10 Activity Logs
Oracle® Communications Security Shield Cloud Service (Security Shield) Activity logs provide a view of user activity to help with troubleshooting and audits. You can see logged activity such as configuration changes to access control lists, threshold parameters, and on-premises software components.
Activity Log Controls and Actions
The Oracle® Communications Security Shield Cloud Service (Security Shield) Activity Log displays logged information in categories, which you can search for details. Security Shield creates the logs while registering a Session Border Controller (SBC) or the Cloud Communication Service (CCS) or when unregistering an SBC or CCS for a tenant.
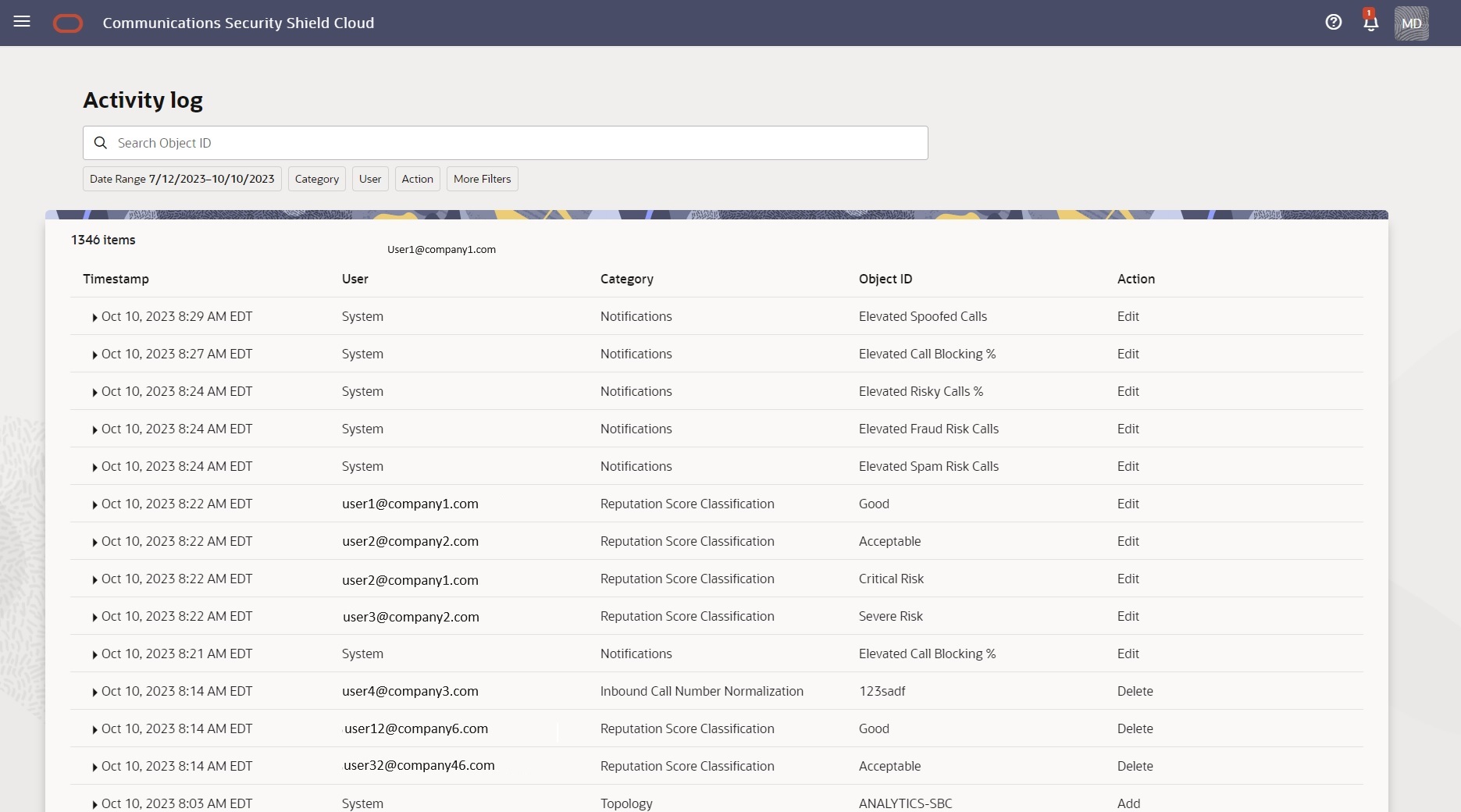
The following screen capture shows the Activity Log page. The Activity Log can display up to 1,050 logs, which you can view by scrolling down the table.
Activity Log Triggers
- Call Type Classifications and Reputation Score Classifications—When a user changes the enforcement action.
- Access Control Lists—When a user creates, edits, or deletes and Access Control List.
- Notifications—When a user enables or disables notifications and when the system triggers alerts.
- Automatic Threat Protection—When a user updates thresholds.
- Outbound Number Management—When a user modifies outbound numbers and settings.
- Number Normalization—When a user enables or disables number normalization fields.
Activity Log Column Descriptions
- Timestamp—Shows the date, time, and time zone of the log entry.
- User—Shows the name or email address of the user who performed the action on the date of the timestamp.
- Category—Shows the log category. Access Control Lists | Autonomous Threat Protection | Reputation Score Classification | Configuration Wizard.
- Object ID—Shows the name of the affected object within the Category, for example, a phone number on an Access Control List or an enforcement action on a Telemarketing Call Classification.
- Action—Shows the action performed on the affected object. Add | Edit | Delete.
- Activity Details—Shows the details of the action performed on the object, including both the former value and new value. Click the twister control to the left of the Timestamp to see Activity Details.
Note:
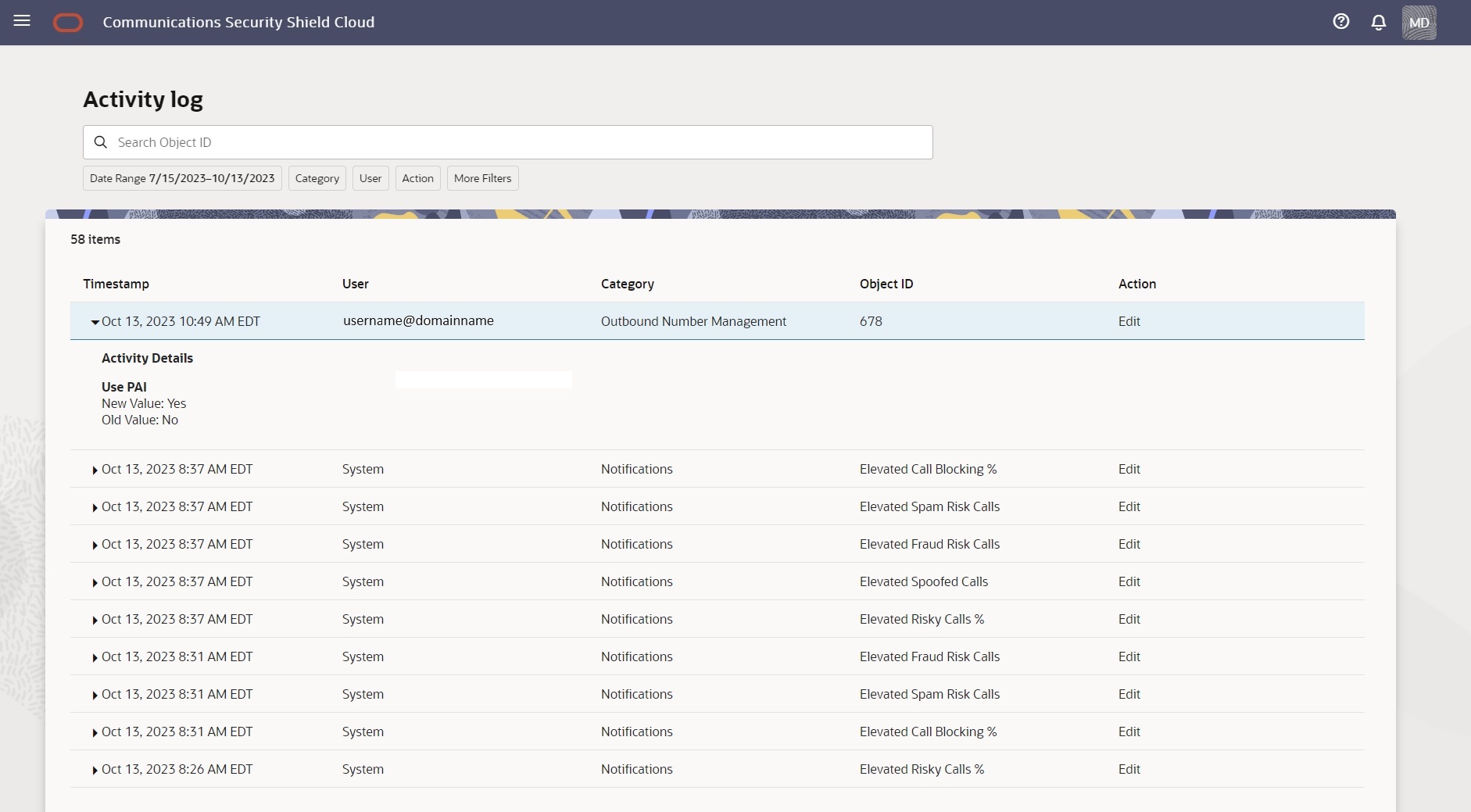
You cannot remove an activity log. Only the system can remove an activity log, which occurs when the maximum number of logs accrues (100,000).The following screen capture shows an example of an expanded log, showing the Activity Details. The Activity Details show the name of the affected configuration parameter, which is Use PAI in this example, and the Old and New values for the parameter.
The Activity Log builds the results of searches dynamically, where the search results show only users and categories for which a logged event occurred. For example, suppose you search for UsernameAbcd@companynameXyz.com and UsernameAbcd@companynameXyz.com did not perform any logged event in the time frame you selected for your search. The results will not display UsernameAbcd@companynamexyzin the results list. The same behavior applies to searching by category, where the results display only the categories in which a logged event occurred.
Multiple Users and Log Viewing
When User1 is viewing the Activity Log and User2 makes changes to a configuration, User1 does not immediately see the changes. User1 must refresh the table to see User2's changes.
Search the Activity Log Using Filter Chips
To help you find logs, the Oracle® Communications Security Shield Cloud Service (Security Shield) Activity Log tab displays a set of filter chips that you move to the Search field to help narrow your search.
Note:
The Search with filters function does not support saving searches.- Access the Activity Log page.
- Move one or more of the filter chips into the Search field.
- Date Range—Click the chip to display the date range picker, where you set a custom date range.
- User—Click the chip to display a list of users and select a user.
- Category—Click the chip to display a list of categories and select one or more categories. Choices: Topology | Reputation Score Classification | Access Control List | Notifications | Inbound Call Number Normalization
- Action—Click the chip to display a list of actions and select one or more actions. Valid Values: Add | Edit | Delete.
- More Filters—Click the chip to display a list of fixed time frames for the search. Valid Values: Last 24 Hours | Last 7 Days | Last 30 Days.
- View the logs and click the twister by the timestamps to see the details of each one.
Search the Activity Log Using the Object ID
At the top of the page, the Activity Log tab displays the Search field to help you find activity logs for a certain object that the Oracle® Communications Security Shield Cloud Service (Security Shield) logs. The term "Object" can refer to a call classification type, the name of a system in your network, an Anonymous Threat Protection setting, a phone number, or the name of an Access Control List.
- Find the object ID, such as the name of an object within the Category, for example, a phone number on an Access Control List, or an enforcement action on a Telemarketing Call Classification.
Use the following procedure to save time searching when you know the Object ID.