9 Upgrading Network Integrity
This chapter explains how to upgrade your existing system to the latest release of Oracle Communications Network Integrity.
This chapter explains how to recover your system after an upgrade failure. See "About Rolling Back Network Integrity" for more information.
About Upgrading Network Integrity
Upgrading to a new release of Network Integrity consists of the following tasks:
-
Planning the upgrade. See "Planning Your Upgrade" for more information.
-
Reviewing the upgrade impacts. See "Upgrade Impacts" for more information.
-
Performing the pre-upgrade tasks.
-
Upgrading Network Integrity.
-
Performing the post-upgrade tasks.
See "Upgrading Network Integrity" for more information.
Before upgrading a production environment, you should first test the upgrade in a test environment. See "Testing the Upgrade in a Test Environment" for more information.
In this chapter, the release you are upgrading from is called the old release, the release you are upgrading to is called the new release.
Supported Upgrade Paths
This release of Network Integrity supports direct upgrades to version 8.0 from releases 7.3.6.3, 7.3.6.4, 7.4, and 7.5.
See Upgrading Network Integrity for more information.
Planning Your Upgrade
Depending on the components affected by the upgrade, your upgrade team may include the following:
-
A database administrator, to manage the database upgrade and tune the database.
-
A system integrator, to handle new and existing customizations.
-
A system administrator, to manage the Oracle WebLogic Server and Network Integrity software upgrade.
-
A UNIX administrator, to manage accounts, network setup, and IP configurations.
Identify who might be affected by the upgrade. For example:
-
You might need to give your system administrators and Network Integrity users notice of any system downtime.
-
Tell your system administrators in advance about any changes to the system architecture (for example, Oracle database, client, or WebLogic Server upgrades).
-
Train your administrators, users, cartridge developers, or system integrators on new functionality introduced by the upgrade that has an impact on their role.
You might need to make changes to your system after the upgrade is complete to accommodate new or modified features or functionality. For example, if the new release provides new security functionality, additional system configuration steps may be required. See "Upgrade Impacts" for more information.
The best way to estimate the duration of an upgrade is to perform the upgrade procedure on a test system with a copy of the production data. See "Testing the Upgrade in a Test Environment" for more information.
It is not necessary to shut down Network Integrity or the Network Integrity WebLogic Server domain before an upgrade. However, you must ensure that Network Integrity is not running any operations, such as scans or blackouts.
Oracle recommends scheduling your upgrade during non-peak hours to minimize the disruption to your operations.
Testing the Upgrade in a Test Environment
Oracle recommends running the upgrade procedure on a test system with a copy of your production data before upgrading your production system. Test the upgrade by doing the following:
-
Successfully completing all the pre-upgrade, upgrade, and post-upgrade tasks.
-
Comparing the default behavior between the old and the new releases.
-
Recreating any custom configurations and extensions.
-
Confirming that all new behavior and functionality works.
-
Ensuring that the database tables are properly installed.
-
Ensuring that the database data is correct.
-
Starting the WebLogic Server domain.
-
Ensuring that users and user permissions are correct.
-
Ensuring that productized and custom cartridges build and deploy properly.
-
Logging into Network Integrity and verifying the version number of installed components.
Upgrade Impacts
This section explains any important system changes introduced by an upgrade. Upgrading to this version of Network Integrity requires the following system changes:
New features and new functionality are described in Network Integrity Release Notes.
Fusion Middleware Changes
You must upgrade your version of Oracle Fusion Middleware and apply applicable patches.
See Software Requirements for more information.
Java Development Kit Changes
The new version of Network Integrity requires an updated version of the Java Development Kit (JDK) on the Network Integrity application server. See "Software Requirements" for more information.
During the upgrade, you will need to update the Network Integrity domain to point to the new JDK.
WebLogic Server Changes
You must upgrade your version of WebLogic Server and apply applicable patches.
See "Software Requirements" for more information on software versions.
Application Component Changes
The Oracle NextGen Installer updates all the Network Integrity components.
Design Studio Changes
This version of Network Integrity requires an updated version of Oracle Communications Service Catalog and Design - Design Studio. See "Network Integrity System Requirements" for more information.
Design Studio can be set up before or after you upgrade Network Integrity. See "Design Studio Installation Overview (1)" in Design Studio installation documentation for more information. Rather than upgrading Design Studio, install the new version and keep the old version until after you have finished upgrading Network Integrity.
Cartridge Changes
You must undeploy cartridges that you do not want to migrate to the new release before beginning the upgrade.
After the upgrade is complete, cartridges must be migrated to the new release of Network Integrity using the Design Studio Cartridge Migration Tool. It is possible that migrated cartridges contain minor compilation errors that prevent them from building and deploying. If a cartridge fails to build, open it in Design Studio and correct any compilation errors.
Upgrading Network Integrity
Network Integrity supports two upgrade approaches from release 8.0:
In-Place Upgrade
This section describes the procedures to upgrade Network Integrity to release 8.0 from the following versions:
- Release 7.3.6.3
- Release 7.3.6.4
- Release 7.4
- Release 7.5
Note:
If you are using Fusion Middleware Infrastructure 12.2.1.3, you must first upgrade to 12.2.1.4 before proceeding with these steps.
See Oracle Fusion Middleware documentation for more information.
In addition, ensure that your database is on Oracle Database 19c (19.26) or Oracle Database 23ai.
See Software Requirements for more information on software versions.
Pre-Upgrade Tasks
This section provides the pre-upgrade tasks to be performed for the In-Place upgrade method.
Perform all the following tasks before upgrading Network Integrity:
-
Back up the Network Integrity and MDS databases. See "Network Integrity System Administration Overview" in Network Integrity System Administrator's Guide for more information.
-
Back up the Network Integrity WebLogic Server domain. For more information, see the WebLogic Server documentation.
Note:
Verify that the file/folder being backed up meets the file size or path name length requirements for the backup utility being used. For example, the maximum path name length for the tar application is 256 characters.
- Undeploy all cartridges that you do not want migrated to the new
version of Network Integrity. See Migrating Cartridges for more information.
For example, you should undeploy cartridges that you are no longer licensed to use, or cartridges that provide functionality you longer want to use.
For more information, see Problem: Inability To Run Scans or Resolve Discrepancies After Upgrading.WARNING:
After you upgrade Network Integrity, you cannot undeploy a non-migrated cartridge. If you do not undeploy cartridges that cannot be migrated or are not migrated, Network Integrity does not function. -
Undeploy the cartridges to avoid any old scan names after the upgrade. Perform this step only if you are upgrading from an environment earlier than 7.4.0.
-
If your version of Network Integrity is 7.3.6.3 or below, perform the following steps before starting the upgrade.
-
Stop all managed servers except the Administration Server.
-
Undeploy snmpAdapter from the WebLogic Administration Console
-
Restart all managed servers.
-
- Install the Fusion Middleware Infrastructure and apply any required
patches.
See Software Requirements for version information regarding Fusion Middleware Infrastructure and any applicable patches.
-
Before upgrading the WebLogic domain, Update the existing WLSSchemaDataSource as follows:
Note:
Perform this step only if you are upgrading your WebLogic domain from version 12c to 14c. If your WebLogic domain is already running on 14c, proceed directly to step 8.- Log in to the WebLogic Administration Console.
- In the left navigation pane, expand Services and click Data Sources.
- On the Data Sources page, proceed based on your database
type:
- Standard database: Select WLSSchemaDataSource and continue with step d.
- RAC database: Select each WLSSchemaDataSource RAC node individually, such as WLSSchemaDataSource-rac0, WLSSchemaDataSource-rac1 and perform steps d and e for each node.
- On the Configuration tab, select the Connection Pool sub-tab.
- In the Properties section, update the User value from <PREFIX>_WLS_RUNTIME to <PREFIX>_WLS.
- Shutdown all WebLogic servers before performing the following pre-upgrade steps.
- Upgrade the database schemas:
- Navigate to
MW_HOME/oracle_common/upgrade/bin/ua
whereMW_HOME is the directory in which Oracle Fusion Middleware 14c is installed.
This directory contains the Upgrade Assistant (UA) tool, which you use to upgrade the schema.
- Launch the UA tool to upgrade the schema.
The Welcome screen appears.
- Click Next.
The Upgrade Type screen appears.
-
On the Upgrade Type screen, select Individually Selected Schemas, and click Next.
-
The Available Components screen appears which lists the available components that can be upgraded.
-
Select the below components and click Next.
Common Infrastructure Services Oracle Audit Services Oracle Metadata Services Oracle Platform Security Services Oracle WebLogic Server
The Domain Directory screen appears.
-
Select the existing WebLogic domain directory that needs to be upgraded and click Next.
The Prerequisites screen appears.
- Confirm that the database backup is complete by selecting the
following checkboxes:
- All affected servers are down
- All affected data is backed up
- Database version is certified by Oracle for Fusion Middleware upgrade
- Certification and system requirements have been met
-
Click Next.
The OPSS Schema screen appears.
- From the Database Type list, select the database type.
- In the Database Connect String field, enter the
hostname:portnumber/ServiceName string.
Note:
For a RAC database, provide RAC Server DB Information, in the following format: hostname:portnumber/ServiceName
- In the DBA User Name field, enter the database administrator user name.
- In the DBA Password field, enter the password for the administrator user.
- Click Connect.
If the provided details are valid, the Schema User Name and Schema Password fields are enabled.
- From the Schema User Name list, select the OPSS schema.
- In Schema Password field, enter the schema password, and click Next.
- Repeat the same procedure for all remaining schemas (for
example, MDS, IAU, STB, WLS, etc.) until all schema credentials are provided
and click Next.
The Examine screen appears.
- Verify that all listed schemas show the status as ready for
upgrade, and then click Next.
The Upgrade Summary screen appears.
- Verify the details of the schemas to be upgraded and click
Upgrade.
The Upgrading Progress screen appears. You can monitor the progress of the upgrade from this screen.
- After the upgrade completes, click Next.
The Upgrade Success screen appears.
- Verify that the upgrade was successful and click Close.
For more information on upgrading schemas (using the Upgrade Assistant), see Oracle Fusion Middleware documentation.
- Navigate to
MW_HOME/oracle_common/upgrade/bin/ua
-
Reconfigure the WebLogic domain configurations using the Fusion Middleware Reconfiguration Wizard.
- Run the
reconfig.shscript located in: MW_HOME/oracle_common/common/bin/reconfig.sh, where MW_HOME is the directory in which Oracle Fusion Middleware 14c is installed. - On the Select Domain screen, from the Existing Domain
Location list, select the domain that you want to upgrade and click
Next.
The Reconfiguration Setup Progress screen appears, displaying the progress of the reconfiguration setup process.
- Click Next.
The Reconfig Summary screen appears.
- Click Next.
The Domain Mode and JDK screen appears. The domain mode cannot be changed during reconfiguration. It is inherited from the existing WebLogic domain that is being upgraded.
- Select the JDK option and select the folder
(JAVA_HOME) where the JDK is installed. Then, click
Next.
Ensure that you have installed the correct version of the JDK. See Software Requirements for more information.
- The JDBC Data Sources screen appears. Click Next.
- The JDBC Data Sources Test screen appears. Click Next.
- The Database Configuration Type screen appears.
Details are automatically retrieved from the existing WebLogic domain being upgraded.
Verify the information, click Get RCU Configuration to confirm, and then click Next.
- The JDBC Component Schema screen appears.
- For single-instance database (Standard DB): Verify the values in the fields and click Next, the JDBC Test screen appears. Continue with step j.
- For Oracle Real Application Clusters (RAC) database:
- Select the check box left to Component Schema.
- Select the Convert to RAC multi data source option.
- Click Next.
The Oracle RAC Multi Data Source Component Schema screen appears.
- Verify the details retrieved.
- In the Host Name field, enter the host name/IP address of the RAC database node.
- In the Instance Name field, enter the instance name of the RAC database node.
- In the Port field, enter the listener port of the RAC database node.
- Add additional RAC database nodes by clicking Add Host and providing their details.
- Click Next.
The JDBC Test screen appears. Continue with step j.
- Verify that all the JDBC component connections
pass the validation test and click Next.
The Advanced Configuration screen appears.
- On the Advanced Configuration screen:
- If upgrading a standalone environment, select Administration Server only.
- If upgrading a clustered environment, select the
following options.
- Administration Server
- Topology
- Deployments and Services
- Click Next.
The Administration Server screen appears.
- The details are automatically fetched from the existing
WebLogic domain that is being upgraded, Review the values, and click
Next.
If upgrading a standalone environment continue with q.
- Continue navigating through the subsequent screens, reviewing the details on each. Click Next to proceed, updating settings only if necessary.
- On the Deployments Targeting screen, the existing configuration
is displayed.
Note:
In a clustered environment, ensure that NICMWSAdapter, cartridge_management_ws are present only on the first managed server.
Review the details and click Next.
- The Services Targeting screen appears. The existing configuration is displayed. Review the details and click Next.
- The Configuration Summary screen appears.
- Review the detailed configuration settings of the domain and
click Reconfig.
The Reconfiguration Progress screen appears, which displays the progress of the reconfiguration process.
After the reconfiguration process is completed, click Next.
- The End of Configuration screen appears. ClickFinish.
For more information on reconfiguring the domain, see Oracle Fusion Middleware documentation.
- Run the
- Upgrade the WebLogic domain configurations by doing the following:
- Navigate to the
MW_Home/oracle_common/upgrade/bin/uadirectory.
where MW_Home is the directory in which Oracle Fusion Middleware 14c is installed.
This directory contains the Fusion Middleware Upgrade Assistant which is used to upgrade the WebLogic domain configurations.
- Launch the Fusion Middleware Upgrade Assistant.
The Welcome screen appears.
- Click Next.
The Upgrade Type screen appears.
- Select All Configurations used by a domain.
In the Domain Directory field, select the WebLogic domain directory you want to upgrade, and then click Next.
- The Component List screen appears, click Next.
The Prerequisites screen appears.
- Select all the checkboxes, click Next.
- Navigate through the subsequent screens by clicking Next on each screen and specifying your settings as necessary.
- On the Upgrade Success screen, verify that the upgrade was
successful and click Close.
For more information on upgrading domain component configurations, see Oracle Fusion Middleware documentation.
- Navigate to the
MW_Home/oracle_common/upgrade/bin/uadirectory.
- Start the Network Integrity Administration server. If this is a clustered server environment, start the cluster member servers.
Note:
If there are any JNDI issues and if managed server status goes to Admin state, then delete NetworkIntegrity.ear and NICMWSAdapter.ear from deployments and start the managed server.
Upgrading Network Integrity
This section assumes that you have completed the steps in Pre-UpgradeTasks before proceeding with the upgrade of Network Integrity.
In-Place Upgrade Using Interactive Install
To upgrade Network Integrity using the In-Place upgrade method:
- Create a directory (dir)for a temporary installation directory.
- Download the Network Integrity Installer software from the Oracle
software delivery website: https://edelivery.oracle.com
and save it to dir:
-
Export JDK Home by running the following command, See Software Requirements for JDK version information:
export JAVA_HOME=$JDK_HOME - Run the Oracle Nextgen Network Integrity Installer using the following
command:
java -jar NetworkIntegrityInstaller_{release}.jarThe Installer Welcome screen appears.
- Click Next.
- One of the following screens is displayed:
- If Network Integrity is the first Oracle product that you are
installing on the system, the Specify Inventory directory and credentials
screen appears. Enter the full path of the inventory directory, select the
Operating System group name, and then click Next.
The Installation Location screen appears. Continue with step 7.
Note:
The inventory directory manages all Oracle products installed on your system.
- If you have installed any Oracle products on the system prior to installing Network Integrity, The Installation Location Screen appears. Continue with step 7.
- If Network Integrity is the first Oracle product that you are
installing on the system, the Specify Inventory directory and credentials
screen appears. Enter the full path of the inventory directory, select the
Operating System group name, and then click Next.
- In NI_Home field, enter or browse the path to the folder where you previously installed the old release of Network Integrity. And click Next.
- The Installation Type Screen appears. Select upgrade, click
Next.
The WebLogic admin server connection screen appears.
- The Installer retrieves information about your old Network Integrity installation, such as connection details and usernames.
- Verify the WebLogic Administration Server connection information, enter
the WebLogic Server password, and click Next.
The Target Selection screen appears.
- Select the target WebLogic server or cluster where you want to upgrade
Network Integrity and click Next.
The DB Type Selection screen appears.
- Select the same database type that is used by your old Network
Integrity installation:
- If your old installation is connected to a standalone database,
select Standard Oracle Enterprise Database, and click Next.
The Standard DB Connection screen appears. Do the following:
- Verify that the retrieved field values are correct and click Next.
- In the Password field,enter the database server password for the user specified in the User Name field.
- Click Next.
- If your old installation is connected to an Oracle Real
Application Clusters (RAC) database,select Oracle Real Application
Cluster Database, and click Next.
The RAC DB Connection screen appears. Do the following:
- Verify that the retrieved field values are correct and click Next.
- In the Password field,enter the database server password for the user specified in the User Name field.
- Click Next.
The MDS Schema User Connection screen appears.
- If your old installation is connected to a standalone database,
select Standard Oracle Enterprise Database, and click Next.
- Do the following:
- Verify that the retrieved value in the Schema User Name field is correct.
- In the Schema User Password field, enter the schema user password for the user specified in the Schema User Name field.
- Click Next.
The Disable Unsecured Port screen appears.
- Select whether to disable the unsecured listen port by doing one of the
following:
- Select Yes if you are configuring Network Integrity to communicate and listen over SSL-enabled ports only, by disabling Non-SSL Ports.
- Select No if you are configuring Network Integrity to communicate and listen over both SSL and Non-SSL ports.
- The Java Home Location Screen appears, Verify the java home path and
click Next.
The Installation Summary screen appears.
- Review the details and click Install.
- The Install Progress screen appears, showing the status of the upgrade installation. When the installer completes the upgrade, click Next.
- The Installation Complete screen appears displaying the success of the upgrade. This screen also provides the URLs for accessing the new release of Network Integrity. Make a note of the URLs.
- In the Installer, click Finish.
In-Place Upgrade Using Silent Mode
You can use the silent install mode when you are upgrading Network Integrity using the same configuration repeatedly. The silent install mode does not use the GUI and runs in the background.
About the Response File
The Network Integrity installer uses a response file, which contains a pre-defined set of values, such as server connection details. The response file comes in a template form to upgrade Network Integrity in silent mode.
The following response file templates come as part of the Network Integrity installation package: oracle.communications.integrity.rsp
The response file templates contain all the fields that the installer requires to perform upgrade in silent mode
When you extract the installer JAR file, the response file templates are saved in the Response directory at the following location: Disk1/stage/Response.
describes the Network Integrity response file template properties, along with the values that should be specified for a complete upgrade scenario.
Table 9-1 Network Integrity Response File Template Properties
| Response File Template Name | Property Name | Description (with Default Values) |
|---|---|---|
| Installation Location Details (Required) | ORACLE_HOME | Directory path where the NI application will be installed. |
| Installation Type Details (Required) | INSTALLATION_TYPE | Type of installation (Allowed values: Complete or
Upgrade).
Set to "Upgrade" for an In-Place upgrade. |
| WebLogic Admin Server Connection Details (Required) | APP_ADMIN_HOST | Host name or IP address of the WebLogic Admin Server. |
| WebLogic Admin Server Connection Details (Required) | APP_ADMIN_PORT | Port number for the WebLogic Admin Server (values
provided must be enclosed in double quotes).
For SSL-based deployment, provide the SSL port value and specify the keystore file location in the APP_SERVER_KEYSTORE property. |
| WebLogic Admin Server Connection Details (Required) | APP_SERVER_USER | Username for the WebLogic Admin Server. |
| WebLogic Admin Server Connection Details (Required) | APP_SERVER_PASSWD | Password for the WebLogic Admin Server. |
| WebLogic Admin Server Connection Details (Required) | APP_SERVER_KEYSTORE | Path to the keystore file required for SSL-based
deployment.
Example:, certs/Keystore.jks |
| Target Selection Details (Required) | APP_TARGET_NAME | Name of the target (such as AdminServer or CL1) where the NI application was previously installed and will be upgraded. |
| Database Selection Details (Required) | DATABASE_TYPE | Type of database used.
Accepted values: Standard Oracle Enterprise Database or Oracle Real Application Cluster Database Use the same type that you used in the production environment. |
| Standard DB Details (Required only if DATABASE_TYPE = Standard Oracle Enterprise Database) | DB_HOST_NAME | Host name of the standard Oracle database. |
| Standard DB Details (Required only if DATABASE_TYPE = Standard Oracle Enterprise Database) | DB_HOST_PORT | Port number of the standard Oracle database (enclose in double quotes). |
| Standard DB Details (Required only if DATABASE_TYPE = Standard Oracle Enterprise Database) | DB_USER_NAME | Username with SYSDBA privileges for the standard Oracle database. |
| Standard DB Details (Required only if DATABASE_TYPE = Standard Oracle Enterprise Database) | DB_PASSWORD | Password for the SYSDBA user of the standard Oracle database. |
| Standard DB Details (Required only if DATABASE_TYPE = Standard Oracle Enterprise Database) | DB_SERVER_SERVICE | Service name of the standard Oracle database. |
| RAC DB Details (Required only if DATABASE_TYPE = Oracle Real Application Cluster Database) | RAC_CONNECTION_STRING | Connection string details for Oracle RAC in the format:
HostName1:Port1:Service1,HostName2:Port2:Service2 |
| RAC DB Details (Required only if DATABASE_TYPE = Oracle Real Application Cluster Database) | RAC_SERVER_USER | Username for connecting to the Oracle RAC database |
| RAC DB Details (Required only if DATABASE_TYPE = Oracle Real Application Cluster Database) | RAC_SERVER_PASSWORD | Password for the Oracle RAC database server. |
| NI Schema Table Creation (Not Required). For the In-Place upgrade, do not enter any value. | DB_SCHEMA | Flag to indicate whether to create the app schema table
Allowed values: “true” or “false”). |
| MDS Schema Information Details (Required ) | SCHEMA_OWNER_NAME | Username for the MDS (Metadata Services) schema user.
Note: These details are related to the upgraded MDS schema. |
| MDS Schema Information Details (Required ) | SCHEMA_OWNER_PASSWD | Password for the MDS (Metadata Services) schema
user.
Note: These details are related to the upgraded MDS schema. |
| Security Provider Selection Details (Not Required). For the In-Place upgrade, do not enter any value. | SECURITY_PROVIDER_NAME | Type of security provider to select.
Allowed values: Embedded_LDAP or External_LDAP |
| Embedded LDAP Details (Not Required). For the In-Place upgrade, do not enter any value. | LDAP_USER_NAME | Username to be created in the embedded LDAP directory. |
| Embedded LDAP Details (Not Required). For the In-Place upgrade, do not enter any value. | LDAP_PASSWD | Password for the newly embedded LDAP user.
Note: The password requirements are as follows.
|
| External LDAP Details (Not Required). For the In-Place upgrade, do not enter any value. | LDAP_SERVER_HOST | Host name of the external LDAP server. |
| External LDAP Details (Not Required). For the In-Place upgrade, do not enter any value. | LDAP_SERVER_PORT | Port number of the external LDAP server. |
| External LDAP Details (Not Required). For the In-Place upgrade, do not enter any value. | LDAP_SERVER_USER | Username for connecting to the external LDAP server. |
| External LDAP Details (Not Required). For the In-Place upgrade, do not enter any value. | LDAP_SERVER_PASSWORD | Password for the external LDAP server user. |
| External LDAP Details (Not Required). For the In-Place upgrade, do not enter any value. | LDAP_USER_BASE_DN | User BASE DN information of external LDAP server. |
| External LDAP Details (Not Required). For the In-Place upgrade, do not enter any value. | LDAP_GROUP_BASE_DN | Group BASE DN information of external LDAP server. |
| External LDAP Details (Not Required). For the In-Place upgrade, do not enter any value. | LDAP_SERVER_KEYSTORE | Path to the keystore file for the external LDAP server (for example, certs/externalLDAPKeystore.jks). |
| NI Internal user Details (Not Required). For the In-Place upgrade, do not enter any value. | LDAP_DEF_USER_PASSWD |
Password for the NI internal user. Note: The password requirements are as
follows.
|
| Disable Non-SSL Port Option (Required) | DISABLE_NONSSLPORT | Option to disable the non-SSL port (Allowed Values: set to “true” to disable, or “false” to keep enabled). |
Before using the response file, ensure that any optional properties or values that are not required by the installer are left empty.
Starting Silent Mode Installation
Before you begin upgrading Network Integrity in silent mode, ensure that you have provided all required input values in the response file template.
To upgrade Network Integrity in silent mode using In-Place Upgrade:
- Export JDK Home by running one of the following command, See Software Requirements for JDK version
information:
export JAVA_HOME=$JDK_HOME -
Use the following command to start the silent installer,here absolute_path is the fully qualified response file location:
java -jar NetworkIntegrityInstaller_{release}.jar -responseFile {absolute_path}The installation runs silently in the background.
Note:
The installer shuts down all of the servers, including the Administration Server and the Managed Servers, after a silent installation. Start all of the servers manually after the installation is complete.
- At the end of the installation, the command window displays the location of the installer log files. Users can review these logs files to verify that the installation was successful.
- Start the AdminServer, using the following
command:
./startNI.sh
- If you use a Cluster environment, start the managed servers, using the
following
command:
./startNI.sh cluster_managed_server_name admin_server_URL
-
Open the following file once the installation is complete, to get the URL to access Network Integrity:
NI_Home/install/readme.txt
For example: /opt/integrity/Oraclecommunications/install/readme.txt
-
Copy the URL and paste it in the browser window's address field and press Enter to access Network Integrity.
You can now access the Network Integrity application.
For information on verifying the successful upgrade of Network Integrity, see "Verifying the Network Integrity Installation".
After verifying a successful upgrade, perform the required post-installation actions. See Network Integrity Post-Installation Tasks for more information.
Post-Upgrade Tasks
After upgrading Network Integrity, do the following, if necessary:
-
Verify that the Network Integrity software upgrade was completed successfully. See "Verifying the Network Integrity Installation" for more information.
-
If you configured an Inventory System in the old version of Network Integrity and specified a password, you need to re-enter the password.
-
In the new version of Network Integrity, click Manage Import System.
-
Click Edit.
-
Enter the password and click Save and Close.
-
-
Migrate your cartridges to the new version of Network Integrity. See "Migrating Cartridges" for more information.
-
Re-deploy your cartridges. See "Deploying Network Integrity Cartridges" for more information.
Blue Green Upgrade
The Blue Green Upgrade is designed to minimize downtime and risk by creating a backup environment and thoroughly testing the new version before replacing the production system.
- Blue environment: This refers to the current (running) production environment that is active.
- Green environment: This refers to the staging environment where the backed-up MDS schema (secured and synchronized using Data Guard) is upgraded and validated by the uploading to the new version (8.0 release). All upgrade and testing operations are performed in the Green environment, ensuring no disruption to the Blue environment. Once the validation is completed, the Green environment is promoted as the new production environment.
- Phase 1: Staging and ValidationStaging and Validation
- Phase 2: Staging Update and Production SwitchoverStaging Update and Production Switchover
- Phase 3: Upgrading the Blue EnvironmentUpgrading the Blue Environment
Prerequisites for Blue Green Upgrade
The prerequisites for upgrading Network Integrity using Blue Green upgrade is as following:
- Primary production environment (Blue environment): The environment running with the older version of Network Integrity. It is also the production environment of Network Integrity.
- Secondary container database (CDB) (Green environment): You must provision a new
Oracle CDB with the same CDB as the Blue environment.
Note:
PDB-level data replication using Data Guard is supported only in Oracle Database 23ai. For more information, see Oracle Data Guard documentation. - Establish Data Guard Configuration: You must implement Oracle Data Guard for real-time data replication between the Blue and Green environments to ensure that the MDS schema from production is replicated.
Staging and Validation
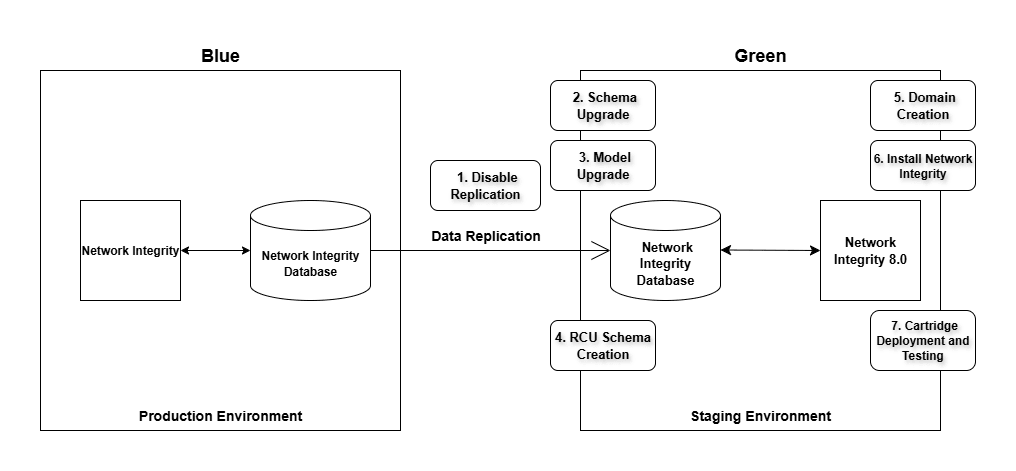
Figure 9-1 depicts the first phase of the Blue Green upgrade method.
Figure 9-1 Phase 1: Staging and Validation
To carry out the first phase of Blue Green Upgrade:
Note:
The Blue environment is the live production instance and remains online throughout the staging and validation phase. The Green environment will be configured and upgraded separately for staging and validation with the latest application version.
- Temporarily disable Data Guard replication between the Blue and Green CDBs.
- Perform the upgrade on the Green CDB to a database version compatible with NI 8.0.0.0 application version.
- Create the RCU schema using Oracle Fusion Middleware 14c RCU utility by following
the steps outlined in Installing and Configuring the Oracle Database.
Note:
- Create the RCU schema in the same PDB as the MDS-replicated data in the designated staging CDB.
- Use an RCU schema prefix that differs from the production environment prefix.
- Perform domain creation using the Oracle Fusion Middleware 14c Domain Creation
Utility by following the steps in Installing and Configuring Oracle WebLogic Server.
Note:
- Ensure that the domain configuration matches that of the production environment.
- During the domain creation process, use the newly created RCU schema from the previous step and associate it with the domain.
- Upgrade the replicated MDS schema (the production schema replicated to
the staging CDB using Data Guard) by using the Oracle Fusion Middleware 14c Schema
Upgrade Utility:
- Navigate to MW_HOME/oracle_common/upgrade/bin/ua where MW_HOME is the directory in which Oracle Fusion Middleware 14C is installed.
- Launch the UA tool to upgrade the schema.
The Welcome screen appears.
- Click Next.
The Upgrade Type screen appears.
- Select Individually Selected Schemas, and click Next.
The Available Components screen appears. It lists the available components that can be upgraded.
- Select the Oracle Metadata Section component and click
Next.
The Domain Directory screen appears.
- Select the newly created WebLogic domain directory and click
Next.
The Prerequisites screen appears.
- Confirm that the database backup is complete by selecting the following
checkboxes and click Next:
- All affected servers are down
- All affected data is backed up
- Database version is certified by Oracle for Fusion Middleware upgrade
- Certification and system requirements have been met
The MDS Schema screen appears.
- From the Database Type list, select the database.
- In the Database Connect String field, enter the value in
hostname:portnumber/ServiceName format.
Note:
For a RAC database, provide RAC Server DB Information in the following format: hostname:portnumber/ServiceName. - In the DBA User Name field, enter the database administrator user.
- In the DBA Password field, enter the password for the administrator.
- Click Connect.
If the provided details are valid, the Schema User Name and Schema Password fields become enabled.
- From the Schema User Name list, select the replicated MDS Schema.
- In the Schema Password field, enter the replicated MDS Schema
password, and click Next.
The Examine screen appears.
- Verify that all listed schemas show the status as ready for upgrade,
and then click Next.
The Upgrade Summary screen appears.
- Verify the details of the schemas to be upgraded and click
Upgrade.
The Upgrading Progress screen appears. You can monitor the progress of the upgrade from this screen.
- After the upgrade completes, click Next.
The Upgrade Success screen appears.
- Verify successful upgrade and click Close.
- Perform Model Upgrade on Replicated MDS Schema using
NIDBTools.jar file.
- Extract the jar file to a temporary directory (e.g., temp).
- Run the NIDBTools.jar file using the following command and provide
the following details when prompted:
java -jar NIDBTOOLS.jar
- In the Enter Database Hostname field: Enter the hostname of the staging database.
- In the Enter Database Port Number field: Enter the port number of the staging database.
- In the Enter Database Service Name field: Enter the service name of the staging database.
- In the Enter MDS Schema Username field: Enter the replicated MDS schema name (e.g, NISchema_MDS).
- In the Enter MDS Schema Password field: Enter the password for the replicated MDS schema.
- In the Enter DB Version to Upgrade field: Select the target version from the allowed values (7.3.6.3.0, 7.3.6.4.0, 7.4.0.0.0, 7.5.0.0.0, 7.5.0.1.0, 8.0.0.0.0). Provide 8.0.0.0.0 as the target version.
- In the Enter NIDBTools Extracted Location field: Provide the path to the temporary directory (temp) where the NIDBTools.jar file was extracted.
- Install Network Integrity 8.0 by following the instructions in Upgrading Network Integrity Using Blue Green Upgrade.
Staging Update and Production Switchover
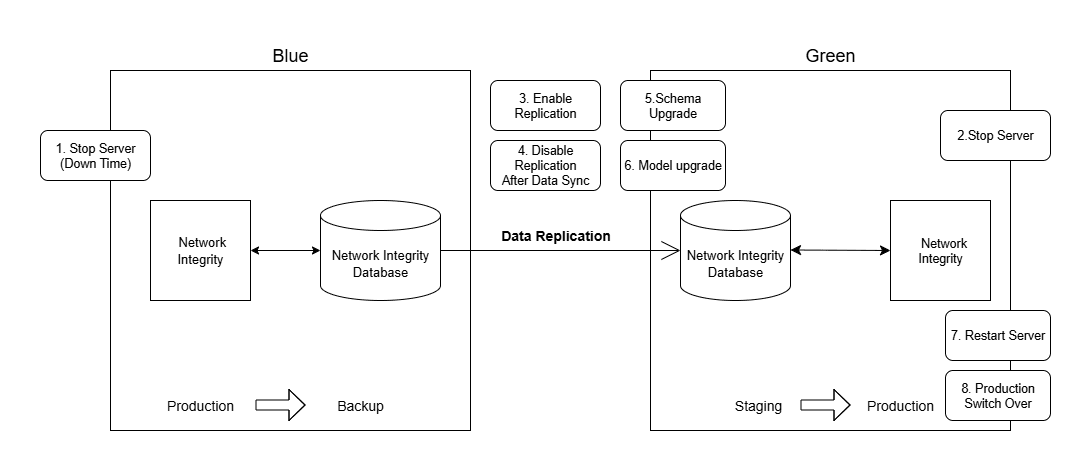
Figure 9-2 depicts the second phase of the Blue Green upgrade method.
Figure 9-2 Phase 2: Staging Update and Production Switchover
Note:
Upon completion of the staging and validation phase, the Blue environment must be taken offline, resulting in a scheduled downtime.To carry out the second phase of Blue Green Upgrade:
-
Shut down the Blue and Green application Servers.
-
Create a data dump of all newly created RCU schemas on the Green application server.
Note:
Backup of the upgraded MDS schema is not required. -
On the production CDB (Blue application server), create a new RCU schema using the Oracle Fusion Middleware 14c Repository Creation Utility (RCU) with the same schema prefix used on the Green application server.
-
Import the schema dump from the Green application server to the corresponding schema on the Blue application server.
Note:
You must perform this step because, because, when Data Guard is re-enabled, any schemas that exist on the standby (Green) but not on the primary (Blue) are removed from the standby during the resynchronization to maintain data consistency. To preserve the newly created schemas, ensure they are present on the primary before reactivating Data Guard. -
Reactivate Data Guard to synchronize the Green PDB with the most recent data from the Blue production environment.
Note:
This process will revert the Green MDS schema to the older version currently used in the production database. This step is mandatory to ensure that all the latest production data is transferred to the staging environment. - Monitor and verify that data synchronization is achieved.
- Disable Data Guard.
- Connect to the staging PDB as a SYSDBA user and manually update the
SCHEMA_VERSION_REGISTRY table for the replicated MDS schema by setting VERSION to
'12.2.1.0.0', EDITION to NULL, and UPGRADED to 'N'.
Note:
This step must be performed so that the schema upgrade utility considers the replicated MDS schema as eligible for upgrade. - Perform the schema upgrade again on the replicated MDS schema by following the step 5 of the Staging and Validation phase.
- Perform the model upgrade again on the replicated MDS schema as described in 6 of the Staging and Validation phase.
- Restart all Green environment servers after clearing the tmp files and cache from each server.
- Redeploy all the latest 8.0.0.0 cartridges that were deployed during the Blue-Green upgrade and perform Sanity Test.
- Redirect production traffic to the upgraded Green environment by updating the production URLs accordingly.
Once this phase is completed, the Green environment will function as the new production environment.
Upgrading the Blue Environment
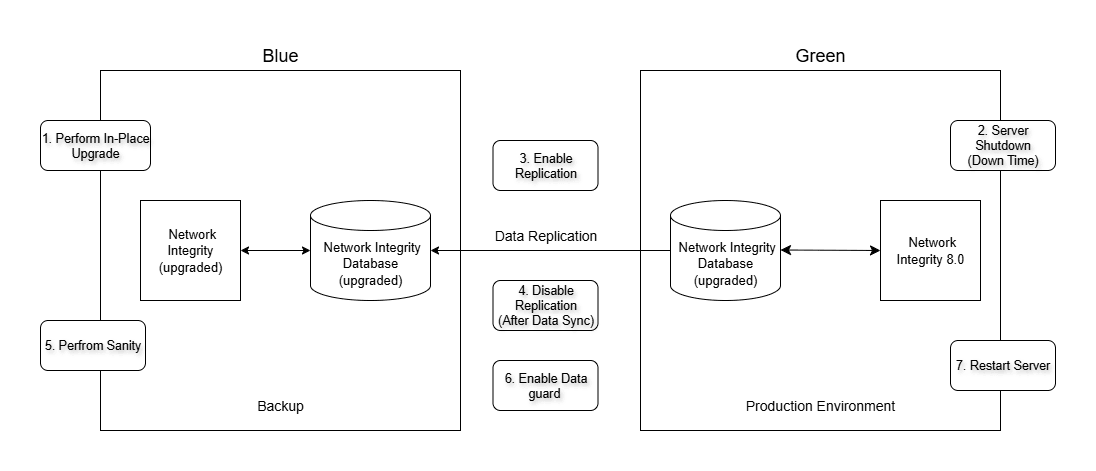
Figure 9-3 depicts the third phase of the Blue Green upgrade method.
Figure 9-3 Phase 3: Upgrading the Blue Environment
After completing the second phase of the Blue Green upgrade, the Green environment functions as the active production environment. The Blue environment will function as backup once the upgrade and data synchronization is completed.
To upgrade the Blue environment:
- Upgrade the Blue environment using the in-place upgrade steps outlined in In-Place Upgrade.
- Shut down the Green Environment servers.
Note:
This process requires downtime for the production setup running on the Green environment. You must plan an appropriate downtime window and complete all the following steps during this period. - Initiate Data Guard replication from Green to Blue environments to synchronize all data changes.
- Suspend Data Guard replication once synchronization is completed.
- Test the Blue environment to make sure everything works correctly.
- Shut down Blue environment server and keep it as a backup.
- Enable Data Guard replication from Green to Blue environments.
- Start the Green environment for production use.
After completing these steps, the Green environment will operate as the primary production setup, while the Blue environment functions as the standby or backup.
Upgrading Network Integrity Using Blue Green Upgrade
Blue Green Upgrade Using Interactive Install
To upgrade Network Integrity using Interactive installer (using Blue Green method):
- Create a directory (dir).
- Download the Network Integrity Installer software from the Oracle software delivery website and save it to dir:
- Export JDK Home by running one of the following command. See Software Requirements for JDK version information.
export JAVA_HOME=$JDK_HOME
- Run the Oracle Nextgen Network Integrity Installer using the following
command:
java -jar NetworkIntegrityInstaller_{release}.jarThe Installer Welcome screen appears.
- Click Next.
- One of the following screens is displayed:
- If Network Integrity is the first Oracle product that you are installing on
the system, the Specify Inventory directory and credentials screen
appears.
Enter the full path of the inventory directory, select the Operating System group name, and then click Next .The Installation Location Screen appears.
-
If you have installed any Oracle products on the system prior to installing Network Integrity, the The Installation Location Screen appears.
- If Network Integrity is the first Oracle product that you are installing on
the system, the Specify Inventory directory and credentials screen
appears.
- In NI_Home field, enter or browse the path to the folder where you want to
install Network Integrity and click Next.
The Installation Type Screen appears.
-
Select Complete and click Next.
The WebLogic Administration Server Connection Information screen appears.
- Do the following:
- In the Host Name field, enter the IP address or the host name of the Administration
- In the Port Number field, enter the Administration Server port
- In the User Name field, enter user name with which you connected to the Administration Server.
- In the Password field, enter the password for the user name that you provided in the User Name field.
- Select or deselect the Use SSL checkbox as per your requirements.
- In the Keystore field, enter the keystore location if the Use SSL checkbox is selected.
-
Click Next.
The Target Selection screen appears
-
Select the option for the server, or cluster, where you want to deploy Network Integrity, and click Next.
The DB Type Selection Page appears.
Note:
If you select cluster option, ensure that all the managed servers are running.
- In the Database Type Selection screen, select the same database type as used in the
Blue side production environment
- If the Standard Oracle Enterprise Database option is selected. the
Standard DB Connection screen appears.
- In the Host Name field, enter the IP address or the host name of the system where the standby database is installed.
- In the Port Number field, enter the port number with which the installer connects to the standby database.
- In the User Name field, enter the user name of the standby database, SYSDBA.
- In the Password field, enter the password for the user name that you provided in the User Name.
- In the Service name field, enter the service name that uniquely identifies your database on the system.
- Click Next.
The NI Schema Table Creation screen appears.
- If the Oracle Real Application Cluster Database option is selected,
the RAC DB Connection screen appears.
- In the RAC Database Connection String field, enter the
connection details to connect to the Oracle RAC database of standby
Database.
For example:
HOST NAME1:PORT1:SERVICE NAME1,HOST NAME2:PORT2:SERVICE NAME2
-
In the User Name field, enter the user name for the Oracle RAC database SYSDBA.
-
In the Password field, enter the password for the user name that you provided in the User Name field.
-
Click Next.
The Network Integrity Schema Table Creation screen appears.
- In the RAC Database Connection String field, enter the
connection details to connect to the Oracle RAC database of standby
Database.
- If the Standard Oracle Enterprise Database option is selected. the
Standard DB Connection screen appears.
- Select No and click Next.
The MDS Schema User Connection screen appears.
-
Do the following:
- In the Schema User Name field, enter the name for the MDS schema
- In the Schema User Password field, enter the password for the MDS schema user to access the schema.
- Click Next.
The Security Provider Selection screen appears.
Caution:
You need to use the replicated MDS schema which got updated.
- Select the type of security provider you want to use by performing one of the
following steps:
- If you select Embedded_LDAP option, the Admin User Creation screen
appears.
(Optional) Do the following:
- In the User Name field, enter the user name for accessing and using Network Integrity.
-
In the Password field, define a password for the Network Integrity.
Note:
The password requirements are as follows:- Password length must be between 8 to 12 characters.
- It should contain at least one uppercase letter, one lowercase letter, one number and one special character.
- It must not contain the username either directly or in reverse.
- You may use a character 3 times in a row maximum, but not more than 4 times in total.
-
In the Confirm Password field, enter the password again to confirm it.
- Click Next. The Internal user Creation screen appears.
- If you select External Security Provider, the External Security
Provider Connection Information screen appears.
Do the following:
- In the LDAP Server Host Name field, enter the host name for the external LDAP
- In the LDAP Server Port Number field, enter the port number for the external LDAP server.
- In the LDAP Server User Name field, enter the user name for the external LDAP
- In the LDAP Server Password field, enter the password for the external LDAP
- In the User Base DN field, enter the user base
- In the Group Base DN field, enter the group base.
- Click Next.
the Internal user Creation screen appears.
- If you select Other Security Provider, and click Next, the Disable unsecured Port screen appears. Proceed directly to step 16.
- If you select Embedded_LDAP option, the Admin User Creation screen
appears.
- In Internal user Creation Screen, do the following:
-
In the User Password field, define a password for the Network Integrity internal user.
Note:
The password requirements are as follows:- Password length must be between 8 to 12 characters.
- It should contain at least one uppercase letter, one lowercase letter, one number and one special character.
- It must not contain the username either directly or in reverse.
- You may use a character 3 times in a row maximum, but not more than 4 times in total.
- In the Confirm The User Password field, enter the password again to confirm it.
- Click Next.
The Disable Unsecured Listen Port screen appears.
-
- Select whether to disable the unsecured listen port by doing one of
the following:
- Select Yes if you are configuring Network Integrity to communicate and listen over SSL-enabled ports only, by disabling non-SSL Ports.
- Select No if you are configuring Network Integrity to communicate and listen over both SSL and non-SSL ports.
- Click Next.
The Java Home Location screen appears.
-
Accept the default settings and click Next.
The Installation Summary screen appears.
-
Review the content in the summary and click Next.
The Installation Progress Screen appears.
-
You can view the installation progress.
Note:
During the installation progress, two pop-up messages will appear. The first message asks for confirmation to stop the WebLogic Servers and the second message lists the order in which the servers must be manually restarted. Click OK on both the messages to continue.
-
On successful installation of Network Integrity, the Installation Complete screen appears.
-
Click Exit to close the Installation Wizard.
- To start the server, do the following:
- Start the AdminServer using the following
command:
./startNI.sh
- If your are using Cluster environment ,Start the managed servers, using the
following
command:
./startNI.sh cluster_managed_server_name admin_server_URL
- Start the AdminServer using the following
command:
- Open the following file once the installation is complete, to get the URL to access Network Integrity: NI_Home/install/readme.txt, where NI_Home is the directory where Network Integrity is installed.
-
Copy the URL and paste it in the browser window's address field and press Enter to access Network Integrity.
You can access Network Integrity.
For more information on verifying the successful installation of Network Integrity, see Verifying the Network Integrity Installation.
After verifying a successful installation, perform the required post-installation actions. For more information, see Network Integrity Post-Installation Tasks.
Blue Green Upgrade Using Silent Mode
You can use the silent install mode when you are installing Network Integrity using the same configuration repeatedly. The silent mode does not use the GUI and runs in the background.
About the Response File
The Network Integrity installer uses a response file, which contains a pre-defined set of values, such as server connection details. The response file comes in a template form to install Network Integrity in silent mode.
The following response file templates come as part of the Network Integrity installation package: oracle.communications.integrity.rsp
The response file templates contain all the fields that the installer requires to perform installation in silent mode
When you extract the installer JAR file, the response file templates are saved in the Response directory at the following location: Disk1/stage/Response.
Table 9-2 describes the Network Integrity response file template properties, along with the values that should be specified for a complete installation scenario.
Table 9-2 Response File Template Properties
| Response File Template Name | Property Name | Description (with Default Value) |
|---|---|---|
| Installation Location Details (Required) | ORACLE_HOME | Directory path where the NI application will be installed |
| Installation Type Details (Required) | INSTALLATION_TYPE | Type of installation (Allowed values: Complete or Upgrade). Set "Complete" for Blue Green Upgrade . |
| WebLogic Admin Server Connection Details (Required) | APP_ADMIN_HOST | Hostname or IP address of the WebLogic Admin Server |
| WebLogic Admin Server Connection Details (Required) | APP_ADMIN_PORT | Port number for the WebLogic Admin Server (enclose in double quotes). For SSL-based deployment, provide the SSL port value and specify the keystore file location in the APP_SERVER_KEYSTORE property. |
| WebLogic Admin Server Connection Details (Required) | APP_SERVER_USER | Username for the WebLogic Admin Server |
| WebLogic Admin Server Connection Details (Required) | APP_SERVER_PASSWD | Password for the WebLogic Admin Server |
| WebLogic Admin Server Connection Details (Required) | APP_SERVER_KEYSTORE | Path to the keystore file required for SSL-based deployment (e.g., certs/Keystore.jks) |
| Target Selection Details (Required) | APP_TARGET_NAME | Name of the target (such as AdminServer or CL1) where the NI application will be installed |
| Database Selection Details (Required) | DATABASE_TYPE | Type of database used (Accepted values: Standard Oracle Enterprise Database or Oracle Real Application Cluster Database).Use the Same Type used in Production environment. |
| Standard DB Details (Required only if DATABASE_TYPE = Standard Oracle Enterprise Database) | DB_HOST_NAME | Hostname of the standard Oracle database |
| Standard DB Details (Required only if DATABASE_TYPE = Standard Oracle Enterprise Database) | DB_HOST_PORT | Port number of the standard Oracle database (enclose in double quotes) |
| Standard DB Details (Required only if DATABASE_TYPE = Standard Oracle Enterprise Database) | DB_USER_NAME | Username with SYSDBA privileges for the standard Oracle database |
| Standard DB Details (Required only if DATABASE_TYPE = Standard Oracle Enterprise Database) | DB_PASSWORD | Password for the SYSDBA user of the standard Oracle database |
| Standard DB Details (Required only if DATABASE_TYPE = Standard Oracle Enterprise Database) | DB_SERVER_SERVICE | Service name of the standard Oracle database |
| RAC DB Details (Required only if DATABASE_TYPE = Oracle Real Application Cluster Database) | RAC_CONNECTION_STRING | Connection string details for Oracle RAC, in the format: HostName1:Port1:Service1,HostName2:Port2:Service2 |
| RAC DB Details (Required only if DATABASE_TYPE = Oracle Real Application Cluster Database) | RAC_SERVER_USER | Username for connecting to the Oracle RAC database |
| RAC DB Details (Required only if DATABASE_TYPE = Oracle Real Application Cluster Database) | RAC_SERVER_PASSWORD | Password for the Oracle RAC database server |
| Network Integrity Schema Table Creation (Required only if INSTALLATION_TYPE=Complete) | DB_SCHEMA | Flag to indicate whether to create the app schema table (Allowed values: “true” or “false”). For Blue Green Upgrade installation, provide “false” |
| MDS Schema Information Details (Required) | SCHEMA_OWNER_NAME |
Username for the MDS (Metadata Services) Note: Details of Replicated upgraded MDS schema Details |
| MDS Schema Information Details (Required) | SCHEMA_OWNER_PASSWD |
Password for the MDS (Metadata Services) schema user Note: Details of Replicated upgraded MDS schema Details |
| Security Provider Selection Details | SECURITY_PROVIDER_NAME | Type of security provider to select (Allowed values: Embedded_LDAP or External_LDAP) |
| Embedded LDAP Details (User creation is optional; values can be left empty even if SECURITY_PROVIDER_NAME is set to Embedded LDAP) | LDAP_USER_NAME | Username to be created in the embedded LDAP directory |
| Embedded LDAP Details (User creation is optional; values can be left empty even if SECURITY_PROVIDER_NAME is set to Embedded LDAP) | LDAP_PASSWD |
Password for the newly embedded LDAP user Note: Password Requirements: · Length must be between 8 to 12. · It should contain at least one uppercase letter, one lowercase letter, one number and one special character. · It must not contain username directly or in reverse · No character can appear more than 4 times in total or more than 3 times in a row. |
| External LDAP Details (Required only if SECURITY_PROVIDER_NAME=External LDAP) | LDAP_SERVER_HOST | Hostname of the external LDAP server |
| External LDAP Details (Required only if SECURITY_PROVIDER_NAME=External LDAP) | LDAP_SERVER_PORT | Port number of the external LDAP server |
| External LDAP Details (Required only if SECURITY_PROVIDER_NAME=External LDAP) | LDAP_SERVER_USER | Username for connecting to the external LDAP server |
| External LDAP Details (Required only if SECURITY_PROVIDER_NAME=External LDAP) | LDAP_SERVER_PASSWORD | Password for the external LDAP server user |
| External LDAP Details (Required only if SECURITY_PROVIDER_NAME=External LDAP) | LDAP_USER_BASE_DN | User BASE DN information of external LDAP server |
| External LDAP Details (Required only if SECURITY_PROVIDER_NAME=External LDAP) | LDAP_GROUP_BASE_DN | Group BASE DN information of external LDAP server |
| External LDAP Details (Required only if SECURITY_PROVIDER_NAME=External LDAP) | LDAP_SERVER_KEYSTORE | Path to the keystore file for the external LDAP server (e.g., certs/externalLDAPKeystore.jks) |
| NI Internal user Details (Required) | LDAP_DEF_USER_PASSWD |
Password for the NI internal user Password Requirement: Length must be between 8 to 12. · It should contain at least one uppercase letter, one lowercase letter, one number and one special character. · It must not contain username directly or in reverse · No character can appear more than 4 times in total or more than 3 times in a row. |
| Disable Non-SSL Port Option (Required) | DISABLE_NONSSLPORT | Option to disable the non-SSL port (Allowed Values: set to “true” to disable, or “false” to keep enabled) |
Note:
Before using the response file, ensure that any optional properties or values not required by the installer are left empty.Starting Silent Mode Installation
Before you begin installing Network Integrity in silent mode, ensure that you have provided all required input values in the response file template.
To upgrade Network Integrity in silent mode (using Blue Green method):
- Export JDK Home by running the following command. See Software Requirements for JDK version information.
export JAVA_HOME=$JDK_HOME
- Use the following command to start the silent installer, here absolute_path
is the fully qualified response file
location:
java -jar NetworkIntegrityInstaller_{release}.jar -responseFile {absolute_path}The installation runs silently in the background.
Note:
The installer shuts down all of the servers, including the Administration Server and the Managed Serversm after silent installation. You must start all of the servers manually after the installation is complete. - At the end of the installation, the command window displays the location of the installer log files. Users can review these logs to verify that the installation was successful.
- To start the server, do the following:
- Start the AdminServer, using the following
command:
./startNI.sh
- If your are using a Cluster environment, start the managed servers using the
following
command:
./startNI.sh cluster_managed_server_name admin_server_URL
- Start the AdminServer, using the following
command:
- Open the following file once the installation is complete to get the URL to access
Network Integrity: NI_Home/install/readme.txt
Where NI_Home is the directory where Network Integrity is installed.
-
Copy the URL and paste it in the browser window's address field and press Enter to access Network Integrity.
You can access Network Integrity.
For more information on verifying the successful installation of Network Integrity, see Verifying the Network Integrity Installation.
After verifying a successful installation, perform the required post-installation actions. For more information, see Network Integrity Post-Installation Tasks.
Migrating Cartridges
If you developed or extended cartridges for the old version of Network Integrity, you must migrate them to the new version of Network Integrity to continue to use them.
Production cartridges (those with binaries supplied by Oracle) are already compatible with and can be deployed to the new version of Network Integrity.
Migrate your old custom cartridges to be compatible with the new version of Network Integrity using the Design Studio Cartridge Migration Tool. See "Getting Started with Design Studio for Network Integrity (1)" in Design Studio Platform Online Help for more information.
The procedure for migrating cartridges assumes you have two Design Studio environments: one for the old version of Network Integrity, and one for the new version of Network Integrity.
Ensure the imported project is not read-only. The cartridge migration will fail if the project is read-only.
It is important to make sure that all the dependent projects exist in the workspace before importing a Network Integrity project. The migration tool will automatically set the dependencies when migrating Network Integrity projects, if the dependent projects exist in the workspace. If multiple projects are imported into Design Studio at the same time, move the dependent project to the top of the order in the cartridge upgrade dialog, so that the dependent project will be migrated first.
To migrate a custom cartridge (a cartridge with binaries not supplied by Oracle):
-
Using the old Design Studio environment for Network Integrity, do the following:
-
Select the Design Studio perspective.
-
Select the Studio Projects view.
-
Select the cartridge project and, from the Project menu, deselect Build Automatically.
-
From the Project menu, select Clean.
-
Select the Navigation view.
-
Right-click the cartridge project folder and select Close Project.
-
-
Using the new installation of Design Studio for Network Integrity, do the following:
-
Select the Design Studio perspective.
-
Select the Studio Projects view.
-
Right-click anywhere in the Studio Projects view and select Import.
The Import Project dialog box appears.
-
Verify that the imported project is not “read-only."
-
Locate the cartridge project and import it.
-
Double-click the cartridge project folder.
The cartridge properties appear.
-
Verify that the Target Version field value matches the Network Integrity version.
Note:
If the Target Version field is not editable, it may mean that the cartridge is sealed, read-only, or under source control.
-
Perform all necessary pre-build steps particular to your cartridge.
-
From the Project menu, enable Build Automatically.
-
From the Project menu, select Clean.
The cartridge project is automatically built. The binary file is produced and written to the cartridgeBin directory.
-
About Rolling Back Network Integrity
If the Installer fails to successfully upgrade Network Integrity, you must manually restore the WebLogic server domain, the database schema, and the database domain. See "Network Integrity System Administration Overview" in Network Integrity System Administrator's Guide for more information about restoring the database. See your WebLogic Server documentation for more information about restoring the WebLogic Server domain.