3 E5-OAM SNMP Configuration
Chapter 3, E5-OAM SNMP Configuration, describes support for SNMP V2 traps on the E5-OAM feature and the procedures necessary to configure the EAGLE to support this feature.
E5-OAM SNMP Feature Overview
The E5-OAM Simple Network Management Protocol (SNMP) feature allows the EAGLE to directly communicate with a Network Management System (NMS), sending SNMP traps northbound to up to two NMSs. The NMSs receive UAM/UIM data in the form of SNMP traps when alarms are raised and cleared.
The E5-OAM SNMP feature is a FAK controlled feature (P/N
893-0404-01) that uses Management Information Base(s) (MIB) for EAGLE Alarm
Traps. Once activated and turned on, these traps are sent to an NMS or set of
NMSs specified by the
ent/chg/rtrv-snmp-host commands. It
allows configured NMSs to request a resynchronization for all of the existing
UAMs. Each provisioned NMS receives a heartbeatTrap at a rate determined by the
NMS declaration, so the NMS will know it is connected during low periods of
UAM/UIM activity.
General Feature Information
- An ON-OFF feature "SNMP Traps on E5OAM" with P/N 893-0404-01 is used to control the activation of the SNMP agent on the E5-OAM.
- The EAGLE only supports SNMP V2c traps, a SET for starting/stopping the resynchronization, and a limited GET to determine the status of the resynchronizations.
- Synchronization of alarm events from the EAGLE to the NMS are supported by the EAGLE.
- The EAGLE currently uses SNMPv2 to implement SNMP function, which lacks modern means to authenticate users and implement private data exchanges; therefore, operators are advised to route SNMP traffic between the EAGLE and the OCEEMS using a secure network.
Feature Key Activation
This SNMP implementation is a FAK controlled feature (893-0404-01) that will use MIBs for EAGLE Alarm Traps, to provide for both UAM and UIMs. This FAK can only be activated and turned "on" or "off" for E5-OAM cards. No temporary key is allowed for this feature.
SNMP Agent Activation
Once the SNMP FAK has been activated and turned on,
alarm traps will be sent to an NMS or set of NMSs specified by the
ent/chg/rtrv-snmp-host commands.
NMS Provisioing
The SNMP FAK must be enabled before any NMS hosts can be
provisioned. One or two NMSs can be provisioned to receive traps and UIMs. For
each NMS, a host name and IP address must be specified with the
ent-snmp-host command. Optional
parameters allow the SNMP command and trap port numbers to be changed, as well
as allow the TRAP community string to be specified for the traps sent to the
NMS, and set the heartbeat interval. Once a host is provisioned, the optional
parameters may be changed with the
chg-snmp-host command.
Once the FAK is enabled, the system-wide SNMP options
can be changed with the
chg-snmpopts command. This command
enables the GET and SET community strings to be changed, and enables or
disables sending UIM as traps to the NMS.
Hardware Requirements
The hardware requirements and configuration include these items:
- The SNMP feature is only supported on the E5-MASP card.
- This feature requires an Ethernet connection:
Note:
The Ethernet port used for SNMP connects to the corresponding E5-OAM MASP backplane (either 850-0330-06/07 or 7333412) connector.
Refer to Hardware Reference for more information about the E5-MASP card.
E5-OAM SNMP Configuration Procedure
- Connecting the Ethernet cables. See Connecting Ethernet Cables.
- Provisioning the IP Address and IP Host. See Provisioning IP Address and IP Host.
- Provisioning a Default Router and Enabling the SNMP Feature. See Provisioning Default Router and Enabling SNMP Feature.
- Provisioning V2 Traps. See Provisioning V2 Traps.
- Provisioning the SNMP Options and turning on the SNMP Feature. See Provisioning the SNMP Options and Turning on the SNMP Feature.
Connecting Ethernet Cables
- Connect the Ethernet cables from network to the Port A connectors of each MASP.
Provisioning IP Address and IP Host
CHG-IP-LNK / RTRV-IP-LNK
chg-ip-lnk command is used to provision the IP link table. The chg-ip-lnk command assigns an IP address to the MASP. The rtrv-ip-lnk command is used to display the configuration. Use these commands to configure and display the IP address for the SNMP feature. For example:
- Enter the
chg-ip-lnk:loc=<card_loc>:port=a:ipaddr=<ip_addr>:submask=255.255.255.0: speed=100:mcast=yescommand to assign an IP address to the MASP. Enter this command for each MASP card. - Enter the
rtrv-ip-lnkcommand to verify the IP assignment.
ENT-IP-HOST / DLT-IP-HOST / RTRV-IP-HOST
The ent-ip-host, dlt-ip-host and rtrv-ip-host commands are used to define, delete and retrieve the MASP host name for the IP Address. Use these commands to define the host name for the IP address. For example:
- Enter the
ent-ip-host:host=<host_name>:ipaddr=<ip_addr>command to configure the MASP host name and IP address. Enter this command for each MASP card. - Enter the
rtrv-ip-hostto verify the host name and IP address entry.
Refer to Commands Manual for a complete description of these commands.
Provisioning Default Router and Enabling SNMP Feature
CHG-IP-CARD / RTRV-IP-CARD
chg-ip-card command is used to assign a default router to the MASP. For example:
- Enter the
chg-ip-card:loc=<card_loc>:srchordr=local:domain=<domain_name>:defrouter=<ip_addr>command to assign a default router to the MASP. Enter this command for each MASP card. - Enter the
rtrv-ip-cardto verify the IP assignment. - Enter the
enable-ctrl-feat:partnum=893040401:fak=yyyyyyyyyyyyyto enable the SNMP feature.
Refer to Commands Manual for a complete description of these commands.
Provisioning V2 Traps
The Network Management System (NMS) must be provisioned to receive traps:
ENT-SNMP-HOST / CHG-SNMP-HOST / DLT-SNMP-HOST / RTRV-SNMP-HOST
The ent-snmp-host command is used to provision up to two NMS hosts. The chg-snmp-host command is used to change the SNMP port configuration. The rtrv-snmp-host command is used to display the configuration. Use these commands to configure and display the NMS host information.
The default command port that the E5-OAM monitors for GET and SET requests is 161. The default trap port that the E5-OAM uses to send traps to the NMSs is 162. The default heartbeat interval is 60 seconds.
Refer to Commands Manual for a complete description of these commands.
- Enter the
ent-snmp-host:host=<host>:ipaddr=<ip_addr>command to provision an NMS to receive the traps. - Enter the
rtrv-snmp-hostcommand to verify the host entry.
Provisioning the SNMP Options and Turning on the SNMP Feature
The SNMP Option is turned OFF by default. Configuring the SNMP Option enables the GET and SET community strings to be changed, and enables or disables sending UIMs as traps to the NMS. The SNMP Option must be configured and turned on before this procedure can be completed:
Functionality
In the Eagle SNMP configuration, one or more administrative computers, called managers, have the task of monitoring a group of devices on the computer network. Each managed system (i.e., STP) executes a software component called an agent which reports information via SNMP to the manager.
SNMP agents report management data on STPs as variables. The protocol also permits active management tasks, such as modification of certain of these variables. The variables accessible via SNMP are organized in hierarchies. These hierarchies, and other metadata (such as type and description of the variable), are described by the Management Information Bases (MIBs). These MIBs are common to both the manager and the agent.
- A managed device (STP)
- An agent - software which runs on the managed devices
- Network management system (NMS) - software which runs on the manager
In the Eagle environment, a managed device is the STP itself. Each MASP implements an SNMP northbound interface that allows unidirectional (read-only) or bidirectional (read-write) access to node-specific information. The agent exchanges node-specific information with the NMSs. See Figure 3-1.
Figure 3-1 SNMP Basic Block Diagram
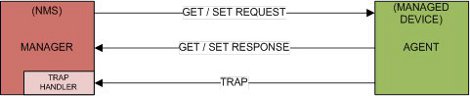
An agent is a network-management software module that resides on the managed device (STP). An agent has local knowledge of management information and translates that information to or from an SNMP specific form.
A network management system (NMS) executes applications that monitor and control managed devices. NMSs provide the bulk of the processing and memory resources required for network management. The Eagle supports connections to one or two NMSs.
An SNMP GET Request is a manager-to-agent request to retrieve the value of a variable or list of variables. A GET Response with current values is returned.
An SNMP SET Request is a manager-to-agent request to change the value of a variable or list of variables. The Eagle implementation supports the setting of the resyncVar variable only.
- Object Value = 0 is the normal default (no-resynchronization requested)
- Object Value = 1 indicates a resynchronization request
An SNMP TRAP is an asynchronous notification from the agent to a manager. A trap includes the time of the UAM/UIM, identification of the device being alarmed, alarm severity, text describing the alarm, a unique alarm identifier, and a unique sequence number.
- UAM Traps are generated for Alarms generated on the Eagle. The device being alarmed is identified by the alarmTrap's "resource" and "sub-resource" pairings.
- UIM Traps are generated, including the "System Alive" message, and other informational messages. The device reporting the informational message is identified by the alarmTrap's "resource" and "sub-resource" pairings.
Data Flows
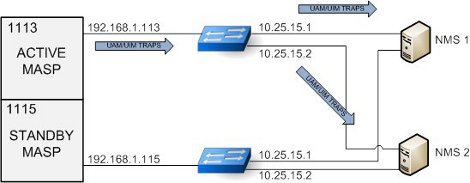
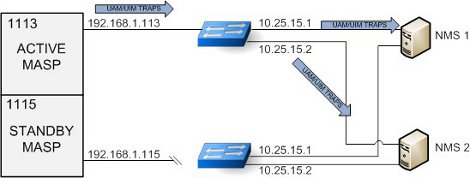
Under normal operating conditions, the Active MASP generates asynchronous traps which represent UIMs and UAMs. The traps are transmitted to one or two NMSs over the Active MASP IP link. Figure 3-2 example shows a typical network configuration for normal Eagle SNMP functions. The standby network configuration is available, so when a MASP switch of activity occurs, SNMP activity will be transmitted over its connections when the standby MASP becomes active.
Figure 3-2 UAM/UIM Trap Flow
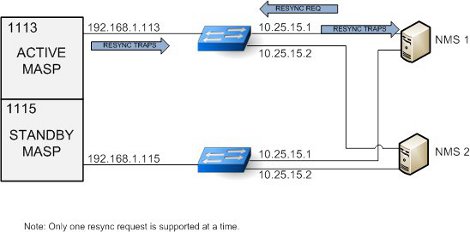
When an NMS becomes out of sync with the Eagle alarm status, the NMS may issue a SET request to initiate a resynchronization. The SET request is directed to the Active MASP only. Incoming synchronous EAGLE alarms and UIMs are buffered during an active resynchronization, and transmitted to the NMS once the resynchronization is complete in the same order they were received. The resynchAlarmTrap responses will be returned from the Active MASP. See Figure 3-3.
Figure 3-3 Resynchronization Request/Trap Flow
When the Active MASP IP link is inoperable, no asynchronous traps will not pass through the Standby MASP IP link, and resynchronization requests will not be handled by the Standby MASP. Because the alarm status is maintained on the Active MASP, only the Active MASP can transmit the UIM and UAM traps to the NMSs. If this situation occurs, either repair the IP link between the Active MASP and at the NMS, or switch MASP activity to the standby MASP. See Figure 3-4.
Figure 3-4 UAM/UIM Trap Flow with Active Link Down
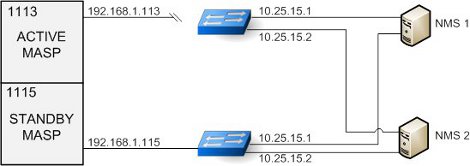
Asynchronous UAM/UIM trap flows when the Standby MASP link is down are identical to the normal data flows. An inoperable link on the Standby MASP does not interfere with normal data flows. See Figure 3-5.
Figure 3-5 UAM/UIM Trap Flow with Standby Link Down
Resynchronization
- Resynchronization requests
from an NMS should only be sent under the following conditions:
- When a Heartbeat Trap has not been received within a few seconds of the time provisioned on Eagle for that NMS,
- When the server has been restarted.
- When a Sequence number mis-match is detected on NMS.
- A scheduled resynchronization is not recommended.
- A resyncStartTrap is sent by the Eagle to acknowledge that the Eagle is processing the resynchronization request.
- A resyncAlarmTrap is sent by the Eagle and generated to the NMS that requested the resynchronization for each active alarm.
- A resyncStopTrap is sent by the Eagle to indicate all actively alarmed devices have had traps sent for their alarms, and the resynchronization is complete.
- A resyncRequiredTrap is sent by the Eagle to the NMS to all configured NMSs to indicate that the active OAM has determined there is a need to resynchronization with all NMSs. Currently this may be due to either: an OAM reboot or during a resynchronization the buffer area holding incoming UAM/UIMs has been exceeded, and one or more of the incoming UAM/UIMs have been lost.
- It is assumed the NMS
defined in the
ent-snmp-hostcommand will be present and monitoring the SNMP Traps sent by the Eagle. - The NMS should be configured to potentially receive SNMP traps from 2 possible IP addresses.
- The Ethernet connection shall be configured for a speed of 100Mbps or higher (when available).
- There are alarms which have no effect of incrementing or decrementing alarm counts, such as re-notification alarms. These alarms will be trapped as "informational (2)" priority.
- All Eagle clearing alarms will have a priority of "Clear (3)".
- The following UAMs will
all have a priority of "informational (2)" and not change the active alarm, nor
alarm state of the device:
- UAM # 314 - Route is allowed
- UAM # 315 - Route is restricted
- UAM # 316 - Route is prohibited
- UAM # 178 - Security Log failed
- UAM # 337 - DPC-SS status changed
- If alarm inhibits are turned on for a device, alarms at the inhibited level(s) are not displayed. Since the SNMP traps use the same trigger mechanisms for their generation as the other alarms, then they are also not displayed when the alarm is inhibited. The customer who chooses to use alarm inhibits with SNMP on EAGLE does so at their own risk.
- Only the Active OAM is the source for traps.
- The NMS will receive traps from one of two EAGLE SNMP IP addresses. It will be up to the NMS to correlate these SNMP Traps and know that the information from an Eagle can be coming from one of two IP addresses.
- No filtering of UAMs will be done by EAGLE for SNMP traps.
- Resynchronization requests must be sent to the active MASP. Resynchronization requests sent to the standby MASP will not be acknowledged.
- During a resynchronization, all UAM/UIMs to all NMSs will be buffered until the resynchronization is completed irrespective of which NMS has initiated the resynchronization. Then the Buffered UAM/UIMs will be displayed on all NMSs before synchronous alarm and UIMs are displayed. During the brief interval of resynchronization there might be no UAM/UIM stream available on the NMS even if it is not the originator of resynchronization request.
- Calculations for the
buffer area for incoming UIM/UAMs during a resynchronization are based on 7000
active alarms, an incoming rate of new UAM/UIMs of total 8 per second, and a
trap rate of 84 traps per second. If these limits are exceeded, the buffer
limit may be reached and a resyncRequiredTrap will be sent out to all NMSs. In
order to avoid resynchronization loop issues, the user can do the following:
- Clean up their network to avoid the excessive alarms and UIMs.
- Use the
chg-snmpopts:SNMPUIM=OFFcommand to halt incoming UIMs. - Temporarily reduce or
disable a UIM or set of UIMs that are flooding out by using the
set-uim-acthreshcommand. - Perform resynchronization only during periods of low activity.
SNMP MIBs
The following MIBs will need to be compiled into the NMS to interface with the EAGLE. They are shown here for reference only. Text files of these three MIBs are available on the Oracle Software Delivery Cloud (OSDC) site, https://edelivery.oracle.com, in a .zip file separate from the EAGLE software download file.
TEKELEC-TOPLEVEL-REG
TEKELEC-TOPLEVEL-REG DEFINITIONS ::= BEGIN
-- Copyright 2000 Tekelec Corporation
IMPORTS
enterprises FROM RFC1155-SMI;
tekelecCorp OBJECT IDENTIFIER ::= { enterprises 323 }
tekelecPrivate OBJECT IDENTIFIER ::= { tekelecCorp 1 }
tekelecRegistration OBJECT IDENTIFIER ::= { tekelecCorp 2 }
tekelecGeneric OBJECT IDENTIFIER ::= { tekelecCorp 3 }
tekelecCapabilities OBJECT IDENTIFIER ::= { tekelecCorp 4 }
tekelecProductGroups OBJECT IDENTIFIER ::= { tekelecCorp 5 }
tekelecRequirements OBJECT IDENTIFIER ::= { tekelecCorp 6 }
tekelecExperimental OBJECT IDENTIFIER ::= { tekelecCorp 7 }
tekelecCallCenterGroup OBJECT IDENTIFIER ::= {tekelecProductGroups 1 }
tekelecDiagnosticsGroup OBJECT IDENTIFIER ::= {tekelecProductGroups 2 }
tekelecSwitchingGroup OBJECT IDENTIFIER ::= {tekelecProductGroups 3 }
experimental OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 1}
generic OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 2 }
tekelecEAGLE OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 3}
tekelecLSMS OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 4}
tekelecOAP OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 5 }
tekelecIP7 OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 6 }
tekelecINSIGHT7 OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 7}
tekelecTALON OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 8}
tekelecVOX OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 9 }
tekelecSCP OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 10}
tekelecIVR OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 11}
tekelecNetworkSwitch OBJECT IDENTIFIER ::= {tekelecSwitchingGroup 12 }
tekelecSentinel OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 13}
tekelecTekServer OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 14 }
tekelecIP7EDGE OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 15}
tekelecTekCore OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 16}
tekelecSMAC OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 17}
tekelecTPD OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 18}
tekelecExtensions OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 19 }
tekelecEPAP OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 20}
tekelecELAP OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 21}
tekelec EAGLEXGServiceBroker OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 22}
tekelecECAP OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 23}
tekelecEAGLEEMS OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 24}
tekelecEAGLEXGHlrRouter OBJECT IDENTIFIER ::= {tekelecSwitchingGroup 25 }
tekelecEAGLEXGNPQueryRouter OBJECT IDENTIFIER ::= {tekelecSwitchingGroup 26 }
tekelecIAS OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 27}
tekelecEAGLEXGDSR OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 28 }
tekelecPCRF OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 29}
tekelecSDS OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 30}
tekelecTVOE OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 31}
tekelecUDR OBJECT IDENTIFIER ::= { tekelecSwitchingGroup 32}
ENDTEKELEC-EAGLE-COMMONOBJECTS
--
*****************************************************************************
--
-- Copyright 2010 Tekelec Corporation
--
-- The assignments of Tekelec enterprise MIB OIDs is officially
tracked by -- Technical Reference document TR003056. Each time this MIB is
updated a -- corresponding change must be made to this document to avoid
conflicts.
--
--*****************************************************************************
TEKELEC-EAGLE-COMMONOBJECTS DEFINITIONS ::= BEGIN
IMPORTS
enterprises,
OBJECT-TYPE,
MODULE-IDENTITY,
Unsigned32 FROM SNMPv2-SMI
DateAndTime,
DisplayString,
TEXTUAL-CONVENTION FROM SNMPv2-TC
tekelecEAGLE FROM TEKELEC-TOPLEVEL-REG;
tekelecEagleCommonObjects MODULE-IDENTITY
LAST-UPDATED "201206160000Z" -- June 16, 2012
ORGANIZATION "Tekelec"
CONTACT-INFO "
Postal: Tekelec
5200 Paramount Parkway
Morrisville, NC 27560
USA Tel: 919-460-5500"
DESCRIPTION "This MIB defines the Tekelec Eagle Common Objects"
-- ----------------------------------------------------------
--
-- Revision History --
-- ----------------------------------------------------------
REVISION "201206160000Z" -- June 16, 2012
DESCRIPTION
"Initial Version"
::= { tekelecEAGLE 1 }
-- ----------------------------------------------------------
--
-- TEXTUAL CONVENTIONS
--
-- ----------------------------------------------------------
EagleSeverity ::= TEXTUAL-CONVENTION
STATUS current
DESCRIPTION "The severity of Alarms in the Eagle"
SYNTAX INTEGER { informational (2),
clear (3),
minor (4),
major (5),
critical (6)
}
-- ----------------------------------------------------------
--
-- ALARM OBJECTS DEFINITION --
-- ----------------------------------------------------------
eagleAlarmObjects OBJECT IDENTIFIER
::= {tekelecEagleCommonObjects 1 }
eagleMRNTime OBJECT-TYPE
SYNTAX DateAndTime
MAX-ACCESS read-only
STATUS current
DESCRIPTION
"Timestamp when MRN was produced by the Eagle."
::= { eagleAlarmObjects 1 }
eagleMRNResourceName OBJECT-TYPE
SYNTAX DisplayString
MAX-ACCESS read-only
STATUS current
DESCRIPTION
"Unique name or identifier to identify the Eagle on the domain."
::= { eagleAlarmObjects 2 }
eagleMRNSubResourceName OBJECT-TYPE
SYNTAX DisplayString
MAX-ACCESS read-only
STATUS current
DESCRIPTION
"Unique name or identifier to identify an alarmable object within the Eagle."
::= { eagleAlarmObjects 3 }
eagleMRNSeverity OBJECT-TYPE
SYNTAX EagleSeverity
MAX-ACCESS read-only
STATUS current
DESCRIPTION
"The severity of MRN CLEAR|MINOR|MAJOR|CRITICAL|NONE) ."
::= { eagleAlarmObjects 4 }
eagleMRNTextMessage OBJECT-TYPE
SYNTAX DisplayString
MAX-ACCESS read-only
STATUS current
DESCRIPTION
"Original information describing the MRN."
::= { eagleAlarmObjects 5 }
eagleMRNNumber OBJECT-TYPE
SYNTAX Unsigned32
MAX-ACCESS read-only
STA number identifying a MRN."
::= { eagleAlarmObjects 6 }
eagleMRNSequence OBJECT-TYPE
SYNTAX Unsigned32
MAX-ACCESS read-only
STATUS current
DESCRIPTION
"Unique sequence number identifying an SNMP Alarm Trap instance."
::= { eagleAlarmObjects 7 }
TUS current
DESCRIPTION
"Unique number identifying a MRN."
::= { eagleAlarmObjects 6 }
eagleMRNSequence OBJECT-TYPE
SYNTAX Unsigned32
MAX-ACCESS read-only
STATUS current
DESCRIPTION
"Unique sequence number identifying an SNMP Alarm Trap
instance."
::= { eagleAlarmObjects 7 }
ENDTEKELEC-EAGLE-MIB
--*****************************************************************************
--
-- Copyright 2010 Tekelec Corporation
--
-- The assignments of Tekelec enterprise MIB OIDs is officially
tracked by
-- Technical Reference document TR003056. Each time this MIB is
updated a
-- corresponding change must be made to this document to avoid
conflicts.
--
--*****************************************************************************
TEKELEC-EAGLE-MIB DEFINITIONS ::= BEGIN
IMPORTS
MODULE-IDENTITY,
OBJECT-TYPE,
NOTIFICATION-TYPE FROM SNMPv2-SMI
DisplayString FROM SNMPv2-TC
eagleMRNSeverity,
eagleMRNTime,
eagleMRNResourceName,
eagleMRNSubResourceName,
eagleMRNTextMessage,
eagleMRNNumber,
eagleMRNSequence FROM TEKELEC-EAGLE-COMMONOBJECTS
tekelecEAGLE FROM TEKELEC-TOPLEVEL-REG;
tekelecEagleOam MODULE-IDENTITY
LAST-UPDATED "201206160000Z" -- June 16, 2012
ORGANIZATION "Tekelec"
CONTACT-INFO
" Postal: Tekelec
5200 Paramount Parkway
Morrisville, NC 27560
USA
Tel: 919-460-5500"
DESCRIPTION
"This MIB defines the Tekelec Eagle OAM Objects"
-- ----------------------------------------------------------
--
-- Revision History
--
-- ----------------------------------------------------------
REVISION "201206160000Z" -- June 16, 2012
DESCRIPTION "Initial Version"
::= { tekelecEAGLE 2 }
-- ----------------------------------------------------------
--
-- EAGLE NBI OBJECTS DEFINITION
--
-- ----------------------------------------------------------
tekelecEagleOamObjects OBJECT IDENTIFIER ::= { tekelecEagleOam 1 }
resyncVar OBJECT-TYPE
SYNTAX INTEGER(0..1)
MAX-ACCESS read-write
STATUS current
DESCRIPTION "The object is available to be set by the NMS to
indicate a request for alarm resynchronization. Object value=0 indicates a request to stop an ongoing
resnchronization and Object value=1 indicates a resynchronization request."
::= { tekelecEagleOamObjects 1 }
-- ----------------------------------------------------------
--
-- EAGLE TRAPS DEFINITION
--
-- ----------------------------------------------------------
tekelecEagleOamTraps OBJECT IDENTIFIER ::= { tekelecEagleOam 2 }
alarmTrap NOTIFICATION-TYPE
OBJECTS { eagleMRNTime,
eagleMRNResourceName,
eagleMRNSubResourceName,
eagleMRNSeverity,
eagleMRNTextMessage,
eagleMRNNumber,
eagleMRNSequence }
STATUS current
DESCRIPTION "The trap is sent by the EAGLE to NMS when an alarm
occurs."
::= { tekelecEagleOamTraps 1 } resyncAlarmTrap NOTIFICATION-TYPE
OBJECTS { eagleMRNTime,
eagleMRNResourceName,
eagleMRNSubResourceName,
eagleMRNSeverity,
eagleMRNTextMessage,
eagleMRNNumber,
eagleMRNSequence }
STATUS current
DESCRIPTION "The trap is sent by the EAGLE to NMS when an alarm
occurs."
::= { tekelecEagleOamTraps 2 } resyncStartTrap NOTIFICATION-TYPE
OBJECTS { eagleMRNResourceName,
eagleMRNSeverity,
eagleMRNTextMessage}
STATUS current
DESCRIPTION "The trap is sent by the EAGLE to NMS when the Eagle
is about to start resynchronization."
::= { tekelecEagleOamTraps 3 } resyncStopTrap NOTIFICATION-TYPE
OBJECTS { eagleMRNResourceName,
eagleMRNSeverity,
eagleMRNNumber,
eagleMRNTextMessage}
STATUS current
DESCRIPTION "The trap is sent by the EAGLE to NMS when
resynchronization is complete."
::= { tekelecEagleOamTraps 4 } resyncRejectTrap NOTIFICATION-TYPE
OBJECTS { eagleMRNResourceName,
eagleMRNSeverity,
eagleMRNTextMessage}
STATUS current
DESCRIPTION "The trap is sent by the EAGLE to NMS when a
resynchronization request is rejected by EAGLE"
::= { tekelecEagleOamTraps 5 } resyncRequiredTrap NOTIFICATION-TYPE
OBJECTS { eagleMRNResourceName,
eagleMRNSeverity,
eagleMRNTextMessage}
STATUS current
DESCRIPTION "The trap is sent by the EAGLE to NMS when a
resynchronization is required by EAGLE"
::= { tekelecEagleOamTraps 6 } heartbeatTrap NOTIFICATION-TYPE
OBJECTS { eagleMRNResourceName,
eagleMRNSeverity,
eagleMRNTextMessage}
STATUS current
DESCRIPTION "The trap is periodically sent by the EAGLE to NMS to indicate that the Eagle is up"
::= { tekelecEagleOamTraps 7 }
END