4 Running Test Cases Using ATS
4.1 Running NWDAF Test Cases using ATS
This section describes how to run Networks Data Analytics Function (NWDAF) test cases using ATS.
Prerequisites
To run NWDAF test cases, ensure that the following prerequisites are met:
- The ATS version must be compatible with the NWDAF release.
- The NWDAF and ATS must be deployed in the same namespace.
- The NWDAF must be deployed using the appropriate
values.yamlfile as per the configuration to be tested. - Ensure a nodePort or LoadBalancer port is available for "ocats-nwdaf-deploy".
Logging into ATS
Running ATS
Before logging into ATS, you need to ensure that ATS is deployed successfully using HELM charts.
For more information on verifying ATS deployment, see Verifying ATS Deployment.
Note:
To modify default log in password, refer to Modifying Login Password.Build the Jenkins host IP and load the Jenkins tool, run the following command to obtain the ocats-nwdaf-deploy service port:
kubectl get svc -n <namespace> | grep ocats-nwdaf-deploy- Obtain the node and pod name, run the following command:
kubectl get pod -o=custom-columns=NODE:.spec.nodeName,NAME:.metadata.name -n <namespace> | grep ocats-nwdaf-deploy - If an external IP is used, obtain the external Kubernetes node IP. Run the following command:
kubectl get no -o wide - Build the IP host as <External Node IP> : <Host IP>
ATS Login
-
To log in to ATS, open a browser and provide the IP Address and port details as <Worker-Node-IP>:<Node-Port-of-ATS>.
Figure 4-1 ATS Login
To run ATS, enter the login credentials. Click Sign in.
-
Cuztomize Jenkins page appears. Close this page.
- Jenkins is ready! page appears, click Start Using Jenkins.
-
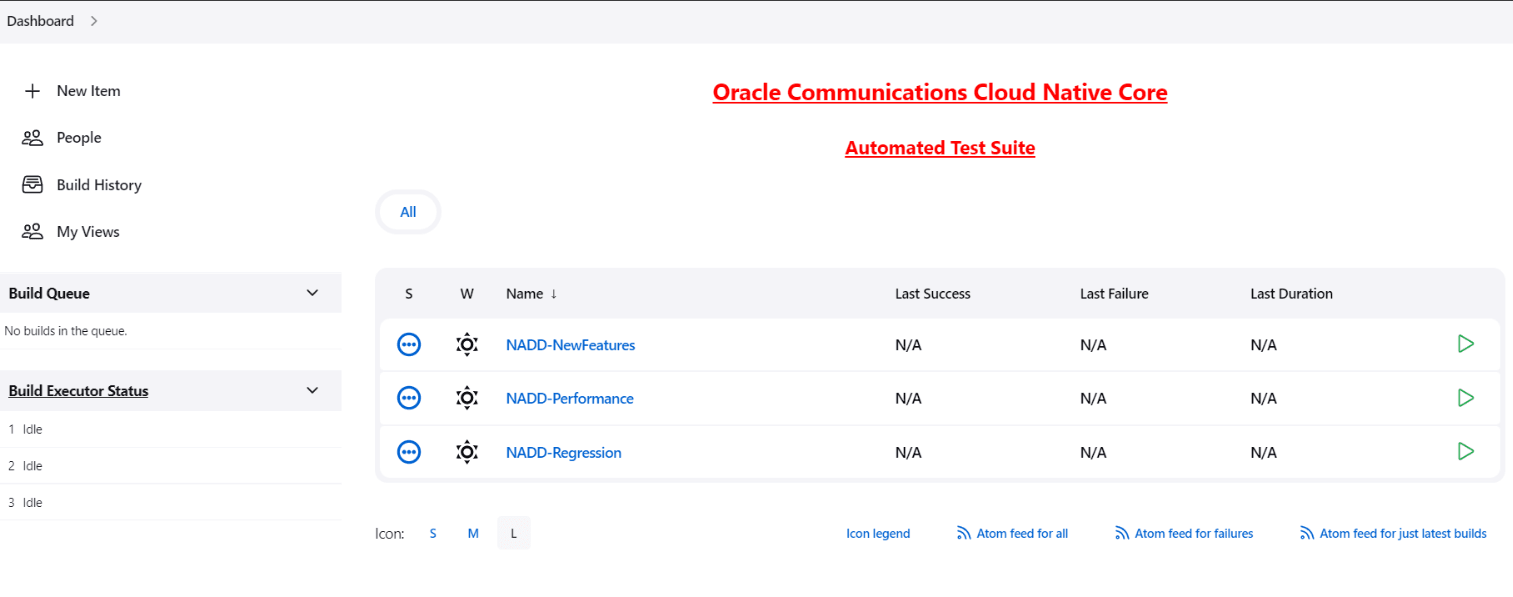
Dashboard screen displaying the NWDAF preconfigured pipelines appears.
Figure 4-2 Pipelines
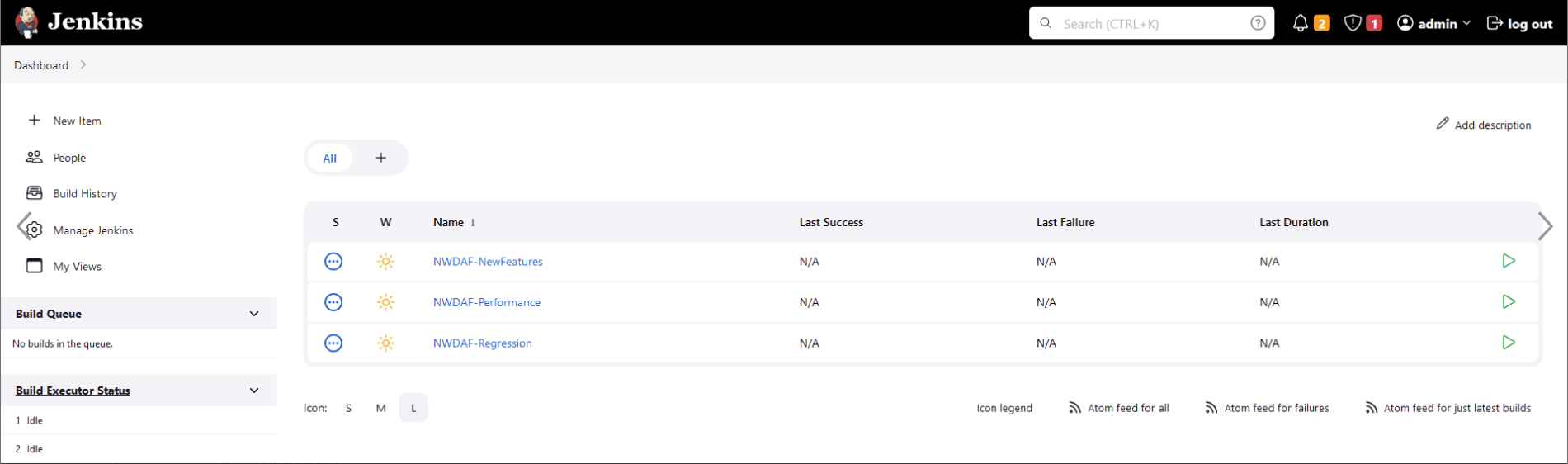
The NWDAF ATS has three configured pipelines:
- NWDAF-NewFeatures
- NWDAF-Performance
- NWDAF-Regression
Configure NWDAF Pipelines
To run configure a pipeline perform the following steps:
- The user database access includes permission to retrieve, update, and delete information.
- The user has logged in to the Jenkins page with admin credentials.
- Select the pipeline you want to run the test cases on, click NWDAF-NewFeatures in the Name column. The following screen appears:
Figure 4-3 Pipeline Configuration

In the above screen:
- Click Configure to configure the NWDAF pipeline.
- Click Build History box to view all the previous pipeline executions, and the Console Output of each execution.
- The Stage View represents the previously executed pipelines for reference.
- The Test Results Analyzer is the plugin integrated into the OCNWDAF-ATS. This option can be used to display the build-wise history of all the executions. It will provide a graphical representation of the past execution together.
- Click Configure to configure the environment parameters of the pipeline. User must wait for the page to load completely. Once the page loads completely, move to the Pipeline section:
Note:
Make sure that the following page loads completely before you perform any action on it. Also, do not modify any configuration other than shown below.Figure 4-4 Configure Pipeline
Note:
Remove the existing default content of the pipeline script. - Depending on the pipeline you want to configure, use the respective script. The following scripts are available at:
/var/lib/jenkins/ocnwdaf_tests/pipeline_scripts:- NewFeatures_Pipeline_script.txt
- Regression_Pipeline_script.txt
- Performance_Pipeline_script.txt
- Update the script of the pipeline you want to configure, and update the parameters according to the ATS and NWDAF environment you want to test.
- - b : Use this option to update the namespace according to the current namespace being used.
- - c : Use this option to update the service name of the Ingress gateway according to the current service name of the Ingress gateway being used.
Run the following command in the NWDAF console to verify the current service name of the Ingress gateway:
kubectl get svc -n <namespace_name> | grep ingressFor example:
kubectl get svc -n mdc-nwdaf-qa | grep ingressFigure 4-5 Ingress Gateway
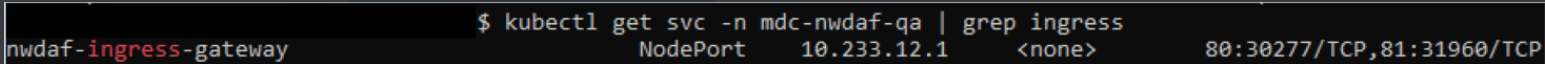
- Verify if the same name is assigned to "-c = NWDAF api gateway" host field, if not update to match the current name. Use the option "-c nwdaf-ingress-gateway \" .
- -g : Use this option to update the service name of the MESA simulator according to the current service name of the MESA simulator being used.
Run the following command in the NWDAF console to verify the current service name of the Mesa simulator:
kubectl get svc -n <namespace_name> | grep mesaFor example:
kubectl get svc -n mdc-nwdaf-qa | grep mesaFigure 4-6 Mesa Simulator
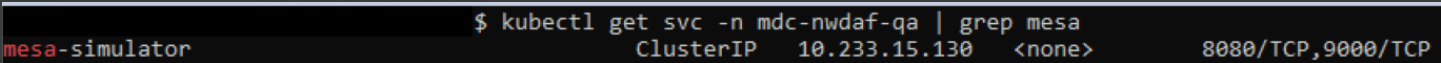
- Verify if the same name is assigned to "-g = MESA simulator API" host field, if not update to match the current name. Use the option "-g mesa-simulator \" .
- -i : Use this option to update the service name of the NWDAF Configuration Service according to the current service name of the NWDAF Configuration Service being used.
Run the following command in the NWDAF console to verify the current service name of the NWDAF Configuration Service:
kubectl get svc -n <namespace_name> | grep configurationFor example:
kubectl get svc -n mdc-nwdaf-qa | grep configurationFigure 4-7 Configuration Service
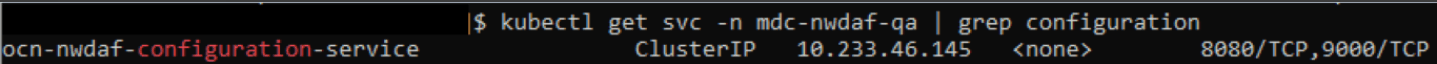
- Verify if the same name is assigned to "-i = NWDAF CONFIGURATION API" host field, if not update to match the current name. Use the option "-i ocn-nwdaf-configuration-service \" .
- Update the following parameters according to the database setup:
- -q : Use this option to update the NWDAF database host name, it can be FQDN or IP address.
For example:
-q 10.75.245.174 \
- -r : Use this option to update the NWDAF database port, it can be Cluster IP or Node Port.
For example:
-r 32648 \
- -q : Use this option to update the NWDAF database host name, it can be FQDN or IP address.
- Update the -s db_user_id and -t db_user_psw variables with the current data base user credentials, follow the steps listed below:
- Provide the userid and password of the database to be encrypted. Navigate to ocats-nwdaf-deploy pod and run the command:
kubectl exec -it <pod_name> -n <namespace_name> bashFor example:
kubectl exec -it ocats-nwdaf-deploy-54f98c447c-l6vxq -n ocnwdaf-ns bash - From the console, run the following command:
cd /env/lib/python3.9/site-packages/ocnnwdaf_lib/db_mgt - To update the user id run the following command from the console:
python -c "from db_connection_mgt import *; print(encode_values_data('<user>'))" - To update the password run the following command from the console:
python -c "from db_connection_mgt import *; print(encode_values_data('<password>'))" - Copy and paste the encrypted user id and password into the pipeline script located in the bottom of the page.
For example:
Figure 4-8 Sample Output

Figure 4-9 Pipeline Script
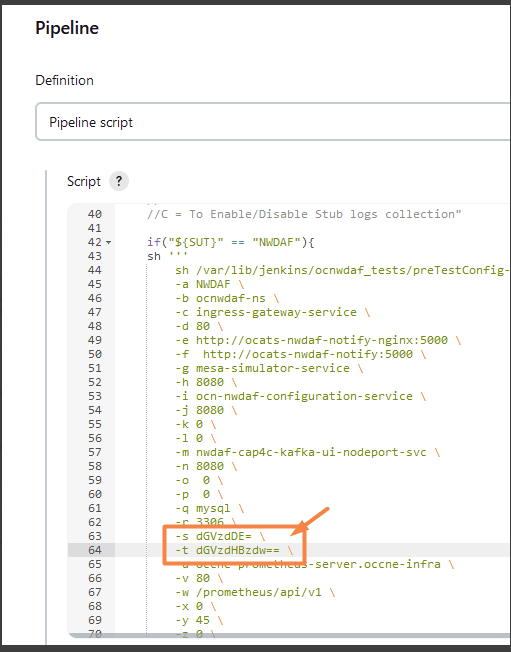
- Select the Use Groovy Sandbox checkbox.
- Provide the userid and password of the database to be encrypted. Navigate to ocats-nwdaf-deploy pod and run the command:
- Click Save. Perform the above steps for NWDAF-Regression and NWDAF-Performance pipelines.
Run the NWDAF ATS test scrips
- To run the test cases, click Build with Parameters.
- The TestSuite multi-option page is displayed, ensure the SUT value is NWDAF.
Figure 4-10 TestSuite Page

- To run all scripts available, select All and click Build.
- To run scripts on a specific feature, select Single/MultipleFeatures option and select the Feature you want to run the test on and click Build.
Figure 4-11 Single/Multiple Features

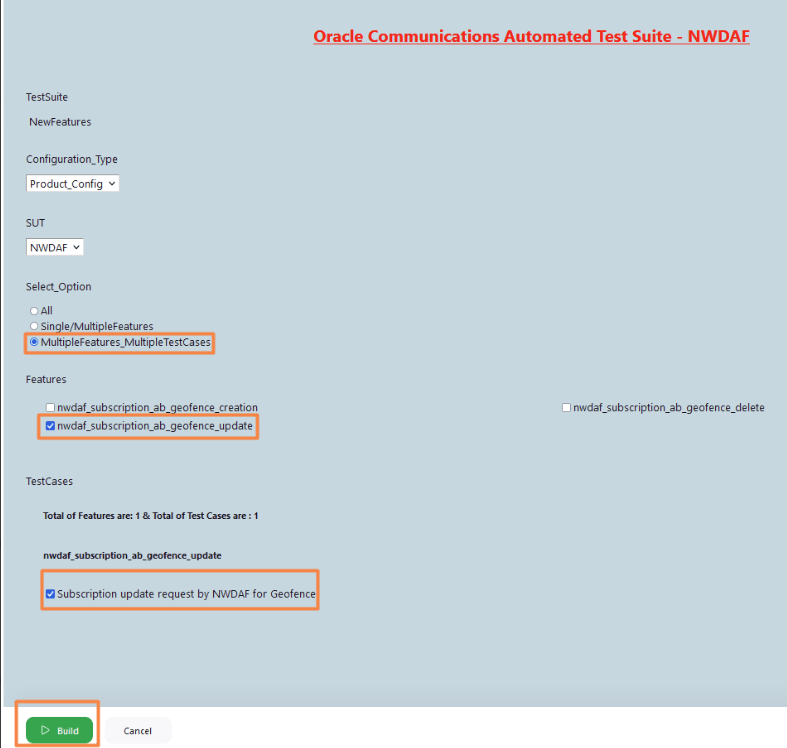
- To run scripts on a specific test scenario, select MultipleFeatures_MultipleTestCases option and select the Feature and the TestCases you want to run the test on and click Build.
Figure 4-12 Multiple Features and Testcases
- The Build History menu displays the list of running jobs, select the latest job displayed in the list.
- Click the Console Output option for this job. The jobs progress can be visualized in the log. The job progress also displays results for test cases and pipelines completed.
For example:
Figure 4-13 Sample Output
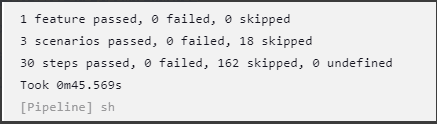
Figure 4-14 Sample Output
4.2 Running OCNADD Test Cases using ATS
4.2.1 Prerequisites
- The ATS version must be compatible with the OCNADD release.
- The OCNADD, ATS, and Stub must be deployed in the same namespace.
4.2.2 Logging into ATS
Running ATS
[ocnadd@k8s-bastion ~]$ helm status ocats -n ocnadd
NAME: ocats
LAST DEPLOYED: Sat Nov 3 03:48:27 2022
NAMESPACE: ocnadd
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
# Copyright 2018 (C), Oracle and/or its affiliates. All rights reserved.
Thank you for installing ocats-ocnadd.
Your release is named ocats , Release Revision: 1.
To learn more about the release, try:
$ helm status ocats
$ helm get ocats[ocnadd@k8s-bastion ~]$ kubectl get pod -n ocnadd | grep ocats
ocats-ocats-ocnadd-54ffddb548-4j8cx 1/1 Running 0 9h
[ocnadd@k8s-bastion ~]$ kubectl get svc -n ocnadd | grep ocats
ocats-ocats-ocnadd LoadBalancer 10.20.30.40 <pending> 8080:12345/TCP 9hFor more information on verifying ATS deployment, see Verifying ATS Deployment.
Note:
If LoadBalancer IP is provided, then give <LoadBalancer IP>:8080Figure 4-15 ATS Login
- Enter the login credentials. Click
Sign in. The following screen appears.
Figure 4-16 OCNADD Pre-Configured Pipelines
OCNADD ATS has three pre-configured pipelines.
- OCNADD-NewFeatures: This pipeline has all the test cases delivered as part of OCNADD ATS - 23.2.0.
- OCNADD-Performance: This pipeline is not operational as of now. It is reserved for future releases of ATS.
- OCNADD-Regression: This pipeline is not operational as of now. It is reserved for future releases of ATS.
4.2.3 OCNADD-NewFeatures Pipeline
OCNADD-NewFeatures Pipeline
- Click OCNADD-NewFeatures in the Name column. The
following screen appears:
Figure 4-17 Configuring OCNADD-New Features
 In the above screen:
In the above screen:- Click Configure to configure OCNADD-New Features.
- Click Build History box to view all the previous pipeline executions, and the Console Output of each execution.
- The Stage View represents the previously executed pipelines for reference.
- The Test Results Analyzer is the plugin integrated into the OCNADD-ATS. This option can be used to display the build-wise history of all the executions. It will provide a graphical representation of the past execution together.
- Click Configure. Once the page loads completely, click the Pipeline tab:
Note:
Make sure that the Configure page loads completely before you perform any action on it. Also, do not modify any configuration other than shown below.The Pipeline section of the configuration page appears as follows:Figure 4-18 Pipeline Section
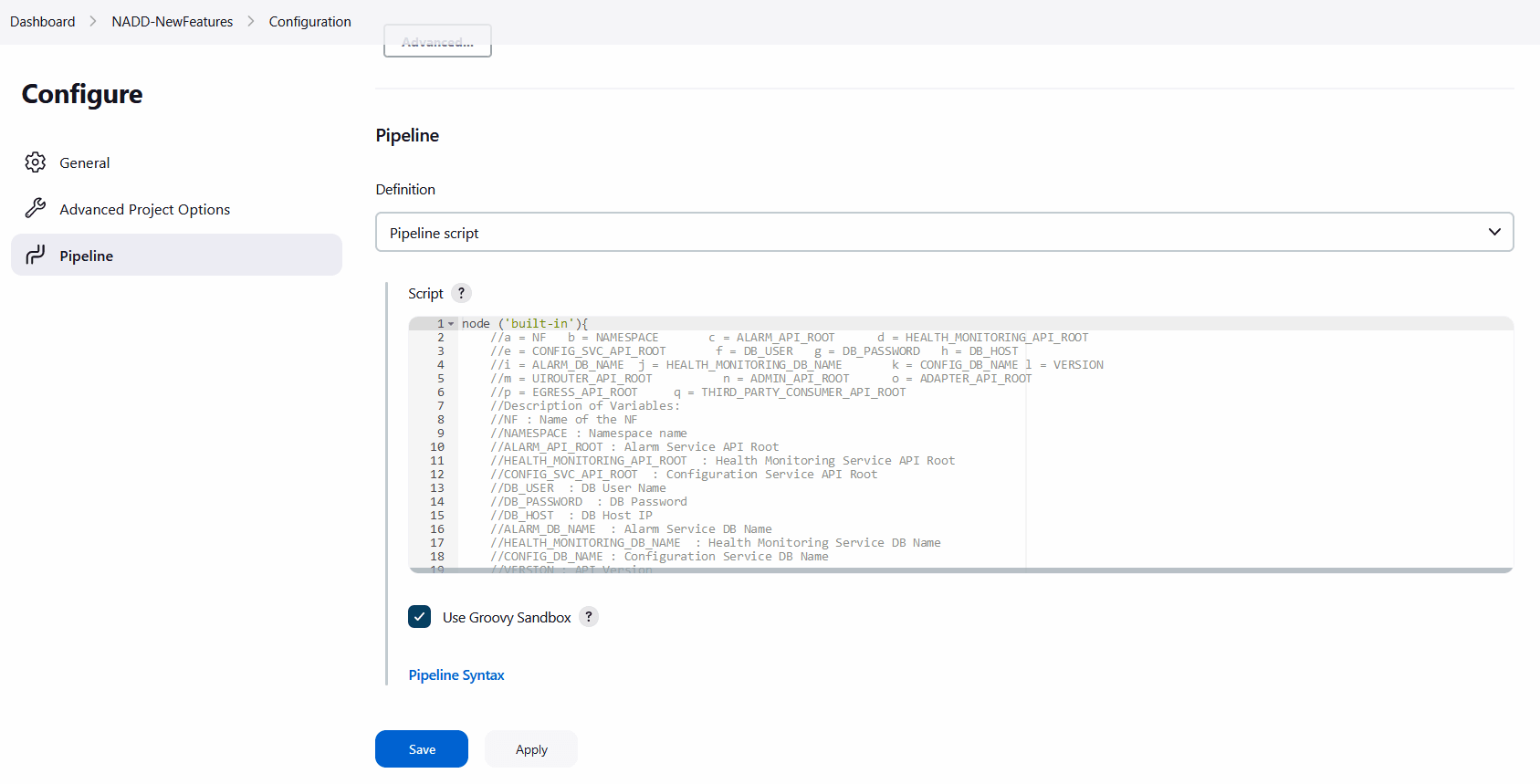
Important:
Remove the existing default content of the pipeline script and copy the following script content.The content of the pipeline script is as follows:node('built-in'){ //a= NF b = NAMESPACE c = VERSION d = DB_HOST e = DB_USER f = DB_PASSWORD //g= ALARM_DB_NAME h = HEALTH_MONITORING_DB_NAME i = CONFIG_DB_NAME //j= ALARM_API_ROOT k = HEALTH_MONITORING_API_ROOT l = CONFIG_SVC_API_ROOT //m= UIROUTER_API_ROOT n = ADMIN_API_ROOT o = THIRD_PARTY_CONSUMER_API_ROOT //p= BACKUP_RESTORE_IMG_PATH q = ALERT_MANAGER_URI //Descriptionof Variables: //NF: Name of the NF //NAMESPACE: Namespace name //VERSION: API Version //DB_HOST: DB Host IP //DB_USER: DB User Name //DB_PASSWORD: DB Password //ALARM_DB_NAME: Alarm Service DB Name //HEALTH_MONITORING_DB_NAME: Health Monitoring Service DB Name //CONFIG_DB_NAME: Configuration Service DB Name //ALARM_API_ROOT: Alarm Service API Root //HEALTH_MONITORING_API_ROOT: Health Monitoring Service API Root //CONFIG_SVC_API_ROOT: Configuration Service API Root //UIROUTER_API_ROOT: UI Router API Root //ADMIN_API_ROOT: Admin Service API Root //THIRD_PARTY_CONSUMER_API_ROOT: Third Pary Consumer API Root //BACKUP_RESTORE_IMG_PATH: Repository path forBackup restore image //ALERT_MANAGER_URI: Alert Manager API Root sh ''' sh /var/lib/jenkins/ocnadd_tests/preTestConfig-NewFeatures-NADD.sh \ -a NADD \ -b v3 \ -c <ocnadd-namespace> \ -d <DB_HOST> \ -e <DB_USER> \ -f <DB_PASSWORD> \ -g alarm_schema \ -h healthdb_schema \ -i configuration_schema \ -j ocnaddalarm:9099 \ -k ocnaddhealthmonitoring:12591 \ -l ocnaddconfiguration:12590 \ -m ocnaddbackendrouter:8988 \ -n ocnaddadminservice:9181 \ -o ocnaddthirdpartyconsumer:9094 \ -p <repo-path>/ocdd.repo/ocnaddbackuprestore:<tag> \ -q occne-kube-prom-stack-kube-alertmanager.occne-infra.svc.<domainName>:80/<clusterName> \ ''' if(env.Include_Regression && "${Include_Regression}" == "YES"){ sh '''sh /var/lib/jenkins/common_scripts/merge_jenkinsfile.sh''' load "/var/lib/jenkins/ocnadd_tests/jenkinsData/Jenkinsfile-NADD-Merged" } else{ load "/var/lib/jenkins/ocnadd_tests/jenkinsData/Jenkinsfile-NADD-NewFeatures" } }You can modify pipeline script parameters from "-b" to "-q" on the basis of your deployment environment, click on 'Save' after making the necessary changes.
The description of all the script parameters is as follows:
- a: Name of the NF to be tested in the capital (NADD).(Must not be modified)
- b: Namespace in which the NADD is deployed. (ocnadd)
- c: API Version. (v3)
- d: DB Host IP as provided during deployment of NADD. (10.XX.XX.XX)
- e: DB Username as provided during deployment of NADD.
- f: DB password as provided during deployment of NADD.
- g: DB Schema Name of ocnaddalarm microservice as provided during deployment of NADD. (alarm_schema)
- h: DB Schema Name of ocnaddhealthmonitoring microservice as provided during deployment of NADD. (healthdb_schema)
- i: DB Schema Name of ocnaddconfiguration microservice as provided during deployment of NADD. (configuration_schema)
- j: API root endpoint to reach ocnaddalarm microservice of NADD. (<Worker-Node-IP>:<Node-Port-of-ocnaddalarm>) or default value
- k: API root endpoint to reach ocnaddhealthmonitoring microservice of NADD. (<Worker-Node-IP>:<Node-Port-of-ocnaddhealthmonitoring>) or default value
- l: API root endpoint to reach ocnaddconfiguration microservice of NADD. (<Worker-Node-IP>:<Node-Port-of-ocnaddconfiguration>) or default value
- m: API root endpoint to reach ocnaddbackendrouter microservice of NADD. (Not used in the current release, use the default value)
- n: API root endpoint to reach ocnaddadminservice microservice of NADD. (Not used in the current release, use the default value)
- o: API root endpoint to reach ocnaddthirdpartyconsumer microservice of NADD. (<Worker-Node-IP>:<Node-Port-of-ocnaddthirdpartyconsumer>) or default value
- p: Repository path for ocnaddbackuprestore image.
- q: API root endpoint to reach alert manager microservice.
Running OCNADD Test Cases
- Click the Build with Parameters link available in the left navigation pane of the NADD-NewFeatures Pipeline screen. The following page appears:
Figure 4-19 Pipeline NADD_NewFeatures

- Select Configuration_Type as Product_Config.
- Set Include_Regression to 'NO' from the drop-down list.
- In Select_Option:
- Select All to run all the feature test cases and click the Build button to execute the pipeline
- Choose Single/MultipleFeatures to run the specific feature test cases and click the Build button to execute the pipeline