Enter the list of valid NF types for Mode 3 routing.
- Suspended State Routing: Enter the list of valid NF types for Mode 2 routing.
- Click Save.
4.2.1.4 Configuring Global Egress Rate Limiting
- In the left navigation pane, click the Global Egress Rate Limiting tab.
- In the Global Egress Rate Limit section,
click Edit.
The Edit Global Egress Rate Limit screen appears.
Figure 4-8 Enabling the Global Egress Rate Limiting
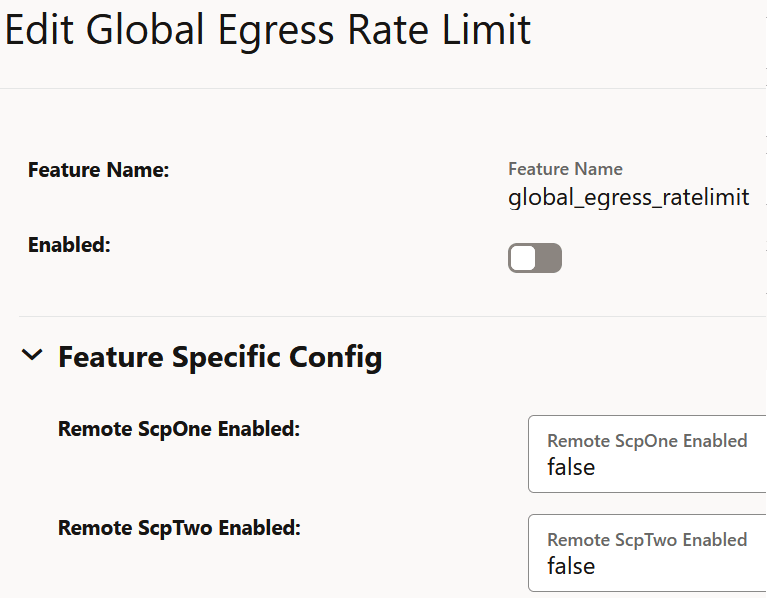
- Set Enabled to true.
By default, this option is set to false.
- In the Feature Specific Config section,
configure the following fields:
- Remote ScpOne Enabled: Set this field to true if
you want to enable egress rate aggregation with the SCP instance as defined in the
coherence.federation.remoteScpOneparameter of theocscp-custom-values.yamlfile. By default, this value is set to false. - Remote ScpTwo Enabled: Set this field to true if
you want to enable egress rate aggregation with the SCP instance as defined in the
coherence.federation.remoteScpTwoparameter of theocscp-custom-values.yamlfile. By default, this value is set to false.
- Remote ScpOne Enabled: Set this field to true if
you want to enable egress rate aggregation with the SCP instance as defined in the
- Click Save.
4.2.1.5 Configuring Support for 5G SBI Roaming
Note:
Ensure that one local and one remote PLMNs are configured before enabling this feature. To configure a remote PLMN, see Configuring SEPP Inter PLMN Routing. A local PLMN is configured at the time of SCP deployment or by editing the CUSTOM_ORACLE_SCP NF type as described in Configuring NF Rule Profile.- In the left navigation pane, click the Interplmn Routing tab.
- In the Interplmn Routing section,
click Edit.
The Edit Interplmn Routing screen appears.
Figure 4-9 Inter PLMN Routing
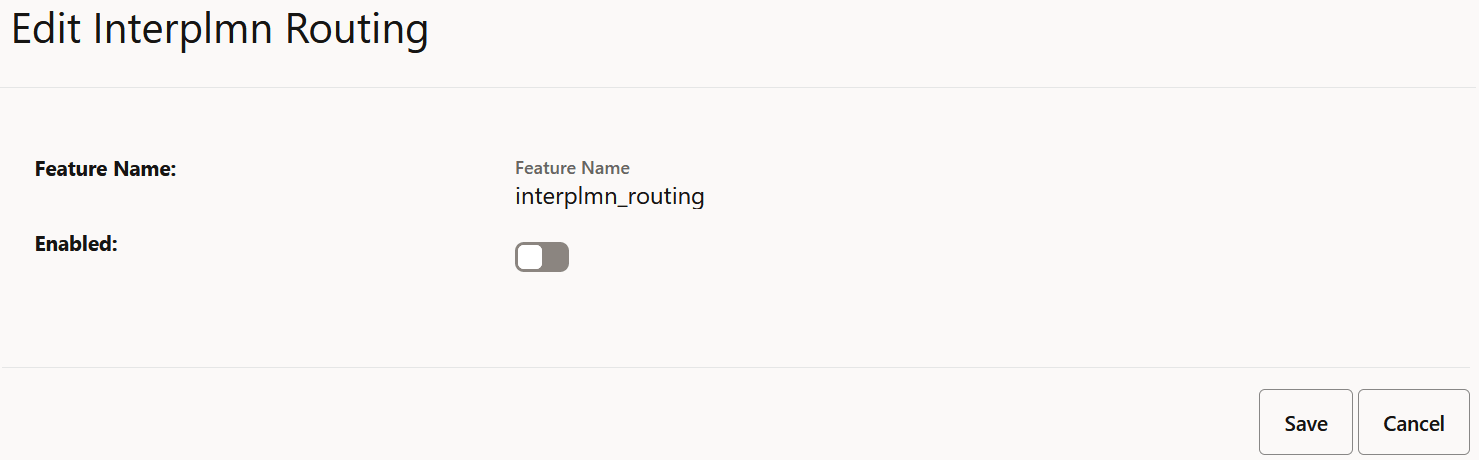
- Set Enabled to true.
By default, this option is set to false.
- Click Save.
4.2.1.6 Configuring Mediation
- From the left navigation pane, click the SCP tab, and then click the SCP Features tab.
- To enable mediation, from the SCP Features list, click the Mediation tab.
- In the Mediation section, click
Edit.
The Edit Mediation screen appears.
Figure 4-10 Enable Mediation
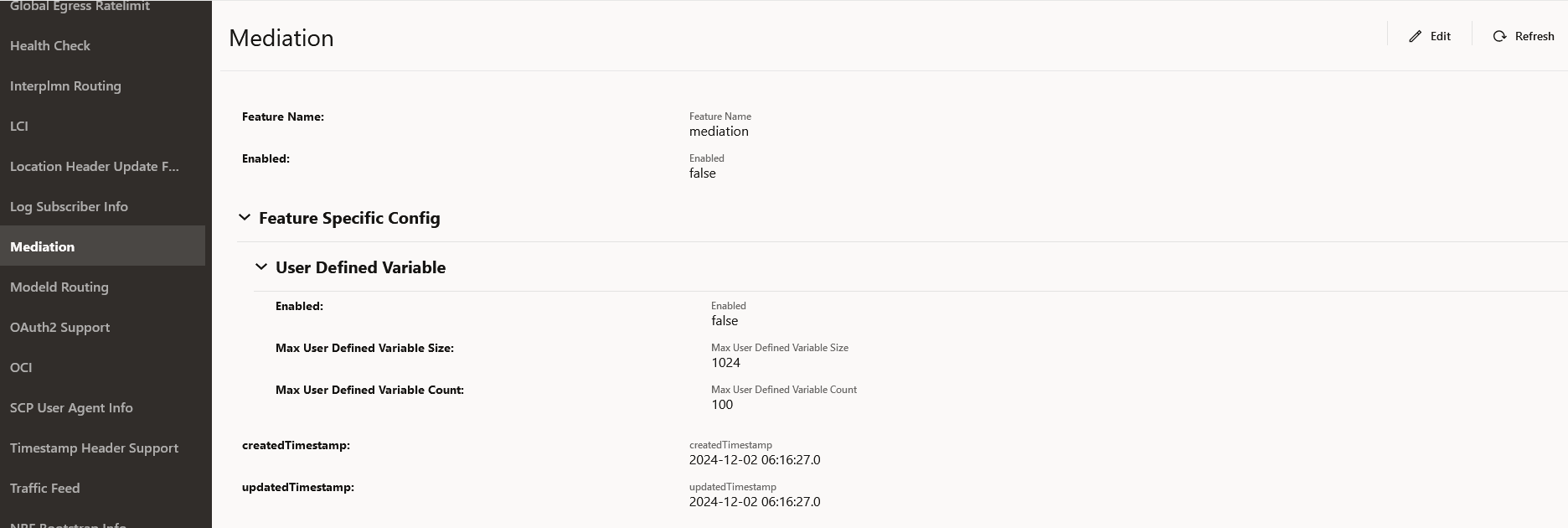
- Set Enabled to true.
By default, this option is set to false.
- In the Feature Specific Config section, configure the following fields:
- Set the Enabled true for enabling the User
Defined Variable feature.
Note:
If the User Defined Variable feature is enabled and any mediation rules are in the Applied state, the enabled field cannot be set back to false until all Applied rules are returned to DRAFT state. - Set the maxUserDefinedVariableSize field to
define the overall max size of all user defined variables included
in the request or response body for mediation.
- Default Value: 1024
- Range: 512 - 4096
- Set the maxUserDefinedVariableCount field to
define the total number of user defined variables that can be
configured for usage at User Defined Variables API.
- Default Value: 100
- Range: 1-250
Note:
If userDefinedVariables are added through the User Defined Variables API, the maxUserDefinedVariableCount cannot be set to a value lower than the number of userDefinedVariables currently stored in the database.
- Set the Enabled true for enabling the User
Defined Variable feature.
- Click Save.
4.2.1.7 Configuring Model D Indirect 5G SBI Communication feature
Perform the following to configure Model D indirect 5G SBI communication feature.
- In the left navigation pane, click the Modeld Routing tab.
- In the Modeld Routing section, click
Edit.
Figure 4-11 Enabling ModelD Routing
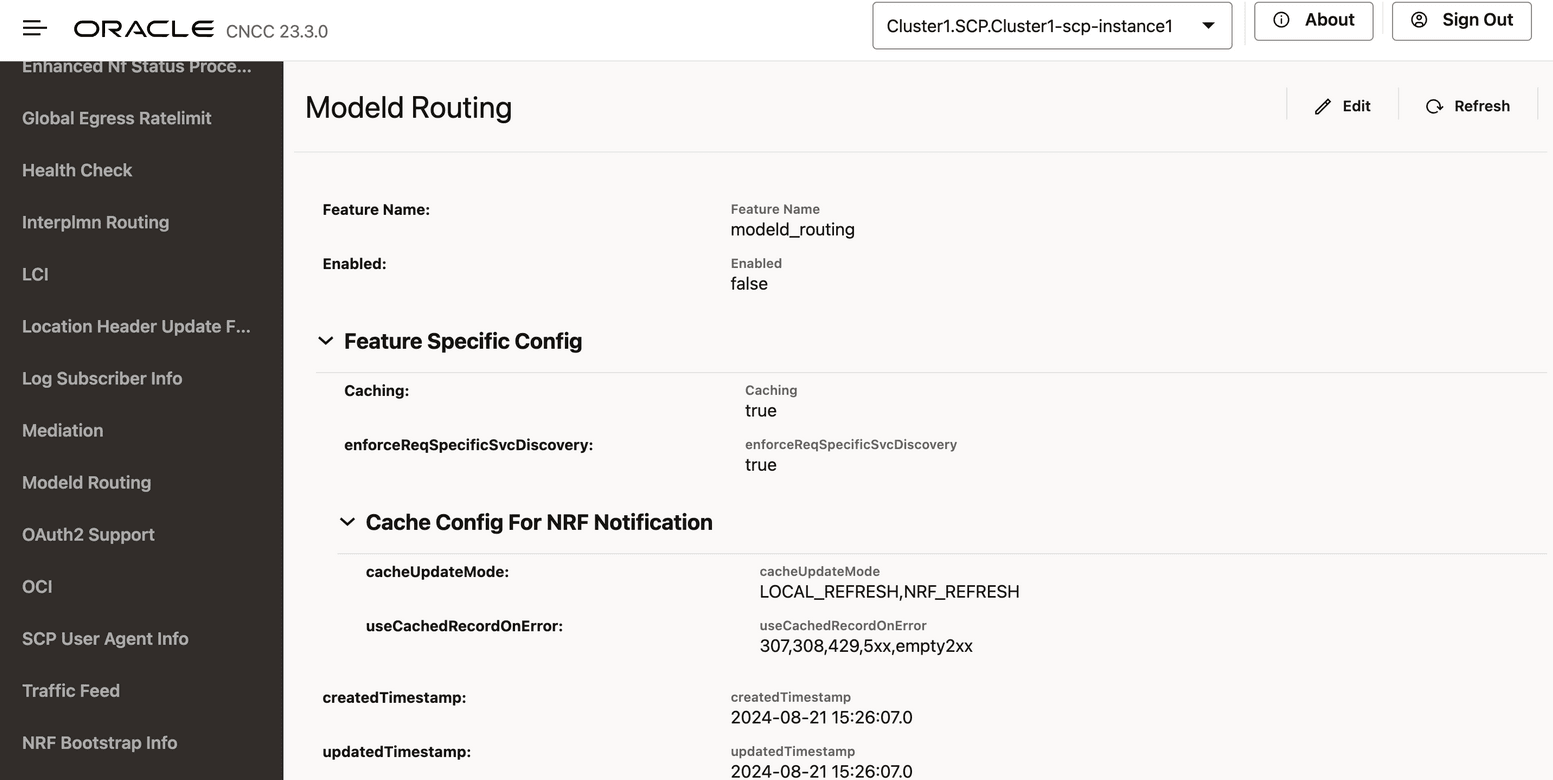
The Edit Modeld Routing screen appears.
- Set Enabled to true.
By default, this option is set to false.
- Set Caching to true or false to enable or disable caching to store discovery responses. By default, this option is set to true.
- Set enforceReqSpecificSvcDiscovery to true or false to to enable or disable NF Service specific Discovery Requests when possible. By default, this option is set to true.
- In the Cache Config For NRF Notification
section, configure the cacheUpdateMode and
useCachedRecordOnError fields
accordingly:
cacheCfgForNrfNotification: Configuration for model-based D cache updates using NRF information.
It includes two fields: cacheUpdateMode and useCachedRecordOnError.- cacheUpdateMode field is a list with
three possible values:
- NONE: No cache update will occur, and the notification will be ignored. Setting the value to "NONE" disables this feature.
- LOCAL_REFRESH: The cache is updated locally if the NF-profile attribute being modified belongs to the local cache update category. If cacheUpdateMode is set to LOCAL_REFRESH only and the modified attribute requires an NRF discovery update, the notification is ignored.
- NRF_REFRESH: The cache is refreshed through a new discovery request to NRF if the NF-profile attribute being modified requires an NRF discovery update. If cacheUpdateMode is set to NRF_REFRESH only and the modified attribute requires a local update, the notification is ignored.
- useCachedRecordOnError field
indicates that SCP uses the existing invalid cached response for the
defined error codes if it receives an error response from NRF, if the
request times out, or if it receives a 2xx response with no profiles.
- Allowed values: NONE, 5xx, empty2xx, and any
valid reroutable error codes defined in the Routing Options
section. These include:
301, 302, 303, 304, 307, 308, 400, 401, 403, 404, 405, 406, 407, 408, 409, 410, 411, 412, 413, 414, 415, 416, 417, 421, 422, 425, 426, 428, 429, 431, 451, 500, 501, 502, 503, 504, 505, 506, 507, 508, 510, 511. - Default values:
"307", "308", "429", "5xx", "empty2xx". - NONE: This value indicates that no error codes are configured. No other error codes can be used when "NONE" is set.
- 5xx: Indicates all supported error codes starting with 5.
- empty2xx: This custom string is defined to handle cases where the NRF discovery response returns a 200 OK status with an empty list of profiles. If this value is configured, SCP will use the old invalid cached response.
- Allowed values: NONE, 5xx, empty2xx, and any
valid reroutable error codes defined in the Routing Options
section. These include:
- cacheUpdateMode field is a list with
three possible values:
- Click Save.
4.2.1.8 Configuring SCP User Agent Info
Perform the following to configure SCP User Agent Info.
- In the left navigation pane, click the SCP User Agent Info tab.
- In the SCP User Agent Info section, click
Edit.
The SCP User Agent Info screen appears.
Figure 4-12 SCP User Agent Info
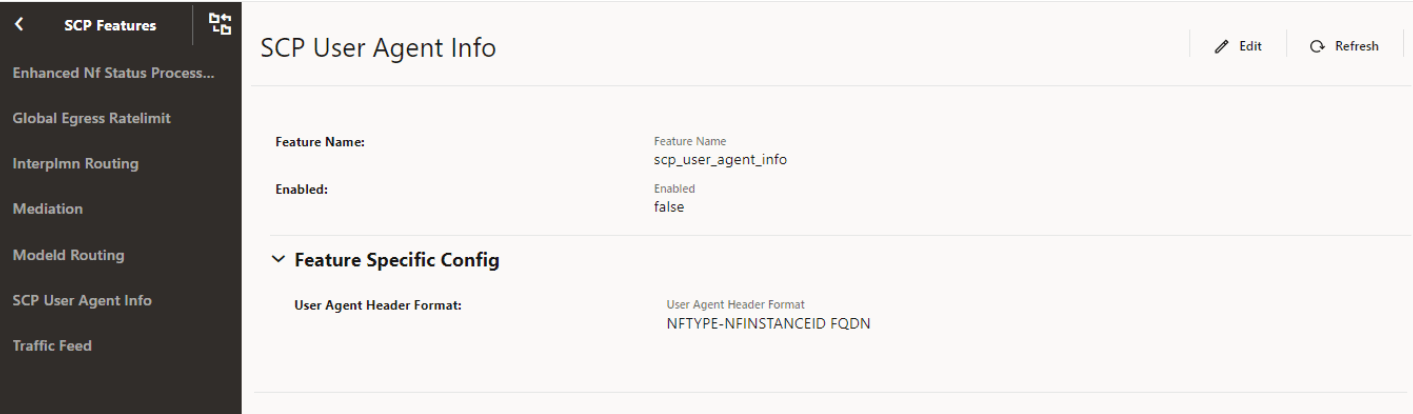
- Set Enabled to true.
By default, this option is set to false.
- Expand the Feature Specific Config option, in the
User Agent Header Format field, select the required
format to set the "User-Agent" header format.
For more information about the "User-Agent" header formats, see "Configuring SCP Features" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- Click Save.
4.2.1.9 Configuring Message Feed
Perform the following to configure message feed.
- In the left navigation pane, click the Traffic Feed tab.
- In the Traffic Feed section, click
Edit.
The Traffic Feed screen appears.
Figure 4-13 Message Feed
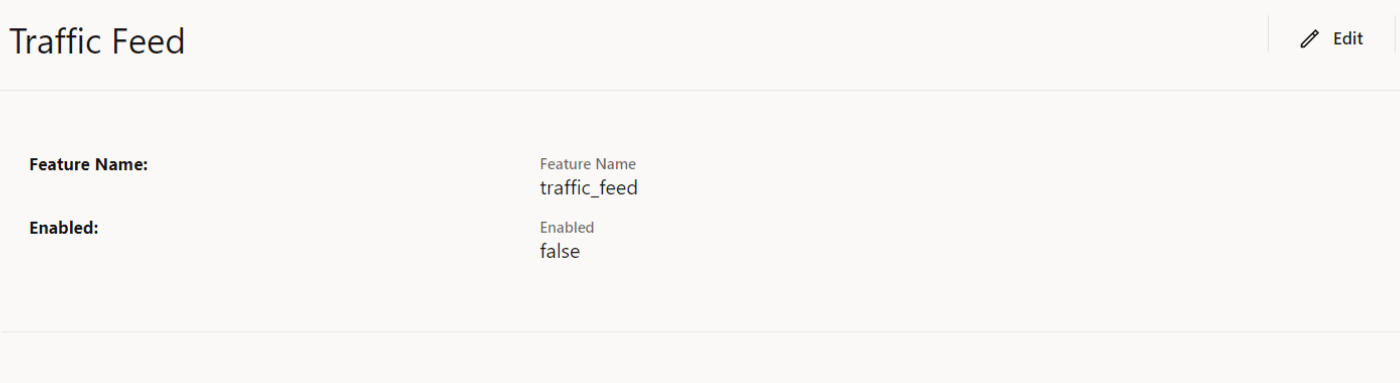
- Set Enabled to true.
By default, this option is set to false.
- Click Save.
4.2.1.10 Configuring Load Control Information (LCI)
Perform the following procedure to enable configuring load control information (LCI).
- In the left navigation pane, click the LCI tab.
- In the LCI section, click
Edit.
Figure 4-14 Editing LCI
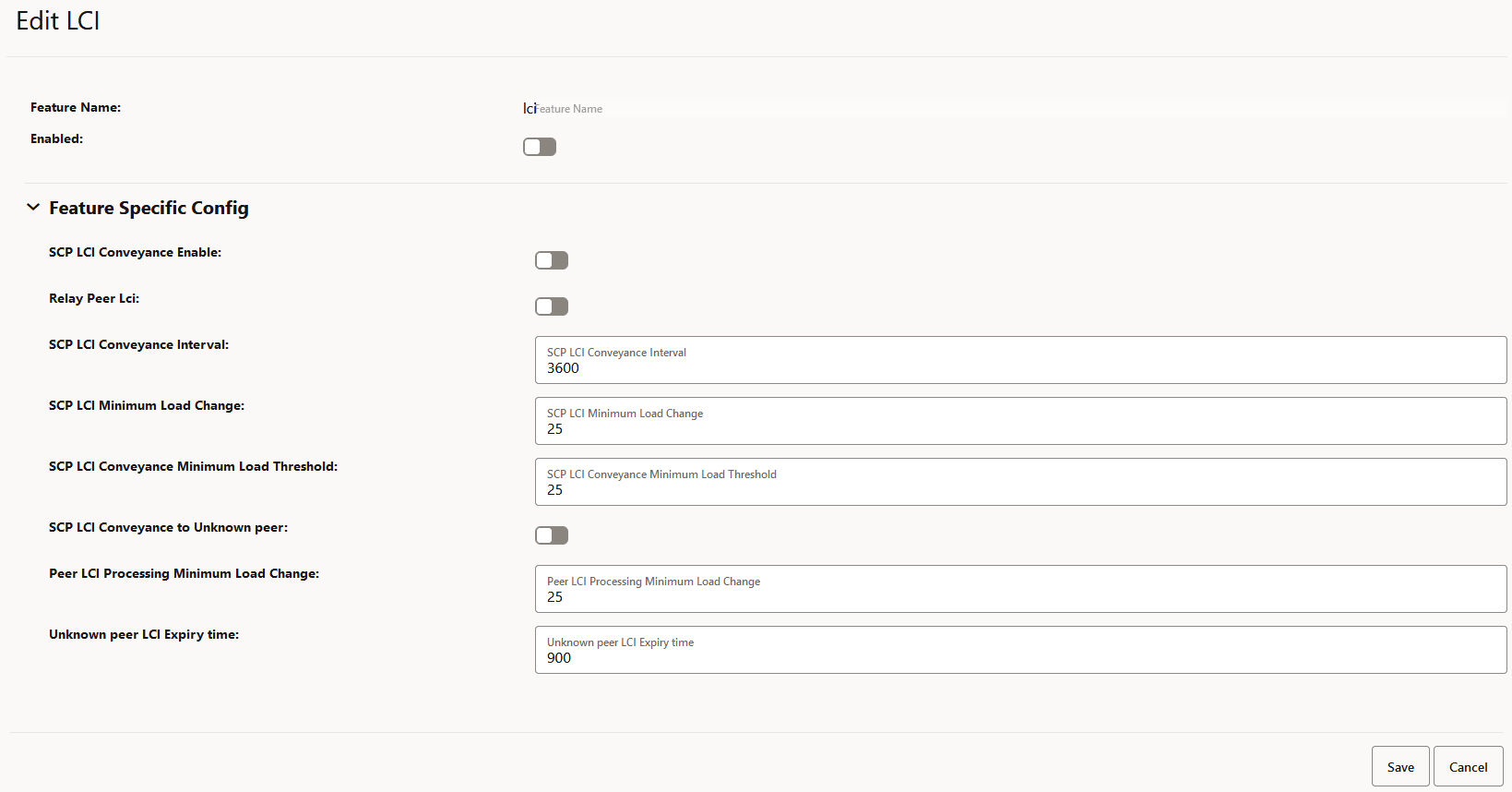
- Set Enabled to true.
By default, this option is set to false.
- In the Feature Specific Config section, complete the
following configurations:
Note:
All the parameters are mandatory to configure the LCI feature.- SCP LCI Conveyance Enable: Set to true to enable SCP to add its LCI in request and response.
- Relay Peer Lci: Set to true to allow SCP to forward the received LCI header from producer NF.
- SCP LCI Conveyance Interval: Enter a value from 100 milliseconds to 3600000 milliseconds to report the SCP LCI update interval.
- SCP LCI Minimum Load Change: Enter a value from 0 to 25 to report the minimum delta value when reporting LCI based on load change.
- SCP LCI Conveyance Minimum Load
Threshold: Enter a value from 0 to 60 to set a minimum load
change threshold to trigger the generation of an LCI header and its
reporting to peers if allowed.
Note:
If the SCP load value is less than the configured SCP LCI Conveyance Minimum Load Threshold value, SCP sends its load value as 0%. - SCP LCI Conveyance to Unknown peer: Set
to true to allow SCP to send its LCI to an unknown peer NF, a peer NF that
is not registered with SCP.
Note:
- SCP sends its LCI in all the messages that go to peer NFs that are not registered with SCP.
- If the SCP load value is less than the configured SCP LCI Conveyance Minimum Load Threshold value, SCP sends its load value as 0%.
- Peer LCI Processing Minimum Load Change: Enter a value from 0 to 25 to define a minimum load change threshold in peer NF's load as indicated in LCI, which can trigger a re-evaluation of routing rules.
- Unknown peer LCI Expiry time: Enter a value between 30 seconds to 900 second to set the minimum number of seconds required to remove an unknown peer's LCI from cache.
- Click Save.
4.2.1.11 Configuring Host Preference for Egress Message Requests
Perform the following procedure to configure host preference for egress message requests.
- In the left navigation pane, click the Egress Host Preference tab.
- In the Egress Host Preference section, click
Edit.
Figure 4-15 Editing Egress Host Preference
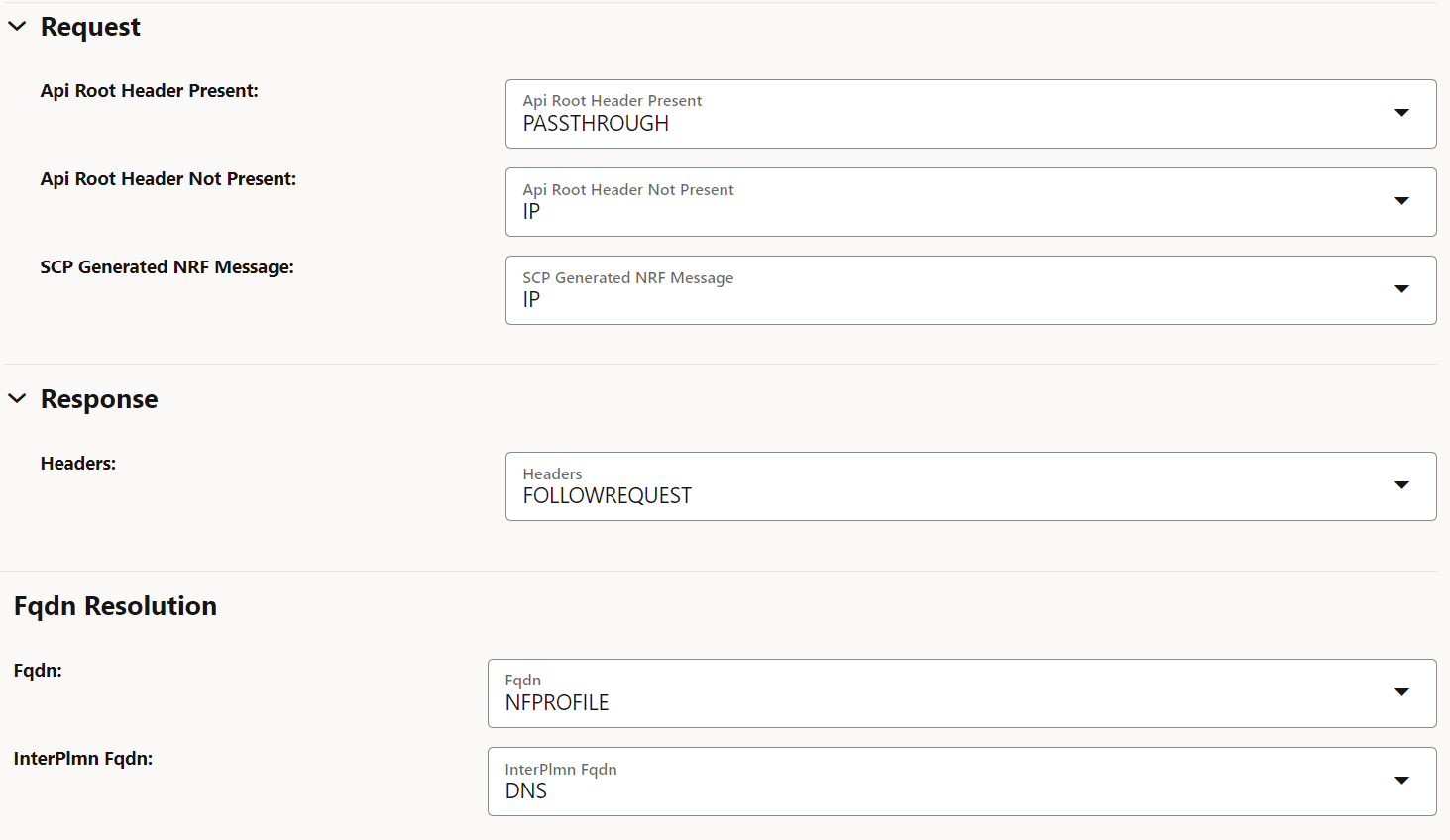
- Set Enabled to true.
By default, this option is set to false.
- In the Feature Specific Config section, to configure the host
preference, set the following fields as described in the following table:
Table 4-1 Host Preference
Field Name Description Api Root Header Present This parameter indicates the host preference (":authority" header) for egress message requests if the 3gpp-Sbi-Target-apiRoot header is present in the ingress message request. You can set this field to PASSTHROUGH to use the same type of host in egress message requests as received through ingress message requests.
Default value: PASSTHROUGH
Range: IP, FQDN, or PASSTHROUGH
Api Root Header Not Present This parameter indicates the host preference (":authority" header) for egress message requests if the 3gpp-Sbi-Target-apiRoot header is absent in ingress message requests. Default value: IP
Range: IP or FQDN
SCP Generated NRF Message This parameter indicates the host preference (":authority" header) for SCP generated NRF messages. Default value: IP
Range: IP or FQDN
Fqdn This parameter indicates the resolution preference of egress message requests host FQDN if present. Default value: NFPROFILE
Range: DNS or NFPROFILE
InterPlmn Fqdn This parameter indicates the resolution preference of egress message requests inter-plmn FQDN if present. Default value: DNS
Range: DNS or NFPROFILE
- Click Save.
4.2.1.12 Configuring CCA Header Validation
Perform the following option to configure CCA Header validation.
- In the left navigation pane, click the CCA Header Validation tab.
- In the CCA Header Validation section, click
Edit.
Figure 4-16 Edit CCA Header Validation
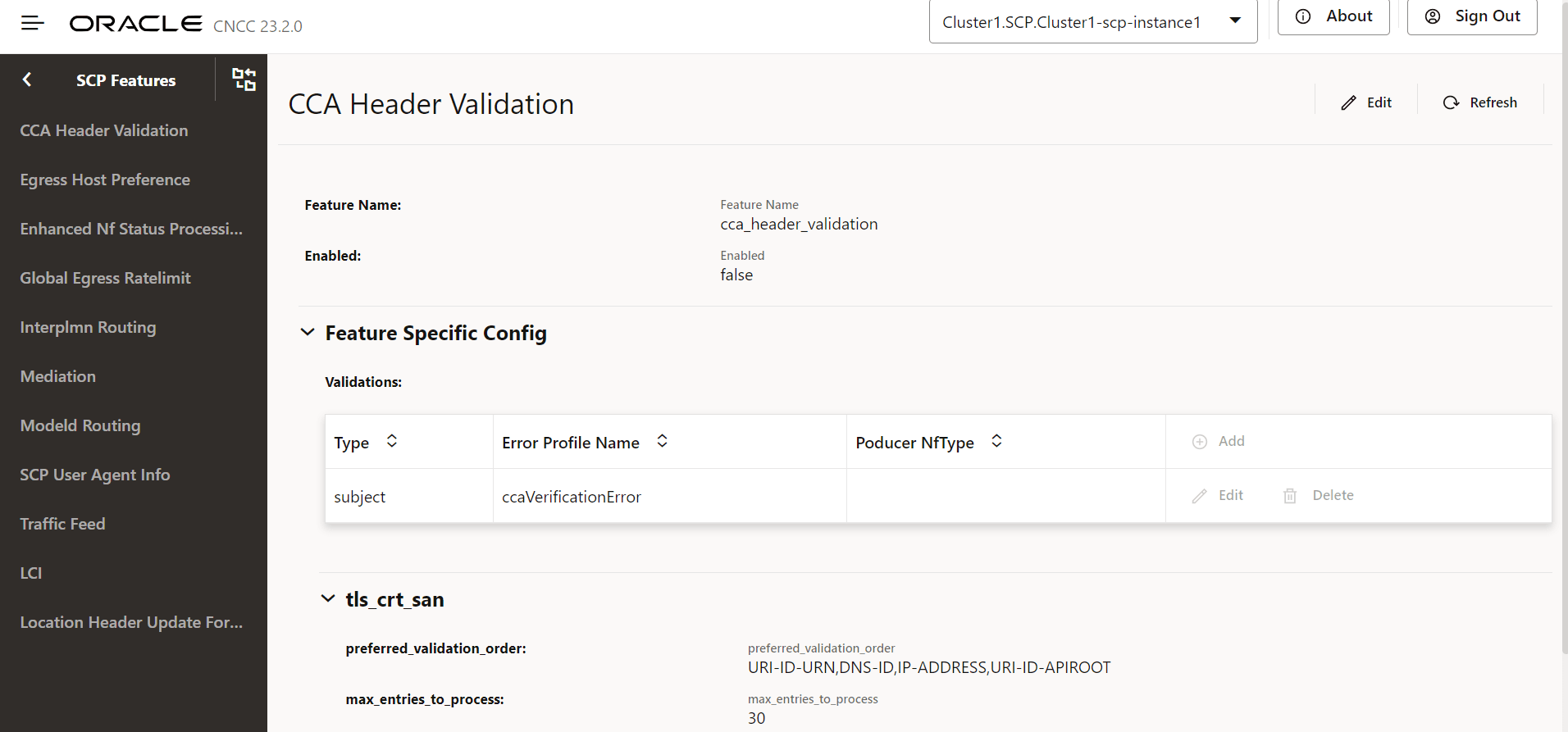
- Set Enabled to true.
By default, this option is set to false.
Note:
SCP supports the 3gpp-Sbi-Client-Credentials header with x5c - X.509 URL, not x5u - X.509 URL. - In the Feature Specific Config section, to configure the
validations, set the following fields as described in the following table:
Table 4-2 Validations
Field Name Description Type Type of validation: - headerPresence: SCP checks the presence of
the 3gpp-Sbi-Client-Credentials header in the ingress
request.
- Validation will pass if the header is present.
- Validation will fail if the header is not present.
- subject: SCP checks the NF instance ID from
the "sub" parameter in the 3gpp-Sbi-Client-Credentials
header with the NF instance ID from the list of SANs in
the client's TLS certificate. SANs directly have the NF
Instance Id or the client's other identity, like the
FQDN or IP address, which will be used to get the NF
Instance Id. If the 3gpp-Sbi-Client-Credentials header
is not present, then this validation will not be
performed.
- Validation will pass if the NF instance ID from the "sub" parameter matches the NF instance ID from the SAN.
- Validation will fail if the NF instance ID from the "sub" parameter doesn't match the NF instance ID from the SAN.
Error Profile Name The error profile name is used to generate an error response if the corresponding validation fails. Error profiles can be configured using the REST API: /ocscp/scpc-configuration/{version}/errorProfileConfig.Product NF Type Default Value: Null preferred_validation_order An order format-wise from which the SCP picks SAN from the client's TLS certificate for verification of the "subject" type of validation. Note: Applicable only when validation type "subject" is selected.
max_entries_to_process Maximum number of SANs from the client's TLS certificate that SCP picks for validation. Note: Applicable only when validation type "subject" is selected.
- headerPresence: SCP checks the presence of
the 3gpp-Sbi-Client-Credentials header in the ingress
request.
- Click Add to add validations:
Figure 4-17 Add Validations
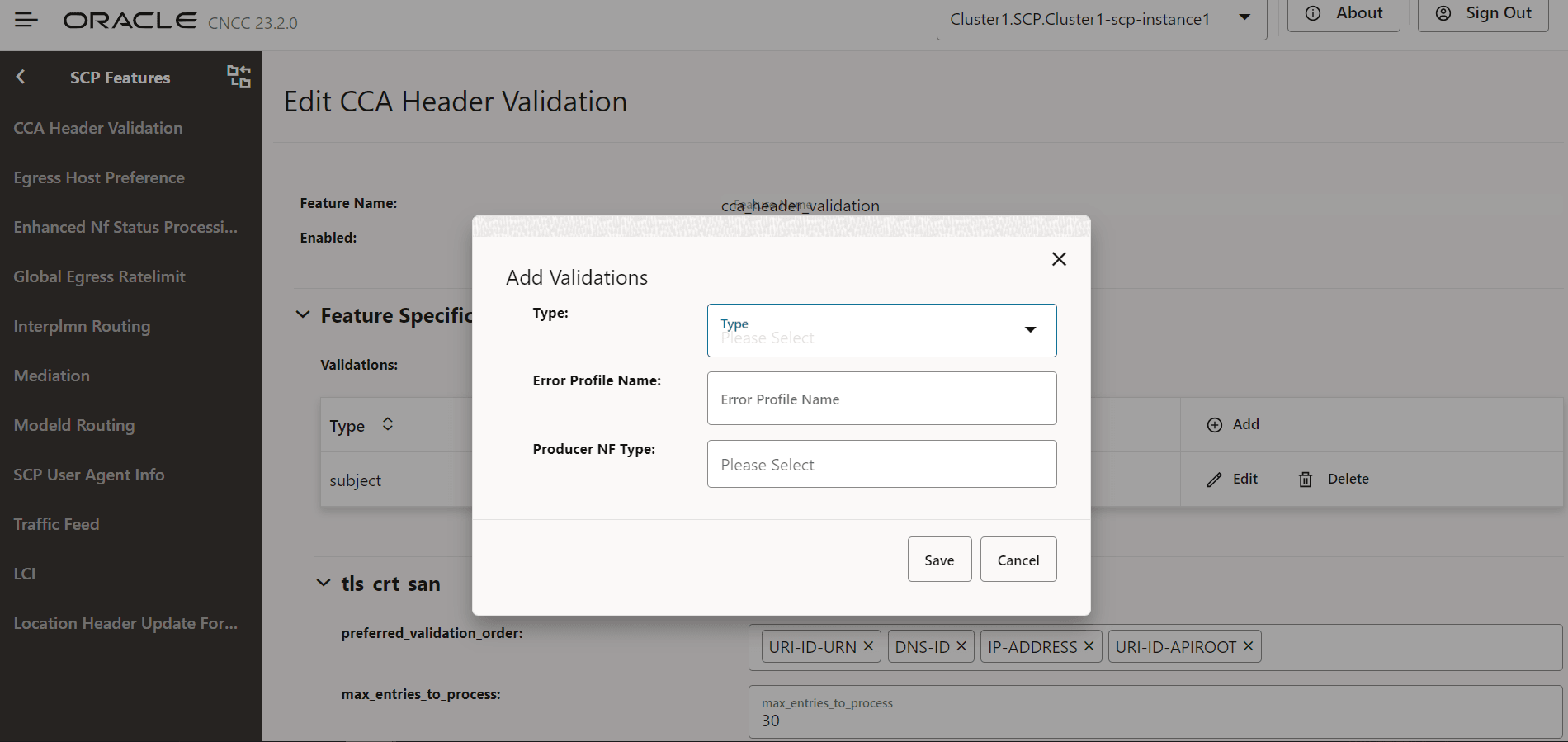
- Click Save.
4.2.1.13 Configuring Location Header Update for Host Mismatch
Perform the following the procedure to configure location header update for host mismatch.
- In the left navigation pane, click the Location Header Update For Host Mismatch tab.
- In the Location Header Update For Host Mismatch
section, click Edit.
Figure 4-18 Edit Location Header Update For Host Mismatch
- Set Enabled to true.
By default, this option is set to false.
- Click Save.
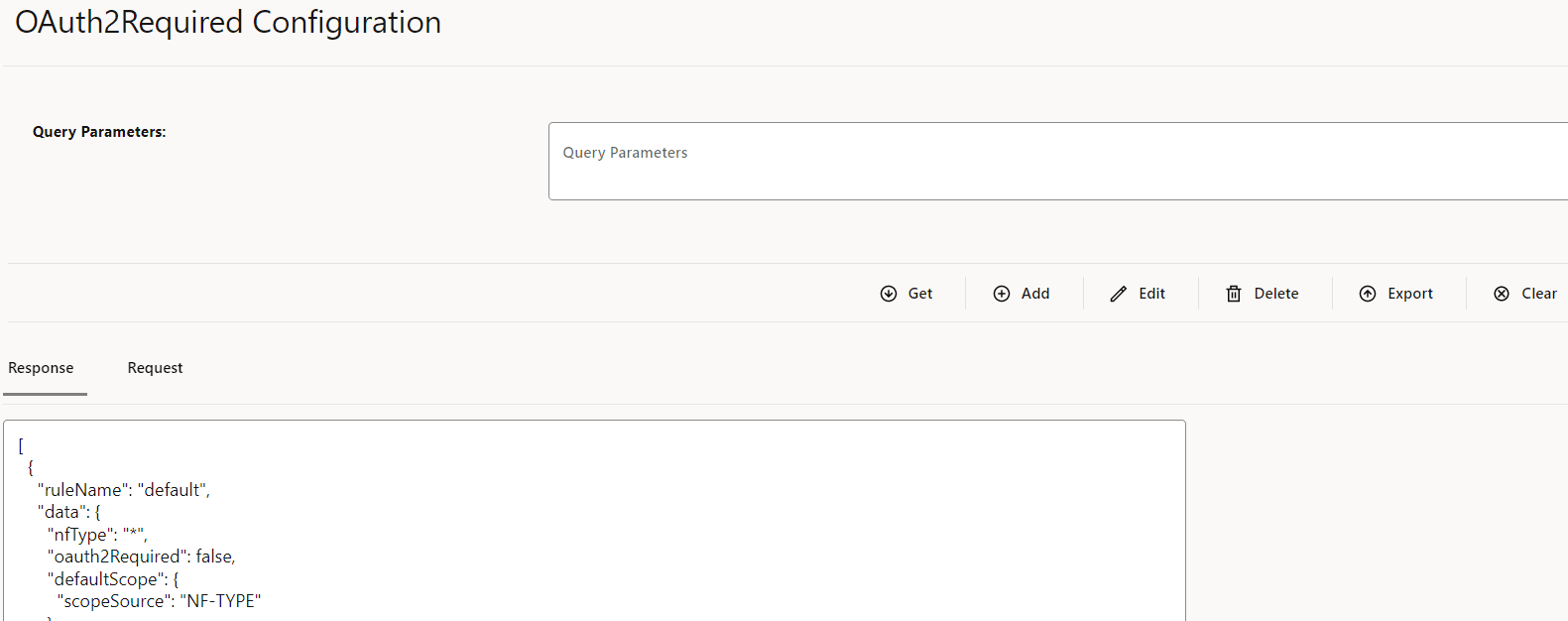
4.2.1.14 Configuring Support for OAuth2.0
Perform the following the procedure to configure support for OAuth2.0.
- In the left navigation pane, click the OAuth2 Support tab.
- In the OAuth2 Support section, click
Edit.
Figure 4-19 OAuth2 Support
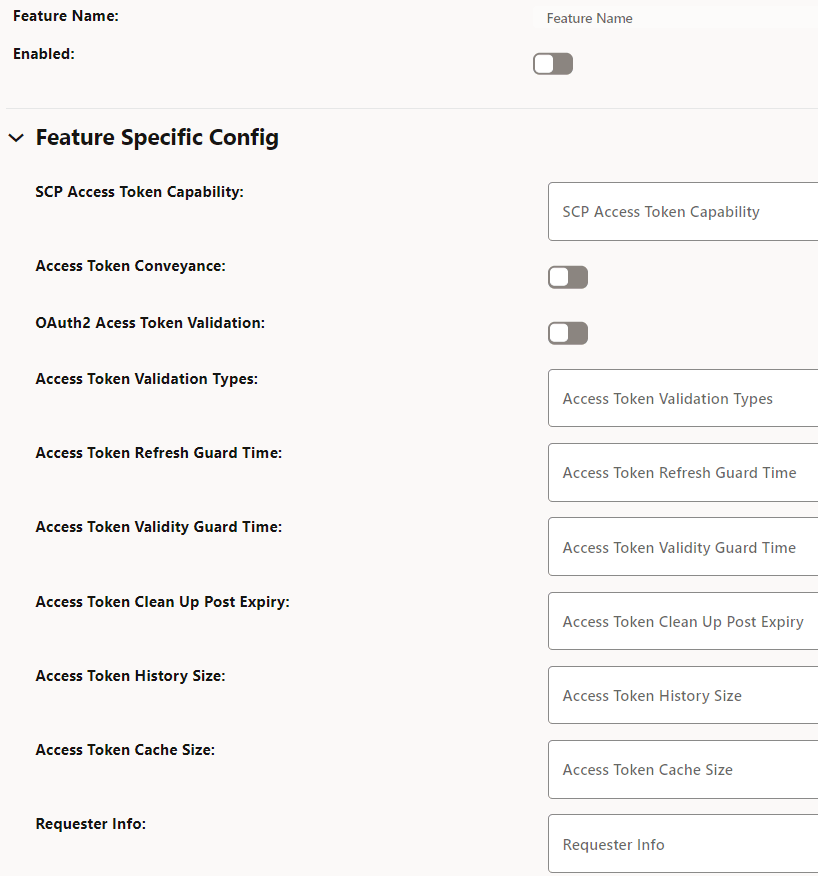
- Set Enabled to true.
By default, this option is set to false.
- In the Feature Specific Config section, complete the
following configurations:
Table 4-3 Configure Access Token
Field Name Description SCP Access Token Capability This field indicates Access token support for the listed indirect communication modes at SCP. (ENUM). Possible values: [INDIRECT_COM_WITH_DELEG_DISC, INDIRECT_COM_WITHOUT_DELEG_DISC]- INDIRECT_COM_WITH_DELEG_DISC: SCP initiates access token request toward NRF in delegated discovery service request.
- INDIRECT_COM_WITHOUT_DELEG_DISC: SCP is expected to forward the service request with or without access token as per configuration at SCP. SCP is not expected to initiate access token request toward NRF.
Access Token Conveyance This field conveys acquired access token in the "3gpp-Sbi-Access-Token" header in service response to consumer NFs.- Default value: true
- Range: true or false
OAuth2 Access Token Validation This field enables or disables validation of OAuth2 access token from consumer NFs. - Default value: Disabled
- Range: Disabled or Enabled
Access Token Validation Types This field configures the list of required validation types in the network. - Default value: empty as default
- Range: Disabled or Enabled
Access Token Refresh Guard Time This field initiates proactive refresh of cached access token when the configured time expires. The proactive refresh occurs if the relevant SBI messages are in exchange. - Default value: 60000ms
- Range: 100ms - 300000ms
Access Token Validity Guard Time This field indicates the time before the access token expiry when SCP considers not to use the existing access token and obtains new access token in the service request forwarded to producer NFs. - Default value: 30000ms
- Range: 100ms - 300000ms
Access Token Clean Up Post Expiry This field indicates the duration to purge the token from cache. - Default value: 900000ms
- Range: 0ms - 3600000ms
Access Token History Size This field indicates the number of access tokens signature history to identify whether the access token initiated by SCP or not. - Default value: 10 records
- Range: 0 - 20 records
Access Token Cache Size This field indicates the number of access tokens that can be cached in SCP. - Default value: 50000 records
- Range: 5000 - 100000 records
Requester Info This field indicates access token requester (consumer NF) Info to generate the access token request. - Prioritized list of default values:
- DISCOVERY-HEADERS
- CCA-HEADER
- USER-AGENT-HEADER
Cache Enabled This option enables or disables caching of access tokens. - Default value: true
- Range: true or false
- Click Save.
4.2.1.15 Configuring SCP Health Check API
Perform the following the procedure to configure SCP health check API.
- In the left navigation pane, click the Health Check tab.
- In the Health Check section, click
Edit.
Figure 4-20 Health Check
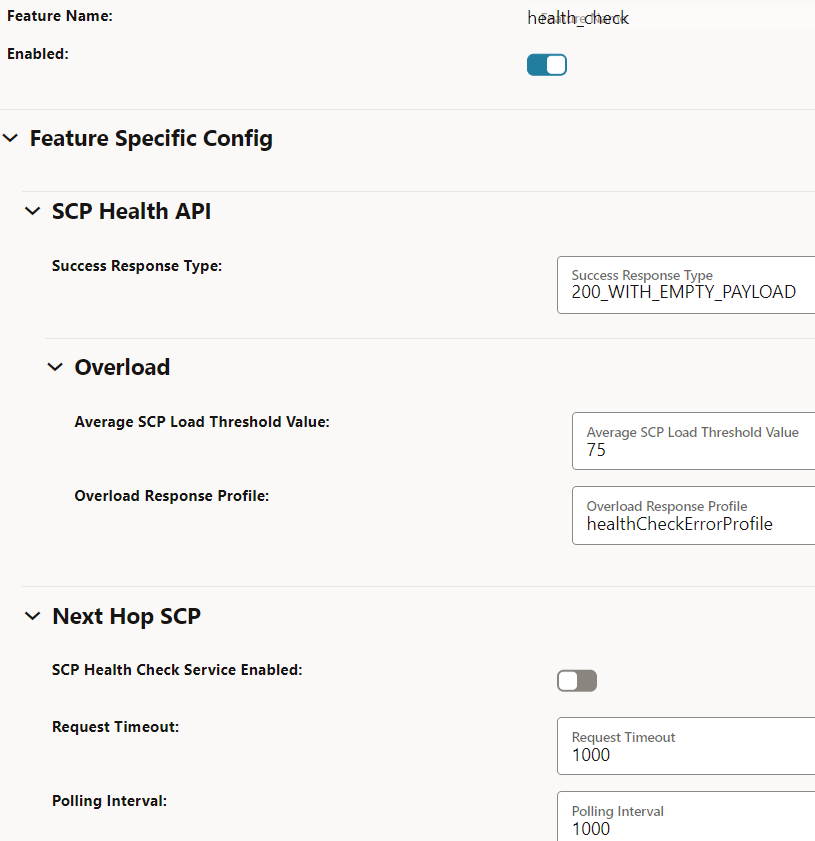
- Ensure that Enabled is set to true.
This is the default configuration.
- In the Feature Specific Config section, you can modify the
following configurations:
Table 4-4 Configure Health Check API
Field Name Description Success Response Type This field indicates successful responses for a healthy SCP. - Default value: 200StatusCodeAndEmptyPayload
- Range: 200WithPayLoad, 200WithEmptyPayload, and 204WithNoContent
Average SCP Load Threshold Value This field provides the overall average SCP load threshold value. - Default value: 75%
- Range: 75% - 90%
Overload Response Profile This field indicates the error profile configuration for the health query response in the exception conditions. - Default value: healthCheckErrorProfile. For more information about this option, see "Configuring Error Profiles" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
SCP Health Check Service Enabled This option enables or disables the SCP health check API feature in inter-scp scenarios. - Default value: false
- Range: true or false
Request Timeout This field indicates the timer to monitor the waiting time for health check response in inter-scp scenarios. - Default value: 1000ms
- Range: 300ms -60000ms
Polling Interval This field indicates the duration to control the periodicity of health check requests in inter-scp scenarios. - Default value: 1000ms
- Range: 300ms -60000ms
Consecutive Error Response This field indicates the total number of consecutive failure responses that leads to failover in inter-scp scenarios. - Default value: 3
- Range: 1 - 20
Consecutive Success Response This field indicates the total number of consecutive successful responses that leads to fallback in inter-scp scenarios. - Default value: 3
- Range: 1 - 20
- Click Save.
4.2.1.16 NRF Configuration using DNS SRV Resolution
Perform the following procedure to NRF configuration using DNS SRV resolution.
- In the left navigation pane, click the NRF Bootstrap Info tab.
- In the NRF Bootstrap Info section, click
Edit.
Figure 4-21 Edit NRF Bootstrap Info
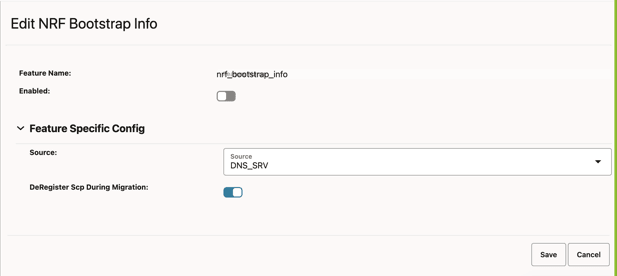
- Set Enabled to true.
By default, this option is set to false.
- In the Feature Specific Config section, enter the following
input for the following configurations:
Table 4-5 Configure NRF Source Configuration
Field Name Description Source This field is used to select whether the NRF Configuration Using DNS SRV Resolution feature should be enabled or disabled. SCP will enable the feature if the source is DNS_SRV. The default value is DNS_SRV.
deRegisterScpDuringMigration In the migration from static to DNS SRV task, if static and DNS SRV NRF configurations are the same, then this parameter will be used to deregister SCP with the old or static NRFset.- Default value: false
- Range: true or false
- Click Save.
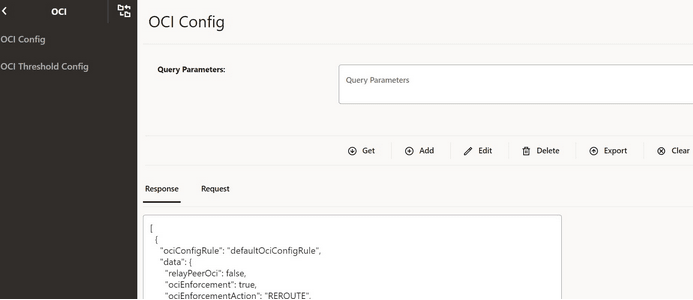
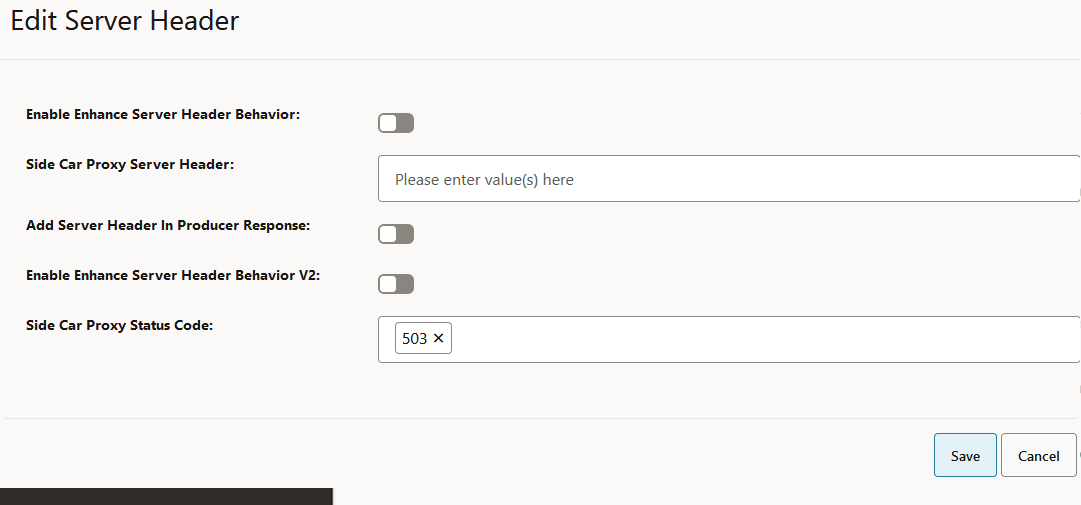
4.2.1.17 Configuring Overload Control Based on the Overload Control Information Header
Perform the following procedure to configure overload control based on the overload control information header.
- From the SCP Features list, click the OCI tab.
- On the OCI page, click the Edit icon.
Figure 4-22 Edit OCI
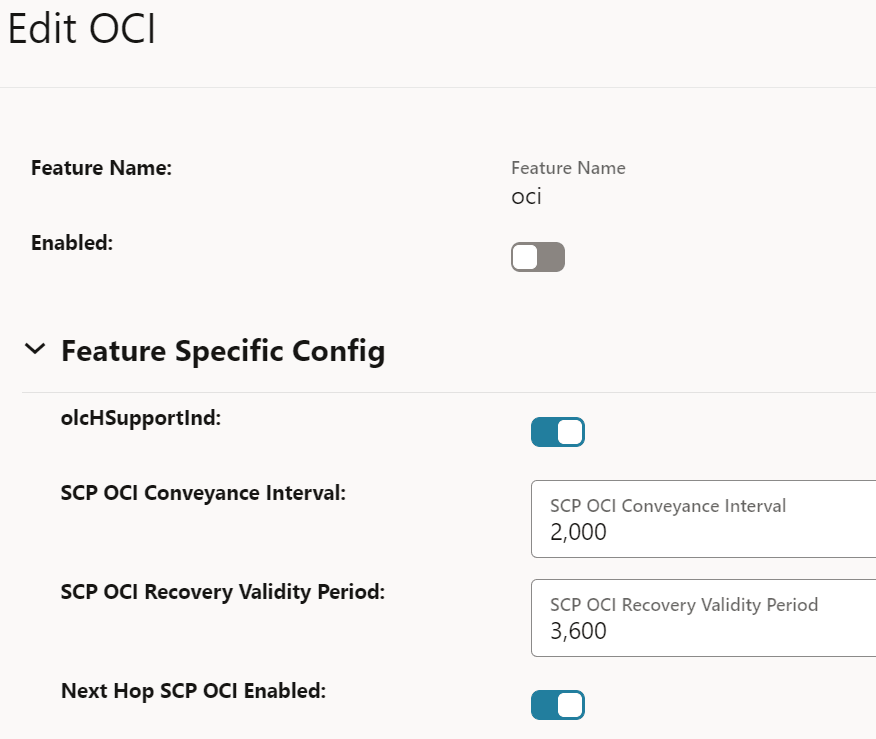
- In the Edit OCI section, set
Enabled to true.
By default, this option is set to false.
Figure 4-23 Enabling OCI
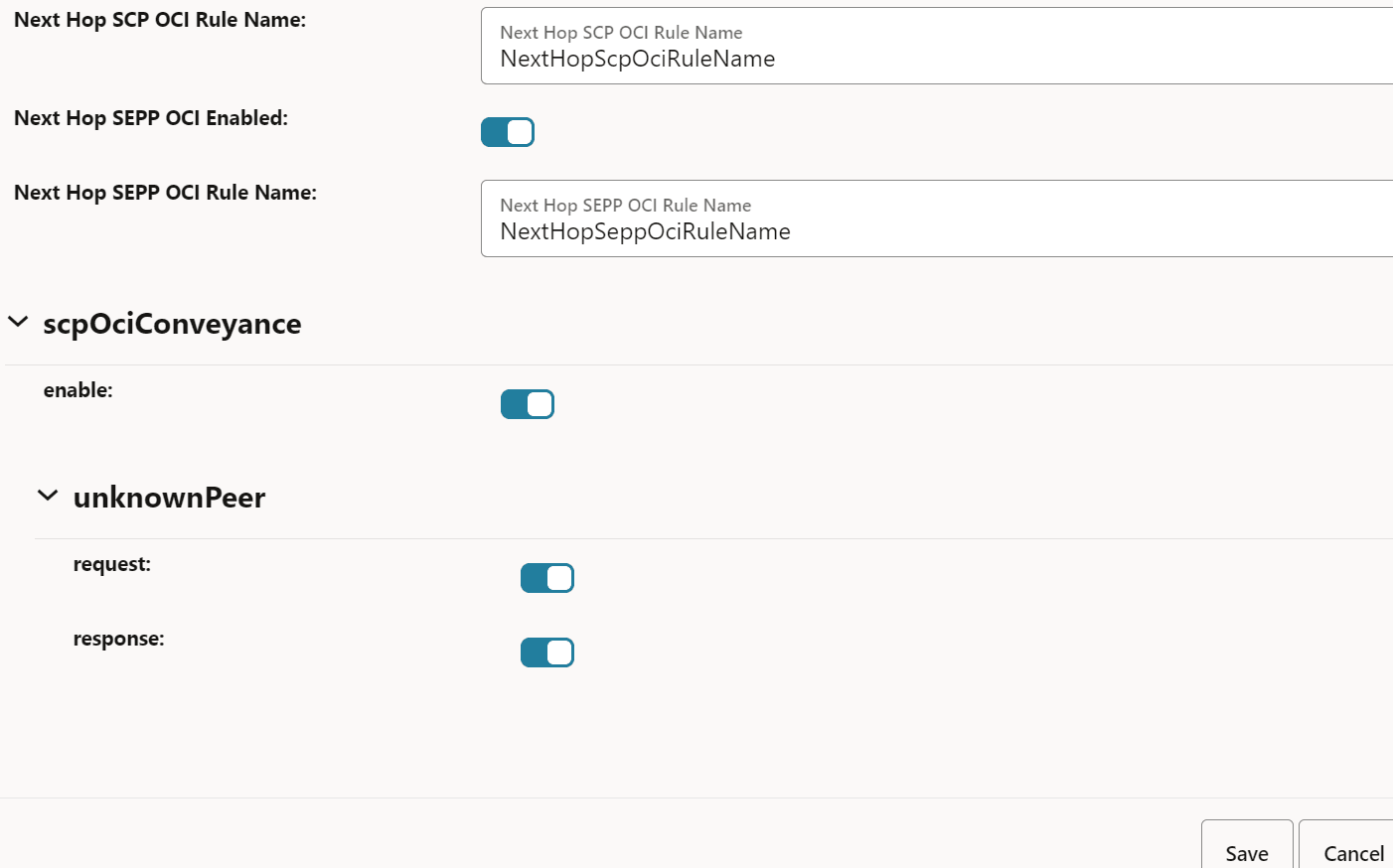
- To configure OCI, in the Feature Specific Config
section, set the following fields:
Table 4-6 Configure OCI
Field Name Description olcHSupportInd This option indicates that SCP supports the Overload Control Information (OCI) feature based on the 3gpp-Sbi-Oci header. By default, this option is enabled.
SCP OCI Conveyance Interval This field indicates the interval for reporting SCP OCI to peer NFs. For every interval until the validity period, the last sent OCI is reported to peer NF irrespective of any change to SCP OCI. Sending SCP OCI periodically ensures that the peer NF has not missed an earlier reported SCP OCI. The same OCI header as sent on the last OCI threshold change or validity period expiry is sent. - Default value: 2000 milliseconds
- Range: 2000 to 3600000 milliseconds
Note: OCI is sent to peer NFs only if there is a message for that NF.
SCP OCI Recovery Validity Period This field indicates the validity period to send OCI headers to peers when SCP recovers from an overloaded state. SCP sends OCI to peers with reduction metric as 0. - Default value: 3600 seconds
- Range: 5 to 3600 seconds
Next Hop SCP OCI Enabled This option enables or disables the OCI feature between SCP instances and SCP scope OCI. By default, this option is enabled.
Next Hop SCP OCI Rule Name If the Next Hop SCP OCI Enabled option is enabled, the OCI feature enforcement is done based on the ociConfigRule REST API configuration with the name provided as the value for this option. By default, this value is NextHopScpOciRuleName.
Next Hop SEPP OCI Enabled This option enables or disables OCI enforcement between SCP and SEPP interfaces and SEPP scope OCI. By default, this option is enabled.
Next Hop SEPP OCI Rule Name If the Next Hop SEPP OCI Rule Name option is enabled, the OCI feature enforcement is done based on the ociConfigRule REST API configuration with the name provided as the value for this option. By default, this value is NextHopSeppOciRuleName.
scpOciConveyance If this option is set to true, SCP starts conveying the 3gpp-Sbi-Oci header based on self-overload information. By default, this option is enabled.
unknownPeer
- request
If this field is set to true, SCP starts conveying the 3gpp-Sbi-Oci header based on self-overload information to requests to unknown peers. For unknown peers, identification of peer NFs is done based on the message request's FQDN. By default, this option is enabled.
unknownPeer
- response
If this option is set to true, SCP starts conveying the 3gpp-Sbi-Oci header based on self-overload information to responses to unknown peers. If this parameter is set to true, SCP adds self-OCI header in every response message. By default, this option is disabled.
- Click Save.
4.2.1.18 Configuring Enhanced NFProfile Processing
- In the left navigation pane, click the Ignore Unknown Nf
Service tab.
The Ignore Unknown Nf Service page appears.
Figure 4-24 Ignore Unknown Nf Service
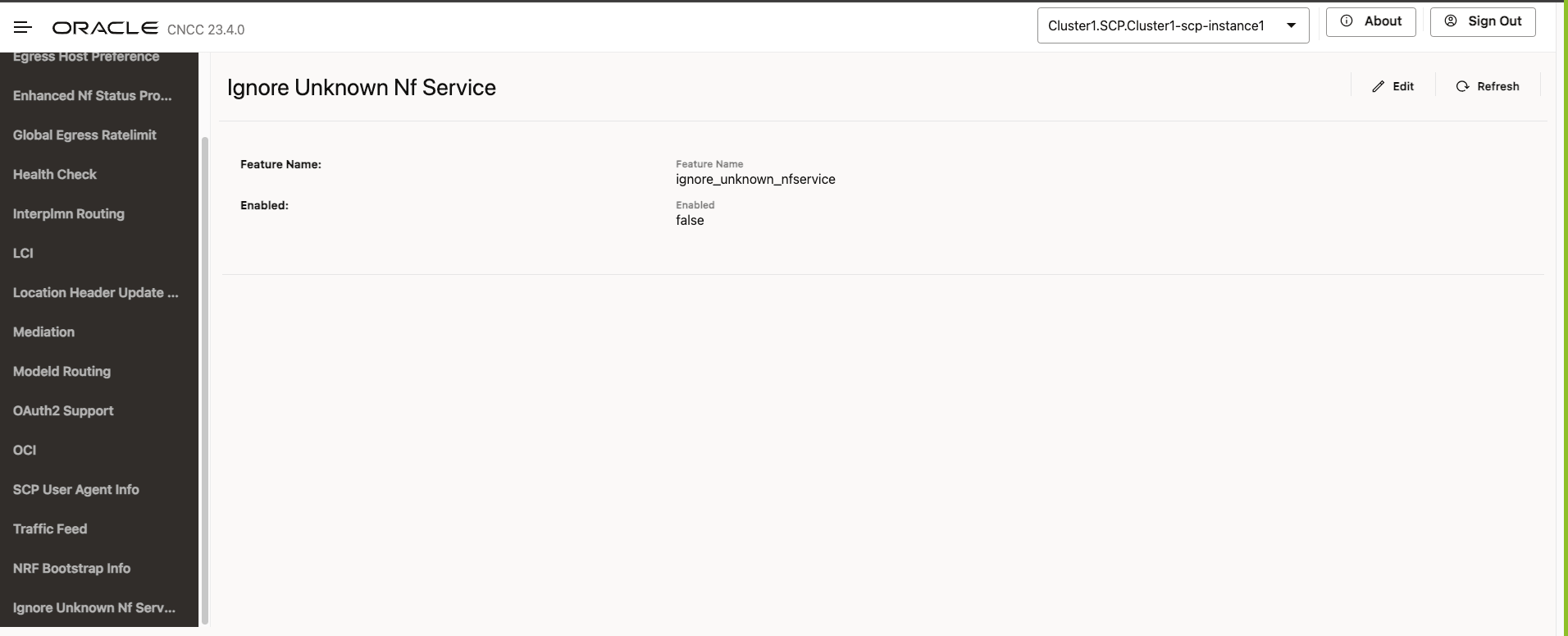
- On the Ignore Unknown Nf Service page, click the Edit icon.
- In the Edit Ignore Unknown Nf Service
section, set Enabled to true.
By default, this option is set to false.
4.2.1.19 Configuring 3GPP Timestamp Headers Support
- In the left navigation pane, click the SCP tab, and then click the SCP Features tab.
- From the SCP Features list, click Timestamp Header Support.
- In the Timestamp Header Support
section, click Edit.
Figure 4-25 Edit Timestamp Headers Support

- Set Enabled to true.
By default, this option is set to false.
- In the Feature Specific Config section,
configure the following fields as required:
- Dynamic Response Timeout: This
field, when set to true, enables SCP to perform dynamic response time
calculations based on the received timestamp headers. It updates or adds
the 3gpp-Sbi-Sender-Timestamp and 3gpp-Sbi-Max-Rsp-Time headers in the
egress SBI request.
- Date Type: Boolean
- Default Value: true
- Range: true or false
- Update Timestamp Headers: This field,
when set to true and dynamicResponseTimeout is false, allows SCP to add
or update the 3gpp-Sbi-Sender-Timestamp and 3gpp-Sbi-Max-Rsp-Time
headers in the egress SBI request. The 3gpp-Sbi-Sender-Timestamp is set
to reflect the current timestamp at scp-worker, while the
3gpp-Sbi-Max-Rsp-Time will be set to the configured responseTimeout
value for the specific service.
- Date Type: Boolean
- Default Value: true
- Range: true or false
Note:
When dynamicResponseTimeout is true, the value of updateTimestampHeaders will not have any impact and should be set to true. In this case, SCP will always add or update the 3gpp-Sbi-Sender-Timestamp and 3gpp-Sbi-Max-Rsp-Time headers in the egress SBI request. - Response Transit Time: This field
specifies the minimum estimated transit time required (in milliseconds)
for the response to reach back from SCP to the original sender, whether
it's the Consumer NF, SCP, or SEPP.
- Default
Value:
"responseTransitTime": { "downstreamNF": 50, "downstreamSCP": 100, "downstreamSEPP": 300 } - Range: NA
- Default
Value:
- Downstream NF: This field specifies
the minimum estimated transit time required (in milliseconds) for the
response to return to the original requester NF.
- Date Type: Integer
- Default Value: 50
- Range: 0 - 10000
- Downstream SCP: This field specifies
the minimum estimated transit time required (in milliseconds) for the
response to return to the original requester SCP.
- Date Type: Integer
- Default Value: 100
- Range: 0 - 10000
- Downstream SEPP: This field
specifies the minimum estimated transit time required (in milliseconds)
for the response to return to the original requester SEPP.
- Date Type: Integer
- Default Value: 300
- Range: 0 - 10000
- Dynamic Response Timeout: This
field, when set to true, enables SCP to perform dynamic response time
calculations based on the received timestamp headers. It updates or adds
the 3gpp-Sbi-Sender-Timestamp and 3gpp-Sbi-Max-Rsp-Time headers in the
egress SBI request.
- Click Save.
Note:
For optimal functionality, this feature requires NTP (Network Time Protocol) synchronization across all nodes communicating with the SCP, including the SCP itself.
4.2.1.20 Configuring Enhanced Notifications Handling
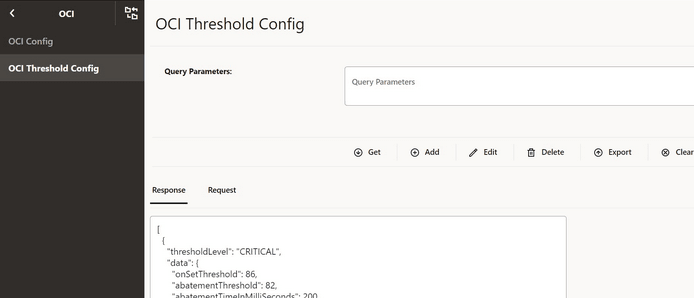
4.2.2 Configuring OCI
4.2.3 Configuring OCI Threshold Levels
4.2.4 Viewing cnDBTier APIs on the CNC Console
Note:
The following cnDBTier APIs are read only.4.2.4.1 Backup List
- From the left navigation pane, click the SCP tab, and then click the cnDBTier tab.
- Click the Backup List to view the list of
completed backups along with Backup ID, Backup size, and Creation Timestamp.
The Backup List screen is displayed.
Table 4-9 Backup List
Fields Description Backup Details This field displays information such as backup Id, backup size, and backup creation timestamp. Site Name This field displays the name of the current site to which SCP is connected. Backup Id This field displays the ID of the stored backup. Backup Size (bytes) This field displays the size of the stored backup. Creation TimeStamp This field displays the time recorded when the backup was stored.
4.2.4.2 cnDBTier Backup Status
- From the left navigation pane, click the SCP tab, and then click the cnDBTier Backup Status tab.
- On the cnDBTier Backup Status page, click
Refresh to view the latest cnDBTier backup status as
described in the following table:
Table 4-10 cnDBTier Backup Status
Fields Description Current Timestamp This field displays the current system time. Is Backup In Progress This field displays whether any backup is in progress or not. Next Backup Scheduled Timestamp This field displays the time for the next scheduled backup.
4.2.4.3 cnDBTier Version
- From the left navigation pane, click the SCP tab, and then click the cnDBTier tab.
- Click the cnDBTier Version to view the
version.
Table 4-11 cnDBTier Version Attributes
Fields Description cnDBTier Version This field displays the cnDBTier version. NDB Version This field displays the network database (NDB) version.
4.2.4.4 Database Statistics Report
- From the left navigation pane, click the SCP tab, and then click the cnDBTier tab.
- Click the Database Statistics Report to view
the available database.
Table 4-12 Database Statistics Report
Fields Description Database Count This field displays the number of available database. Database Tables Count This field displays the available database names and their table count. Database Name This field displays the database name. Table Count This field displays the table count for each database. Database Table Rows Count This field displays the table rows present in each table. Click on View icon available next to the database name to view the View Database Table Rows Count screen.Table 4-13 View Database Table Rows Count
Fields Description Database Name This field displays the database name. Tables This field displays the table names and the corresponding rows in each table. Table Name This field displays the table name. Row Count This field displays the table rows present in each table.
4.2.4.5 Georeplication Recovery
- From the left navigation menu, navigate to SCP and then click cnDBTier tab.
- Click Georeplication Recovery to access the
Georeplication Recovery Status of the cnDBTier cluster. This includes options
such as Update Cluster As Failed, Start Georeplication Recovery, and
Georeplication Recovery Status.
- Click the Update Cluster As Failed to mark the
cluster as FAILED.
The Update Cluster As Failed page is displayed.
Table 4-14 Update Cluster As Failed
Fields Description Cluster Names This field displays a list of cnDBTier clusters that can be marked as failed. Failed Cluster Names This field displays a cnDBTier cluster that is marked as failed. Click Update Cluster. The selected cluster name is updated in the Failed Cluster Names field.
- Click the Start Georeplication
Recovery to start the georeplication recovery process
for a failed site.
The Start Georeplication Recovery page is displayed.
Table 4-15 Start Georeplication Recovery
Attribute Description Failed Cluster Name This field displays a list of all the clusters that have been marked as failed. Backup Cluster Name (Optional) This field displays a list of all the healthy clusters. If no cluster is selected, the system uses the first available healthy cluster for the backup. Click Start Georeplication Recovery to initiate georeplication recovery.
- Click the Georeplication Recovery
Status to view the status of georeplication recovery for
cnDBTier clusters.
The Georeplication Recovery Status page is displayed.
Table 4-16 Georeplication Recovery Status
Attribute Description Local Cluster Name This field displays the name of the local cluster. Georeplication Recover Status Details This field displays the details of the georeplication recovery status of cnDBTier clusters. Cluster Name This field displays the clusters by name. Georeplication Recovery Status This field displays the current georeplication recovery status of the corresponding cluster.
The following are the statuses of Georeplication Recovery:Table 4-17 Georeplication Recovery Status
Georeplication Recovery Status Description ACTIVE The cluster is in a healthy state, and replication is up and running with its respective mate cluster. REINSTALLED The cluster enters this state during fatal error recovery when the end user reinstalls the cluster. STARTDRRESTORE When Georeplication recovery is started, the cluster will transition into this state. INITIATEBACKUP When Georeplication recovery is started, the cluster will identify a healthy cluster for backup initiation and transition into this state. CHECKBACKUP When the backup is initiated, the georeplication recovery cluster will monitor the progress of the backup until its completion. If the backup fails, the cluster will restart the backup. COPY_BACKUP Upon completion of the backup, the georeplication recovery cluster will request the transfer of the backup from the healthy cluster to the georeplication recovery cluster. CHECK_BACKUP_COPY When backup copy is started georeplication recovery cluster will monitor for the backup transfer progress till it's completion and if it's fails the cluster will re-initiates the backup transfer. BACKUPCOPIED When the backup copy is started, the georeplication recovery cluster will monitor the progress of the backup transfer until its completion. If the transfer fails, the cluster will restart the backup transfer. BACKUPEXTRACTED This state indicates that the backup has been successfully extracted at the georeplication recovery cluster, allowing the restoration of the backup to start. FAILED This state is used by end user to mark specific cluster as failed and hence georeplication recovery is essential to recover the cluster.This state can also indicates that georeplication recovery started and the database is restored using the healthy cluster backup. UNKNOWN This state is used by the end user to mark a specific cluster as failed, necessitating georeplication recovery for cluster recovery. Additionally, this state can indicate that georeplication recovery has started and the database has been restored using the backup from the healthy cluster. RECONNECTSQLNODES This state is used to instruct SQL nodes to be offline during backup restoration to prevent any records from entering the binlog of the georeplication recovery cluster. BACKUPRESTORE This state indicates that the backup, successfully copied from the healthy cluster, is currently being used to restore the georeplication recovery cluster. RESTORED When the backup is successfully restored in the georeplication recovery cluster, the cluster will enter this state to start the reestablishment of replication channels. BINLOGINITIALIZED This state indicates the start of binlogs for the restoration of replication channels, necessary to start the restore process RECONFIGURE When the binlog is restarted, the georeplication recovery cluster will reestablish the replication channels with respect to all its mate clusters. - Click the Update Cluster As Failed to mark the
cluster as FAILED.
4.2.4.6 Georeplication Status
- From the left navigation pane, click the SCP tab, and then click the cnDBTier tab.
- Click the Georeplication Status to view the
local site and remote site name to which SCP is connected.
Table 4-18 Georeplication Status
Fields Description Local Site Name This field displays the local site name to which SCP is connected. Remote Site Name This field displays the remote site name. Replication Status This field displays the replication status with corresponding sites. Seconds Behind Remote Site This field displays the number of seconds that the last record read by the local site is behind the latest record written by the remote site for all the replication groups. - Click the View icon in the
Actions menu to view the View
Georeplication Status screen.
Table 4-19 Georeplication Status
Fields Description Replication Group Delay This field displays the number of seconds that the last record read by the local site is behind the latest record written by the remote site for individual replication groups. Replication Channel Group Id This field displays the ID of the replication channel group. - Click the View icon to view the
Replication Group Delay attributes.
Table 4-20 View Replication Group Delay
Fields Description Channel Details This field displays the channel details such as Remote Replication IP and Role. Remote Replication IP This field displays the IP of the remote replication channel. Role This field displays the role of the replication channel IP.
- Click the View icon in the
Actions menu to view the View
Georeplication Status screen.
4.2.4.7 Replication HeartBeat Status
- From the left navigation pane, click the SCP tab, and then click the cnDBTier tab.
- Click the Replication HeartBeat Status to
view the connectivity between local site and remote site name to which SCP is
connected.
Table 4-21 Replication HeartBeat Status Details
Fields Description Site Name This field displays the name of the current site to which SCP is connected. HeartBeat Details This field displays information such as the remote site name, heartbeat status, heartbeat lag, and replication channel group id. Remote Site Name This field displays the remote site name. Heartbeat Status This field displays the connectivity status with corresponding sites. Heartbeat Lag This field displays the delay or latency in seconds it took to synchronize between sites. Replication Channel Group Id This field displays the ID of the replication channel group.
4.2.4.8 Local Cluster Status
- From the left navigation pane, click the SCP tab, and then click the cnDBTier tab.
- Click the Local Cluster Status to view the
local cluster status for the current site:
Table 4-22 Local Cluster Status
Fields Description Cluster Name This field displays the name of the current cluster to which SCP is connected. Cluster Status This field displays the local cluster status for the current site.
4.2.4.9 On Demand Backup
- From the left navigation pane, click the SCP tab, and then click the cnDBTier tab.
- Click the On Demand Backup to create a new
backup and view the status of initiated on-demand backups.
Table 4-23 On Demand Backup Details
Fields Description Site Name This field displays the name of the current site in which the cnDBTier cluster is deployed. DR Status This field displays the disaster recovery status. Backup Id This field displays the ID of the stored backup. Backup Status This field displays the status of backup. Transfer Status The field displays the status of the local transfer. Remote Transfer Status The field displays the status of remote transfer. Initiate Backup The field displays whether the backup is initiated or not. - Click the Edit icon.
The Edit On Demand Backup screen appears.
Note:
The Edit mode is available only for Initiate Backup. - Enable the Initiate Backup option click
Save.
A confirmation message "Save successfully" appears.
- Click theCancel to navigate back to the On Demand Backup screen.
- Click the Refresh to reload the On Demand Backup screen.
- Click the Edit icon.
4.2.4.10 cnDBTier Health
- From the left navigation menu, navigate to
SCP and then click cnDBTier
tab.
The cnDBTier page is displayed.
- Click cnDBTier Health to view the health
status of the microservices like replication, backup manager, monitor services,
and NDB services.
The cnDBTier Health page is displayed.
- Click the Backup Manager Health Status to view the
health status of the backup manager.
The Backup Manager Health Status page is displayed.
Note:
The following APIs are read-only.Table 4-24 Backup Manager Health Status
Fields Description Service Name This attribute displays the service name of the backup manager microservice. Service Status This attribute displays the service status of the backup manager microservice. Possible values are UP and DOWN.
DB Connection Status This attribute displays the database connection status of the backup manager microservice. Possible values are UP and DOWN.
Overall Backup Manager Service Health This attribute displays the overall health status of the backup manager microservice. Possible values are UP and DOWN.
Backup Executor Health Status This attribute displays the following information like node id and DB connection status of the backup executor. Node Id This attribute displays the id of the node. DB Connection Status This attribute displays the backup executor database connection status with the nodes. Possible values are UP and DOWN.
- Click the Monitor Health Status to
view the health status of the services.
The Monitor Health Status page is displayed.
Note:
The following APIs are read-only.Table 4-25 Monitor Health Status details
Attribute Description Service Name This attribute displays the service name of the monitor microservice. DB Connection Status This attribute displays the database connection status of the monitor microservice. Possible values are UP and DOWN.
Metric Scrape Status This attribute displays the status of the metric scrape, that is if the metrics are fetched or not. If the metrics are fetched then the service is up and vice versa. Possible values are UP and DOWN.
Overall Monitor Service Health This attribute displays the overall health status of the monitor microservice. Possible values are UP and DOWN.
- Click the NDB Health Status to view
the health status of the network database.
The NDB Health Status page is displayed.
Note:
The following APIs are read-only.Table 4-26 NDB Health Status details
Attribute Description Local Site Name This attribute displays the name of the current site. For example, site 1, site 2. NDB Health Status Details This attribute displays the health status of the network database like name of the NDB service, status of the service, health status of PVC. Service Name This attribute displays the service name. For example, ndbmgmd-0, ndbmtd-0, ndbmyappsqld-1, ndbmysqld-2. Service Status This attribute displays the status of the service. Possible values are UP and DOWN.
PVC Health Status This attribute displays the health status of the PVC. Possible values are UP, DOWN, and NA.
Note: This attribute is set to NA when some of the database pods are not connected to the PVC.
- Click the Replication Health Status
to view the health status of the replication sites.
The Replication Health Status page is displayed.
Note:
The following APIs are read-only.Table 4-27 Replication Health Status details
Attribute Description Local Site Name This attribute displays the name of the current site (site 1, site 2 ). Health Status Details This attribute displays the health status details of the local site like replication service name, replication service status, database connection status of the replication service, and the overall health status of the replication micorservices. The number of rows in this table varies depending on the type of deployment (for example, two-site, three-site deployments). Service Name This attribute displays the name of the available replication service. Service Status This attribute displays the status of the available replication service. Possible values are UP and DOWN.
DB Connection Status This attribute displays the database connection status of the replication microservice. Possible values are UP and DOWN.
Overall Replication Service Health This attribute displays the overall health status of the replication microservice. Possible values are UP and DOWN.
- Click the Backup Manager Health Status to view the
health status of the backup manager.
4.2.5 Configuring NRF SRV
- From the left navigation pane, navigate to SCP and click the NRF SRV Configuration tab.
- In the NRF SRV
FQDN section, click the
Add button to create the new
NRF SRV configuration for the given NRF SRV FQDN.
You can configure the NRF configurations at run time, and this NRF SRV FQDN shall be mapped to target NRF FQDNs. SCP uses this NRF SRV FQDN to query the DNS SRV server to get the actual target NRF FQDNs. NRF SRV FQDN
Figure 4-28 Add NRF SRV Configuration
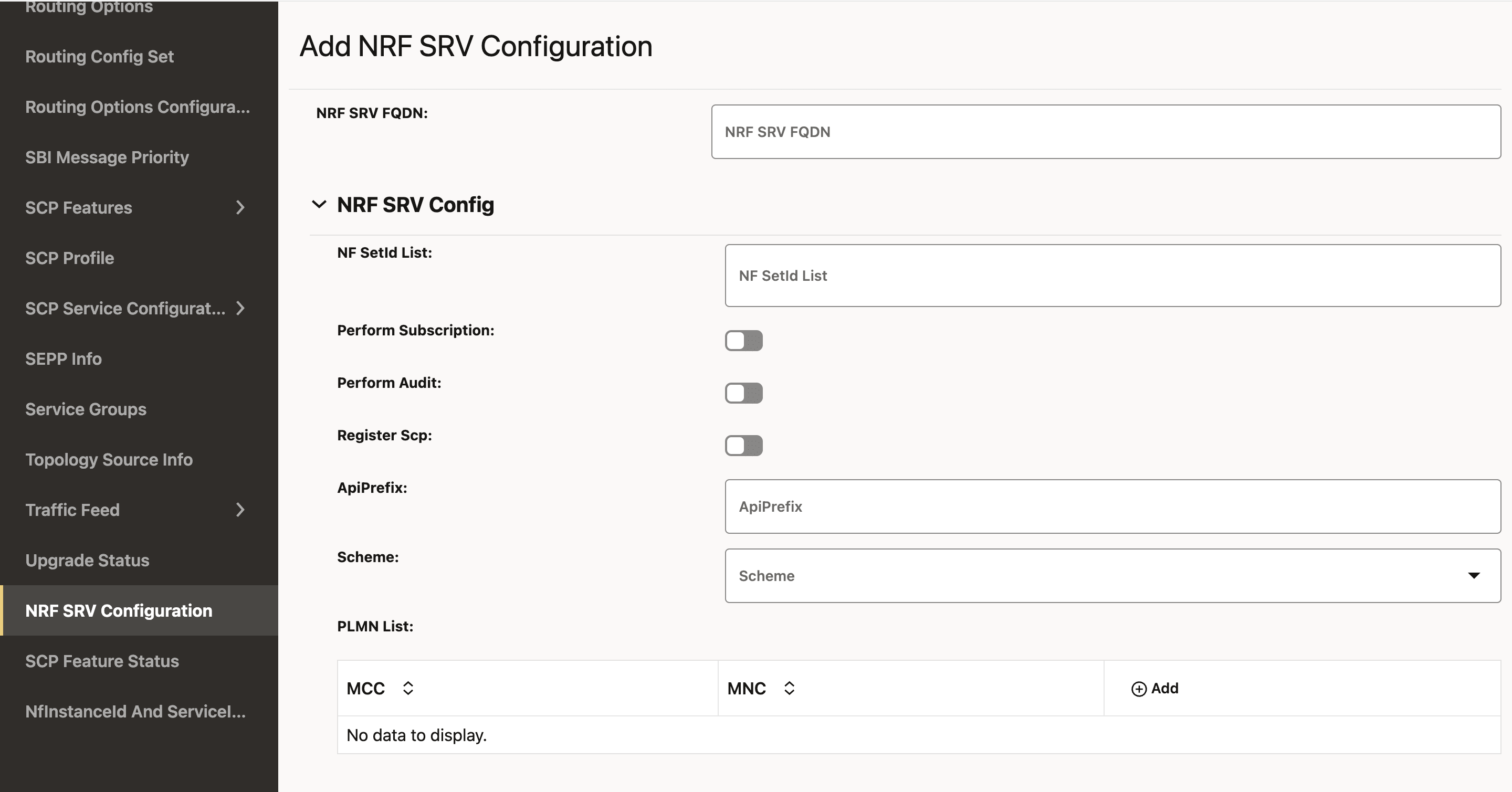
- To configure the NRF SRV, enter the input for the
following fields:
Table 4-28 NRF SRV Configuration
Field Name Description NF SetId List This is the SetId list for this NRF SRV configuration. You can configure multiple nfSetIds, but the NRF profile and rule creation will only take into account the nfSetId from the 0th index.
This setId must be unique for each NRF SRV configuration; that is, this setId must not be present in any other NRF SRV configuration.
Perform Subscription This field allows to decide whether NRF from this NRF SRV should be used for a subscription or not. The possible values are true or false.
Perform Audit This field allows to decide whether NRF from this NRF SRV should be used for a audit or not. The possible values are true or false.
Register SCP This field allows to decide whether to register SCP with the NRF from the NRF Set. The possible values are true or false.
Scheme This field is used for the URI Scheme. The supported value is http/https. PLMN List This field indicates the list of NRFs serving Public Land Mobile Network (PLMN). A PLMN has a unique PLMN code, which consists of a MCC (Mobile Country Code) and an MNC (Mobile Network Code).
Click the Add button to add MCC and MNC, respectively.
Versions This field lists the NFServiceVersion. Configuring multiple API versions is permissible, but at least one entry in the version list must have its apiVersionInUri set to "v1." This is because SCP currently utilizes "v1" for its self-generated requests towards NRF.
- Click the Add button to add NFServiceVersion.
- The supported value of apiVersionInUri is v1/v2.
- The apiFullVersion should be in format x.y.z., for example, 1.0.0.
apiPrefix This field is used in the URI while communicating with NRF. serviceNames Indicates the service name of the NRF SRV configuration.
The nnrf-nfm and nnrf-disc are mandatory for NRF SRV configurations.
The supported value is nnrf-nfm/nnrf-disc/nnrf-oauth2.isInterPlmnFqdn When isInterPLMNfqdn is true, it enables InterPLMN request routing. This means requests coming from foreign PLMNs to the SCP can be routed. SCP will perform intra-PLMN routing to local NRFs based on the interplmnFQDN. - In the NRF SRV FQDN section, click the Edit icon to update the existing NRF SRV configuration.
- Click Save.
4.2.6 Configuring NRF
4.2.7 Configuring Upgrade and Rollback Event
4.2.8 OAuth2.0 Configurations
You must log in to the CNC Console while performing the procedures described in the subsequent subsections. Using these procedures, you can perform the followings tasks:
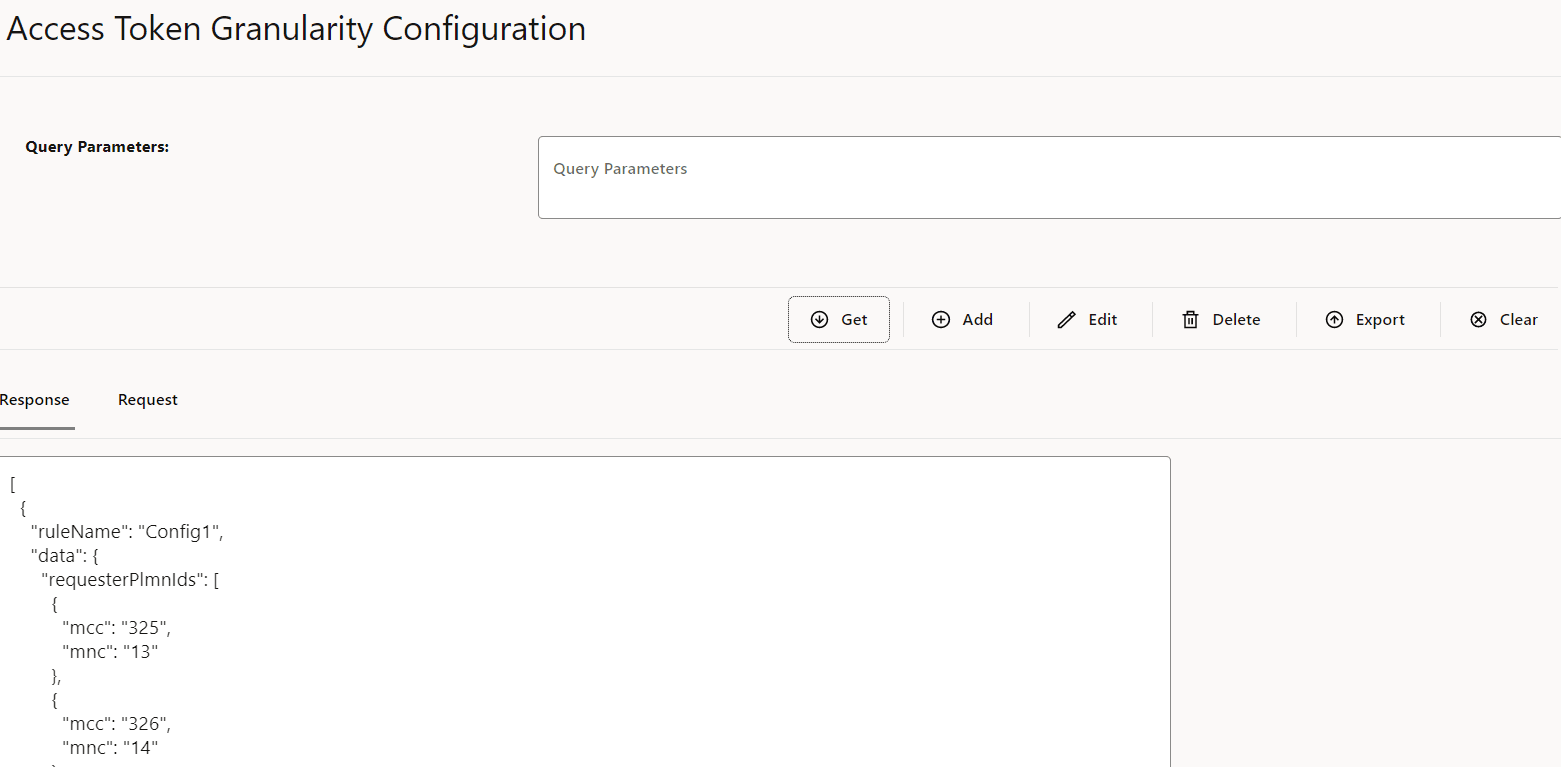
- Configure access token granularity
- Configure OAuth2.0 Local PLMN
4.2.9 Configuring Error Profile
Perform the following procedure to configure different error profiles, which can be used to build "ProblemDetails" sent in the response body to the consumer.
- From the left navigation pane, click the SCP
tab, and then click the Error Profile tab.
Figure 4-34 Error Profile
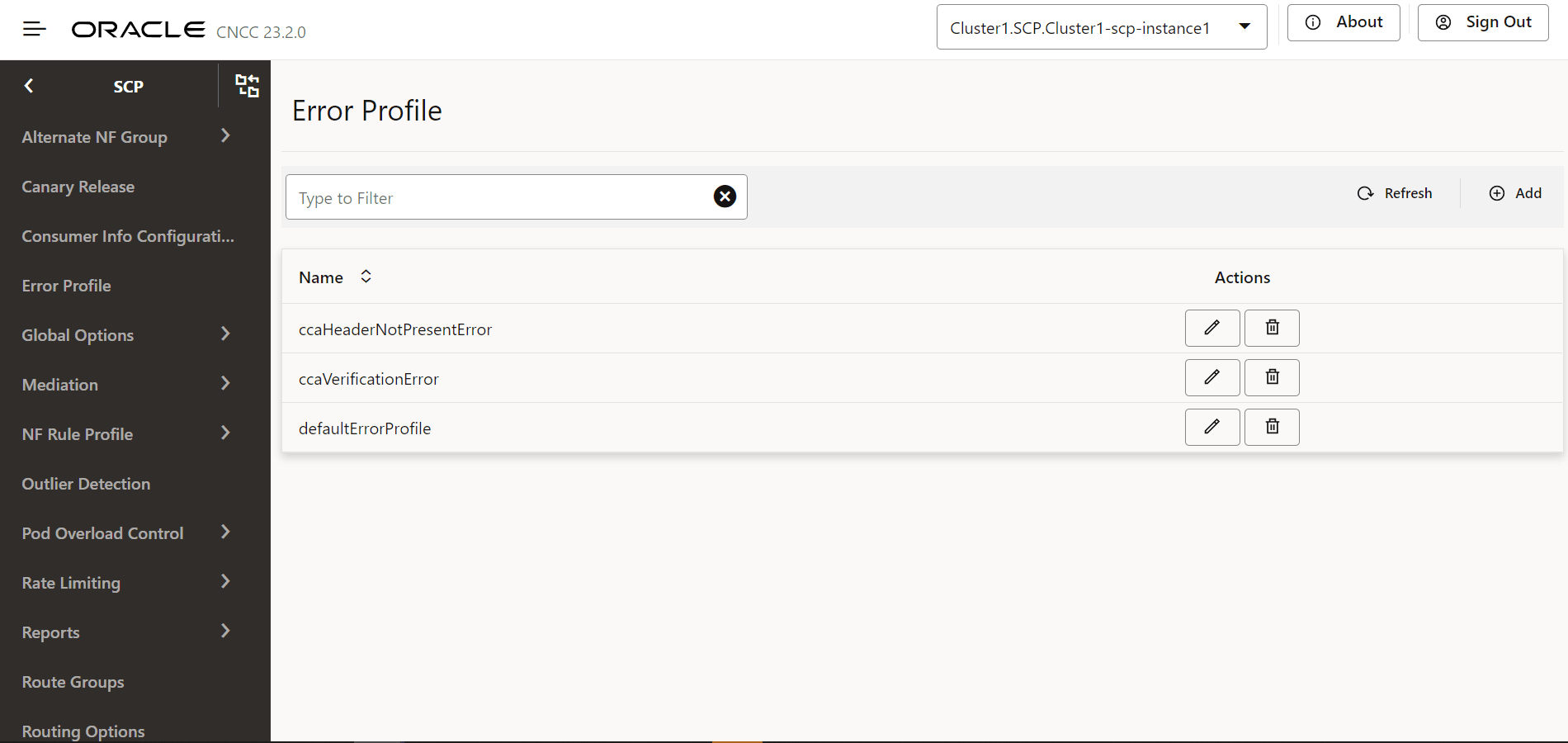
- Click Edit icon from the Actions column for the error profiles
that must be modified. The Edit Error Profile screen appears.
Figure 4-35 Edit Error Profile
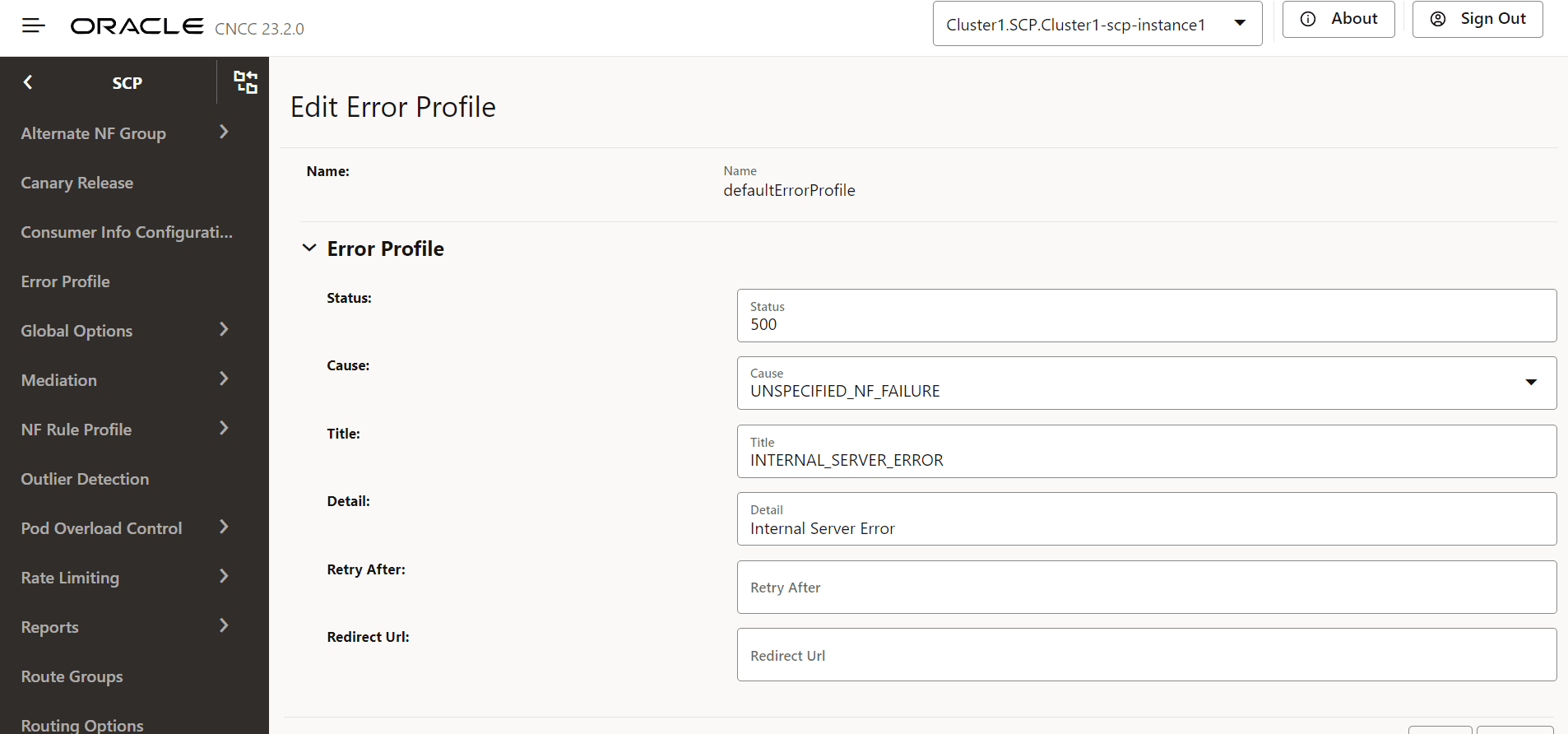
- If the required cause is not available in the Cause
drop-down list, select CUSTOM to customize the cause:
Figure 4-36 Customize the Cause
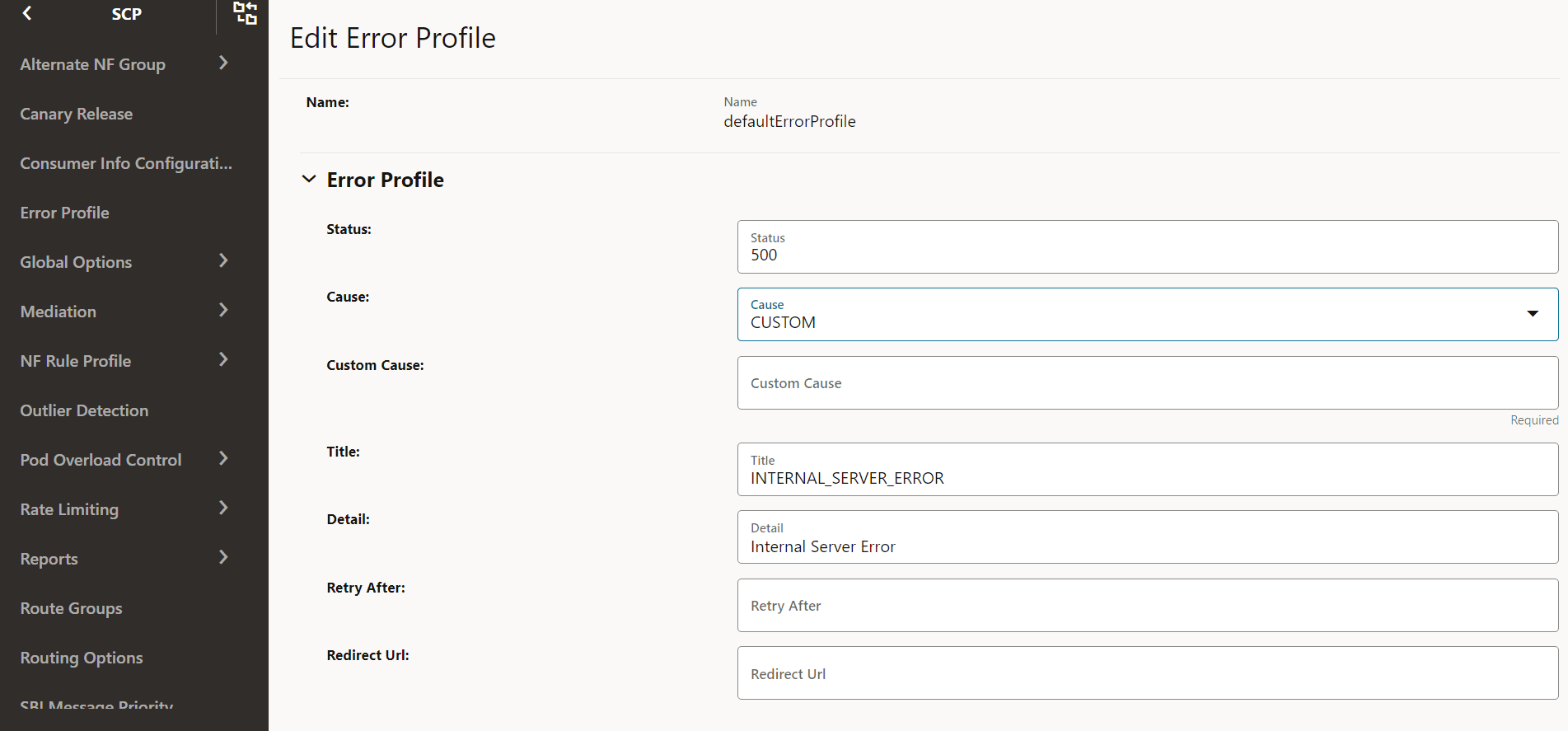
- Make the required modifications for the following parameters:
Table 4-34 Edit Error Profile
Field Description Status HTTP Status Code Cause The list of error causes that are specific to the occurrence of the problem. Custom Cause User defined custom cause. This field will be used only if cause field value is set to "CUSTOM". Title If this field is null, a standard HTTP status code description is added. Detail If present, the same data is used; otherwise, the application can add it optionally. Retry After Indicates the number of seconds after client should retry. Redirect URL Indicates the AbsoluteURL of the resource to which the message is redirected to. For information about configuring error profiles, see "Configuring Error Profile" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- Click Save.
4.2.10 Configuring Canary Release
Following is the procedure to configure Canary Release parameters:
- From the left navigation menu, navigate to SCP and then select Canary Release.
- Click Edit from the
Actions column for the required service that must be modified. The Edit Canary Release
Screen appears.
Figure 4-37 Canary Release
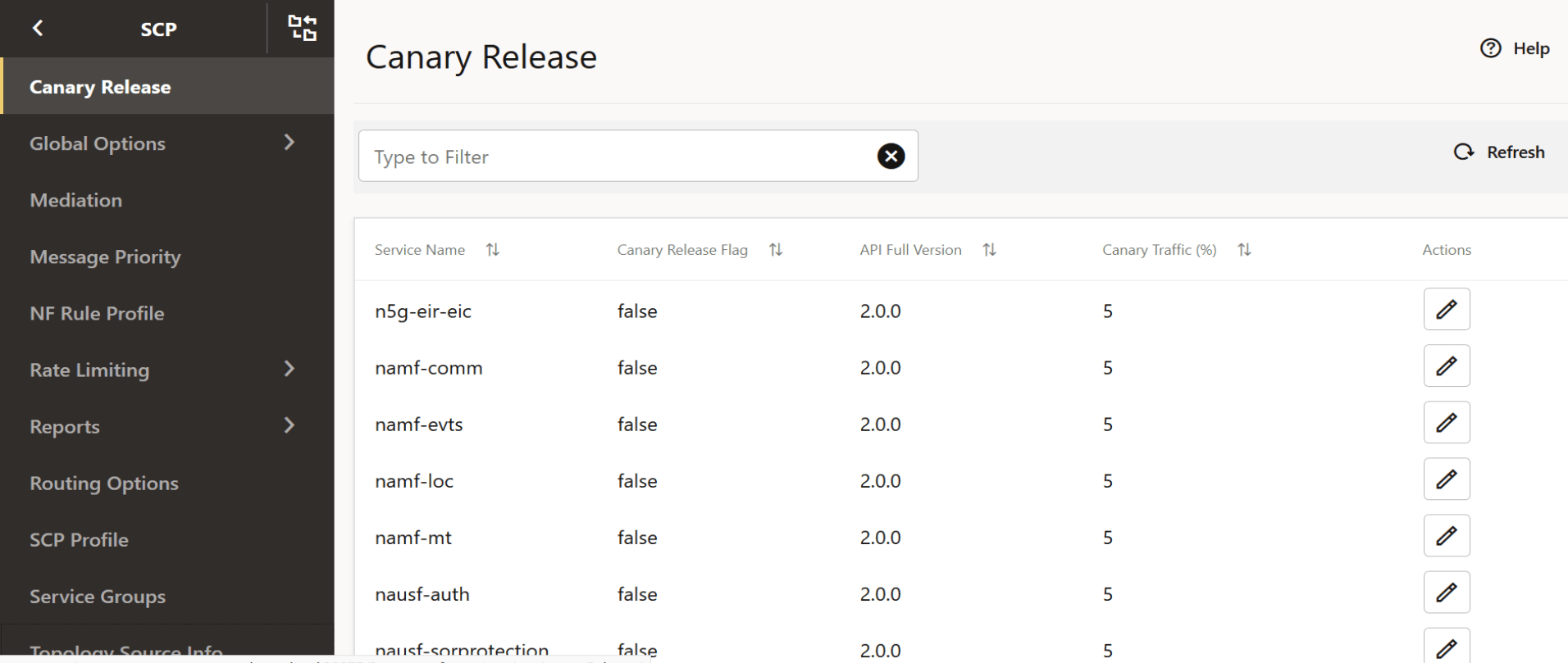
- Make the required modifications for the following parameters:
- Canary Release Flag: Enable/Disable the flag using toggle.
- API Release Version: Provide the release version of the API.
- Canary Traffic: Set the value for the traffic that should be distributed to Canary Release.
For more information about the configuration parameters, see Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.Figure 4-38 Edit Canary Release
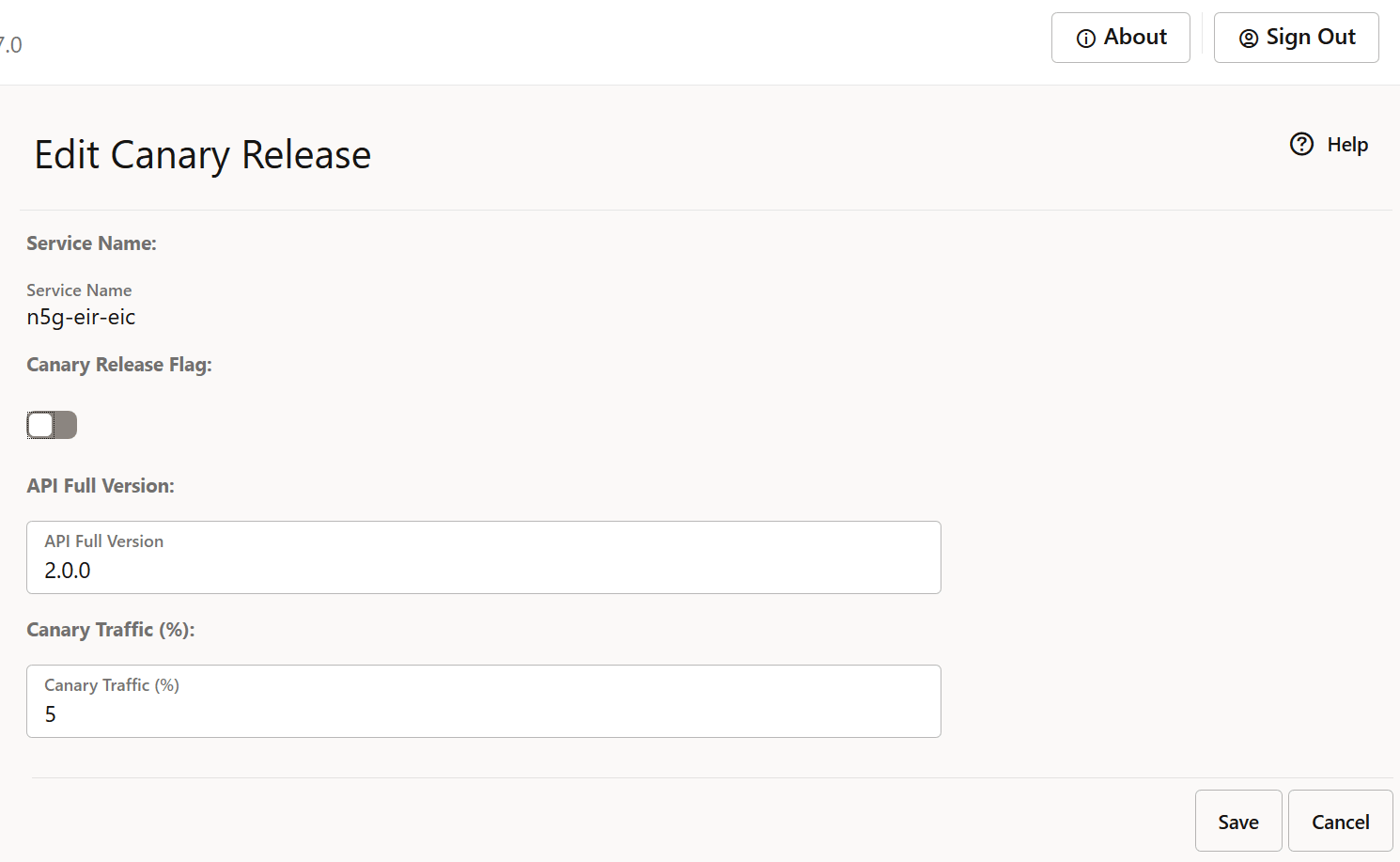
- Click Save.
- Click Refresh to view the updated values on the screen.
4.2.11 Configuring Global Options
Perform the following procedure to configure global options.
Logging Config
- From the left navigation menu, navigate to SCP and select Global Options.
- Select Logging Config.
- Click Edit from the top right side to edit or update Logging
Config parameters.
Figure 4-39 Logging Config
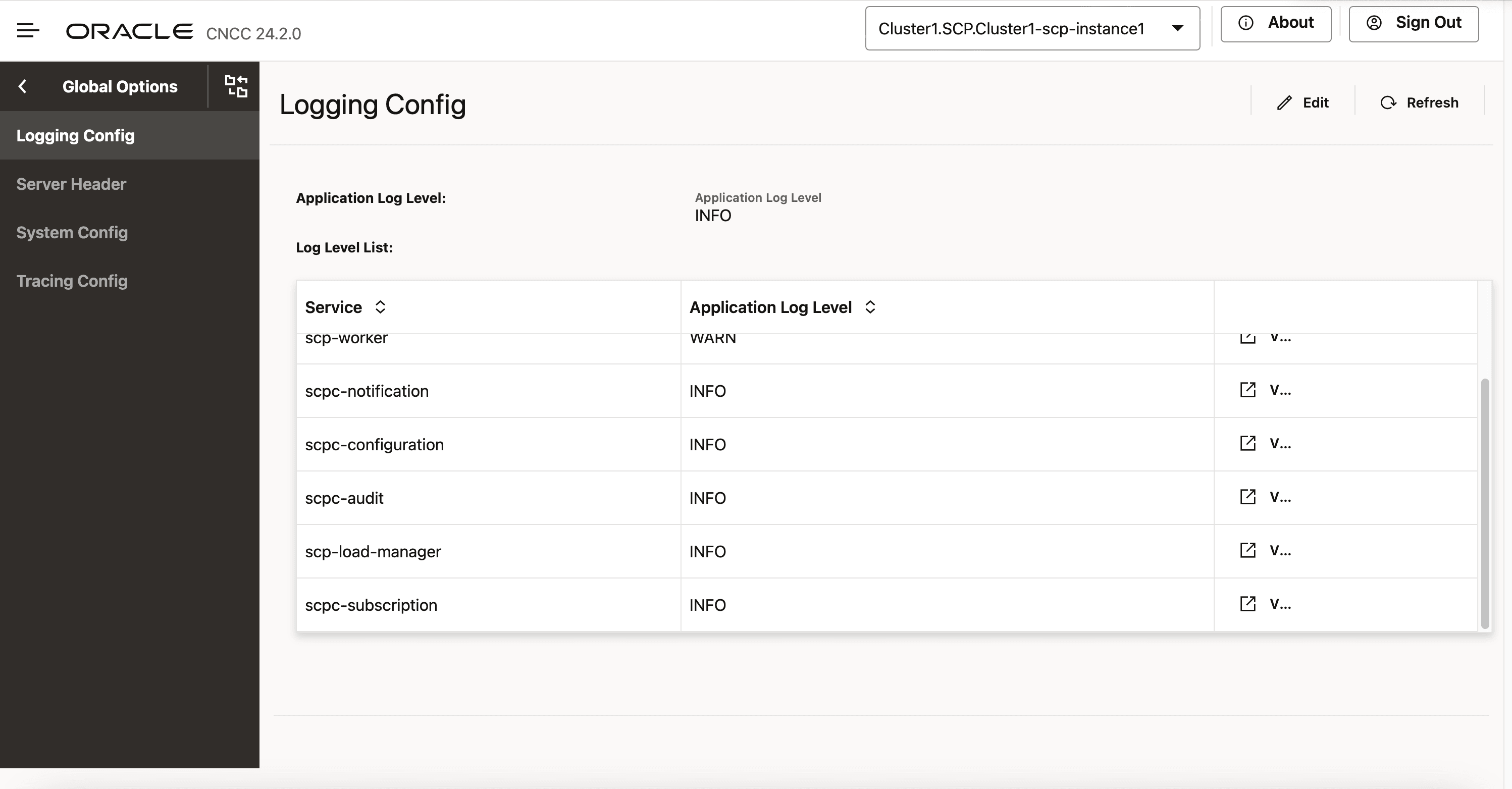
- Select Service Type from the drop-down list to select any
one of the following service type:
- scpc-audit
- scpc-alternate-resolution
- scpc-subscription
- scpc-configuration
- scpc-notification
- scp-worker
- scp-cache
- scp-nrfproxy
- scp-loadmanager
- Select the Application Log Level from the drop-down list to
set the constraints of the log.
The description of each logging level is as follows:
Table 4-35 Logging Level
Logging Level Description DEBUG A log level used for events considered to be useful during software debugging when more granular information is required. INFO The standard log level indicating that something happened, the application entered a certain state, and so on. WARN Indicates that something unexpected happened in the application, a problem, or a situation that might disturb one of the processes. But that doesn’t mean that the application has failed. The WARN level should be used in situations that are unexpected, but the code can continue the work. ERROR The log level that should be used when the application reaches an issue preventing one or more functionalities from properly functioning. TRACE The TRACE log level captures all the details about the behavior of the application. It is mostly diagnostic and is more granular and finer than DEBUG log level. Note: The scpc-notification, scpc-audit, and scpc-loadmanager microservices supports the TRACE log level.
For instance, when you select "scpc-notification" as the service type from the Service drop-down list, the Application Log Level drop-down list will display the "TRACE" log level.
Figure 4-40 TRACE Log Level
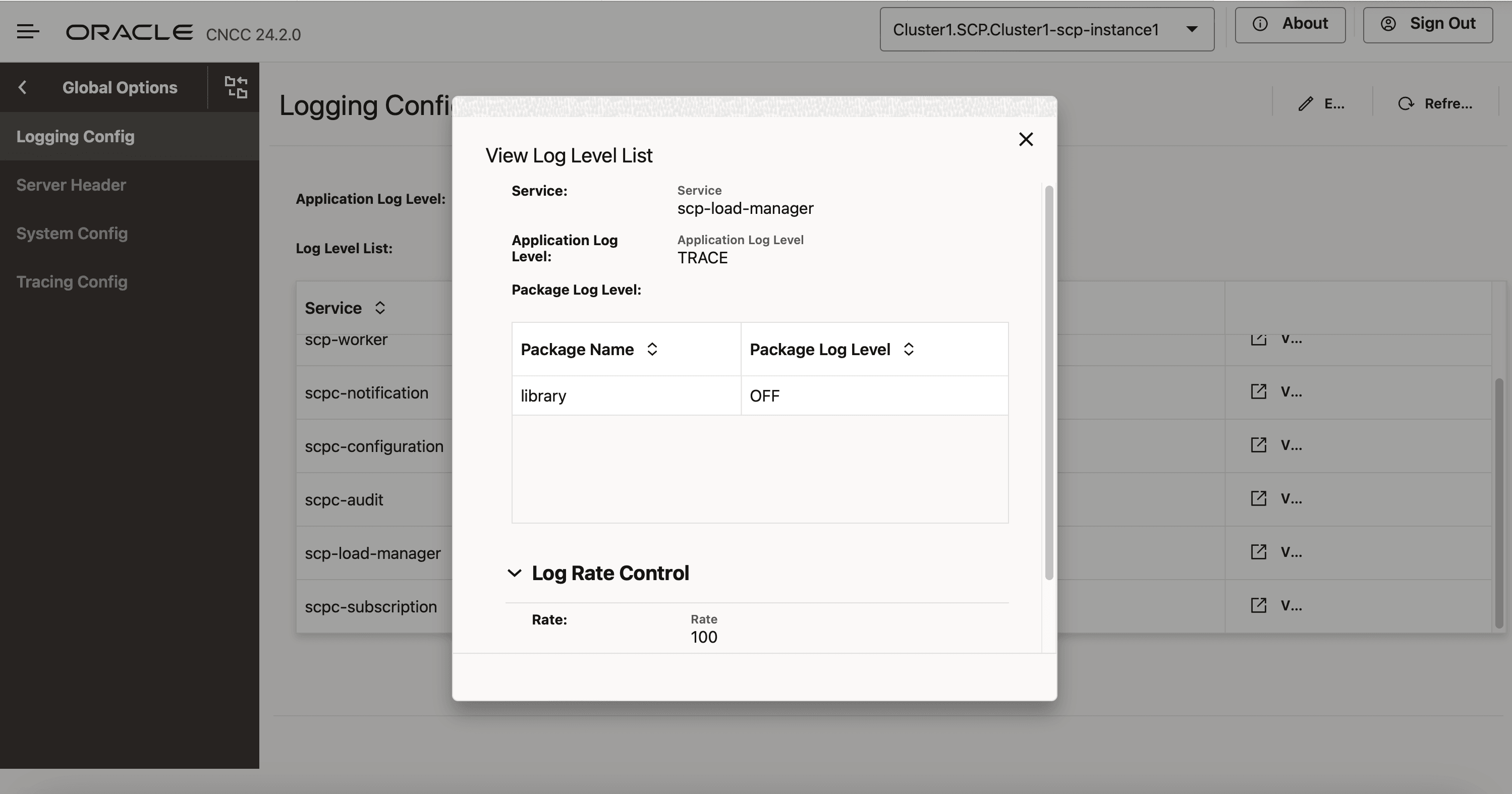
- Click Add provided under Package Log Level section to specify the name of the package and its log level.
- Click Save.
Note:
You can also Edit and Delete the packages under Package Log Level.
System Config
Perform the following procedure to edit the system config parameters.
- From the left navigation menu, navigate to SCP and select Global Options.
- Select System Config.
- Click Edit from the top right side to edit or update
System Config parameters.
Figure 4-41 System Config
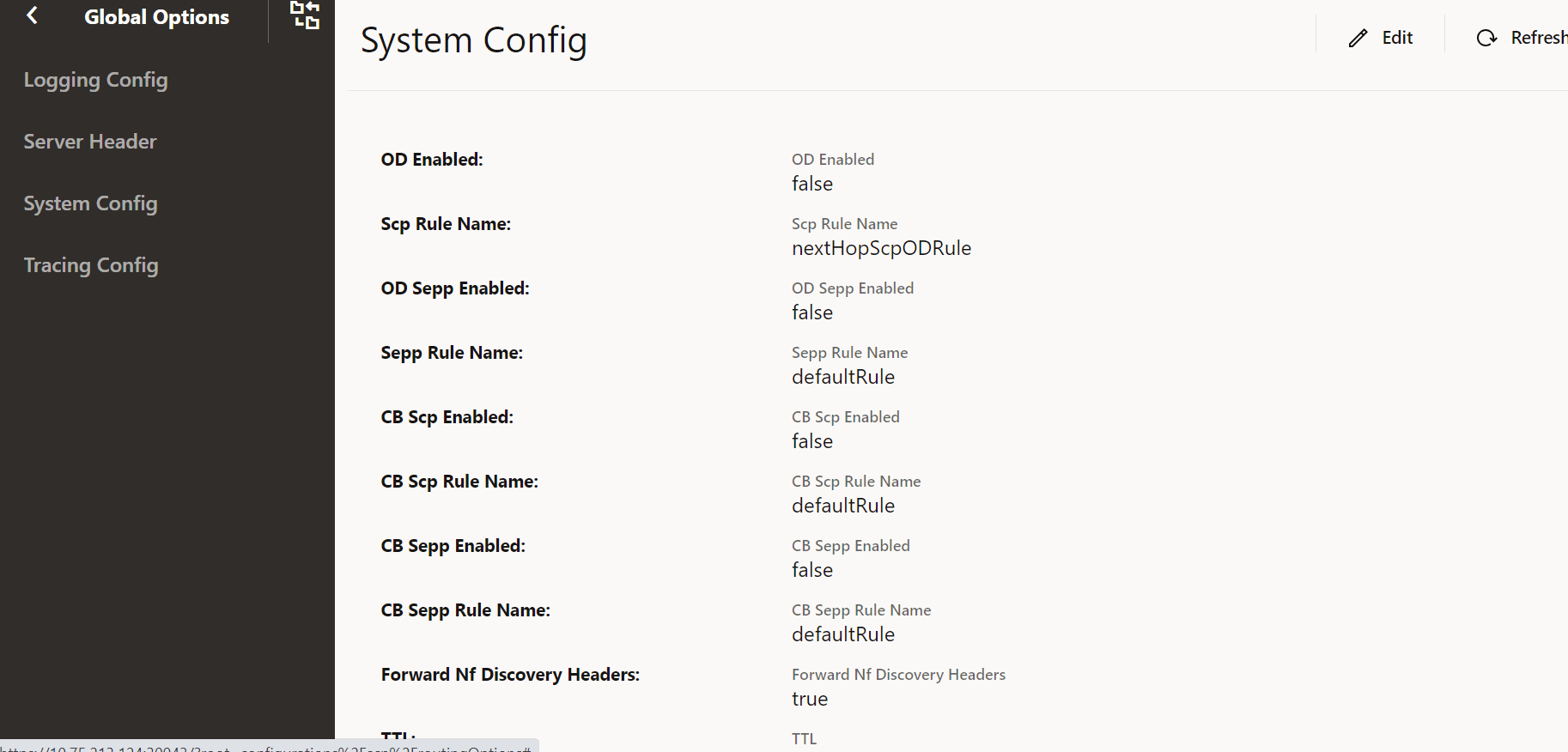
- Update the attributes as described in "Configuring
System Options" in Oracle Communications Cloud Native Core, Service Communication Proxy REST
Specification Guide.
Note:
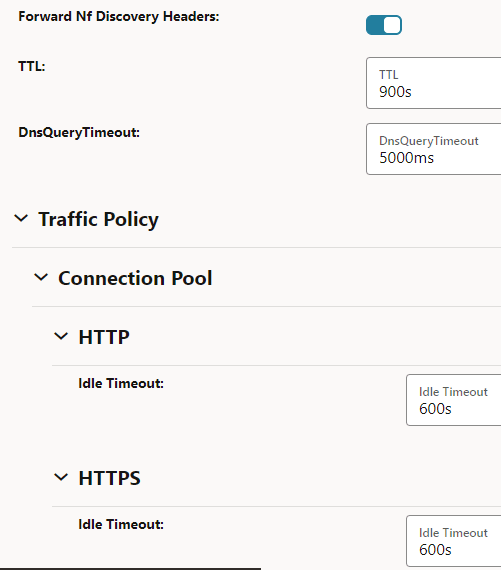
Ensure that Forward Nf Discovery Headers is set to true to forward discovery headers to Nexthop SCP as part of the Model D Indirect 5G SBI Communication feature.The default value is true.
- Click Save after performing the modifications.
Tracing Config
Perform the following procedure to edit tracing config options.
- From the left navigation menu, navigate to SCP and select Global Options.
- Select Tracing Config.
- Click Edit from the top right side to edit or update
Tracing Config options.
Figure 4-42 Tracing Config
- Set the following switches as required:
- Tracing Enabled
- Message JSON Body Enabled
For information about tracing parameters, see "Updating HELM Configurable Parameters with REST APIs" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- Click Save after performing the modifications.
4.2.12 Mediation Configuration
This section outlines procedures for setting up trigger points to define filter criteria, configuring routing options, creating mediation rules, adjusting log levels, and defining user variables.
4.2.12.1 Configuring Mediation Trigger Point
Note:
For each trigger point configuration, the combination of NfType, serviceName, httpMethods, messageType and triggerPoints methods must be unique. No new records can be added with the same combination.- From the left navigation pane, click the SCP tab, and then click the Mediation tab.
- To configure trigger points for defining the filter criteria for a message, in the left navigation pane, click the Trigger Points tab.
- In the Trigger Points section, click Add.
- In the Add Trigger Points section
and add the fields as described in the following table:
Table 4-36 Trigger Points Field Description
Field Description Group Id Enter the group ID for which the mediation configuration is required. The Mediation configuration for a specific group is applicable to the mediation requests or responses received only from the same group. The HTTP Mediation service consumer NFs, which requires the same mediation rules, can be grouped together using this group ID.
Rule Name Enter a unique rule name for each mediation configuration, which will serve as the primary key. Message Type Select whether the message is a notification or a service request. The allowed message types are svc-request-message, notification-message, or both notification-message, svc-request-message.
Service Name Select the service of NFType for which mediation configuration is required. NF Type Select the NFType for which mediation configuration is required. Http Methods Select the HTTP methods, such as GET, POST, PUT, PATCH, DELETE, and OPTIONS. Mediation Trigger Points Select trigger points to be enabled based on matches with one or more of the following: requestIngress, requestEgress, responseIngress, and responseEgress. Match Indicates the list of match blocks to be satisfied for the rule to be activated. Minimum number of blocks = 1
Maximum number of blocks = 20
Add Option to add HTTP headers, JSON body, and User Defined Variables criteria. Match Parameter Semantics- Match Blocks using OR Semantics:
The match wrapper consists of multiple match blocks, which are evaluated using OR semantics. This means that for the overall match wrapper to evaluate to
true, it is sufficient for any one match block to satisfy the conditions.For example, if the match wrapper contains three match blocks, the entire wrapper will be considered a match as long as at least one of the blocks matches the conditions.
- Internal Components of a Match Block (AND Semantics)
Each match block contains three components:
- Body: A list of match conditions for body fields.
- Headers: A list of match conditions for headers.
- userDefinedVariables (UDVs): A list of match conditions for user-defined variables.
These components are evaluated using AND semantics:- All conditions within each component (for example, all body conditions, all header conditions, and all UDV conditions) must be satisfied.
- Furthermore, all three components (body, headers, and userDefinedVariables) must match in order for the block to be considered a match.
- Match Blocks using OR Semantics:
- In the Match section, click
Add.
The Add Match dialog box appears.
- In the Header section, click
Add to set the header details as follows:
- Name: Enter a name for the header.
- Value: Enter a value of the header.
- Match Type: Select a range type from the Match Type drop-down.
- In the Body section, click
Add to set the JSON body details as follows:
- Name: Enter a name for the body.
- Value: Enter a value for the header.
- Match Type: Select a range type from the Match Type drop-down.
- In the User Defined Variables
section, click Add to set the user defined variable
details as follows:
- Name: Select the user-defined variable names from the Name drop-down.
- Value: Enter a value for the header.
- Match Type: Select a range type from the Match Type drop-down.
- In the Range section, if the header type has a numeric value, enter the range of that value in Start and End fields.
- Click Remove to discard the changes made to the Range section.
- In the Action section, select the
action type from the Action Type drop-down.
This field allows you to select the action for the trigger point rules that match the configured trigger point rules setup. The allowed values are forwardToMediationService and setTriggerPointsInvocation.
The significance of setTriggerPointInvocation is to avoid extra SCP-Worker to mediation service hop at requestIngress or requestEgress trigger points for the scenarios where response message mediation is required based on request message content.
For more information, see the "Configuring Mediation Trigger Point" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- In the Trigger Point List, select the list of
trigger points to be invoked for matching the configured trigger point rule.
For more information about the order of invocation, see the "Configuring Mediation Trigger Point" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
Note:
This is only applicable for Action Type =setTriggerPointsInvocation. Additionally, the first value in the triggerPointList should not precede the first value in the parent triggerPoints.Example (not allowed)
triggerPoints: ["requestEgress"], "action": { "actionType": "setTriggerPointsInvocation", "triggerPointList": [ "requestIngress" ] }In this example,
"requestIngress"is listed after"requestEgress", which violates the rule that the first trigger point in thetriggerPointListshould not occur before the first trigger point in the parenttriggerPoints. - In the Trigger Points section,
click Edit and configure the fields as required.
Figure 4-43 Edit Mediation Trigger Points
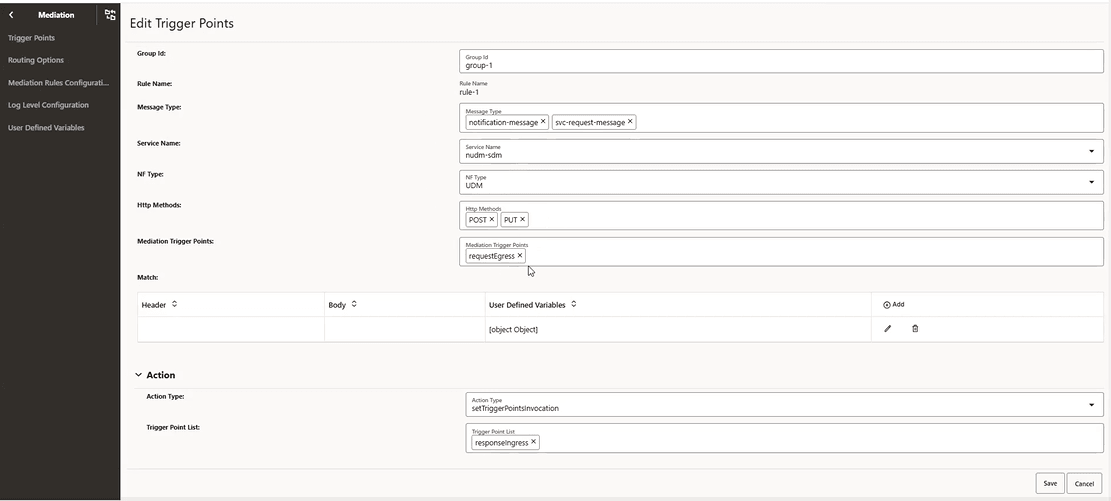
- Click Save to save the changes.
- Click Cancel to reset all the fields.
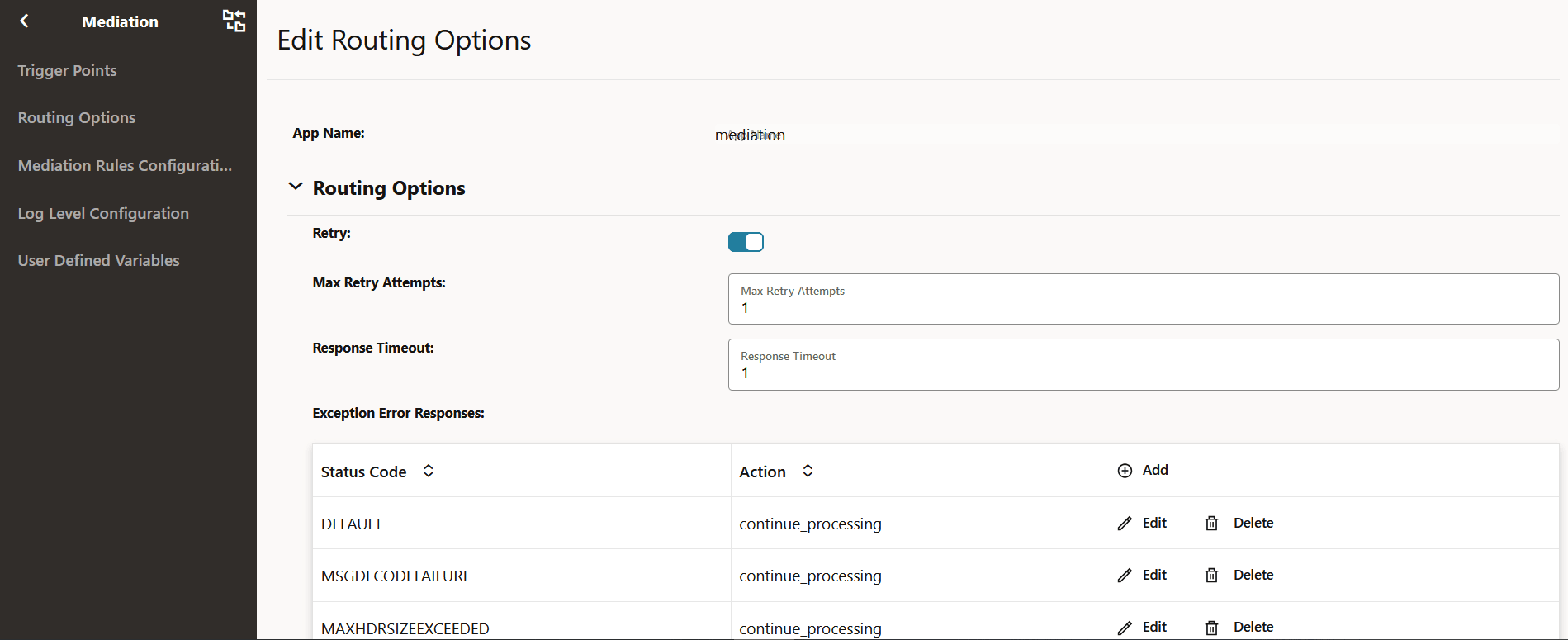
4.2.12.2 Configuring Routing Options for Mediation
4.2.12.4 Configuring Mediation Log Levels
- From the left navigation pane, click the SCP tab, and then click the Mediation tab.
- On Mediation tab, click the
Log Level Configuration subtab.
The Log Level Configuration screen with a list of default log level type of mediation and mediation-test service assigned during deployment appears.
- Click the View icon to view the log level of mediation or mediation test service.
- Click the Edit icon to edit or update the log level of
mediation or mediation test service.
The Edit Log Level Configuration screen allows you to configure the fields as described in the following table:
Table 4-40 Edit Log Level Configuration
Field Description Service Type Indicates the name of the type of service. For examples, mediation and mediation-test Application Log Level Indicates the type of log level. The following are the supported log levels:- WARN: Designates potentially harmful situations.
- INFO: Designates informational messages that highlight the progress of the application at coarse-grained level.
- ERROR: Designates error events that might still allow the application to continue running.
- DEBUG: Designates fine-grained
informational events that are most useful to debug
an application.
The default value is WARN.
Package Log Level Indicates the package level log information.
Log Rate Control Indicates the log rate control information. - Select the application log level from the Application Log Level drop-down list to collect the logs as per the requirement.
- Click Save to update the log level of service.
Package Log level Configuration
- On the Package Log level section, click the
EDIT icon next to the package name.
The Edit Package Log Level screen allows you to configure the fields as described in the following table:
Table 4-41 Edit Package Log Level
Field Description Package Name Indicates the name of the package. It should be a valid library name. - The valid package names are org, io, springfox, com.zaxxer, reactor, validator, and library.
- The default package name is library.
Package Log Level Indicates the type of package log level. The following are the supported log levels:- WARN: Designates potentially harmful situations.
- INFO: Designates informational messages that highlight the progress of the application at a coarse-grained level.
- ERROR: Designates error events that might still allow the application to continue running.
- DEBUG: Designates fine-grained informational events that are most useful to debug an application
- OFF: Disables the log rate.
The default value is OFF
- Edit the package name and Package Log Level from the drop-down menu and click Save.
Log Rate Control Configuration
- The Log Rate Control section allows you to configure
the fields as described in the following table:
Table 4-42 Log Rate Control
Field Description Rate Indicates the average number of logs allowed per second. - The default rate is 1.
- The range is in between 1 and 10000
Log Level Indicates the type of log level where rate control is applied. The following are the supported log levels:
- WARN: Designates potentially harmful situations.
- INFO: Designates informational messages that highlight the progress of the application at a coarse-grained level.
- ERROR: Designates error events that might still allow the application to continue running.
- DEBUG: Designates fine-grained informational events that are most useful to debug an application
- OFF: Designates to turn off logging.
The default value is OFF
- Select the log level from the Log Level drop-down to change the log level type, and click Save.
4.2.12.5 Configuring Mediation Support for User Defined Variables
- From the left navigation pane, click the SCP tab, and then click the Mediation tab.
- On Mediation tab,
click the User Defined Variables
subtab.
The User Defined Variables screen displays a list of user-defined variables saved in the database. A user-defined variable can be edited, deleted, or viewed.
Figure 4-46 User Defined Variables Configuration
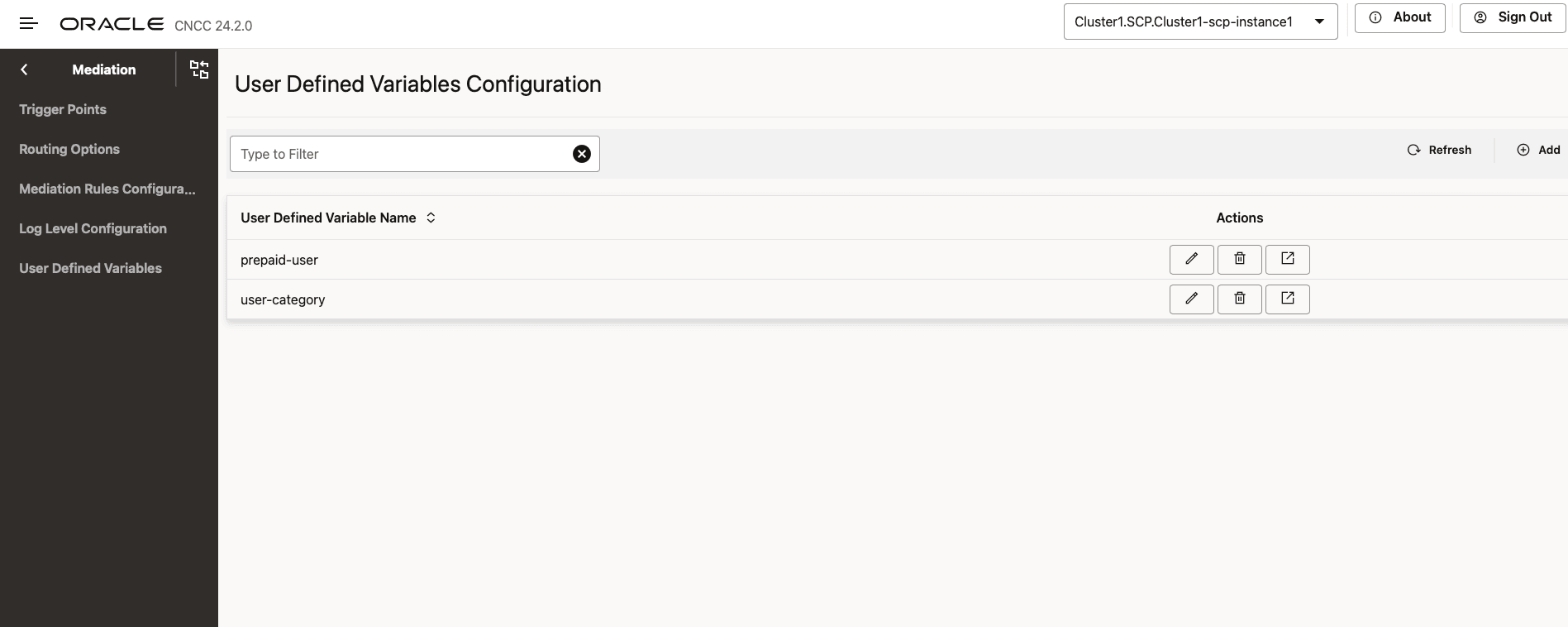
- Click the View icon to view the configured user-defined variable.
- Click the Add to create a
user-defined variable.
The Add User Defined Variable screen allows you to configure the fields to create user defined variables to configure rules as described in the following table:
Table 4-43 Add User Defined Variable
Field Description User Defined Variable Name This field is used to specify the name of the user-defined variable. Ensure the name is unique. Data This section allows to define and configure user-defined variable data-related settings. Type This field is used to specify the data type (for example, STRING, LONG, JSON, BOOLEAN). Size This field is used to define the size limit for the user-defined variable data. This field is conditional and required only when the type is STRING or JSON. The allowed size range is between 1 and 1024 bytes only.
Description This field is used to provide a brief explanation for the data being defined. Note:
Ensure that no special characters are used. - Click the Edit icon to edit
the configured user-defined variable.
The Edit User Defined Variable screen allows you to configure the fields as described in the following table:
Table 4-44 Edit User Defined Variable
Field Description User Defined Variable Name This field specifies the name of the user-defined variable. Note: The name of the user-defined variable cannot be edited.
Data This section allows users to define and configure user-defined variable data-related settings. Type This field specifies the data type (for example, STRING, LONG, JSON, BOOLEAN). Size This field is used to define the size limit for the data. This field is conditional and required only when the type is STRING or JSON. The allowed size range is between 1 and 1024 bytes only.
Description This field provides a brief explanation for the data being defined. Note:
If a user-defined variable is APPLIED in any rules or configured at trigger points, it cannot be deleted. In this case, the only editable field is the size, which can only be incremented. - Click Save to update
changes.
Users can use these user-defined variables in SCP trigger points and mediation rules.
4.2.13 Configuring NF Rule Profile
Note:
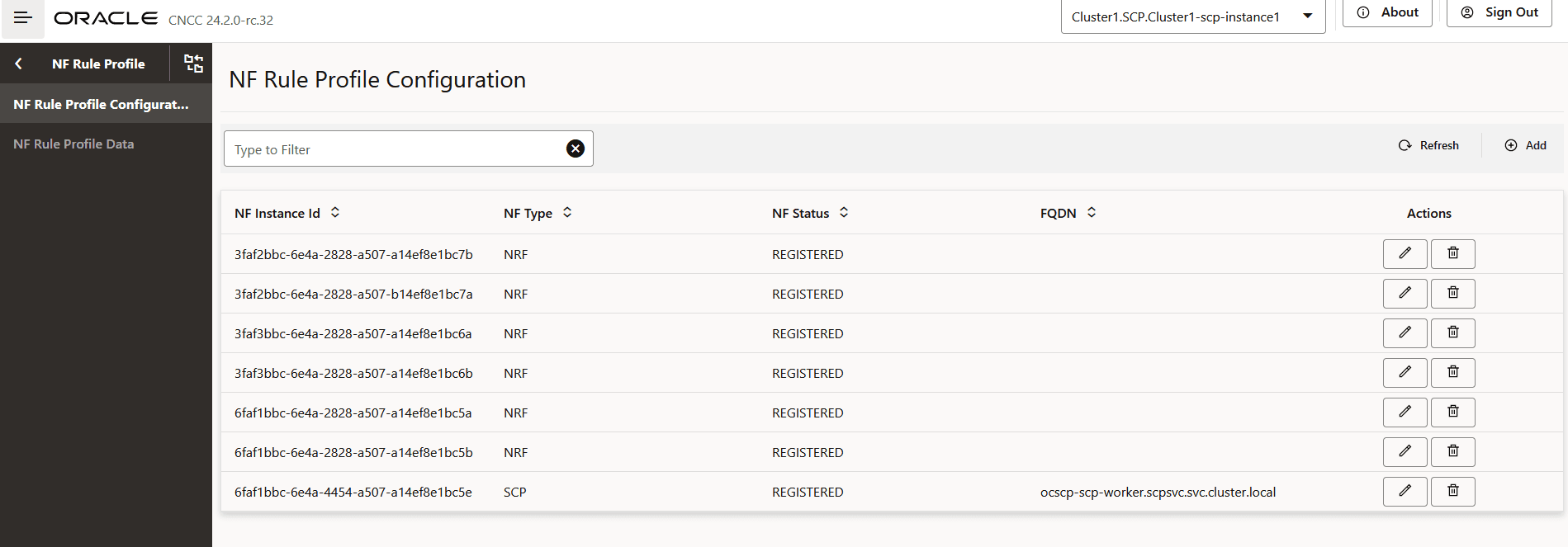
When the learning source is set to "Local", users can modify the 5G NF profile regardless of whether it was learned from NRF (source='NRF') or configured statically (source='Local'). By setting the source to Local, the system does not delete already determined profiles.- From the left navigation, navigate to SCP, and then click NF Rule Profile.
- To add or configure an NF rule profile, click the NF
Rule Profile Configuration tab in the left navigation
pane.
Figure 4-47 NF Rule Profile Configuration
- Click Add to add NF rule profile.
Figure 4-48 Add NF Rule Profile
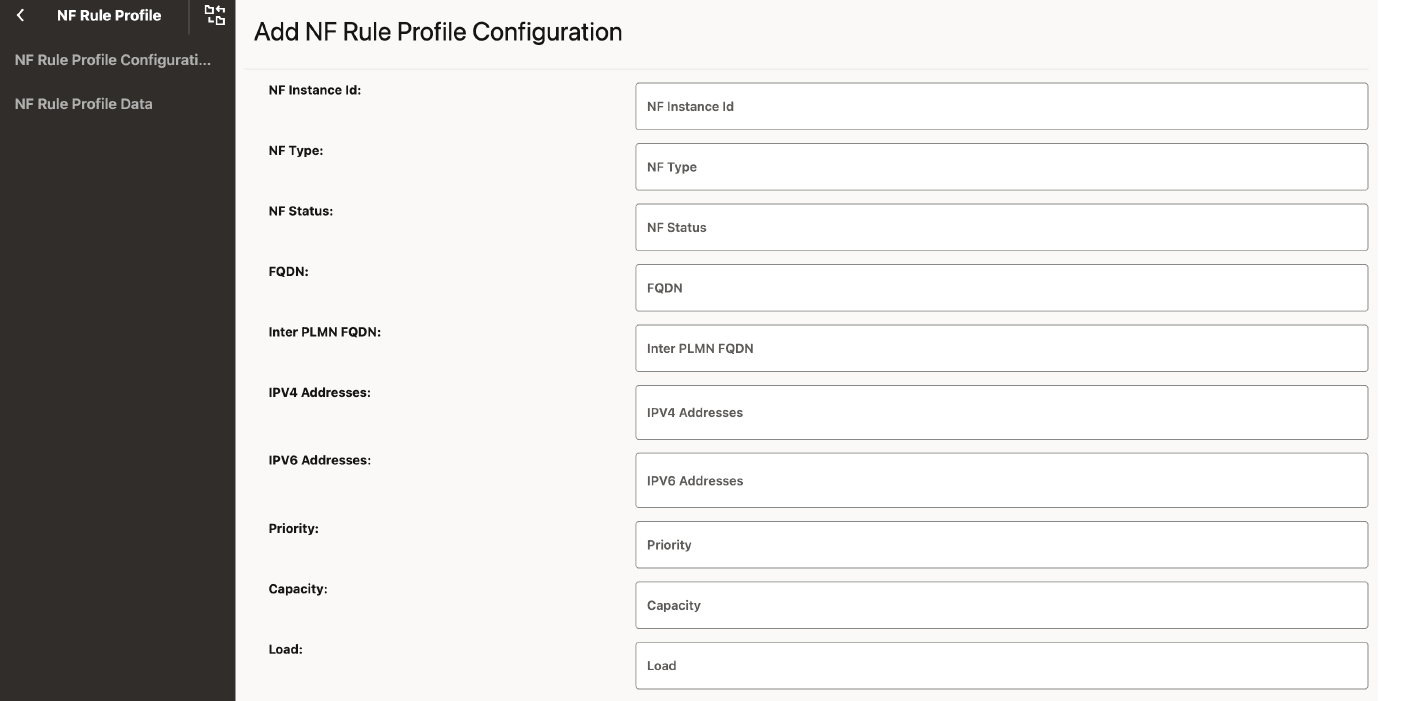
- Add the following parameters for all the NF Info:
- Group Id: Identity of the NF info.
- Routing Indicators: List of Routing Indicator information.
- Click Add to add the SUPI Ranges.
- Click Save to save the SUPI Ranges.
- Click Remove if you want to remove the NF Info.
- Click Add to add the NF info details.
- Click Save to save the NF Rule Info.
- Click Refresh to view the updated values on the screen.
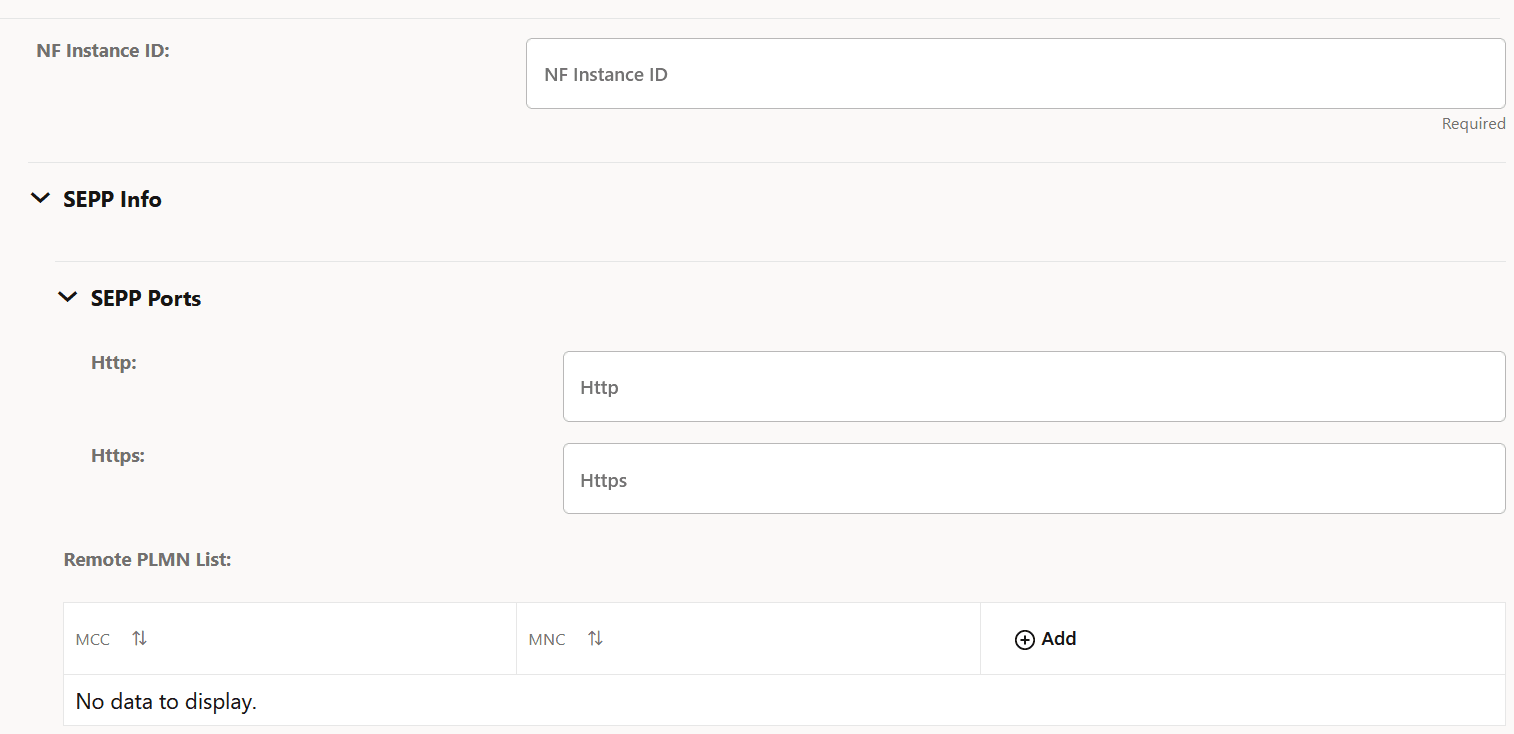
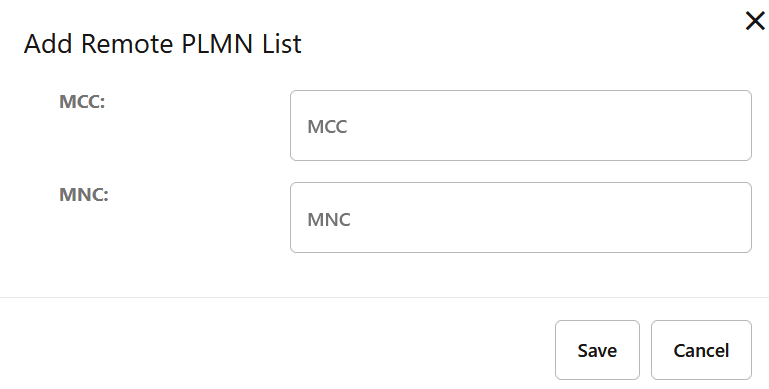
- To configure a local PLMN, in the PLMN List section, click Add and enter the required Mobile Country Code (MCC) and Mobile Network Code (MNC) values in the displayed fields.
Perform the following procedure to edit the IP addresses which are present under NF service level:
- In the NF Service section, to modify any NF service, click the corresponding Edit icon.
- In the IP End Points
section, click Add to add IP end points.
Figure 4-49 Adding IP End Points
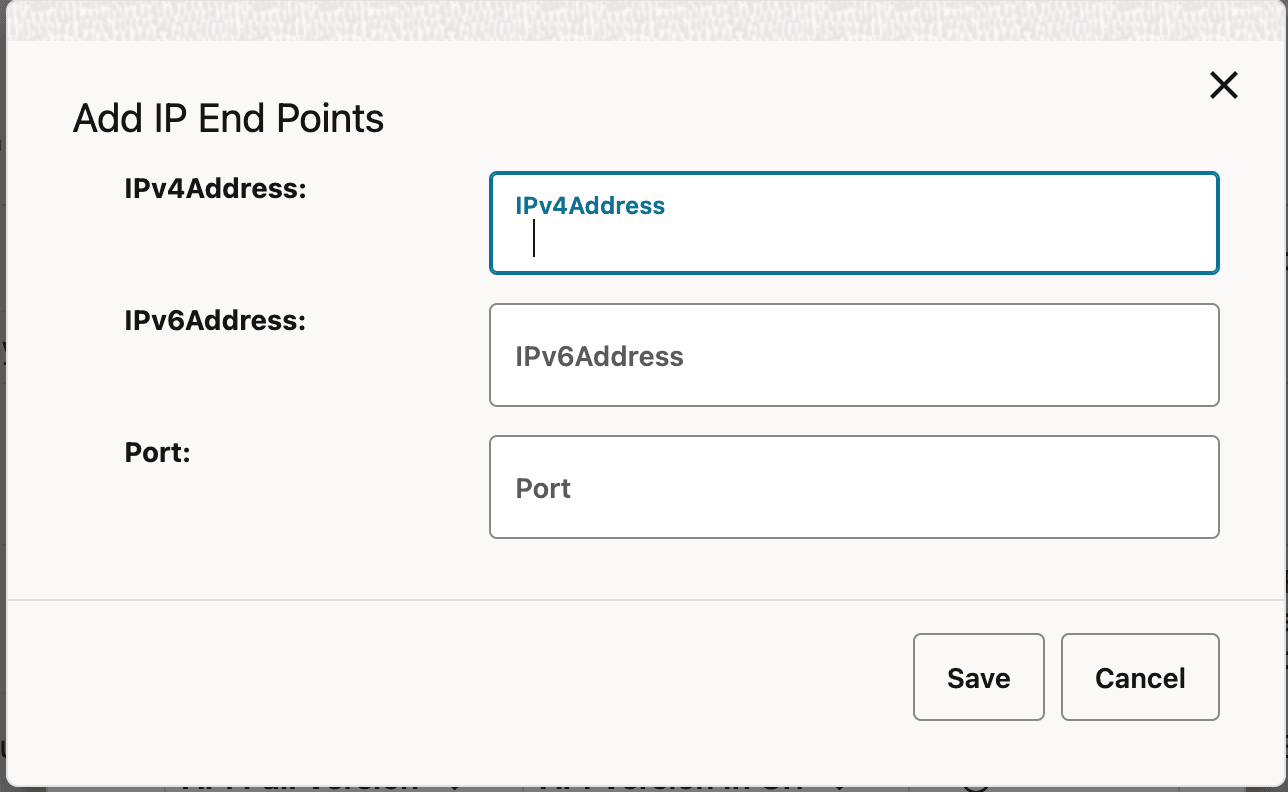
- Enter IP address in one of the following fields:
- IPv4Address
- IPv6Address
Note:
The system displays an error message if you enter IP address in both the above mentioned fields.For more information about IPv4Address and IPv6Address configurations, see "Configuring Route Groups" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- In the Port field, enter the port number.
- Click the Edit icon to edit or add
the API full versions.
Figure 4-50 Edit NF Services
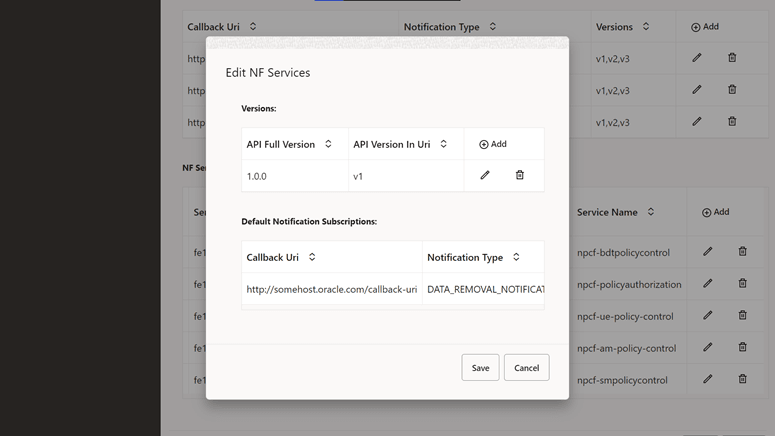
- Click Save to save the NF Rule Info.
Note:
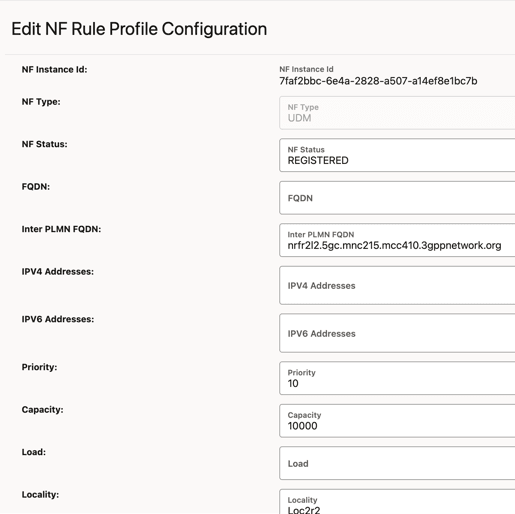
Users cannot modify values for profiles in Default Notification Subscription if the learning source is set to NRF. They can only view it. Editing is only possible when the learning source is set to "Local".- In the NF Rule Profile Configuration section, click
Edit from Actions. The Edit NF Rule
Profile Configuration screen appears.
Figure 4-51 Edit NF Rule Profile Configuration
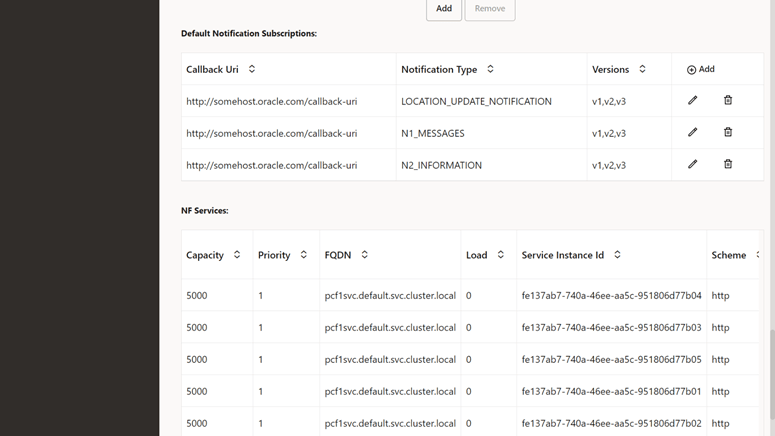
- In the Default Notification
Subscription section, click the Edit
icon for the required callback URI that must be modified. The
Edit Default Notification Subscription screen
appears.
Figure 4-52 Default Notification Subscription
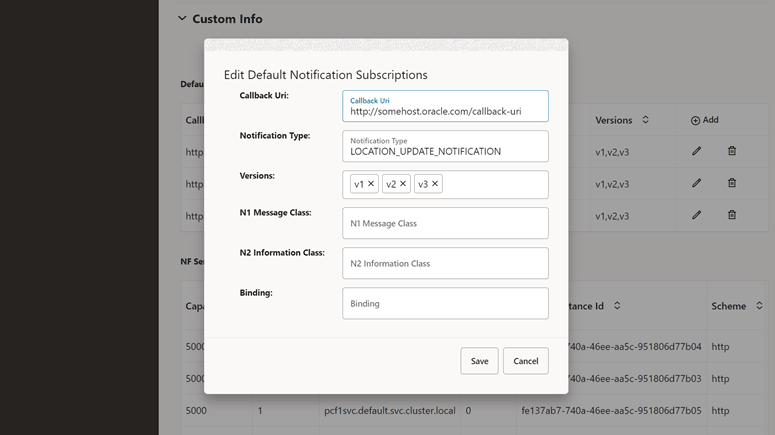
- Make the required modifications for the following fields:
Table 4-45 Default Notification Subscriptions
Attribute name Description Callback Uri This attribute contains a default notification endpoint to be used by a NF service producer towards an NF service consumer that has not explicitly registered a callback URI with the NF service producer, for example, as a result of an implicit subscription. Notification Type Type of notification for which the corresponding callback URI is provided. Versions API versions, for example, v1, are supported for the default notification type. N1 Message Class If the notification type is N1_MESSAGES, this IE must be present to identify the class of N1 messages to be notified. N2 Information Class If the notification type is N2_INFORMATION, this IE must be present to identify the class of N2 information to be notified. Binding When present, this IE contains the value of the binding indication for the default subscription notification, which is the value part of the 3gpp-Sbi-Binding header. See the note for details. Note:
When delivering a notification for a default subscription to a specific NF consumer but the latter is not reachable, a NF service producer uses the binding indication for default subscription to reselect an alternative NF service consumer instance. For example, an AMF notifies corresponding uplink LPP or NRPPa messages through a default subscription to the LMF instance that previously sent downlink LPP or NRPPa messages during a location procedure. If the original LMF instance is not reachable, the AMF selects an alternative LMF instance using the binding indication and delivers the notification to the selected LMF instance.Figure 4-53 Edit Default Notification Subscriptions
- Click Save to save the NF Rule Info.
- Click Refresh to view the updated values on the screen.
4.2.13.1 Fetching NF Rule Profile Data
- From the left navigation menu, navigate to SCP and then click NF Rule Profile.
- To retrieve the default notification subscription data for a specific NF rule profile, click on the NF Rule Profile Data tab in the left navigation pane.
- The NF Rule Profile Data screen is displayed as follows:
Figure 4-54 NF Rule Profile Data
- Enter the Query Parameters in the field. These parameters may include NFType, ServiceName, NF instance ID, Maximum number of NF profiles (limit), or max-payload-size. For more information, see the "Configuring NF Topology Groups" section in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- Click Get to fetch the response data. The data is displayed
in the Response pane.
Figure 4-55 Response data
- Click Clear to clear the response data.
4.2.14 Configuring SCP Profile
Editing SCP Profile
- From the left navigation menu, navigate to
SCP and then select SCP Profile.
Figure 4-56 SCP Profile
- Click Edit under NF
Services section. The Edit SCP Profile
Screen appears. For more information about configuration parameters, see
Oracle Communications Cloud Native Core, Service Communication Proxy REST
Specification Guide.
Note:
- To add a new location to Remaining Localities and Serving Localities, type the new location name, and then click Enter.
- Use Edit or Delete buttons available in the next column to update or delete the NF services.
4.2.15 Configuring Topology Source Info
- From the left navigation menu,
navigate to SCP and then select Topology Source
Info.
Figure 4-57 Topology Source Info
- Click Edit from the Actions column for the required service that must be modified. The Edit Topology Source Info Screen appears.
- Update the Status of the
specific NF Type in the Edit Topology Source Info as per your
requirement.
Figure 4-58 Edit Topology Source Info
- Click Save to save the Topology Source Info.
- Click Refresh to view the updated values on the screen.
4.2.16 Fetching Routing Rules
- From the left navigation menu, navigate to SCP and then select Reports.
- Select Routing Rules R16. The Routing Rules R16 screen
is displayed as follows:
Figure 4-59 Routing Rules R16
- Enter the Query Parameters in the field.
- Click Get to fetch the response data. The data is displayed
in the Response pane.
Figure 4-60 Response data
Note:
In case the response data is above the configured display limit, a message is displayed stating "Response data has crossed the configured display limit (5 MB), please click on Export to download it as a file.". Currently, the display limit cannot be modified, it is set to 5 MB. - Click Export to download of the response data file.
- Click Clear to clear the response data.
4.2.17 Configuring Ingress Rate Limiting
- From the left navigation menu, navigate to SCP and then select Rate Limiting.
- Select Ingress Rate Limiting. The screen is displayed.
Figure 4-61 Ingress Rate Limiting
- Enter the Query Parameters in the field.
- Click Get to fetch the response data. The data is displayed
in the Response pane.
Note:
In case the response data is above the configured display limit, a message is displayed stating "Response data has crossed the configured display limit (5 MB), please click on Export to download it as a file.". Currently, the display limit cannot be modified, it is set to 5 MB. - Click Add to add the ingress rate limiting configuration using the Request Body.
- Click Edit to edit the Request Body of the ingress rate limiting configuration.
- Click Delete to delete the ingress rate limiting configuration based on the query parameters.
4.2.18 Configuring Egress Rate Limiting
- From the left navigation menu, navigate to SCP and then select Rate Limiting.
- Select Egress Rate Limiting. The screen is displayed.
Figure 4-62 Egress Rate Limiting
- Enter the Query Parameters in the field.
- Click Get to fetch the response data. The data is displayed
in the Response pane.
Note:
In case the response data is above the configured display limit, a message is displayed stating "Response data has crossed the configured display limit (5 MB), please click on Export to download it as a file.". Currently, the display limit cannot be modified, it is set to 5 MB. - Click Add to add the egress rate limiting configuration using the Request Body.
- Click Edit to edit the Request Body of the egress rate limiting configuration.
- Click Delete to delete the egress rate limiting configuration based on the query parameters.
4.2.19 Configuring Server Header
4.2.20 Configuring Pod Overload Control Policies
For more information about pod overload policies, see Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- From the left navigation pane, navigate to SCP and click Pod Overload Control, and then click Worker.
- To configure Pod Overload Control Policy, in the left navigation pane, click
the Overload Control Policy tab.
- To configure Pod Overload Action Policy, in the left navigation pane, click the
Overload Action Policy tab.
- To configure Pod Overload Discard Policy, in the left navigation pane, click
the Overload Discard Policy tab.
4.2.21 Configuring SBI Message Priority
For more information about SBI Message Priority parameters, see Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
4.2.22 Configuring DNS SRV based Alternate Routing
You must log in to the CNC Console while performing the procedures described in the subsequent subsections. Using these procedures, you can perform the followings tasks:
- Set the routing mode.
- Configure the default Time To Live (TTL) value.
- Refresh the DNS SRV records in DB.
- Add and fetch DNS SRV records from DB.
4.2.22.1 Configuring Routing Modes
4.2.22.2 Configuring the Default TTL Value
4.2.23 Configuring SBI Message Priority and Error Profiles for Egress Congestion Control
4.2.24 Configuring the nextHopSCP Routing Option
4.2.25 Configuring SEPP Inter PLMN Routing
4.2.26 Configuring Route Groups
4.2.27 Configuring Ingress Rate Limiter Consumer Info
Perform the following procedure to configure consumer information for ingress rate limiting.
4.2.28 Configuring SCP Services
- From the left navigation pane, click the SCP tab, and then click the SCP Service Configuration tab.
- In the left navigation pane, click the SCPC-AlternateResolution tab and do the following:
- In the SCPC-AlternateResolution Service Configuration section, expand the SCP Service Configuration option.
- To view the Thread Watchdog configuration values, expand the Thread Watchdog Configuration option.
- To view the Connectivity Watchdog configuration values, expand the Connectivity Watchdog Configuration option.
- In the left navigation pane, click the SCPC-Audit tab and do the following:
- In the SCPC-Audit Service Configuration section, expand the SCP Service Configuration option.
- To view the Thread Watchdog configuration values, expand the Thread Watchdog Configuration option.
- To view the Connectivity Watchdog configuration values, expand the Connectivity Watchdog Configuration option.
- In the left navigation pane, click the SCPC-Configuration tab and do the following:
- In the SCPC-Configuration Service Configuration section, expand the SCP Service Configuration option.
- To view the Thread Watchdog configuration values, expand the Thread Watchdog Configuration option.
- To view the Connectivity Watchdog configuration values, expand the Connectivity Watchdog Configuration option.
- In the left navigation pane, click the SCPC-Configuration tab and do the following:
- In the SCPC-Configuration Service Configuration section, expand the SCP Service Configuration option.
- To view the Thread Watchdog configuration values, expand the Thread Watchdog Configuration option.
- To view the Connectivity Watchdog configuration values, expand the Connectivity Watchdog Configuration option.
- In the left navigation pane, click the SCPC-Notification tab and do the following:
- In the left navigation pane, click the SCPC-Subscription tab and do the following:
- In the SCPC-Subscription Service Configuration section, expand the SCP Service Configuration option.
- To view the Thread Watchdog configuration values, expand the Thread Watchdog Configuration option.
- To view the Connectivity Watchdog configuration values, expand the Connectivity Watchdog Configuration option.
- In the left navigation pane, click the SCP-NrfProxy tab and do the following:
- In the left navigation pane, click the SCP-Worker tab and do the following:
4.2.29 Configuring Outlier Detection
4.2.30 Configuring Traffic Feed
- From the left navigation pane, click the SCP tab, and then click the Traffic Feed tab.
- To configure OCNADD fields, in the left navigation pane, click the Data Director tab.
- In the Traffic Feed Data Director Configuration section, click Edit and configure the fields as described in the "Configuring Traffic Feed Data Director" section of the Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- To configure Trigger Points, in the left navigation pane, click the Trigger Points tab.
- In the Trigger Points section, click Add and configure the fields as described in the "Configuring Traffic Feed Trigger Point Config" section of the Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- Click Save.
4.2.31 Congestion Control Configurations
- From the left navigation menu, navigate to SCP and then select Congestion Control.
- Click Edit icon from the
Actions column for the required service that must be modified.
The Edit Congestion Control screen appears.
Note:
The default rule name cannot be deleted. The new rule name can be added, modified, or deleted.Figure 4-79 Congestion Control
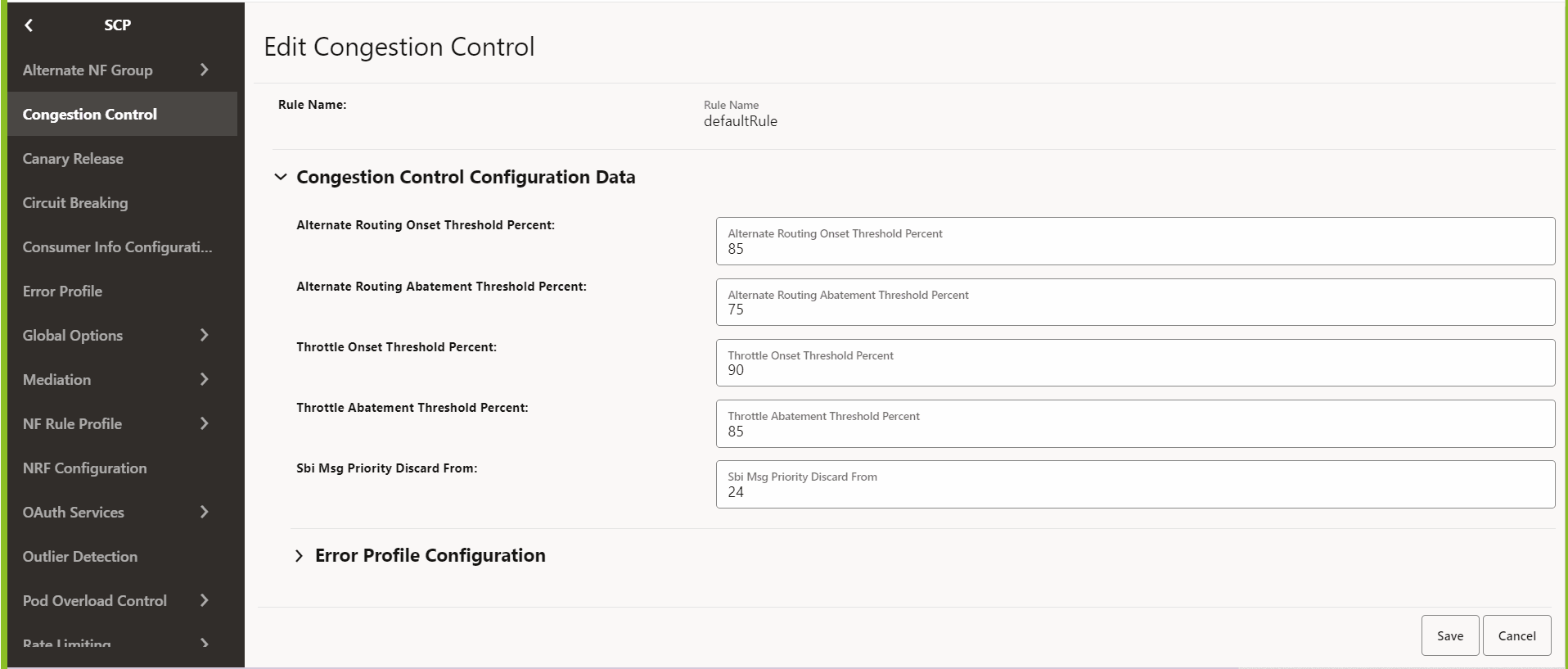
- Make the required modifications for the following parameters:
- Alternate Routing Onset Threshold Percent: Set the threshold percentage for onset alternate routing.
- Alternate Routing Abatement Threshold Percent: Set the threshold percentage for alternate routing abatement.
- Throttle Onset Threshold Percent: Set the threshold percentage for onset throttling.
- Throttle Abatement Threshold Percent: Set the threshold percentage for throttle abatement.
- SBI Msg Priority Discard From: Set the priority
for message, after which the messages can be discarded. For example,
if the value is 30, then messages with priority 0-29 are high
priority, and other low-priority messages will be throttled.
Note:
All the parameters are mandatory.
- Click Save.
- Click Cancel to reset all the fields.
- Click Delete from the Actions column to delete the record.
4.2.32 Configuring Routing Options
Perform the following procedure to configure routing options.
- From the left navigation menu, navigate to SCP, and then click the Routing Options tab.
- From the left navigation menu, click the Routing Options Config tab.
- In the Routing Options Config section, perform one of the
following steps:
- To configure a new routing option, click
Add and configure the following fields:
Table 4-57 Field Name
Field Name Description Config Name Unique configuration name to identify the records. Number of characters is 256. Allowed character combinations should be alpha-numeric, hyphen, and underscore.
Message Type List of types of messages, such as notifications and SBI-messages, for which the routing configurations will apply. Notification Type Indicates the notification type. NF Type The NF type of the producer NF or server for which routing options are configured. This is either 3GPP defined NFType as per TS 29.510 or custom NFType. NF Service Name The NF service name of producer NF or server for which routing options are configured. This is either 3GPP defined serviceName as per TS29.510 or any custom service name.
Method Indicates the method type. If no value is provided, '*' is configured in this field. This indicates that SCP-Worker will match any method type from following list: - GET
- PUT
- POST
- PATCH
- OPTIONS
- TRACE
- HEAD
- CONNECT
- DELETE
Note: Both Method and API Specific Resource Uri should be configured for service operation specific configurations.
API Specific Resource Uri REGEX expression which is used to validate resource URI in the RX request. Note: Both Method and API Specific Resource Uri should be configured for service operation specific configurations.
Consumer NFType Configures consumer NFType, for example, client or sender. It decides routing options based on the consumer NFType that sends the message to SCP for routing. In the current implementation, this field supports "*" as value, which means match all.
Routing Config Set Name Name of the Routing Config set record. For more information, see "Configuring Routing Options Config" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide. Created Timestamp Indicates the timestamp of the created record. This is not required in the request, but it is present in the response. Updated Timestamp Indicates the timestamp of the updated record. This is not required in the request, but it is present in the response. For more information about the above mentioned fields, see "Configuring Routing Options Config" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- To edit or remove any existing routing option configurations, select an existing routing options instance from the Config Name column, and click the corresponding Edit or Delete icon.
- To configure a new routing option, click
Add and configure the following fields:
- Click Save.
- To retrieve the query parameters, from the left navigation pane, click the Routing Options Config Query tab.
- In the Query Parameters field, enter the query parameter,
such as nftype=UDM, and click Get.
Response and request configuration information appears in Response and Request fields.
4.2.33 Configuring Routing Config Set
- From the left navigation menu, navigate to SCP, and then click the Routing Options tab.
- From the left navigation menu, click the Routing Config Set tab.
- In the Routing Config Set section, click Edit from the Actions column for the required service that must be modified.
- Enter or modify the required values as described in "Configuring Routing Config Set" and "Configuring Routing Options Config" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- In the Reroute Condition
List, configure the list of error codes for rerouting:
- Click Add to add new status code.
- Click Edit or Delete icon to edit or remove any existing error code from the reroute condition list.
- Click Save.
- Click Cancel to reset all the fields.
4.2.34 Configuring NFTypes-NFServices
4.2.35 Configuring NF Service Feature Config
4.2.36 Configuring NF Service Feature Config Set
4.2.37 Circuit Breaking Configurations
- From the left navigation menu, navigate to SCP, and then click the Circuit Breaking tab.
- In the Circuit Breaking section, click Edit
icon from the Actions column for the
required service that must be modified.
The Edit Circuit Breaking screen appears.
Figure 4-80 Edit Circuit Breaking
- In the HTTP2 Max Requests field, set the maximum number of requests SCP routes to an NF service instance (peer destination) and waiting for their responses before stopping further routing requests to it. The maximum allowed value is 1000.
- Enter or modify the required values as described in "Circuit Breaking Configurations" in Oracle Communications Cloud Native Core, Service Communication Proxy REST Specification Guide.
- Click Save.
- Click Cancel to reset the field.
4.2.38 Viewing SCP Feature Status
Perform the following procedure to fetch the runtime status of NRF migration task.
- From the left navigation pane, click the SCP tab, and then click the SCP Feature Status tab.
- On the SCP Feature Status page, the following
columns display the SCP feature status.
Table 4-60 SCP Feature Status
Column Name Description Feature Name Displays the names of the features, such as nrf_bootstrap_info. Admin State Displays the admin state of the feature. Possible statuses are mentioned below: - ENABLED: This indicates that the user has enabled the feature.
- DISABLED: This indicates that the user has disabled the feature.
Runtime Status Displays the current runtime status of the feature. Possible statuses are mentioned below: - DISABLED: This indicates that the feature is
disabled.
For example, in the nrf_bootstrap_info feature, this state means SCP is running with a statically configured NRF. If the user has changed the 'Admin State' from ENABLED to DISABLED, this state means the feature is successfully disabled.
- IN_PROGRESS: This indicates the enabling or disabling of
the feature is currently is in progress when the 'Admin
State' is set to ENABLED or DISABLED.
For example, in the nrf_bootstrap_info feature, when the 'Admin State' is ENABLED, the migration from static to DNS SRV based NRF topology is in progress. In the nrf_bootstrap_info feature, when the 'Admin State' is DISABLED, the migration from a DNS SRV based NRF topology to static NRF topology is in progress.
- FAILED_RETRY: This indicates that the process of
enabling or disabling the feature (as indicated by the
'Admin State') has encountered failure and is undergoing
retries.
For example, in the nrf_bootstrap_info feature, this state means either of the migration tasks has failed and going through retries.
- ENABLED: This indicates the feature is successfully
enabled.
For example, in the nrf_bootstrap_info feature, this state means the migration from static to a DNS SRV based NRF topology is successful.
Creation Timestamp Displays the time of creation of the event, for example, creationTimestamp": "2021-05-26T01:17:15.000+00:00 Update Timestamp Displays the time of updation of the event, for example, creationTimestamp": "2021-05-26T06:24:15.000+00:00
4.2.39 Get NF Discovery Response Cache Configuration Data
- Log in to the CNC Console using your login credentials as described in Oracle Communications Cloud Native Core, Service Communication Proxy User Guide.
- On the CNC Console Home page, in the upper pane, select the required SCP instance from the Please Select Instance drop-down list.
- From the left navigation pane, click the SCP tab, and
then click the NF Discovery Response Cache Configuration
tab. The SCP Features section displays the list of two subtabs to be configured
using the CNC Console:
- NF Discovery Response Cache Configuration
- NF Discovery Response Cache Configuration Data
- In the NF Discovery Response Cache Configuration Data
subtab, click Get to retrieve NF discovery cache
configuration data based on the query parameters.
Figure 4-81 NF Discovery Response Cache Configuration Data
Table 4-61 Button and Field Description
Button and Field Names Description Get Retrieves NF discovery response cache configuration data. You can modify this data using the Edit button.
Clear Refreshes the existing screen by removing the data.
4.2.40 Configuring NF Profile Level Attribute
4.2.41 Configuring NF Profile Level Attribute Configuration Data
4.2.42 Configuring NF Delegated Discovery Response Cache
- Log in to the CNC Console using your login credentials as described in Oracle Communications Cloud Native Core, Service Communication Proxy User Guide.
- On the CNC Console Home page, in the upper pane, select the required SCP instance from the Please Select Instance drop-down list.
- From the left navigation pane, click the SCP tab, and
then click the NF Discovery Response Cache Configuration
tab. The SCP Features section displays the list of two subtabs to be configured
using the CNC Console:
- NF Discovery Response Cache Configuration
- NF Discovery Response Cache Configuration Data
- From the left navigation pane, click the NF Discovery Response Cache Configuration subtab.
- The NF Discovery Response Cache Configuration screen
displays a list of rules saved in database.
Figure 4-82 NF Discovery Response Cache Configuration
- Click Add to create NF discovery response
cache configuration rule.
The Add NF Discovery Response Cache Configuration Rule screen allows you to configure the fields to create new rule as described in the following table:
Table 4-64 Field Description
Field Names Description Rule Name Indicates the name of the rule. This value should be unique. Target NF Type Indicates the NF type of producer for which delegated discovery is being made. The allowed values for this field are:- * : This value denotes all the
valid NF types.
or
- a valid NF type that SCP supports.
Service Names Indicates the list of service names supported by producer NF for which delegated discovery is being made. The allowed values for this field are:- * : This value denotes all the
service names for that target NF type.
or
- a valid NF service that a NF type supports.
Exclude Discovery Query Parameters Indicates the list of Exclude Query Info objects. Maximum size of this list is 20.
Note:
For more information about valid NF type and services supported by SCP, see Supported NF Types and Services chapter in the Oracle Communications Cloud Native Core, Service Communication Proxy User Guide. - * : This value denotes all the
valid NF types.
- In the Exclude Discovery Query Parameters
section, click Add to define the query header to exclude
as described in the following table:
Table 4-65 Field Description
Field Description Exclude Query Info Exclude Query Info has one field called query Header. The value of this query header is one of the query parameters that is forwarded along with the discovery request to NRF. Query Header Indicates the query parameters that is forwarded along with the discovery request to NRF. The allowed values for this field are:- None: This value denotes that caching is done for all the discovery responses.
- *: This value denotes that caching will not be done for all the discovery responses.
- SubscriberIds: An UE ID-related NF discovery query parameters.
- Supported Query Parameters: The query parameters that is forwarded along with the discovery request to NRF. For more information, see 'Supported Query Parameters' chapter.
The following table lists the eight subscriber IDs covered by the keyword "SubscriberIds":Table 4-66 SubscriberIds
SubscriberIds Description supi If included, this Information Element (IE) shall contain the SUPI of the requester UE to search for an appropriate NF. SUPI may be included if the target NF type is "PCF," "CHF," "AUSF," "UDM," or "UDR.". ue-ipv4-address The IPv4 address of the UE for which a BSF or P-CSCF needs to be discovered. ip-domain The IPv4 address domain of the UE for which a BSF needs to be discovered. ue-ipv6-prefix The IPv6 prefix of the UE for which a BSF or P-CSCF needs to be discovered. gpsi If included, this IE shall contain the GPSI of the requester UE to search for an appropriate NF. GPSI may be included if the target NF type is "CHF," "PCF," "UDM," or "UDR.". external-group-identity If included, this IE shall contain the external group identifier of the requester UE to search for an appropriate NF. This may be included if the target NF type is "UDM" or "UDR". routing-indicator Routing indicator information that allows to route network signaling with SUCI (see 3GPP 23.003 [12]) to an AUSF and UDM instance capable of serving the subscriber. May be included if the target NF type is "AUSF" or "UDM.".
Pattern: "^[0-9]{1,4}$"
msisdn If included, this IE shall contain the external group identifier of the requester UE to search for an appropriate NF. This may be included if the target NF type is "UDM" or "UDR". - Click Add to add the created rules.
- Click Remove to remove the created or existing rules.
- Click Save to save the updates.
- Click Cancel to reset all the fields.
- Click the Edit icon to edit the existing rule.
The Edit NF Discovery Response Cache Configuration Rule screen allows you to configure the fields as described in the following table:
Table 4-67 Field Description
Field Description Rule Name Indicates the name of the rule. This value should be unique. Target NF Type Indicates the NF type of producer for which delegated discovery is being made. The default value for this field is *, which denotes that caching will not be done for all the discovery responses. Service Names Indicates the list of service names supported by producer NF for which delegated discovery is being made. The default value for this field is *, which denotes that caching will not be done for all the discovery responses. Exclude Discovery Query Parameters Indicates the list of ExcludeQueryInfo objects. Maximum size of this list is 20. Note:
- defaultNFTypeDiscovery rule is applicable to any Model D request where discovery is happening without service names (in these requests, the 3gpp-sbi-discovery-service-names header is not present) and no other custom rule match is found. For this rule, caching will not happen for the list of query headers mentioned in the ExcludeQueryInfo.
- defaultNFServiceDiscovery rule is applicable to a Model D request where the request 3gpp-sbi-discovery-service-names header is also present in the incoming request and no other custom rule match is found. For this rule, caching will not happen for the list of query headers mentioned in the ExcludeQueryInfo.
- You cannot delete the default rules, but the exclude query info for these rules can be edited.
- Click Save.
Note:
By default, users can configure up to 100 rules using this API.