5 About Integrating Offline Mediation Controller REST Services Manager with Cloud Native
You can integrate an external application with Oracle Communications Offline Mediation Controller cloud native by using Offline Mediation Controller REST Services Manager (RSM).
About Offline Mediation Controller REST Services Manager
- Manage Nodes
- Manage Node Managers
- Retrieve a list of node chains
- Compile and save the NPL rules file
- Export node configurations and customizations
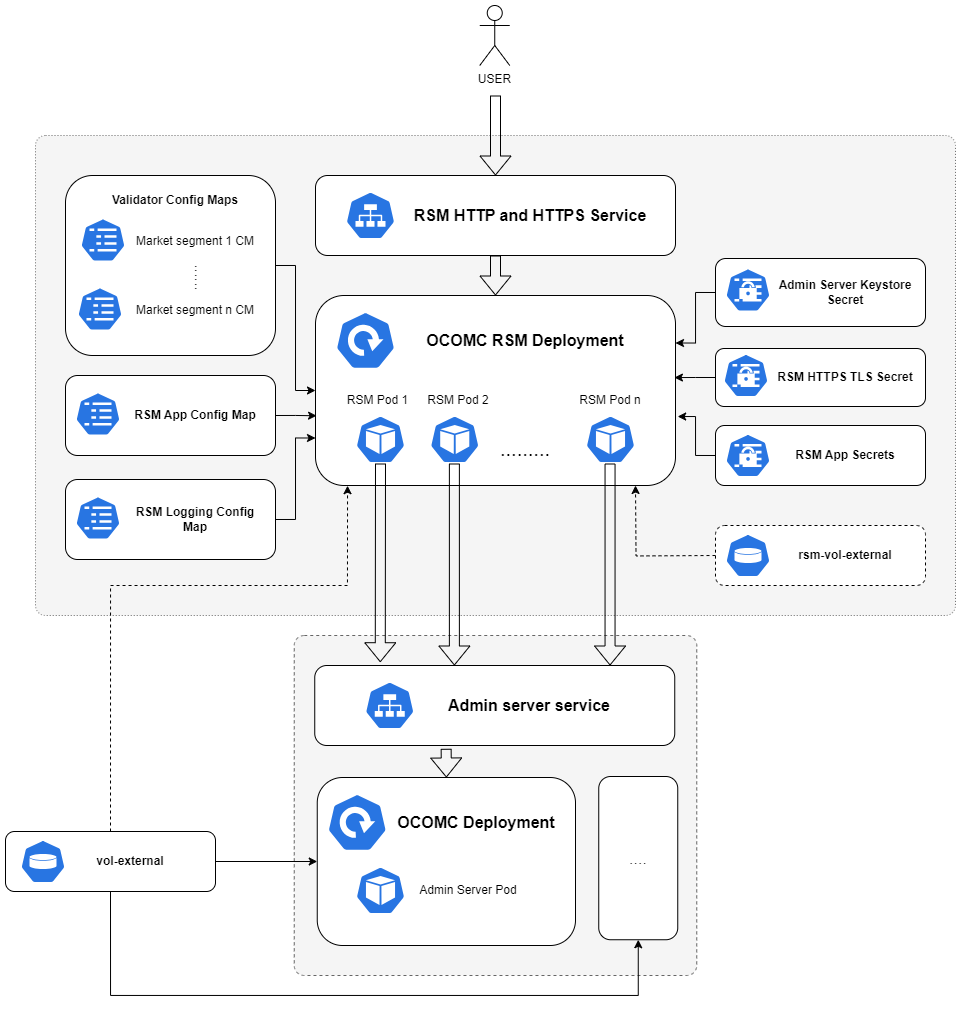
About Offline Mediation Controller REST Services Manager (RSM) Cloud Native Architecture
Figure 5-1 Offline Mediation Controller REST Services Manager (RSM) Cloud Native Architecture
- RSM Deployment: The primary deployment of RSM with all the necessary components and configurations.
- RSM HTTP and HTTPS Service: This service exposes RSM to ports, allowing access to RSM through HTTP and HTTPS protocols.
- Validator ConfigMap: There is a unique ConfigMap for each market segment.
- RSM App ConfigMap: The ConfigMap contains the application.yaml file, which holds the configurations required to initiate the RSM server.
- RSM Logging ConfigMap: The ConfigMap holds the log4j2.yaml file, encompassing logging-related configurations.
- Admin Server Keystore Secret: This secret contains the administration server KeyStore file in a Base64-encoded format.
- RSM HTTPS TLS Secret: This secret contains the HTTPS TLS store utilized by RSM when the HTTPS protocol is enabled.
- RSM App Secret: This secret contains all confidential information necessary to launch the RSM server.
- vol-external: This is an optional PV reference. RSM will incorporate it only if the flag rsm.pvc.ocomcExternal.enabled in the override-values.yaml file is set to true. When enabled, the RSM will share the vol-external PV of the OCOMC core deployment. It is mandatory to enable this flag if the node chain solution includes cartridges containing sensitive information such as FTP or database passwords.
- rsm-vol-external: This PV is optional and can be enabled by setting the flag rsm.pvc.external.enabled to true in the values.yaml file. When enabled, the RSM will load custom cartridges from the specified PV into the classpath. The source directory for it can be configured in the override-values.yaml file.
Installing Offline Mediation Controller REST Services Manager
The Offline Mediation Controller REST Services Manager can be installed along with core Offline Mediation Controller components using a unified Helm chart.
- Configure and install all required third-party software. See "Setting Up Prerequisite Software".
- Configure the Offline Mediation Controller server and REST Services Manager connection. See "Configuring the Offline Mediation Controller Core and REST Services Manager Connection".
- Configure the RSM server. See "Configuring the REST Services Manager (RSM) Server".
- Load custom validators. See "Configuring and Loading Custom Validators".
- Deploy Offline Mediation Controller REST Services Manager. See "Deploying Offline Mediation Controller Services".
Setting Up Prerequisite Software
- Ensure that you have downloaded the latest software that is compatible with Offline Mediation Controller cloud native. See "Offline Mediation Controller Cloud Native System Requirements" in Offline Mediation Controller Compatibility Matrix.
- Ensure that your environment setup is complete. See "Setting Up Your Environment".
- Download the Offline Mediation Controller cloud native Helm chart. See "Downloading Packages for the Offline Mediation Controller Cloud Native Helm Charts".
Configuring the Offline Mediation Controller Core and REST Services Manager Connection
- In your override-values.yaml file for oc-cn-ocomc, set the
following keys:
- ocomcRSM.rsm.adminServerConnection.hostname: Specify the hostname where the Offline Mediation Controller Admin Server is running.
- ocomcRSM.rsm.adminServerConnection.port: Specify the port where Offline Mediation Controller Admin Server listens.
- If Offline Mediation Controller core uses SSL, do the following:
- Copy your adminClientTruststore.jks file from the vol-keystore PV of Offline Mediation Controller core to the oc-cn-ocomc/rsm/ocomc-rsm-keystore directory.
- In your override-values.yaml file, set the following
keys:
- ocomcRSM.rsm.adminServerConnection.ssl.enabled: Set this key to true. This enables SSL between REST Services Manager and the Admin Server.
- ocomcRSM.rsm.adminServerConnection.ssl.keystoreName: Specify the name of your KeyStore file, such as adminClientTruststore.jks.
- If authentication is enabled for Offline Mediation Controller core,
set the following keys in your override-values.yaml file:
- ocomcRSM.rsm.adminServerConnection.username: Specify the user name for logging in to the Admin Server.
- ocomcRSM.rsm.adminServerConnection.password: Specify the password for logging in to the Admin Server.
Configuring the REST Services Manager (RSM) Server
- Enable HTTPS in RSM by doing the following:
- Copy your generated .p12 KeyStore file to the RSM Helm chart directory (oc-cn-ocomc/charts/oc-cn-ocomc-rsm/ocomc-rsm-keystore).
- Set the following keys in your override-values.yaml
file for oc-cn-ocomc:
- ocomcRSM.rsm.https.enabled: Set this to true.
- ocomcRSM.rsm.https.ketsotreName: Specify the name of the KeyStore file with the extension.
- ocomcRSM.rsm.https.keystorePassPhrase: Specify the KeyStore passphrase.
- Expose RSM through a NodePort by setting the following keys in your
override-values.yaml file:
- ocomcRSM.rsm.service.type: Set this to NodePort.
- ocomcRSM.rsm.service.nodePort: Specify the port number.
- ocomcRSM.rsm.https.service.nodePort: If the HTTPS port is enabled, specify the port for exposing the HTTPS port outside the cluster.
- Enable Oracle Access Management Auth by setting the following keys
in your override-values.yaml file:
- ocomcRSM.rsm.security.provider: Set this to OAM.
- ocomcRSM.rsm.security.configuration.oam: Fill in the Oracle Access Management and Oracle Unified Directory configuration details.
- Set the log levels to the appropriate level in the ocomcRSM.rsm.logging.packagingLogging keys in your override-values.yaml file.
Configuring and Loading Custom Validators
In Offline Mediation Controller REST Services Manager, you can configure custom validators.
- Enable custom validators for Offline Mediation Controller RSM. In your override-values.yaml file for oc-cn-ocomc, set the ocomcRSM.rsm.customisation.nodeConfigValidator.validators.enabled key to true.
- Create a subdirectory within the RSM Helm chart directory (oc-cn-ocomc-rsm/ocomc-rsm-validator) with the name of the market segment for the validator. For example, create a directory named oc-cn-ocomc-rsm/ocomc-rsm-validator/my-market.
- Copy the validator YAML files into the directory created in the previous step.
- In your override-values.yaml file, set the ocomcRSM.rsm.customisation.nodeConfigValidator.validators.marketSegments key to a list of supported market segments.
About the Offline Mediation Controller REST Services Manager Keys
Table 5-1 Offline Mediation Controller REST Services Manager Keys
| Key | Path in values.yaml file | Description |
|---|---|---|
|
imagePullSecrets |
- |
The location of your imagePullSecrets, which stores the credentials (or Secret) for accessing your private Docker registry. |
|
name |
ocomcRSM.rsm |
The name to use for the deployment. The final name of the deployment is derived using the name provided. |
|
fullname |
ocomcRSM.rsm |
The final name of the deployment to use. This would be used for the deployment without any modification. |
|
replicas |
ocomcRSM.rsm |
The total number of RSM pods to run in the deployment. |
|
restartCount |
ocomcRSM.rsm |
Tracks the number of restarts. To restart the pods, increment the value by 1 and run the helm upgrade command. |
|
annotations |
ocomcRSM.rsm |
The custom annotations to add to the deployment (should be a key-value pair). |
|
additionalLabels |
ocomcRSM.rsm |
The custom labels to add to the deployment (should be a key-value pair). |
|
nodeSelectors |
ocomcRSM.rsm |
The node selector to use for the deployment. |
|
imageRepository |
ocomcRSM.rsm.container |
The repository from where the RSM image can be pulled. Note: The repository URI should not end with a trailing slash. |
|
imagePullPolicy |
ocomcRSM.rsm.container |
The image pull policy to use for the deployment. The default value is IfNotPresent, which specifies not to pull the image if it's already present. Applicable values are IfNotPresent and Always. |
|
image |
ocomcRSM.rsm.container |
The RSM image name and tag concatenated with a colon (:). Ensure to align with the RSM image version to be deployed. |
|
enabled |
ocomcRSM.rsm.https |
Whether RSM should run with HTTPS. |
|
keystoreName |
ocomcRSM.rsm.https |
The KeyStore file name with its extension to use for HTTPS. The file must be present in the oc-cn-ocomc-rsm/ocomc-rsm-keystore directory. |
|
keystorePassPhrase |
ocomcRSM.rsm.https |
The passphrase for the HTTPS KeyStore file. |
|
service.nodePort |
ocomcRSM.rsm.https |
The node port to use for HTTPS service. This would be used when the service type of RSM is set to NodePort. |
|
hostname |
ocomcRSM.rsm.adminServerConnection |
The host name for accessing the admin server. |
|
port |
ocomcRSM.rsm.adminServerConnection |
The port at which the admin server is listening on. |
|
username |
ocomcRSM.rsm.adminServerConnection |
The user name to use for logging into the admin server. |
|
password |
ocomcRSM.rsm.adminServerConnection |
The password for the specified user to use during login. |
|
ssl.enabled |
ocomcRSM.rsm.adminServerConnection |
Whether Offline Mediation Controller core is SSL enabled. |
|
ssl.keystoreName |
ocomcRSM.rsm.adminServerConnection |
If Offline Mediation Controller Core is SSL enabled, specify the admin-server TrustStore file name, including its extension, to use during the connection to the admin server. The file must be present in the oc-cn-ocomc-rsm/ocomc-rsm-keystore directory. By default, the TrustStore in Offline Mediation Controller core can be copied from OMC_home/config/GUI/adminClientTruststore.jks. |
|
testNodeChain.enabled |
ocomcRSM.rsm |
Whether node chain testing is enabled (true) or not (false). The default is false. |
|
ocomcExternal.enabled |
ocomcRSM.rsm.pvc |
Whether RSM shares the same external PV of the Offline Mediation Controller core. Enabling this is mandatory when RSM is involved in creating node chain solutions involving cartridges with sensitive password information (FTP or database passwords). The mount path is /app/volumes/ocomc-ext. |
|
ocomcExternal.name |
ocomcRSM.rsm.pvc |
The name of the external volume in Offline Mediation Controller Core. |
|
external.enabled |
ocomcRSM.rsm.pvc |
Whether to create an external PV for RSM. The mount path is /app/volumes/ext. |
|
external.name |
ocomcRSM.rsm.pvc |
The name for RSM's external volume. |
|
external.accessModes |
ocomcRSM.rsm.pvc |
The access mode to use for RSM's external PV. |
|
external.storage |
ocomcRSM.rsm.pvc |
The storage to use for the RSM's external PV. |
|
name |
ocomcRSM.rsm.storageClass |
The storage class to use if RSM's external PV is enabled. |
|
cartridgeFolder |
ocomcRSM.rsm.configEnv |
The directory path where RSM retrieves and loads cartridges from. |
|
nodeTypeMapper.enabled |
ocomcRSM.rsm.customisation |
Whether to load custom nodeMappers into RSM. The content of the file needs to be added to oc-cn-ocomc-rsm/templates/configmap-nodetypemapper.yaml. |
|
nodeConfigValidator.enableCache |
ocomcRSM.rsm.customisation |
Whether caching should be enabled to the Node Config Validator. |
|
nodeConfigValidator.validators.enabled |
ocomcRSM.rsm.customisation |
Whether to load custom validators into RSM. |
|
nodeConfigValidator.validators.marketSegments |
ocomcRSM.rsm.customisation |
The list of market segments of the validators to load. The name must map to a directory in the oc-cn-ocomc-rsm/ocomc-rsm-validator directory. |
|
nodeTypeMetadata.enabled |
ocomcRSM.rsm.customisation |
Whether to load custom node type metadata files into RSM. |
|
nodeTypeMetadata.marketSegments |
ocomcRSM.rsm.customisation |
The list of market segments of the metadata node to load. The name must map to a directory in the oc-cn-ocomc-rsm/ocomc-rsm-metadata directory. |
|
additional labels |
ocomcRSM.rsm.service |
The custom labels to add for the service. |
|
additionalAnnotation |
ocomcRSM.rsm.service |
The custom annotations to add for the deployment. |
|
service.type |
ocomcRSM.rsm.service |
The Kubernetes service type to use. |
|
nodePort |
ocomcRSM.rsm.service |
The NodePort that RSM should be exposed to, if service type is set to NodePort. |
|
provider |
ocomcRSM.rsm.security |
The security provider for user authentication. |
|
clientId |
ocomcRSM.rsm.security.configuration.oam |
The Oracle Access Management (OAM) application client ID. |
|
clientSecret |
ocomcRSM.rsm.security.configuration.oam |
The OAM application client secret. |
|
tokenEndpointUri |
ocomcRSM.rsm.security.configuration.oam |
The OAM token endpoint URI. |
|
authorizationEndpointUri |
ocomcRSM.rsm.security.configuration.oam |
The OAM authorization endpoint URI. |
|
introspectEndpointUri |
ocomcRSM.rsm.security.configuration.oam |
The OAM introspect endpoint URI. |
|
oauthIdentityDomainName |
ocomcRSM.rsm.security.configuration.oam |
The OAM client's identity domain name. |
|
oudHostName |
ocomcRSM.rsm.security.configuration.oam |
The Oracle Unified Directory (OUD) server's host name. |
|
oudAdminUserName |
ocomcRSM.rsm.security.configuration.oam |
The OUD server's administration user name. |
|
oudAdminUserPassword |
ocomcRSM.rsm.security.configuration.oam |
The OUD server's administration user password. |
|
oudHttpPort |
ocomcRSM.rsm.security.configuration.oam |
The OUD HTTP port. |
|
oudHttpsPort |
ocomcRSM.rsm.security.configuration.oam |
The OUD HTTPS port. |
|
oudUsersBaseDn |
ocomcRSM.rsm.security.configuration.oam |
The user's base DN in OUD. |
|
oudGroupsBaseDn |
ocomcRSM.rsm.security.configuration.oam |
The group's base DN in OUD. |
|
jvmOpts |
ocomcRSM.rsm |
The required JVM configuration for RSM. |
|
terminationGracePeriodSeconds |
ocomcRSM.rsm |
The termination grace period for the pod. This is optional. |
|
format.type |
ocomcRSM.rsm.logging |
The logging layout to use. The value should be a supported log4j logging layout. |
|
format.pattern |
ocomcRSM.rsm.logging |
The logging pattern to use. |
|
rootLevel |
ocomcRSM.rsm.logging |
The RSM's root logging level. |
|
packageLogging |
ocomcRSM.rsm.logging |
The logging levels specific to individual packages. |